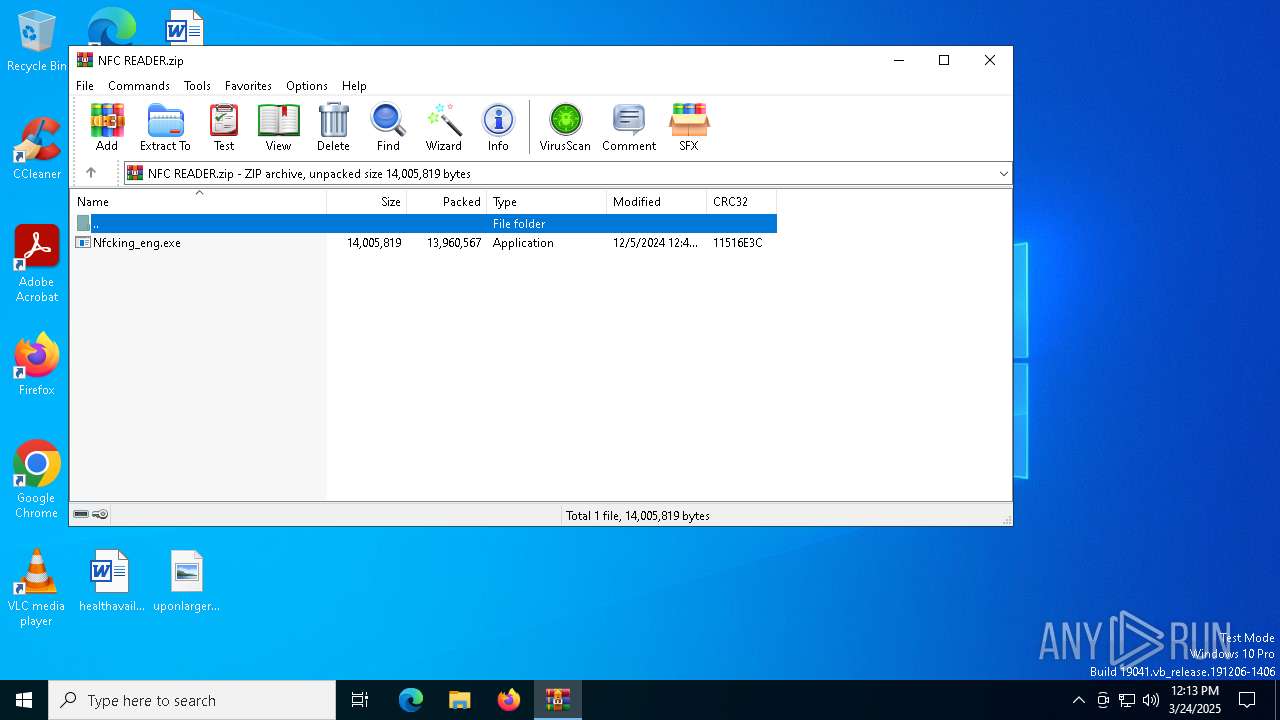
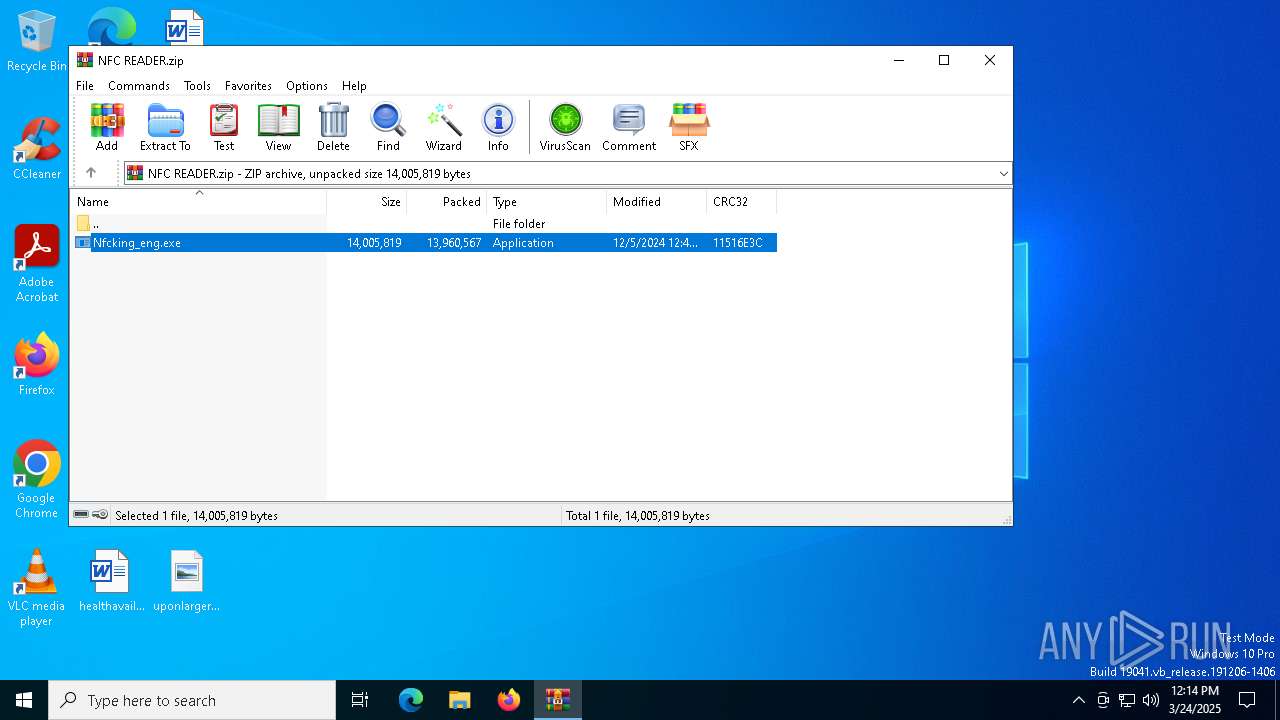
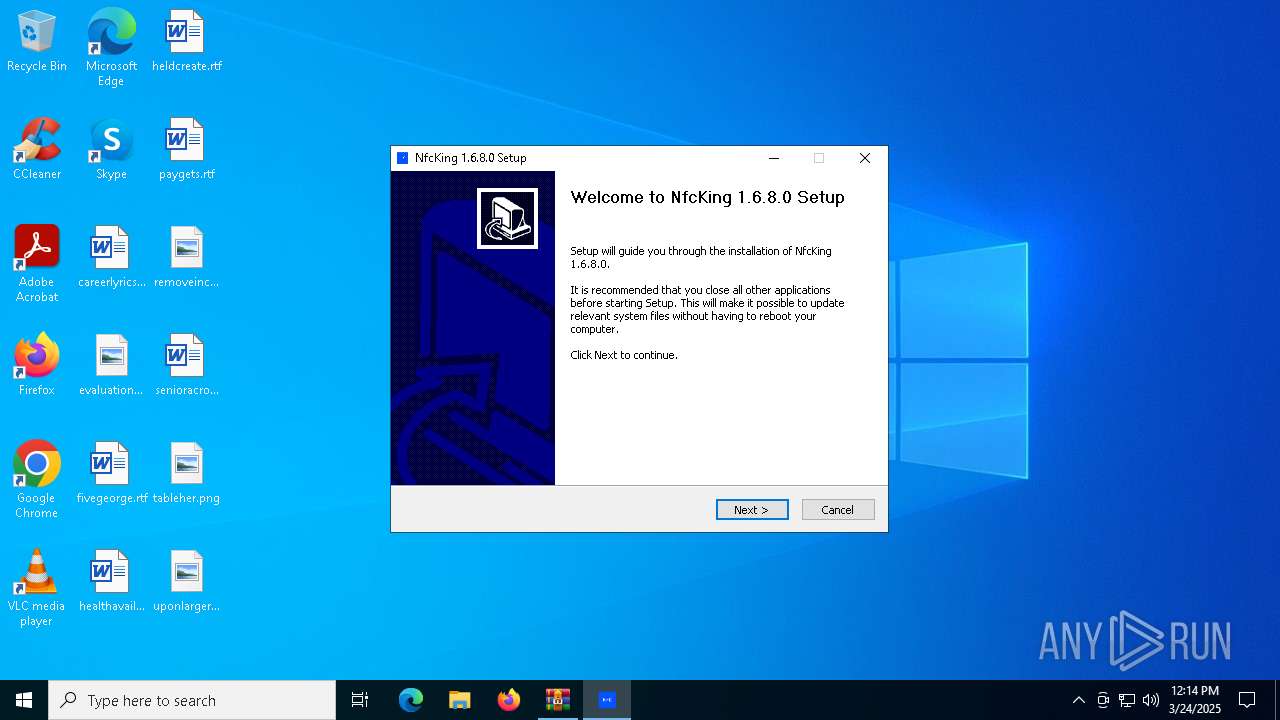
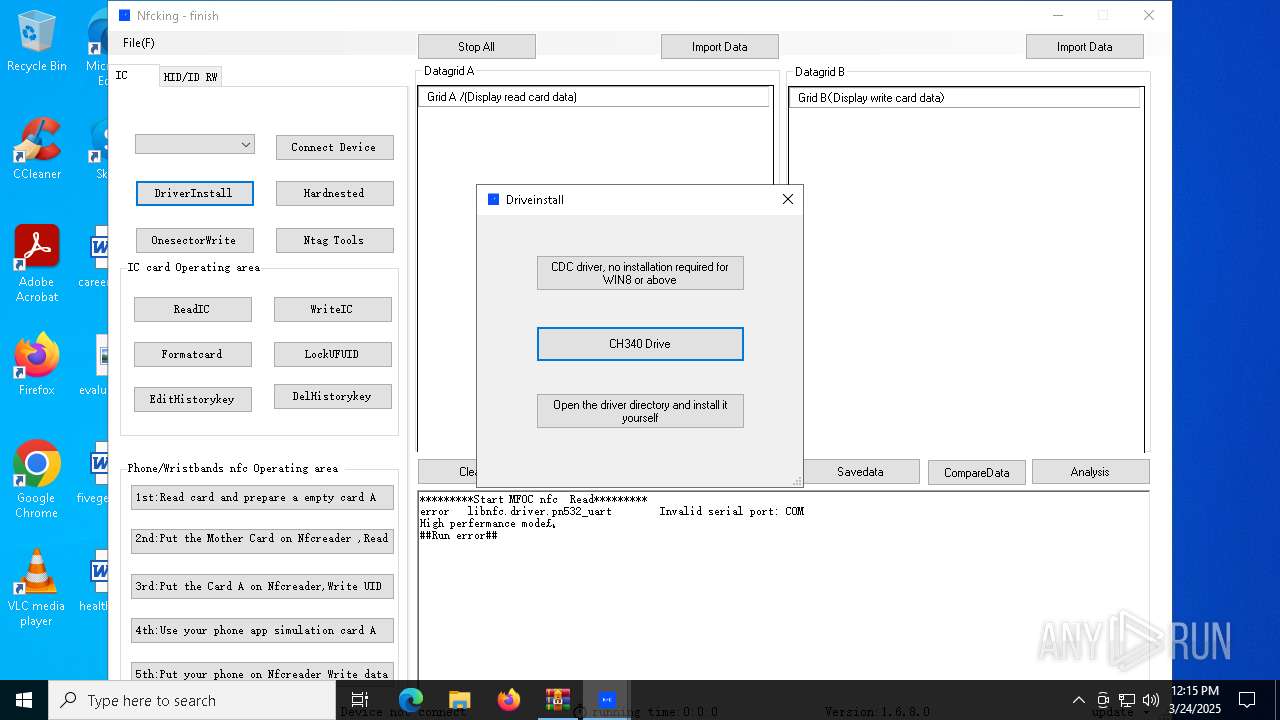
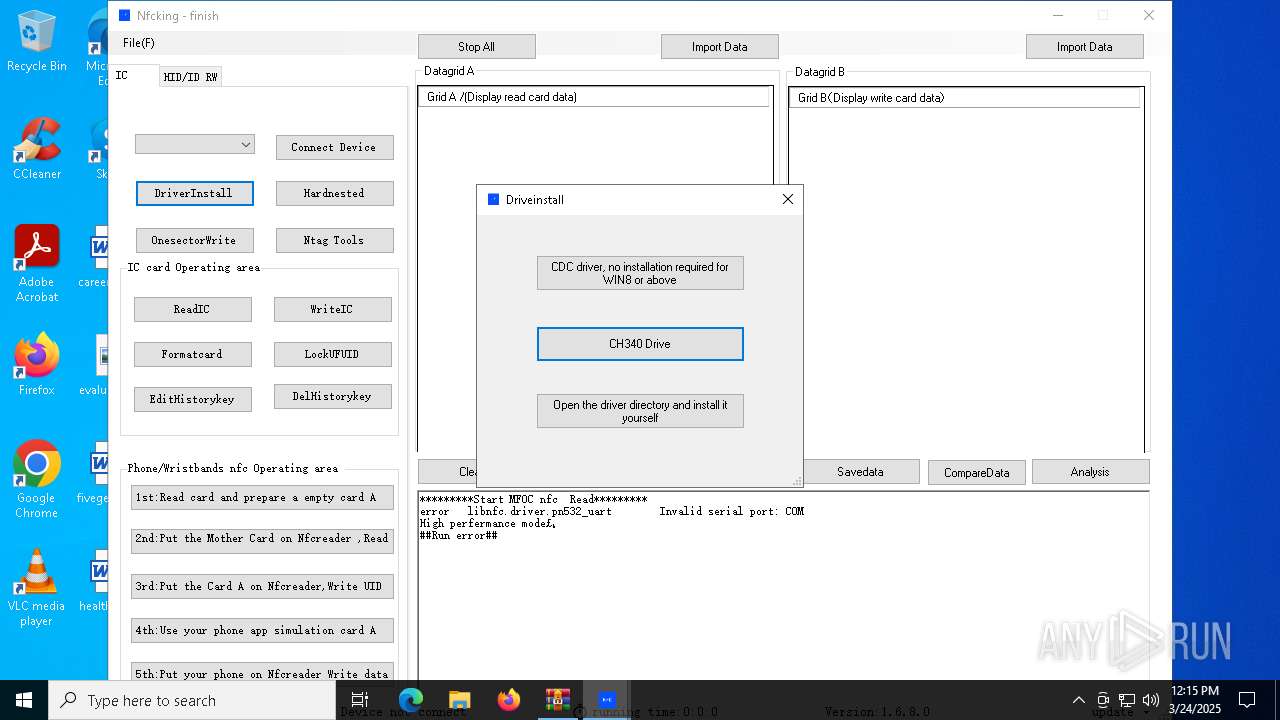
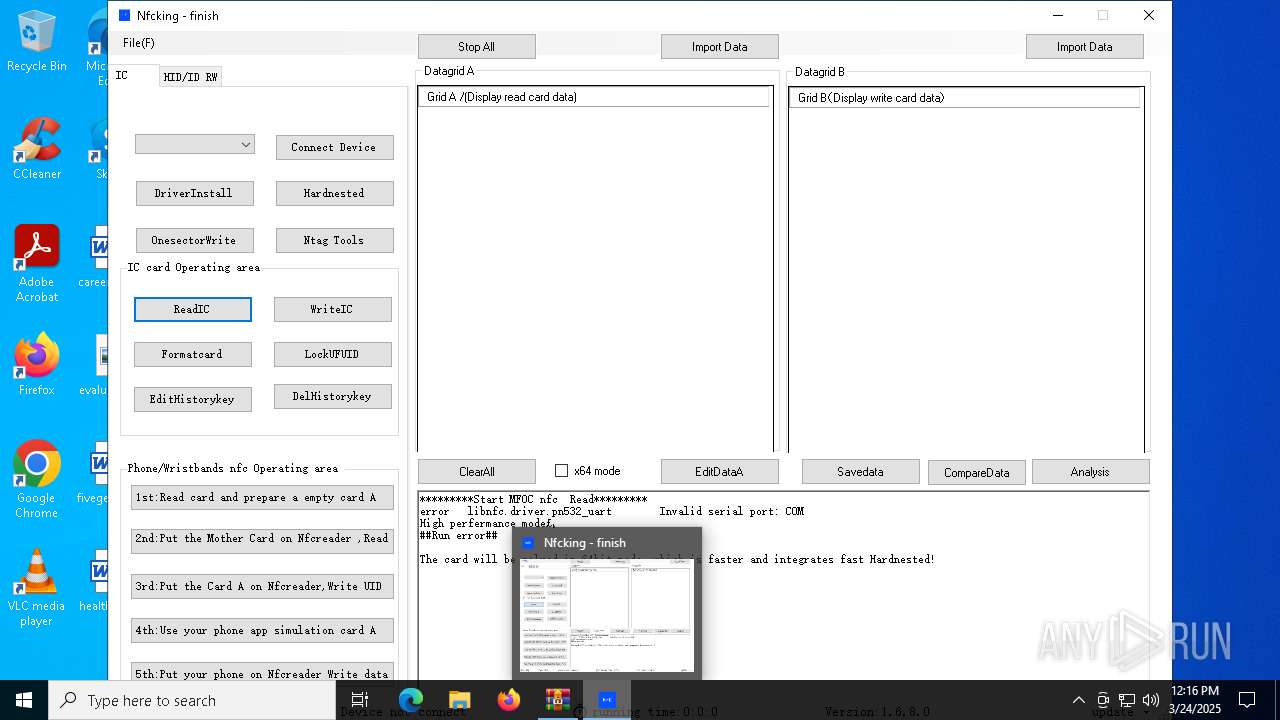
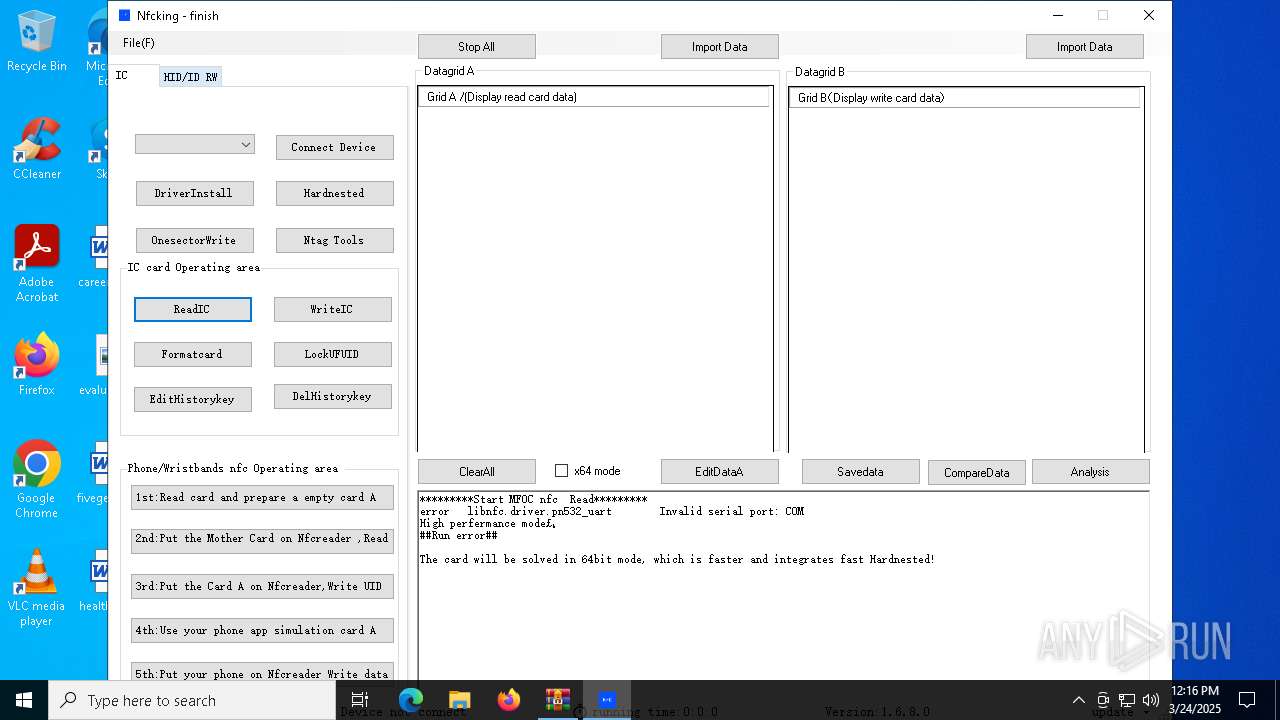
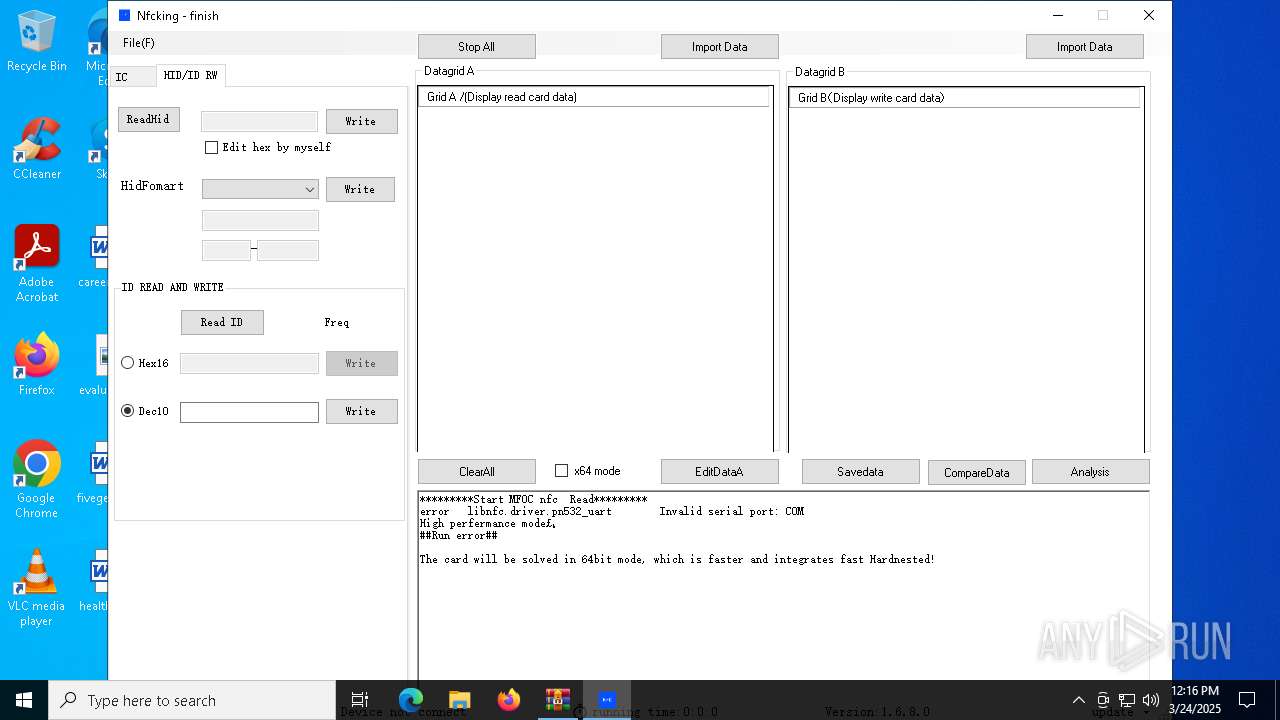
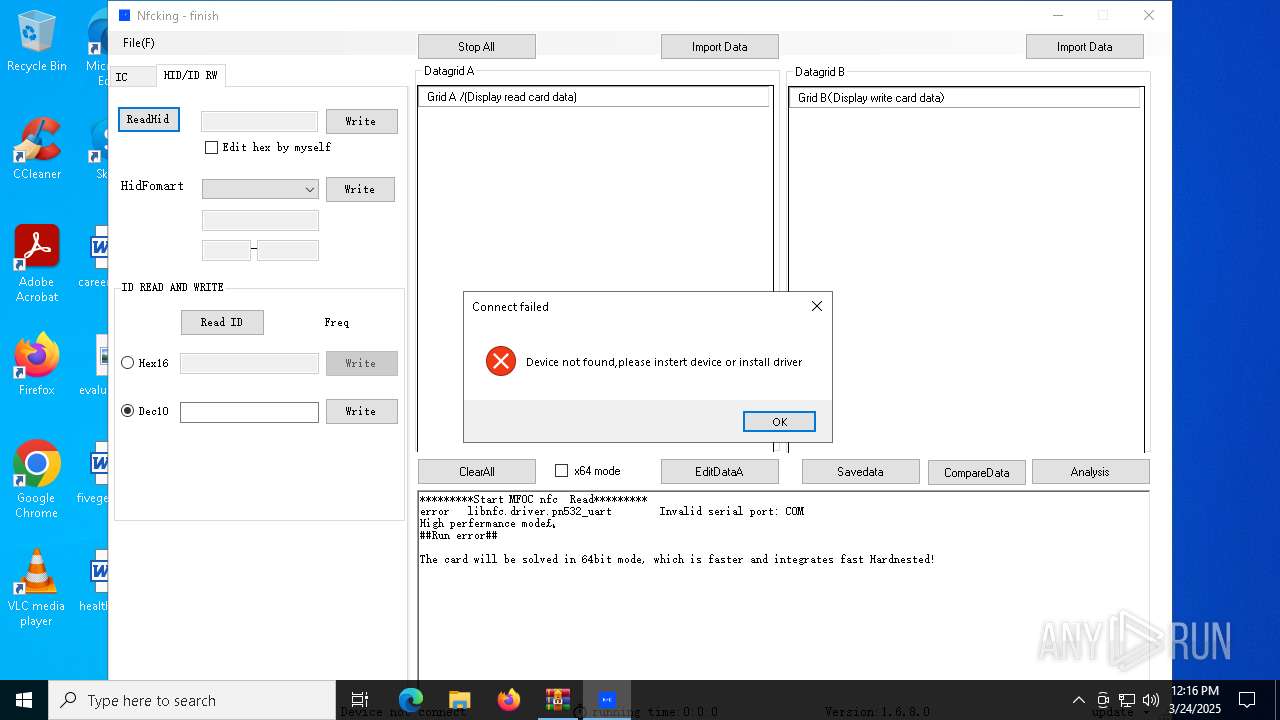
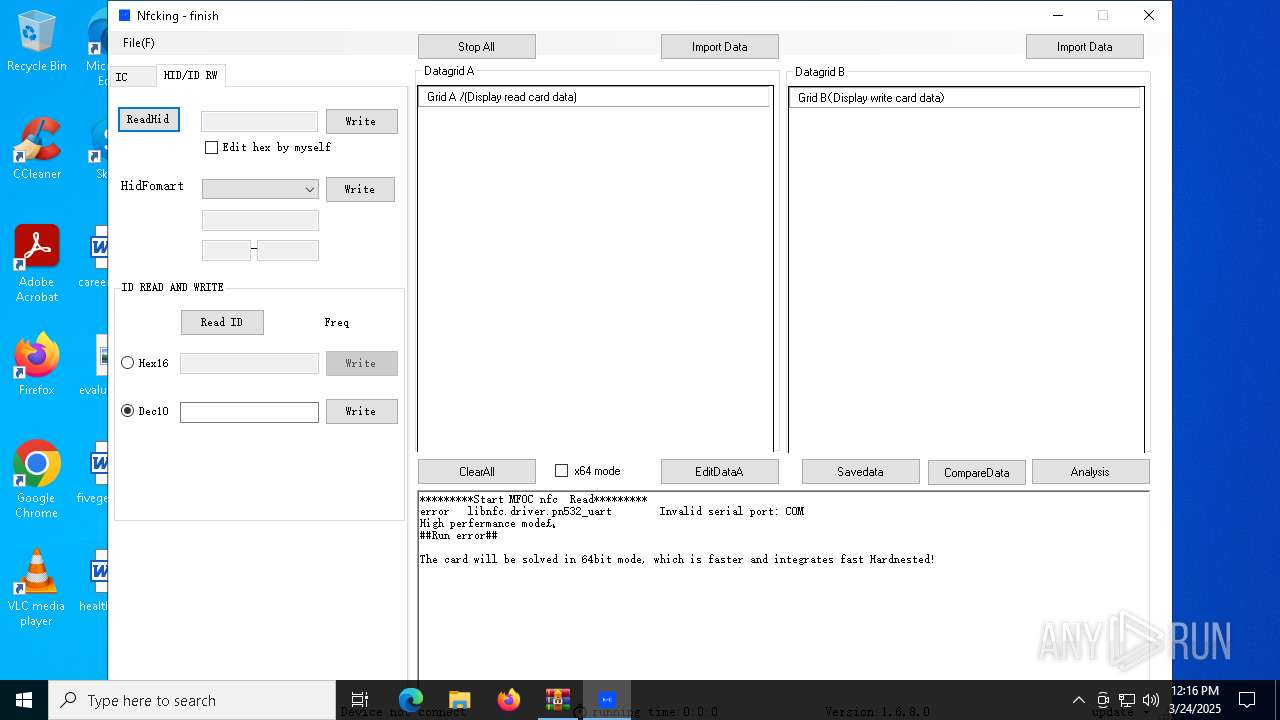
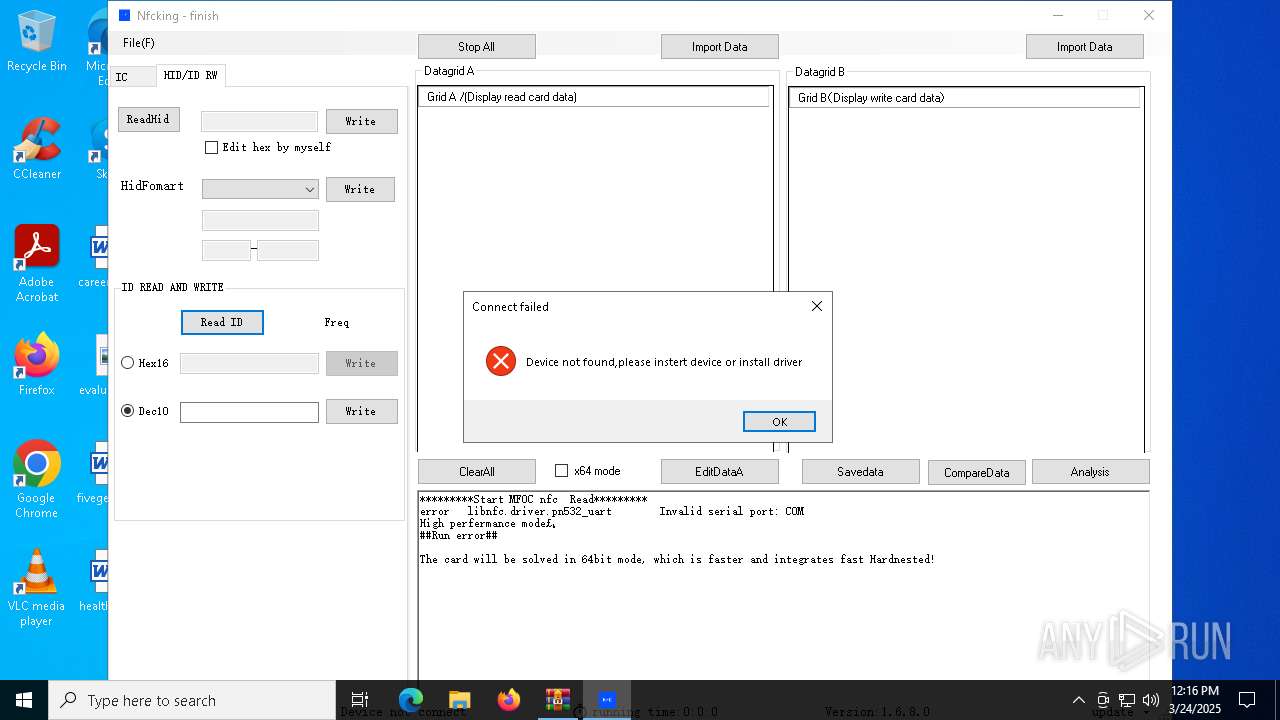
| File name: | NFC READER.zip |
| Full analysis: | https://app.any.run/tasks/4f42e6b8-e2d6-48c2-a103-88e1163d3151 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 12:13:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 1428CEF16138F7ACC606AE65B4B1B511 |
| SHA1: | 89EE8C435B150E1D60150BA3B80E2D6ACC78EEC6 |
| SHA256: | 25AAD9A377D8A9A4B2E47F672B4C9AA5886B0755EC5B836AF99222C98B631EBA |
| SSDEEP: | 196608:HxW+4UFTkLfMHiySgjFvx6qmetR5ySGG2E:HxF/tkLfMHi88HetR5ySG+ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4112)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- Nfcking_eng.exe (PID: 1272)
Creates file in the systems drive root
- Nfcking_eng.exe (PID: 1272)
The process drops C-runtime libraries
- Nfcking_eng.exe (PID: 1272)
Process drops legitimate windows executable
- Nfcking_eng.exe (PID: 1272)
Malware-specific behavior (creating "System.dll" in Temp)
- Nfcking_eng.exe (PID: 1272)
Creates a software uninstall entry
- Nfcking_eng.exe (PID: 1272)
The process creates files with name similar to system file names
- Nfcking_eng.exe (PID: 1272)
Reads security settings of Internet Explorer
- Nfcking.exe (PID: 6324)
Found regular expressions for crypto-addresses (YARA)
- Nfcking.exe (PID: 6324)
Executes application which crashes
- mfoc.exe (PID: 2420)
Drops a system driver (possible attempt to evade defenses)
- Nfcking_eng.exe (PID: 1272)
Executable content was dropped or overwritten
- Nfcking_eng.exe (PID: 1272)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4112)
Checks supported languages
- Nfcking_eng.exe (PID: 1272)
- Nfcking.exe (PID: 6324)
Manual execution by a user
- Nfcking_eng.exe (PID: 6324)
- Nfcking_eng.exe (PID: 1272)
Create files in a temporary directory
- Nfcking_eng.exe (PID: 1272)
Creates files or folders in the user directory
- Nfcking_eng.exe (PID: 1272)
- WerFault.exe (PID: 2040)
Reads the machine GUID from the registry
- Nfcking.exe (PID: 6324)
Reads the software policy settings
- slui.exe (PID: 6080)
- slui.exe (PID: 2320)
Reads the computer name
- Nfcking.exe (PID: 6324)
- Nfcking_eng.exe (PID: 1272)
The sample compiled with chinese language support
- Nfcking_eng.exe (PID: 1272)
The sample compiled with english language support
- Nfcking_eng.exe (PID: 1272)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:12:05 20:44:34 |
| ZipCRC: | 0x11516e3c |
| ZipCompressedSize: | 13960567 |
| ZipUncompressedSize: | 14005819 |
| ZipFileName: | Nfcking_eng.exe |
Total processes
148
Monitored processes
10
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | mfoc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | "C:\Users\admin\Desktop\Nfcking_eng.exe" | C:\Users\admin\Desktop\Nfcking_eng.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2040 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 2420 -s 380 | C:\Windows\SysWOW64\WerFault.exe | — | mfoc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | "nfc-bin/mfoc.exe" -O "./nfc-data/tmp/Mfoc.tmp" -x 3 -H " | C:\NfcKing\nfc-bin\mfoc.exe | Nfcking.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 4112 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\NFC READER.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6080 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6108 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6324 | "C:\Users\admin\Desktop\Nfcking_eng.exe" | C:\Users\admin\Desktop\Nfcking_eng.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6324 | "C:\NfcKing\NfcKing.exe" | C:\NfcKing\Nfcking.exe | — | Nfcking_eng.exe | |||||||||||
User: admin Company: 无锡思柯锐迪电子科技有限公司 Integrity Level: HIGH Description: NFC_TOOLS Version: 1.6.8.0 Modules
| |||||||||||||||
Total events
6 398
Read events
6 373
Write events
22
Delete events
3
Modification events
| (PID) Process: | (4112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\NFC READER.zip | |||
| (PID) Process: | (4112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4112) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1272) Nfcking_eng.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Width |
Value: 318 | |||
| (PID) Process: | (1272) Nfcking_eng.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Height |
Value: 288 | |||
Executable files
57
Suspicious files
22
Text files
45
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1272 | Nfcking_eng.exe | C:\Users\admin\AppData\Local\Temp\nsw2CBB.tmp\StartMenu.dll | executable | |
MD5:26836307758E048D1CE0AFE754D6A972 | SHA256:A6919F5F3B53A9C8C015413BABE7A9872491A2583E49BB3C261E60785C3C3534 | |||
| 1272 | Nfcking_eng.exe | C:\NfcKing\config\libnfc.conf | text | |
MD5:03C7C29DFA47390CB2223C2C990EE19A | SHA256:301EC7C5785472BECE7D5F4F1BEBB9303E515280E5F2D95DFAF931F94C20574E | |||
| 1272 | Nfcking_eng.exe | C:\NfcKing\driver\DRIVER\CH341S64.SYS | executable | |
MD5:37C29F723A1174B21E7CC6E66D7C2C37 | SHA256:A4FCDE254D367E9C469BF0BD0DBF9770916CF5CF14770722E62989727E526B65 | |||
| 1272 | Nfcking_eng.exe | C:\NfcKing\Be.Windows.Forms.HexBox.dll | executable | |
MD5:7A6A1DEAFC87DDA48858F80B3C3EEC0F | SHA256:ED3AA1A6C806D4229EF3C48B6AC1CE9D07BAD53E9ED4BC21BEF728FD373C5CA3 | |||
| 1272 | Nfcking_eng.exe | C:\NfcKing\driver\DRIVER\CH341SER.INF | binary | |
MD5:E0C91A52D8EC671A970B09BA6C1E86D1 | SHA256:520531702508875890B3924205D774B5A5C1C71C8A2E4A576AFBD72CF724BC85 | |||
| 1272 | Nfcking_eng.exe | C:\NfcKing\driver\Cdc_com.exe | executable | |
MD5:182D502ACF9BE563D439550ED89AE54F | SHA256:8501A7D62A40C4468801052A7B38DD19B382419338F01721C778FE6D36C94F61 | |||
| 1272 | Nfcking_eng.exe | C:\NfcKing\driver\DRIVER\CH341SER.VXD | executable | |
MD5:BE7438420F1DA854917F58CAD557476D | SHA256:2A946F316EDD7E1185DEEAFDC2DE52B2D2843198BE098A724233C12F9CCD0DAE | |||
| 1272 | Nfcking_eng.exe | C:\NfcKing\Crapto1Sharp.dll | executable | |
MD5:C8903D18A45AB817D572B6B2CF426084 | SHA256:5E0BCFA74CB4643C6B21B3C471C773E75CE824E1D9EC265F153080F6B4F84DC4 | |||
| 1272 | Nfcking_eng.exe | C:\NfcKing\driver\DRIVER\CH341S98.SYS | executable | |
MD5:B6F4A83911336E84BEAD8F8905285FAB | SHA256:0ECD1222627271EA31D3B64796992B6DAF5133D64CC26D43B3873CBE32FD59CB | |||
| 1272 | Nfcking_eng.exe | C:\NfcKing\driver\CH341SER.EXE | executable | |
MD5:05A4D6A351F7990586E218D5FC3DB75E | SHA256:391A615225980F5E93BB9A6196F82A6B03B67A001B9DD3A64353F4B0BA2884B8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
25
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.16.164.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.34:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
904 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4776 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
904 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.34:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 2.16.164.34:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 20.198.162.76:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
6544 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
4776 | backgroundTaskHost.exe | 20.74.47.205:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |