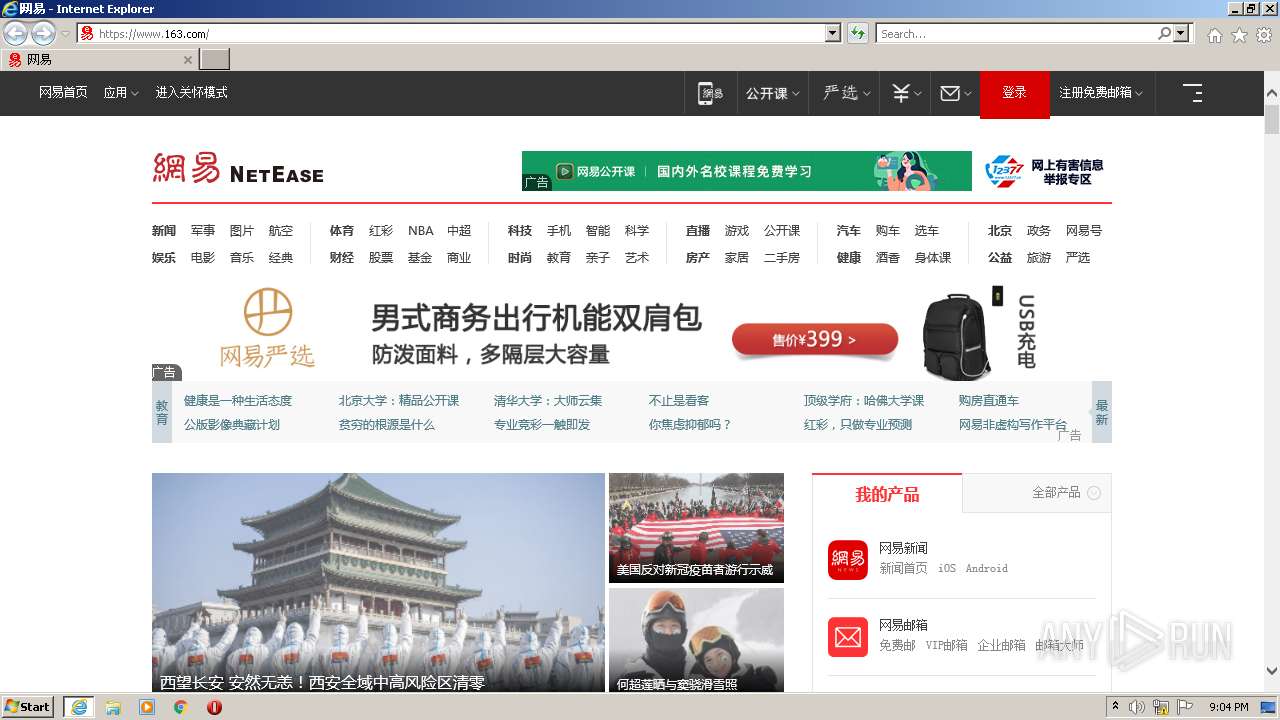
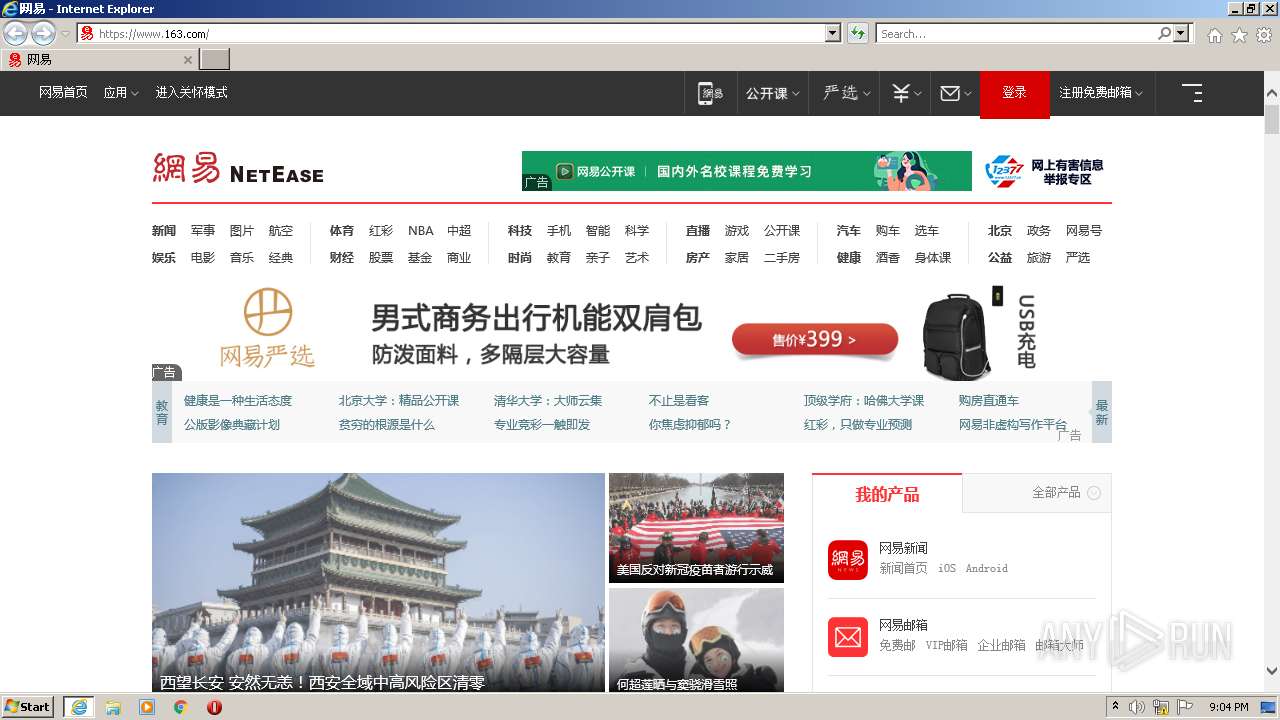
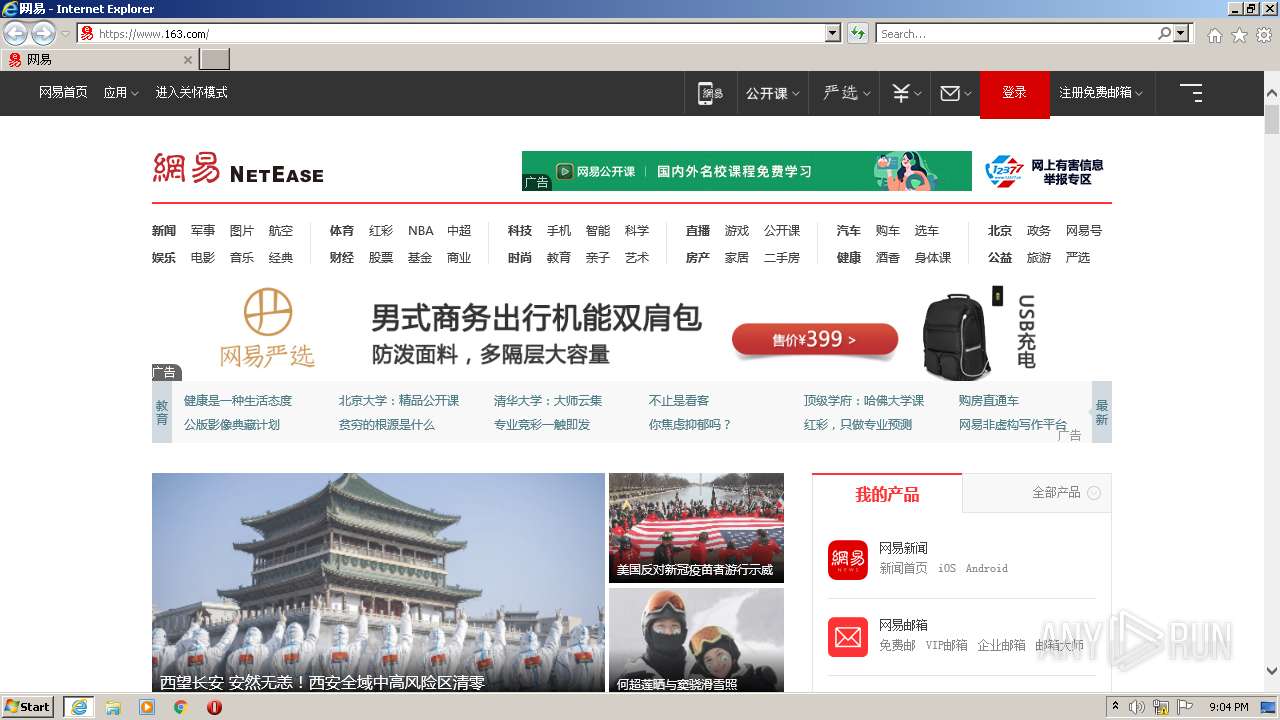
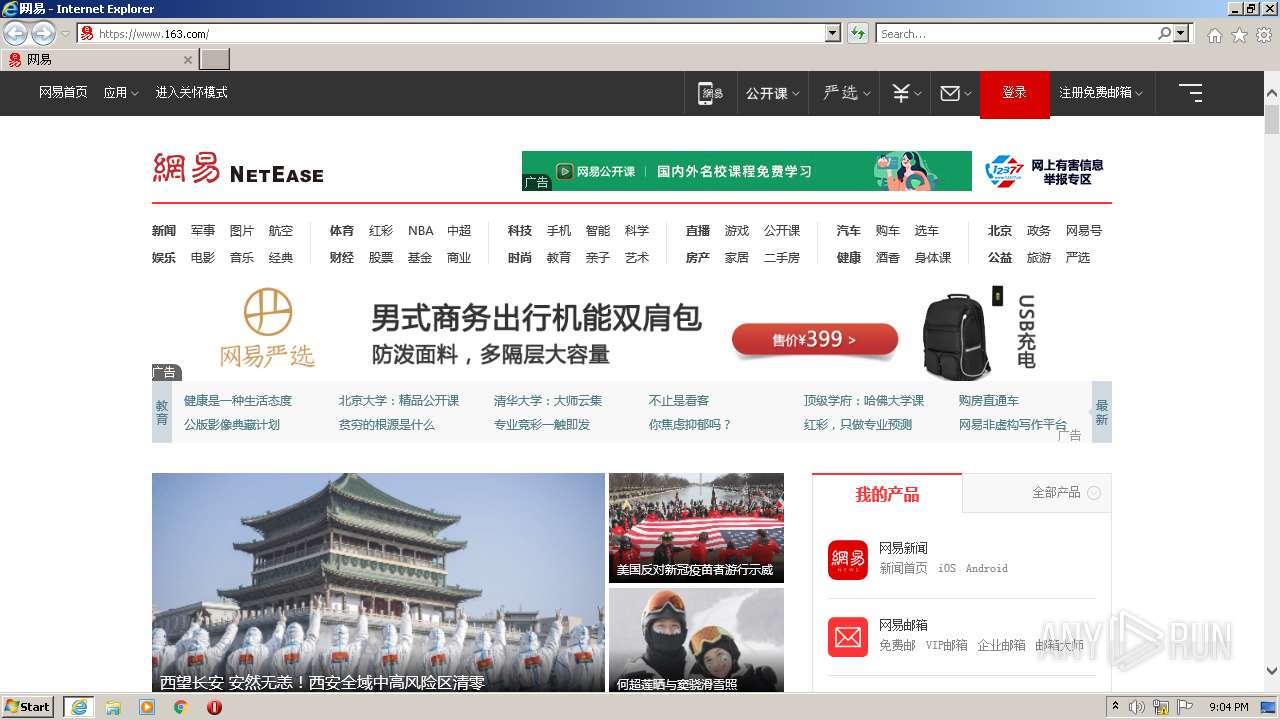
| URL: | https://www.163.com/ |
| Full analysis: | https://app.any.run/tasks/d0574a5a-3c6a-4f59-8701-007840bb182b |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 21:03:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A417BC4BD4FF4070E58B0C4F2DA08C48 |
| SHA1: | 41A2FFF99877861504C7AE82497592AEE4AAD51D |
| SHA256: | 25A878BBC3FE9722335F46B69AC9297B1C6A8EB7DEAFED0F11E3A3DB33FBFF42 |
| SSDEEP: | 3:N8DSLZR:2OLZR |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2504)
INFO
Reads the computer name
- iexplore.exe (PID: 1408)
- iexplore.exe (PID: 2504)
Checks supported languages
- iexplore.exe (PID: 2504)
- iexplore.exe (PID: 1408)
Checks Windows Trust Settings
- iexplore.exe (PID: 2504)
- iexplore.exe (PID: 1408)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 2504)
Application launched itself
- iexplore.exe (PID: 1408)
Reads settings of System Certificates
- iexplore.exe (PID: 2504)
- iexplore.exe (PID: 1408)
Reads internet explorer settings
- iexplore.exe (PID: 2504)
Creates files in the user directory
- iexplore.exe (PID: 2504)
Changes internet zones settings
- iexplore.exe (PID: 1408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
37
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1408 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.163.com/" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2504 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1408 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
17 218
Read events
16 877
Write events
341
Delete events
0
Modification events
| (PID) Process: | (1408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30937445 | |||
| (PID) Process: | (1408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30937445 | |||
| (PID) Process: | (1408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1408) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
24
Text files
322
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2504 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2504 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 2504 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D56B4E335E80143B4541C1723368A393_7B2E01AECDFCD0266F9E901FBB504576 | binary | |
MD5:— | SHA256:— | |||
| 2504 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\3FE2BD01AB6BC312BF0DADE7F797388F_F7F9B7BDCC367A8E3539D28F7D4D4BA2 | der | |
MD5:— | SHA256:— | |||
| 2504 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D56B4E335E80143B4541C1723368A393_7B2E01AECDFCD0266F9E901FBB504576 | der | |
MD5:— | SHA256:— | |||
| 2504 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\3FE2BD01AB6BC312BF0DADE7F797388F_F2379ADA3CBEBD919394FF2BE001D546 | binary | |
MD5:— | SHA256:— | |||
| 2504 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\K719AOEL.htm | html | |
MD5:— | SHA256:— | |||
| 1408 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2504 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8F8712BCE78D28F9C5E3E950CD93EADA_8B635952FC4E9ABE537360E5F156E4E7 | der | |
MD5:— | SHA256:— | |||
| 2504 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\FA0A17BC17FF10008872A7205D0D43E2_608DEF97DFACECDA8E97C6F270153A4F | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
145
DNS requests
41
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2504 | iexplore.exe | GET | 200 | 47.246.46.205:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRc9osyRBU0ybHlZFuU293oOS1mlwQUBr2mm2B5UDG%2B1akCSqDQlVOLLzQCEALTRbSmAuqHYB5ltnll2bM%3D | US | der | 471 b | whitelisted |
2504 | iexplore.exe | GET | 200 | 47.246.46.205:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAsTYrbuap0%2Blokw8W4gfTk%3D | US | der | 471 b | whitelisted |
2504 | iexplore.exe | GET | 200 | 47.246.46.205:80 | http://ocsp.digicert.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAL34fmCutAJr%2FR9yVdBsvY%3D | US | der | 471 b | whitelisted |
2504 | iexplore.exe | GET | 200 | 157.185.155.6:80 | http://cms-bucket.ws.126.net/2022/0124/88e1471bj00r66xs10016c000550038c.jpg?imageView&thumbnail=185y116&quality=85 | US | image | 5.86 Kb | malicious |
2504 | iexplore.exe | GET | 200 | 157.185.155.6:80 | http://cms-bucket.ws.126.net/2022/0124/daeae6b2j00r66y4r006ac000sg00izc.jpg?imageView&thumbnail=380y187&quality=100 | US | image | 34.9 Kb | malicious |
2504 | iexplore.exe | GET | 200 | 163.171.128.148:80 | http://nimg.ws.126.net/?url=http://videoimg.ws.126.net/cover/20220123/HetVpxKqX_cover.jpg&thumbnail=380x2147483647&quality=75&type=jpg | US | image | 10.5 Kb | malicious |
2504 | iexplore.exe | GET | 200 | 79.133.177.225:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAoEcNCWvIoSyJCm34Ju7Es%3D | RU | der | 471 b | whitelisted |
2504 | iexplore.exe | GET | 200 | 79.133.177.225:80 | http://ocsp.dcocsp.cn/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSmVYFXwi%2FRq9wx3PKhB8lC%2FFYUyAQUkZ9eMRWuEJ%2BtYMH3wcyqSDQvDCYCEAvcoGL5m7sUP8xwGUHQxBA%3D | RU | der | 471 b | whitelisted |
2504 | iexplore.exe | GET | 200 | 157.185.155.6:80 | http://cms-bucket.ws.126.net/2022/0124/5c8247d6j00r66y3x0029c000sg00iwc.jpg?imageView&thumbnail=185y116&quality=100&quality=100 | US | image | 9.91 Kb | malicious |
2504 | iexplore.exe | GET | 200 | 157.185.155.6:80 | http://cms-bucket.ws.126.net/2022/0124/b7b48c60p00r66va500bec000ak0057c.png?imageView&thumbnail=453y225&quality=85 | US | image | 54.7 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2504 | iexplore.exe | 163.171.128.148:443 | www.163.com | — | US | malicious |
2504 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
2504 | iexplore.exe | 47.246.46.205:80 | ocsp.digicert.cn | — | US | unknown |
— | — | 163.171.128.148:443 | www.163.com | — | US | malicious |
1408 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
1408 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2504 | iexplore.exe | 79.133.177.225:80 | ocsp.dcocsp.cn | SOT LINE Limited Company | RU | malicious |
— | — | 163.171.128.148:80 | www.163.com | — | US | malicious |
2504 | iexplore.exe | 157.185.155.6:80 | cms-bucket.ws.126.net | — | US | unknown |
2504 | iexplore.exe | 163.171.128.148:80 | www.163.com | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.163.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.cn |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
static.ws.126.net |
| malicious |
urswebzj.nosdn.127.net |
| malicious |
nimg.ws.126.net |
| malicious |
cms-bucket.ws.126.net |
| malicious |