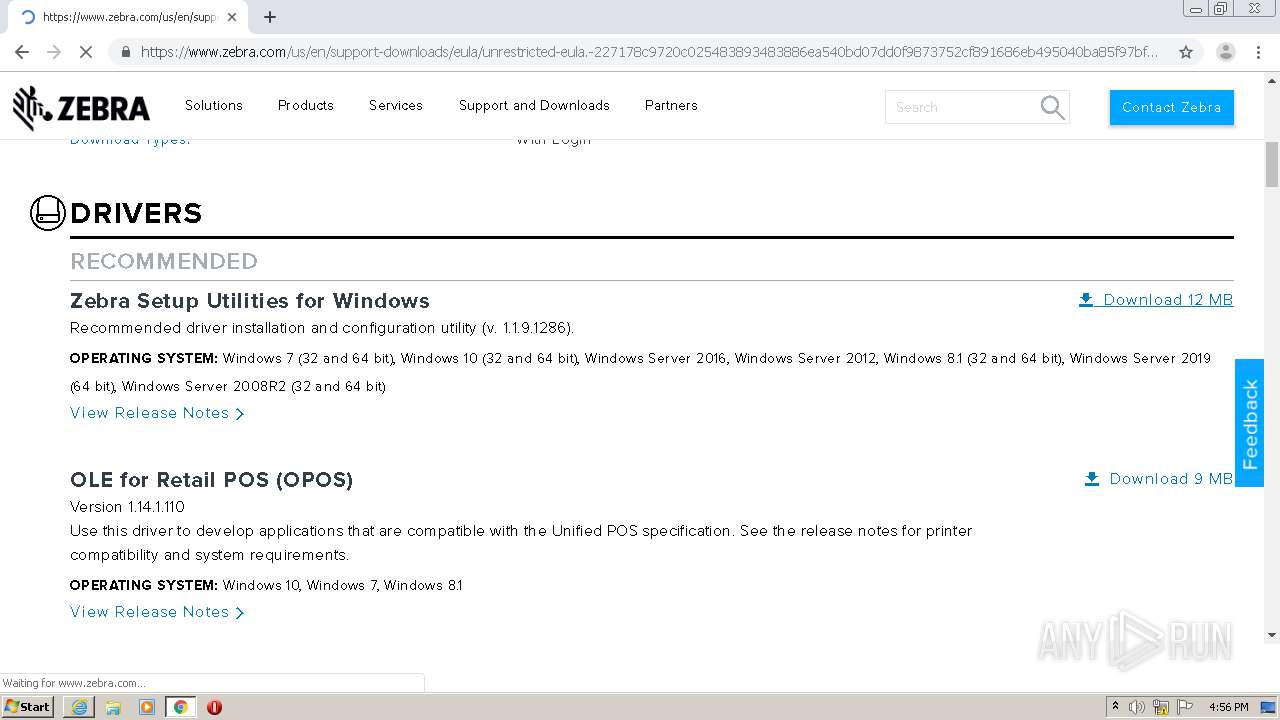
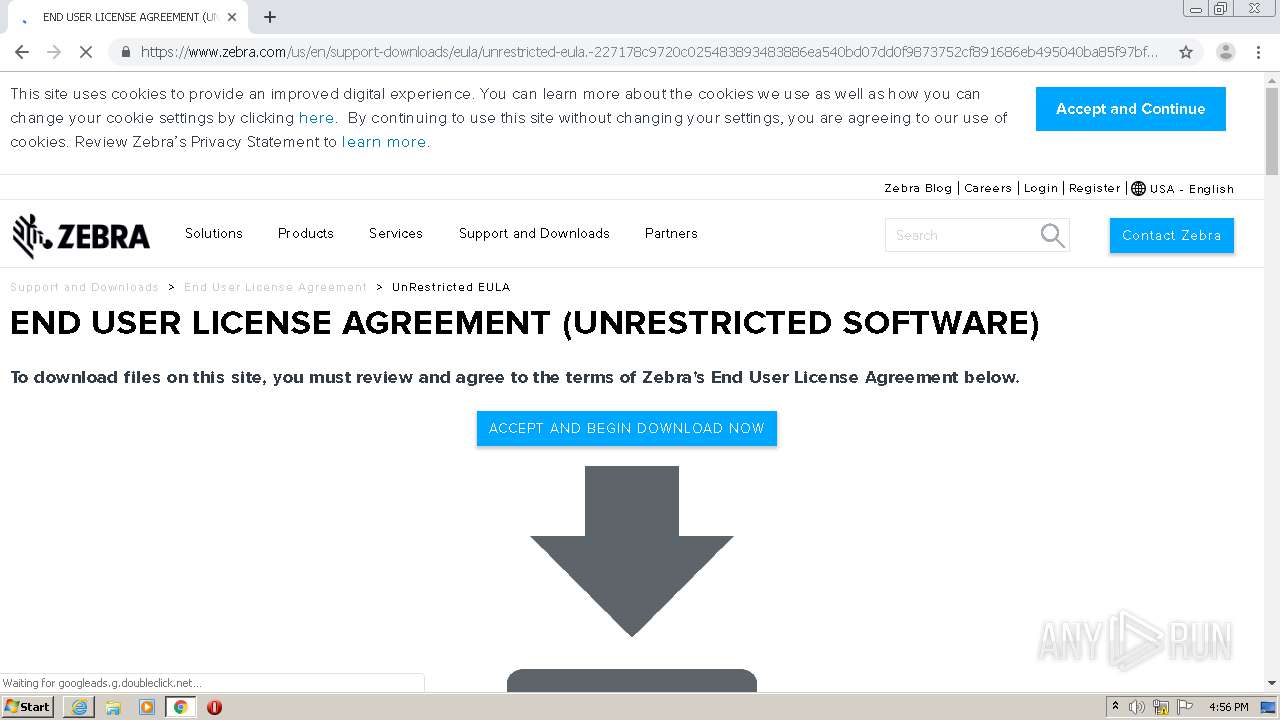
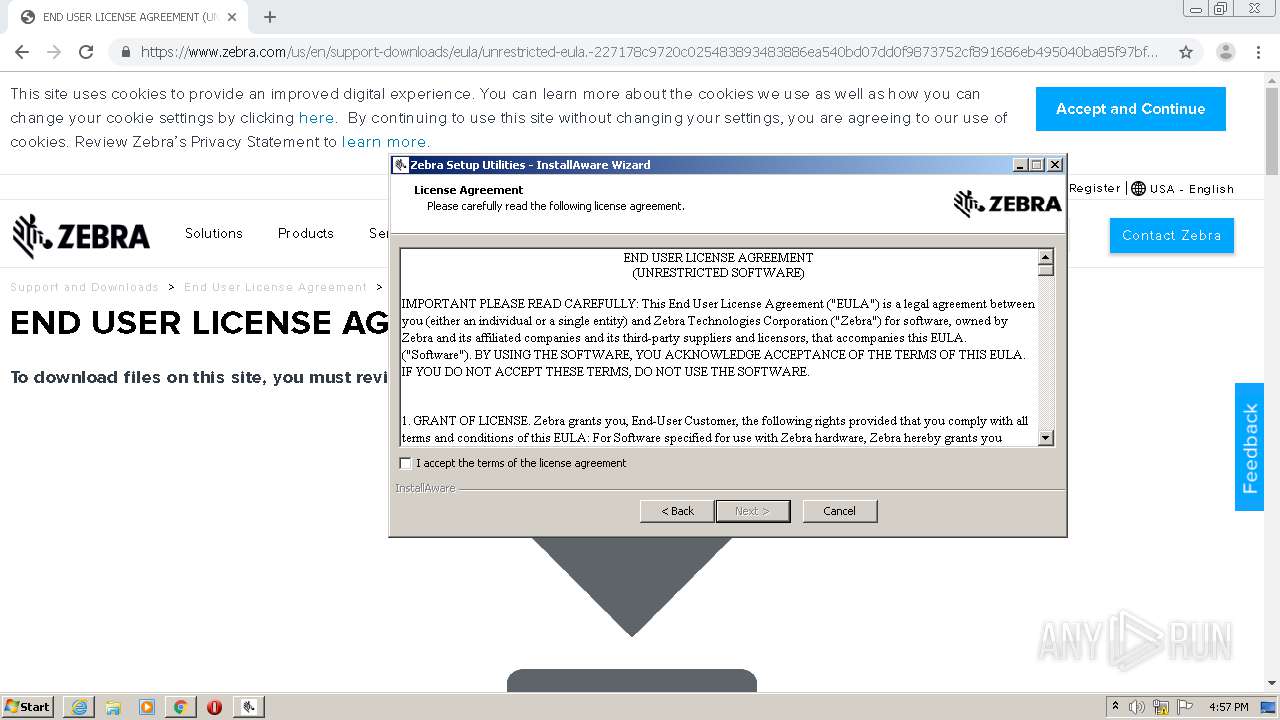
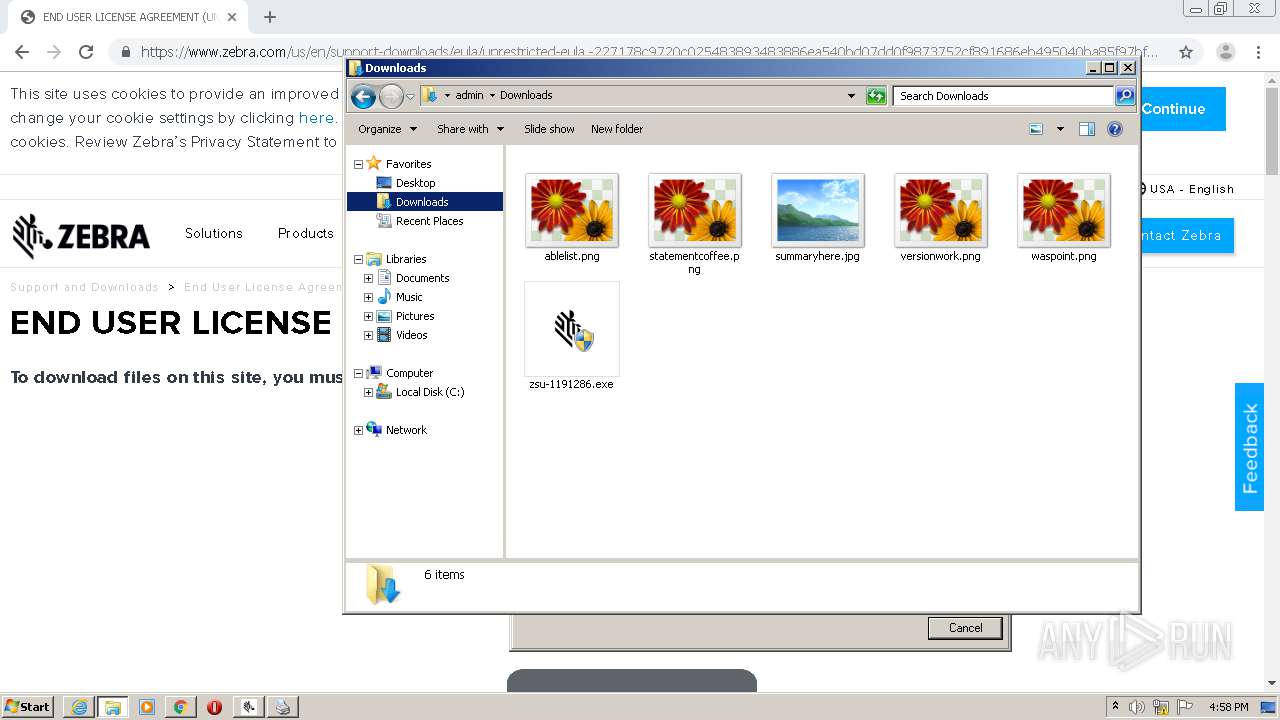
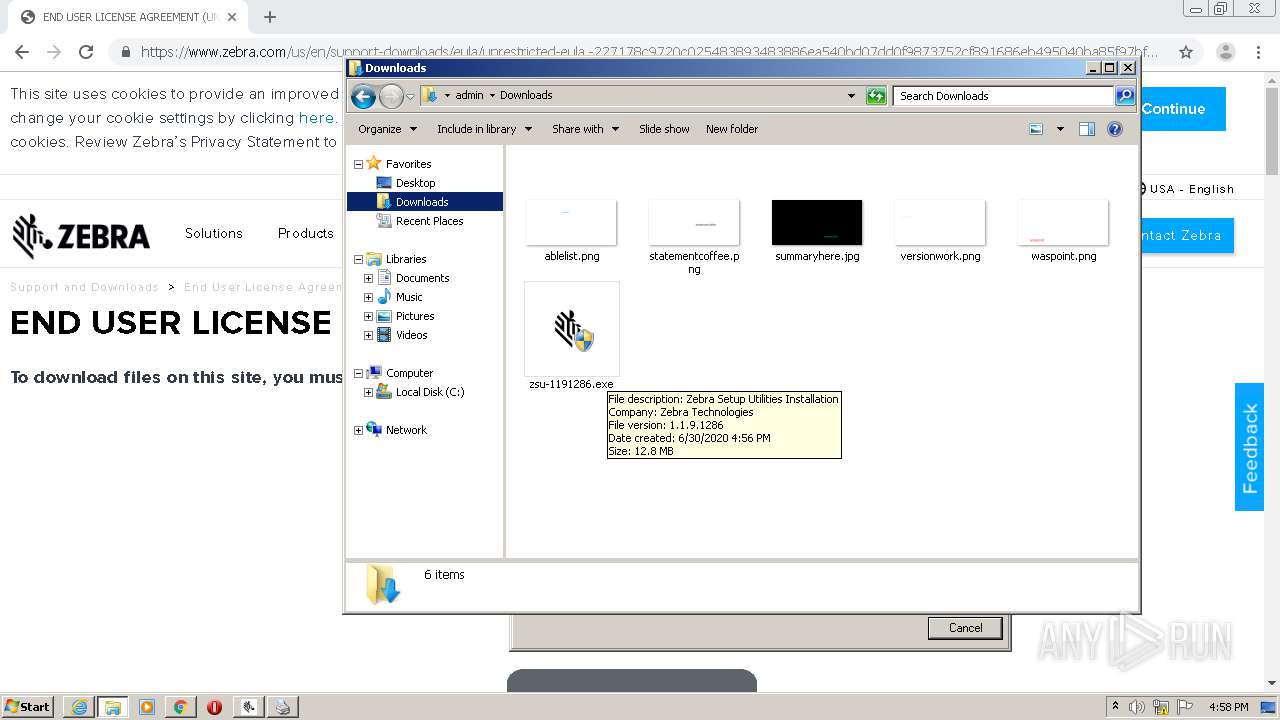
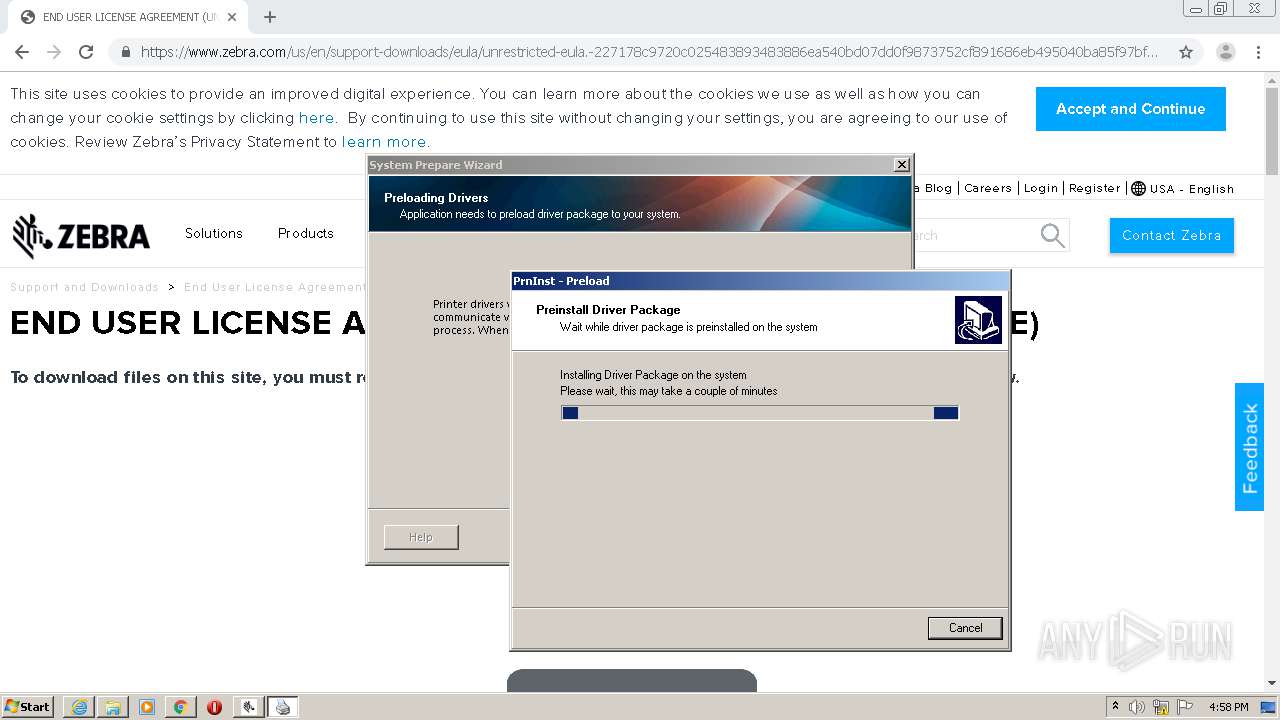
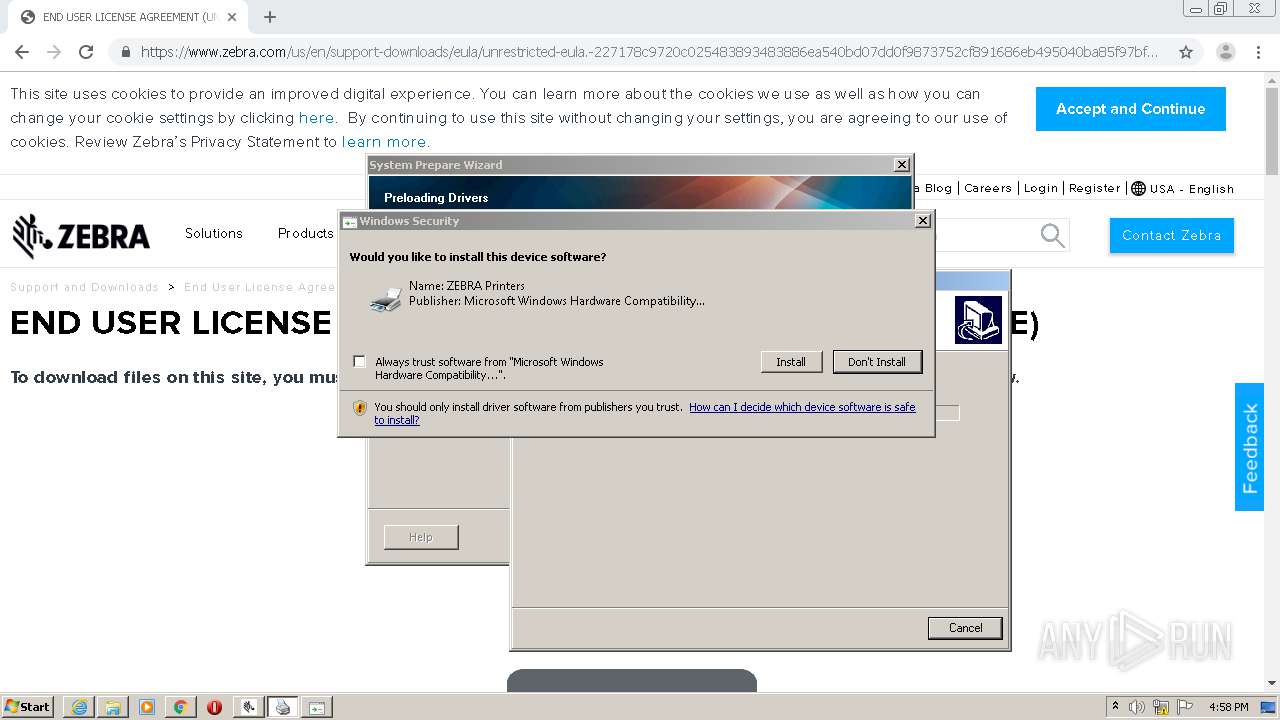
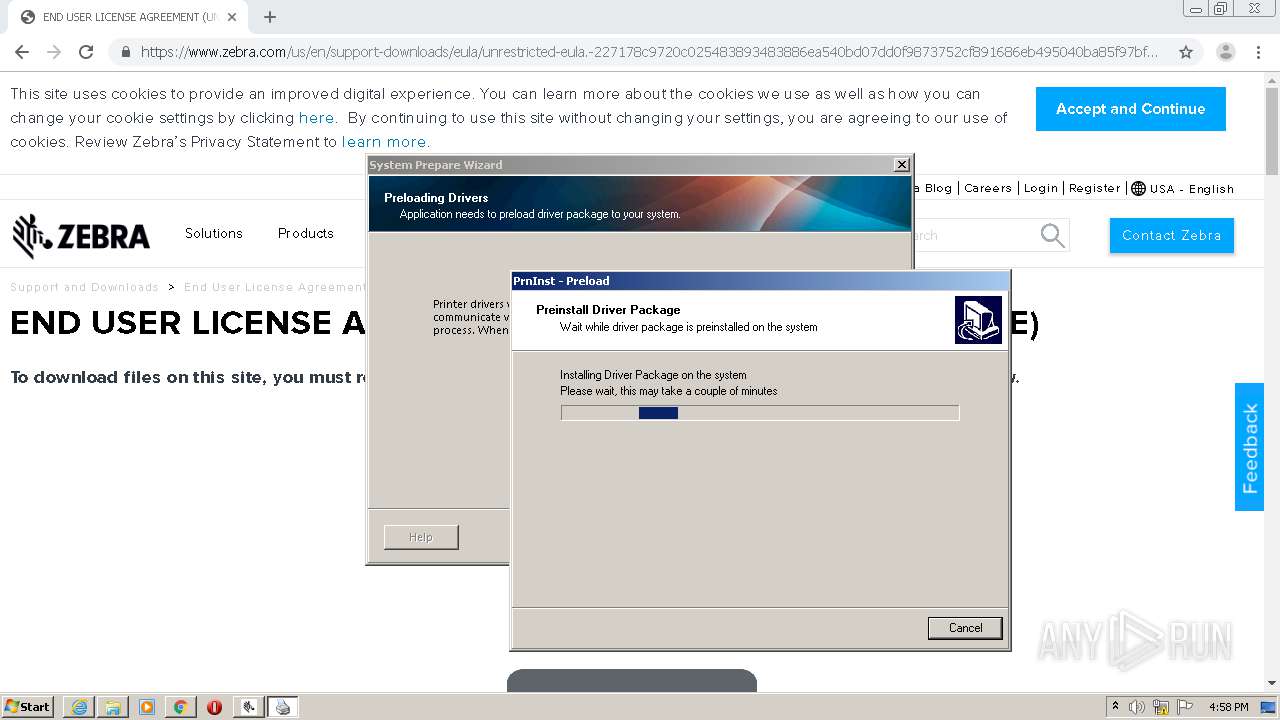
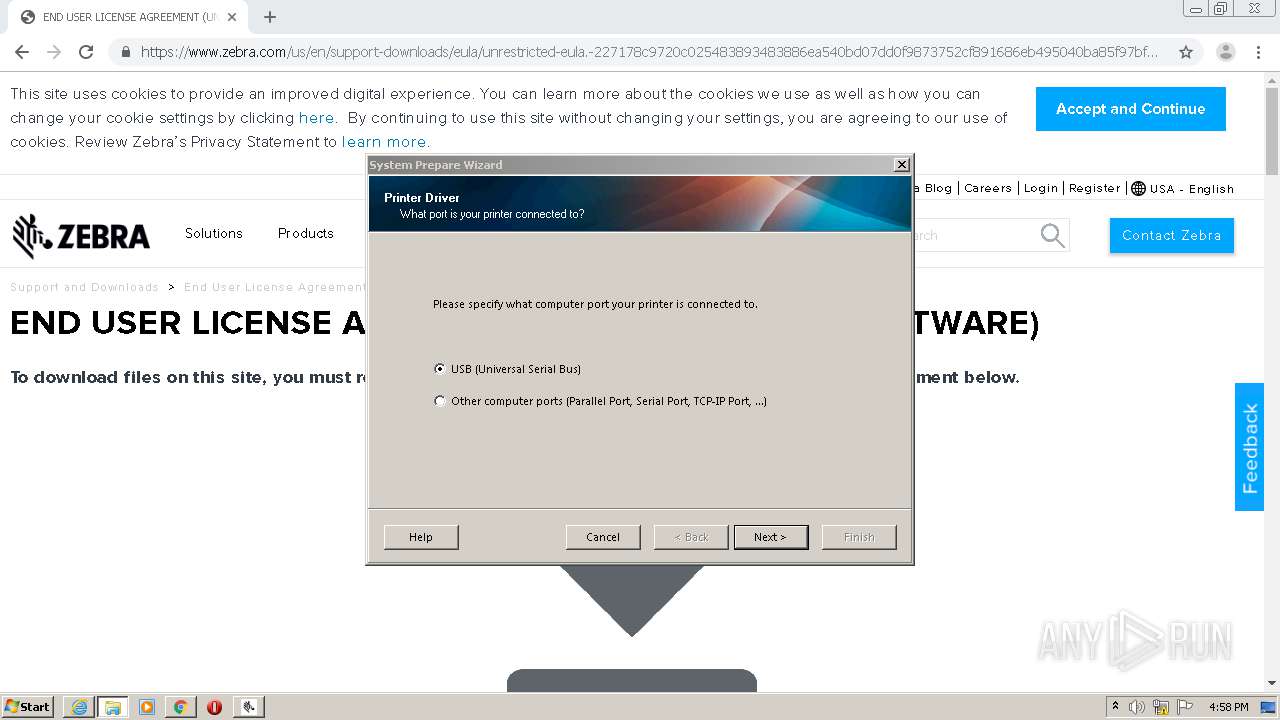
| URL: | https://www.zebra.com/us/en/support-downloads/eula/unrestricted-eula.-227178c9720c025483893483886ea540bd07dd0f9873752cf891686eb495040ba85f97bf163f9fdbc62ce8bbe325bdf8d7c463f51a4ad0a6a906cd075f933a451ef3005a5bc81cd05c75f414a9073d4b71395853b10f27e.html# |
| Full analysis: | https://app.any.run/tasks/96204593-d8b7-4535-b74d-08eedbb167d6 |
| Verdict: | Malicious activity |
| Analysis date: | June 30, 2020, 15:54:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 5EE1C884B43211D87B355C4EEE375E39 |
| SHA1: | E94B5C9383617C6E19277B05F6DBD6A4F3DECDF9 |
| SHA256: | 259F95C3D5B439E1709FE7FF90EA749EB03B77227CAF97C904F624DA9F34735A |
| SSDEEP: | 6:2OLoyoY2VKnRuEEgoZSWog6g+DANPuEWSHSLtDn:2RQRuEEgosyoAduEI |
MALICIOUS
Application was dropped or rewritten from another process
- zsu-1191286.exe (PID: 2784)
- zsu-1191286.exe (PID: 2584)
- zsu-1-1-9-1286.exe (PID: 3764)
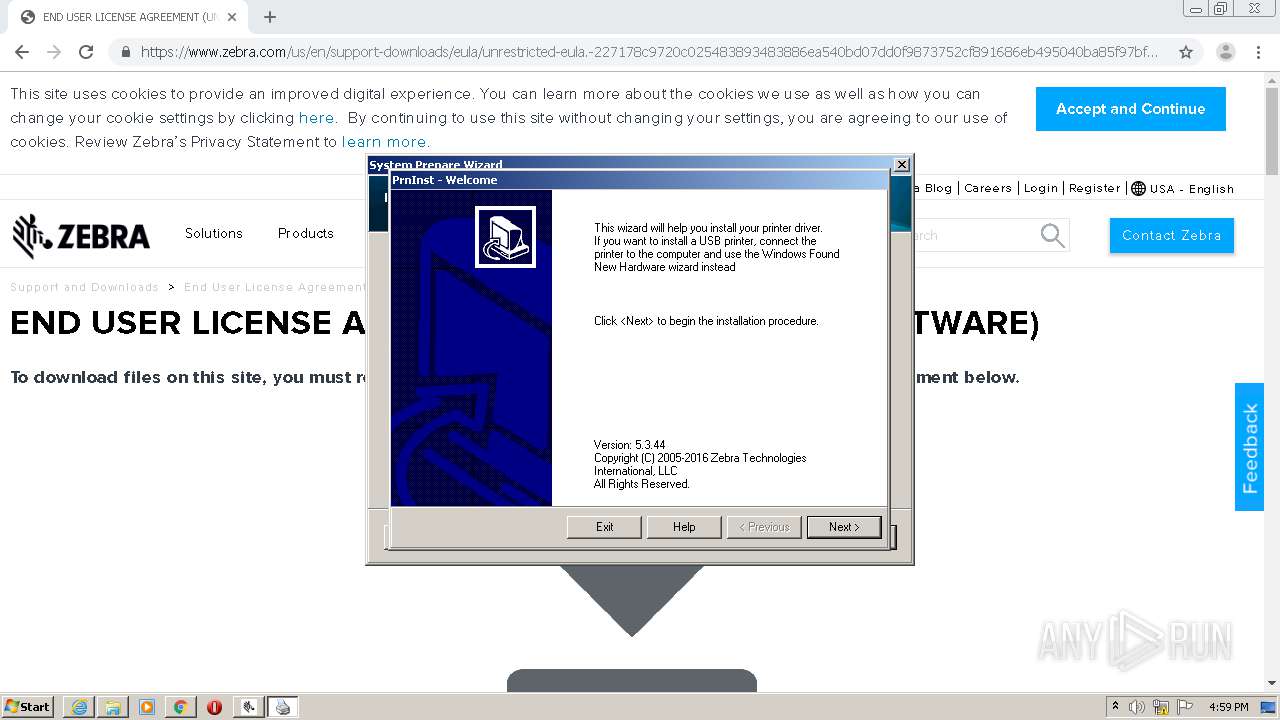
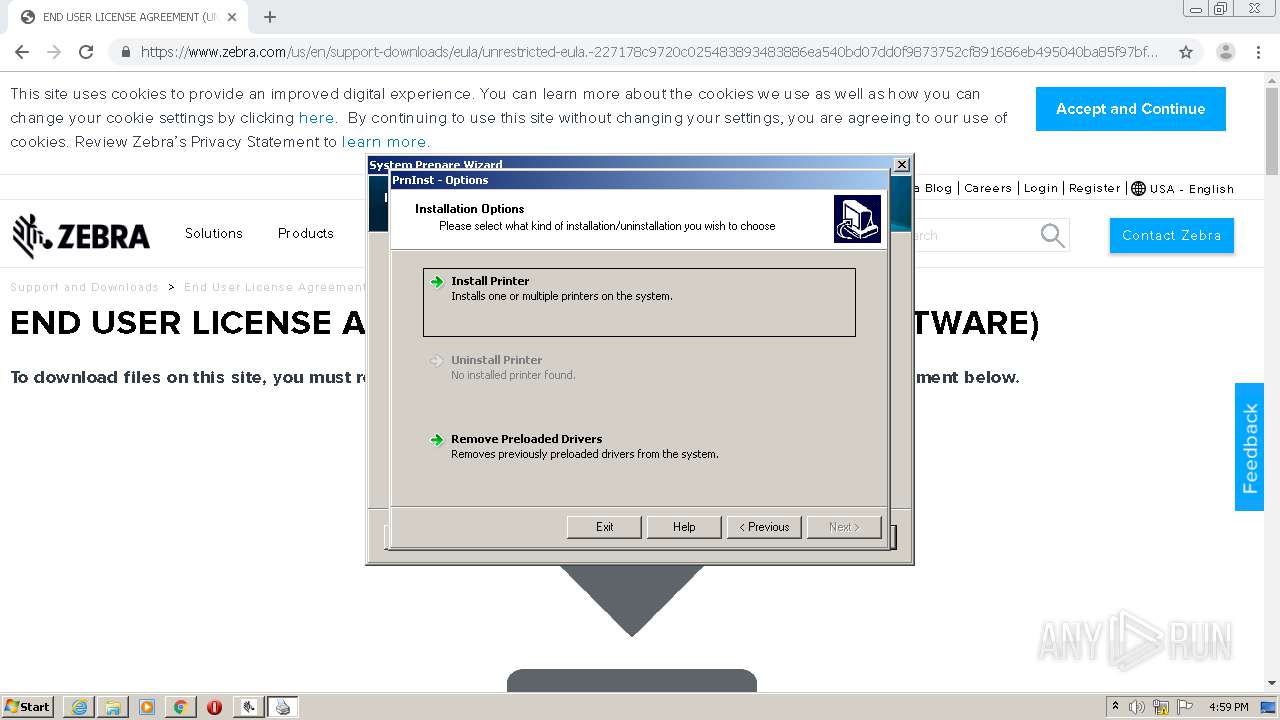
- PrnUtils.exe (PID: 2376)
- PrnInst.exe (PID: 1340)
- PrnInst.exe (PID: 1000)
Loads dropped or rewritten executable
- zsu-1-1-9-1286.exe (PID: 3764)
- PrnUtils.exe (PID: 2376)
- PrnInst.exe (PID: 1340)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 3968)
- chrome.exe (PID: 1464)
- zsu-1191286.exe (PID: 2584)
- zsu-1-1-9-1286.exe (PID: 3764)
- msiexec.exe (PID: 2684)
- PrnInst.exe (PID: 1340)
- DrvInst.exe (PID: 2836)
Modifies files in Chrome extension folder
- chrome.exe (PID: 1464)
Reads Windows owner or organization settings
- zsu-1-1-9-1286.exe (PID: 3764)
Reads the Windows organization settings
- zsu-1-1-9-1286.exe (PID: 3764)
Creates files in the program directory
- zsu-1-1-9-1286.exe (PID: 3764)
- zsu-1191286.exe (PID: 2584)
Creates a software uninstall entry
- zsu-1-1-9-1286.exe (PID: 3764)
Executed via COM
- DrvInst.exe (PID: 2836)
Uses RUNDLL32.EXE to load library
- DrvInst.exe (PID: 2836)
Executed as Windows Service
- vssvc.exe (PID: 3988)
Creates files in the Windows directory
- DrvInst.exe (PID: 2836)
Creates files in the driver directory
- DrvInst.exe (PID: 2836)
Removes files from Windows directory
- DrvInst.exe (PID: 2836)
INFO
Application launched itself
- iexplore.exe (PID: 444)
- chrome.exe (PID: 1464)
- msiexec.exe (PID: 2684)
Creates files in the user directory
- iexplore.exe (PID: 444)
- iexplore.exe (PID: 588)
Reads Internet Cache Settings
- iexplore.exe (PID: 444)
- iexplore.exe (PID: 588)
- chrome.exe (PID: 1464)
Reads settings of System Certificates
- iexplore.exe (PID: 444)
- chrome.exe (PID: 1464)
- chrome.exe (PID: 3968)
- iexplore.exe (PID: 588)
- DrvInst.exe (PID: 2836)
Reads the hosts file
- chrome.exe (PID: 3968)
- chrome.exe (PID: 1464)
Changes internet zones settings
- iexplore.exe (PID: 444)
Reads internet explorer settings
- iexplore.exe (PID: 588)
Creates a software uninstall entry
- msiexec.exe (PID: 2684)
Manual execution by user
- chrome.exe (PID: 1464)
- explorer.exe (PID: 2784)
Creates files in the program directory
- msiexec.exe (PID: 2684)
Searches for installed software
- DrvInst.exe (PID: 2836)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3988)
Adds / modifies Windows certificates
- DrvInst.exe (PID: 2836)
- iexplore.exe (PID: 444)
Changes settings of System certificates
- DrvInst.exe (PID: 2836)
- iexplore.exe (PID: 444)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
99
Monitored processes
51
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,8709472624927315624,16173186310965599544,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12254927607809347205 --renderer-client-id=32 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2960 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,8709472624927315624,16173186310965599544,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14202709947731925827 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2276 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 444 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.zebra.com/us/en/support-downloads/eula/unrestricted-eula.-227178c9720c025483893483886ea540bd07dd0f9873752cf891686eb495040ba85f97bf163f9fdbc62ce8bbe325bdf8d7c463f51a4ad0a6a906cd075f933a451ef3005a5bc81cd05c75f414a9073d4b71395853b10f27e.html# | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,8709472624927315624,16173186310965599544,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1858142231637366411 --renderer-client-id=33 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4408 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 588 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:444 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 660 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,8709472624927315624,16173186310965599544,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=448444179346260828 --renderer-client-id=28 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4784 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 720 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,8709472624927315624,16173186310965599544,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=3580657228890033898 --mojo-platform-channel-handle=3696 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 916 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,8709472624927315624,16173186310965599544,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12014895768981851763 --mojo-platform-channel-handle=4724 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
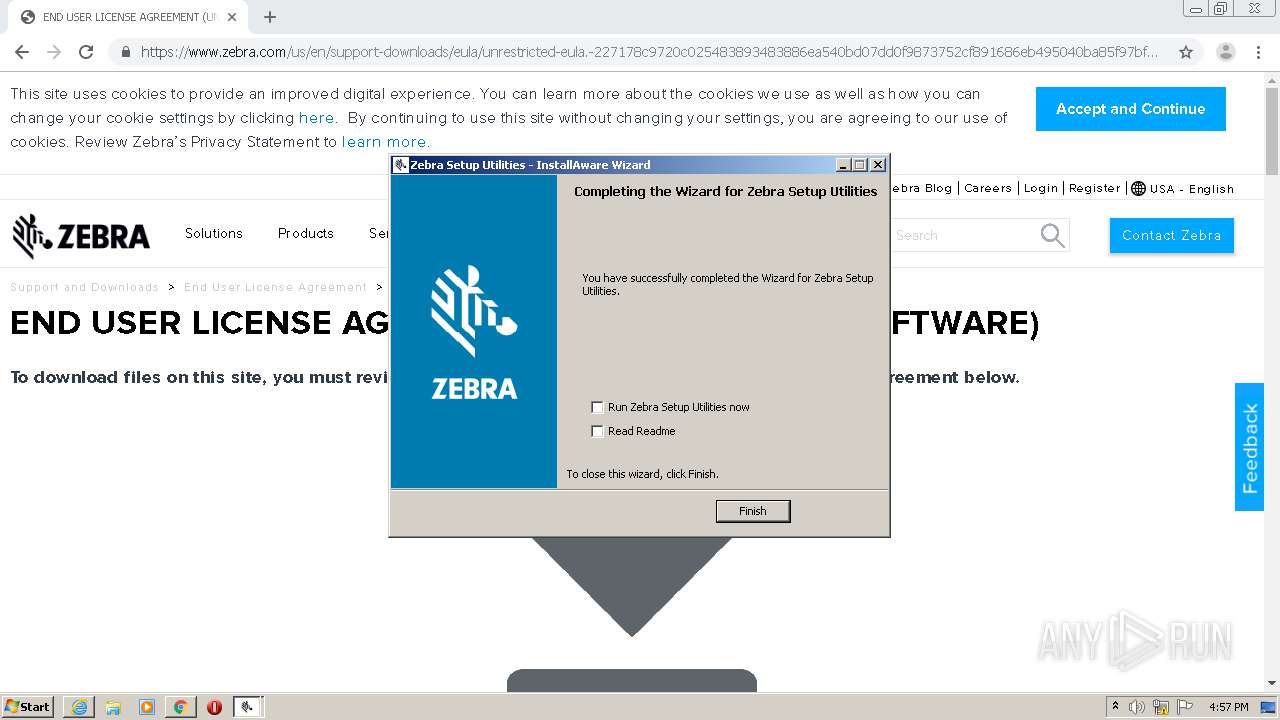
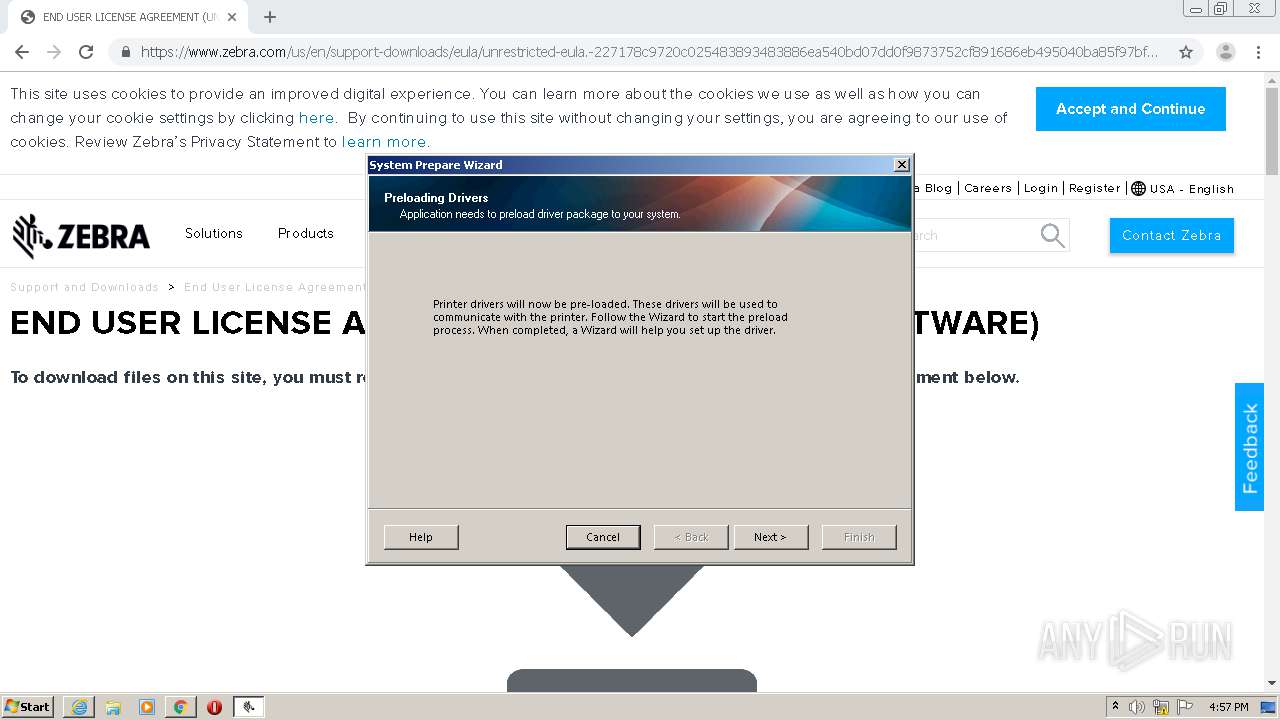
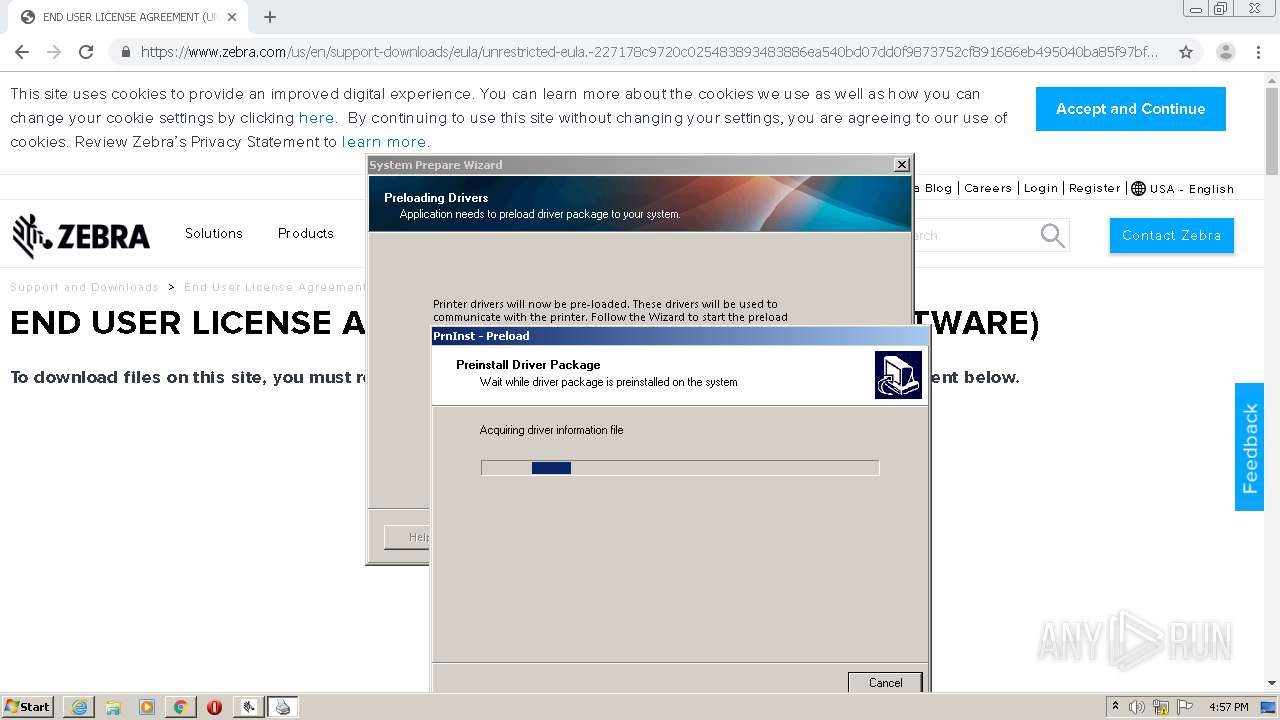
| 1000 | "C:\Program Files\Zebra Technologies\Zebra Setup Utilities\Driver\PrnInst.exe" | C:\Program Files\Zebra Technologies\Zebra Setup Utilities\Driver\PrnInst.exe | — | PrnUtils.exe | |||||||||||
User: admin Company: Zebra Technologies International, LLC Integrity Level: HIGH Description: Printer Installation Wizard Exit code: 0 Version: 5.3.44 Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,8709472624927315624,16173186310965599544,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9302200162029721630 --renderer-client-id=23 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4740 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
10 058
Read events
2 491
Write events
6 055
Delete events
1 512
Modification events
| (PID) Process: | (444) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3570596586 | |||
| (PID) Process: | (444) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30822134 | |||
| (PID) Process: | (444) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (444) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (444) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (444) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (444) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (444) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (444) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (444) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
263
Suspicious files
412
Text files
2 981
Unknown types
143
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 588 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabA068.tmp | — | |
MD5:— | SHA256:— | |||
| 588 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarA069.tmp | — | |
MD5:— | SHA256:— | |||
| 588 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\clientlibrarymanager.min[1].js | html | |
MD5:— | SHA256:— | |||
| 588 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\nlo6klb[1].js | text | |
MD5:— | SHA256:— | |||
| 588 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_D975BBA8033175C8D112023D8A7A8AD6 | der | |
MD5:— | SHA256:— | |||
| 588 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\atoz-campaign[1].js | text | |
MD5:— | SHA256:— | |||
| 588 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | der | |
MD5:— | SHA256:— | |||
| 588 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\languagedropdown[1].js | text | |
MD5:— | SHA256:— | |||
| 588 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1E11E75149C17A93653DA7DC0B8CF53F_54131AB1DB00301B25091F277DEEB0D4 | der | |
MD5:— | SHA256:— | |||
| 588 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\contexthub.kernel[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
87
TCP/UDP connections
358
DNS requests
167
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
588 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
588 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAza5nSVYZrPeIlAtSf0Rcs%3D | US | der | 471 b | whitelisted |
588 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
588 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
588 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAza5nSVYZrPeIlAtSf0Rcs%3D | US | der | 471 b | whitelisted |
588 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
588 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAtb9ltrp%2FvQiykNkEU33uA%3D | US | der | 471 b | whitelisted |
588 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
588 | iexplore.exe | GET | 200 | 192.124.249.22:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
588 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
588 | iexplore.exe | 151.101.192.114:443 | cdn.evgnet.com | Fastly | US | unknown |
588 | iexplore.exe | 161.71.1.37:443 | service.force.com | — | GB | unknown |
588 | iexplore.exe | 104.108.57.39:443 | www.zebra.com | Akamai Technologies, Inc. | NL | unknown |
588 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
588 | iexplore.exe | 2.16.186.59:443 | use.typekit.net | Akamai International B.V. | — | whitelisted |
444 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
588 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
588 | iexplore.exe | 52.222.174.122:443 | api.demandbase.com | Amazon.com, Inc. | US | unknown |
588 | iexplore.exe | 52.30.78.155:443 | dpm.demdex.net | Amazon.com, Inc. | IE | unknown |
588 | iexplore.exe | 184.30.223.226:443 | s.go-mpulse.net | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.zebra.com |
| unknown |
ocsp.digicert.com |
| whitelisted |
use.typekit.net |
| whitelisted |
cdn.evgnet.com |
| whitelisted |
assets.adobedtm.com |
| whitelisted |
service.force.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |