| URL: | https://ws.onehub.com/files/f1z2yhg4 |
| Full analysis: | https://app.any.run/tasks/207d4ba2-c1be-4869-8506-3c2d595eb45d |
| Verdict: | Malicious activity |
| Analysis date: | August 04, 2024, 05:40:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 5B13C85745BF375A70F0C40941150A20 |
| SHA1: | 931B9006FD5B82FDA8227633CD245B8BB62E1151 |
| SHA256: | 259F2A92CFAA7B52DE7CEFF28103B75B869CCA04F271465C382165D8471B30D8 |
| SSDEEP: | 3:N8H5EyU0Ki:2WyL |
MALICIOUS
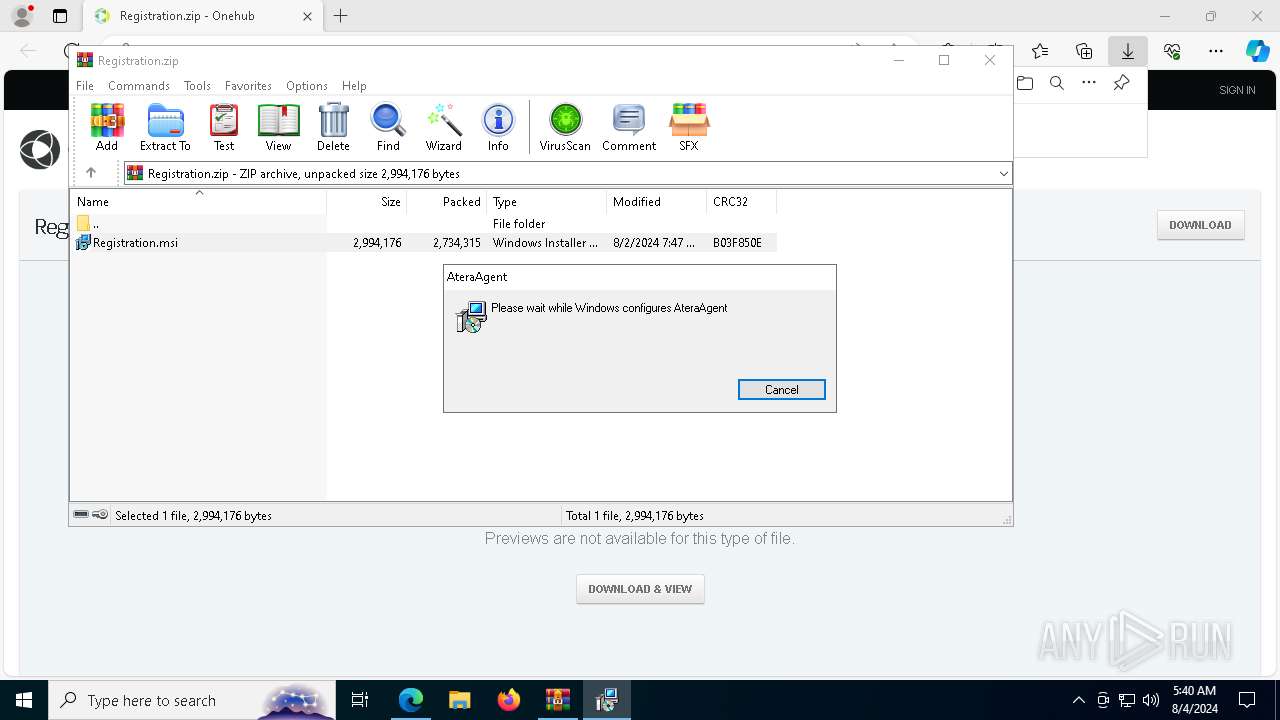
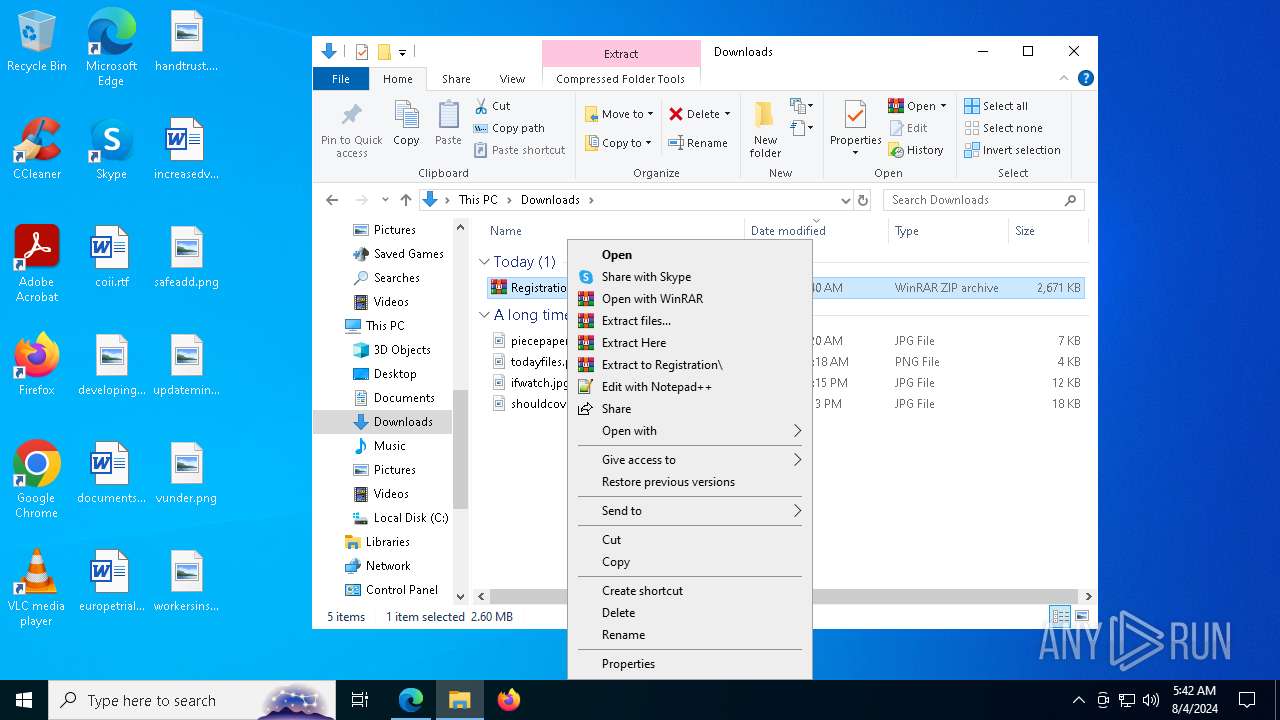
Drops the executable file immediately after the start
- msiexec.exe (PID: 7980)
- AteraAgent.exe (PID: 6344)
- AteraAgent.exe (PID: 6868)
- AgentPackageTicketing.exe (PID: 7708)
- AgentPackageUpgradeAgent.exe (PID: 9132)
- AteraAgent.exe (PID: 7288)
- PreVerCheck.exe (PID: 7056)
- msiexec.exe (PID: 9084)
- SplashtopStreamer.exe (PID: 8300)
- SetupUtil.exe (PID: 472)
- AgentPackageUpgradeAgent.exe (PID: 8712)
- AgentPackageUpgradeAgent.exe (PID: 9048)
- 6-0-30.exe (PID: 8780)
- AgentPackageRuntimeInstaller.exe (PID: 7416)
- 6-0-30.exe (PID: 7180)
- dotnet-runtime-6.0.30-win-x64.exe (PID: 6344)
- AgentPackageTicketing.exe (PID: 7636)
Starts NET.EXE for service management
- msiexec.exe (PID: 7640)
- net.exe (PID: 6620)
- net.exe (PID: 8836)
- msiexec.exe (PID: 7668)
- net.exe (PID: 8412)
Changes powershell execution policy (Bypass)
- AgentPackageAgentInformation.exe (PID: 2476)
- AgentPackageAgentInformation.exe (PID: 8612)
- AgentPackageAgentInformation.exe (PID: 6164)
Bypass execution policy to execute commands
- powershell.exe (PID: 6364)
- powershell.exe (PID: 8620)
- powershell.exe (PID: 8700)
Changes the autorun value in the registry
- dotnet-runtime-6.0.30-win-x64.exe (PID: 6344)
SUSPICIOUS
Reads security settings of Internet Explorer
- cookie_exporter.exe (PID: 1556)
- WinRAR.exe (PID: 8136)
- AteraAgent.exe (PID: 6184)
- AteraAgent.exe (PID: 6344)
- AteraAgent.exe (PID: 6868)
- AgentPackageAgentInformation.exe (PID: 2476)
- AgentPackageAgentInformation.exe (PID: 8612)
- AteraAgent.exe (PID: 7316)
- AteraAgent.exe (PID: 7288)
- AgentPackageAgentInformation.exe (PID: 6164)
- SplashtopStreamer.exe (PID: 8300)
- SetupUtil.exe (PID: 472)
- 6-0-30.exe (PID: 8780)
Process drops legitimate windows executable
- WinRAR.exe (PID: 8136)
- msiexec.exe (PID: 7980)
- rundll32.exe (PID: 32)
- rundll32.exe (PID: 8116)
- rundll32.exe (PID: 7012)
- rundll32.exe (PID: 2960)
- AteraAgent.exe (PID: 6344)
- AteraAgent.exe (PID: 6868)
- AgentPackageUpgradeAgent.exe (PID: 9132)
- rundll32.exe (PID: 7420)
- rundll32.exe (PID: 8168)
- rundll32.exe (PID: 7068)
- rundll32.exe (PID: 2476)
- WinRAR.exe (PID: 8700)
- AteraAgent.exe (PID: 7288)
- AgentPackageUpgradeAgent.exe (PID: 8712)
- AgentPackageUpgradeAgent.exe (PID: 9048)
- 6-0-30.exe (PID: 7180)
- 6-0-30.exe (PID: 8780)
- AgentPackageRuntimeInstaller.exe (PID: 7416)
- dotnet-runtime-6.0.30-win-x64.exe (PID: 6344)
Checks Windows Trust Settings
- msiexec.exe (PID: 7980)
- AteraAgent.exe (PID: 6184)
- AteraAgent.exe (PID: 7316)
- msiexec.exe (PID: 9084)
- SRManager.exe (PID: 7424)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7980)
Executable content was dropped or overwritten
- rundll32.exe (PID: 32)
- rundll32.exe (PID: 7012)
- rundll32.exe (PID: 8116)
- rundll32.exe (PID: 2960)
- AteraAgent.exe (PID: 6344)
- AteraAgent.exe (PID: 6868)
- AgentPackageTicketing.exe (PID: 7708)
- AgentPackageUpgradeAgent.exe (PID: 9132)
- rundll32.exe (PID: 7068)
- rundll32.exe (PID: 7420)
- rundll32.exe (PID: 8168)
- rundll32.exe (PID: 2476)
- AteraAgent.exe (PID: 7288)
- PreVerCheck.exe (PID: 7056)
- SplashtopStreamer.exe (PID: 8300)
- SetupUtil.exe (PID: 472)
- AgentPackageUpgradeAgent.exe (PID: 8712)
- AgentPackageUpgradeAgent.exe (PID: 9048)
- 6-0-30.exe (PID: 7180)
- 6-0-30.exe (PID: 8780)
- AgentPackageRuntimeInstaller.exe (PID: 7416)
- dotnet-runtime-6.0.30-win-x64.exe (PID: 6344)
- AgentPackageTicketing.exe (PID: 7636)
Uses TASKKILL.EXE to kill process
- msiexec.exe (PID: 7640)
- msiexec.exe (PID: 7668)
- cmd.exe (PID: 8448)
- cmd.exe (PID: 4280)
- cmd.exe (PID: 7820)
- cmd.exe (PID: 8000)
- cmd.exe (PID: 2064)
- cmd.exe (PID: 8120)
- cmd.exe (PID: 7876)
- cmd.exe (PID: 7644)
- cmd.exe (PID: 8176)
- cmd.exe (PID: 7864)
Reads the date of Windows installation
- AteraAgent.exe (PID: 6344)
- AteraAgent.exe (PID: 6868)
- AteraAgent.exe (PID: 7288)
- SplashtopStreamer.exe (PID: 8300)
- SetupUtil.exe (PID: 472)
- 6-0-30.exe (PID: 8780)
Starts SC.EXE for service management
- AteraAgent.exe (PID: 6344)
- AteraAgent.exe (PID: 6868)
- AteraAgent.exe (PID: 7288)
Executes as Windows Service
- VSSVC.exe (PID: 7920)
- AteraAgent.exe (PID: 6344)
- AteraAgent.exe (PID: 6868)
- AteraAgent.exe (PID: 7288)
- SRService.exe (PID: 4424)
Starts CMD.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 2476)
- AgentPackageAgentInformation.exe (PID: 8612)
- AgentPackageAgentInformation.exe (PID: 6164)
- msiexec.exe (PID: 9084)
- AgentPackageRuntimeInstaller.exe (PID: 7416)
- SetupUtil.exe (PID: 472)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 3720)
- cscript.exe (PID: 1644)
- cscript.exe (PID: 8488)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 3720)
- cscript.exe (PID: 1644)
- cscript.exe (PID: 8488)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 3720)
- cscript.exe (PID: 1644)
- cscript.exe (PID: 8488)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 3720)
- cscript.exe (PID: 1644)
- cscript.exe (PID: 8488)
The process executes VB scripts
- cmd.exe (PID: 4544)
- cmd.exe (PID: 8716)
- cmd.exe (PID: 8168)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 3720)
- cscript.exe (PID: 1644)
- cscript.exe (PID: 8488)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 3720)
- cscript.exe (PID: 1644)
- cscript.exe (PID: 8488)
The process creates files with name similar to system file names
- WerFault.exe (PID: 8480)
- WerFault.exe (PID: 8860)
- AteraAgent.exe (PID: 6868)
- msiexec.exe (PID: 7980)
- WerFault.exe (PID: 6836)
Starts POWERSHELL.EXE for commands execution
- AgentPackageAgentInformation.exe (PID: 2476)
- cmd.exe (PID: 8772)
- AgentPackageAgentInformation.exe (PID: 8612)
- cmd.exe (PID: 7308)
- cmd.exe (PID: 872)
- AgentPackageAgentInformation.exe (PID: 6164)
Potential Corporate Privacy Violation
- rundll32.exe (PID: 8116)
- rundll32.exe (PID: 2960)
- AgentPackageAgentInformation.exe (PID: 2132)
- AteraAgent.exe (PID: 6868)
- AgentPackageAgentInformation.exe (PID: 2580)
- AgentPackageAgentInformation.exe (PID: 7500)
- AgentPackageAgentInformation.exe (PID: 2476)
- AgentPackageMonitoring.exe (PID: 8320)
- AteraAgent.exe (PID: 6344)
- AgentPackageInternalPoller.exe (PID: 5976)
- AgentPackageSTRemote.exe (PID: 4060)
- AgentPackageTicketing.exe (PID: 7708)
- AgentPackageProgramManagement.exe (PID: 4292)
- AgentPackageAgentInformation.exe (PID: 8612)
- rundll32.exe (PID: 7420)
- AgentPackageMarketplace.exe (PID: 7204)
- AgentPackageMonitoring.exe (PID: 4780)
- rundll32.exe (PID: 2476)
- AteraAgent.exe (PID: 7288)
- AgentPackageMarketplace.exe (PID: 6620)
- AgentPackageInternalPoller.exe (PID: 8332)
- AgentPackageProgramManagement.exe (PID: 2088)
- AgentPackageAgentInformation.exe (PID: 6164)
- AgentPackageMonitoring.exe (PID: 8468)
The process executes Powershell scripts
- cmd.exe (PID: 8772)
- cmd.exe (PID: 7308)
- cmd.exe (PID: 872)
Searches for installed software
- AgentPackageAgentInformation.exe (PID: 2476)
- AgentPackageAgentInformation.exe (PID: 8612)
- AgentPackageProgramManagement.exe (PID: 4292)
- AgentPackageProgramManagement.exe (PID: 2088)
- AgentPackageAgentInformation.exe (PID: 6164)
- 6-0-30.exe (PID: 8780)
- dotnet-runtime-6.0.30-win-x64.exe (PID: 6344)
Executes application which crashes
- cscript.exe (PID: 1644)
- cscript.exe (PID: 3720)
- cscript.exe (PID: 8488)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 8620)
There is functionality for taking screenshot (YARA)
- AgentPackageTicketing.exe (PID: 7708)
- SRFeature.exe (PID: 1080)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 7980)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 9084)
- SRService.exe (PID: 8644)
Starts itself from another location
- AgentPackageUpgradeAgent.exe (PID: 8712)
- 6-0-30.exe (PID: 8780)
Starts a Microsoft application from unusual location
- 6-0-30.exe (PID: 8780)
- dotnet-runtime-6.0.30-win-x64.exe (PID: 6344)
Creates a software uninstall entry
- dotnet-runtime-6.0.30-win-x64.exe (PID: 6344)
The process drops C-runtime libraries
- msiexec.exe (PID: 7980)
INFO
Application launched itself
- msedge.exe (PID: 6368)
Checks proxy server information
- cookie_exporter.exe (PID: 1556)
- msiexec.exe (PID: 7044)
- rundll32.exe (PID: 8116)
- rundll32.exe (PID: 2960)
Checks supported languages
- identity_helper.exe (PID: 6052)
- cookie_exporter.exe (PID: 1556)
- msiexec.exe (PID: 7980)
- msiexec.exe (PID: 4604)
- msiexec.exe (PID: 7640)
- AteraAgent.exe (PID: 6184)
- AgentPackageAgentInformation.exe (PID: 2580)
- AgentPackageAgentInformation.exe (PID: 7500)
- AgentPackageAgentInformation.exe (PID: 2132)
- AgentPackageAgentInformation.exe (PID: 2336)
- AteraAgent.exe (PID: 6344)
- AgentPackageAgentInformation.exe (PID: 2476)
- AteraAgent.exe (PID: 6868)
- AgentPackageMonitoring.exe (PID: 8320)
- AgentPackageAgentInformation.exe (PID: 8612)
- AgentPackageInternalPoller.exe (PID: 5976)
- AgentPackageSTRemote.exe (PID: 4060)
- AgentPackageUpgradeAgent.exe (PID: 9132)
- AgentPackageOsUpdates.exe (PID: 9184)
- AgentPackageTicketing.exe (PID: 7708)
- AgentPackageProgramManagement.exe (PID: 4292)
- AgentPackageMonitoring.exe (PID: 4780)
- TextInputHost.exe (PID: 4788)
- AgentPackageHeartbeat.exe (PID: 4692)
- AgentPackageSystemTools.exe (PID: 8628)
- msiexec.exe (PID: 7668)
- AgentPackageMarketplace.exe (PID: 7204)
- AgentPackageADRemote.exe (PID: 8564)
- AteraAgent.exe (PID: 8932)
- AteraAgent.exe (PID: 7316)
- AteraAgent.exe (PID: 7288)
- AgentPackageADRemote.exe (PID: 8044)
- AgentPackageMarketplace.exe (PID: 6620)
- AgentPackageHeartbeat.exe (PID: 7316)
- AgentPackageAgentInformation.exe (PID: 6164)
- AgentPackageInternalPoller.exe (PID: 8332)
- Agent.Package.Watchdog.exe (PID: 2472)
- AgentPackageProgramManagement.exe (PID: 2088)
- Agent.Package.Availability.exe (PID: 6484)
- AgentPackageSystemTools.exe (PID: 7452)
- SplashtopStreamer.exe (PID: 8300)
- AgentPackageMonitoring.exe (PID: 8468)
- PreVerCheck.exe (PID: 7056)
- msiexec.exe (PID: 9084)
- AgentPackageRuntimeInstaller.exe (PID: 7416)
- _isBC1E.exe (PID: 7492)
- _isBC1E.exe (PID: 8180)
- _isBC1E.exe (PID: 8280)
- _isBC1E.exe (PID: 4544)
- _isBC1E.exe (PID: 8584)
- _isBC1E.exe (PID: 3032)
- _isBC1E.exe (PID: 2128)
- _isBC1E.exe (PID: 7848)
- _isBC1E.exe (PID: 5924)
- _isBC1E.exe (PID: 8044)
- _isC6ED.exe (PID: 8960)
- _isC6ED.exe (PID: 6044)
- _isC6ED.exe (PID: 8744)
- _isC6ED.exe (PID: 1528)
- _isC6ED.exe (PID: 8036)
- _isC6ED.exe (PID: 9044)
- _isC6ED.exe (PID: 1104)
- _isC6ED.exe (PID: 4824)
- _isC6ED.exe (PID: 5940)
- _isC6ED.exe (PID: 8636)
- _isDB41.exe (PID: 8092)
- _isDB41.exe (PID: 7480)
- _isDB41.exe (PID: 1080)
- _isDB41.exe (PID: 752)
- _isDB41.exe (PID: 8644)
- _isDB41.exe (PID: 7824)
- _isDB41.exe (PID: 7600)
- _isDB41.exe (PID: 7500)
- SetupUtil.exe (PID: 7752)
- SetupUtil.exe (PID: 1172)
- _isDB41.exe (PID: 7492)
- _isDB41.exe (PID: 5472)
- _isEBCD.exe (PID: 7452)
- SRSelfSignCertUtil.exe (PID: 8588)
- _isEBCD.exe (PID: 3908)
- SetupUtil.exe (PID: 472)
- _isEBCD.exe (PID: 4780)
- _isEBCD.exe (PID: 9156)
- _isEBCD.exe (PID: 3692)
- _isEBCD.exe (PID: 7376)
- _isEBCD.exe (PID: 7740)
- _isEBCD.exe (PID: 8756)
- SRService.exe (PID: 8644)
- _isEBCD.exe (PID: 8280)
- _isEBCD.exe (PID: 8808)
- _isEF49.exe (PID: 6192)
- _isEF49.exe (PID: 1556)
- _isEF49.exe (PID: 8368)
- _isEF49.exe (PID: 3032)
- _isEF49.exe (PID: 3568)
- _isEF49.exe (PID: 2632)
- _isEF49.exe (PID: 4604)
- _isEF49.exe (PID: 8672)
- _isEF49.exe (PID: 8744)
- SRService.exe (PID: 4644)
- SRService.exe (PID: 4424)
- AgentPackageUpgradeAgent.exe (PID: 8712)
- SRManager.exe (PID: 7424)
- _isEF49.exe (PID: 8100)
- AgentPackageUpgradeAgent.exe (PID: 9048)
- SRUtility.exe (PID: 7332)
- SRServer.exe (PID: 7480)
- SRAgent.exe (PID: 7508)
- SRAppPB.exe (PID: 3076)
- SRFeature.exe (PID: 1080)
- AgentPackageSTRemote.exe (PID: 7632)
- SRUtility.exe (PID: 6124)
- SRDetect.exe (PID: 8280)
- SRUtility.exe (PID: 5288)
- BdEpSDK.exe (PID: 7072)
- AgentPackageHeartbeat.exe (PID: 8652)
- 6-0-30.exe (PID: 7180)
- 6-0-30.exe (PID: 8780)
- dotnet-runtime-6.0.30-win-x64.exe (PID: 6344)
- msiexec.exe (PID: 7840)
- SRVirtualDisplay.exe (PID: 472)
- Agent.Package.Availability.exe (PID: 4784)
- msiexec.exe (PID: 8092)
- AgentPackageHeartbeat.exe (PID: 6364)
- dotnet.exe (PID: 7964)
- dotnet.exe (PID: 32)
- AgentPackageTicketing.exe (PID: 7636)
- msiexec.exe (PID: 5172)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6368)
- WinRAR.exe (PID: 8136)
- AgentPackageAgentInformation.exe (PID: 2476)
- AgentPackageAgentInformation.exe (PID: 8612)
- AgentPackageAgentInformation.exe (PID: 6164)
Reads Environment values
- identity_helper.exe (PID: 6052)
- cookie_exporter.exe (PID: 1556)
- AteraAgent.exe (PID: 6184)
- AteraAgent.exe (PID: 6344)
- AgentPackageAgentInformation.exe (PID: 7500)
- AgentPackageAgentInformation.exe (PID: 2580)
- AgentPackageAgentInformation.exe (PID: 2132)
- AgentPackageAgentInformation.exe (PID: 2336)
- AgentPackageMonitoring.exe (PID: 8320)
- AgentPackageAgentInformation.exe (PID: 8612)
- AgentPackageAgentInformation.exe (PID: 2476)
- AteraAgent.exe (PID: 6868)
- AgentPackageInternalPoller.exe (PID: 5976)
- AgentPackageSTRemote.exe (PID: 4060)
- AgentPackageTicketing.exe (PID: 7708)
- AgentPackageUpgradeAgent.exe (PID: 9132)
- AgentPackageOsUpdates.exe (PID: 9184)
- AgentPackageProgramManagement.exe (PID: 4292)
- AgentPackageMonitoring.exe (PID: 4780)
- AgentPackageHeartbeat.exe (PID: 4692)
- AgentPackageSystemTools.exe (PID: 8628)
- AgentPackageMarketplace.exe (PID: 7204)
- AteraAgent.exe (PID: 8932)
- AgentPackageADRemote.exe (PID: 8564)
- AteraAgent.exe (PID: 7316)
- AteraAgent.exe (PID: 7288)
- AgentPackageADRemote.exe (PID: 8044)
- AgentPackageMarketplace.exe (PID: 6620)
- AgentPackageAgentInformation.exe (PID: 6164)
- AgentPackageHeartbeat.exe (PID: 7316)
- AgentPackageInternalPoller.exe (PID: 8332)
- AgentPackageProgramManagement.exe (PID: 2088)
- AgentPackageSystemTools.exe (PID: 7452)
- AgentPackageMonitoring.exe (PID: 8468)
- AgentPackageRuntimeInstaller.exe (PID: 7416)
- AgentPackageUpgradeAgent.exe (PID: 8712)
- AgentPackageUpgradeAgent.exe (PID: 9048)
- AgentPackageSTRemote.exe (PID: 7632)
- SRManager.exe (PID: 7424)
- AgentPackageHeartbeat.exe (PID: 8652)
- AgentPackageHeartbeat.exe (PID: 6364)
- AgentPackageTicketing.exe (PID: 7636)
The process uses the downloaded file
- msedge.exe (PID: 6368)
- msedge.exe (PID: 7192)
- WinRAR.exe (PID: 8136)
- WinRAR.exe (PID: 8700)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8136)
- msiexec.exe (PID: 7980)
- WinRAR.exe (PID: 8700)
- msiexec.exe (PID: 9084)
Reads the computer name
- identity_helper.exe (PID: 6052)
- cookie_exporter.exe (PID: 1556)
- msiexec.exe (PID: 7980)
- msiexec.exe (PID: 4604)
- msiexec.exe (PID: 7640)
- AteraAgent.exe (PID: 6184)
- AgentPackageAgentInformation.exe (PID: 7500)
- AgentPackageAgentInformation.exe (PID: 2132)
- AgentPackageAgentInformation.exe (PID: 2336)
- AteraAgent.exe (PID: 6344)
- AgentPackageAgentInformation.exe (PID: 2476)
- AgentPackageMonitoring.exe (PID: 8320)
- AgentPackageAgentInformation.exe (PID: 2580)
- AgentPackageAgentInformation.exe (PID: 8612)
- AgentPackageInternalPoller.exe (PID: 5976)
- AteraAgent.exe (PID: 6868)
- AgentPackageSTRemote.exe (PID: 4060)
- AgentPackageTicketing.exe (PID: 7708)
- AgentPackageUpgradeAgent.exe (PID: 9132)
- AgentPackageOsUpdates.exe (PID: 9184)
- AgentPackageProgramManagement.exe (PID: 4292)
- TextInputHost.exe (PID: 4788)
- AgentPackageHeartbeat.exe (PID: 4692)
- AgentPackageMonitoring.exe (PID: 4780)
- AgentPackageSystemTools.exe (PID: 8628)
- msiexec.exe (PID: 7668)
- AgentPackageMarketplace.exe (PID: 7204)
- AteraAgent.exe (PID: 8932)
- AgentPackageADRemote.exe (PID: 8564)
- AteraAgent.exe (PID: 7316)
- AteraAgent.exe (PID: 7288)
- AgentPackageMarketplace.exe (PID: 6620)
- AgentPackageADRemote.exe (PID: 8044)
- AgentPackageHeartbeat.exe (PID: 7316)
- AgentPackageAgentInformation.exe (PID: 6164)
- AgentPackageInternalPoller.exe (PID: 8332)
- Agent.Package.Watchdog.exe (PID: 2472)
- AgentPackageProgramManagement.exe (PID: 2088)
- Agent.Package.Availability.exe (PID: 6484)
- AgentPackageMonitoring.exe (PID: 8468)
- AgentPackageSystemTools.exe (PID: 7452)
- SplashtopStreamer.exe (PID: 8300)
- msiexec.exe (PID: 9084)
- AgentPackageRuntimeInstaller.exe (PID: 7416)
- _isBC1E.exe (PID: 7492)
- _isBC1E.exe (PID: 2128)
- _isBC1E.exe (PID: 8180)
- _isBC1E.exe (PID: 8584)
- _isBC1E.exe (PID: 8280)
- _isBC1E.exe (PID: 3032)
- _isBC1E.exe (PID: 4544)
- _isBC1E.exe (PID: 7848)
- _isBC1E.exe (PID: 8044)
- _isBC1E.exe (PID: 5924)
- _isC6ED.exe (PID: 1104)
- _isC6ED.exe (PID: 6044)
- _isC6ED.exe (PID: 8960)
- _isC6ED.exe (PID: 8744)
- _isC6ED.exe (PID: 1528)
- _isC6ED.exe (PID: 8036)
- _isC6ED.exe (PID: 5940)
- _isC6ED.exe (PID: 8636)
- _isDB41.exe (PID: 8092)
- _isDB41.exe (PID: 7480)
- _isC6ED.exe (PID: 9044)
- _isC6ED.exe (PID: 4824)
- _isDB41.exe (PID: 1080)
- _isDB41.exe (PID: 7600)
- _isDB41.exe (PID: 752)
- _isDB41.exe (PID: 8644)
- _isDB41.exe (PID: 7824)
- _isDB41.exe (PID: 7500)
- _isDB41.exe (PID: 7492)
- _isDB41.exe (PID: 5472)
- SetupUtil.exe (PID: 472)
- SRSelfSignCertUtil.exe (PID: 8588)
- _isEBCD.exe (PID: 7452)
- _isEBCD.exe (PID: 3908)
- _isEBCD.exe (PID: 4780)
- _isEBCD.exe (PID: 9156)
- _isEBCD.exe (PID: 7376)
- _isEBCD.exe (PID: 3692)
- _isEBCD.exe (PID: 7740)
- _isEBCD.exe (PID: 8756)
- _isEBCD.exe (PID: 8280)
- _isEBCD.exe (PID: 8808)
- _isEF49.exe (PID: 6192)
- _isEF49.exe (PID: 8368)
- _isEF49.exe (PID: 4604)
- _isEF49.exe (PID: 2632)
- _isEF49.exe (PID: 3032)
- _isEF49.exe (PID: 3568)
- _isEF49.exe (PID: 8672)
- _isEF49.exe (PID: 8100)
- SRService.exe (PID: 8644)
- _isEF49.exe (PID: 1556)
- _isEF49.exe (PID: 8744)
- SRService.exe (PID: 4644)
- AgentPackageUpgradeAgent.exe (PID: 8712)
- SRService.exe (PID: 4424)
- SRManager.exe (PID: 7424)
- AgentPackageUpgradeAgent.exe (PID: 9048)
- SRServer.exe (PID: 7480)
- SRAgent.exe (PID: 7508)
- SRAppPB.exe (PID: 3076)
- SRFeature.exe (PID: 1080)
- AgentPackageHeartbeat.exe (PID: 8652)
- AgentPackageSTRemote.exe (PID: 7632)
- 6-0-30.exe (PID: 8780)
- dotnet-runtime-6.0.30-win-x64.exe (PID: 6344)
- msiexec.exe (PID: 7840)
- Agent.Package.Availability.exe (PID: 4784)
- msiexec.exe (PID: 8092)
- msiexec.exe (PID: 5172)
- AgentPackageHeartbeat.exe (PID: 6364)
- SRVirtualDisplay.exe (PID: 472)
- AgentPackageTicketing.exe (PID: 7636)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 8136)
- rundll32.exe (PID: 32)
- rundll32.exe (PID: 7012)
- rundll32.exe (PID: 8116)
- rundll32.exe (PID: 2960)
- rundll32.exe (PID: 7420)
- rundll32.exe (PID: 8168)
- rundll32.exe (PID: 7068)
- rundll32.exe (PID: 2476)
- WinRAR.exe (PID: 8700)
Reads the software policy settings
- msiexec.exe (PID: 7044)
- msiexec.exe (PID: 7980)
- rundll32.exe (PID: 8116)
- AteraAgent.exe (PID: 6184)
- AteraAgent.exe (PID: 6344)
- rundll32.exe (PID: 2960)
- AgentPackageAgentInformation.exe (PID: 7500)
- AgentPackageAgentInformation.exe (PID: 2580)
- AgentPackageAgentInformation.exe (PID: 2132)
- AteraAgent.exe (PID: 6868)
- cscript.exe (PID: 3720)
- WerFault.exe (PID: 8480)
- AgentPackageMonitoring.exe (PID: 8320)
- AgentPackageAgentInformation.exe (PID: 2476)
- cscript.exe (PID: 1644)
- WerFault.exe (PID: 8860)
- AgentPackageInternalPoller.exe (PID: 5976)
- AgentPackageSTRemote.exe (PID: 4060)
- AgentPackageUpgradeAgent.exe (PID: 9132)
- AgentPackageTicketing.exe (PID: 7708)
- AgentPackageProgramManagement.exe (PID: 4292)
- AgentPackageAgentInformation.exe (PID: 8612)
- AgentPackageHeartbeat.exe (PID: 4692)
- rundll32.exe (PID: 7420)
- AgentPackageMarketplace.exe (PID: 7204)
- AgentPackageMonitoring.exe (PID: 4780)
- AteraAgent.exe (PID: 7316)
- rundll32.exe (PID: 2476)
- AteraAgent.exe (PID: 7288)
- AgentPackageMarketplace.exe (PID: 6620)
- cscript.exe (PID: 8488)
- AgentPackageHeartbeat.exe (PID: 7316)
- AgentPackageInternalPoller.exe (PID: 8332)
- WerFault.exe (PID: 6836)
- AgentPackageAgentInformation.exe (PID: 6164)
- AgentPackageProgramManagement.exe (PID: 2088)
- msiexec.exe (PID: 9084)
- AgentPackageRuntimeInstaller.exe (PID: 7416)
- AgentPackageMonitoring.exe (PID: 8468)
- SRManager.exe (PID: 7424)
- AgentPackageHeartbeat.exe (PID: 8652)
- AgentPackageHeartbeat.exe (PID: 6364)
- AgentPackageTicketing.exe (PID: 7636)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 7044)
Creates files or folders in the user directory
- msiexec.exe (PID: 7044)
Create files in a temporary directory
- rundll32.exe (PID: 32)
- rundll32.exe (PID: 7012)
- rundll32.exe (PID: 8116)
- rundll32.exe (PID: 2960)
Reads the machine GUID from the registry
- msiexec.exe (PID: 7980)
- AteraAgent.exe (PID: 6184)
- AteraAgent.exe (PID: 6344)
- AgentPackageAgentInformation.exe (PID: 7500)
- AgentPackageAgentInformation.exe (PID: 2580)
- AgentPackageAgentInformation.exe (PID: 2132)
- AgentPackageAgentInformation.exe (PID: 2336)
- AgentPackageAgentInformation.exe (PID: 2476)
- AteraAgent.exe (PID: 6868)
- AgentPackageMonitoring.exe (PID: 8320)
- AgentPackageAgentInformation.exe (PID: 8612)
- AgentPackageSTRemote.exe (PID: 4060)
- AgentPackageInternalPoller.exe (PID: 5976)
- AgentPackageUpgradeAgent.exe (PID: 9132)
- AgentPackageTicketing.exe (PID: 7708)
- AgentPackageOsUpdates.exe (PID: 9184)
- AgentPackageProgramManagement.exe (PID: 4292)
- AgentPackageMonitoring.exe (PID: 4780)
- AgentPackageHeartbeat.exe (PID: 4692)
- AgentPackageSystemTools.exe (PID: 8628)
- AgentPackageMarketplace.exe (PID: 7204)
- AteraAgent.exe (PID: 8932)
- AgentPackageADRemote.exe (PID: 8564)
- AteraAgent.exe (PID: 7316)
- AteraAgent.exe (PID: 7288)
- AgentPackageAgentInformation.exe (PID: 6164)
- AgentPackageADRemote.exe (PID: 8044)
- AgentPackageMarketplace.exe (PID: 6620)
- AgentPackageInternalPoller.exe (PID: 8332)
- AgentPackageHeartbeat.exe (PID: 7316)
- AgentPackageProgramManagement.exe (PID: 2088)
- AgentPackageMonitoring.exe (PID: 8468)
- AgentPackageSystemTools.exe (PID: 7452)
- msiexec.exe (PID: 9084)
- AgentPackageRuntimeInstaller.exe (PID: 7416)
- SRSelfSignCertUtil.exe (PID: 8588)
- SRManager.exe (PID: 7424)
- AgentPackageUpgradeAgent.exe (PID: 9048)
- AgentPackageSTRemote.exe (PID: 7632)
- AgentPackageHeartbeat.exe (PID: 8652)
- dotnet-runtime-6.0.30-win-x64.exe (PID: 6344)
- AgentPackageUpgradeAgent.exe (PID: 8712)
- AgentPackageHeartbeat.exe (PID: 6364)
- AgentPackageTicketing.exe (PID: 7636)
Disables trace logs
- rundll32.exe (PID: 8116)
- AteraAgent.exe (PID: 6344)
- rundll32.exe (PID: 2960)
- AgentPackageAgentInformation.exe (PID: 7500)
- AgentPackageAgentInformation.exe (PID: 2580)
- AgentPackageAgentInformation.exe (PID: 2132)
- AteraAgent.exe (PID: 6868)
- AgentPackageMonitoring.exe (PID: 8320)
- AgentPackageAgentInformation.exe (PID: 2476)
- AgentPackageInternalPoller.exe (PID: 5976)
- AgentPackageSTRemote.exe (PID: 4060)
- AgentPackageTicketing.exe (PID: 7708)
- AgentPackageUpgradeAgent.exe (PID: 9132)
- AgentPackageProgramManagement.exe (PID: 4292)
- AgentPackageAgentInformation.exe (PID: 8612)
- AgentPackageHeartbeat.exe (PID: 4692)
- rundll32.exe (PID: 7420)
- AgentPackageMarketplace.exe (PID: 7204)
- AgentPackageMonitoring.exe (PID: 4780)
- AteraAgent.exe (PID: 7288)
- rundll32.exe (PID: 2476)
- AgentPackageMarketplace.exe (PID: 6620)
- AgentPackageHeartbeat.exe (PID: 7316)
- AgentPackageInternalPoller.exe (PID: 8332)
- AgentPackageProgramManagement.exe (PID: 2088)
- AgentPackageAgentInformation.exe (PID: 6164)
- AgentPackageRuntimeInstaller.exe (PID: 7416)
- AgentPackageMonitoring.exe (PID: 8468)
- AgentPackageHeartbeat.exe (PID: 8652)
- AgentPackageHeartbeat.exe (PID: 6364)
- AgentPackageTicketing.exe (PID: 7636)
Creates files in the program directory
- AteraAgent.exe (PID: 6184)
- AteraAgent.exe (PID: 6344)
- AgentPackageMonitoring.exe (PID: 8320)
- AgentPackageAgentInformation.exe (PID: 2476)
- AteraAgent.exe (PID: 6868)
- AgentPackageInternalPoller.exe (PID: 5976)
- AgentPackageSTRemote.exe (PID: 4060)
- AgentPackageTicketing.exe (PID: 7708)
- AgentPackageProgramManagement.exe (PID: 4292)
- AgentPackageMonitoring.exe (PID: 4780)
- AgentPackageUpgradeAgent.exe (PID: 9132)
- AteraAgent.exe (PID: 7316)
- AteraAgent.exe (PID: 7288)
- AgentPackageInternalPoller.exe (PID: 8332)
- AgentPackageProgramManagement.exe (PID: 2088)
- AgentPackageAgentInformation.exe (PID: 6164)
- AgentPackageMonitoring.exe (PID: 8468)
- AgentPackageRuntimeInstaller.exe (PID: 7416)
- SetupUtil.exe (PID: 472)
- SRSelfSignCertUtil.exe (PID: 8588)
- SRService.exe (PID: 8644)
- SRManager.exe (PID: 7424)
- SRAgent.exe (PID: 7508)
- AgentPackageSTRemote.exe (PID: 7632)
- dotnet-runtime-6.0.30-win-x64.exe (PID: 6344)
- SRVirtualDisplay.exe (PID: 472)
- AgentPackageTicketing.exe (PID: 7636)
Creates a software uninstall entry
- msiexec.exe (PID: 7980)
Manual execution by a user
- WinRAR.exe (PID: 8700)
Reads product name
- SRManager.exe (PID: 7424)
UPX packer has been detected
- SRServer.exe (PID: 7480)
- SRManager.exe (PID: 7424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
473
Monitored processes
322
Malicious processes
29
Suspicious processes
14
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | rundll32.exe "C:\WINDOWS\Installer\MSIE942.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_977375 2 AlphaControlAgentInstallation!AlphaControlAgentInstallation.CustomActions.GenerateAgentId | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 32 | "C:\Program Files\dotnet\dotnet" --list-runtimes | C:\Program Files\dotnet\dotnet.exe | — | AgentPackageRuntimeInstaller.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Host Exit code: 0 Version: 6,0,3024,21525 @Commit: 97d8f4cade971b93794a3805e7d72ee388f Modules
| |||||||||||||||
| 188 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5632 --field-trial-handle=2532,i,8457192517459217091,8765676997262748274,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 368 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 368 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=6612 --field-trial-handle=2532,i,8457192517459217091,8765676997262748274,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 472 | "C:\Program Files (x86)\Splashtop\Splashtop Remote\Server\Support\SetupUtil.exe" /P ST_EVENT | C:\Program Files (x86)\Splashtop\Splashtop Remote\Server\Support\SetupUtil.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Splashtop Inc. Integrity Level: SYSTEM Description: Splashtop® Streamer Setup Utility Exit code: 0 Version: 1.0.4.0 Modules
| |||||||||||||||
| 472 | "C:\Program Files (x86)\Splashtop\Splashtop Remote\Server\SRVirtualDisplay.exe" | C:\Program Files (x86)\Splashtop\Splashtop Remote\Server\SRVirtualDisplay.exe | — | SRManager.exe | |||||||||||
User: SYSTEM Company: Splashtop Inc. Integrity Level: SYSTEM Description: Splashtop Streamer Virtual Monitor Utility Version: 3.70.1.137 Modules
| |||||||||||||||
| 752 | taskkill.exe /F /IM SRChat.exe /T | C:\Windows\SysWOW64\taskkill.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 752 | C:\WINDOWS\TEMP\{FA1B96F2-2402-40E3-8B08-A5D37827E41F}\_isDB41.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{0151FEFF-B9B5-4802-B12B-FD31B6EA90A8} | C:\Windows\Temp\{FA1B96F2-2402-40E3-8B08-A5D37827E41F}\_isDB41.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Flexera Integrity Level: SYSTEM Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 27.0.122 Modules
| |||||||||||||||
| 872 | "cmd.exe" /c powershell.exe -File "C:\Program Files\Microsoft Office\Office16\vNextDiag.ps1" | C:\Windows\System32\cmd.exe | — | AgentPackageAgentInformation.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
200 573
Read events
198 054
Write events
2 278
Delete events
241
Modification events
| (PID) Process: | (6188) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 0 | |||
| (PID) Process: | (6188) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 0 | |||
| (PID) Process: | (6188) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 0 | |||
| (PID) Process: | (6188) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 0 | |||
| (PID) Process: | (6188) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (6188) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31122992 | |||
| (PID) Process: | (6188) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6188) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6188) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6188) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
1 008
Suspicious files
411
Text files
352
Unknown types
33
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RFe5669.TMP | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RFe5678.TMP | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RFe5678.TMP | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RFe5678.TMP | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RFe56b7.TMP | — | |
MD5:— | SHA256:— | |||
| 6368 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
199
DNS requests
134
Threats
66
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
300 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7044 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
7328 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7364 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7044 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAooSZl45YmN9AojjrilUug%3D | unknown | — | — | whitelisted |
7044 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
6184 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
6184 | AteraAgent.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
2532 | svchost.exe | HEAD | 200 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/72e62a8f-bc19-44e7-b14b-c0d389408307?P1=1723336707&P2=404&P3=2&P4=GQRKuk3c2EvPzyDDAw2OfKKH4rVOYbMOGr7AxsO%2bBEC%2bwvsDJUGWicvhO7NZu9lnRRp8dxdpU1l7TKILx%2fJqIw%3d%3d | unknown | — | — | whitelisted |
2532 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/72e62a8f-bc19-44e7-b14b-c0d389408307?P1=1723336707&P2=404&P3=2&P4=GQRKuk3c2EvPzyDDAw2OfKKH4rVOYbMOGr7AxsO%2bBEC%2bwvsDJUGWicvhO7NZu9lnRRp8dxdpU1l7TKILx%2fJqIw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
532 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3068 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6368 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6612 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6612 | msedge.exe | 54.173.137.115:443 | ws.onehub.com | AMAZON-AES | US | unknown |
6612 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6612 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ws.onehub.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
cookie-cdn.cookiepro.com |
| whitelisted |
dp0qkd77b9xjk.cloudfront.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO File Sharing Service Related Domain in DNS Lookup (ws .onehub .com) |
6612 | msedge.exe | Misc activity | ET INFO File Sharing Service Related Domain in DNS Lookup (ws .onehub .com) |
6612 | msedge.exe | Misc activity | ET INFO Observed File Sharing Service Related Domain (ws .onehub .com in TLS SNI) |
6612 | msedge.exe | Misc activity | ET INFO File Sharing Service Related Domain in DNS Lookup (ws .onehub .com) |
6612 | msedge.exe | Misc activity | ET INFO Observed File Sharing Service Related Domain (ws .onehub .com in TLS SNI) |
6612 | msedge.exe | Misc activity | ET INFO Observed File Sharing Service Related Domain (ws .onehub .com in TLS SNI) |
6612 | msedge.exe | Misc activity | ET INFO Observed File Sharing Service Related Domain (ws .onehub .com in TLS SNI) |
2256 | svchost.exe | Misc activity | ET INFO Splashtop Domain in DNS Lookup (splashtop .com) |
4060 | AgentPackageSTRemote.exe | Misc activity | ET INFO Splashtop Domain (splashtop .com) in TLS SNI |
2256 | svchost.exe | Misc activity | ET INFO Splashtop Domain in DNS Lookup (splashtop .com) |
38 ETPRO signatures available at the full report
Process | Message |
|---|---|
AgentPackageMonitoring.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\x64\SQLite.Interop.dll"...
|
AgentPackageMonitoring.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files (x86)\ATERA Networks\AteraAgent\Packages\AgentPackageMonitoring\x64\SQLite.Interop.dll"...
|
Agent.Package.Availability.exe | You must install .NET to run this application.
App: C:\Program Files\ATERA Networks\AteraAgent\Packages\Agent.Package.Availability\Agent.Package.Availability.exe
Architecture: x64
App host version: 6.0.27
.NET location: Not found
Learn about runtime installation:
https://aka.ms/dotnet/app-launch-failed
Download the .NET runtime:
https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x64&rid=win10-x64&apphost_version=6.0.27 |
Agent.Package.Watchdog.exe | You must install .NET to run this application.
App: C:\Program Files\ATERA Networks\AteraAgent\Packages\Agent.Package.Watchdog\Agent.Package.Watchdog.exe
Architecture: x64
App host version: 6.0.27
.NET location: Not found
Learn about runtime installation:
https://aka.ms/dotnet/app-launch-failed
Download the .NET runtime:
https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x64&rid=win10-x64&apphost_version=6.0.27 |
SplashtopStreamer.exe | [8300]2024-08-04 05:42:59 [CUtility::OSInfo] OS 10.0(19045) x64:1 (Last=0) |
SplashtopStreamer.exe | [8300]2024-08-04 05:42:59 [CUnPack::FindHeader] Name:C:\WINDOWS\TEMP\SplashtopStreamer.exe (Last=0) |
SplashtopStreamer.exe | [8300]2024-08-04 05:42:59 [CUnPack::FindHeader] Sign Size:10248 (Last=0) |
SplashtopStreamer.exe | [8300]2024-08-04 05:42:59 [CUnPack::FindHeader] Header offset:434176 (Last=183) |
SplashtopStreamer.exe | [8300]2024-08-04 05:42:59 [CUnPack::UnPackFiles] FreeSpace:231995469824 FileSize:49613312 (Last=0) |
SplashtopStreamer.exe | [8300]2024-08-04 05:42:59 [CUnPack::UnPackFiles] (1/5)UnPack file name:C:\WINDOWS\TEMP\unpack\setup.msi (49613312) (Last=0) |