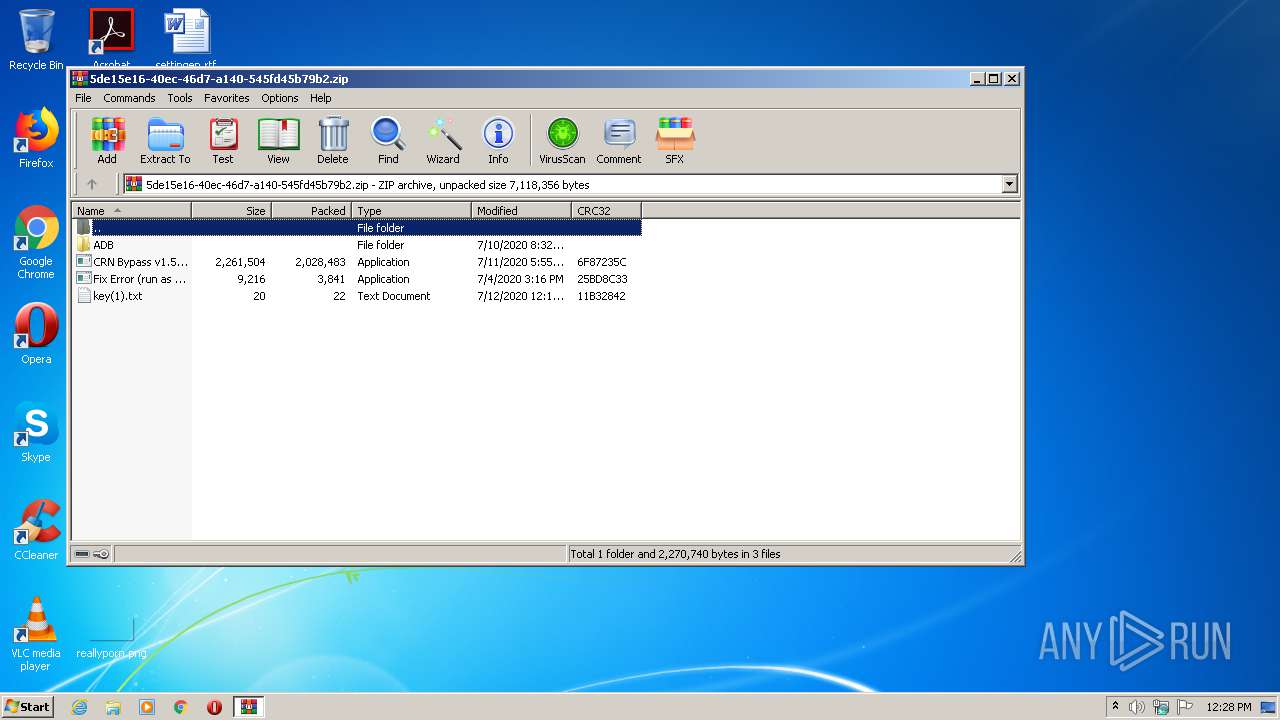
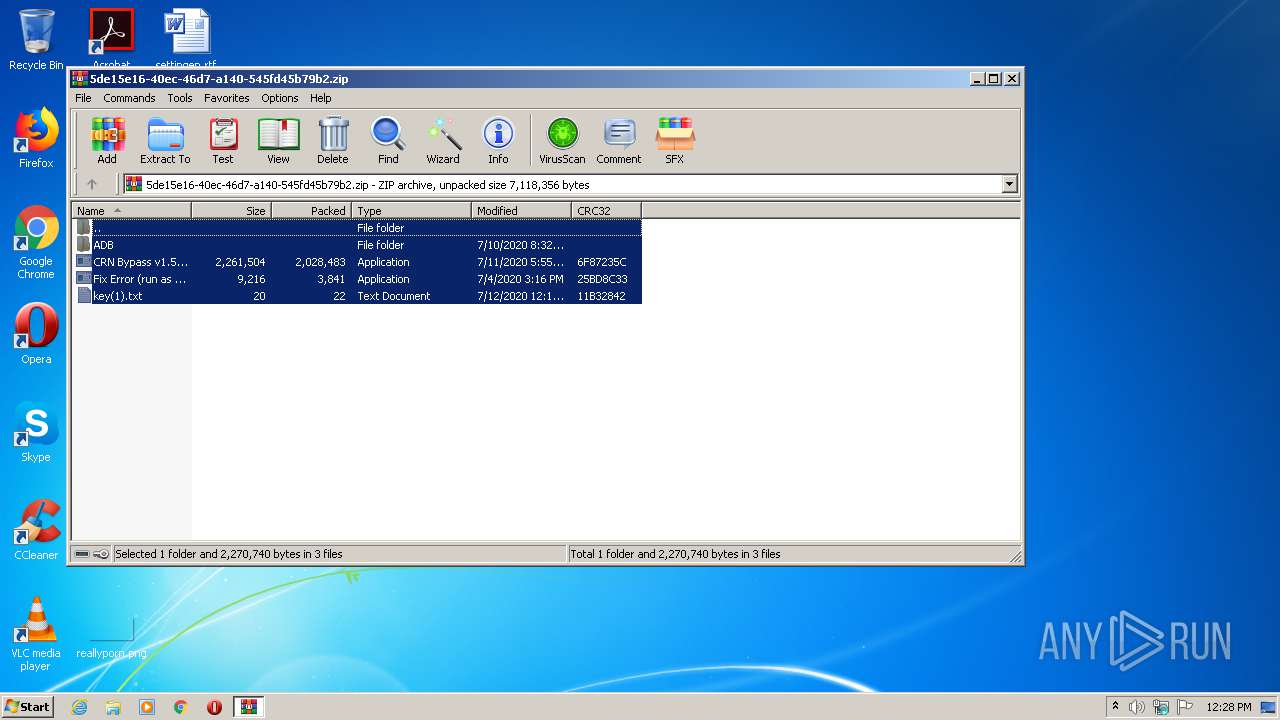
| download: | CRN%20Bypass%20v1.5.1.sp.zip |
| Full analysis: | https://app.any.run/tasks/6127237e-82d1-453c-aeb6-58f9e1e27419 |
| Verdict: | Malicious activity |
| Analysis date: | July 12, 2020, 11:27:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | C7A4433B0DDF7F2F3FD193DFB3F0ED77 |
| SHA1: | 21377EE3CFFFDC44B950C2220133961F49875B36 |
| SHA256: | 259DE2712D2A769833851BE94DB126912D1F2CD25E49B70629EBC6EFD697080F |
| SSDEEP: | 98304:/gE26D/OD9PEDs/CM2KI9rFDQBne+jzXQBA4I8vCvCmuv+e:/g0D/ODVEDsF2lrFDwnhUM5vCmO |
MALICIOUS
Application was dropped or rewritten from another process
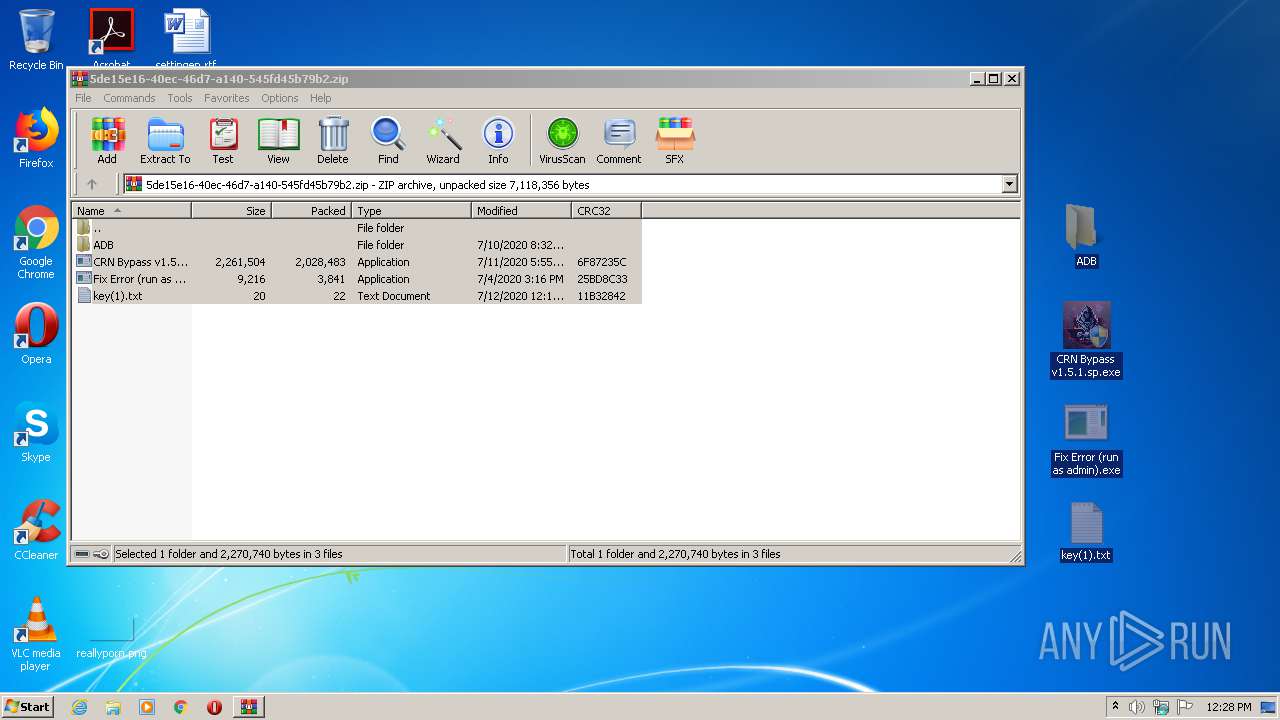
- CRN Bypass v1.5.1.sp.exe (PID: 920)
- CRN Bypass v1.5.1.sp.exe (PID: 2232)
Changes settings of System certificates
- CRN Bypass v1.5.1.sp.exe (PID: 920)
SUSPICIOUS
Application launched itself
- adb.exe (PID: 2288)
- adb.exe (PID: 2344)
- adb.exe (PID: 1240)
- adb.exe (PID: 3052)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2752)
Starts CMD.EXE for commands execution
- CRN Bypass v1.5.1.sp.exe (PID: 920)
Reads internet explorer settings
- CRN Bypass v1.5.1.sp.exe (PID: 920)
Removes files from Windows directory
- CRN Bypass v1.5.1.sp.exe (PID: 920)
Creates files in the Windows directory
- CRN Bypass v1.5.1.sp.exe (PID: 920)
Reads Internet Cache Settings
- CRN Bypass v1.5.1.sp.exe (PID: 920)
Adds / modifies Windows certificates
- CRN Bypass v1.5.1.sp.exe (PID: 920)
INFO
Manual execution by user
- NOTEPAD.EXE (PID: 588)
- CRN Bypass v1.5.1.sp.exe (PID: 920)
- CRN Bypass v1.5.1.sp.exe (PID: 2232)
Reads settings of System Certificates
- CRN Bypass v1.5.1.sp.exe (PID: 920)
Reads the hosts file
- CRN Bypass v1.5.1.sp.exe (PID: 920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:07:11 02:32:20 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | ADB/ |
Total processes
481
Monitored processes
227
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | "ADB\adb.exe" shell iptables -L -n -v dpt:17500 | C:\Users\admin\Desktop\ADB\adb.exe | CRN Bypass v1.5.1.sp.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 332 | "C:\Windows\System32\arp.exe" -a | C:\Windows\System32\arp.exe | — | CRN Bypass v1.5.1.sp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Arp Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 376 | "ADB\adb.exe" shell rm -rf /dev/you | C:\Users\admin\Desktop\ADB\adb.exe | CRN Bypass v1.5.1.sp.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 392 | "ADB\adb.exe" shell iptables -D OUTPUT -p tcp --dport 17500 -j DROP | C:\Users\admin\Desktop\ADB\adb.exe | CRN Bypass v1.5.1.sp.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 588 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\key(1).txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 600 | "C:\Windows\System32\arp.exe" -a | C:\Windows\System32\arp.exe | — | CRN Bypass v1.5.1.sp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Arp Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 620 | "C:\Windows\System32\arp.exe" -a | C:\Windows\System32\arp.exe | — | CRN Bypass v1.5.1.sp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Arp Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 620 | "ADB\adb.exe" shell mv /system/lib/arm/nb/libdl.so /system/lib/arm/nb/libdl.so1 | C:\Users\admin\Desktop\ADB\adb.exe | CRN Bypass v1.5.1.sp.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 648 | "C:\Windows\System32\arp.exe" -a | C:\Windows\System32\arp.exe | — | CRN Bypass v1.5.1.sp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Arp Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 684 | "C:\Windows\System32\arp.exe" -a | C:\Windows\System32\arp.exe | — | CRN Bypass v1.5.1.sp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Arp Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 196
Read events
1 892
Write events
1 304
Delete events
0
Modification events
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\5de15e16-40ec-46d7-a140-545fd45b79b2.zip | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2364) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
0
Suspicious files
0
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2364.13735\ADB\adb.exe | — | |
MD5:— | SHA256:— | |||
| 2364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2364.13735\ADB\AdbWinApi.dll | — | |
MD5:— | SHA256:— | |||
| 2364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2364.13735\ADB\AdbWinUsbApi.dll | — | |
MD5:— | SHA256:— | |||
| 2364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2364.13735\CRN Bypass v1.5.1.sp.exe | — | |
MD5:— | SHA256:— | |||
| 2364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2364.13735\Fix Error (run as admin).exe | — | |
MD5:— | SHA256:— | |||
| 2364 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2364.13735\key(1).txt | — | |
MD5:— | SHA256:— | |||
| 920 | CRN Bypass v1.5.1.sp.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\thongbao[1].txt | text | |
MD5:— | SHA256:— | |||
| 3736 | adb.exe | C:\Users\admin\.android\adbkey.pub | text | |
MD5:— | SHA256:— | |||
| 3736 | adb.exe | C:\Users\admin\.android\adbkey | text | |
MD5:— | SHA256:— | |||
| 920 | CRN Bypass v1.5.1.sp.exe | C:\Windows\config0.dat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
4
DNS requests
2
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
920 | CRN Bypass v1.5.1.sp.exe | GET | 200 | 153.92.6.135:80 | http://filesgame.xyz/Ldbypass/thongbao.txt | US | text | 181 b | suspicious |
920 | CRN Bypass v1.5.1.sp.exe | GET | 200 | 153.92.6.135:80 | http://filesgame.xyz/Ldbypass/dkmconf.dll | US | text | 225 Kb | suspicious |
920 | CRN Bypass v1.5.1.sp.exe | GET | 200 | 153.92.6.135:80 | http://filesgame.xyz/Ldbypass/extest.bat | US | text | 418 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
920 | CRN Bypass v1.5.1.sp.exe | 153.92.6.135:80 | filesgame.xyz | Hostinger International Limited | US | suspicious |
920 | CRN Bypass v1.5.1.sp.exe | 172.67.187.231:443 | api.auth.gg | — | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.auth.gg |
| whitelisted |
filesgame.xyz |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
920 | CRN Bypass v1.5.1.sp.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
920 | CRN Bypass v1.5.1.sp.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
920 | CRN Bypass v1.5.1.sp.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |