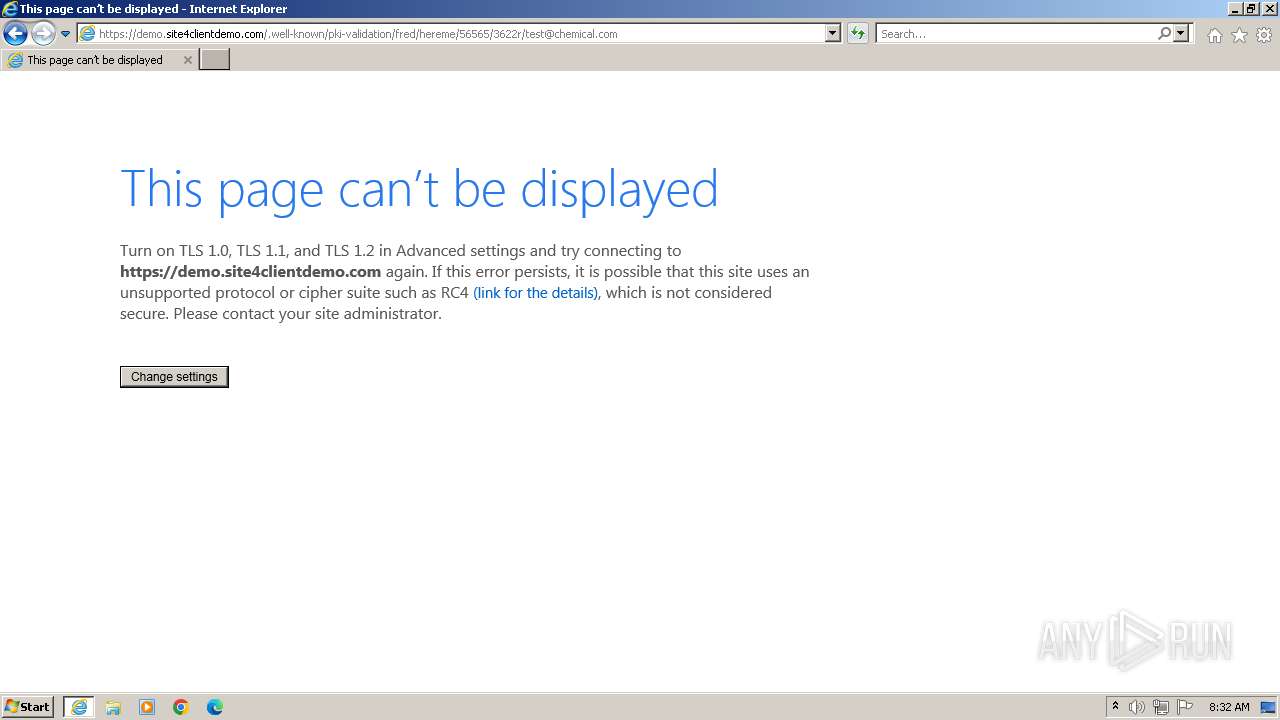
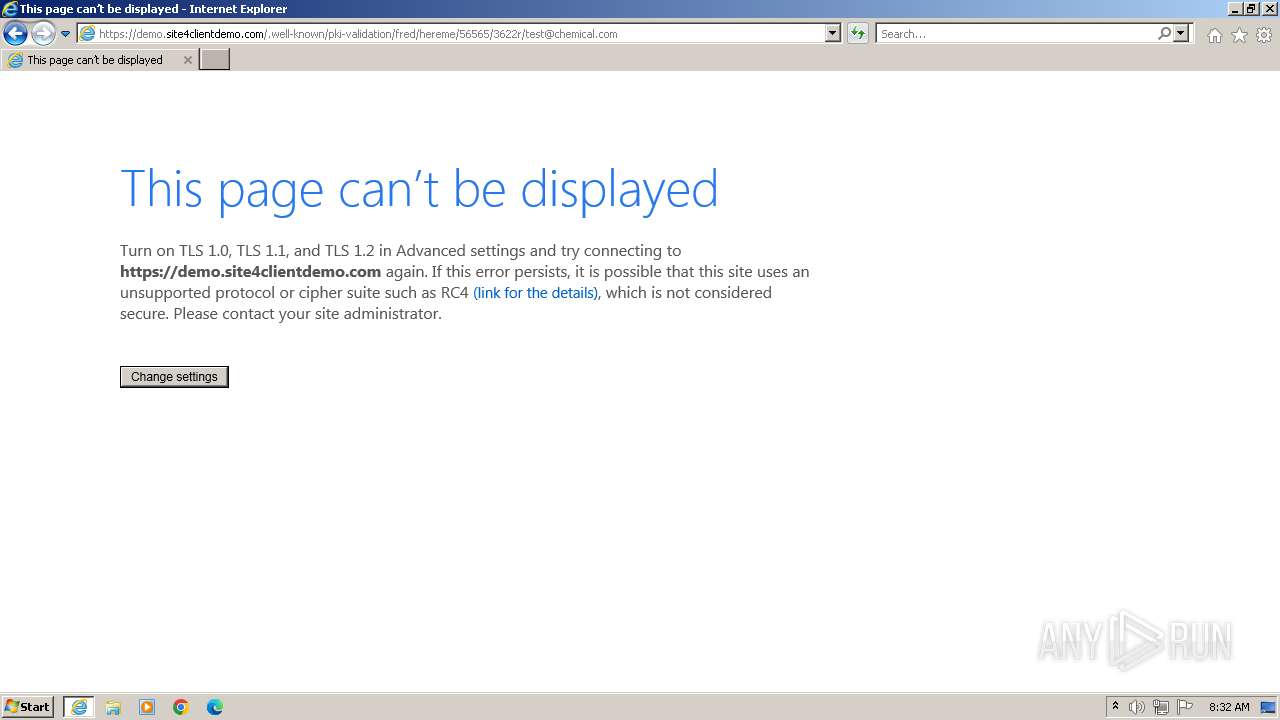
| URL: | http://www.artisteer.com/?p=affr&redirect_url=https://demo.site4clientdemo.com/.well-known/pki-validation/fred/hereme/56565/3622r/test@chemical.com |
| Full analysis: | https://app.any.run/tasks/ad34d139-6760-4ded-8260-eb7b743ea082 |
| Verdict: | Malicious activity |
| Analysis date: | June 14, 2024, 07:31:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C1485E7FDCA4D1AFD9CA953ED206D434 |
| SHA1: | F4BA761BB0DAB00ED33E612F40B9D31068E0027A |
| SHA256: | 259AFD39B304E97BBAC747AD68C9B1A880E4E3AB0EDAE6CF810404D2F1597FCD |
| SSDEEP: | 3:N1KJS4kmNBQwIVYA35DLRgnLKHFITEJMPK8XA3QzKU6AWRagZI:Cc4kmNBQvOA3NWUAgsDAgF6AWRxZI |
MALICIOUS
PHISHING has been detected (SURICATA)
- iexplore.exe (PID: 4040)
SUSPICIOUS
No suspicious indicators.INFO
Reads the computer name
- wmpnscfg.exe (PID: 2044)
Application launched itself
- iexplore.exe (PID: 3980)
Manual execution by a user
- wmpnscfg.exe (PID: 2044)
Checks supported languages
- wmpnscfg.exe (PID: 2044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
35
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2044 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3980 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://www.artisteer.com/?p=affr&redirect_url=https://demo.site4clientdemo.com/.well-known/pki-validation/fred/hereme/56565/3622r/test@chemical.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4040 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3980 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
13 990
Read events
13 878
Write events
84
Delete events
28
Modification events
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31112748 | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31112748 | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3980) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
12
Text files
18
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:687CDB0EEA2DFECEAA4A040CF3A968C4 | SHA256:8A8DB8D7E0E0FEC7A89E599FD742586EC2FFC6DC999FFD150A375548F32332A5 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\49QRMLNG.htm | html | |
MD5:7CF01E72E9CE078F24AA76325B13ACA5 | SHA256:8856478E3A0E98ED2A9F6CC6955C9A175652A2296DD73445EF84C8B09CB1D384 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\OBR40UQO.txt | text | |
MD5:0687EF49AEC1059A3305B7DBB31BD3C3 | SHA256:3FA40740A46D651D5BBD6EED3CF3A3913932EECECD071559692EC4E100BAEF46 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\ScriptResource[2].js | text | |
MD5:293225A1852BC02172824F2EAA147BBC | SHA256:478E3E804DA65473CC8A91566105A2AEC5F8F3B3E2DFE1B61FADCA8B8A7AD5B7 | |||
| 3980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:47FDD9AA186FD9DB2630E249BF71E922 | SHA256:F45268068F427D7994C0E239E776E22A4A60E9F5C9DC16D7E472F19C14547295 | |||
| 4040 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\TYX336G5.txt | text | |
MD5:F3FDAF7FB294D793CC30861DF01C1DD7 | SHA256:D601244D25A4E4A8D0C0A621D2FB962A063BBA0245F2976D5BCC15A8C75182CF | |||
| 3980 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:C38E8F3BA03A34838420AA61D646CED8 | SHA256:F3422DA3754E33B84F0C47A04485C15E8ED423E9EF44513E66747FD0B858A161 | |||
| 3980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\urlblockindex[1].bin | binary | |
MD5:FA518E3DFAE8CA3A0E495460FD60C791 | SHA256:775853600060162C4B4E5F883F9FD5A278E61C471B3EE1826396B6D129499AA7 | |||
| 3980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\versionlist.xml | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 3980 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\verA347.tmp | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
31
DNS requests
20
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3980 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
3980 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 200 | 199.241.142.75:80 | http://www.artisteer.com/?p=affr&redirect_url=https://demo.site4clientdemo.com/.well-known/pki-validation/fred/hereme/56565/3622r/test@chemical.com | unknown | — | — | unknown |
3980 | iexplore.exe | GET | 304 | 2.17.107.203:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?32a7a8361135dd15 | unknown | — | — | unknown |
3980 | iexplore.exe | GET | 304 | 2.17.107.144:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?260f79dbb405aab9 | unknown | — | — | unknown |
3980 | iexplore.exe | GET | 304 | 2.17.107.203:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c21588876f974d24 | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 200 | 199.241.142.75:80 | http://www.artisteer.com/WebResource.axd?d=Lo0R_kQ5nI3G8nTRpiWN4FEzUk8kzq9dknh5Oafna5V6VUXel5I291KXC9inc9LBSb7tM7SjbSqyNsZgzqCggfWSChY1&t=638313893260000000 | unknown | — | — | unknown |
4040 | iexplore.exe | GET | 200 | 199.241.142.75:80 | http://www.artisteer.com/ScriptResource.axd?d=dUMhT7Uj5LIFcK_baQE2gF65ZkVUkyIA0E2SxvrWLyzdYm953gw-S5vgTT6TwjLTHVAokFei4pD67-rXrbWIfFVSefALbdrmdsfvx_o4h_B2671x4hiMKhs8aRVjfyaBibaWkc0lJZ4r5db-ejrGlhvv5FxpKABtwCSAS8pHv_f0qzku0&t=636427723659783182 | unknown | — | — | unknown |
3980 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
3980 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4040 | iexplore.exe | 199.241.142.75:80 | — | FIBERHUB | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3980 | iexplore.exe | 23.222.16.32:443 | www.bing.com | Akamai International B.V. | US | unknown |
3980 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
3980 | iexplore.exe | 2.17.107.203:80 | ctldl.windowsupdate.com | Akamai International B.V. | BE | unknown |
3980 | iexplore.exe | 2.17.107.144:80 | ctldl.windowsupdate.com | Akamai International B.V. | BE | unknown |
3980 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4040 | iexplore.exe | 185.199.220.80:443 | demo.site4clientdemo.com | Krystal Hosting Ltd | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
demo.site4clientdemo.com |
| unknown |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4040 | iexplore.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] A suspicious URI containing an email address |