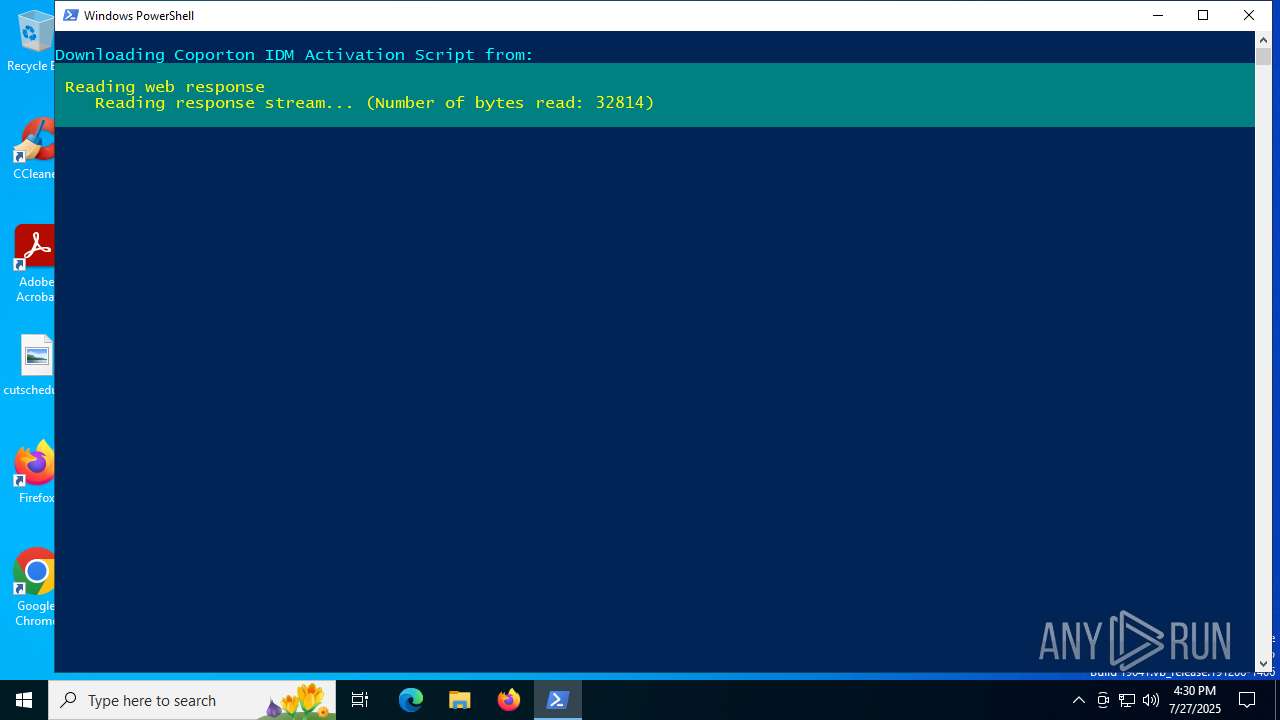
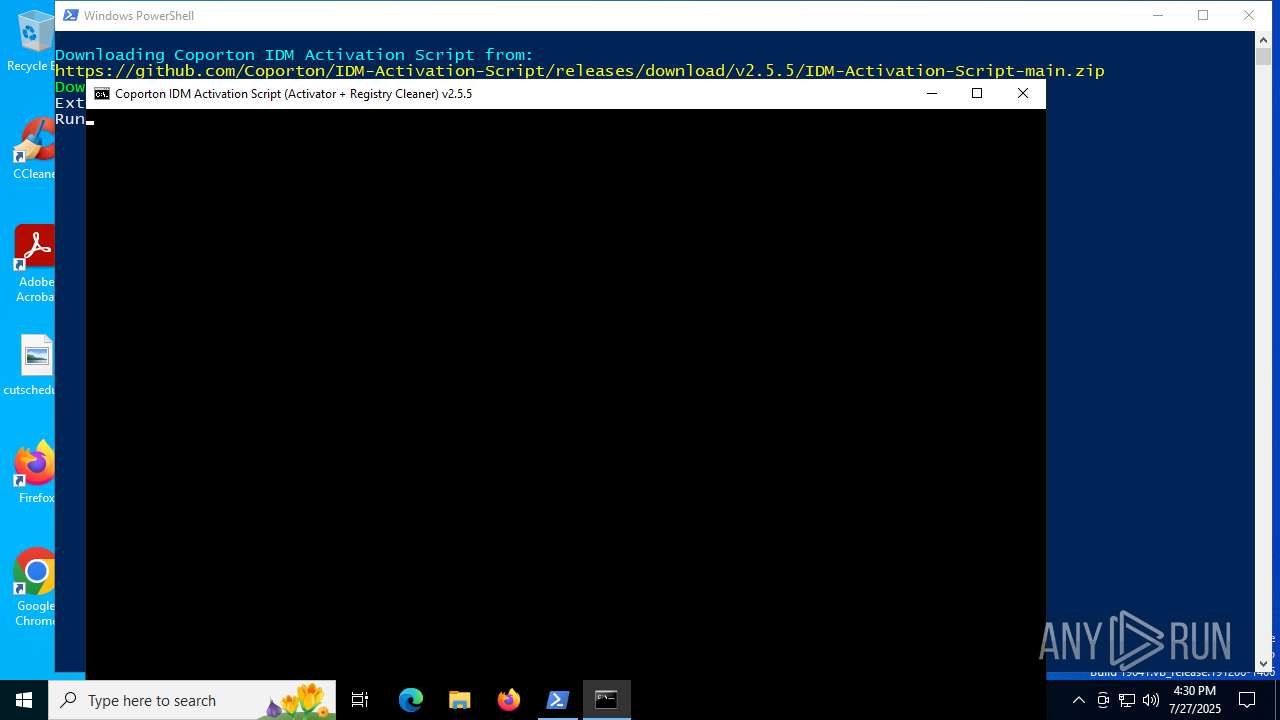
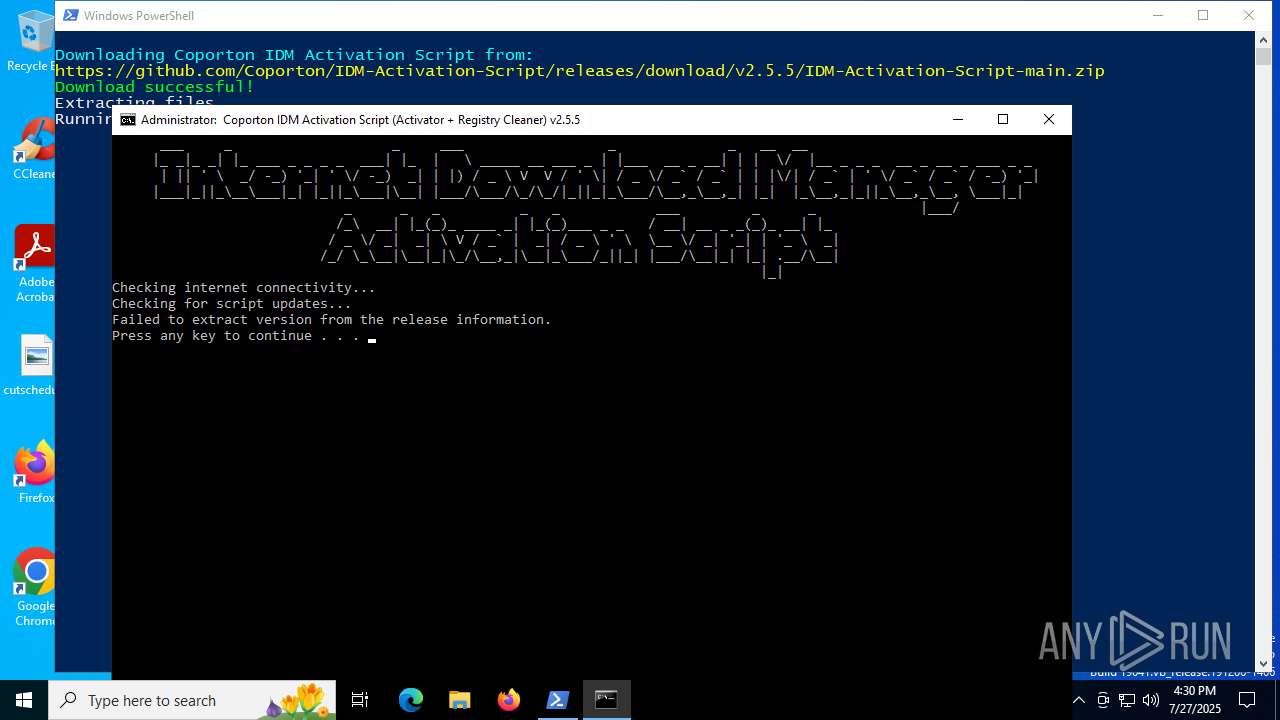
| File name: | activate-idm.ps1 |
| Full analysis: | https://app.any.run/tasks/af09a08a-2575-44a0-b069-2f6316abda7d |
| Verdict: | Malicious activity |
| Analysis date: | July 27, 2025, 16:30:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text, with CRLF line terminators |
| MD5: | 6096F67803669F0471E191E01E1873FF |
| SHA1: | 8DFDD5D195E7C6034321142AFC4AE610430CEA7E |
| SHA256: | 258FAD9D13AA4335575F4E47D44001931F606ADB9A69A94E28ACF6A068FFF4F0 |
| SSDEEP: | 12:9v9AdRRAVxXt4isgAjmRAVWu22gZV1QUcOFFRAVEMxvU:QwVxXuXDVqzDc/VJxvU |
MALICIOUS
Script downloads file (POWERSHELL)
- powershell.exe (PID: 2716)
Bypass execution policy to execute commands
- powershell.exe (PID: 2716)
SUSPICIOUS
Executable content was dropped or overwritten
- powershell.exe (PID: 2716)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 2716)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 2716)
Executing commands from ".cmd" file
- powershell.exe (PID: 2716)
- wscript.exe (PID: 6636)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2716)
- wscript.exe (PID: 6636)
- cmd.exe (PID: 3964)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 4880)
- cmd.exe (PID: 3964)
The process executes VB scripts
- cmd.exe (PID: 4880)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6636)
Starts application with an unusual extension
- cmd.exe (PID: 3964)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5372)
Application launched itself
- cmd.exe (PID: 3964)
INFO
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2716)
Disables trace logs
- powershell.exe (PID: 2716)
Checks proxy server information
- powershell.exe (PID: 2716)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 2716)
The sample compiled with english language support
- powershell.exe (PID: 2716)
Starts MODE.COM to configure console settings
- mode.com (PID: 1740)
- mode.com (PID: 1056)
Checks supported languages
- mode.com (PID: 1740)
- mode.com (PID: 1056)
- chcp.com (PID: 6240)
- curl.exe (PID: 3620)
Execution of CURL command
- cmd.exe (PID: 3964)
Changes the display of characters in the console
- cmd.exe (PID: 3964)
Reads the computer name
- curl.exe (PID: 3620)
Create files in a temporary directory
- curl.exe (PID: 3620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
152
Monitored processes
17
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1056 | mode con: cols=120 lines=40 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1488 | "C:\WINDOWS\system32\cacls.exe" "C:\WINDOWS\system32\config\system" | C:\Windows\System32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1740 | mode con: cols=120 lines=40 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2716 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\AppData\Local\Temp\activate-idm.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3620 | curl -s "https://api.github.com/repos/coporton/IDM-Activation-Script/releases/latest" -o "C:\Users\admin\AppData\Local\Temp\latest_release.json" | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: HIGH Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 3624 | ping -n 1 google.com | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3964 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\AppData\Local\Temp\RE0GA1~1\IDM-AC~1\IASL.cmd" | C:\Windows\System32\cmd.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4100 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4788 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 270
Read events
12 267
Write events
3
Delete events
0
Modification events
| (PID) Process: | (4880) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (6636) wscript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.FriendlyAppName |
Value: Windows Command Processor | |||
| (PID) Process: | (6636) wscript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
Executable files
2
Suspicious files
6
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2716 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\D9XY2EJ1T01TXMDL1OAS.temp | binary | |
MD5:5BB7E599ED14B2594516FA77AF028B77 | SHA256:D5466429E26C18737A9C58D39A96783551DDFA41946A147300FF050C5315A972 | |||
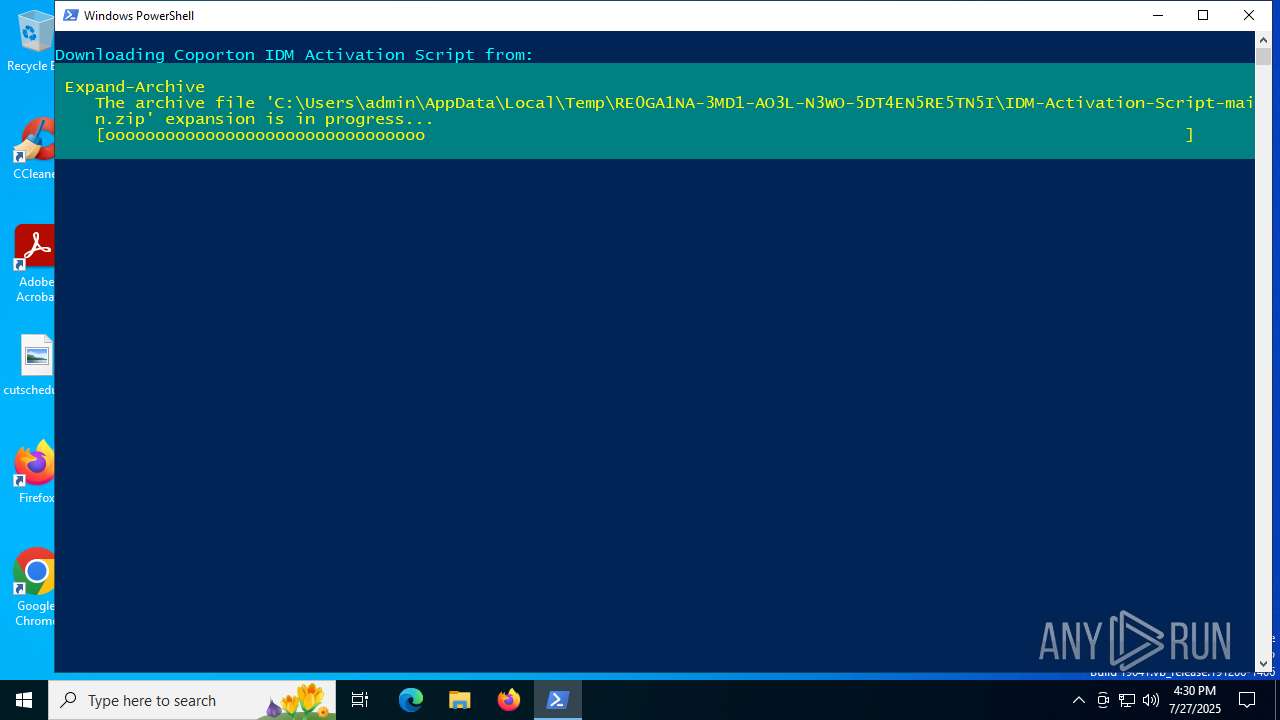
| 2716 | powershell.exe | C:\Users\admin\AppData\Local\Temp\RE0GA1NA-3MD1-AO3L-N3WO-5DT4EN5RE5TN5I\IDM-Activation-Script-main.zip | compressed | |
MD5:D13B27B649C1B810EB5508BC190C8AA3 | SHA256:53B20C5309487AEBB7BBEAE25415AEFCB0ADCEAA3D10C30B35F2B1A06243972A | |||
| 2716 | powershell.exe | C:\Users\admin\AppData\Local\Temp\RE0GA1NA-3MD1-AO3L-N3WO-5DT4EN5RE5TN5I\IDM-Activation-Script-main\src\registry.bin | text | |
MD5:F6761187E06FEAFA15C935FE8D57FE1E | SHA256:0512368B6C65FBD5749FFBF8D8FCEEBB13A352544B883EB8452ED3B8F20040F5 | |||
| 2716 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:5BB7E599ED14B2594516FA77AF028B77 | SHA256:D5466429E26C18737A9C58D39A96783551DDFA41946A147300FF050C5315A972 | |||
| 2716 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_x5prcqky.t21.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2716 | powershell.exe | C:\Users\admin\AppData\Local\Temp\RE0GA1NA-3MD1-AO3L-N3WO-5DT4EN5RE5TN5I\IDM-Activation-Script-main\src\extensions.bin | text | |
MD5:D75CEB6BEC202AC2E4157FA5CCF2EA40 | SHA256:DF89AA1FF1712E82FE4C87348A745D5856D52A683C019509F7FFD02BAE7BEE0F | |||
| 2716 | powershell.exe | C:\Users\admin\AppData\Local\Temp\RE0GA1NA-3MD1-AO3L-N3WO-5DT4EN5RE5TN5I\IDM-Activation-Script-main\src\data.bin | executable | |
MD5:8A78FC740AB4BDC0F219B41B53A01AF7 | SHA256:6D606A196579DCA1478C8D78FC3FA43BA3CEDC2562578CF27AEBC35AB72C3900 | |||
| 2716 | powershell.exe | C:\Users\admin\AppData\Local\Temp\RE0GA1NA-3MD1-AO3L-N3WO-5DT4EN5RE5TN5I\IDM-Activation-Script-main\src\banner_art.txt | text | |
MD5:13BFEF56E214DC91015E3341ACDA17E9 | SHA256:86EA90A9D22AA5CF5DD15C14C869DA34FEA66E427EE4863A9DA68BAC8740B8EE | |||
| 2716 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_evccbzpu.zoc.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2716 | powershell.exe | C:\Users\admin\AppData\Local\Temp\RE0GA1NA-3MD1-AO3L-N3WO-5DT4EN5RE5TN5I\IDM-Activation-Script-main\IASL.cmd | text | |
MD5:6F859F26BE3669D260D528F9D55EE8D7 | SHA256:ECA26504D031FA05CDF97029952843C7471567C76C2794F739F361EAFE5E6950 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
28
DNS requests
24
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5084 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CECoW9cIBGAf3CpJj3Tw5qfI%3D | unknown | — | — | whitelisted |
4228 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4228 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1636 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
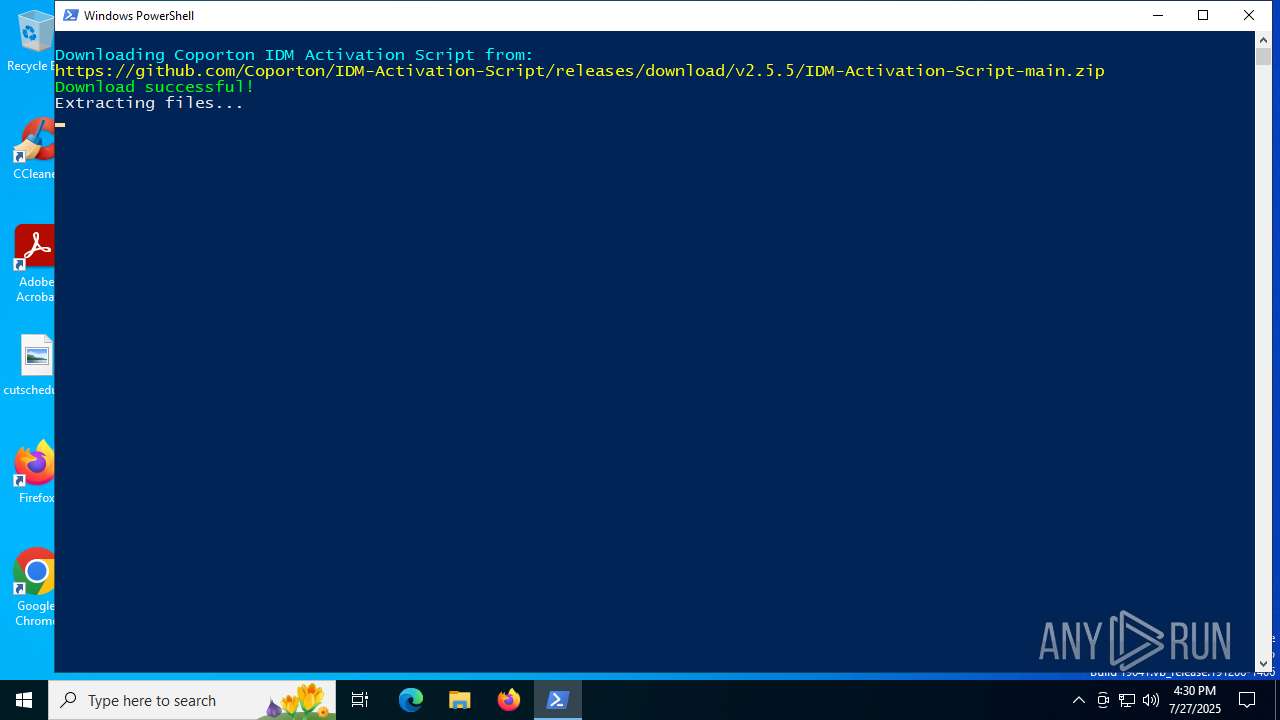
2716 | powershell.exe | 103.118.78.250:443 | coporton.com | Vision Technologies Ltd. | BD | unknown |
2716 | powershell.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
2716 | powershell.exe | 185.199.111.133:443 | release-assets.githubusercontent.com | FASTLY | US | unknown |
2716 | powershell.exe | 169.61.27.133:443 | www.internetdownloadmanager.com | SOFTLAYER | US | whitelisted |
5084 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
coporton.com |
| unknown |
github.com |
| whitelisted |
release-assets.githubusercontent.com |
| unknown |
www.internetdownloadmanager.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access release user assets on GitHub |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |