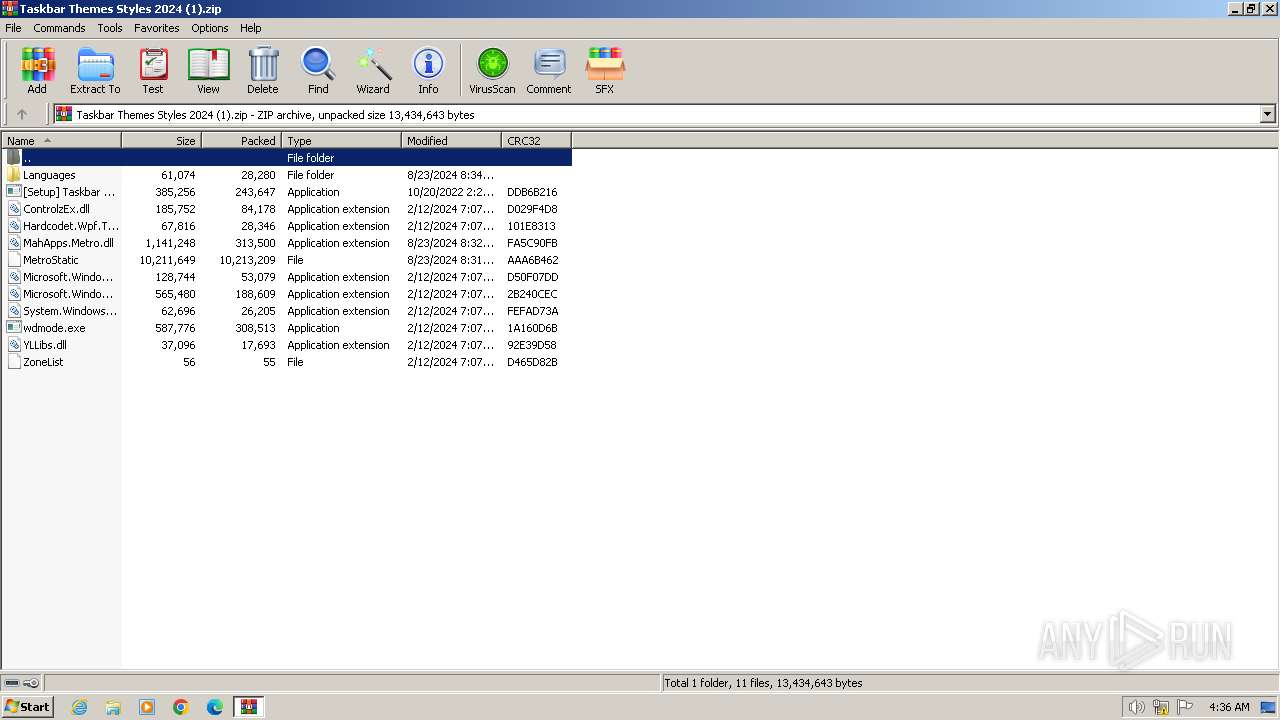
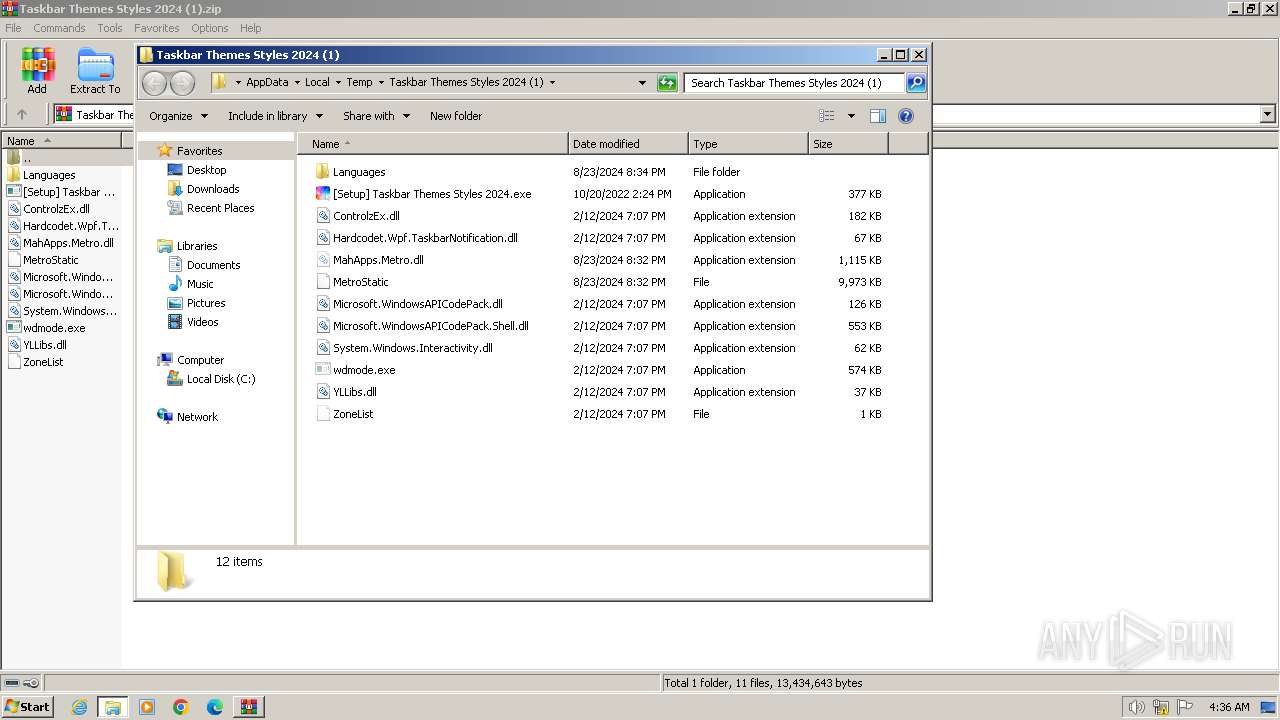
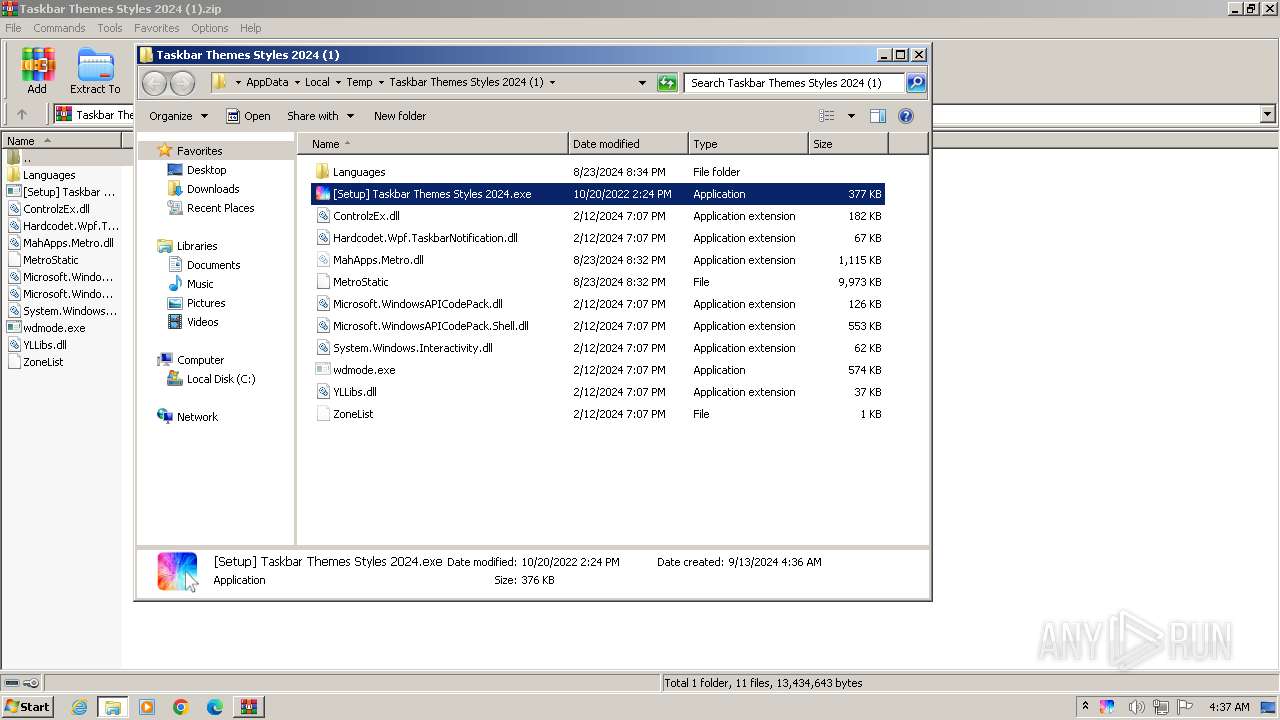
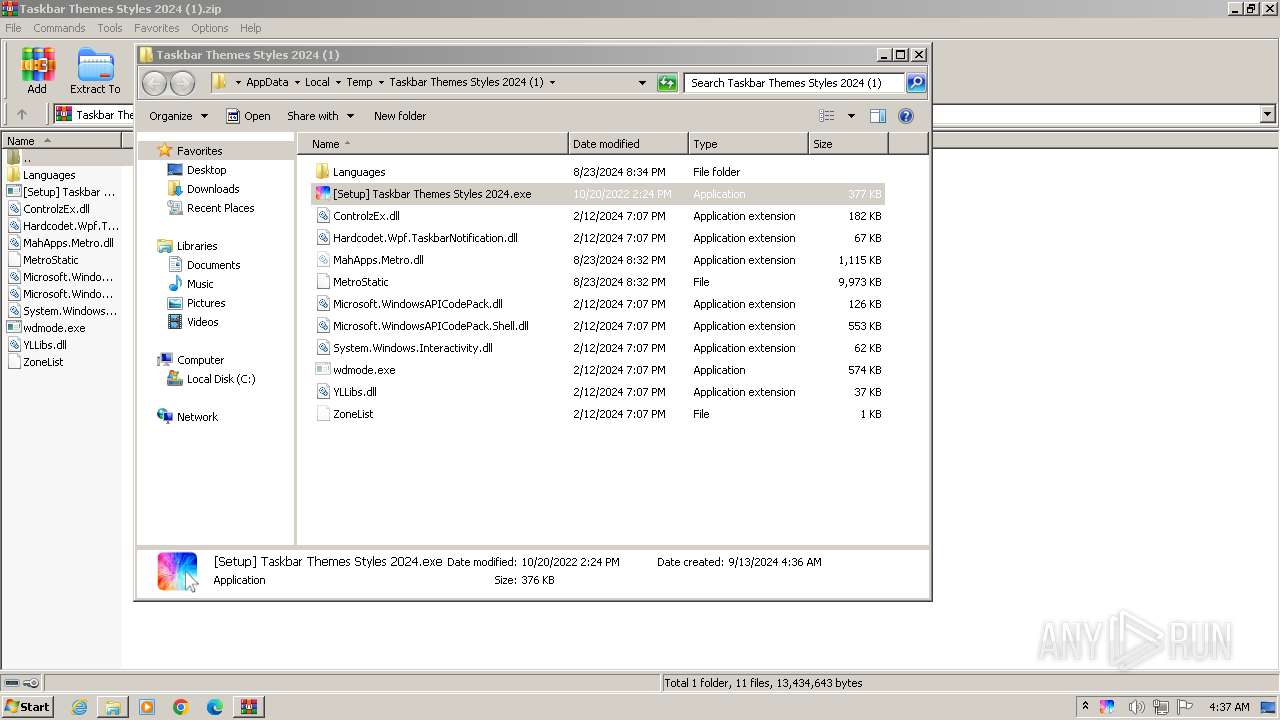
| File name: | Taskbar Themes Styles 2024 (1).zip |
| Full analysis: | https://app.any.run/tasks/93d06629-0a3a-417a-a576-f4fa5790e86a |
| Verdict: | Malicious activity |
| Analysis date: | September 13, 2024, 03:36:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | BBCE5AF5003B12FD1B7DC5B48D497427 |
| SHA1: | AA69ADD762449BB83640DCBE544D28C12AD47F0C |
| SHA256: | 258F173916BB22E869510B99A998F0220B1338F8515B29D06AAD70BF1533193E |
| SSDEEP: | 98304:NCK4TdpZC8KPEANCjdLpwTto9Zx/LtYb3WCvlKcDdA1HwocD9NJ5zjSCaU0v1Y34:YajWsb4doNyVXgI0on7ccdtpkWza/U1 |
MALICIOUS
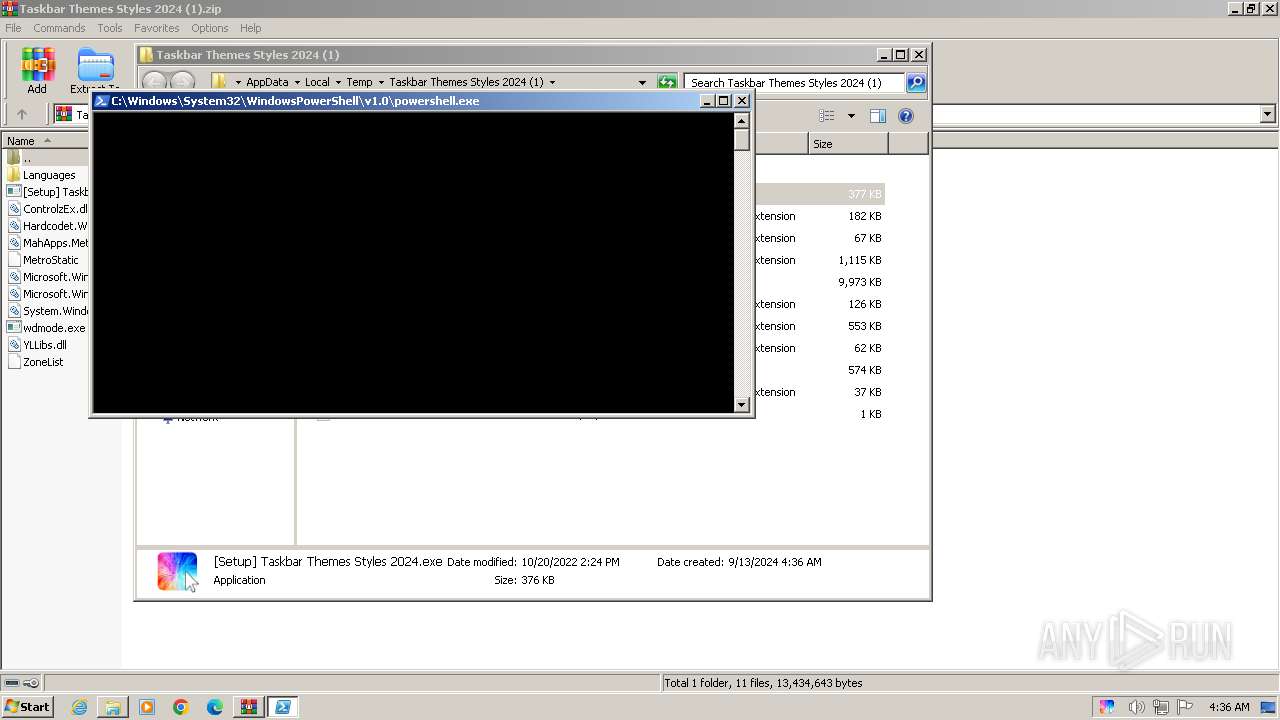
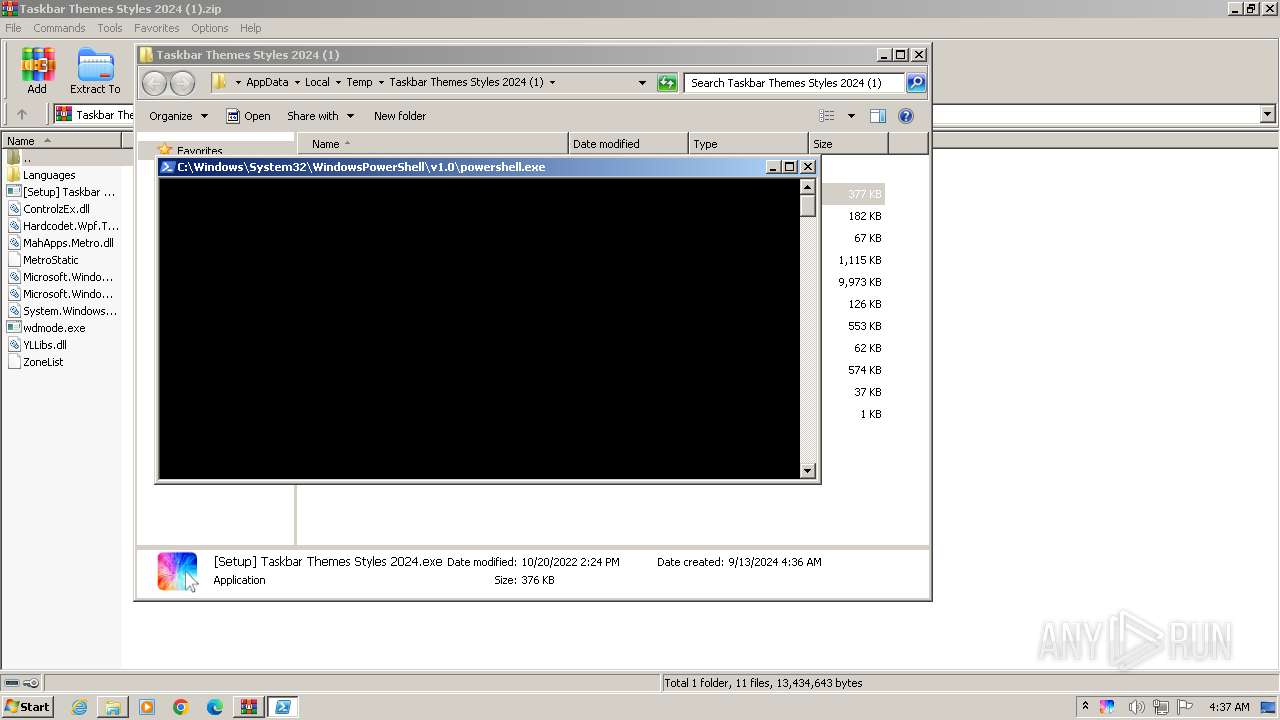
Bypass execution policy to execute commands
- powershell.exe (PID: 1892)
- powershell.exe (PID: 3220)
- powershell.exe (PID: 2512)
Changes powershell execution policy (Bypass)
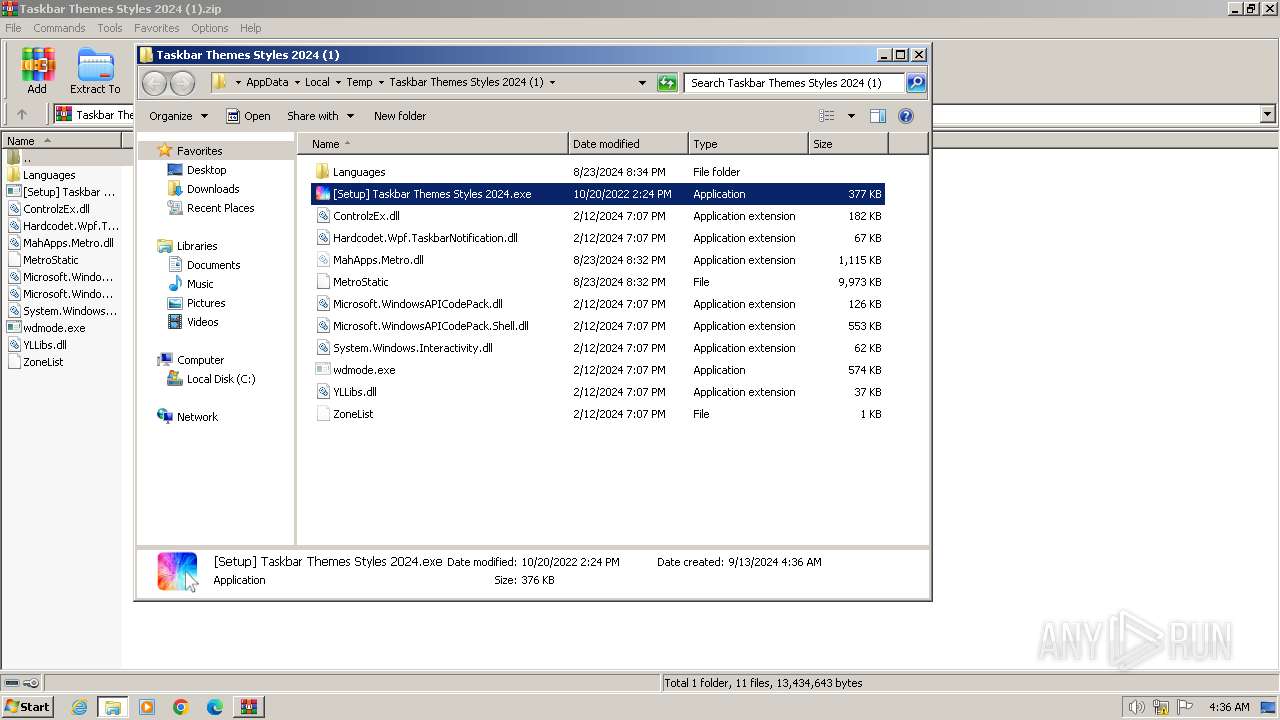
- [Setup] Taskbar Themes Styles 2024.exe (PID: 3564)
- [Setup] Taskbar Themes Styles 2024.exe (PID: 3120)
- [Setup] Taskbar Themes Styles 2024.exe (PID: 1412)
Run PowerShell with an invisible window
- powershell.exe (PID: 1892)
- powershell.exe (PID: 3220)
- powershell.exe (PID: 2512)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 2788)
Starts POWERSHELL.EXE for commands execution
- [Setup] Taskbar Themes Styles 2024.exe (PID: 3564)
- [Setup] Taskbar Themes Styles 2024.exe (PID: 3120)
- [Setup] Taskbar Themes Styles 2024.exe (PID: 1412)
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 2788)
Reads the Internet Settings
- [Setup] Taskbar Themes Styles 2024.exe (PID: 3564)
- [Setup] Taskbar Themes Styles 2024.exe (PID: 3120)
- [Setup] Taskbar Themes Styles 2024.exe (PID: 1412)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 2788)
INFO
Checks supported languages
- [Setup] Taskbar Themes Styles 2024.exe (PID: 3564)
- wmpnscfg.exe (PID: 4080)
- [Setup] Taskbar Themes Styles 2024.exe (PID: 3120)
- [Setup] Taskbar Themes Styles 2024.exe (PID: 1412)
The process uses the downloaded file
- WinRAR.exe (PID: 2788)
Manual execution by a user
- wmpnscfg.exe (PID: 4080)
- [Setup] Taskbar Themes Styles 2024.exe (PID: 3564)
- [Setup] Taskbar Themes Styles 2024.exe (PID: 3120)
- [Setup] Taskbar Themes Styles 2024.exe (PID: 1412)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2788)
Reads the computer name
- [Setup] Taskbar Themes Styles 2024.exe (PID: 3564)
- wmpnscfg.exe (PID: 4080)
- [Setup] Taskbar Themes Styles 2024.exe (PID: 3120)
- [Setup] Taskbar Themes Styles 2024.exe (PID: 1412)
Reads the machine GUID from the registry
- [Setup] Taskbar Themes Styles 2024.exe (PID: 3564)
- [Setup] Taskbar Themes Styles 2024.exe (PID: 3120)
- [Setup] Taskbar Themes Styles 2024.exe (PID: 1412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:10:20 20:24:16 |
| ZipCRC: | 0xddb6b216 |
| ZipCompressedSize: | 243647 |
| ZipUncompressedSize: | 385256 |
| ZipFileName: | [Setup] Taskbar Themes Styles 2024.exe |
Total processes
57
Monitored processes
8
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1412 | "C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1)\[Setup] Taskbar Themes Styles 2024.exe" | C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1)\[Setup] Taskbar Themes Styles 2024.exe | explorer.exe | ||||||||||||
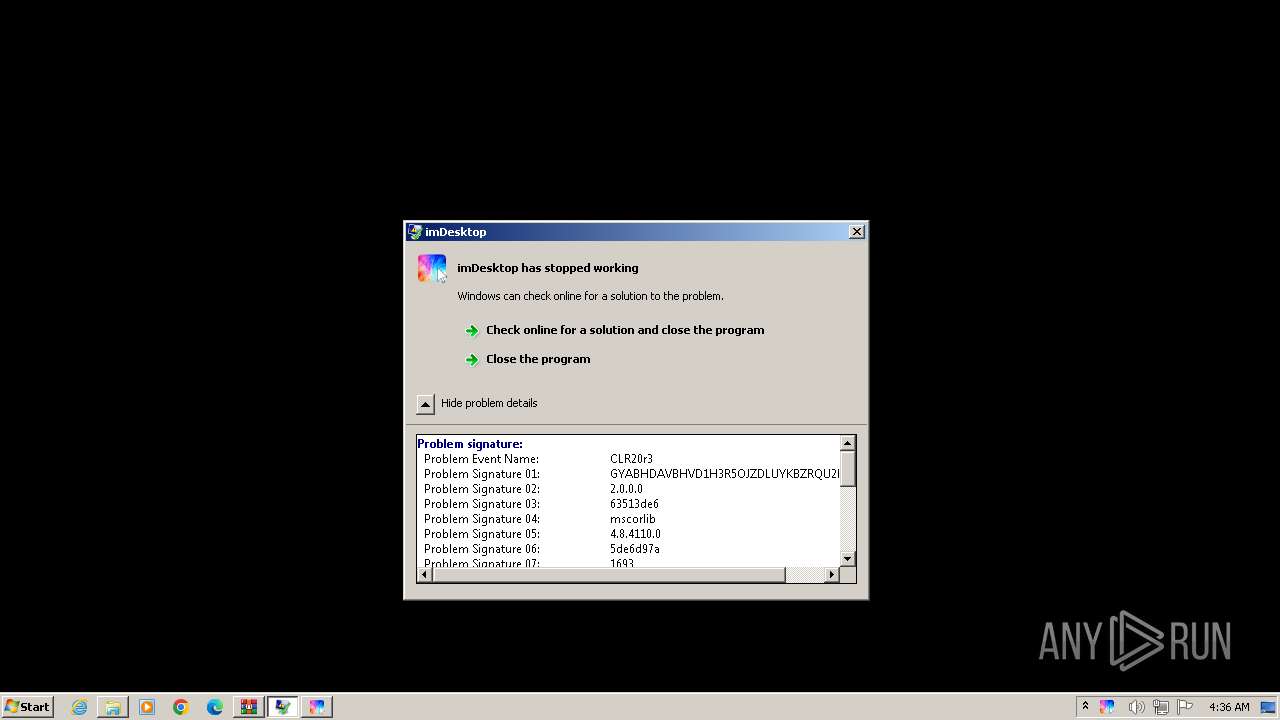
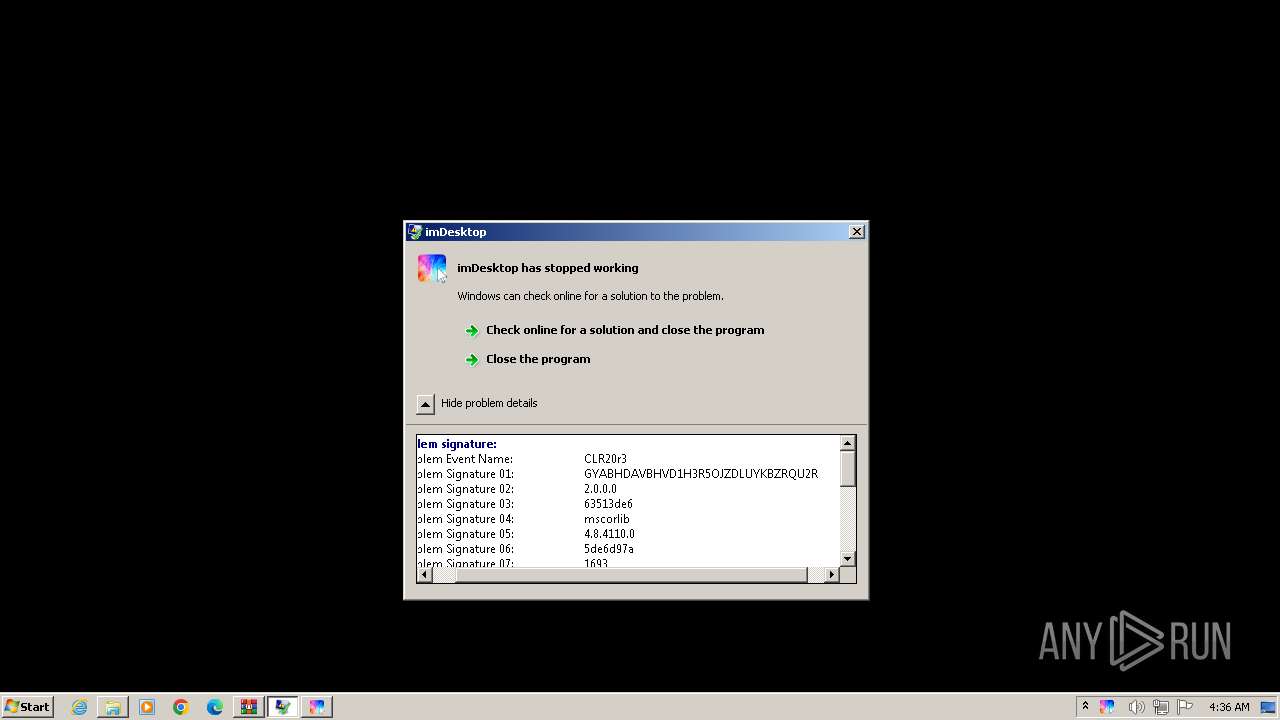
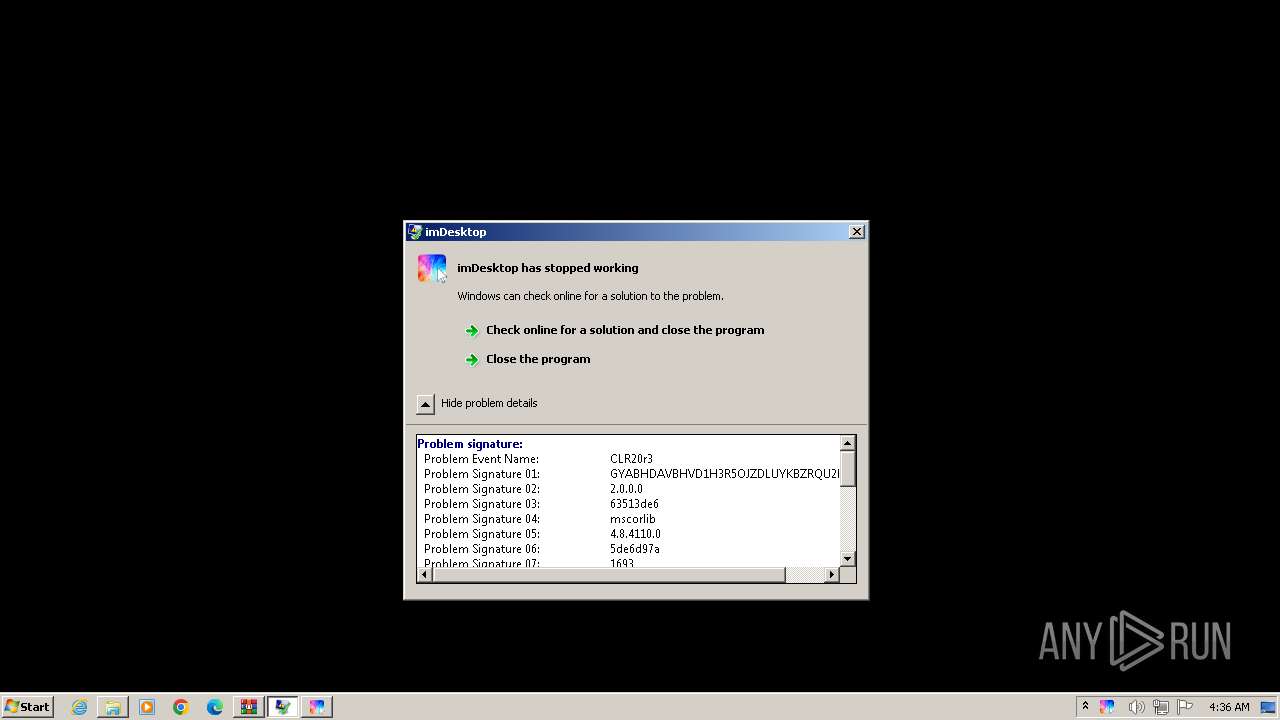
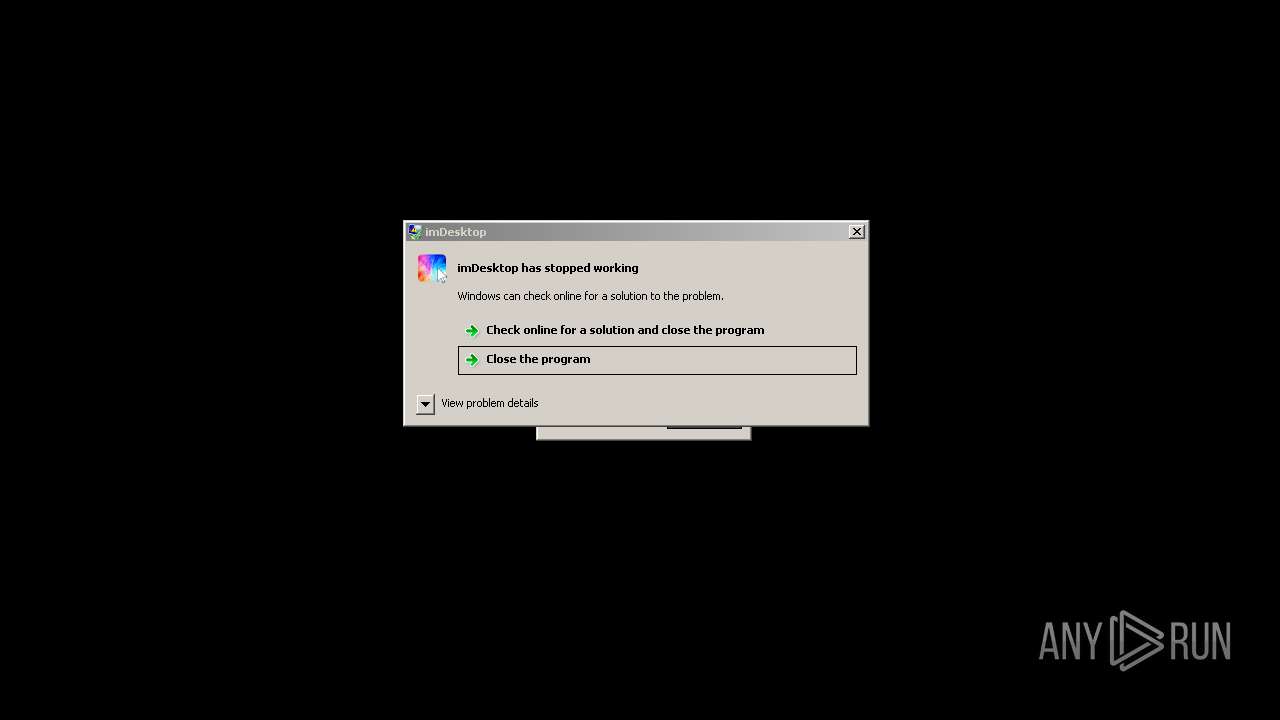
User: admin Company: YL Computing Integrity Level: HIGH Description: imDesktop Version: 2.0.0.0 Modules
| |||||||||||||||
| 1892 | "powershell.exe" -WindowStyle Hidden -ExecutionPolicy Bypass -Command "(Get-CimInstance -ClassName Win32_VideoController).Caption;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | [Setup] Taskbar Themes Styles 2024.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2512 | "powershell.exe" -WindowStyle Hidden -ExecutionPolicy Bypass -Command "(Get-CimInstance -ClassName Win32_VideoController).Caption;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | [Setup] Taskbar Themes Styles 2024.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2788 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3120 | "C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1)\[Setup] Taskbar Themes Styles 2024.exe" | C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1)\[Setup] Taskbar Themes Styles 2024.exe | explorer.exe | ||||||||||||
User: admin Company: YL Computing Integrity Level: HIGH Description: imDesktop Exit code: 3762504530 Version: 2.0.0.0 Modules
| |||||||||||||||
| 3220 | "powershell.exe" -WindowStyle Hidden -ExecutionPolicy Bypass -Command "(Get-CimInstance -ClassName Win32_VideoController).Caption;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | [Setup] Taskbar Themes Styles 2024.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3564 | "C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1)\[Setup] Taskbar Themes Styles 2024.exe" | C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1)\[Setup] Taskbar Themes Styles 2024.exe | — | explorer.exe | |||||||||||
User: admin Company: YL Computing Integrity Level: MEDIUM Description: imDesktop Exit code: 3221225547 Version: 2.0.0.0 Modules
| |||||||||||||||
| 4080 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 236
Read events
6 214
Write events
20
Delete events
2
Modification events
| (PID) Process: | (2788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2788) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1).zip | |||
| (PID) Process: | (2788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2788) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
9
Suspicious files
7
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1)\MetroStatic | — | |
MD5:— | SHA256:— | |||
| 2788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1)\wdmode.exe | executable | |
MD5:42BADC1D2F03A8B1E4875740D3D49336 | SHA256:C136B1467D669A725478A6110EBAAAB3CB88A3D389DFA688E06173C066B76FCF | |||
| 2788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1)\Microsoft.WindowsAPICodePack.dll | executable | |
MD5:ACE419174E1E0C792D028F25F60D6E5F | SHA256:90D56B0A1C7E631E5A12985F9B7CC943A1EBC31E40EC53D56DC9149BBA74BA24 | |||
| 2788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1)\Hardcodet.Wpf.TaskbarNotification.dll | executable | |
MD5:D5D708E9E7625AB2C4AC1C1FAA099350 | SHA256:F6FADF0375D22512B2B3F075362433C0DE173ADFB290B4D8999CDCB7ACEDB0B2 | |||
| 2788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1)\YLLibs.dll | executable | |
MD5:3744D4FD7BA093923174696B56D05F9F | SHA256:3101A828D70C878E777A15EBB522B6A2F82E30FB2217CE66DF0F161A57656301 | |||
| 2788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1)\Languages\English.xml | xml | |
MD5:2091E6D656AE235A0E7977B0D5A51CE3 | SHA256:C3CC0E93F9FFF36858CA43188BFD6B67B39EE207B373C8A1601B973B2F07395A | |||
| 2788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1)\Languages\English.png | image | |
MD5:00214D9E4E6155A04E3997D121641C98 | SHA256:1037BB804C8DA171FB1869872BCD24AA1F0C96AD8CE783861DFF91D3174D12A7 | |||
| 2788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1)\Languages\Chinese(Simplified).xml | xml | |
MD5:2BA8908901C62E486DC7D4CE5822ACF3 | SHA256:BC98DB44EBC96B4BA51AD23A7B716584F40B8A1D5A46AE6751AA948CE9FE9F86 | |||
| 2788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1)\Languages\Bengali.txt | text | |
MD5:42B876B1F17EFAB82F9C4A4808C3B9D9 | SHA256:E46EA74CDD5EFF143112695A3FAA585BA5C319102E5AE57E9AEE69A9076FD2C9 | |||
| 2788 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Taskbar Themes Styles 2024 (1)\Languages\Chinese(Simplified).png | image | |
MD5:18BD6697BC44BCFAA606AEC883FDF1C4 | SHA256:3705C17E9A6CF982234898D0269B94427FB3B1978BECE5CF4F3A6C3BF518DA70 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
9
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 404 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 404 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?02aae7cfd52f5e66 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1372 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
1060 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
240 | WerFault.exe | 104.208.16.93:443 | watson.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
watson.microsoft.com |
| whitelisted |