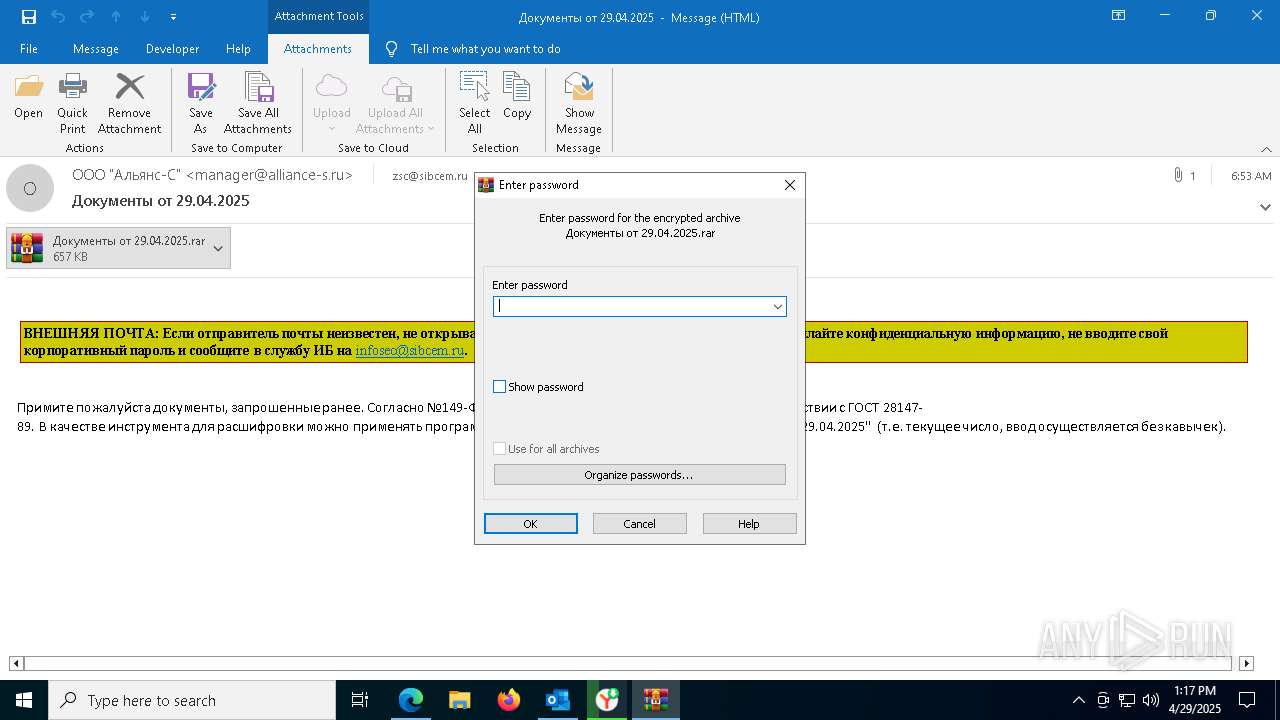
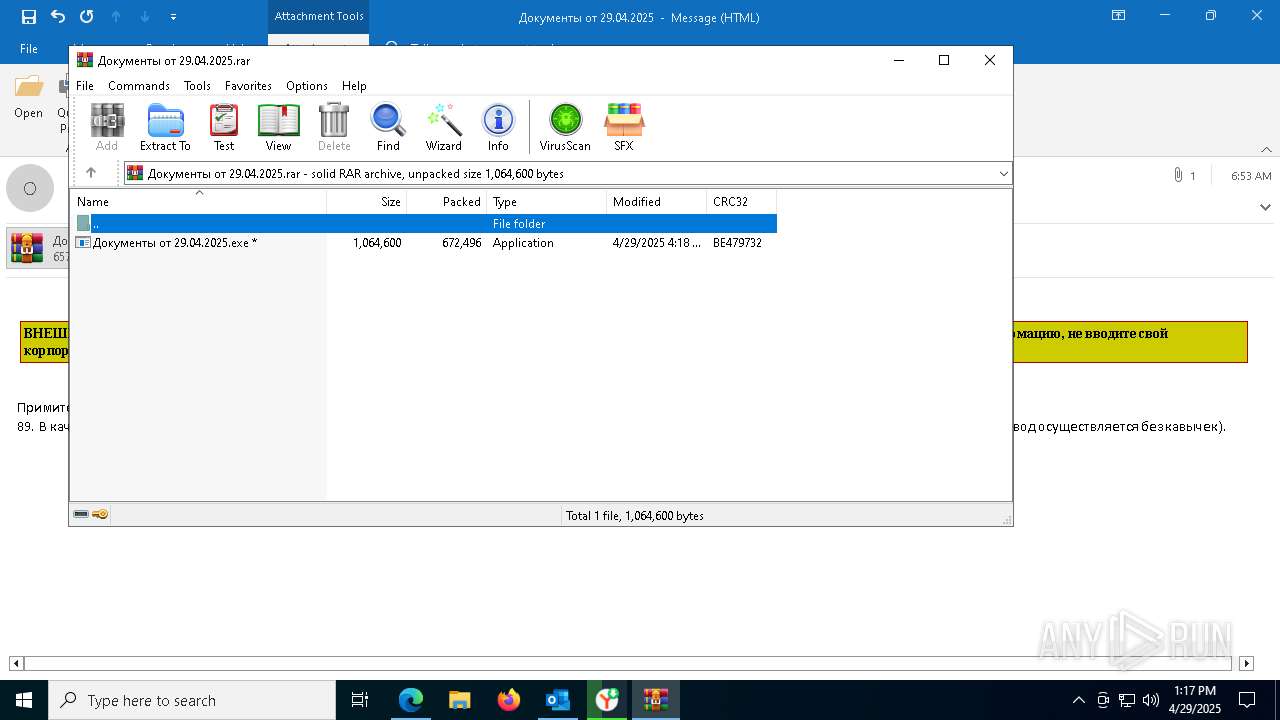
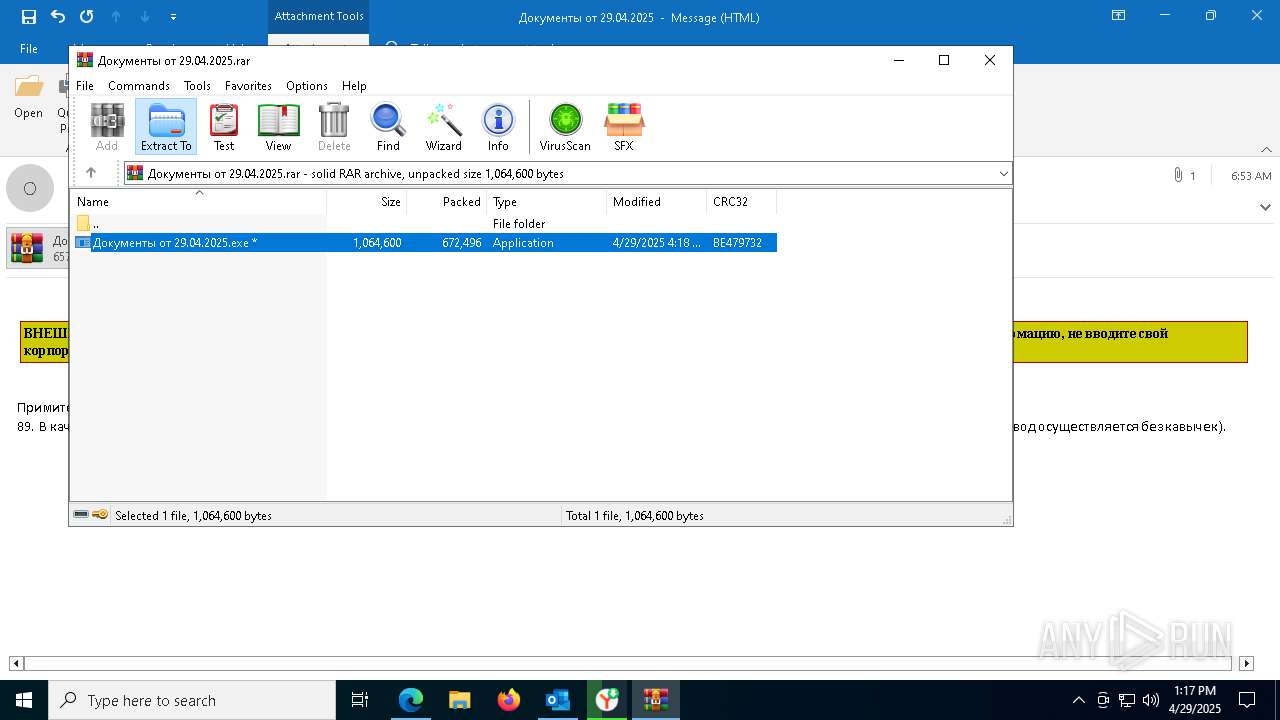
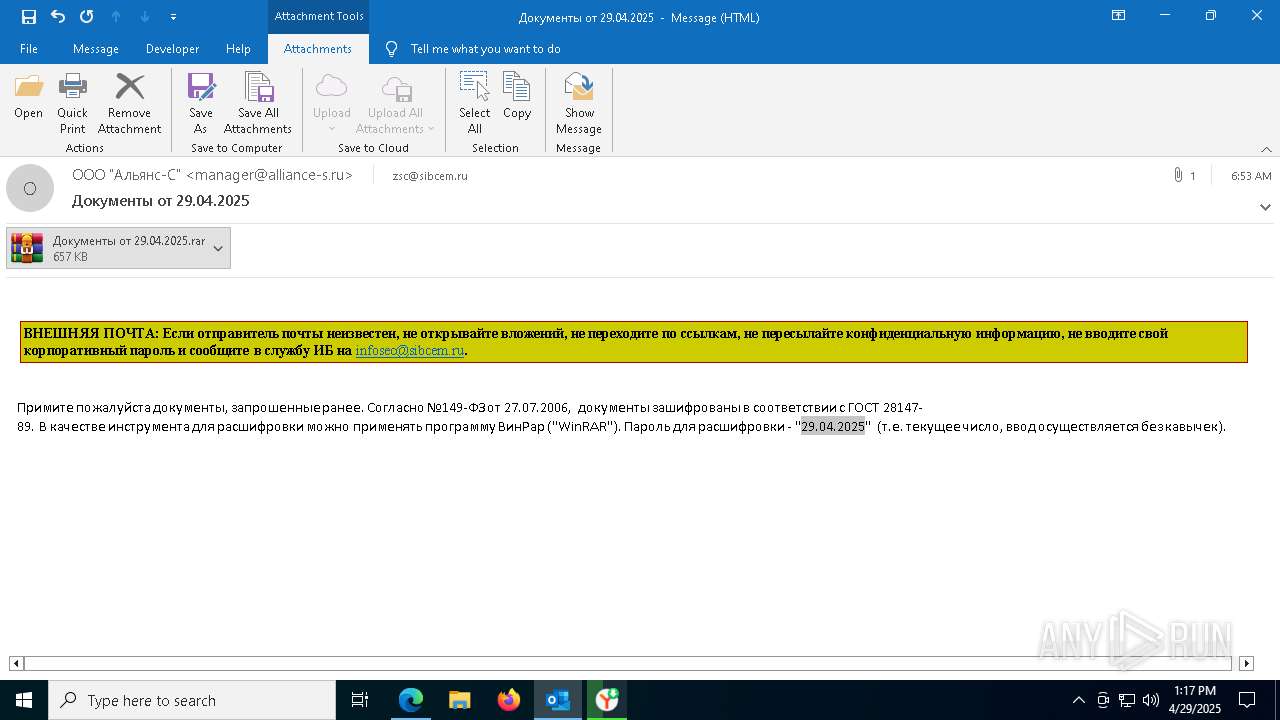
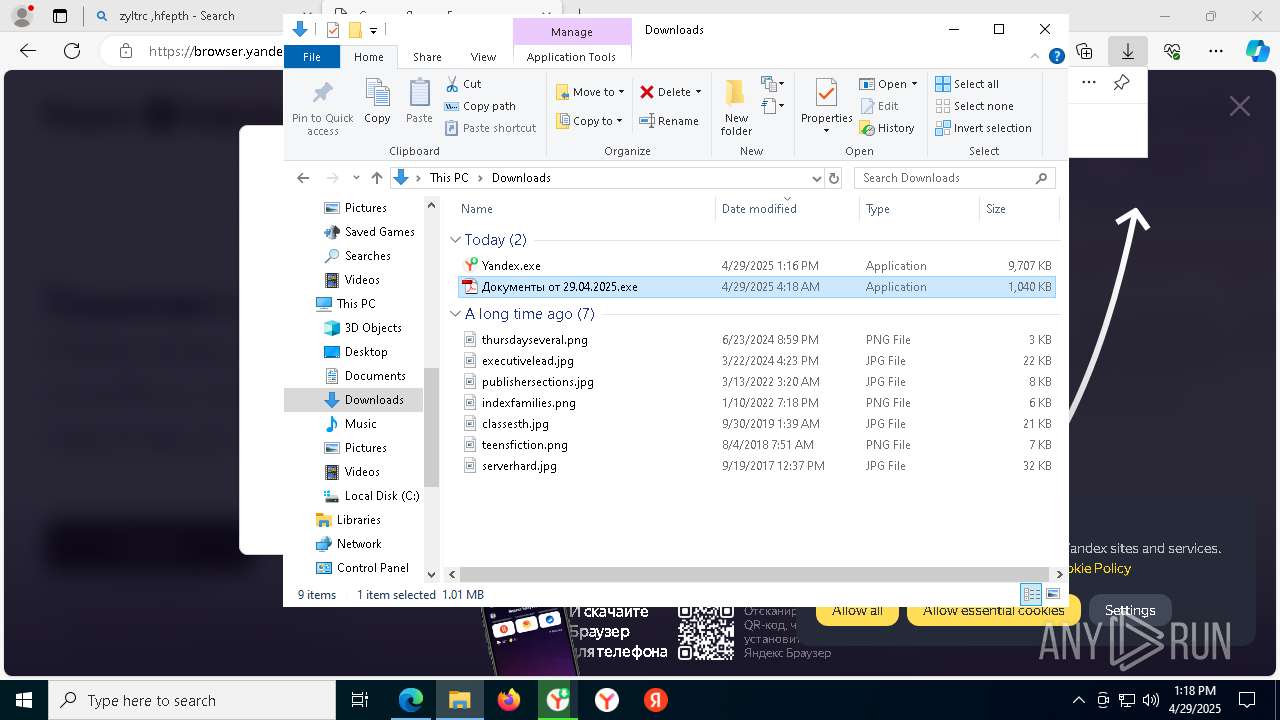
| File name: | backup-message-172.16.20.182_9045-4428092.eml |
| Full analysis: | https://app.any.run/tasks/380fabad-3ac3-451a-bb8d-95191ef59153 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 13:15:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | D2B8970E906BADB2EA83622EE3BBD7C9 |
| SHA1: | 6AF670A3E04EFA53305AC0BC00680516CFF8CA04 |
| SHA256: | 258A0DEC9190630D085C508AE152897BA68E7DCDAAFAACA0649CB8131663447D |
| SSDEEP: | 12288:nPZ3jhPRHIZ9QRs9TnQJtT9fMdSjleE1FqqWZfqDU/WKnmB0s1N8r5CjIoSYIDGN:TRH6EsC5HxNW1CAWKnwIr5CjEDO |
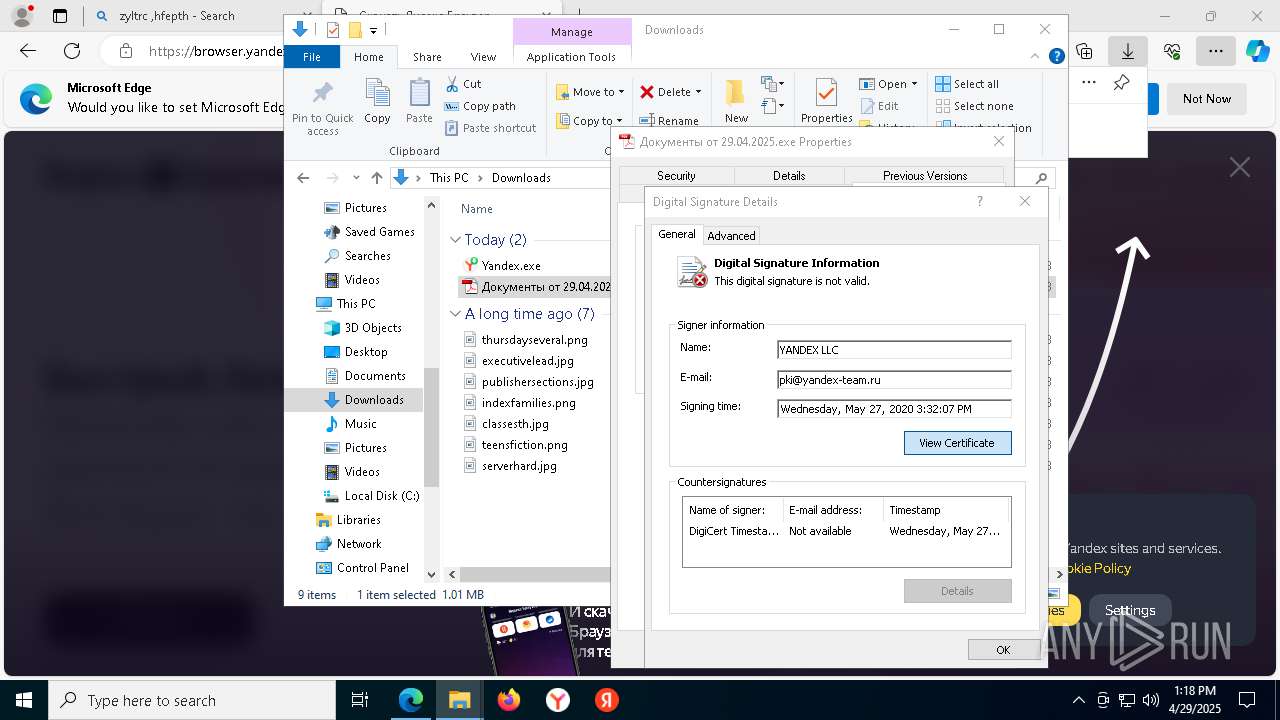
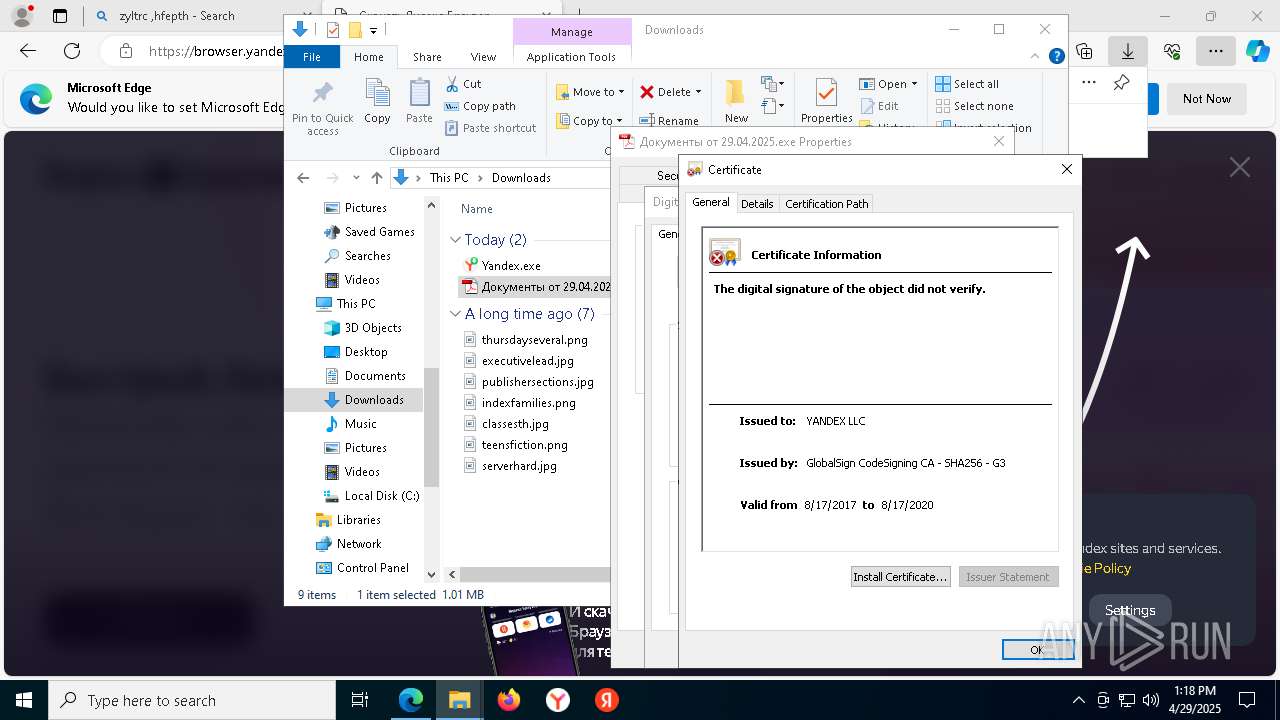
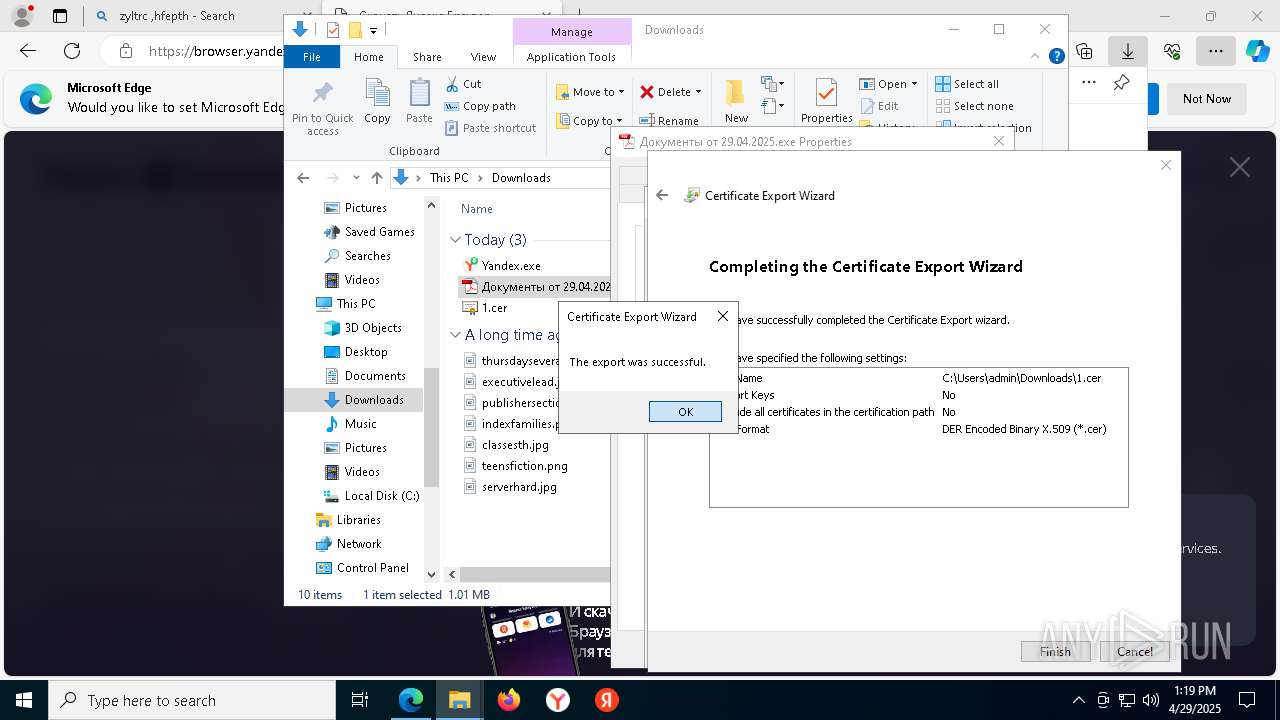
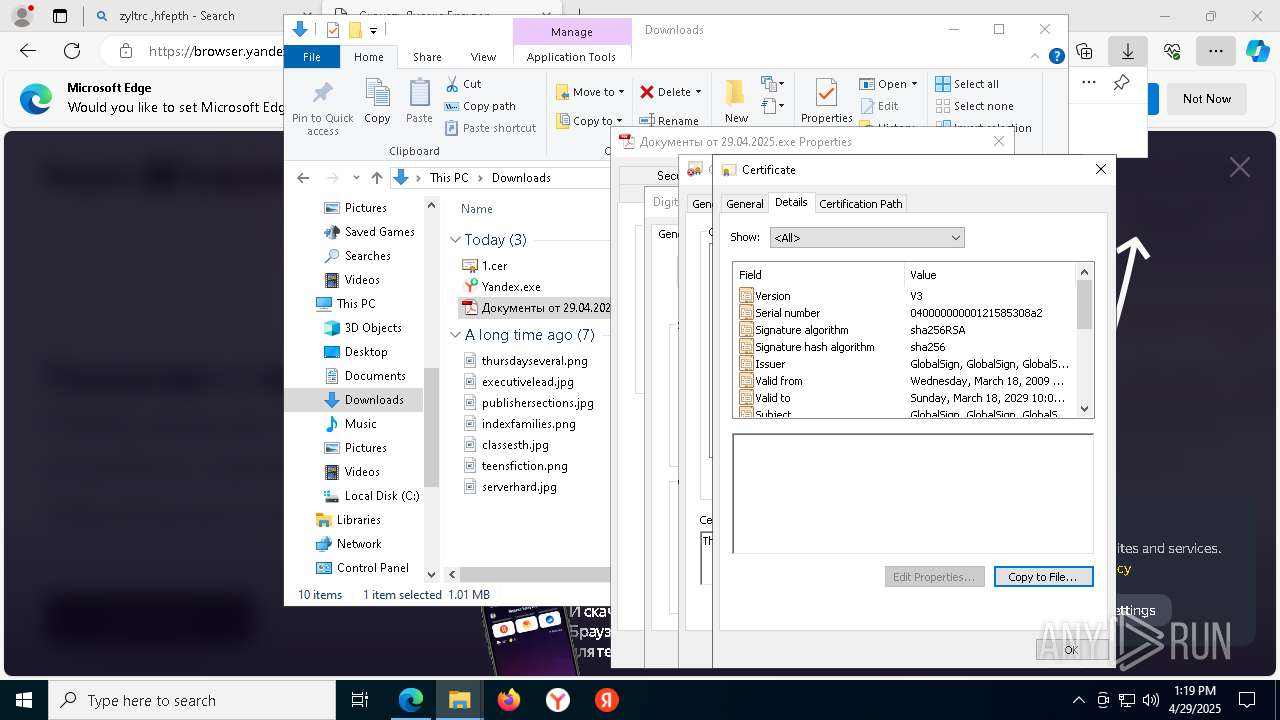
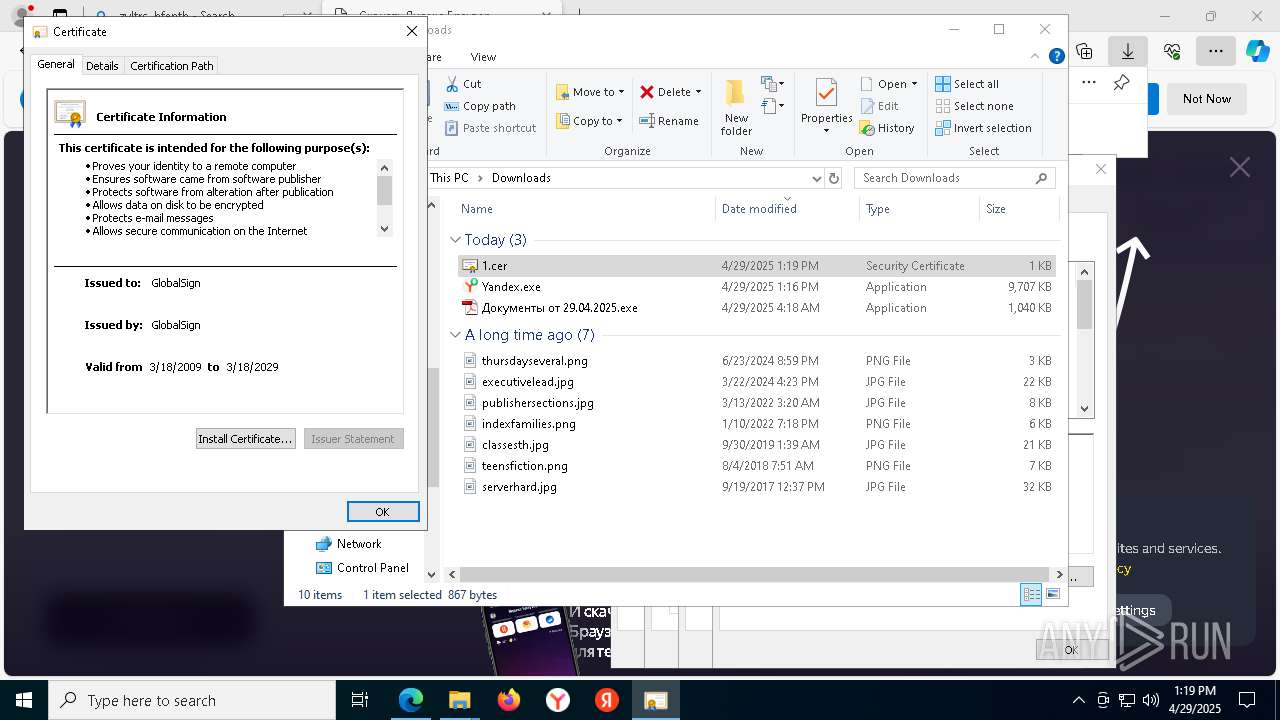
MALICIOUS
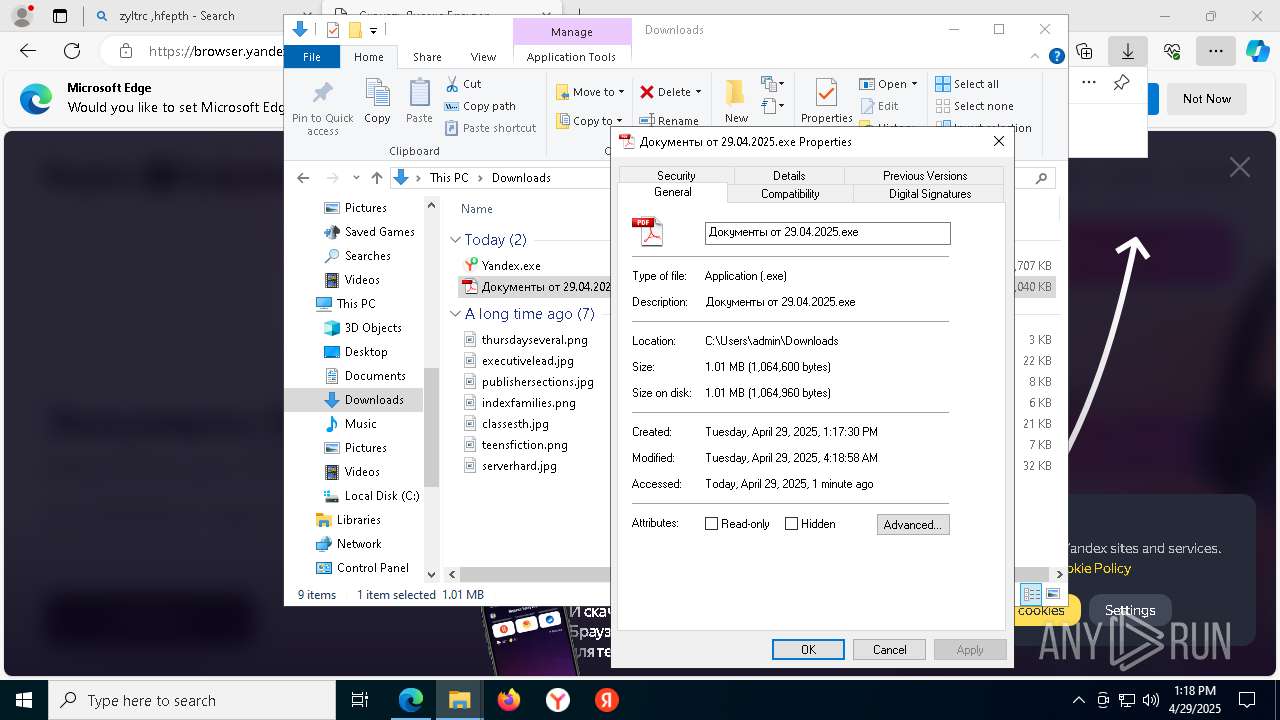
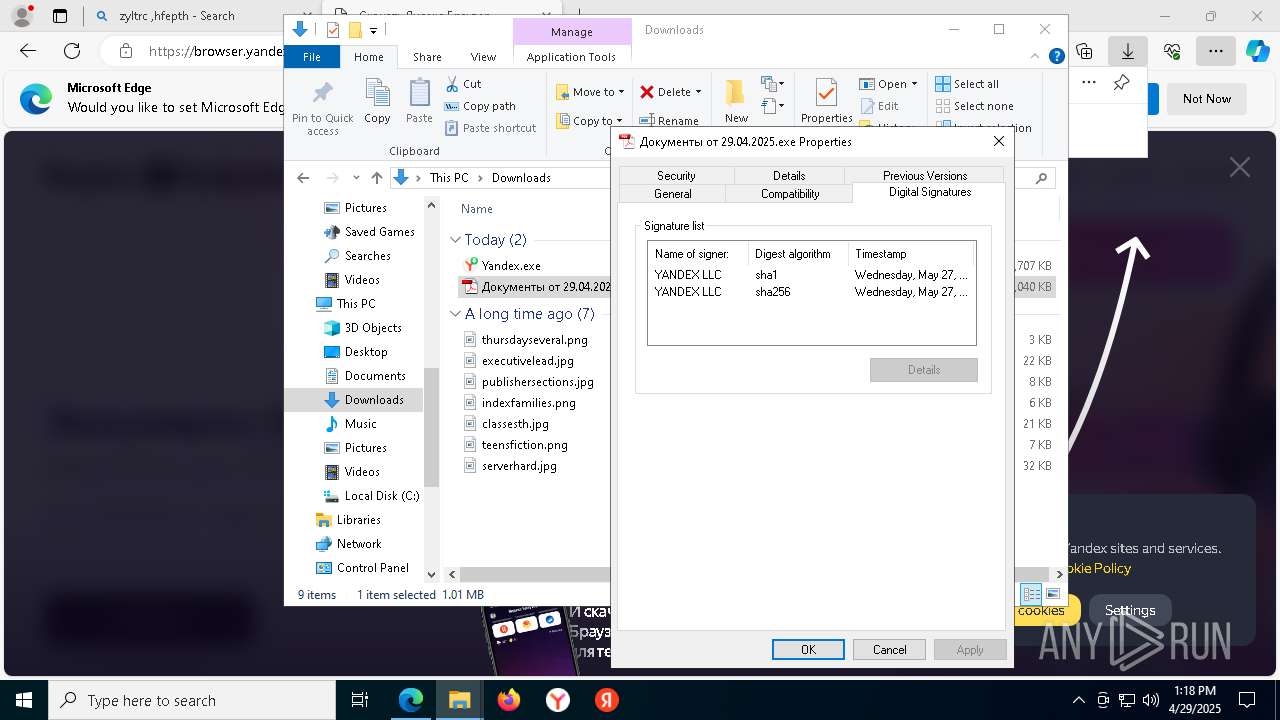
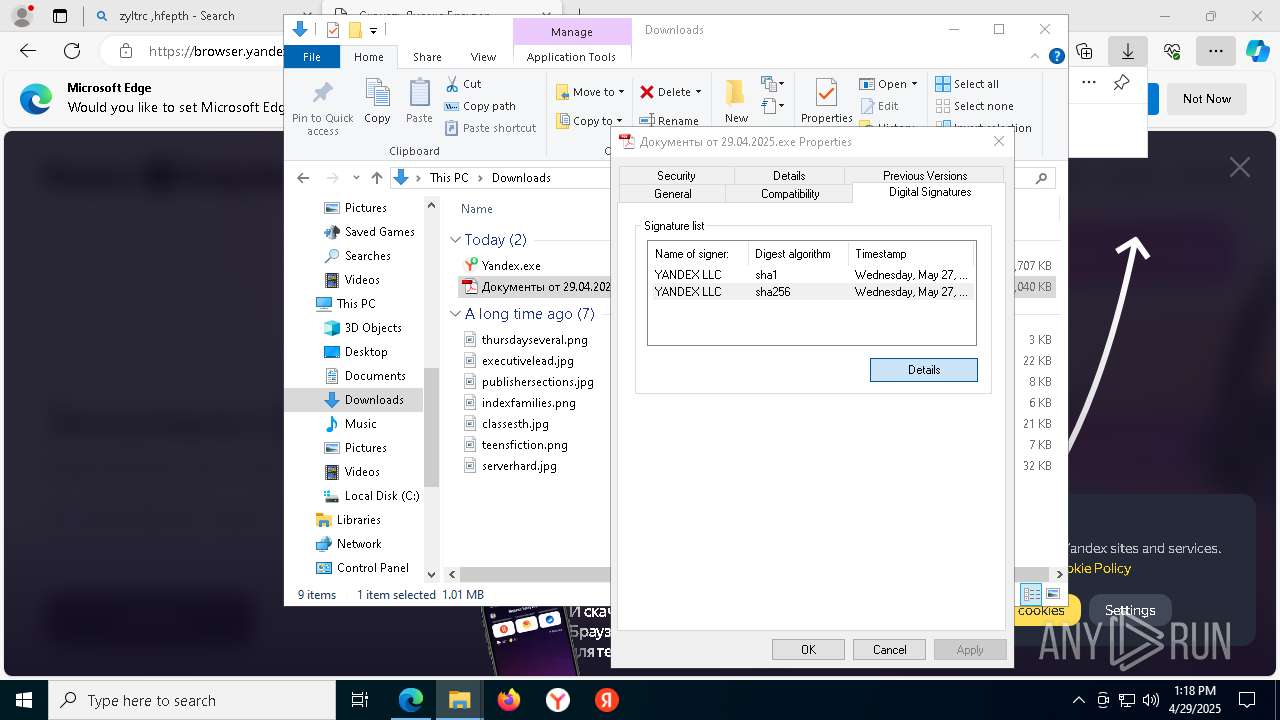
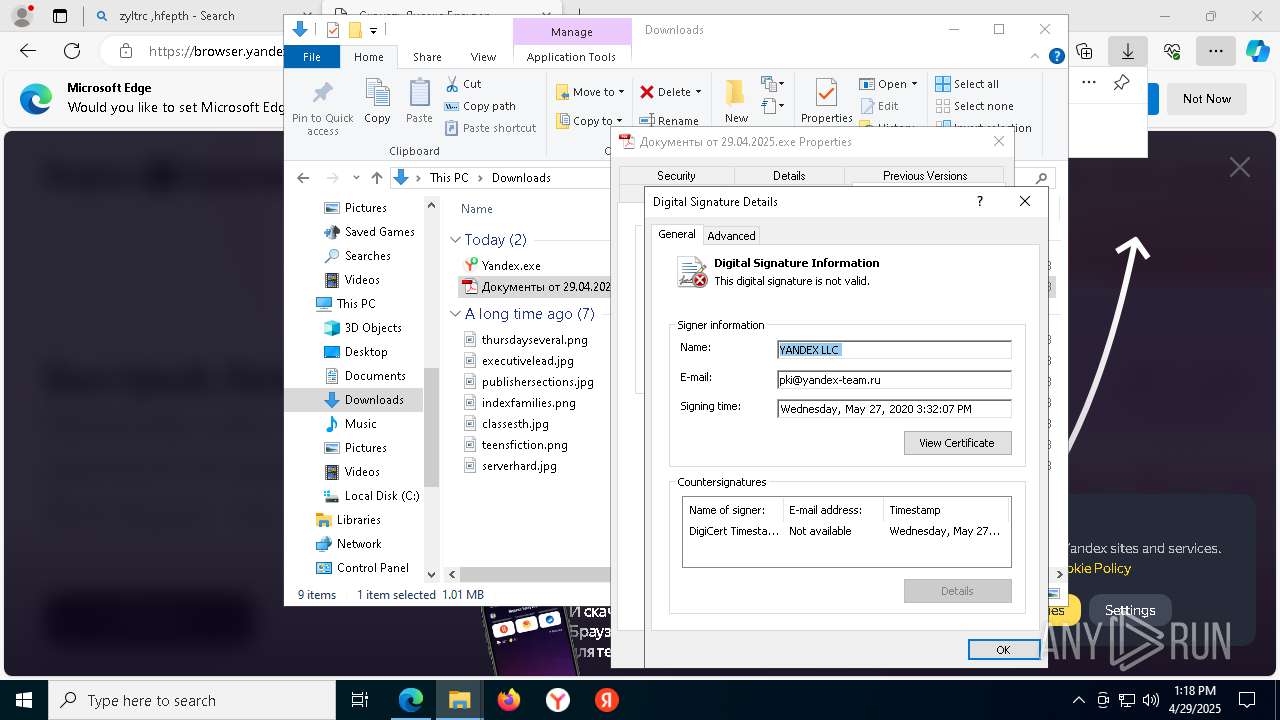
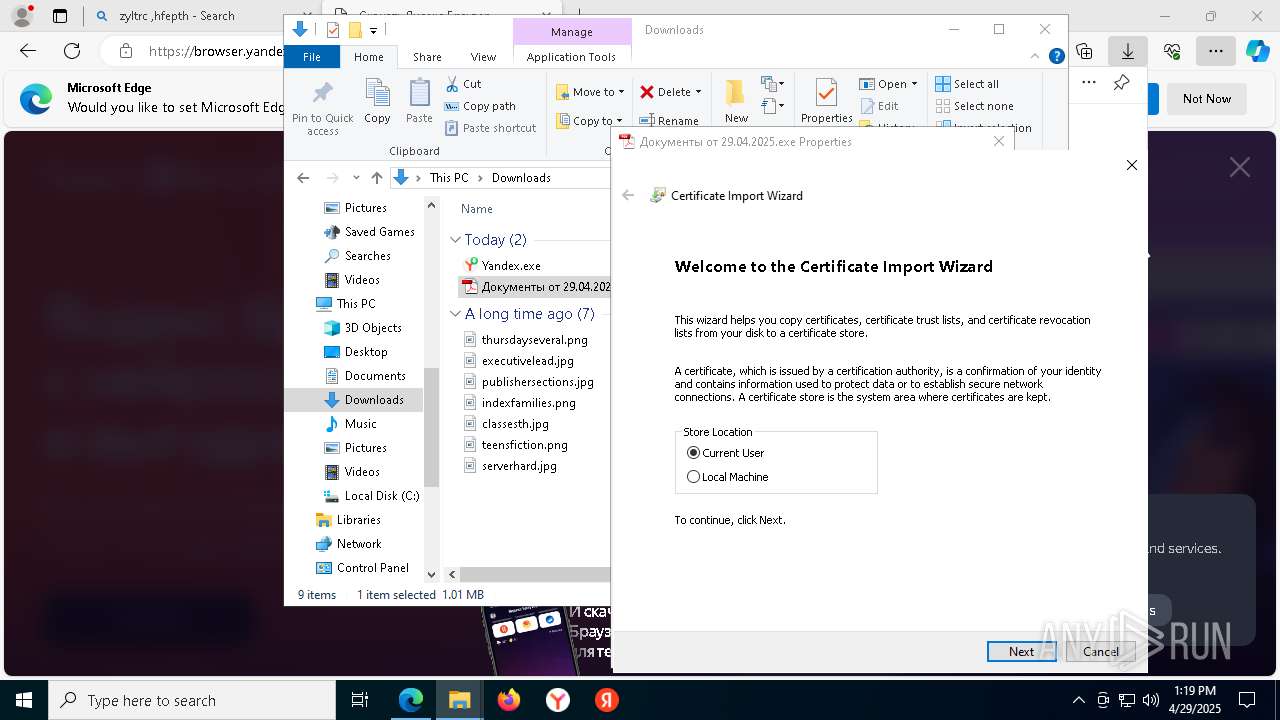
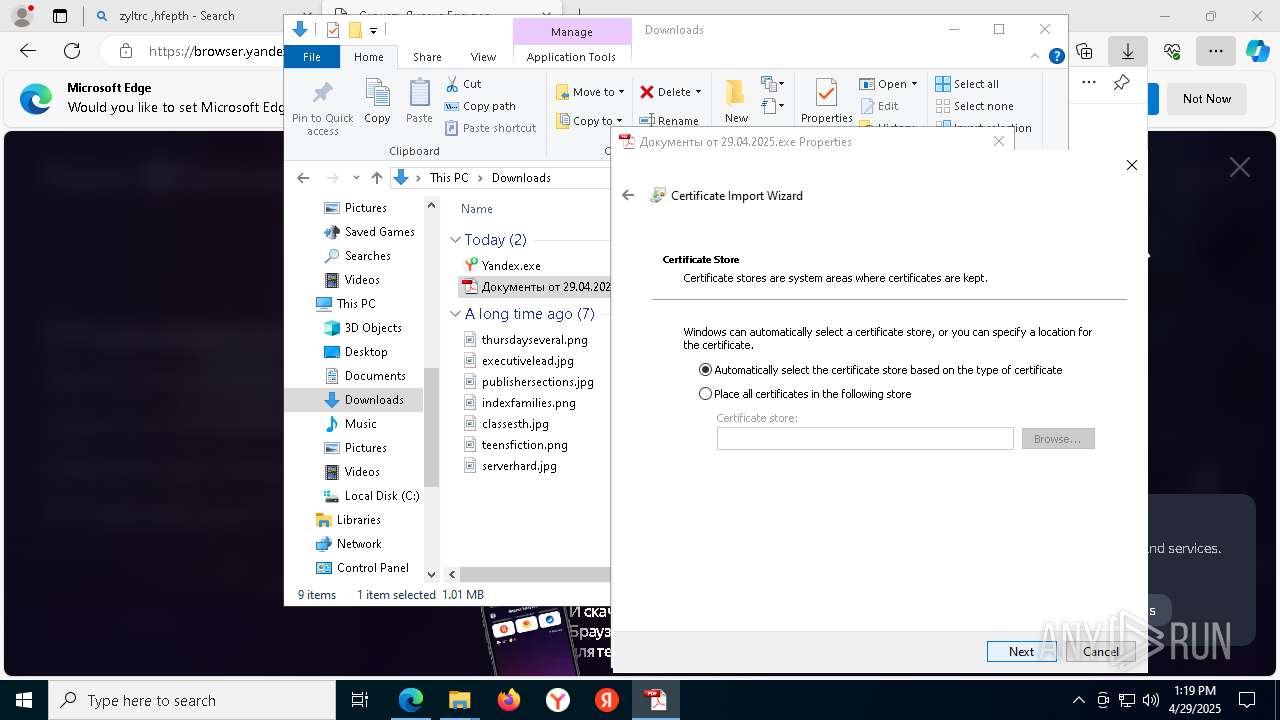
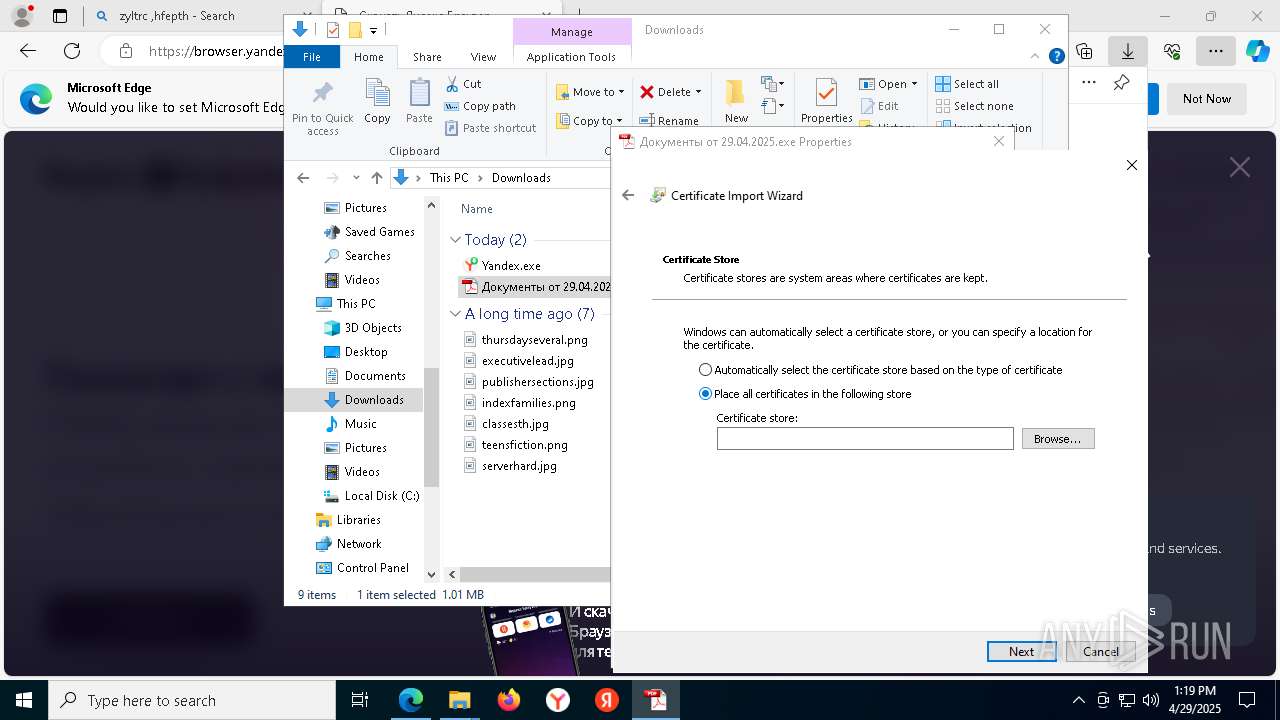
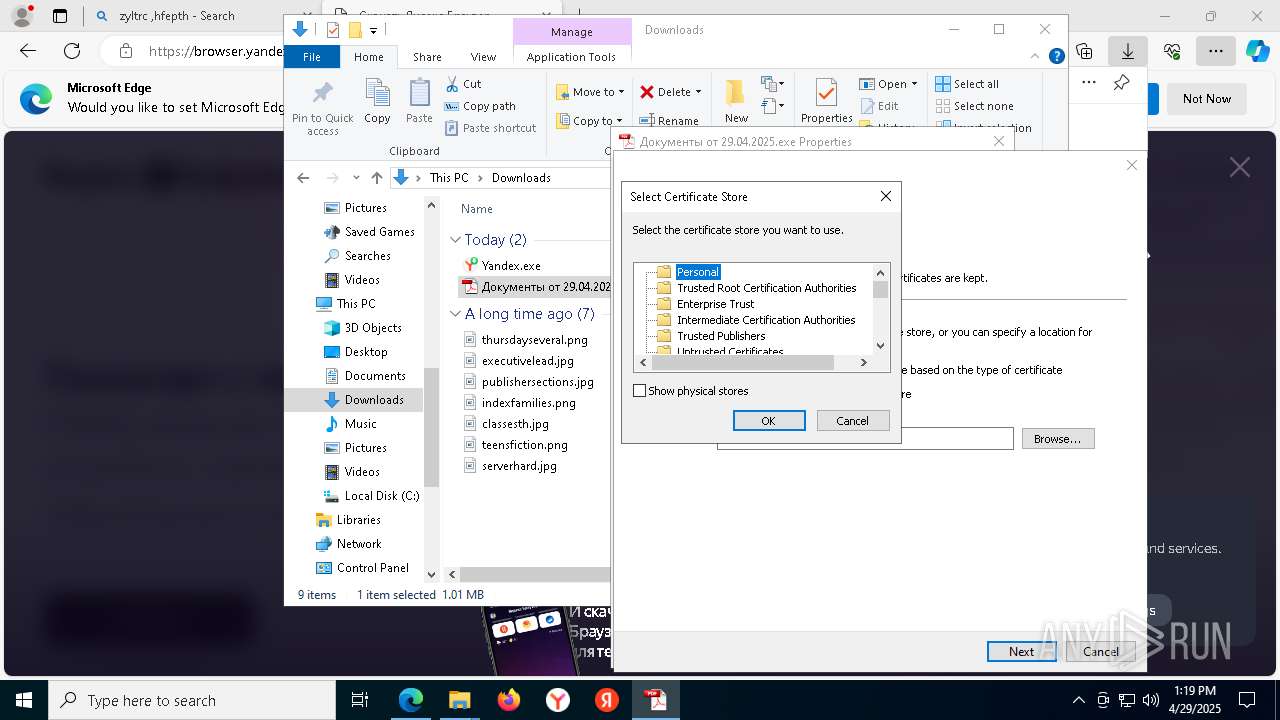
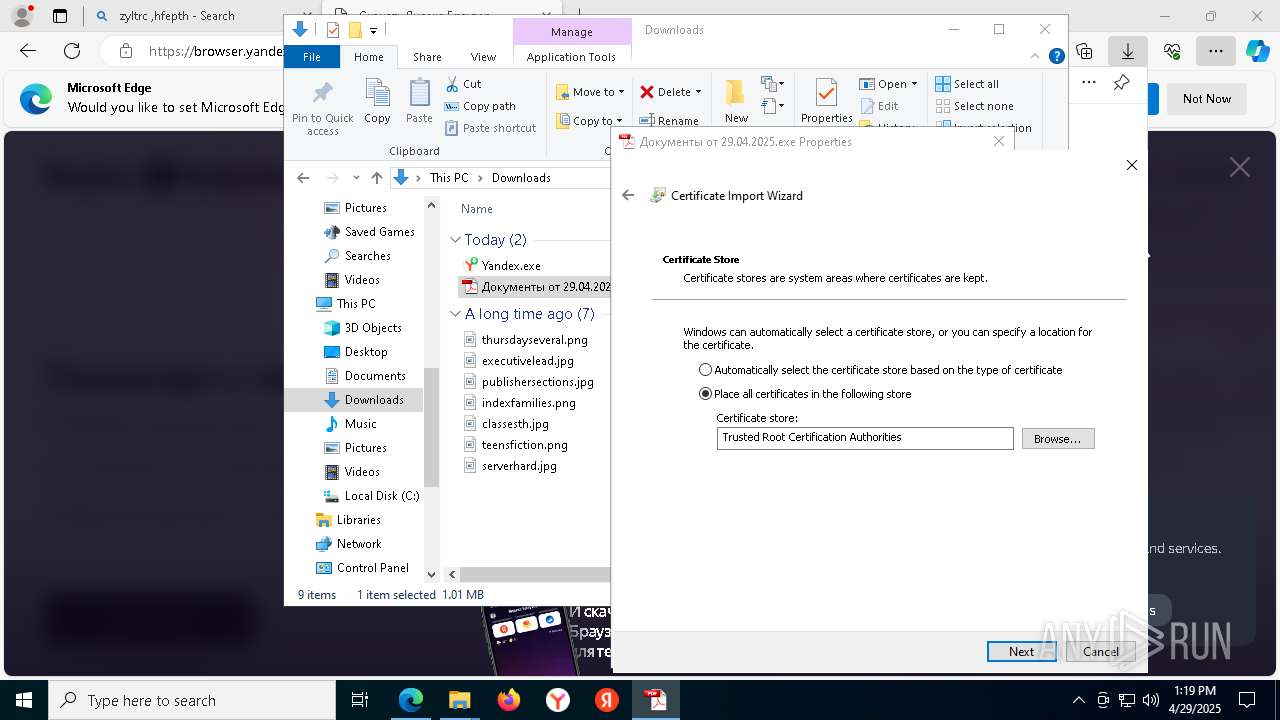
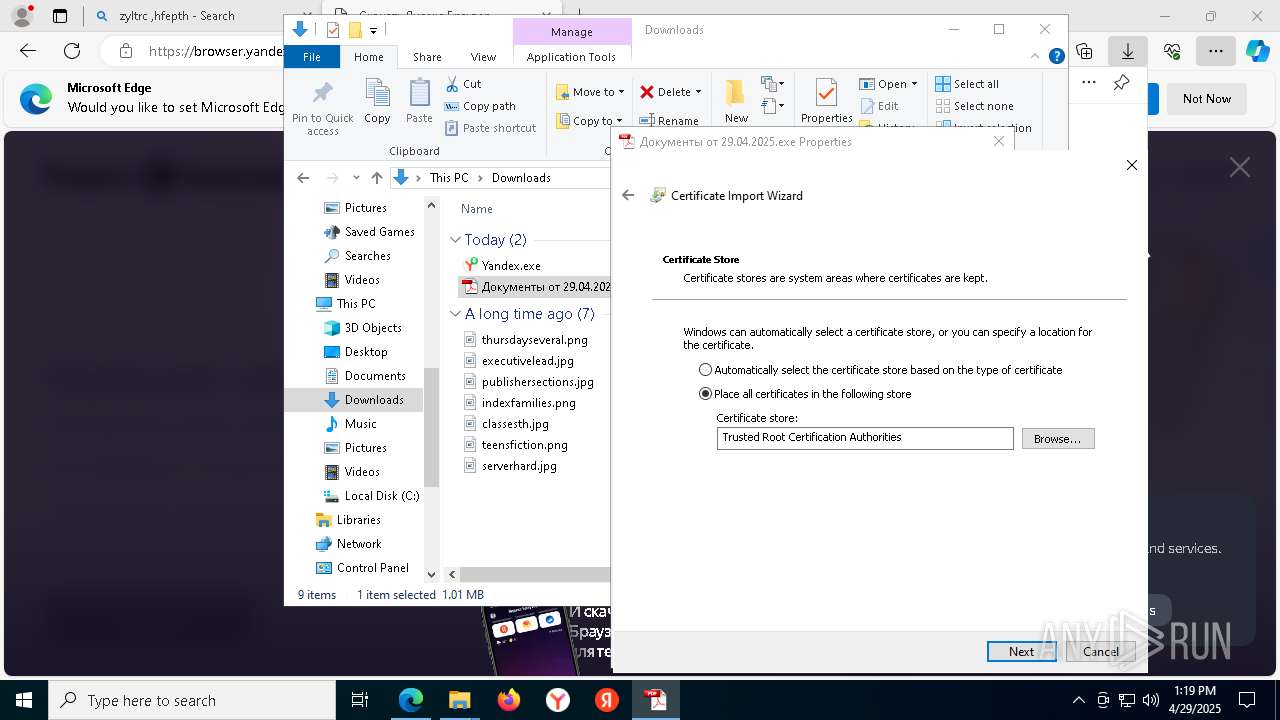
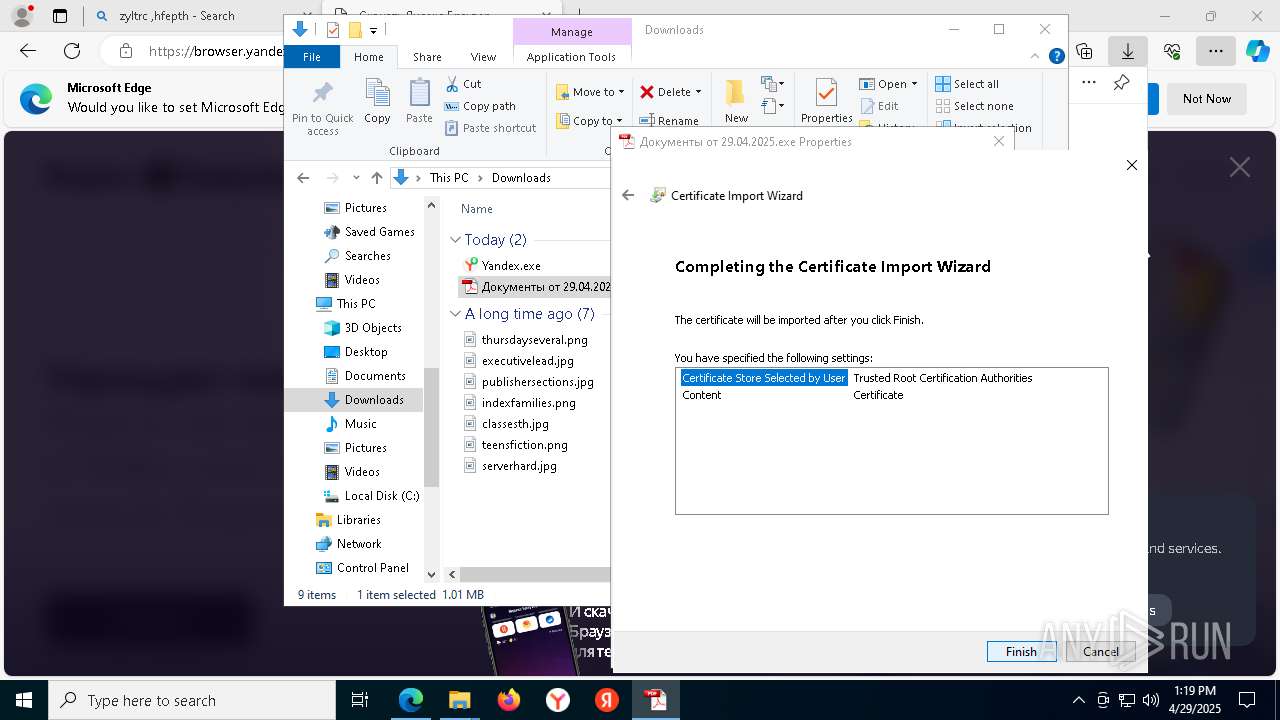
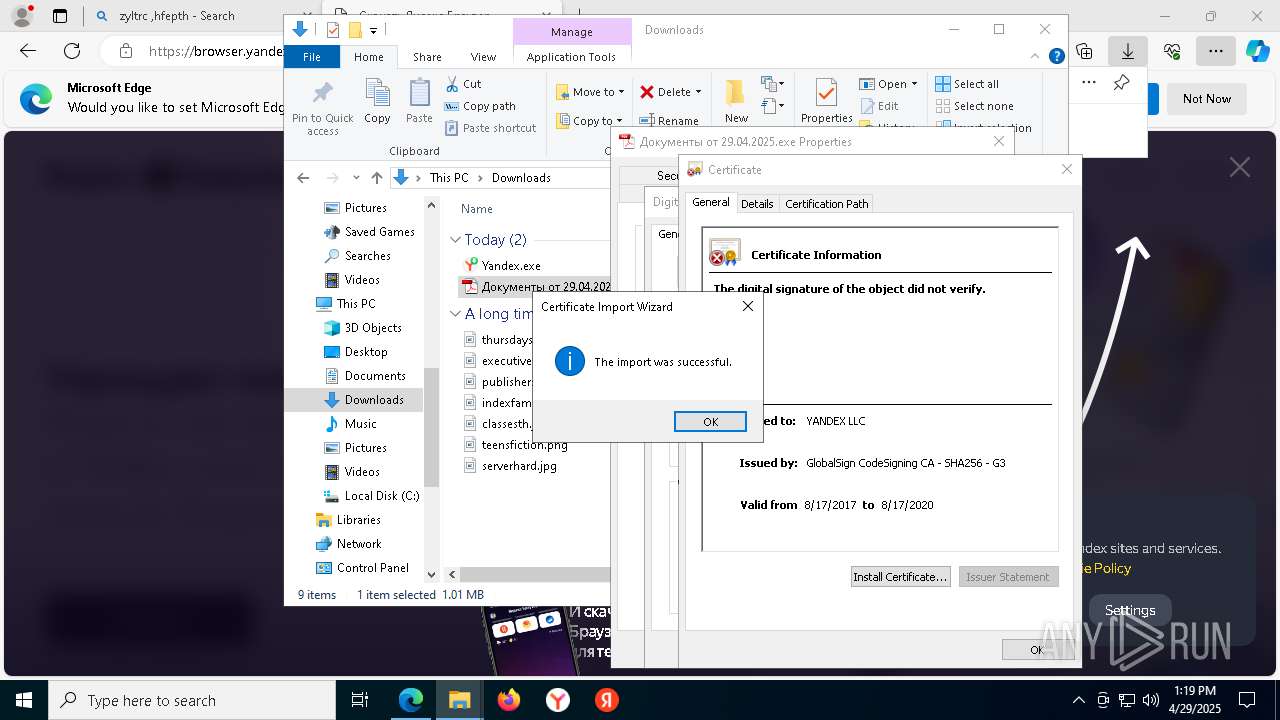
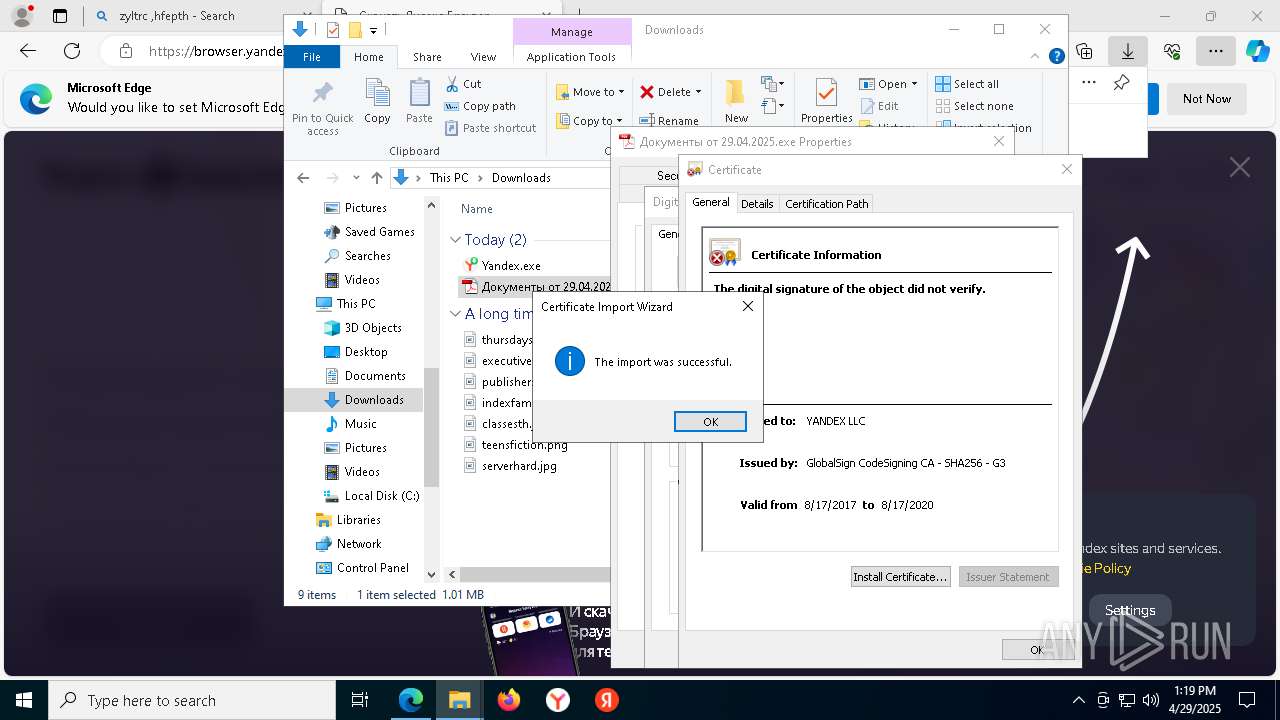
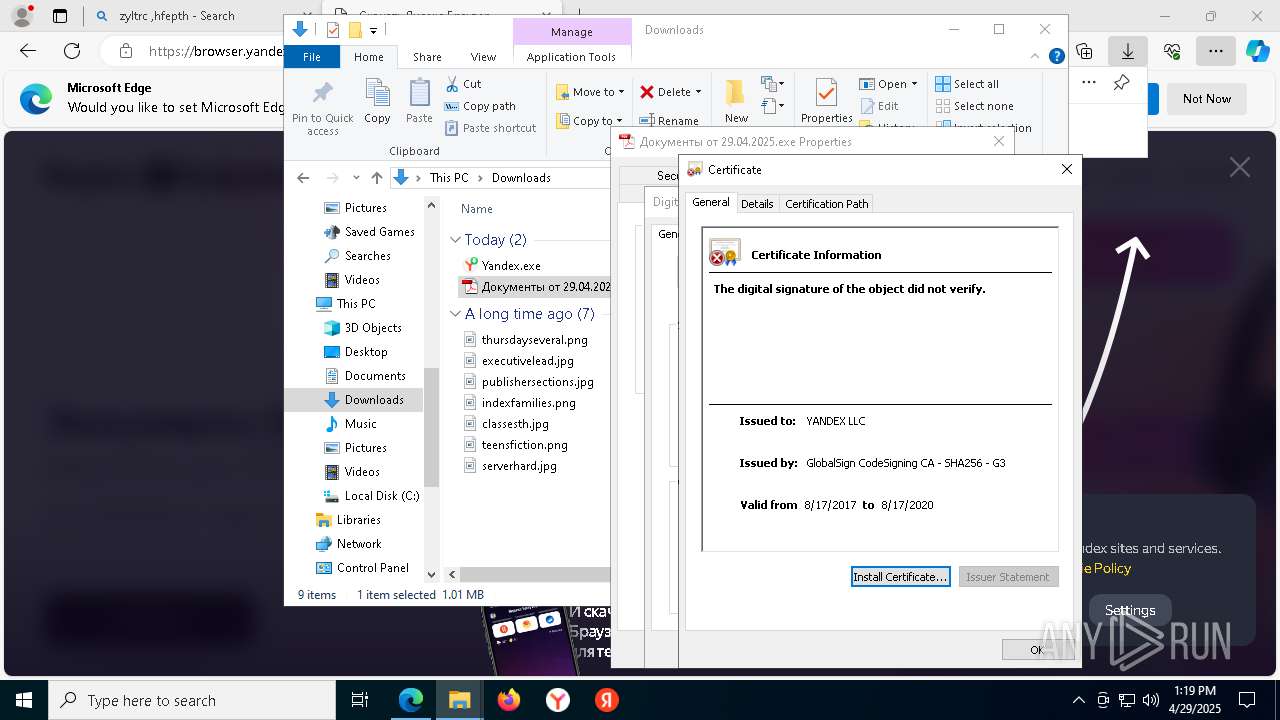
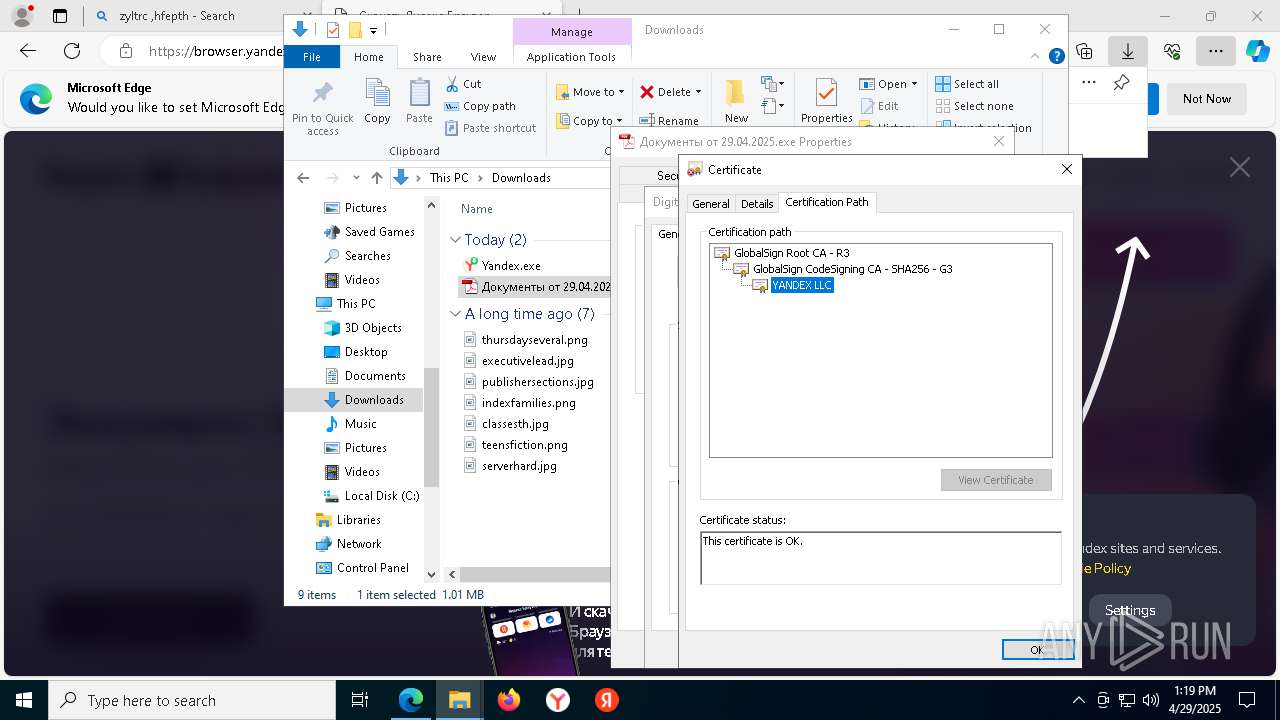
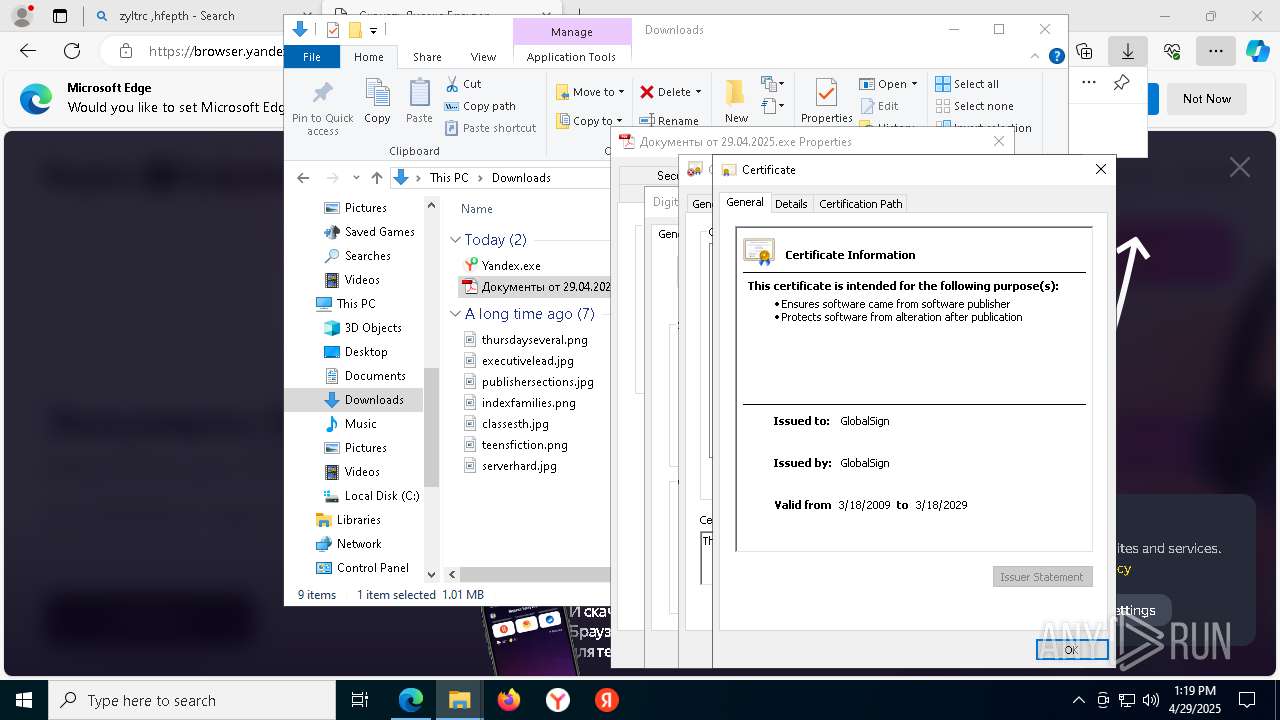
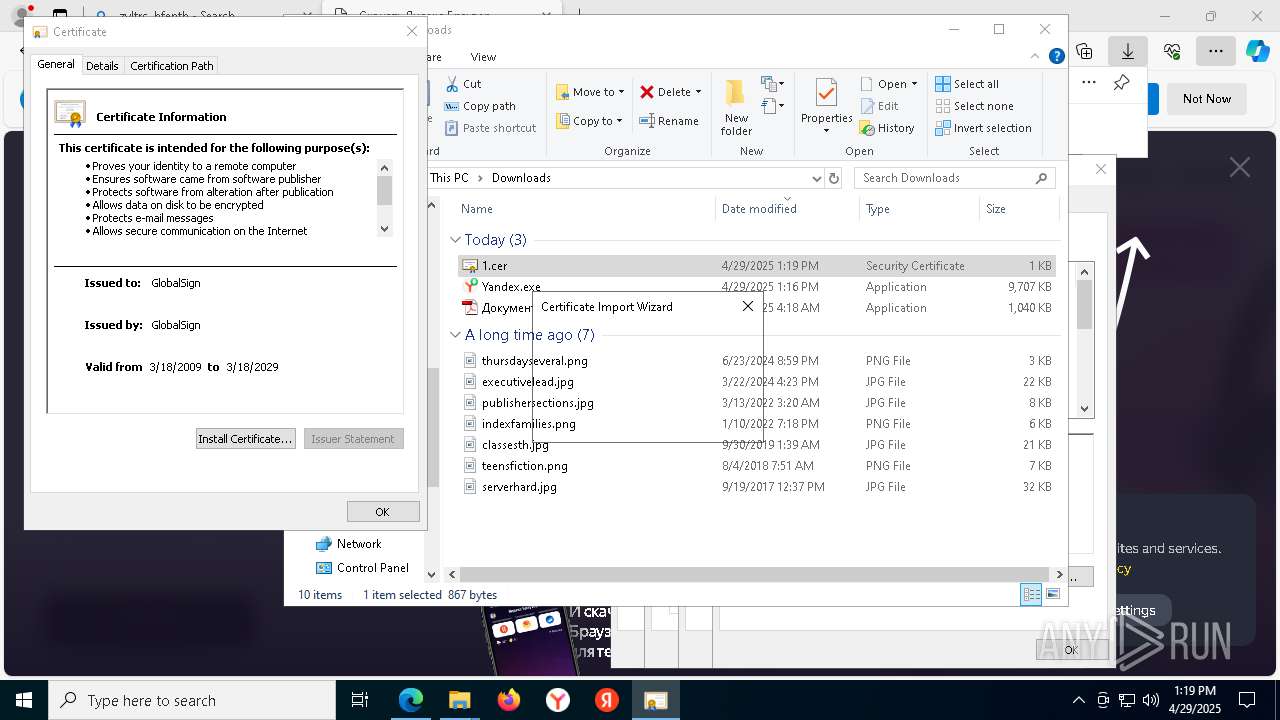
Executing a file with an untrusted certificate
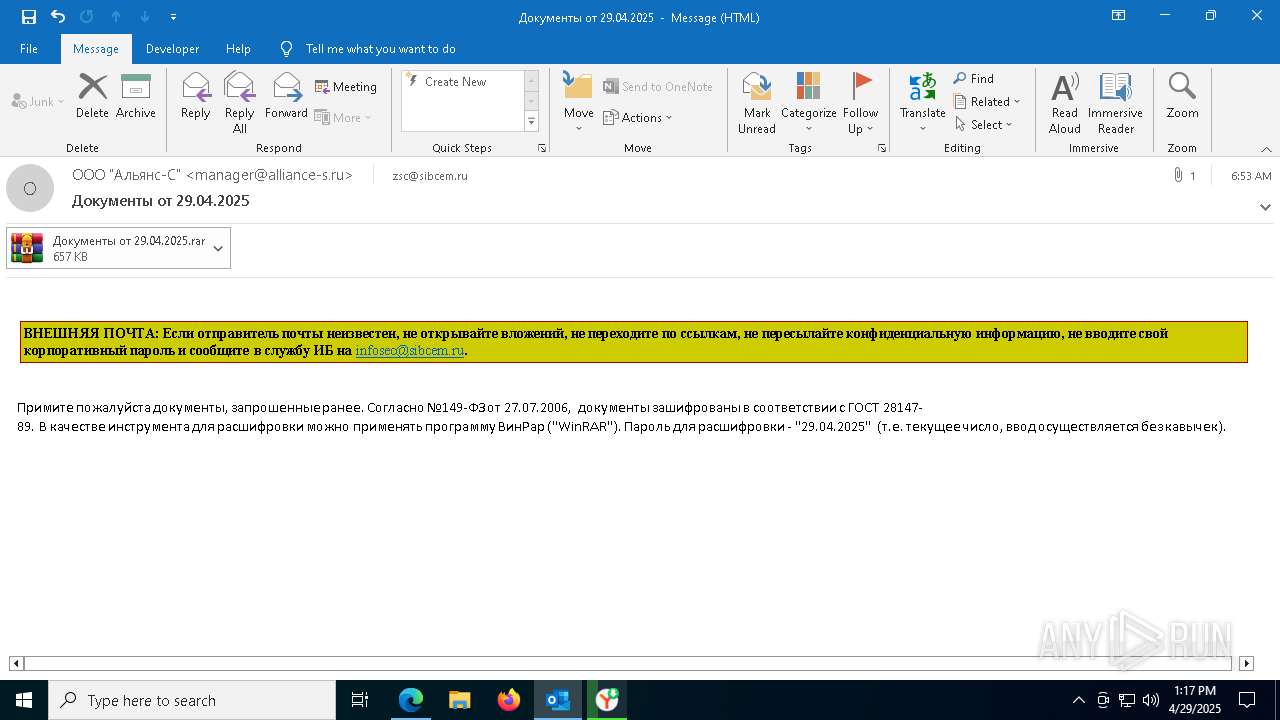
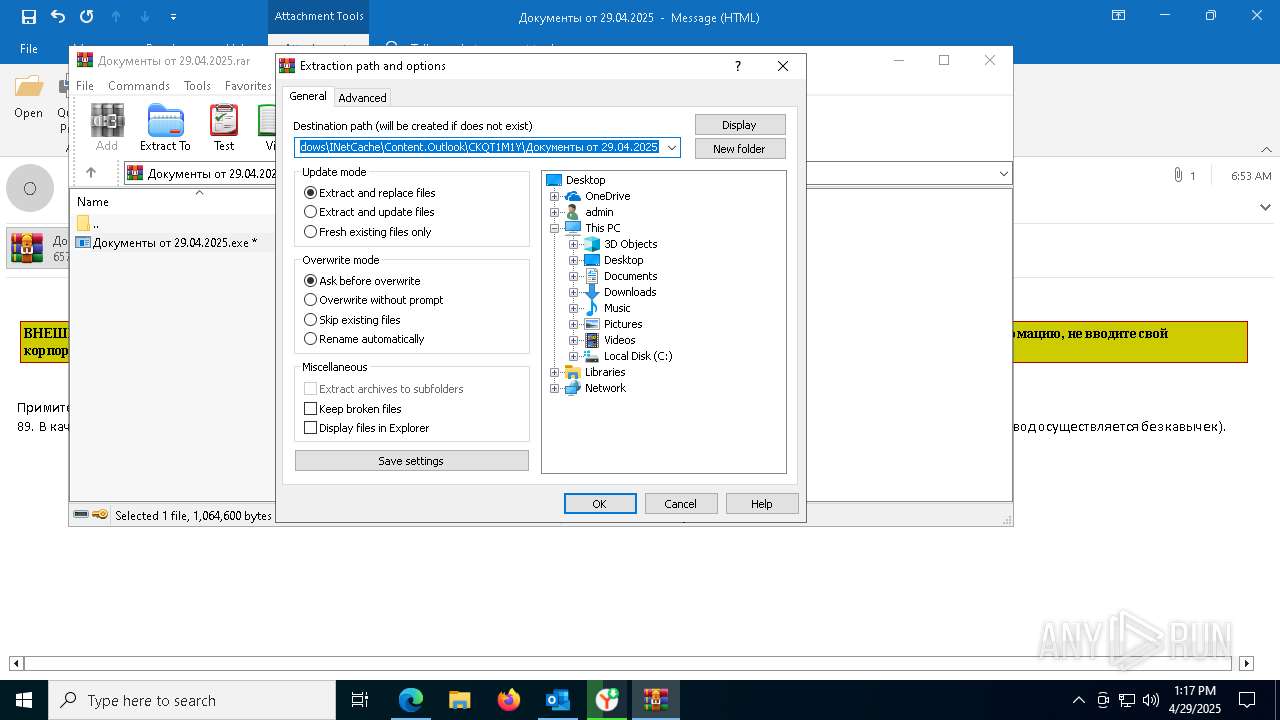
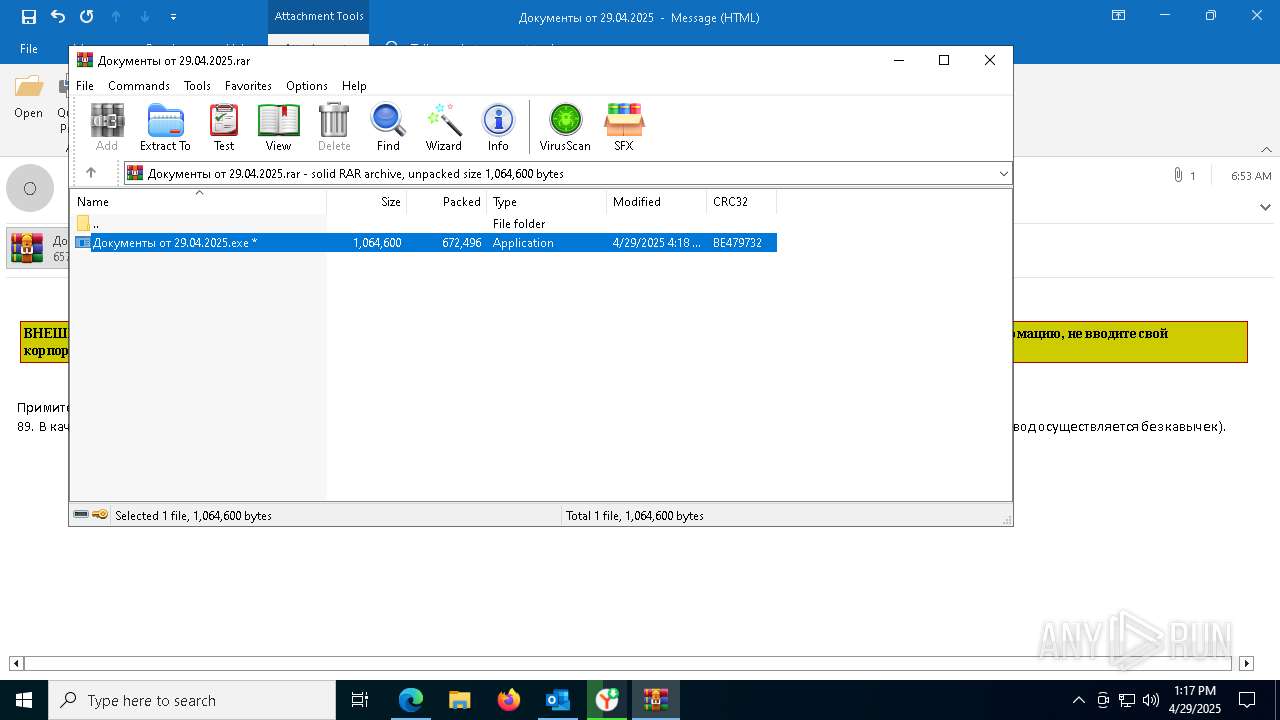
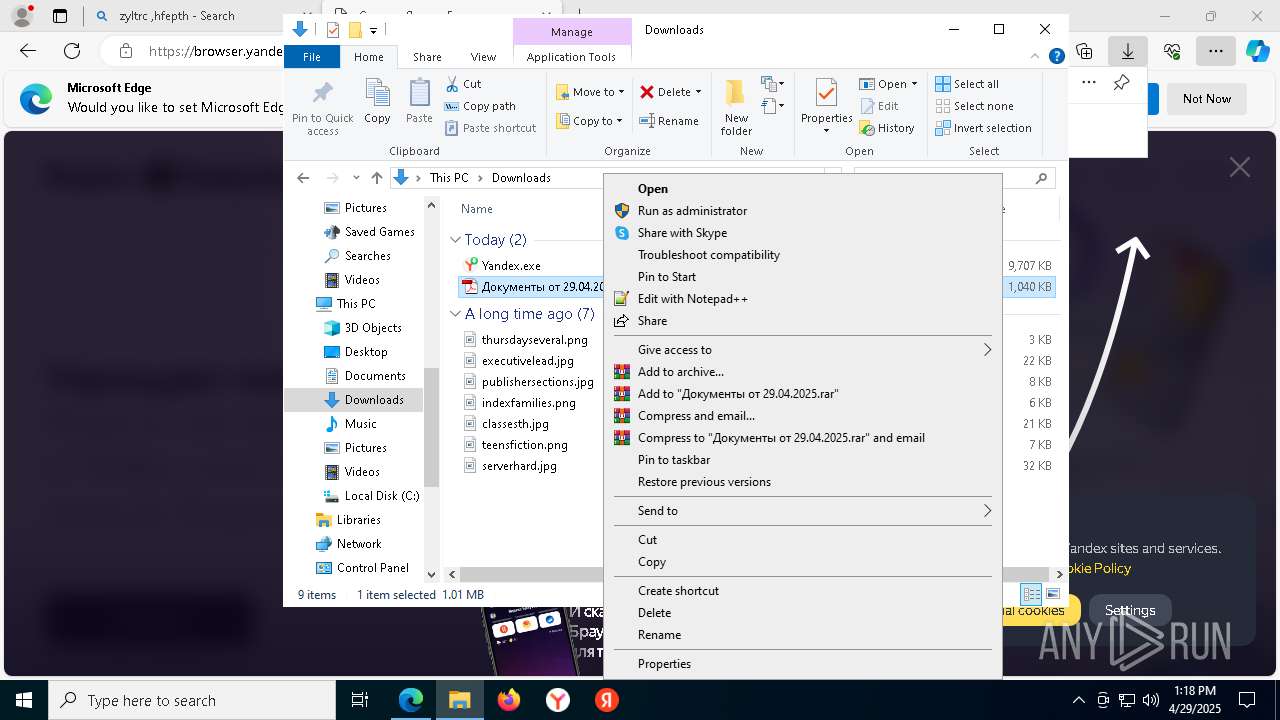
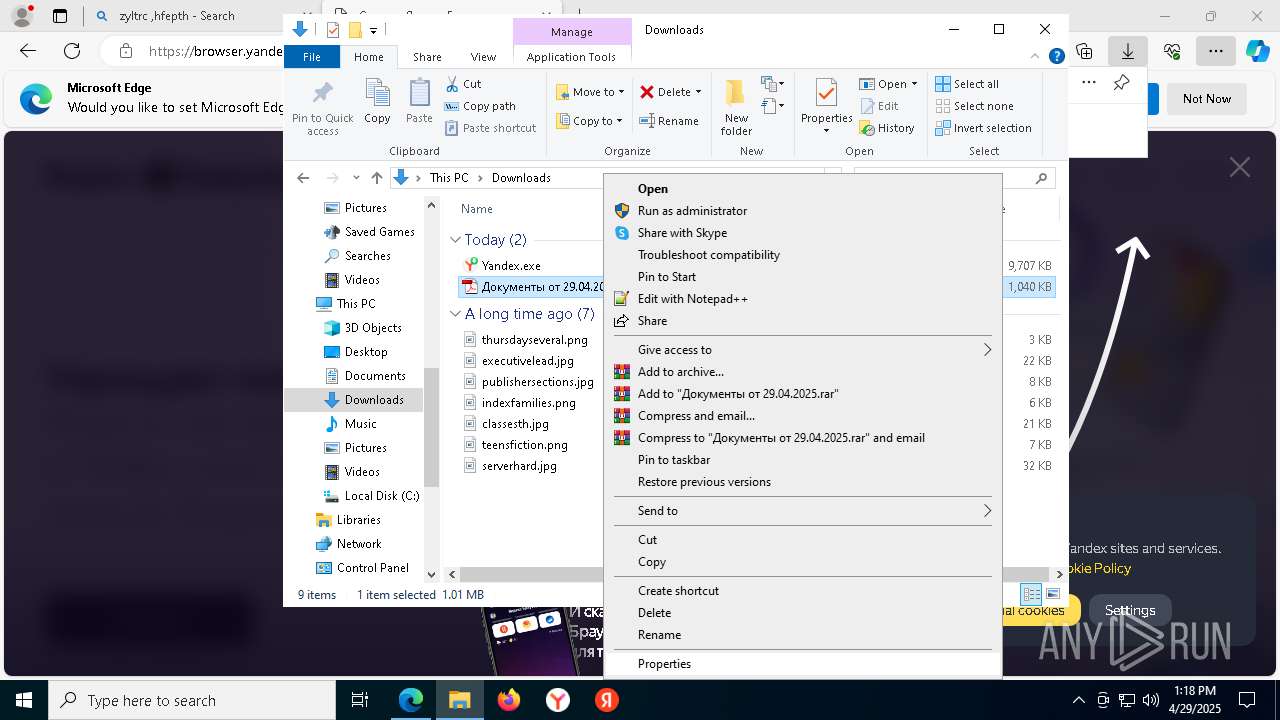
- Документы от 29.04.2025.exe (PID: 8480)
- Документы от 29.04.2025.exe (PID: 6808)
- Документы от 29.04.2025.exe (PID: 8092)
- Документы от 29.04.2025.exe (PID: 8312)
SUSPICIOUS
Reads Microsoft Outlook installation path
- explorer.exe (PID: 5492)
Reads security settings of Internet Explorer
- Yandex.exe (PID: 4108)
Application launched itself
- Yandex.exe (PID: 4108)
- setup.exe (PID: 7608)
- setup.exe (PID: 7672)
- service_update.exe (PID: 8268)
- service_update.exe (PID: 8336)
- browser.exe (PID: 8132)
- setup.exe (PID: 7724)
- rundll32.exe (PID: 5164)
- explorer.exe (PID: 8552)
Executable content was dropped or overwritten
- ybD5CB.tmp (PID: 8028)
- setup.exe (PID: 7672)
- service_update.exe (PID: 7288)
- Yandex.exe (PID: 6824)
Starts application with an unusual extension
- Yandex.exe (PID: 8308)
Starts itself from another location
- service_update.exe (PID: 7288)
- setup.exe (PID: 7672)
- Yandex.exe (PID: 6824)
Executes as Windows Service
- service_update.exe (PID: 8268)
Executes application which crashes
- Документы от 29.04.2025.exe (PID: 8480)
- Документы от 29.04.2025.exe (PID: 8312)
- Документы от 29.04.2025.exe (PID: 6808)
- Документы от 29.04.2025.exe (PID: 8092)
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 5492)
- rundll32.exe (PID: 5164)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
Checks supported languages
- identity_helper.exe (PID: 5756)
- Yandex.exe (PID: 8308)
- Yandex.exe (PID: 4108)
Manual execution by a user
- msedge.exe (PID: 5156)
- Документы от 29.04.2025.exe (PID: 8480)
- Документы от 29.04.2025.exe (PID: 6808)
- browser.exe (PID: 8132)
Application launched itself
- msedge.exe (PID: 5156)
Reads the computer name
- identity_helper.exe (PID: 5756)
- Yandex.exe (PID: 4108)
Reads Environment values
- identity_helper.exe (PID: 5756)
Executable content was dropped or overwritten
- msedge.exe (PID: 5156)
- msedge.exe (PID: 7192)
- WinRAR.exe (PID: 8080)
The sample compiled with english language support
- msedge.exe (PID: 5156)
- ybD5CB.tmp (PID: 8028)
- service_update.exe (PID: 7288)
- setup.exe (PID: 7672)
- msedge.exe (PID: 7192)
Creates files or folders in the user directory
- Yandex.exe (PID: 4108)
Checks proxy server information
- Yandex.exe (PID: 4108)
Process checks computer location settings
- Yandex.exe (PID: 4108)
Reads the software policy settings
- Yandex.exe (PID: 4108)
- slui.exe (PID: 7180)
Reads the machine GUID from the registry
- Yandex.exe (PID: 4108)
Yandex updater related mutex has been found
- Yandex.exe (PID: 8308)
- Yandex.exe (PID: 4108)
The sample compiled with russian language support
- setup.exe (PID: 7672)
Create files in a temporary directory
- Yandex.exe (PID: 4108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
292
Monitored processes
144
Malicious processes
2
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | C:\Users\admin\AppData\Local\Yandex\YandexBrowser\Application\browser.exe --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Yandex\YandexBrowser\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Yandex\YandexBrowser\User Data\Crashpad" --url=https://crash-reports.browser.yandex.net/submit --annotation=machine_id= --annotation=main_process_pid=8132 --annotation=metrics_client_id=08a516fc66984dbaadae65fb5518d8d9 --annotation=plat=Win64 --annotation=prod=Yandex --annotation=session_logout=False --annotation=ver=25.4.0.1973 --initial-client-data=0x178,0x17c,0x180,0x154,0x184,0x7ffc8898ac80,0x7ffc8898ac8c,0x7ffc8898ac98 | C:\Users\admin\AppData\Local\Yandex\YandexBrowser\Application\browser.exe | — | browser.exe | |||||||||||
User: admin Company: YANDEX LLC Integrity Level: MEDIUM Description: Yandex with voice assistant Alice Exit code: 0 Version: 25.4.0.1973 Modules
| |||||||||||||||
| 900 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6828 --field-trial-handle=1960,i,11592115911513733292,2520099887901033997,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1128 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=6928 --field-trial-handle=1960,i,11592115911513733292,2520099887901033997,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1228 | "C:\Users\admin\AppData\Local\Yandex\YandexBrowser\Application\browser.exe" --type=utility --utility-sub-type=chrome.mojom.ProfileImport --lang=ru --service-sandbox-type=none --user-id=CB098099-0354-49FC-8243-616EE618864E --brand-id=yandex --process-name="Импорт профилей" --field-trial-handle=2388,i,13912928581664227597,18324006323817689710,262144 --variations-seed-version --mojo-platform-channel-handle=4576 --brver=25.4.0.1973 /prefetch:8 | C:\Users\admin\AppData\Local\Yandex\YandexBrowser\Application\browser.exe | — | browser.exe | |||||||||||
User: admin Company: YANDEX LLC Integrity Level: MEDIUM Description: Yandex with voice assistant Alice Exit code: 0 Version: 25.4.0.1973 Modules
| |||||||||||||||
| 1228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | regini.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1300 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6764 --field-trial-handle=1960,i,11592115911513733292,2520099887901033997,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1764 | "C:\Users\admin\AppData\Local\Yandex\YandexBrowser\Application\clidmgr.exe" --appid=yabrowser --vendor-xml-path="C:\Users\admin\AppData\Local\Temp\clids.xml" | C:\Users\admin\AppData\Local\Yandex\YandexBrowser\Application\clidmgr.exe | — | setup.exe | |||||||||||
User: admin Company: Yandex Integrity Level: HIGH Description: ClidManagerModule Exit code: 0 Version: 1,0,0,44 Modules
| |||||||||||||||
| 1764 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | regini.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | regini.exe "C:\Users\admin\AppData\Local\Temp\scoped_dir7724_1423293012\w.bin" | C:\Windows\System32\regini.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Initializer Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2040 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7336 --field-trial-handle=1960,i,11592115911513733292,2520099887901033997,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
117 436
Read events
114 999
Write events
2 156
Delete events
281
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000000000000000000000 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppLaunch |
| Operation: | write | Name: | MSEdge |
Value: 12 | |||
| (PID) Process: | (6184) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (6184) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\6184 |
| Operation: | write | Name: | 0 |
Value: 0B0E1010F7807DE045454A845A6CD427DB85D3230046F699CDCC8CA1EEED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511A830D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6184) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (6184) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (6184) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6184) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (6184) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (6184) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
Executable files
68
Suspicious files
1 404
Text files
347
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6184 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10cfc5.TMP | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10cfc5.TMP | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10cfd5.TMP | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10cfe4.TMP | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5156 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10cfc5.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
295
DNS requests
237
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.5:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8232 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.22.98.7:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8232 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5156 | msedge.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDGUXKxTApCXyVAZtxQ%3D%3D | unknown | — | — | whitelisted |
5156 | msedge.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
2908 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1746418005&P2=404&P3=2&P4=O7HX9sHhLt8nGlJ%2bTwHhKIHgxGeI88jE%2fgRaagT1eyRkeFg5vATfgSPp8BW8Ut7skg%2bb%2fEHOuP2n066Z7RXaVQ%3d%3d | unknown | — | — | whitelisted |
2908 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1746418005&P2=404&P3=2&P4=O7HX9sHhLt8nGlJ%2bTwHhKIHgxGeI88jE%2fgRaagT1eyRkeFg5vATfgSPp8BW8Ut7skg%2bb%2fEHOuP2n066Z7RXaVQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.5:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6184 | OUTLOOK.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
6184 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5156 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7192 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7192 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |