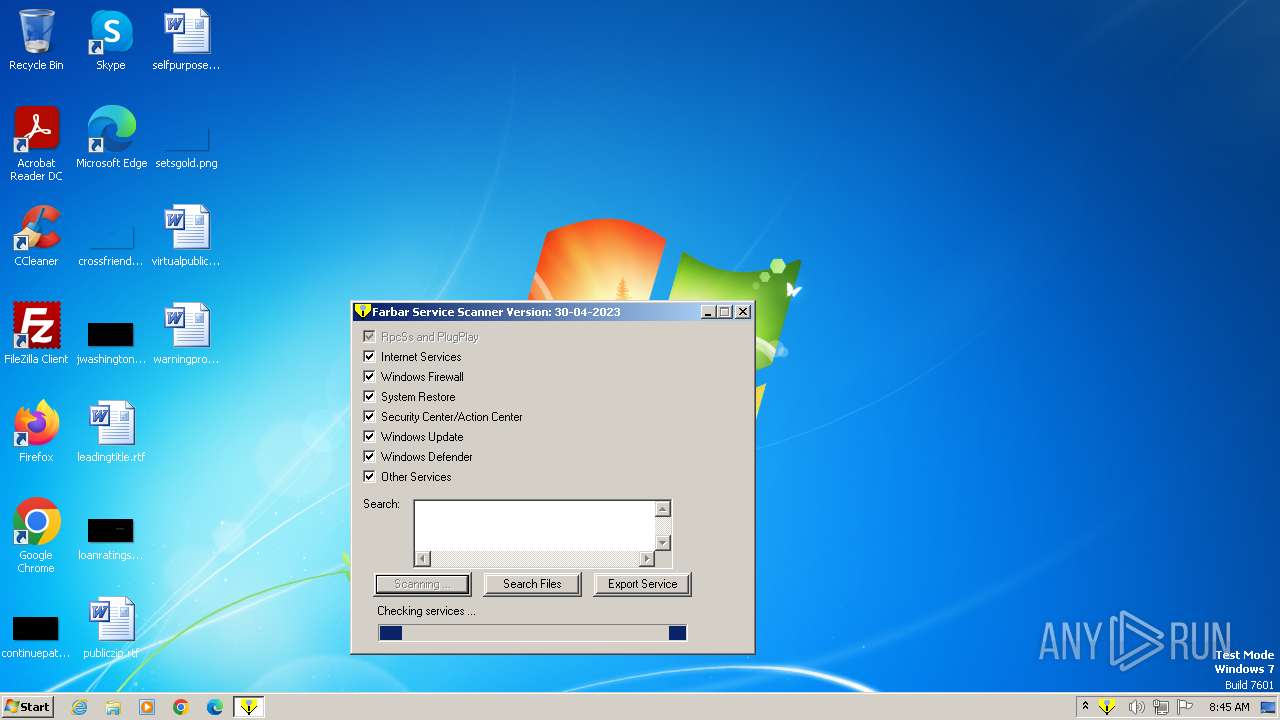
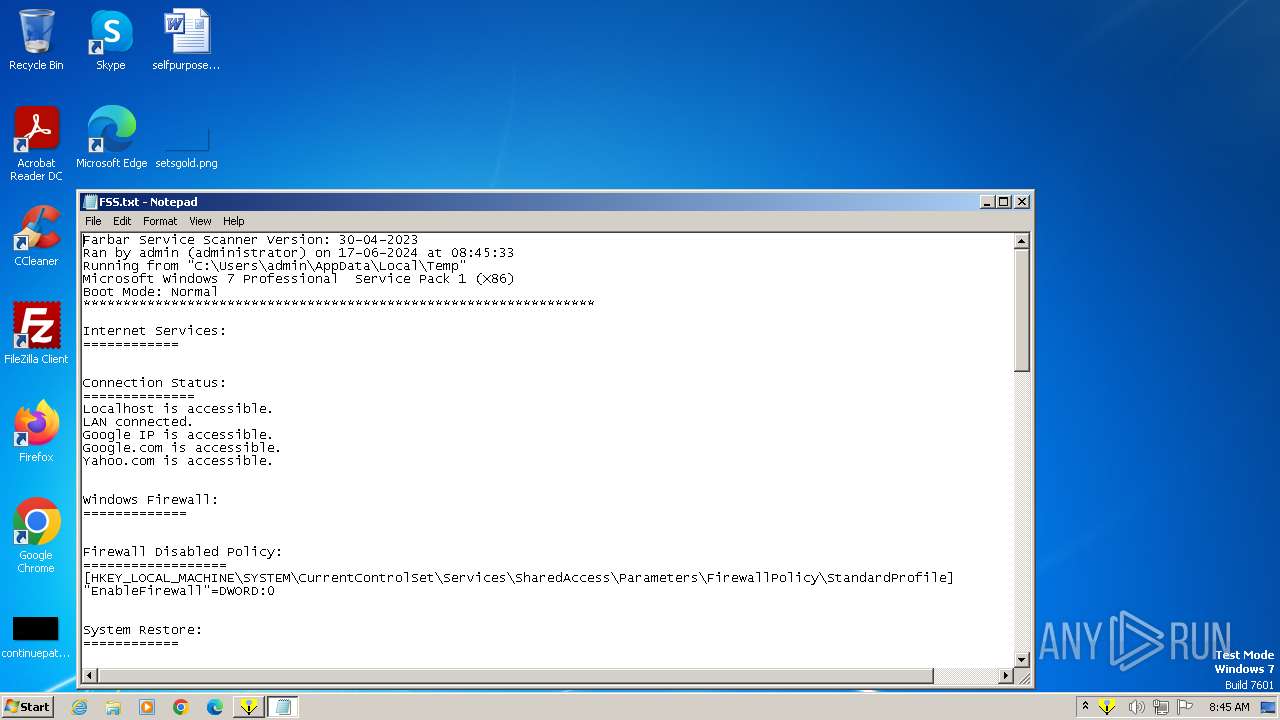
| File name: | FSS.exe |
| Full analysis: | https://app.any.run/tasks/2e925195-7bd7-468a-bd0f-8ddf8023cdae |
| Verdict: | Malicious activity |
| Analysis date: | June 17, 2024, 07:45:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 40008C9437FA2369778FD54C46FCFB0C |
| SHA1: | C97D9B6E808BF80D07E562AD270773FBFCE2FF8E |
| SHA256: | 255E5236769D27D37CB3D4677D50FA442EAA1B422D70F4CD68478C762BF4C293 |
| SSDEEP: | 49152:UPPkzemqoSut3Jh4+QQ/btosJwIA4hHmZlKH2Tw/Pq83zw0bCjvk9G661QGtuA0P:eP/mp7t3T4+B/btosJwIA4hHmZlKH2TA |
MALICIOUS
Drops the executable file immediately after the start
- FSS.exe (PID: 4076)
Starts NET.EXE for service management
- net.exe (PID: 372)
- cmd.exe (PID: 2044)
- cmd.exe (PID: 1580)
- net.exe (PID: 316)
- net.exe (PID: 1704)
- cmd.exe (PID: 1604)
SUSPICIOUS
Detected use of alternative data streams (AltDS)
- FSS.exe (PID: 4076)
Reads the Internet Settings
- FSS.exe (PID: 4076)
Starts CMD.EXE for commands execution
- FSS.exe (PID: 4076)
Executes as Windows Service
- VSSVC.exe (PID: 1056)
Starts SC.EXE for service management
- cmd.exe (PID: 1552)
- cmd.exe (PID: 2368)
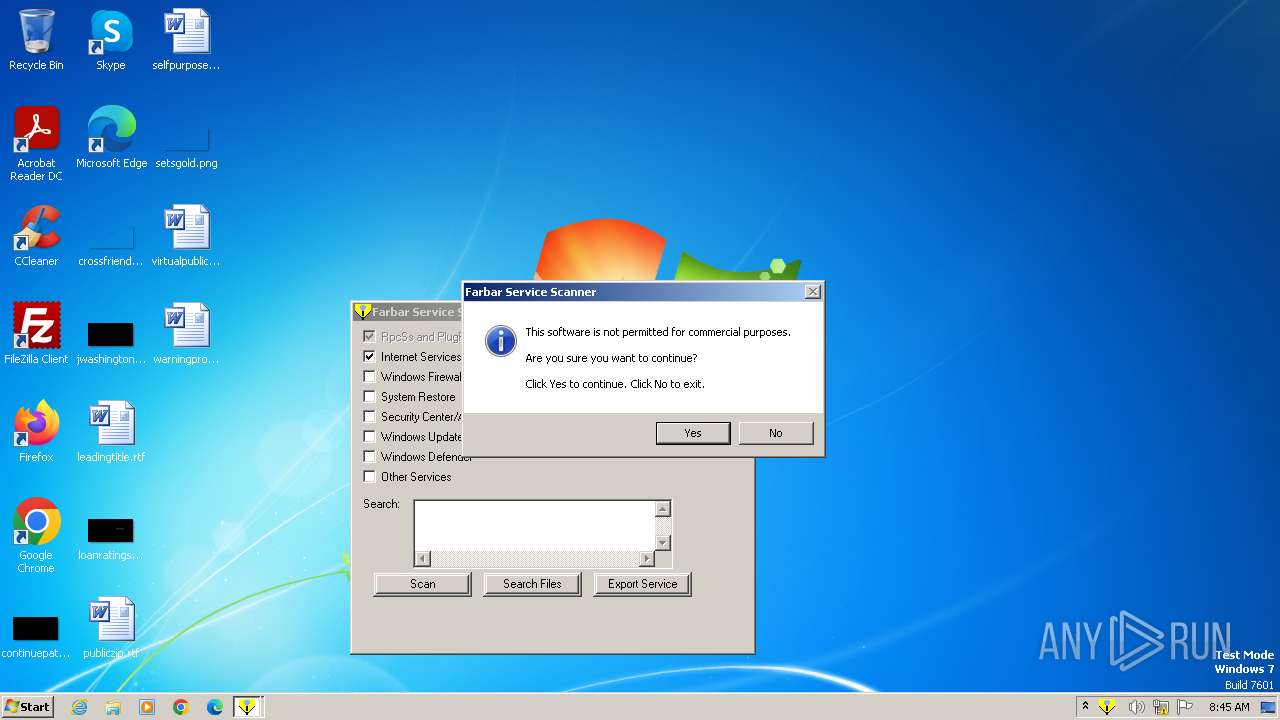
Start notepad (likely ransomware note)
- FSS.exe (PID: 4076)
INFO
Reads mouse settings
- FSS.exe (PID: 4076)
Checks supported languages
- FSS.exe (PID: 4076)
- wmpnscfg.exe (PID: 2304)
Reads the computer name
- FSS.exe (PID: 4076)
- wmpnscfg.exe (PID: 2304)
Reads the machine GUID from the registry
- FSS.exe (PID: 4076)
Checks proxy server information
- FSS.exe (PID: 4076)
Create files in a temporary directory
- FSS.exe (PID: 4076)
Manual execution by a user
- wmpnscfg.exe (PID: 2304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:04:30 16:26:56+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 633856 |
| InitializedDataSize: | 324608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x20577 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 30.4.2023.0 |
| ProductVersionNumber: | 30.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| FileVersion: | 30.4.2023.0 |
| Comments: | http://www.autoitscript.com/autoit3/ |
| FileDescription: | Farbar Service Scanner |
| ProductVersion: | 30-04-2023 |
| LegalCopyright: | © 1999-2022 Jonathan Bennett & AutoIt Team |
| CompanyName: | Farbar |
Total processes
60
Monitored processes
18
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | net start VSS | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 372 | net start SDRSVC | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 524 | C:\Windows\system32\net1 start VSS | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 568 | notepad.exe FSS.txt | C:\Windows\System32\notepad.exe | — | FSS.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1056 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1184 | C:\Windows\system32\net1 start SDRSVC | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1424 | C:\Windows\system32\net1 start wuauserv | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1552 | C:\Windows\system32\cmd.exe /c sc query rpcss >"C:\Users\admin\AppData\Local\Temp\tmp00" | C:\Windows\System32\cmd.exe | — | FSS.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1580 | C:\Windows\system32\cmd.exe /c net start VSS | C:\Windows\System32\cmd.exe | — | FSS.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1596 | sc query rpcss | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 451
Read events
1 437
Write events
14
Delete events
0
Modification events
| (PID) Process: | (4076) FSS.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4076 | FSS.exe | C:\Users\admin\AppData\Local\Temp\cmd17061.txt | — | |
MD5:— | SHA256:— | |||
| 4076 | FSS.exe | C:\Users\admin\AppData\Local\Temp\FSS.txt | text | |
MD5:C946FEB25996ECE5140D50931F77F94A | SHA256:7FB3D93EEB7DFBDD2AD8391A5EADAAEF5DABD13DF8F35A5C294D21C5EED7E201 | |||
| 2368 | cmd.exe | C:\Users\admin\AppData\Local\Temp\tmp00 | text | |
MD5:31F84B0472553D89C8B340DB1D4F695F | SHA256:9D2FC13514AAF2483B5CF42126DF77A485D680ECC2BD1DDB242DBC811A65119B | |||
| 4076 | FSS.exe | C:\Users\admin\AppData\Local\Temp\cmd26675.txt | text | |
MD5:C056D0C5563DD749E12B57EE8F3D1F4E | SHA256:81920D64F8BB9D47CD94B3DA71D2E77357C70833E4F0C5ADAEC3EC16ECD0CC22 | |||
| 1552 | cmd.exe | C:\Users\admin\AppData\Local\Temp\tmp00 | text | |
MD5:31F84B0472553D89C8B340DB1D4F695F | SHA256:9D2FC13514AAF2483B5CF42126DF77A485D680ECC2BD1DDB242DBC811A65119B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2092 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
yahoo.com |
| whitelisted |