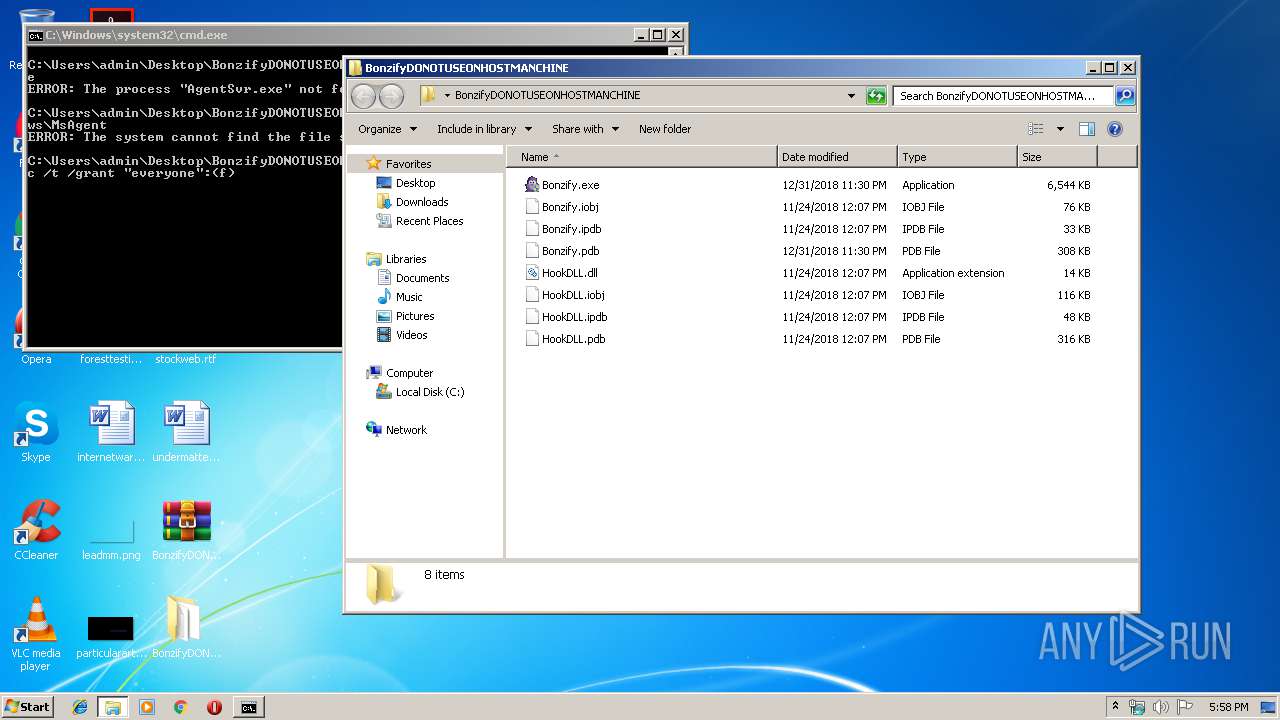
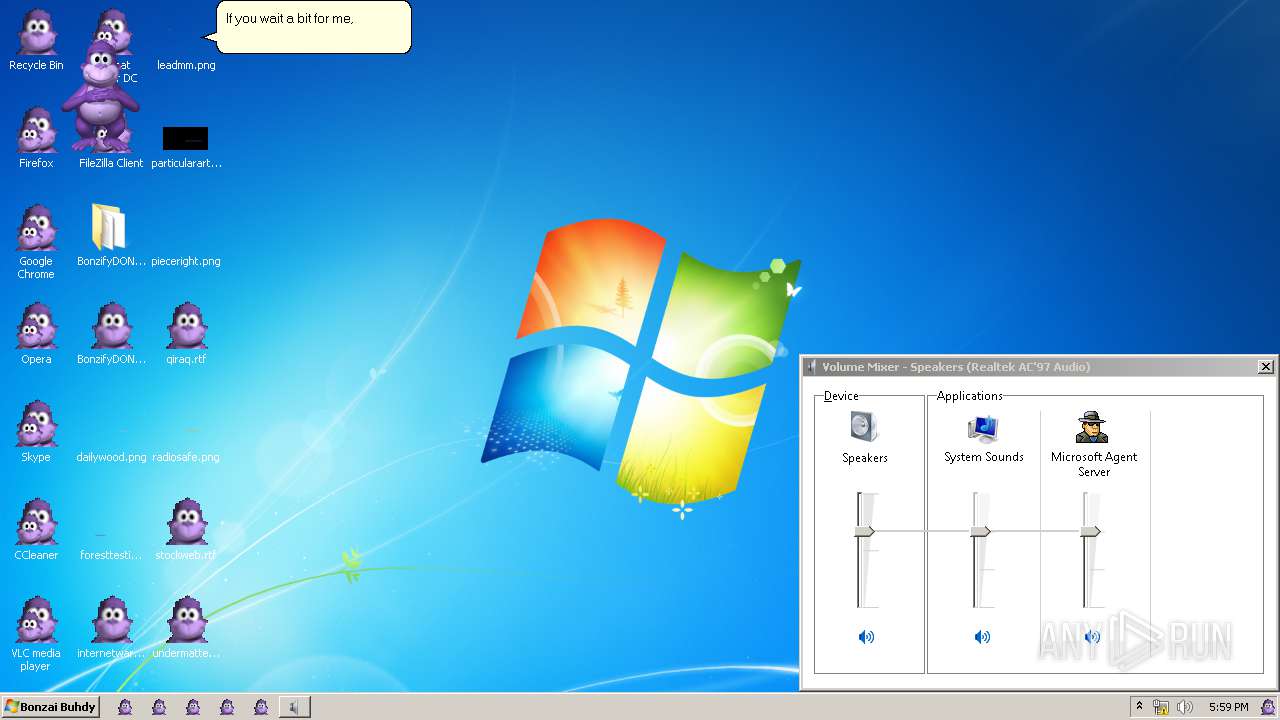
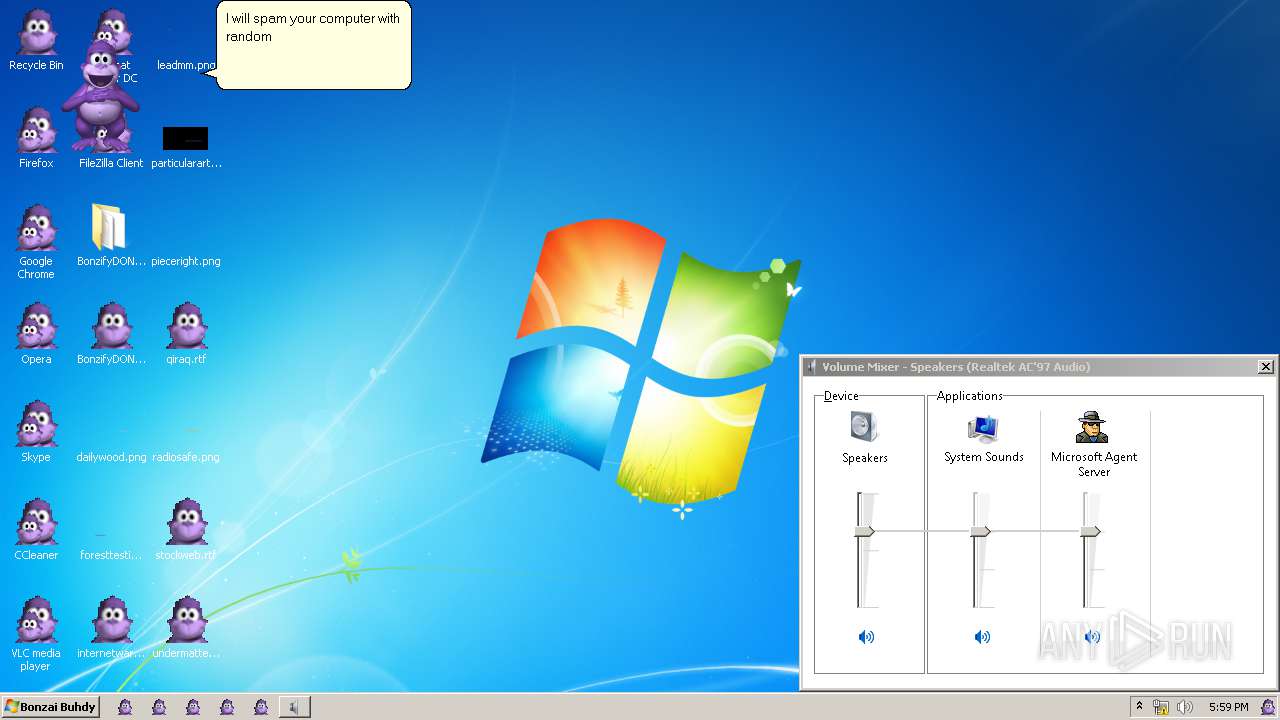
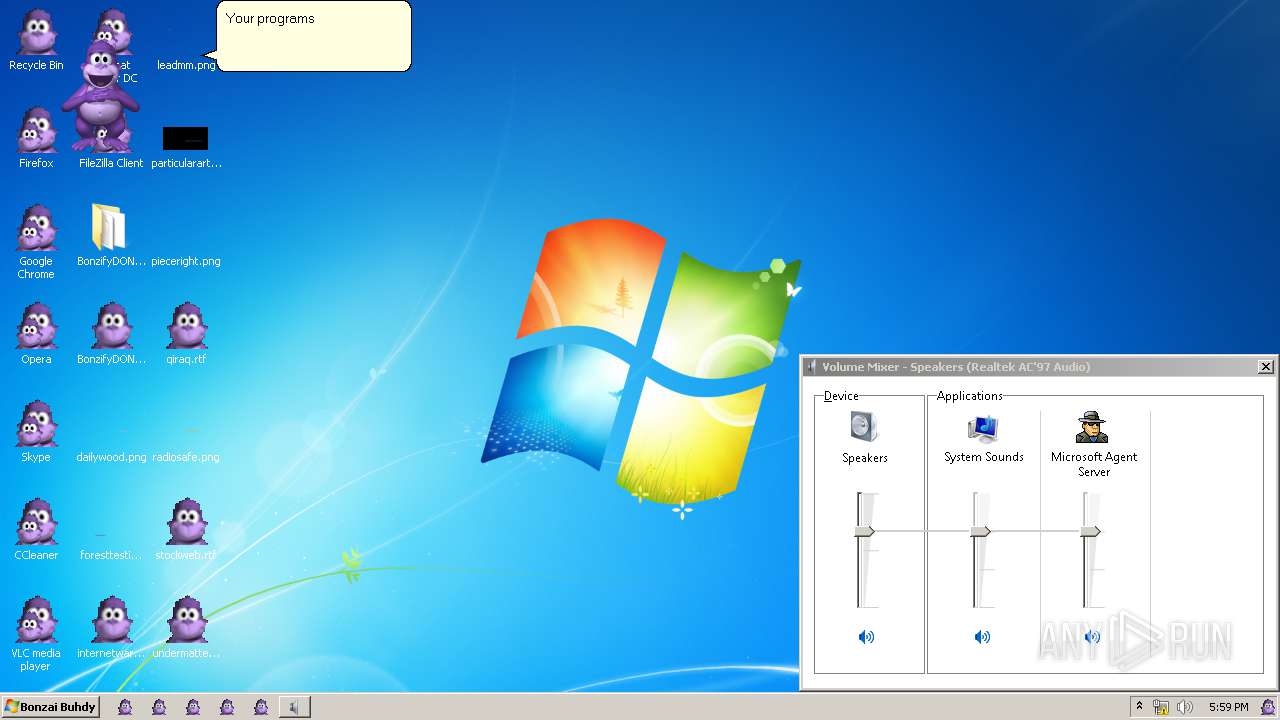
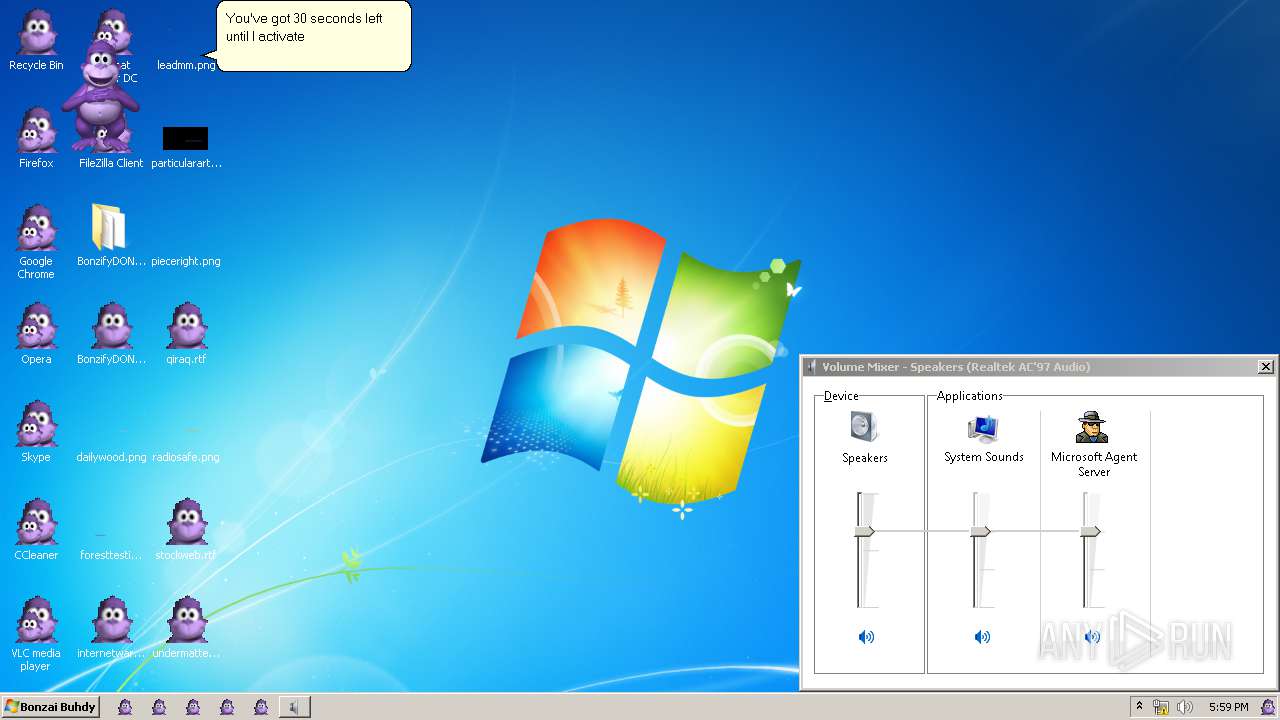
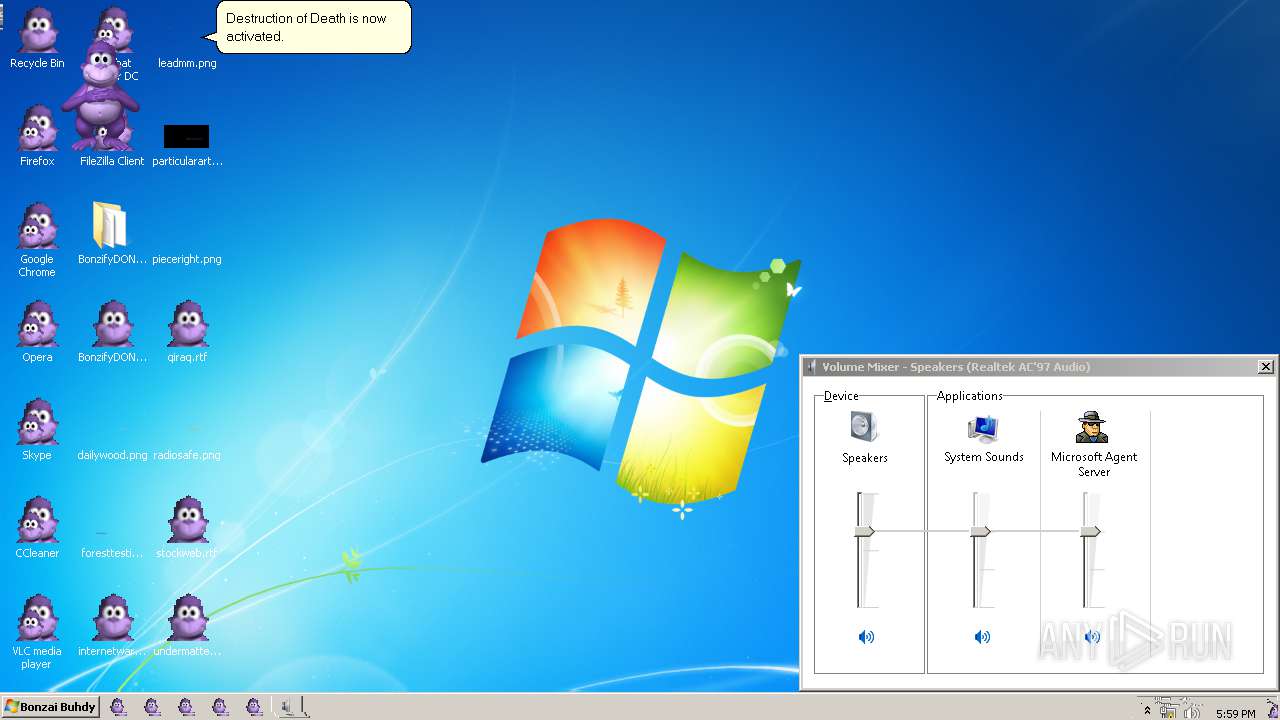
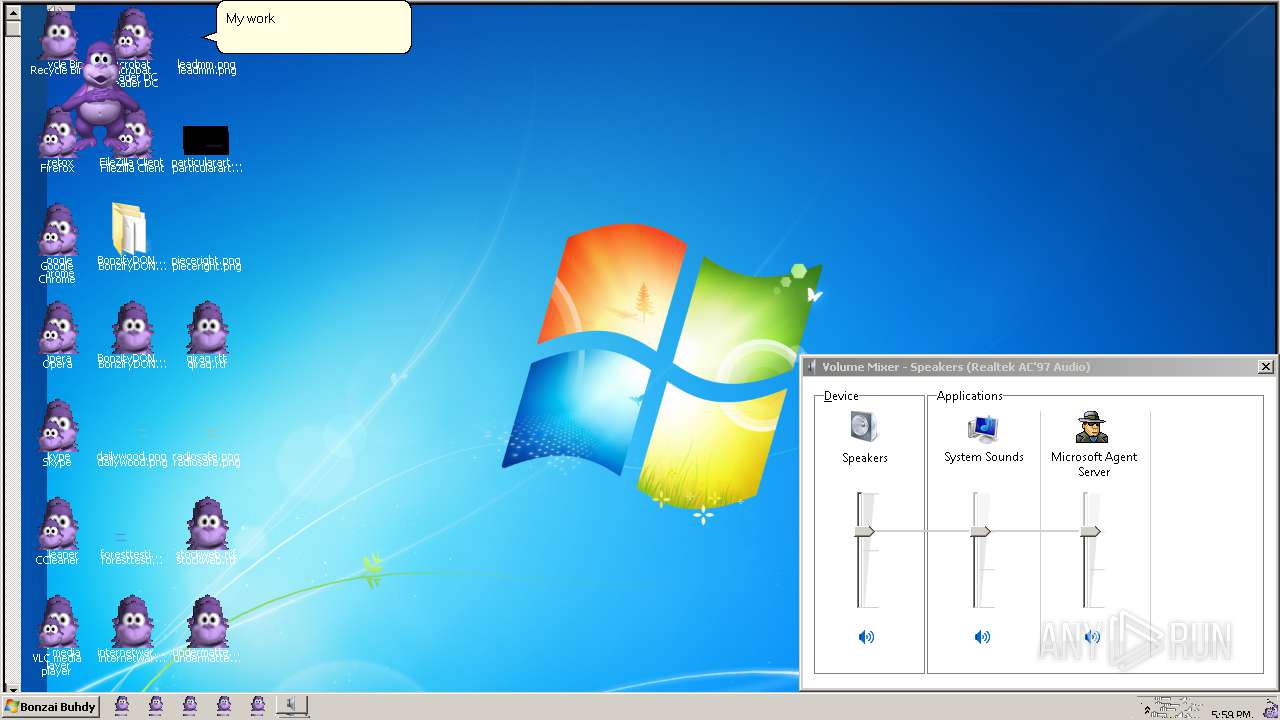
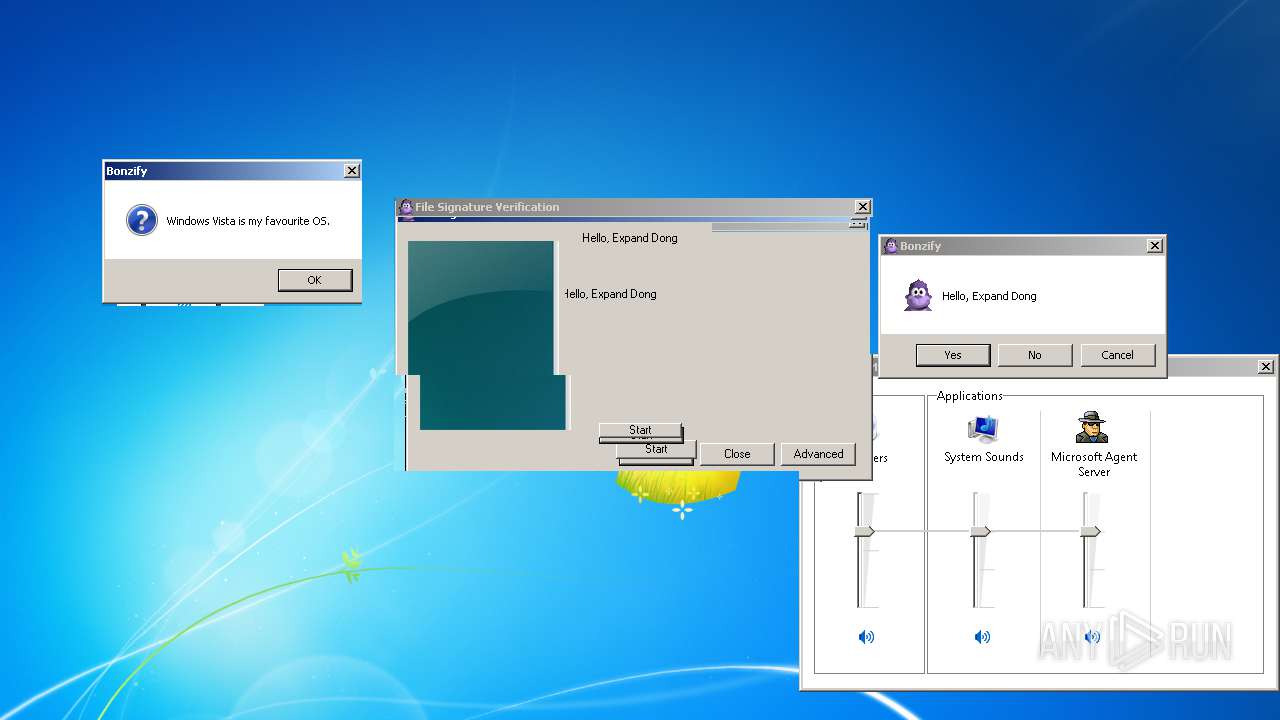
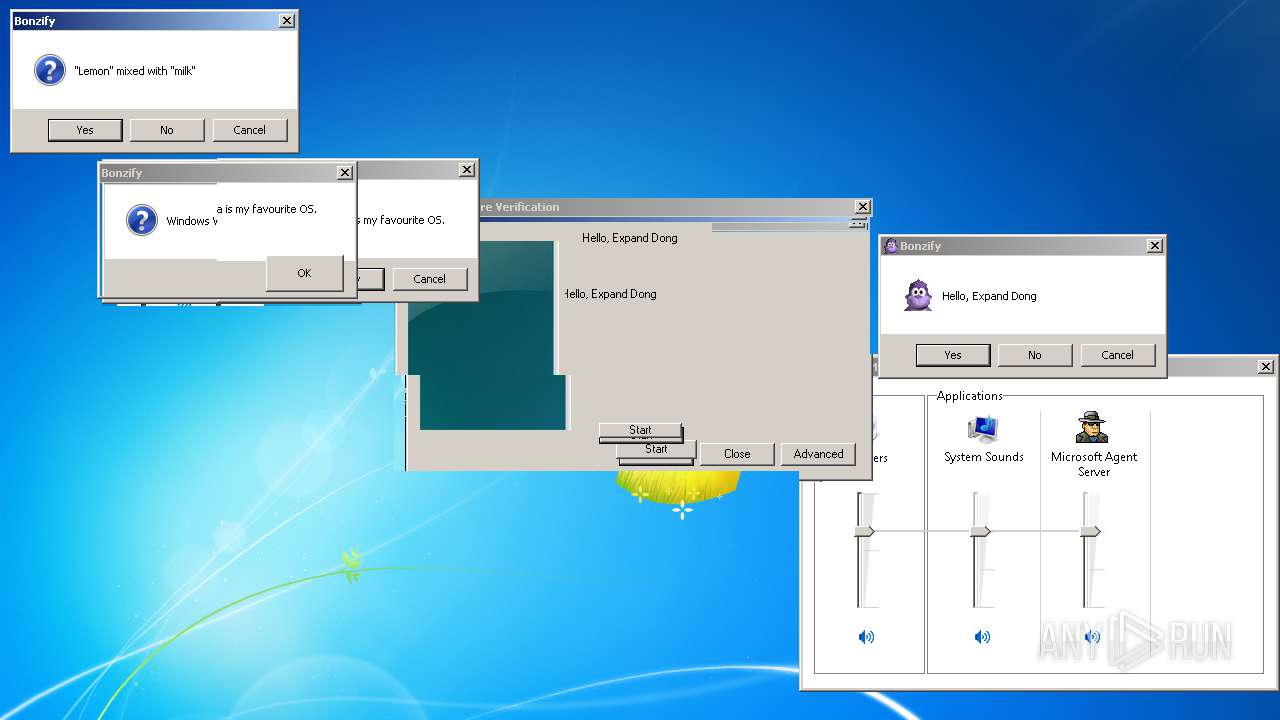
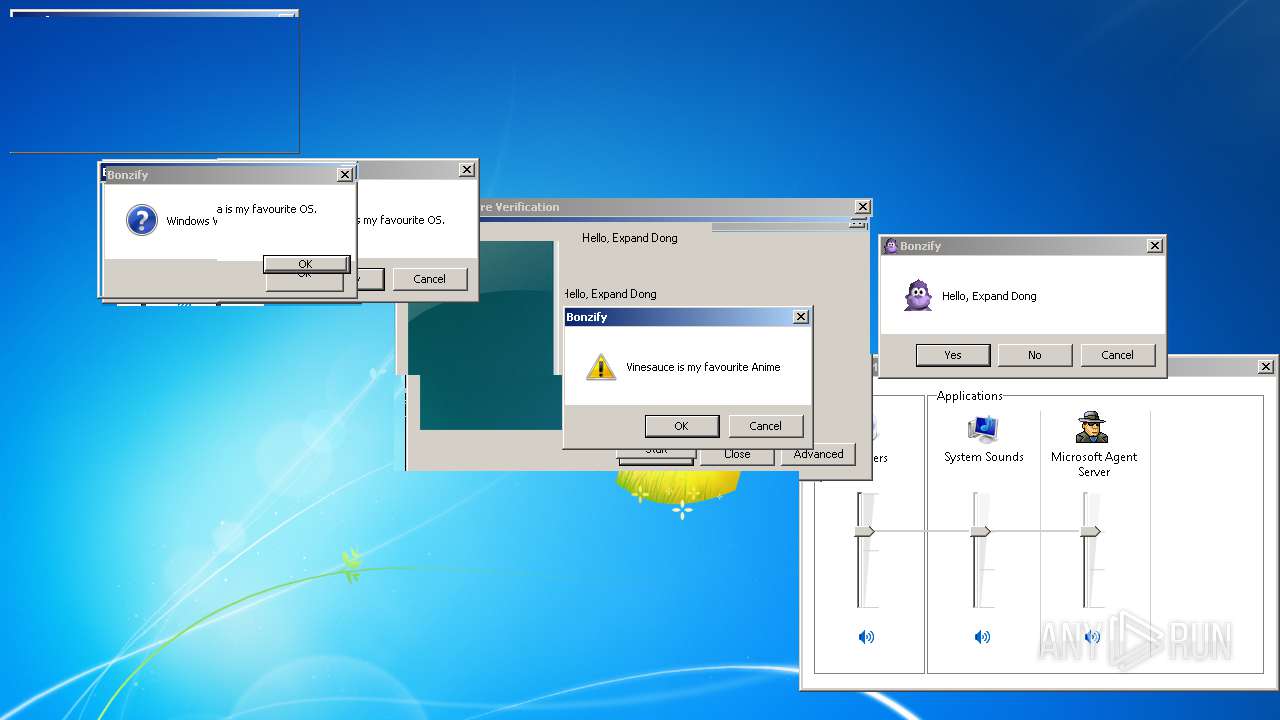
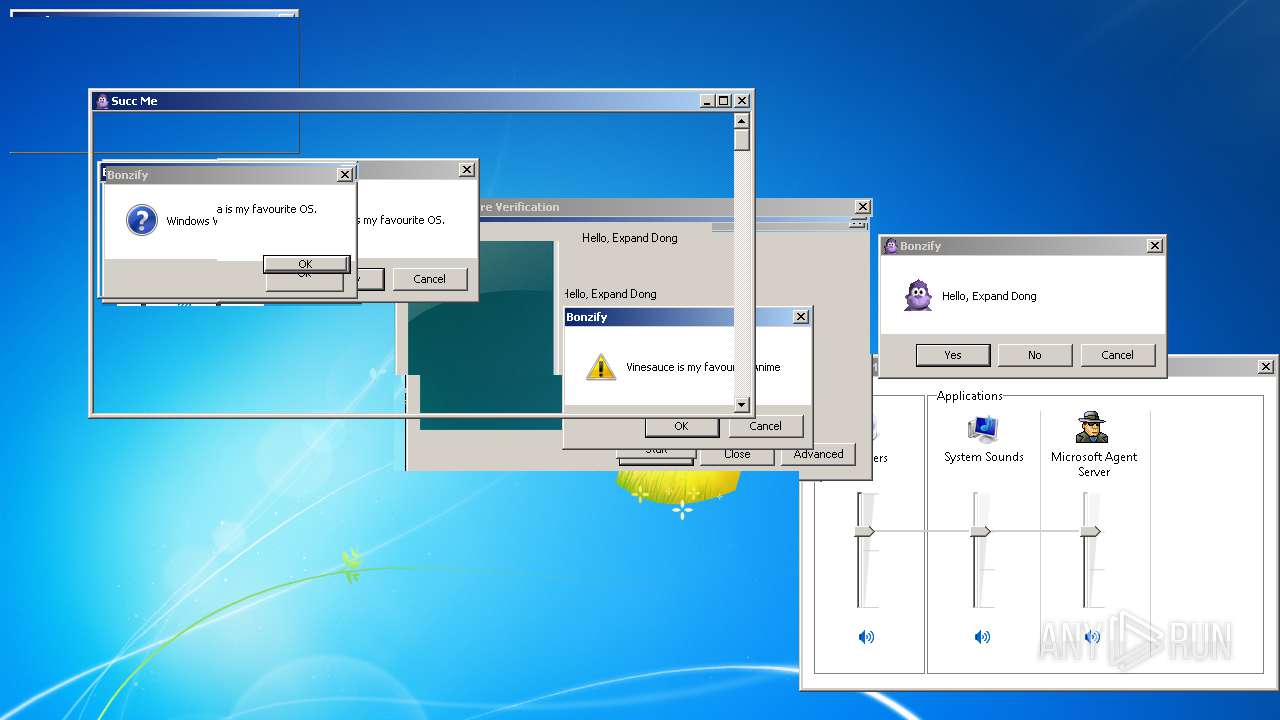
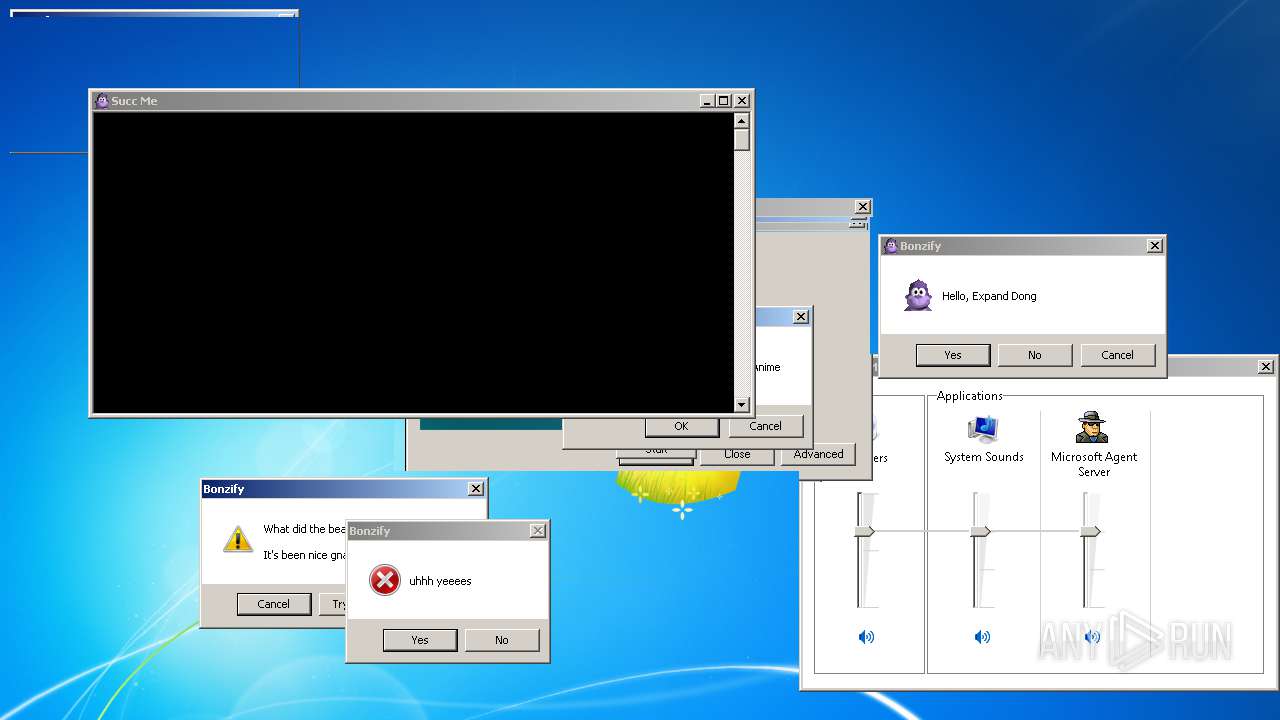
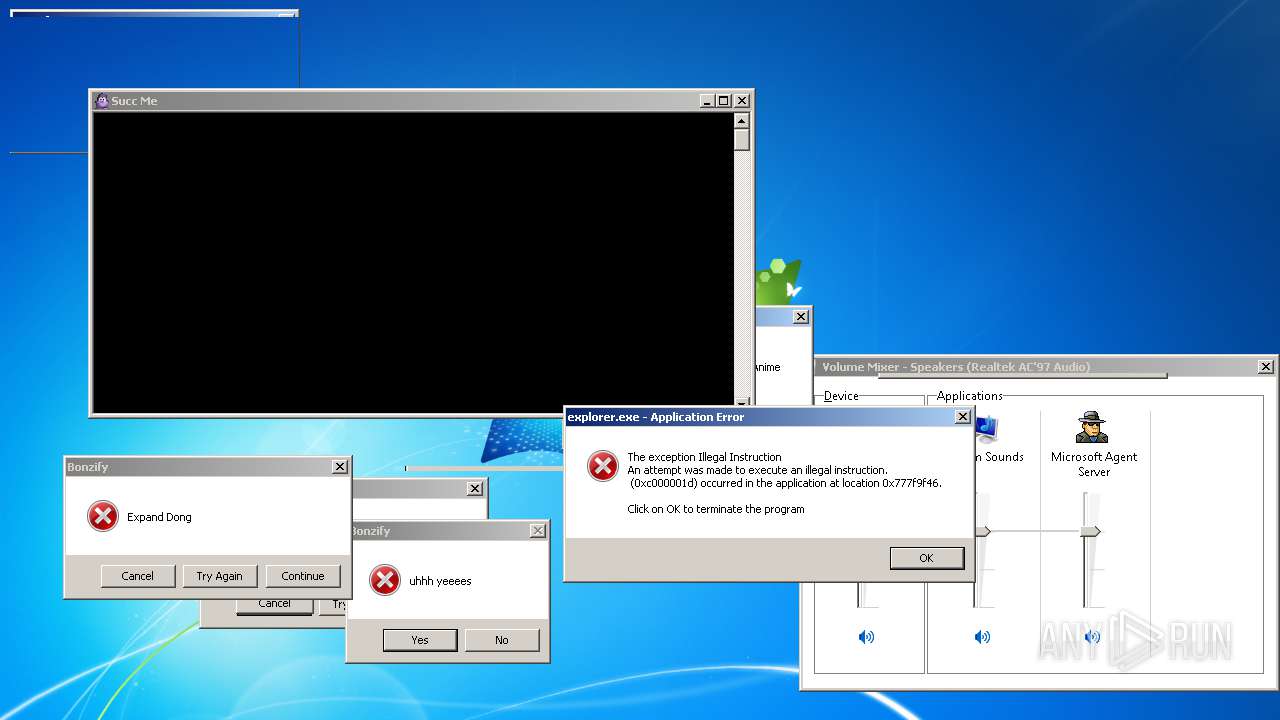
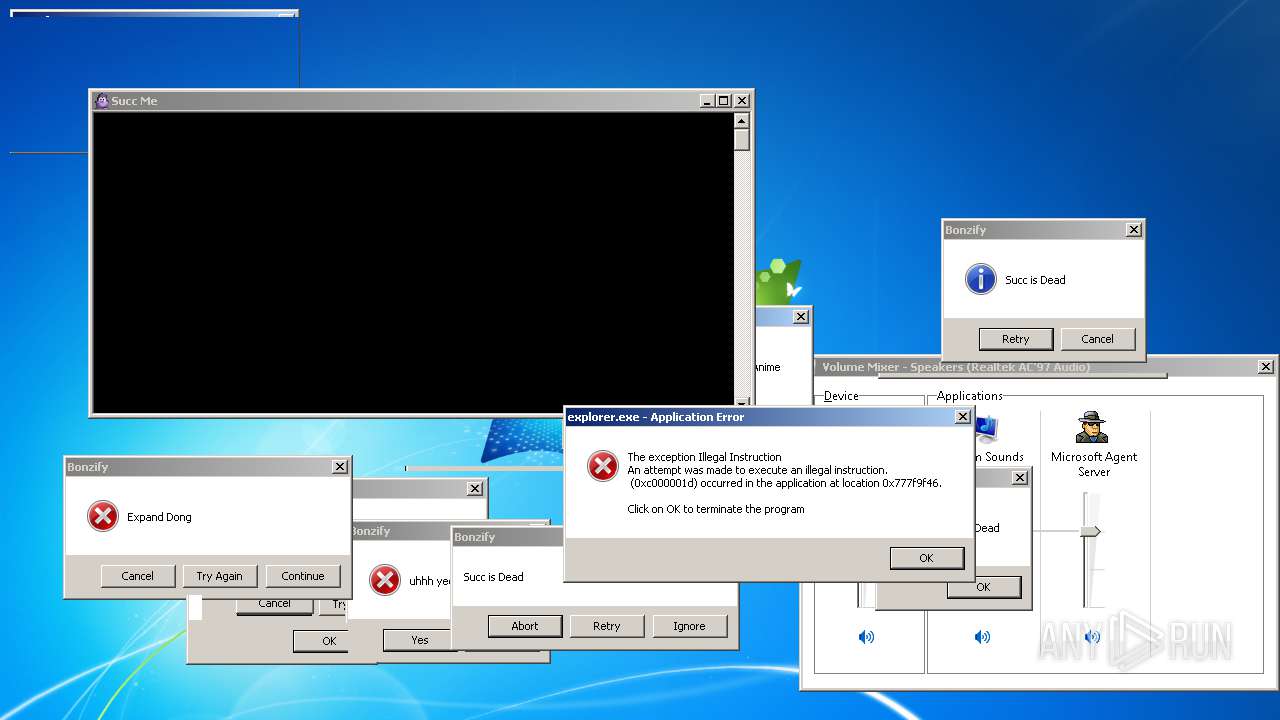
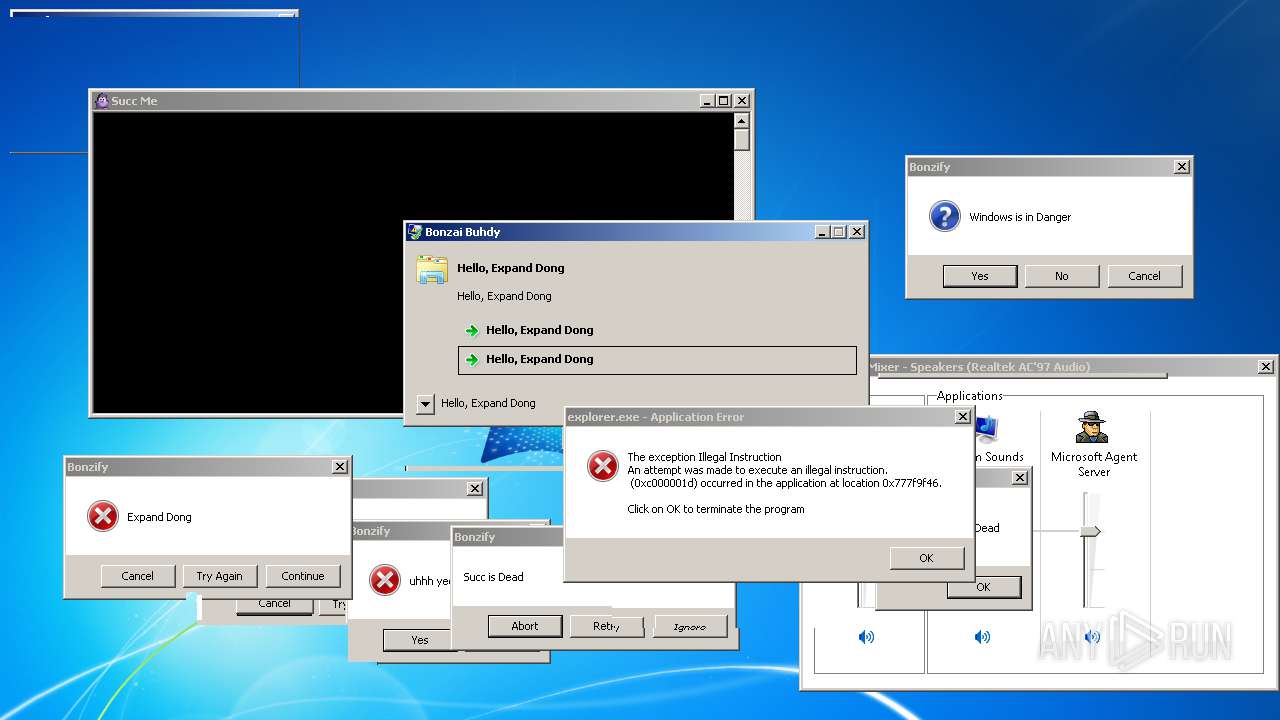
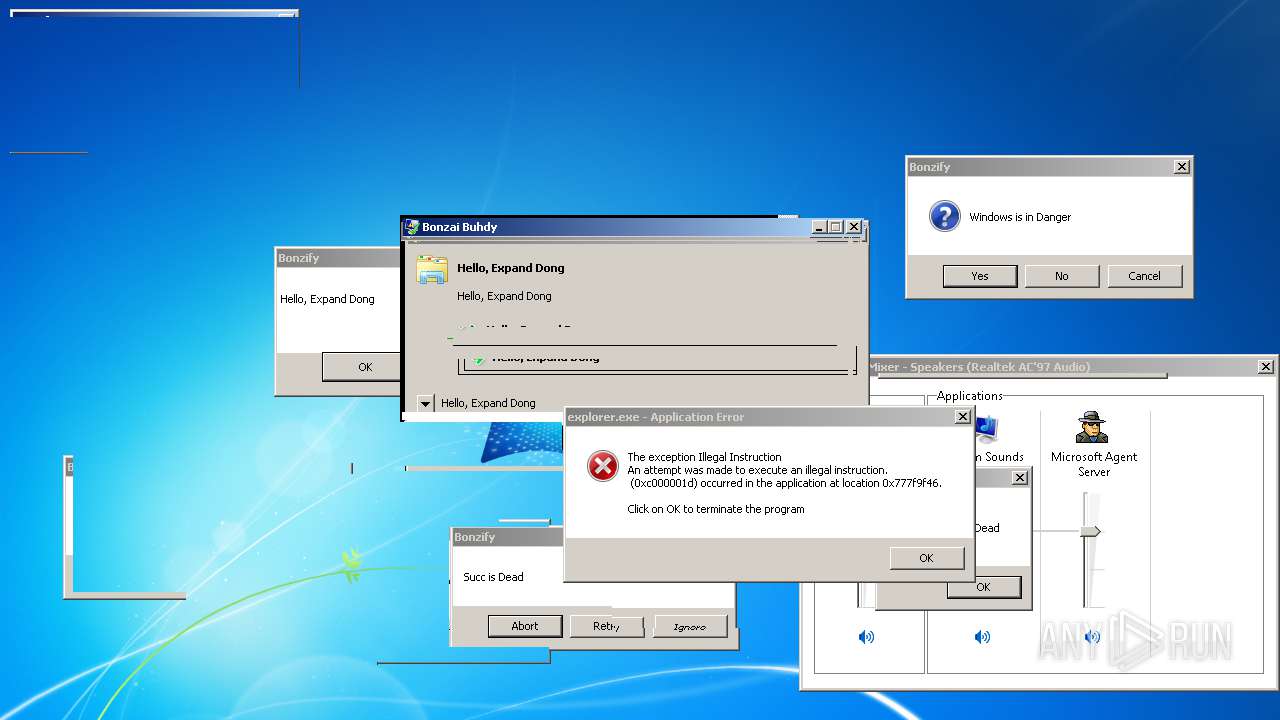
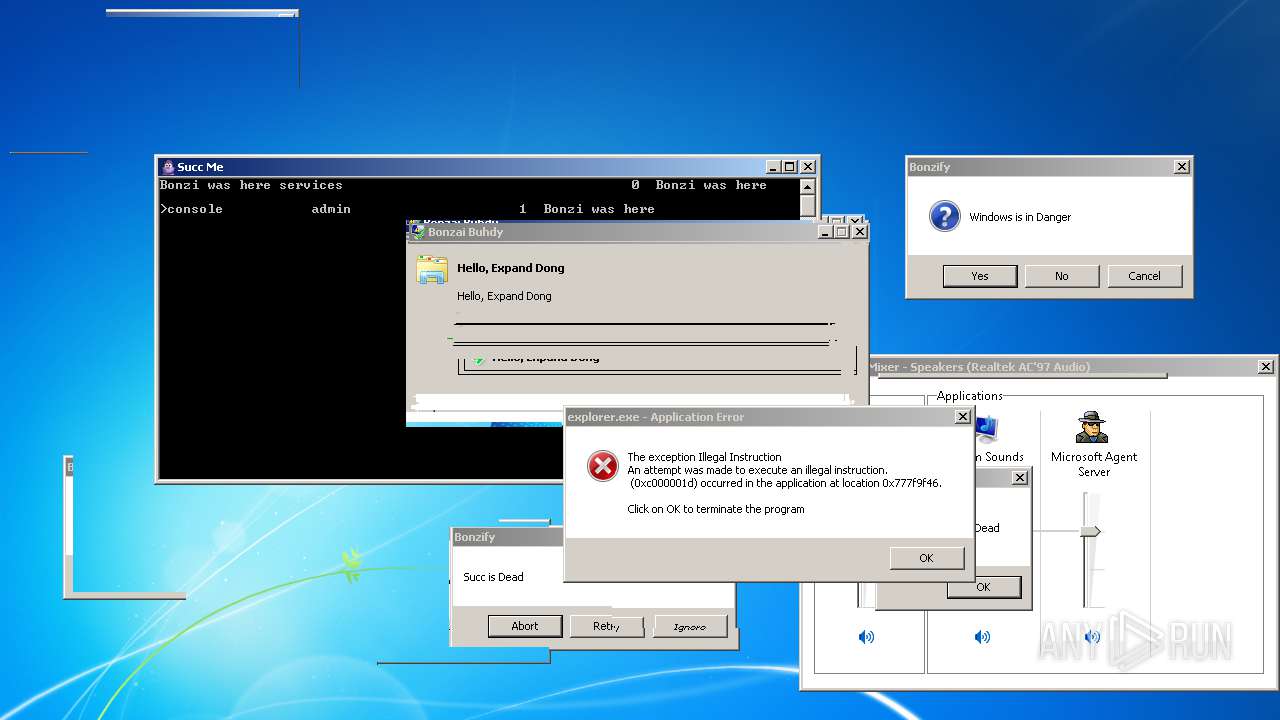
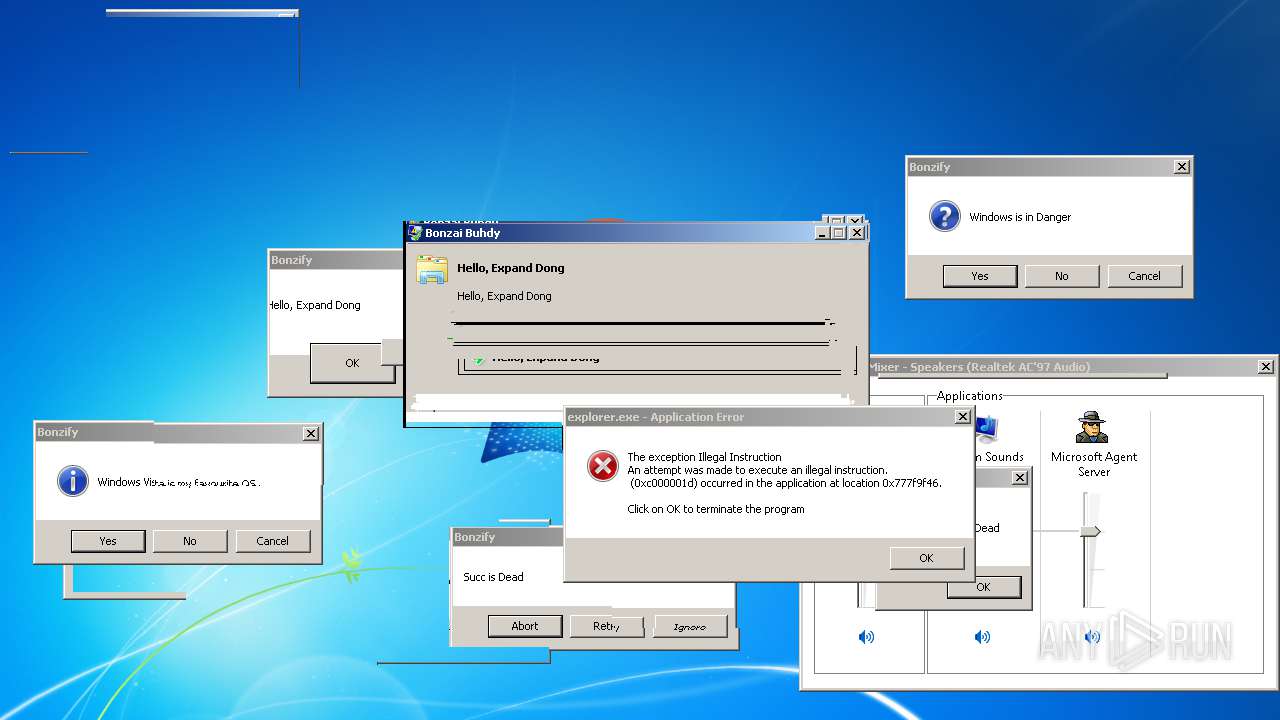
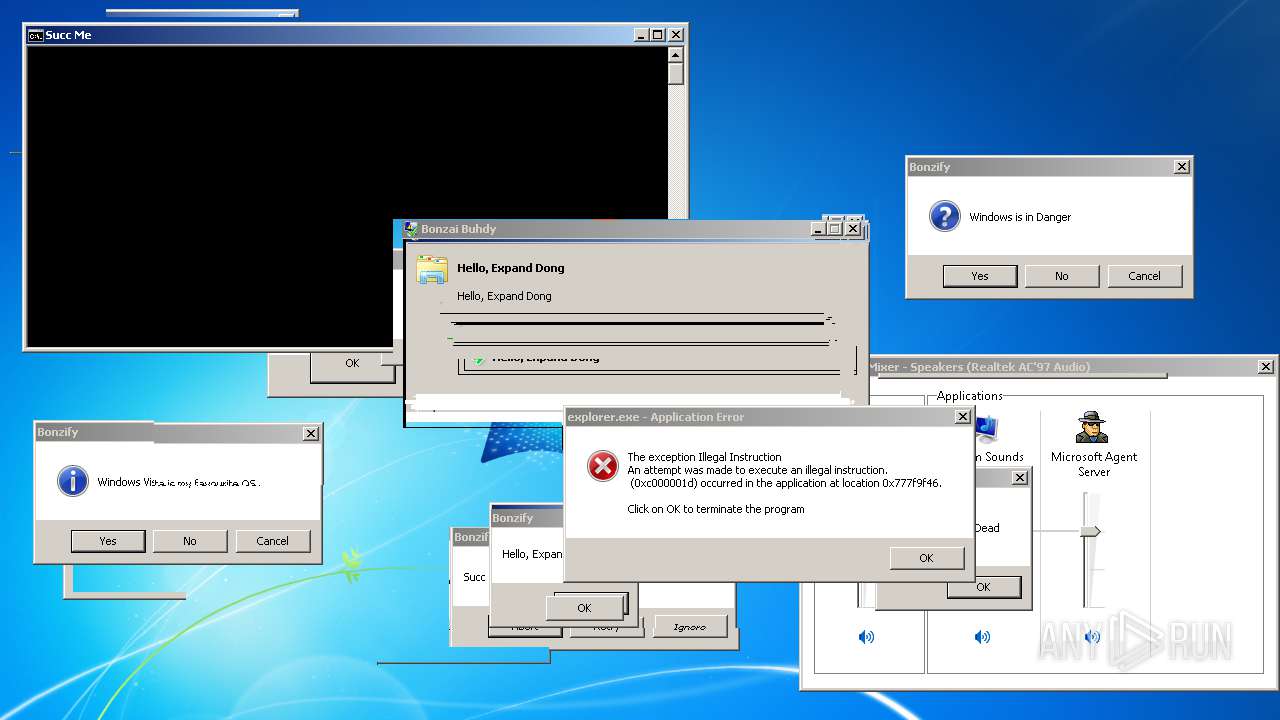
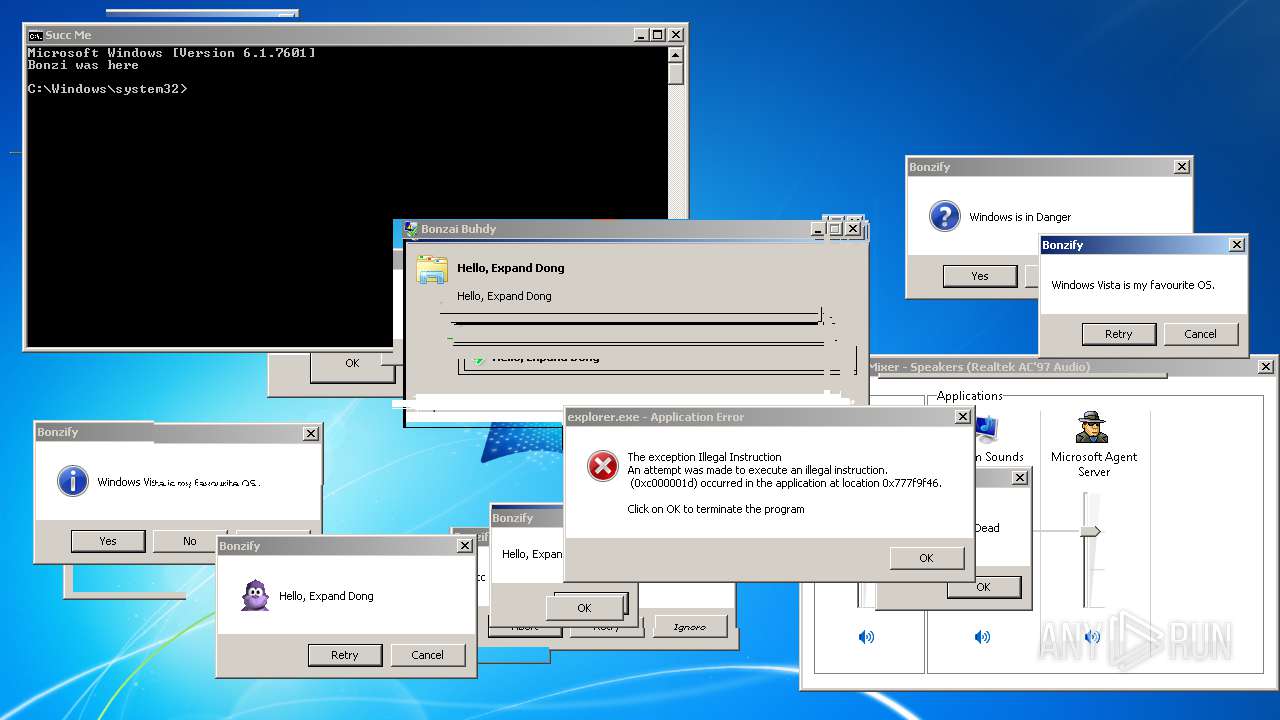
| File name: | BonzifyDONOTUSEONHOSTMANCHINE.zip |
| Full analysis: | https://app.any.run/tasks/2462ab73-5987-4bed-9515-6a98d8d9fefa |
| Verdict: | Malicious activity |
| Analysis date: | October 04, 2019, 16:57:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | E7217F2A4848EBB0020CA09A635DC3D7 |
| SHA1: | 7B5DCB93B0047DEAB8A8AF0BD176C226FE1E9EFD |
| SHA256: | 25583E032BB8D882A70EFBD1A7990AF70B09A8EC384A244FDAB6F807E16080CC |
| SSDEEP: | 98304:m8oleb6y2+cFSgSyv0vdiCkeIXUo3oybZ2ea71WFtI1oSmeRA+98Dp0xl9OEelng:mnC6y2+caliZlB339257YS0Dp0xQV7M |
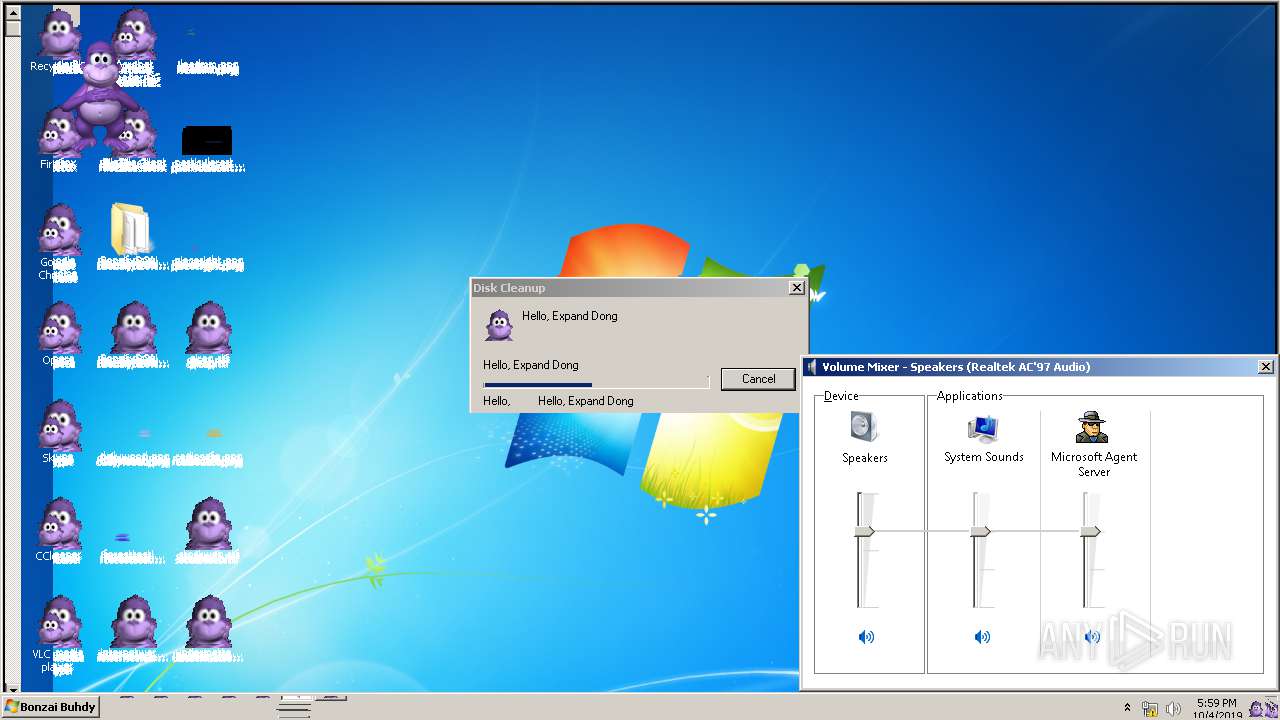
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1472)
- regsvr32.exe (PID: 3140)
- AgentSvr.exe (PID: 3184)
- regsvr32.exe (PID: 552)
- INSTALLER.exe (PID: 2404)
- INSTALLER.exe (PID: 3820)
- SearchProtocolHost.exe (PID: 3624)
- svchost.exe (PID: 956)
- WerFault.exe (PID: 3604)
- conhost.exe (PID: 2620)
- cleanmgr.exe (PID: 1124)
- sigverif.exe (PID: 3216)
- reader_sl.exe (PID: 2504)
- conhost.exe (PID: 2044)
- WMIC.exe (PID: 3480)
- explorer.exe (PID: 4092)
- DllHost.exe (PID: 2300)
- conhost.exe (PID: 3940)
- Microsoft.Workflow.Compiler.exe (PID: 668)
- ielowutil.exe (PID: 3356)
- svchost.exe (PID: 3124)
- conhost.exe (PID: 2444)
- wuapp.exe (PID: 2672)
- WerFault.exe (PID: 1128)
- WerFault.exe (PID: 3088)
- WINWORD.EXE (PID: 3908)
- sethc.exe (PID: 4012)
- explorer.exe (PID: 1944)
- conhost.exe (PID: 3944)
- svchost.exe (PID: 2832)
- iexplore.exe (PID: 3988)
- WerFault.exe (PID: 2704)
- conhost.exe (PID: 2328)
- WerFault.exe (PID: 3012)
- WerFault.exe (PID: 3256)
- cmbins.exe (PID: 2684)
- WerFault.exe (PID: 2368)
- explorer.exe (PID: 2180)
- TRACERT.EXE (PID: 2000)
- dfsvc.exe (PID: 1420)
- conhost.exe (PID: 3468)
- ehsched.exe (PID: 292)
- AppLaunch.exe (PID: 2556)
- svchost.exe (PID: 3964)
- ntvdm.exe (PID: 3240)
- where.exe (PID: 3164)
- PresentationSettings.exe (PID: 1868)
- WerFaultSecure.exe (PID: 2104)
- qwinsta.exe (PID: 2552)
- conhost.exe (PID: 2228)
- conhost.exe (PID: 3580)
- iexplore.exe (PID: 3008)
- msinfo32.exe (PID: 4016)
- dpnsvr.exe (PID: 3648)
- conhost.exe (PID: 2236)
- conhost.exe (PID: 3584)
- cmd.exe (PID: 2244)
- svchost.exe (PID: 3172)
- conhost.exe (PID: 312)
Application was dropped or rewritten from another process
- Bonzify.exe (PID: 2404)
- Bonzify.exe (PID: 2468)
- INSTALLER.exe (PID: 2404)
- INSTALLER.exe (PID: 3820)
Registers / Runs the DLL via REGSVR32.EXE
- INSTALLER.exe (PID: 2404)
- INSTALLER.exe (PID: 3820)
Changes the autorun value in the registry
- INSTALLER.exe (PID: 3820)
- Bonzify.exe (PID: 2468)
- conhost.exe (PID: 3940)
- explorer.exe (PID: 2180)
- conhost.exe (PID: 3468)
- iexplore.exe (PID: 3988)
- conhost.exe (PID: 3580)
Changes AppInit_DLLs value (autorun option)
- Bonzify.exe (PID: 2468)
Loads the Task Scheduler COM API
- explorer.exe (PID: 4092)
Changes internet zones settings
- explorer.exe (PID: 4092)
- cleanmgr.exe (PID: 1124)
- sigverif.exe (PID: 3216)
- conhost.exe (PID: 2328)
- reader_sl.exe (PID: 2504)
- iexplore.exe (PID: 3988)
- conhost.exe (PID: 3468)
- conhost.exe (PID: 3580)
- WerFault.exe (PID: 3012)
- conhost.exe (PID: 3584)
Changes Windows Error Reporting flag
- svchost.exe (PID: 3172)
Runs app for hidden code execution
- WerFault.exe (PID: 3012)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 772)
- Bonzify.exe (PID: 2468)
- INSTALLER.exe (PID: 3820)
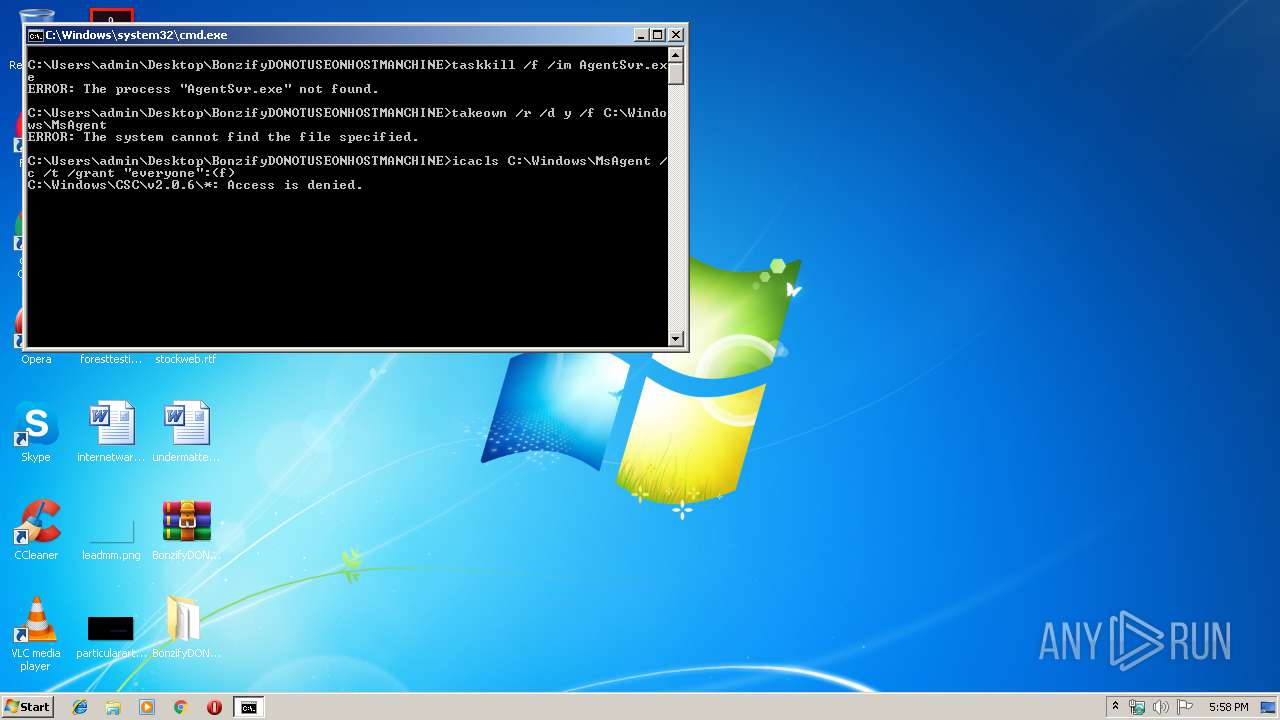
Starts CMD.EXE for commands execution
- Bonzify.exe (PID: 2468)
- WerFault.exe (PID: 3012)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1928)
Uses ICACLS.EXE to modify access control list
- cmd.exe (PID: 1928)
Creates files in the Windows directory
- Bonzify.exe (PID: 2468)
- INSTALLER.exe (PID: 2404)
- INSTALLER.exe (PID: 3820)
Removes files from Windows directory
- INSTALLER.exe (PID: 2404)
- INSTALLER.exe (PID: 3820)
Creates COM task schedule object
- regsvr32.exe (PID: 3380)
- regsvr32.exe (PID: 3400)
- regsvr32.exe (PID: 3604)
- regsvr32.exe (PID: 2556)
- regsvr32.exe (PID: 3688)
- regsvr32.exe (PID: 2604)
- regsvr32.exe (PID: 552)
- regsvr32.exe (PID: 3140)
- regsvr32.exe (PID: 3636)
- explorer.exe (PID: 4092)
- cleanmgr.exe (PID: 1124)
- reader_sl.exe (PID: 2504)
- sigverif.exe (PID: 3216)
- wuapp.exe (PID: 2672)
- iexplore.exe (PID: 3988)
- conhost.exe (PID: 2328)
- conhost.exe (PID: 3468)
- WerFault.exe (PID: 3012)
- conhost.exe (PID: 3580)
- conhost.exe (PID: 3584)
Creates a software uninstall entry
- INSTALLER.exe (PID: 3820)
- iexplore.exe (PID: 3988)
Starts SC.EXE for service management
- explorer.exe (PID: 4092)
Executes application which crashes
- sigverif.exe (PID: 3216)
- WerFault.exe (PID: 3012)
Changes IE settings (feature browser emulation)
- Microsoft.Workflow.Compiler.exe (PID: 668)
Executed via COM
- explorer.exe (PID: 2180)
Starts itself from another location
- WerFault.exe (PID: 3012)
Application launched itself
- iexplore.exe (PID: 3988)
Modifies the open verb of a shell class
- iexplore.exe (PID: 3988)
- WerFault.exe (PID: 3012)
INFO
Manual execution by user
- Bonzify.exe (PID: 2404)
- WinRAR.exe (PID: 772)
- Bonzify.exe (PID: 2468)
- SndVol.exe (PID: 3400)
Dropped object may contain Bitcoin addresses
- Bonzify.exe (PID: 2468)
Application was crashed
- SearchProtocolHost.exe (PID: 3624)
- conhost.exe (PID: 3940)
- explorer.exe (PID: 4092)
- explorer.exe (PID: 2180)
- sigverif.exe (PID: 3216)
- explorer.exe (PID: 1944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:12:31 23:30:28 |
| ZipCRC: | 0x1f63e226 |
| ZipCompressedSize: | 5871582 |
| ZipUncompressedSize: | 6700544 |
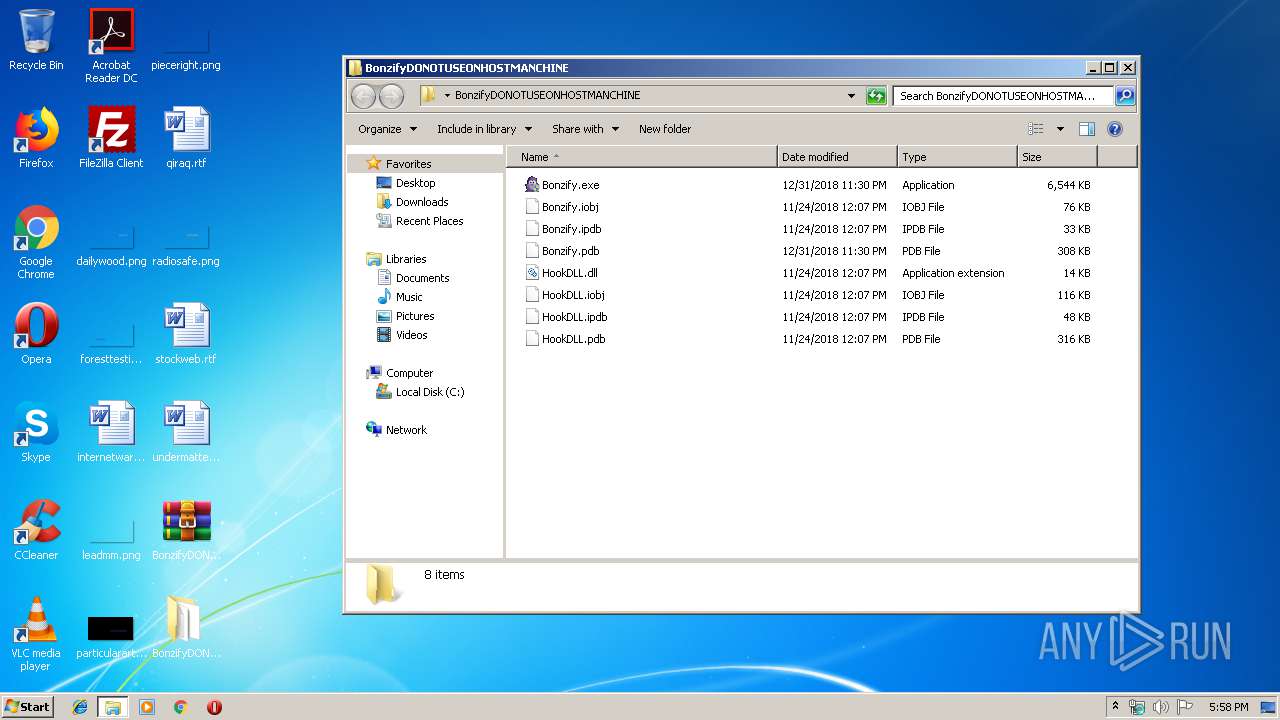
| ZipFileName: | Bonzify.exe |
Total processes
159
Monitored processes
102
Malicious processes
16
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Windows\winsxs\x86_microsoft-windows-ehome-services-ehsched_31bf3856ad364e35_6.1.7600.16385_none_a54954fd9d61ab4b\ehsched.exe" | C:\Windows\winsxs\x86_microsoft-windows-ehome-services-ehsched_31bf3856ad364e35_6.1.7600.16385_none_a54954fd9d61ab4b\ehsched.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Center Scheduler Service Exit code: 2147942405 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 312 | \??\C:\Windows\system32\conhost.exe | C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 552 | regsvr32 /s C:\Windows\lhsp\tv\tv_enua.dll | C:\Windows\system32\regsvr32.exe | — | INSTALLER.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\Microsoft.Workflow.Compiler.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\Microsoft.Workflow.Compiler.exe | — | reader_sl.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft.Workflow.Compiler.exe Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 772 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\BonzifyDONOTUSEONHOSTMANCHINE.zip" C:\Users\admin\Desktop\BonzifyDONOTUSEONHOSTMANCHINE\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 956 | C:\Windows\System32\svchost.exe -k WerSvcGroup | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 3221226356 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1124 | "C:\Windows\System32\cleanmgr.exe" | C:\Windows\System32\cleanmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Disk Space Cleanup Manager for Windows Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1128 | C:\Windows\system32\WerFault.exe -u -p 4092 -s 2100 | C:\Windows\system32\WerFault.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 3221226356 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1148 | "C:\Windows\System32\chglogon.exe" | C:\Windows\System32\chglogon.exe | — | wuapp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change Logon Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1420 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\dfsvc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\dfsvc.exe | — | reader_sl.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ClickOnce Exit code: 3221226356 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
Total events
8 130
Read events
2 640
Write events
5 472
Delete events
18
Modification events
| (PID) Process: | (3696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3696) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\BonzifyDONOTUSEONHOSTMANCHINE.zip | |||
| (PID) Process: | (3696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
15
Suspicious files
20
Text files
29
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 772 | WinRAR.exe | C:\Users\admin\Desktop\BonzifyDONOTUSEONHOSTMANCHINE\Bonzify.exe | executable | |
MD5:— | SHA256:— | |||
| 772 | WinRAR.exe | C:\Users\admin\Desktop\BonzifyDONOTUSEONHOSTMANCHINE\HookDLL.ipdb | binary | |
MD5:— | SHA256:— | |||
| 772 | WinRAR.exe | C:\Users\admin\Desktop\BonzifyDONOTUSEONHOSTMANCHINE\Bonzify.pdb | pdb | |
MD5:— | SHA256:— | |||
| 772 | WinRAR.exe | C:\Users\admin\Desktop\BonzifyDONOTUSEONHOSTMANCHINE\Bonzify.iobj | binary | |
MD5:— | SHA256:— | |||
| 3820 | INSTALLER.exe | C:\Windows\lhsp\tv\SETE75F.tmp | — | |
MD5:— | SHA256:— | |||
| 772 | WinRAR.exe | C:\Users\admin\Desktop\BonzifyDONOTUSEONHOSTMANCHINE\HookDLL.iobj | binary | |
MD5:— | SHA256:— | |||
| 3820 | INSTALLER.exe | C:\Windows\lhsp\tv\SETE770.tmp | — | |
MD5:— | SHA256:— | |||
| 772 | WinRAR.exe | C:\Users\admin\Desktop\BonzifyDONOTUSEONHOSTMANCHINE\HookDLL.pdb | pdb | |
MD5:— | SHA256:— | |||
| 3820 | INSTALLER.exe | C:\Windows\lhsp\help\SETE781.tmp | — | |
MD5:— | SHA256:— | |||
| 772 | WinRAR.exe | C:\Users\admin\Desktop\BonzifyDONOTUSEONHOSTMANCHINE\HookDLL.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|