| URL: | workupload.com/start/E4VWXP2qu96 |
| Full analysis: | https://app.any.run/tasks/7558bc19-297e-4d5e-a688-88c56d877799 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | May 02, 2025, 20:13:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C0B4202036DF27C3A5A9F62A72607382 |
| SHA1: | 792B614CDB33EC01B50B1E83C5B427313EF69F65 |
| SHA256: | 255653AD65DB7BF89444572FC68908FCCE514DF103CA015F1B83BC72F829F086 |
| SSDEEP: | 3:J+ZDo:JQDo |
MALICIOUS
Vulnerable driver has been detected
- WinRAR.exe (PID: 8556)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 7208)
DCRAT mutex has been found
- mshyperComProviderDll.exe (PID: 7640)
Connects to the CnC server
- mshyperComProviderDll.exe (PID: 7304)
- mshyperComProviderDll.exe (PID: 5936)
- mshyperComProviderDll.exe (PID: 5164)
- mshyperComProviderDll.exe (PID: 9160)
- mshyperComProviderDll.exe (PID: 7244)
- mshyperComProviderDll.exe (PID: 7428)
- mshyperComProviderDll.exe (PID: 8288)
- mshyperComProviderDll.exe (PID: 9208)
- mshyperComProviderDll.exe (PID: 4572)
- mshyperComProviderDll.exe (PID: 2392)
- mshyperComProviderDll.exe (PID: 3828)
- mshyperComProviderDll.exe (PID: 8508)
- mshyperComProviderDll.exe (PID: 3016)
DARKCRYSTAL has been detected (SURICATA)
- mshyperComProviderDll.exe (PID: 5936)
- mshyperComProviderDll.exe (PID: 7304)
- mshyperComProviderDll.exe (PID: 7244)
- mshyperComProviderDll.exe (PID: 9160)
- mshyperComProviderDll.exe (PID: 5164)
- mshyperComProviderDll.exe (PID: 7428)
- mshyperComProviderDll.exe (PID: 4572)
- mshyperComProviderDll.exe (PID: 8288)
- mshyperComProviderDll.exe (PID: 9208)
- mshyperComProviderDll.exe (PID: 2392)
- mshyperComProviderDll.exe (PID: 3828)
- mshyperComProviderDll.exe (PID: 3016)
- mshyperComProviderDll.exe (PID: 8508)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 8556)
Process drops legitimate windows executable
- WinRAR.exe (PID: 8556)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 8556)
- mshyperComProviderDll.exe (PID: 7640)
Reads security settings of Internet Explorer
- WebRat Crack.exe (PID: 6004)
- WebRat Crack.exe (PID: 5936)
- WebRat Crack.exe (PID: 6192)
- WebRat Crack.exe (PID: 8792)
Executable content was dropped or overwritten
- WebRat Crack.exe (PID: 6004)
- mshyperComProviderDll.exe (PID: 7640)
- mshyperComProviderDll.exe (PID: 7304)
- mshyperComProviderDll.exe (PID: 5936)
- mshyperComProviderDll.exe (PID: 7244)
- mshyperComProviderDll.exe (PID: 5164)
- mshyperComProviderDll.exe (PID: 9160)
- mshyperComProviderDll.exe (PID: 4572)
- mshyperComProviderDll.exe (PID: 7428)
- mshyperComProviderDll.exe (PID: 9208)
- mshyperComProviderDll.exe (PID: 2392)
- mshyperComProviderDll.exe (PID: 8288)
- mshyperComProviderDll.exe (PID: 3828)
- mshyperComProviderDll.exe (PID: 3016)
- mshyperComProviderDll.exe (PID: 8508)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7208)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 7208)
- mshyperComProviderDll.exe (PID: 7640)
- wscript.exe (PID: 5416)
- mshyperComProviderDll.exe (PID: 7304)
- mshyperComProviderDll.exe (PID: 5936)
- wscript.exe (PID: 2236)
- wscript.exe (PID: 6132)
- mshyperComProviderDll.exe (PID: 7244)
- mshyperComProviderDll.exe (PID: 5164)
- mshyperComProviderDll.exe (PID: 9160)
- mshyperComProviderDll.exe (PID: 7428)
- mshyperComProviderDll.exe (PID: 9208)
- mshyperComProviderDll.exe (PID: 8288)
- mshyperComProviderDll.exe (PID: 3828)
- mshyperComProviderDll.exe (PID: 3016)
- mshyperComProviderDll.exe (PID: 2392)
- wscript.exe (PID: 8636)
- mshyperComProviderDll.exe (PID: 8508)
- mshyperComProviderDll.exe (PID: 4572)
Executing commands from a ".bat" file
- wscript.exe (PID: 7208)
- mshyperComProviderDll.exe (PID: 7640)
- wscript.exe (PID: 5416)
- mshyperComProviderDll.exe (PID: 7304)
- wscript.exe (PID: 6132)
- mshyperComProviderDll.exe (PID: 5936)
- mshyperComProviderDll.exe (PID: 7244)
- wscript.exe (PID: 2236)
- mshyperComProviderDll.exe (PID: 5164)
- mshyperComProviderDll.exe (PID: 9160)
- mshyperComProviderDll.exe (PID: 7428)
- mshyperComProviderDll.exe (PID: 4572)
- mshyperComProviderDll.exe (PID: 9208)
- mshyperComProviderDll.exe (PID: 8288)
- mshyperComProviderDll.exe (PID: 3828)
- mshyperComProviderDll.exe (PID: 3016)
- mshyperComProviderDll.exe (PID: 2392)
- wscript.exe (PID: 8636)
- mshyperComProviderDll.exe (PID: 8508)
Executed via WMI
- schtasks.exe (PID: 6872)
- schtasks.exe (PID: 6028)
- schtasks.exe (PID: 8384)
- schtasks.exe (PID: 5544)
- schtasks.exe (PID: 8372)
- schtasks.exe (PID: 6540)
- schtasks.exe (PID: 4380)
- schtasks.exe (PID: 8568)
- schtasks.exe (PID: 7000)
- schtasks.exe (PID: 9152)
- schtasks.exe (PID: 8932)
- schtasks.exe (PID: 7432)
- schtasks.exe (PID: 904)
- schtasks.exe (PID: 8180)
- schtasks.exe (PID: 1748)
- schtasks.exe (PID: 4692)
- schtasks.exe (PID: 6272)
- schtasks.exe (PID: 9180)
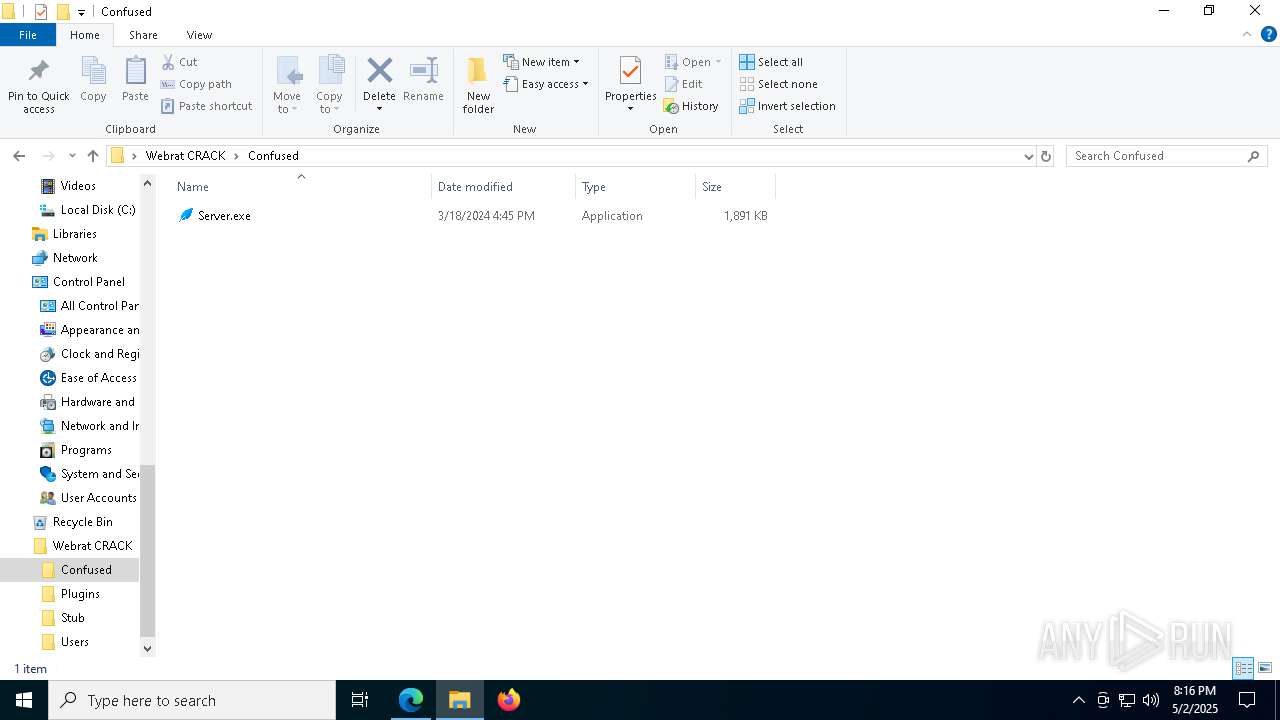
Executes application which crashes
- Server.exe (PID: 8168)
- Server.exe (PID: 8168)
Starts application with an unusual extension
- cmd.exe (PID: 9036)
- cmd.exe (PID: 7824)
- cmd.exe (PID: 6072)
- cmd.exe (PID: 684)
- cmd.exe (PID: 3024)
- cmd.exe (PID: 1660)
- cmd.exe (PID: 8008)
- cmd.exe (PID: 5308)
- cmd.exe (PID: 1328)
- cmd.exe (PID: 4376)
- cmd.exe (PID: 4024)
- cmd.exe (PID: 6892)
- cmd.exe (PID: 2284)
- cmd.exe (PID: 920)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 9036)
- cmd.exe (PID: 684)
- cmd.exe (PID: 1660)
- cmd.exe (PID: 4376)
- cmd.exe (PID: 1328)
- cmd.exe (PID: 4024)
- cmd.exe (PID: 6892)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 7824)
- cmd.exe (PID: 6072)
- cmd.exe (PID: 3024)
- cmd.exe (PID: 8008)
- cmd.exe (PID: 5308)
- cmd.exe (PID: 2284)
- cmd.exe (PID: 920)
INFO
Checks supported languages
- identity_helper.exe (PID: 8992)
- WebRat Crack.exe (PID: 6004)
- WebRat Crack.exe (PID: 5936)
- WebRat Crack.exe (PID: 6192)
- WebRat Crack.exe (PID: 8792)
- mshyperComProviderDll.exe (PID: 7640)
- Server.exe (PID: 8168)
Application launched itself
- msedge.exe (PID: 7456)
The sample compiled with english language support
- WinRAR.exe (PID: 8556)
- msedge.exe (PID: 8804)
Reads the computer name
- identity_helper.exe (PID: 8992)
- WebRat Crack.exe (PID: 6004)
- WebRat Crack.exe (PID: 5936)
- WebRat Crack.exe (PID: 6192)
- WebRat Crack.exe (PID: 8792)
- mshyperComProviderDll.exe (PID: 7640)
- Server.exe (PID: 8168)
The sample compiled with japanese language support
- WinRAR.exe (PID: 8556)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8556)
- msedge.exe (PID: 8804)
Drops encrypted VBS script (Microsoft Script Encoder)
- WebRat Crack.exe (PID: 6004)
Reads Environment values
- identity_helper.exe (PID: 8992)
- mshyperComProviderDll.exe (PID: 7640)
Reads Microsoft Office registry keys
- msedge.exe (PID: 7456)
Manual execution by a user
- WebRat Crack.exe (PID: 5936)
- WebRat Crack.exe (PID: 6004)
- WebRat Crack.exe (PID: 6192)
- WebRat Crack.exe (PID: 8792)
- Server.exe (PID: 8168)
- WebRat Crack.exe (PID: 8560)
- adb(dont open).exe (PID: 5600)
- Server.exe (PID: 8168)
- Taskmgr.exe (PID: 4736)
- Taskmgr.exe (PID: 2096)
Process checks computer location settings
- WebRat Crack.exe (PID: 6004)
- WebRat Crack.exe (PID: 5936)
- WebRat Crack.exe (PID: 6192)
- WebRat Crack.exe (PID: 8792)
Reads the software policy settings
- slui.exe (PID: 8776)
Reads the machine GUID from the registry
- mshyperComProviderDll.exe (PID: 7640)
Creates files in the program directory
- mshyperComProviderDll.exe (PID: 7640)
Failed to create an executable file in Windows directory
- mshyperComProviderDll.exe (PID: 7640)
Changes the display of characters in the console
- cmd.exe (PID: 9036)
- cmd.exe (PID: 7824)
- cmd.exe (PID: 6072)
- cmd.exe (PID: 1660)
- cmd.exe (PID: 3024)
- cmd.exe (PID: 684)
- cmd.exe (PID: 8008)
- cmd.exe (PID: 5308)
- cmd.exe (PID: 1328)
- cmd.exe (PID: 4376)
- cmd.exe (PID: 4024)
- cmd.exe (PID: 6892)
- cmd.exe (PID: 920)
- cmd.exe (PID: 2284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
332
Monitored processes
191
Malicious processes
33
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 684 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\TtX0d4fx4d.bat" " | C:\Windows\System32\cmd.exe | — | mshyperComProviderDll.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | ping -n 10 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | schtasks.exe /create /tn "mshyperComProviderDllm" /sc MINUTE /mo 6 /tr "'C:\ContainerSvc\mshyperComProviderDll.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=7332 --field-trial-handle=2344,i,12752820536351715490,5972446446488561167,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 920 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\hyKfCYp7HR.bat" " | C:\Windows\System32\cmd.exe | — | mshyperComProviderDll.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=7912 --field-trial-handle=2344,i,12752820536351715490,5972446446488561167,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
45 724
Read events
45 654
Write events
69
Delete events
1
Modification events
| (PID) Process: | (7456) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7456) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7456) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7456) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7456) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 60EE3411C3922F00 | |||
| (PID) Process: | (7456) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 0C4A3D11C3922F00 | |||
| (PID) Process: | (7456) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262924 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {FF7EF464-8886-46A2-9284-F2826B062585} | |||
| (PID) Process: | (7456) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262924 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {67B9398D-A1CF-4871-879A-9E5E1C716481} | |||
| (PID) Process: | (7456) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262924 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {D9B059EF-696E-4035-A03F-B021F07204CE} | |||
| (PID) Process: | (7456) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262924 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {6487E2E4-5880-4C92-8CC4-51181698265F} | |||
Executable files
139
Suspicious files
491
Text files
112
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10b344.TMP | — | |
MD5:— | SHA256:— | |||
| 7456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10b344.TMP | — | |
MD5:— | SHA256:— | |||
| 7456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10b344.TMP | — | |
MD5:— | SHA256:— | |||
| 7456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10b344.TMP | — | |
MD5:— | SHA256:— | |||
| 7456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10b354.TMP | — | |
MD5:— | SHA256:— | |||
| 7456 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
67
TCP/UDP connections
190
DNS requests
132
Threats
27
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
9108 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5304 | svchost.exe | HEAD | 200 | 208.89.74.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1746654483&P2=404&P3=2&P4=hN%2fof0R3pyfqSpftDCDU%2bh0dNFZxIt0oPnOUoCK5%2bN%2bD%2fdqe9t%2fN1MNdWH1eQCHIhZoqMEu%2b9K5LQPisHgfhwQ%3d%3d | unknown | — | — | whitelisted |
5304 | svchost.exe | GET | 206 | 208.89.74.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1746654483&P2=404&P3=2&P4=hN%2fof0R3pyfqSpftDCDU%2bh0dNFZxIt0oPnOUoCK5%2bN%2bD%2fdqe9t%2fN1MNdWH1eQCHIhZoqMEu%2b9K5LQPisHgfhwQ%3d%3d | unknown | — | — | whitelisted |
5304 | svchost.exe | GET | 206 | 208.89.74.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1746654483&P2=404&P3=2&P4=hN%2fof0R3pyfqSpftDCDU%2bh0dNFZxIt0oPnOUoCK5%2bN%2bD%2fdqe9t%2fN1MNdWH1eQCHIhZoqMEu%2b9K5LQPisHgfhwQ%3d%3d | unknown | — | — | whitelisted |
5304 | svchost.exe | HEAD | 200 | 208.89.74.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1746650883&P2=404&P3=2&P4=G7uQneuS%2bnkVtVFfDMyFWT0OOGxCIuHhniAteDRSbJJJ6bFpJ0Sbth7N2a8hDjnVRJ4DlfsL3d%2bM52VjFfYI3Q%3d%3d | unknown | — | — | whitelisted |
5304 | svchost.exe | GET | 206 | 208.89.74.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1746650883&P2=404&P3=2&P4=G7uQneuS%2bnkVtVFfDMyFWT0OOGxCIuHhniAteDRSbJJJ6bFpJ0Sbth7N2a8hDjnVRJ4DlfsL3d%2bM52VjFfYI3Q%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7732 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7456 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7732 | msedge.exe | 193.111.198.24:80 | workupload.com | myLoc managed IT AG | DE | whitelisted |
7732 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
workupload.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected Domain Associated with Malware Distribution (nyashware .ru) |
7304 | mshyperComProviderDll.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
7304 | mshyperComProviderDll.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
5936 | mshyperComProviderDll.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
5936 | mshyperComProviderDll.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
7244 | mshyperComProviderDll.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
7244 | mshyperComProviderDll.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
5164 | mshyperComProviderDll.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
5164 | mshyperComProviderDll.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
9160 | mshyperComProviderDll.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |