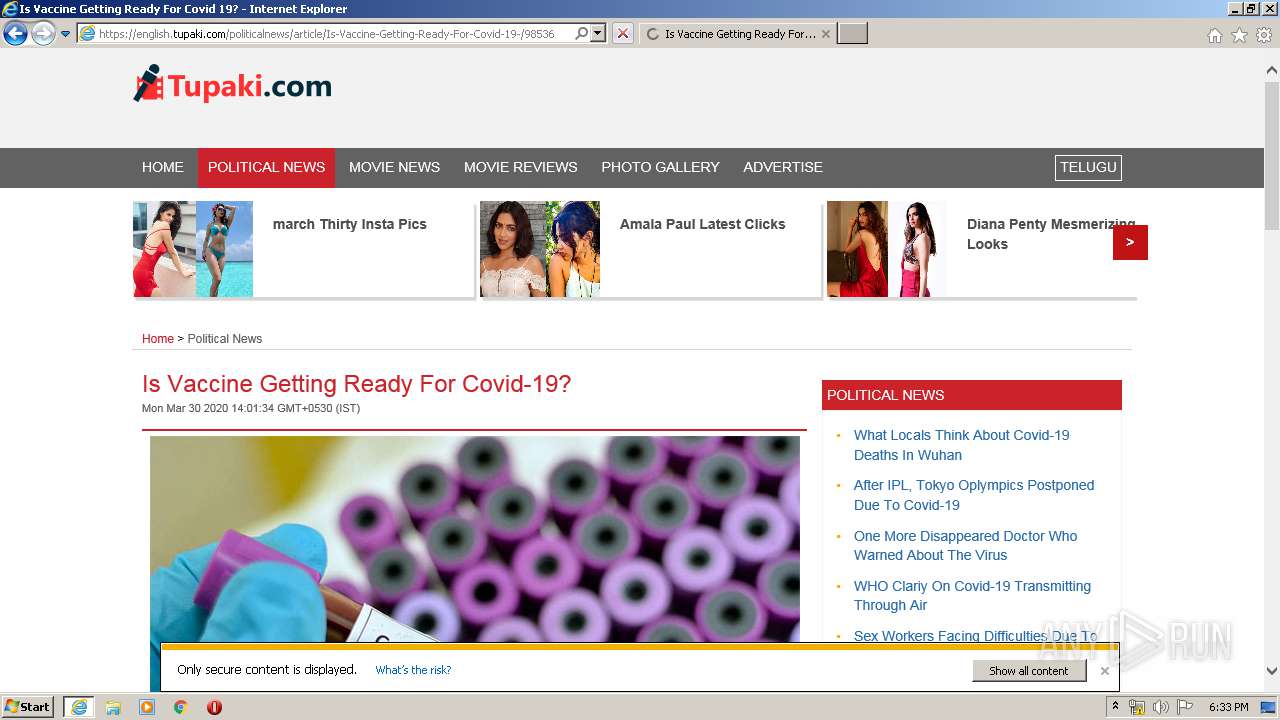
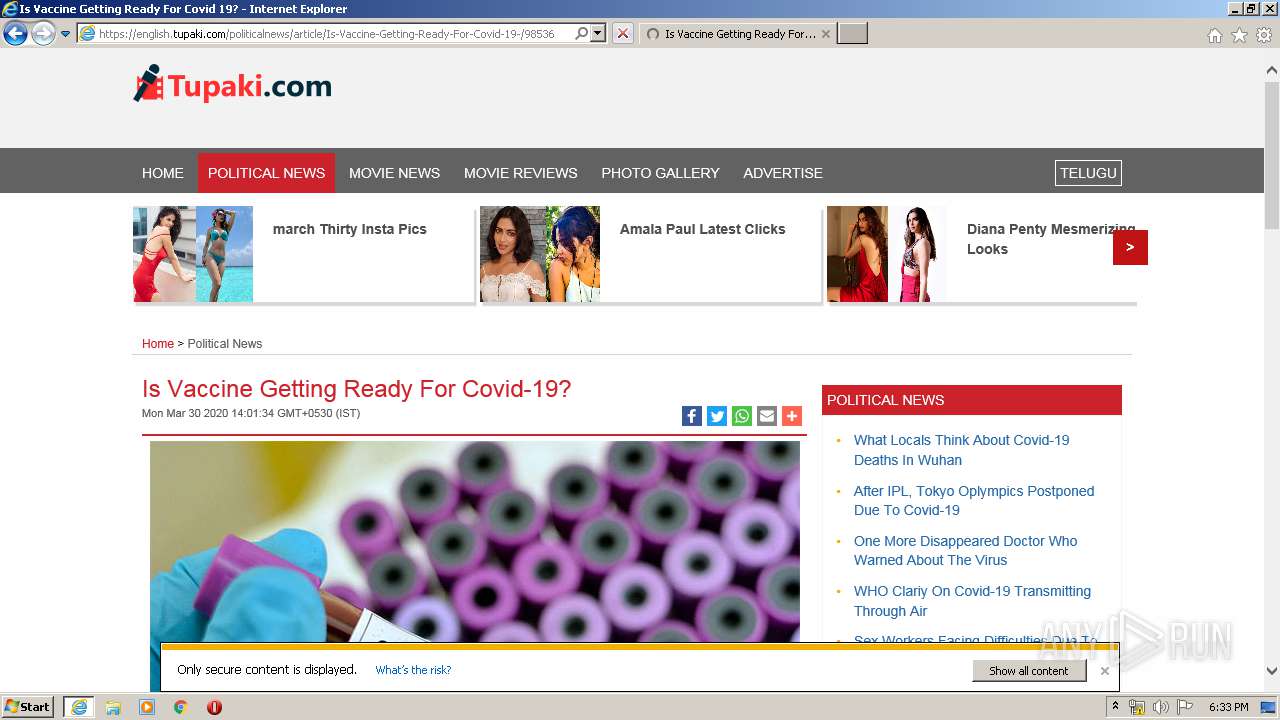
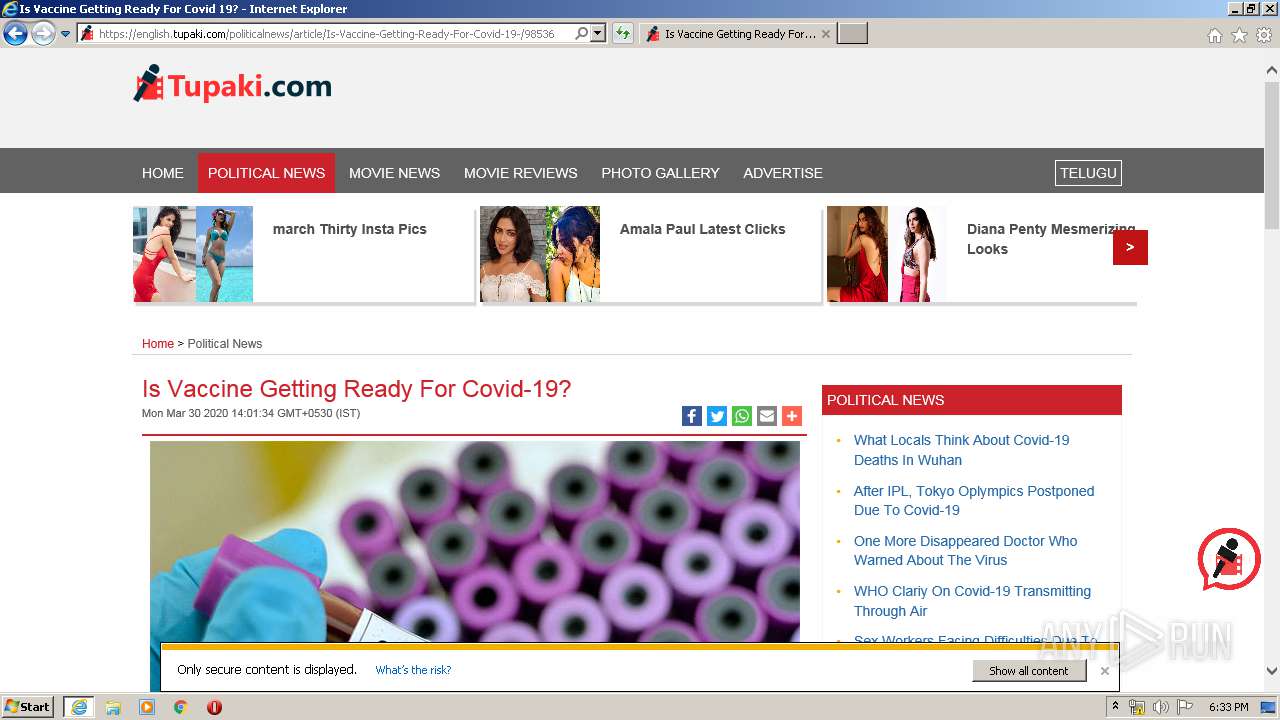
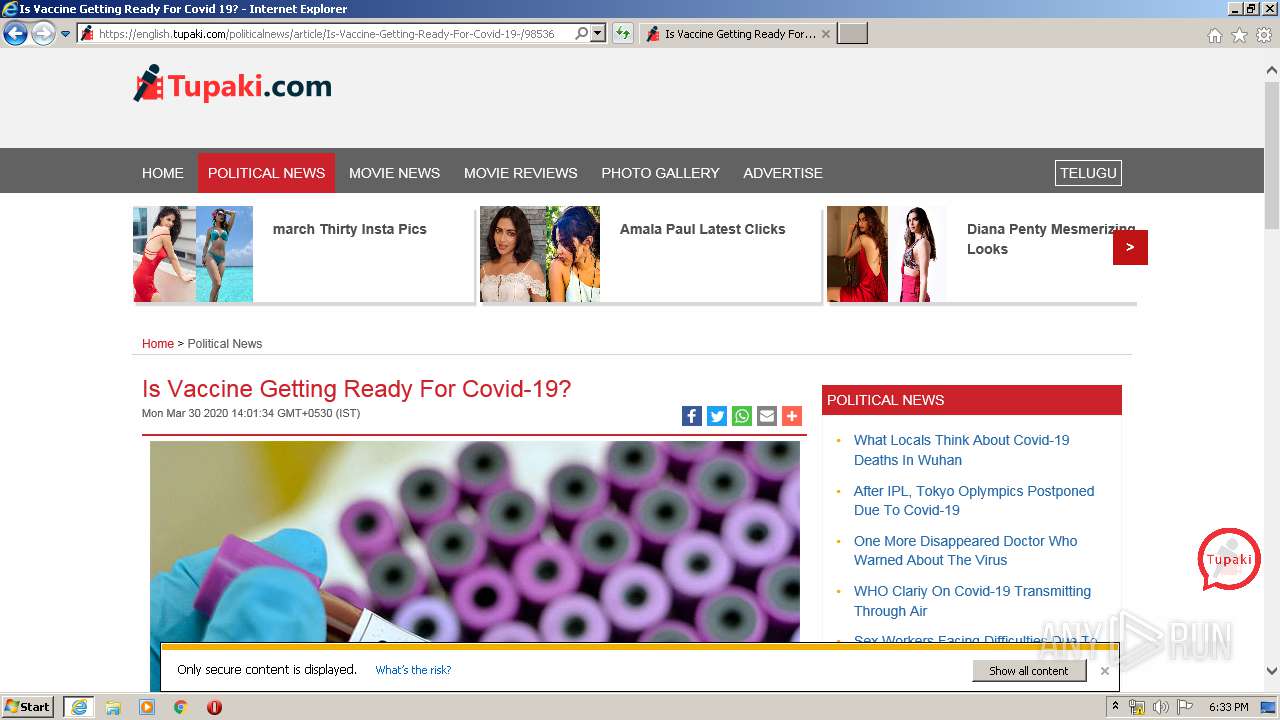
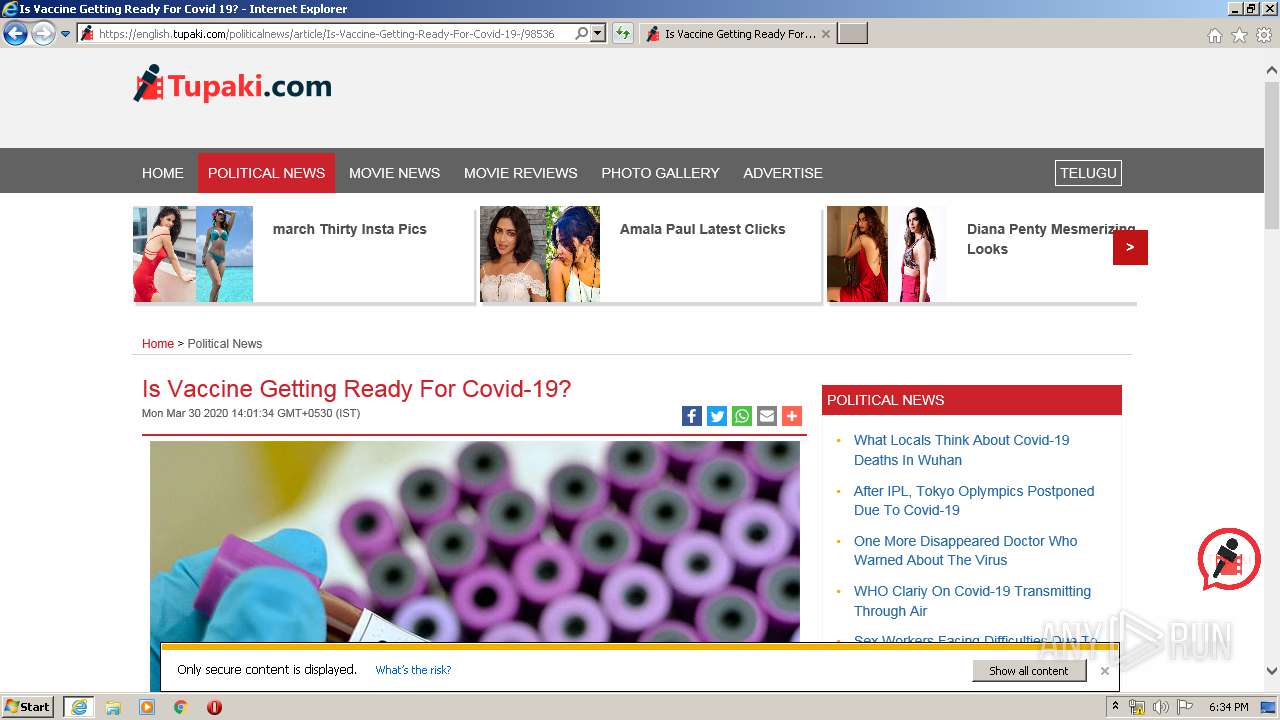
| URL: | http://www.google.com |
| Full analysis: | https://app.any.run/tasks/bb3145b9-e979-486e-8c10-8bba76fd83ac |
| Verdict: | Malicious activity |
| Analysis date: | March 30, 2020, 17:32:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | ED646A3334CA891FD3467DB131372140 |
| SHA1: | 738DDF35B3A85A7A6BA7B232BD3D5F1E4D284AD1 |
| SHA256: | 253D142703041DD25197550A0FC11D6AC03BEFC1E64A1320009F1EDF400C39AD |
| SSDEEP: | 3:N1KJS4IK:Cc4IK |
MALICIOUS
Connects to CnC server
- iexplore.exe (PID: 3864)
SUSPICIOUS
No suspicious indicators.INFO
Changes internet zones settings
- iexplore.exe (PID: 2192)
Reads Internet Cache Settings
- iexplore.exe (PID: 3864)
- iexplore.exe (PID: 2192)
Reads internet explorer settings
- iexplore.exe (PID: 3864)
Reads settings of System Certificates
- iexplore.exe (PID: 3864)
- iexplore.exe (PID: 2192)
Drops Coronavirus (possible) decoy
- iexplore.exe (PID: 3864)
Creates files in the user directory
- iexplore.exe (PID: 3864)
- iexplore.exe (PID: 2192)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3864)
Dropped object may contain TOR URL's
- iexplore.exe (PID: 3864)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2192)
Changes settings of System certificates
- iexplore.exe (PID: 2192)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://www.google.com" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3864 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2192 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
5 093
Read events
397
Write events
3 195
Delete events
1 501
Modification events
| (PID) Process: | (2192) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 1431704014 | |||
| (PID) Process: | (2192) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30803641 | |||
| (PID) Process: | (2192) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2192) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2192) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2192) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2192) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2192) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2192) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2192) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
111
Text files
227
Unknown types
48
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3864 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab6FE9.tmp | — | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar6FEA.tmp | — | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\1UAOJV3W.txt | — | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\453HF2UZ.txt | — | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\8QU1CQCK.txt | text | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\TKP7DMNH.txt | — | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\4V3RLV70.txt | — | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\8RNFF1Z0.txt | — | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\PXKWO8KA.txt | — | |
MD5:— | SHA256:— | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\25GWRYP3.txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
61
TCP/UDP connections
175
DNS requests
71
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3864 | iexplore.exe | GET | 204 | 88.99.151.223:80 | http://cdn-javascript.net/api?key=a1ce18e5e2b4b1b1895a38130270d6d344d031c0&uid=8875x&format=arrjs&r=1585557295514 | DE | — | — | malicious |
3864 | iexplore.exe | GET | 200 | 104.27.182.185:80 | http://peterjonny.com/optout/set/lat?jsonp=__mtz_cb_634479511&key=22ab99ef5bc624cbd8&cv=1585557294&t=1585557294320 | US | — | — | malicious |
3864 | iexplore.exe | GET | 200 | 104.27.182.185:80 | http://peterjonny.com/ext/22ab99ef5bc624cbd8.js?sid=52679_8875_&title=ss&blocks[]=31af2 | US | text | 3.39 Kb | malicious |
3864 | iexplore.exe | GET | 200 | 172.217.23.131:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
3864 | iexplore.exe | GET | 200 | 172.217.23.131:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQD7nI1BmOkYLAgAAAAAMgsX | US | der | 472 b | whitelisted |
3864 | iexplore.exe | GET | 200 | 172.217.23.131:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQD7nI1BmOkYLAgAAAAAMgsX | US | der | 472 b | whitelisted |
2192 | iexplore.exe | GET | 200 | 72.21.91.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3864 | iexplore.exe | GET | 200 | 172.217.23.131:80 | http://ocsp.pki.goog/gts1o1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEGFA%2F%2Fi5YNGTCAAAAAAyCrg%3D | US | der | 471 b | whitelisted |
2192 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3864 | iexplore.exe | GET | 200 | 172.217.23.131:80 | http://ocsp.pki.goog/gts1o1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEC4G%2Bv2mHN8jAgAAAABcZ3g%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3864 | iexplore.exe | 172.217.23.110:443 | consent.google.com | Google Inc. | US | whitelisted |
3864 | iexplore.exe | 216.58.206.3:443 | www.google.dk | Google Inc. | US | whitelisted |
3864 | iexplore.exe | 216.58.210.14:443 | apis.google.com | Google Inc. | US | whitelisted |
2192 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3864 | iexplore.exe | 172.217.16.142:443 | ogs.google.com | Google Inc. | US | whitelisted |
2192 | iexplore.exe | 172.217.22.68:443 | — | Google Inc. | US | whitelisted |
3864 | iexplore.exe | 172.217.16.162:443 | adservice.google.com | Google Inc. | US | whitelisted |
2192 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2192 | iexplore.exe | 72.21.91.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2192 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| malicious |
ocsp.pki.goog |
| whitelisted |
consent.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
www.google.dk |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3864 | iexplore.exe | A Network Trojan was detected | ET MALWARE LNKR CnC Activity M1 |
3864 | iexplore.exe | A Network Trojan was detected | ET MALWARE LNKR CnC Activity M3 |
3864 | iexplore.exe | A Network Trojan was detected | ET MALWARE LNKR Possible Response for LNKR js file |