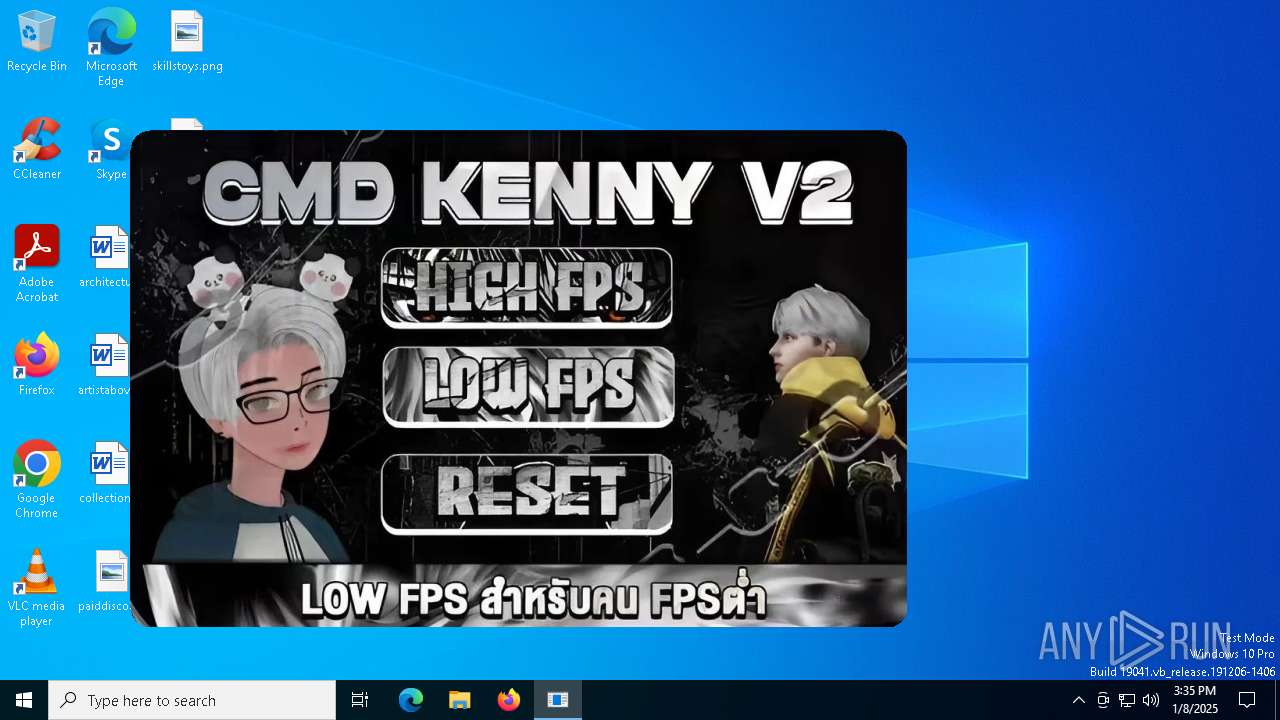
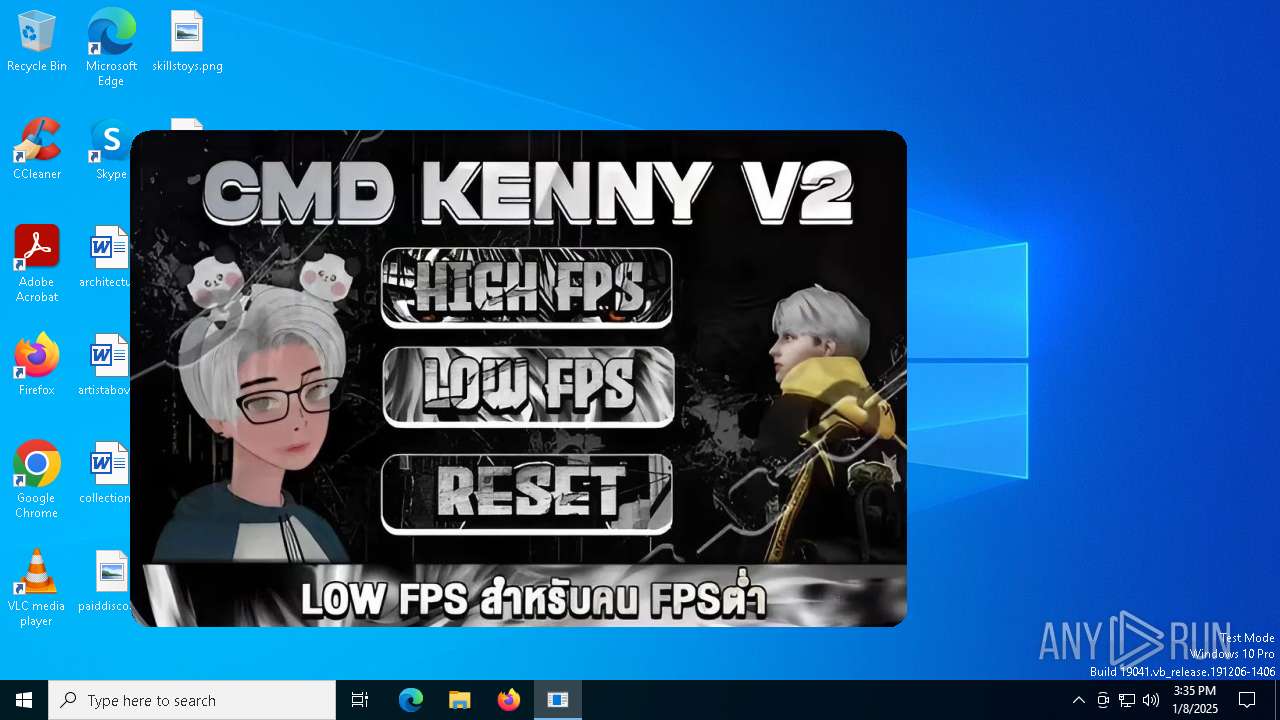
| File name: | KennyV2.exe |
| Full analysis: | https://app.any.run/tasks/3d099c6b-4151-41fb-9411-88a0b33e040f |
| Verdict: | Malicious activity |
| Analysis date: | January 08, 2025, 15:35:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows, 2 sections |
| MD5: | A960243F6E9D8DE8F5E52C6742B433F1 |
| SHA1: | 969BED7E860CB7088F4733B9890DA7E3E5FF33F3 |
| SHA256: | 25325BA782C27E4AED543BA4DC102C5B1B705A1A395EEDB674B1CE610349AECE |
| SSDEEP: | 12288:isaBQvvWxgzeFaXGoNUtiFOMGjYPKarHE:ba+vvWxgzeFaXGoNUgrGjYPKcHE |
MALICIOUS
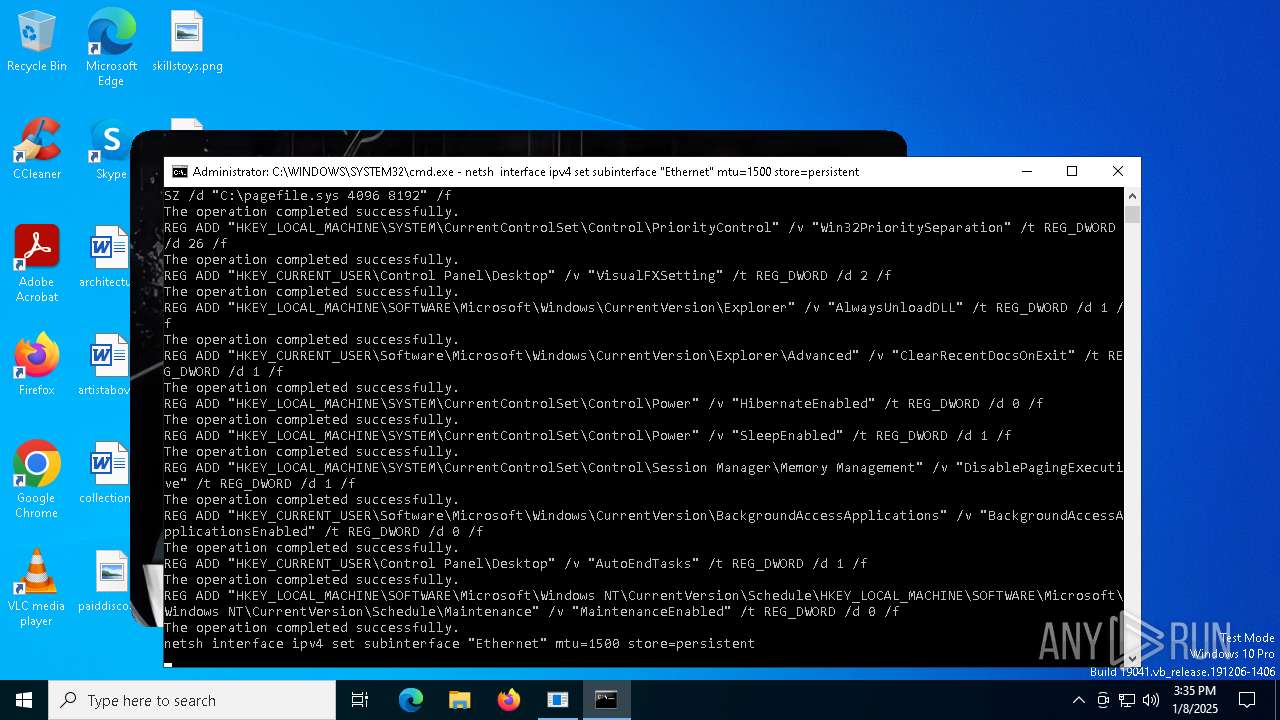
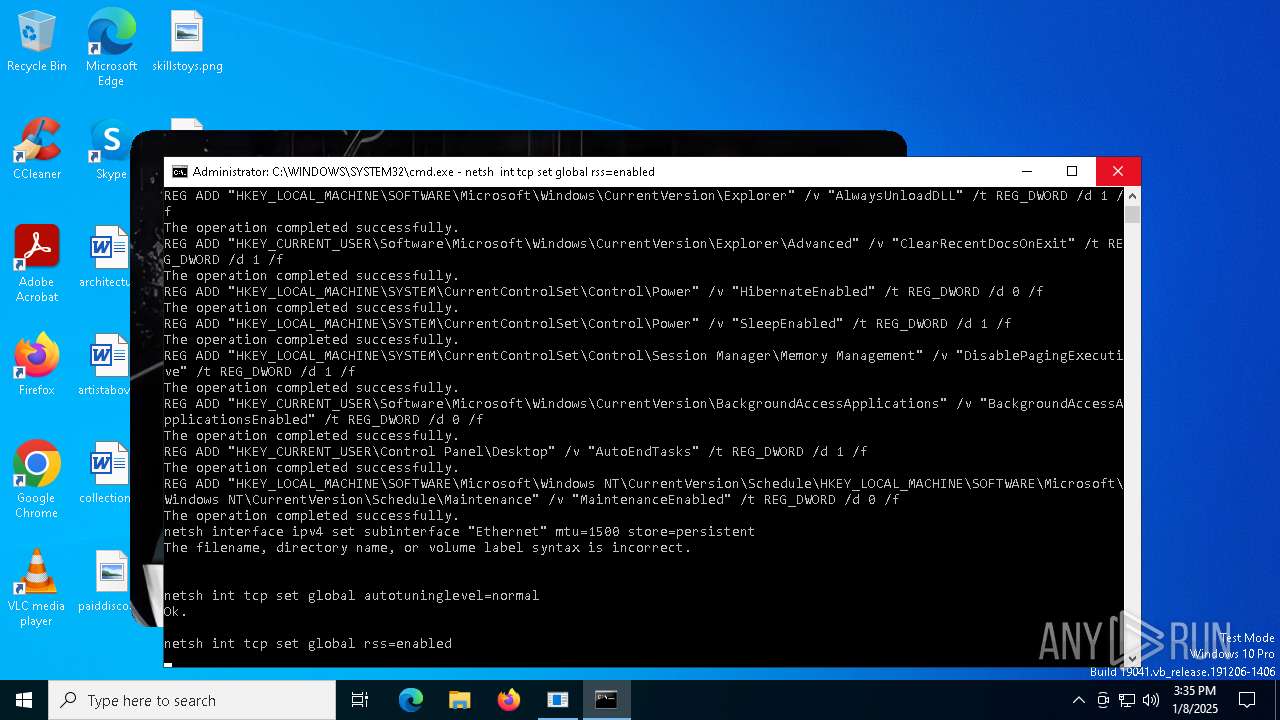
Changes the autorun value in the registry
- reg.exe (PID: 2164)
- reg.exe (PID: 556)
- reg.exe (PID: 4264)
SUSPICIOUS
Starts CMD.EXE for commands execution
- KennyV2.exe (PID: 6608)
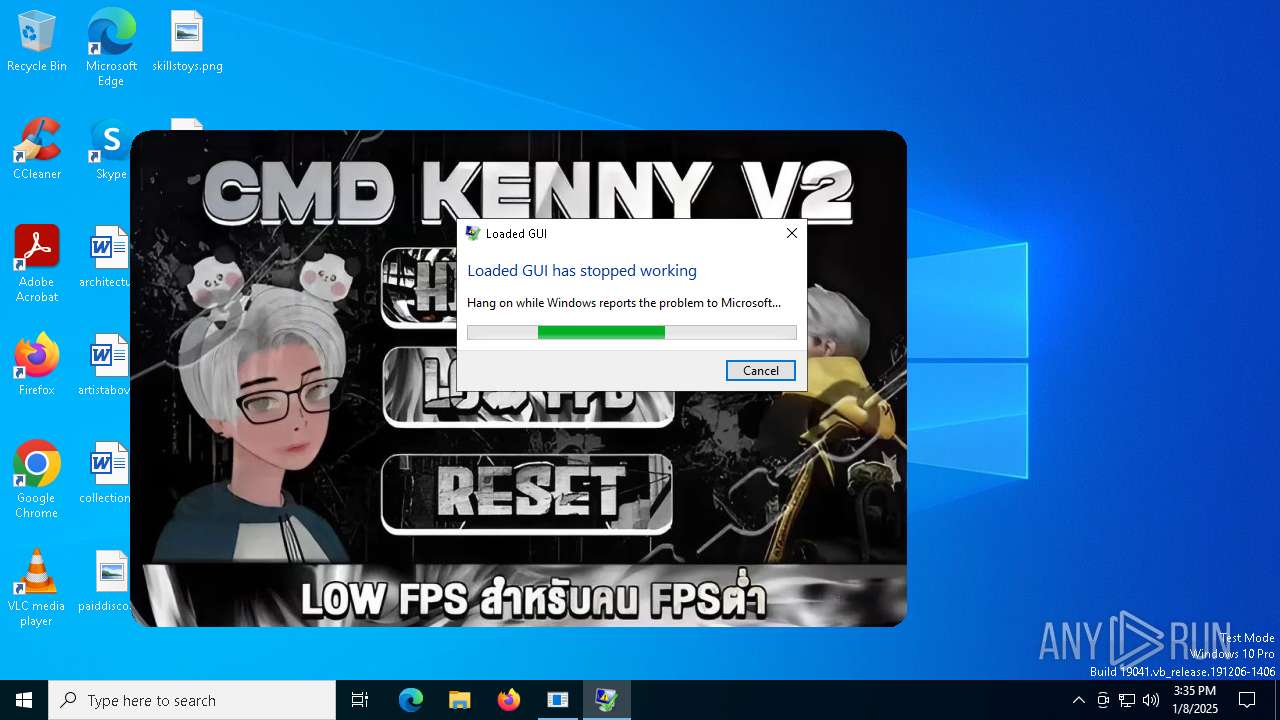
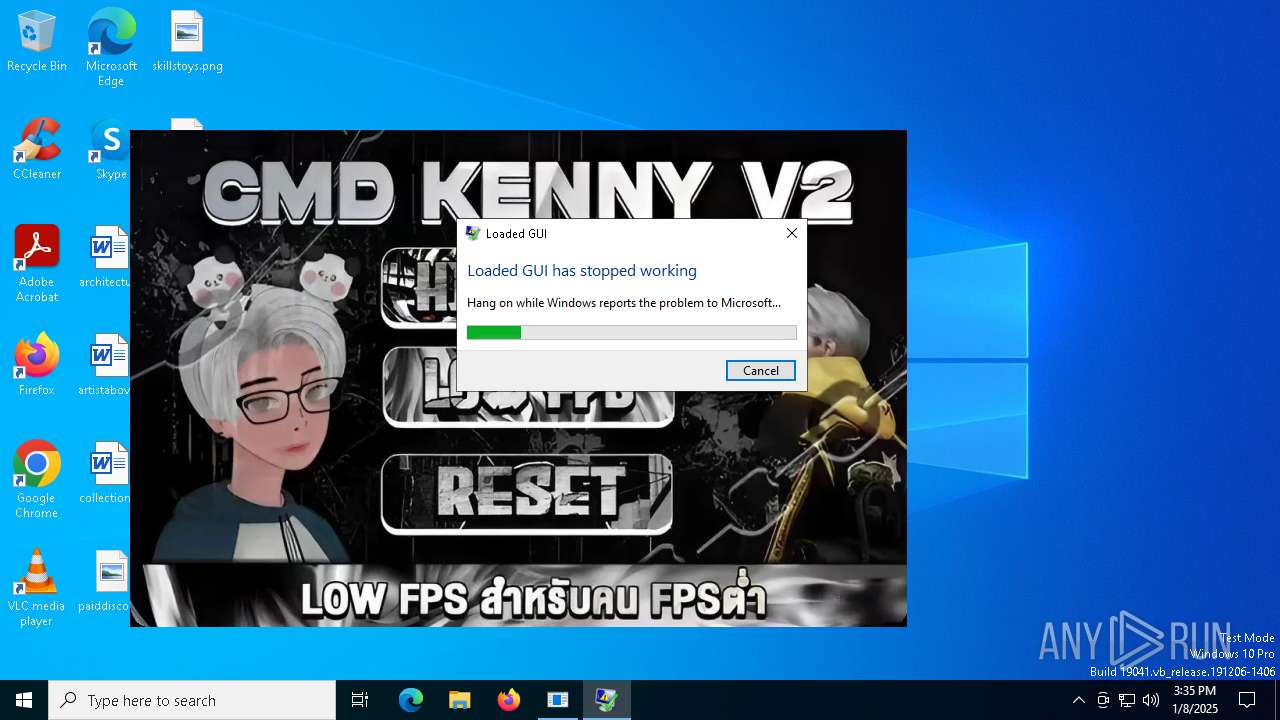
Executes application which crashes
- KennyV2.exe (PID: 6608)
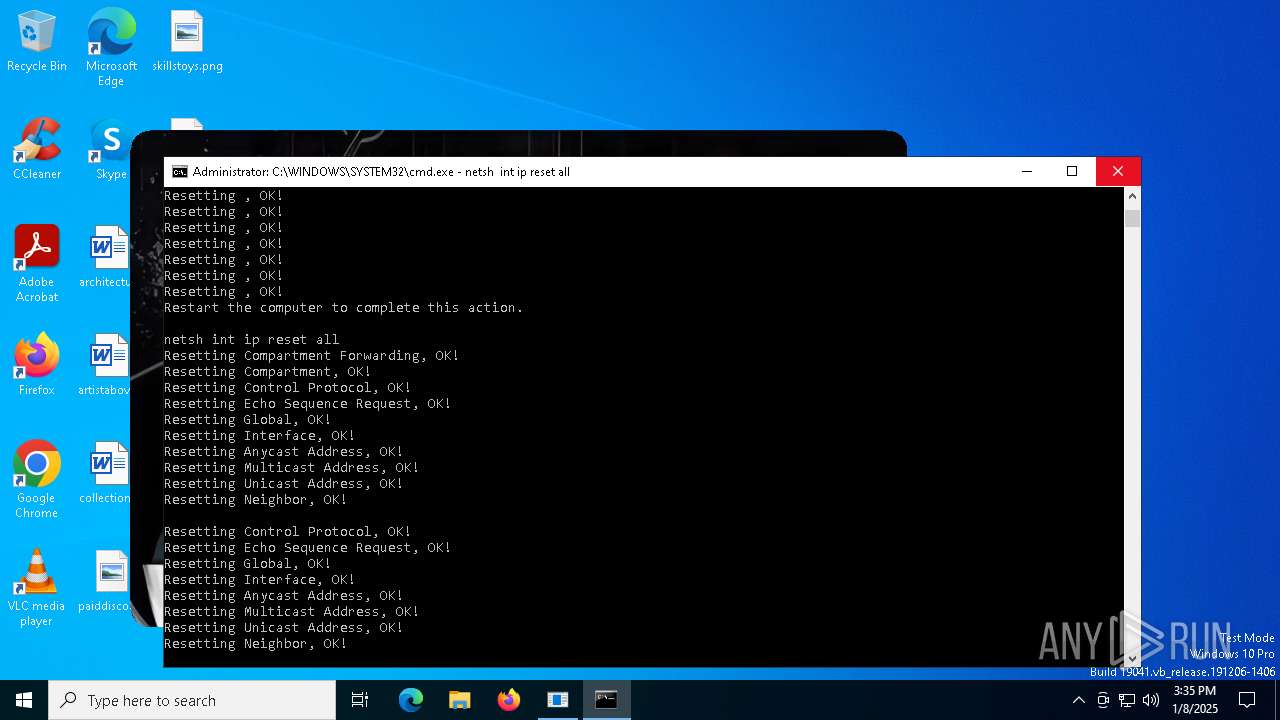
Suspicious use of NETSH.EXE
- cmd.exe (PID: 6828)
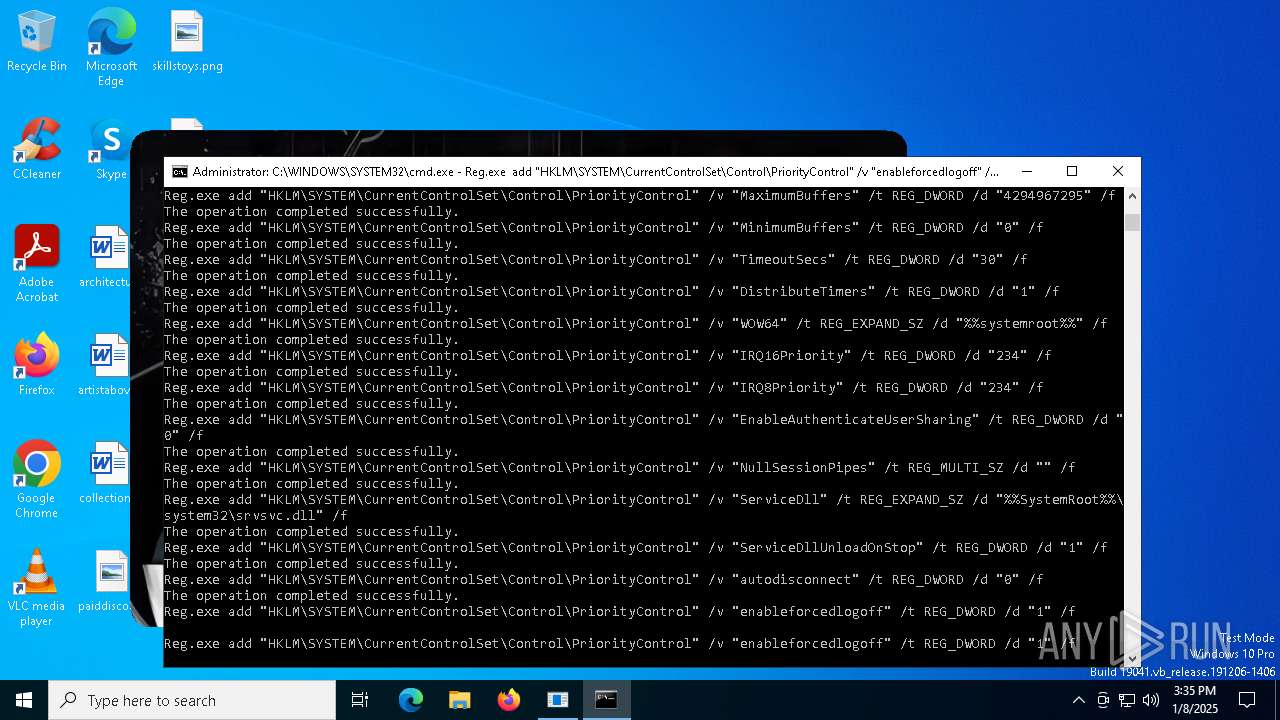
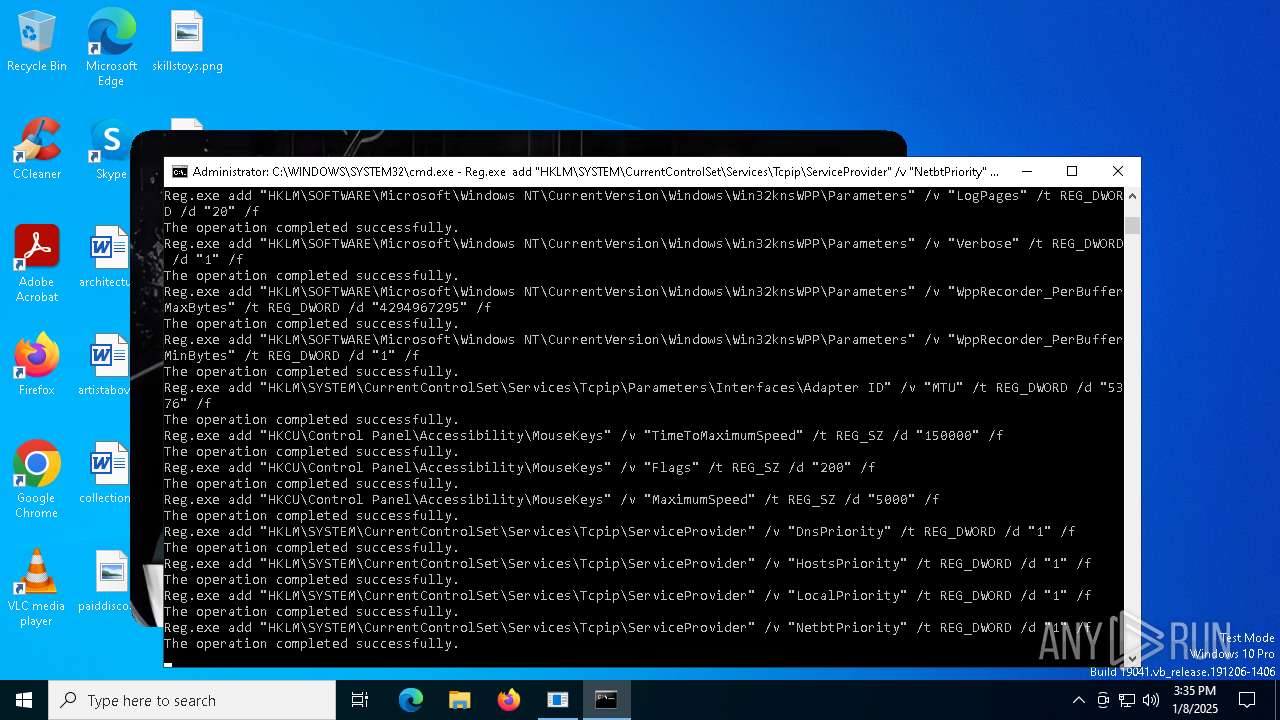
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6828)
INFO
Disables trace logs
- netsh.exe (PID: 3836)
- netsh.exe (PID: 6088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (81.9) |
|---|---|---|
| .exe | | | Win16/32 Executable Delphi generic (6.1) |
| .exe | | | Generic Win/DOS Executable (5.9) |
| .exe | | | DOS Executable Generic (5.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2060:03:24 03:57:46+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 48 |
| CodeSize: | 340480 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Loaded GUI |
| FileVersion: | 1.0.0.0 |
| InternalName: | Loaded GUI.exe |
| LegalCopyright: | Copyright © 2024 |
| LegalTrademarks: | - |
| OriginalFileName: | Loaded GUI.exe |
| ProductName: | Loaded GUI |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
234
Monitored processes
106
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 556 | Reg.exe add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\Win32knsWPP\Parameters" /v "ForceLogsInMiniDump" /t REG_DWORD /d "1" /f | C:\Windows\System32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 876 | Reg.exe add "HKLM\SYSTEM\CurrentControlSet\Control\PriorityControl" /v "enableforcedlogoff" /t REG_DWORD /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | Reg.exe add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\EventCollector\ConfigurationModes\Normal" /v "DeliveryMode" /t REG_SZ /d "Pull" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1512 | REG ADD "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Power" /v "HibernateEnabled" /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1580 | REG ADD "HKEY_CURRENT_USER\Control Panel\Desktop" /v "AutoEndTasks" /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1876 | Reg.exe add "HKLM\SYSTEM\CurrentControlSet\Control\PriorityControl" /v "TimeoutSecs" /t REG_DWORD /d "30" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2008 | netsh int ip reset all | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2072 | Reg.exe add "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\EventCollector\ConfigurationModes\Normal" /v "HeartBeatInterval" /t REG_DWORD /d "1000000000" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2164 | Reg.exe add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\Win32knsWPP\Parameters" /v "LogPages" /t REG_DWORD /d "20" /f | C:\Windows\System32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2324 | netsh int tcp set global rss=enabled | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 045
Read events
6 975
Write events
67
Delete events
3
Modification events
| (PID) Process: | (6972) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters |
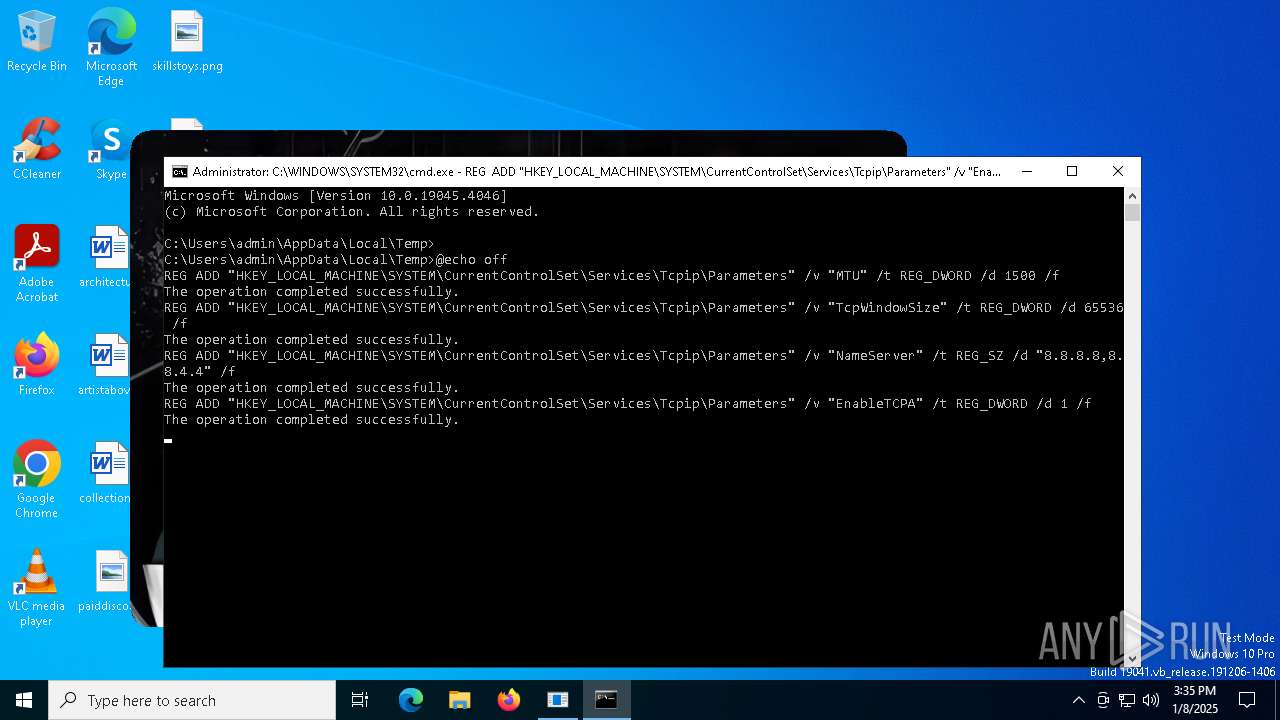
| Operation: | write | Name: | NameServer |
Value: 8.8.8.8,8.8.4.4 | |||
| (PID) Process: | (7020) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters |
| Operation: | write | Name: | EnableRSS |
Value: 1 | |||
| (PID) Process: | (7040) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters |
| Operation: | write | Name: | Tcp1323Opts |
Value: 3 | |||
| (PID) Process: | (7064) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters |
| Operation: | write | Name: | TcpChimney |
Value: 1 | |||
| (PID) Process: | (7148) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters |
| Operation: | write | Name: | TcpMaxHalfOpenRetried |
Value: 80 | |||
| (PID) Process: | (2972) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters |
| Operation: | write | Name: | EnableRSS |
Value: 1 | |||
| (PID) Process: | (6192) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Dnscache\Parameters |
| Operation: | write | Name: | MaxNegativeCacheTtl |
Value: 3600 | |||
| (PID) Process: | (6916) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters |
| Operation: | write | Name: | MTU |
Value: 1500 | |||
| (PID) Process: | (6944) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters |
| Operation: | write | Name: | TcpWindowSize |
Value: 65536 | |||
| (PID) Process: | (6992) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Tcpip\Parameters |
| Operation: | write | Name: | EnableTCPA |
Value: 1 | |||
Executable files
0
Suspicious files
1
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3736 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_KennyV2.exe_98a3124ff6df55a528eaee35b87d491ee87c7d75_dba95bfe_1d39ae1a-b510-4af7-900f-8cd209adeeb4\Report.wer | — | |
MD5:— | SHA256:— | |||
| 3736 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\KennyV2.exe.6608.dmp | — | |
MD5:— | SHA256:— | |||
| 3736 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER9020.tmp.xml | xml | |
MD5:294540200E0BE9E66523CE24D2513D09 | SHA256:B9F3E9262EAF4DD35FDE6711BF167D2BDEEAED61F14360626845E67D873367BC | |||
| 3736 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER8E68.tmp.dmp | dmp | |
MD5:5F64F9F1D01312B7E46E592778D7BC34 | SHA256:B54A200F9361BA7E81B77F14B607668BC77226CA1ABBA7C5882A5D504E63AE03 | |||
| 3736 | WerFault.exe | C:\Windows\appcompat\Programs\Amcache.hve | hiv | |
MD5:4F2BA0FA9206673600BB6E5A88503977 | SHA256:DF4701BAA9E9F56C01A14CF878D2912C7409B13C796B01B32C8444ADEFE35C23 | |||
| 3736 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER8FFF.tmp.WERInternalMetadata.xml | xml | |
MD5:196311E4608420FCB0E5C6D24842FBE8 | SHA256:0D02BC8A8FADAF07C309F5B59E6FBFDA9C535FCA3C7B136E6A81275A3A7DE1B8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
31
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6904 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6904 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
3464 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |