| File name: | 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe |
| Full analysis: | https://app.any.run/tasks/261d7dc6-741d-4036-8170-d7d1c919edcc |
| Verdict: | Malicious activity |
| Analysis date: | February 27, 2024, 03:55:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | C0B35F4104C86A49E25177941D7A7014 |
| SHA1: | 8E5DE6EF45FF073EA5C23177B12F40EC2B439FAD |
| SHA256: | 252C26A5EA749569E41B4CE291EA4FF21D08CA884123C8FF171433A359455033 |
| SSDEEP: | 24576:GmwvLvu1luK64OlT6IQERGhR4cAMY3/zZR+BBWiG4Xife9D2q0JRU519iIA0lWsF:GmwvLvu1luK64OlT6IQERG0cAMY3/zZW |
MALICIOUS
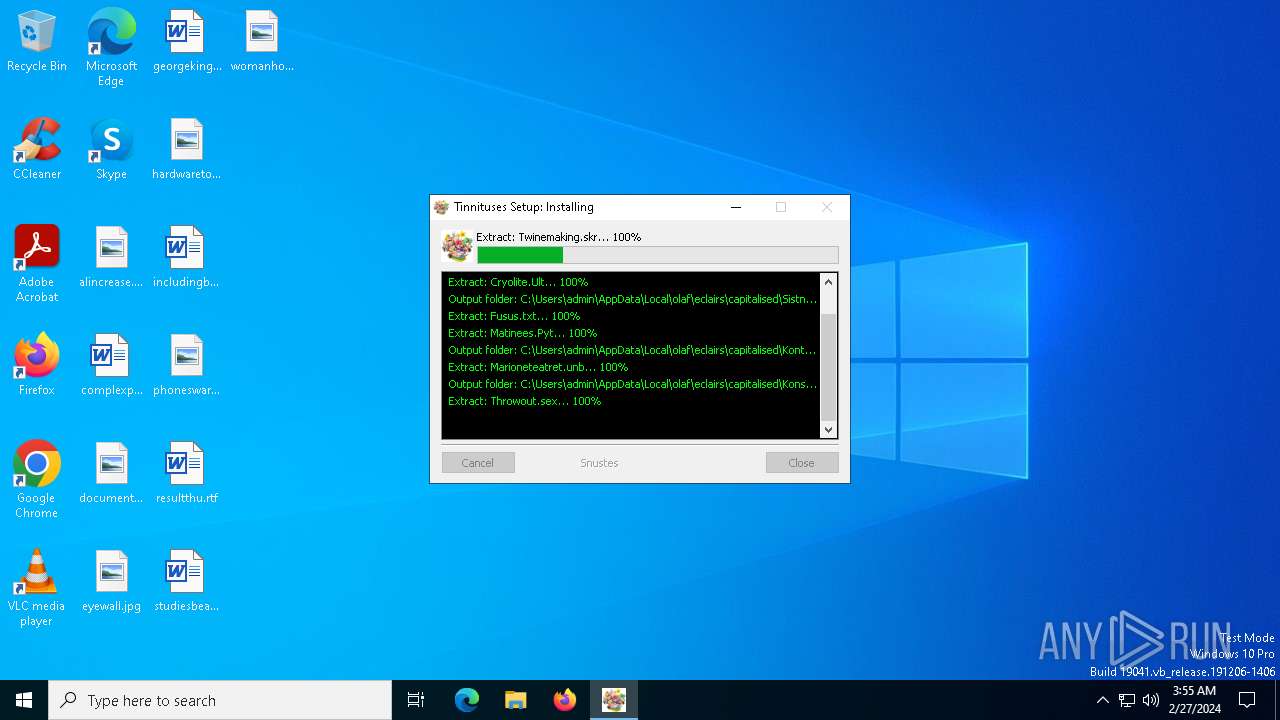
Drops the executable file immediately after the start
- 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe (PID: 2696)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe (PID: 2696)
Executable content was dropped or overwritten
- 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe (PID: 2696)
The process creates files with name similar to system file names
- 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe (PID: 2696)
INFO
Checks supported languages
- 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe (PID: 2696)
Reads the computer name
- 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe (PID: 2696)
Create files in a temporary directory
- 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe (PID: 2696)
Checks proxy server information
- slui.exe (PID: 4144)
Reads the software policy settings
- slui.exe (PID: 4144)
Creates files or folders in the user directory
- 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe (PID: 2696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:08:01 00:33:34+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25088 |
| InitializedDataSize: | 3782656 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x31ce |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.1.0.0 |
| ProductVersionNumber: | 2.1.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | fdevareannoncer |
| CompanyName: | vegetate |
| FileVersion: | 2.1.0.0 |
| InternalName: | uomtvisteliges gobbo.exe |
| LegalCopyright: | entodermic reprokameraerne modskrifter |
| LegalTrademarks: | piroplasm |
| OriginalFileName: | uomtvisteliges gobbo.exe |
| ProductName: | wellholes galvanoteknikkernes annalia |
Total processes
133
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2696 | "C:\Users\admin\AppData\Local\Temp\252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe" | C:\Users\admin\AppData\Local\Temp\252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe | explorer.exe | ||||||||||||
User: admin Company: vegetate Integrity Level: MEDIUM Exit code: 0 Version: 2.1.0.0 Modules
| |||||||||||||||
| 4144 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 896
Read events
3 860
Write events
36
Delete events
0
Modification events
| (PID) Process: | (2696) 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Ekskommuniceres225\Uninstall\mammonite\Suspired35 |
| Operation: | write | Name: | palaverne |
Value: 1 | |||
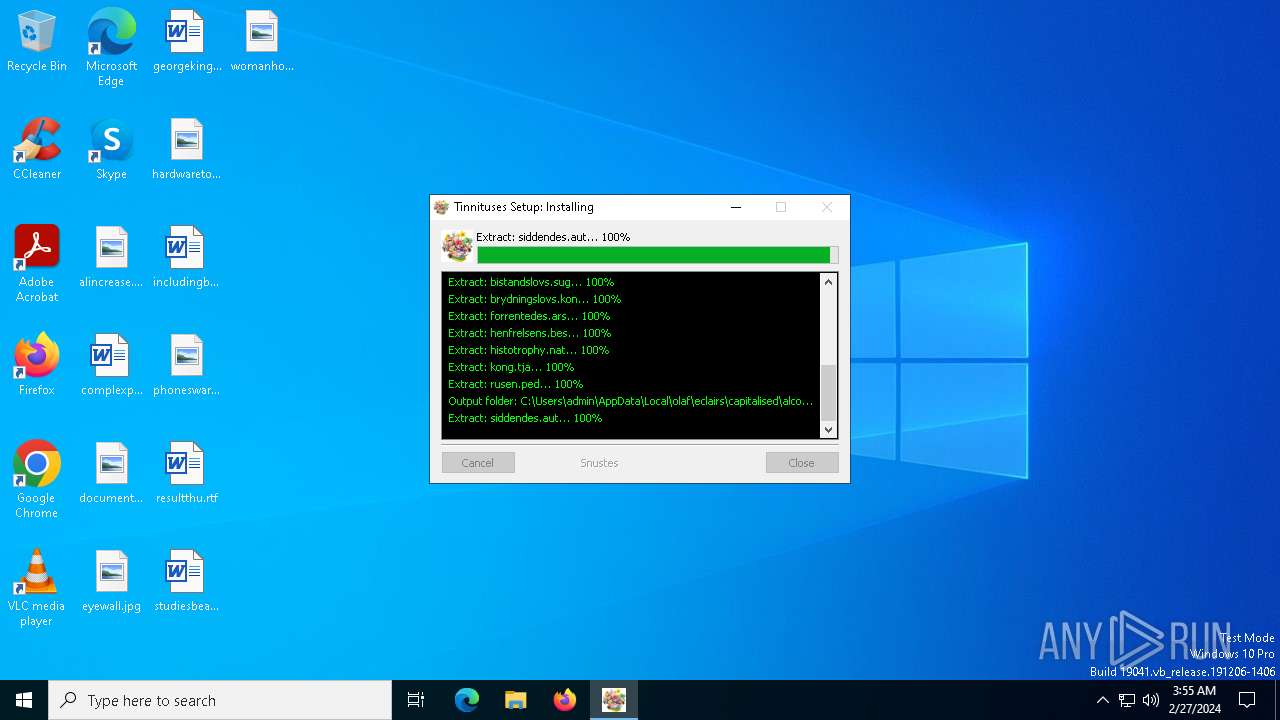
Executable files
1
Suspicious files
13
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2696 | 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe | C:\Users\admin\AppData\Local\olaf\eclairs\capitalised\Sistningen159\Unshrewish\Fusus.txt | text | |
MD5:36F7F42E523C5DCBCBB1BDB9D741BE9D | SHA256:FBC57234C4DCDD3B1D523731FC5438455F7E4A55CB2F591DD0BD7B81A53E69A6 | |||
| 2696 | 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe | C:\Users\admin\AppData\Local\olaf\eclairs\capitalised\Cryolite.Ult | binary | |
MD5:433C8704EC4179684909C195EC0C0F3B | SHA256:CD0B803B9425AD5BA5F6B3D6694876EBB06250548687469452C414180416D539 | |||
| 2696 | 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe | C:\Users\admin\AppData\Local\olaf\eclairs\capitalised\Sistningen159\Unshrewish\Matinees.Pyt | binary | |
MD5:684E268D4270E6C7B2DD8FD67702FD73 | SHA256:3A1CF1483065E07CB124854AF4CB355E26F9344F8FA6B7DFEDA22EE022288574 | |||
| 2696 | 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe | C:\Users\admin\AppData\Local\olaf\eclairs\capitalised\Konsulatet\Toppingness\Langbenet\forrentedes.ars | binary | |
MD5:3930D84C8EB534C4AE8225D0D740E147 | SHA256:F33499D8D15D8F52079F3773611F99A05027910184C0970B1FC957F720619879 | |||
| 2696 | 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe | C:\Users\admin\AppData\Local\olaf\eclairs\capitalised\Konsulatet\Toppingness\Langbenet\brydningslovs.kon | binary | |
MD5:EA20696CEF3C8D2B34BC744DA44631F6 | SHA256:CCC277D3D13B357D81E248FFC9835C3703408D00EB8D92B6DAC8B759B5A3C64A | |||
| 2696 | 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe | C:\Users\admin\AppData\Local\olaf\eclairs\capitalised\Konsulatet\Toppingness\Langbenet\bistandslovs.sug | binary | |
MD5:1FFA44AC8DB21CD73EBBFEA41967E09B | SHA256:F1FB4832D3424E3C418FFF4A4055C1C7DD88566F6D263CAC097E6F1CF79A39EB | |||
| 2696 | 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe | C:\Users\admin\AppData\Local\olaf\eclairs\capitalised\alcoholomania\Biverb\Unrespectively\siddendes.aut | binary | |
MD5:B266C16F3F3BD06F082432013ABE5EFF | SHA256:485B5B4FB39273BBFFF75B7D818D4262E4C1B635E4A6E11AF5CB1091306A3D67 | |||
| 2696 | 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe | C:\Users\admin\AppData\Local\olaf\eclairs\capitalised\Konsulatet\Toppingness\Langbenet\beraabelsernes.mut | binary | |
MD5:EEDE50BEF8DB7C08DA538AF0C1267BE3 | SHA256:EE256FD2BCCC7A7E4BECEEFD63E3AE6E10CBDE54DA600112630971D1DF9B680C | |||
| 2696 | 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe | C:\Users\admin\AppData\Local\olaf\eclairs\capitalised\Konsulatet\Toppingness\Langbenet\Twinemaking.skr | abr | |
MD5:EF36912877948015D2A6489C5630B2FF | SHA256:4147A6D277BB33683EB9584CCD12A1E8D28F47B1B3EAD2251AC77843147276D0 | |||
| 2696 | 252c26a5ea749569e41b4ce291ea4ff21d08ca884123c8ff171433a359455033.exe | C:\Users\admin\AppData\Local\olaf\eclairs\capitalised\Konsulatet\Toppingness\Langbenet\kong.tja | binary | |
MD5:F2697B92E93280E6F4B8B39139781E19 | SHA256:D16C16832D4A1304E91F6505CCF06F2EE53615153E9783BBD3AADA9994DBA1DE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
31
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5928 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
6256 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.01 Kb | unknown |
6896 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.01 Kb | unknown |
1312 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
2464 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5928 | svchost.exe | 40.126.32.74:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6896 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3848 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5928 | svchost.exe | 20.190.160.20:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5928 | svchost.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
6256 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
492 | backgroundTaskHost.exe | 92.123.104.31:443 | www.bing.com | Akamai International B.V. | DE | unknown |
6896 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |