| URL: | https://pendrivelinux.com/yumi-multiboot-usb-creator/ |
| Full analysis: | https://app.any.run/tasks/94c8c98d-f1c2-4104-b389-79df99857434 |
| Verdict: | Malicious activity |
| Analysis date: | November 02, 2023, 15:32:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | B81CB8D8F9C2E35956BB7EB301985AED04555DDD |
| SHA256: | 251E814186CAE2D94DA2F102785330CEBBB2C1C4D9B009A471C2F5712690364A |
| SSDEEP: | 3:N8EhLGK3cOItfG3ttlERMK:2EhyGcStPEt |
MALICIOUS
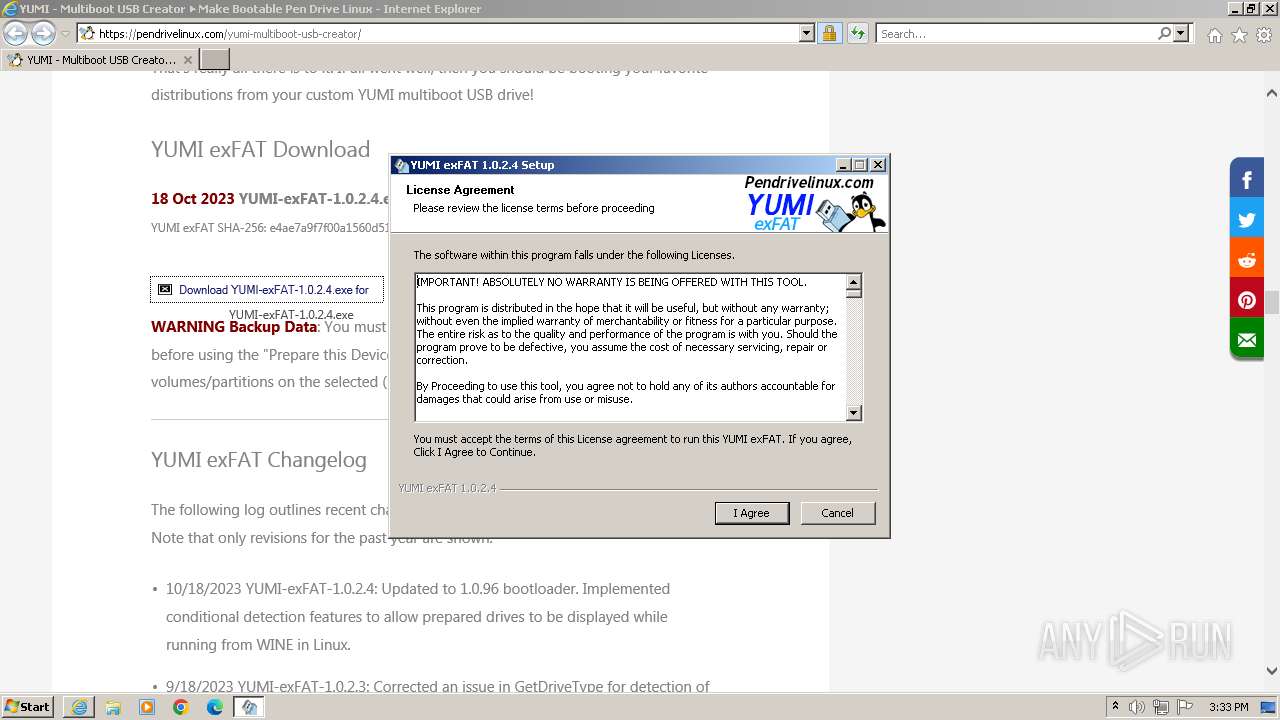
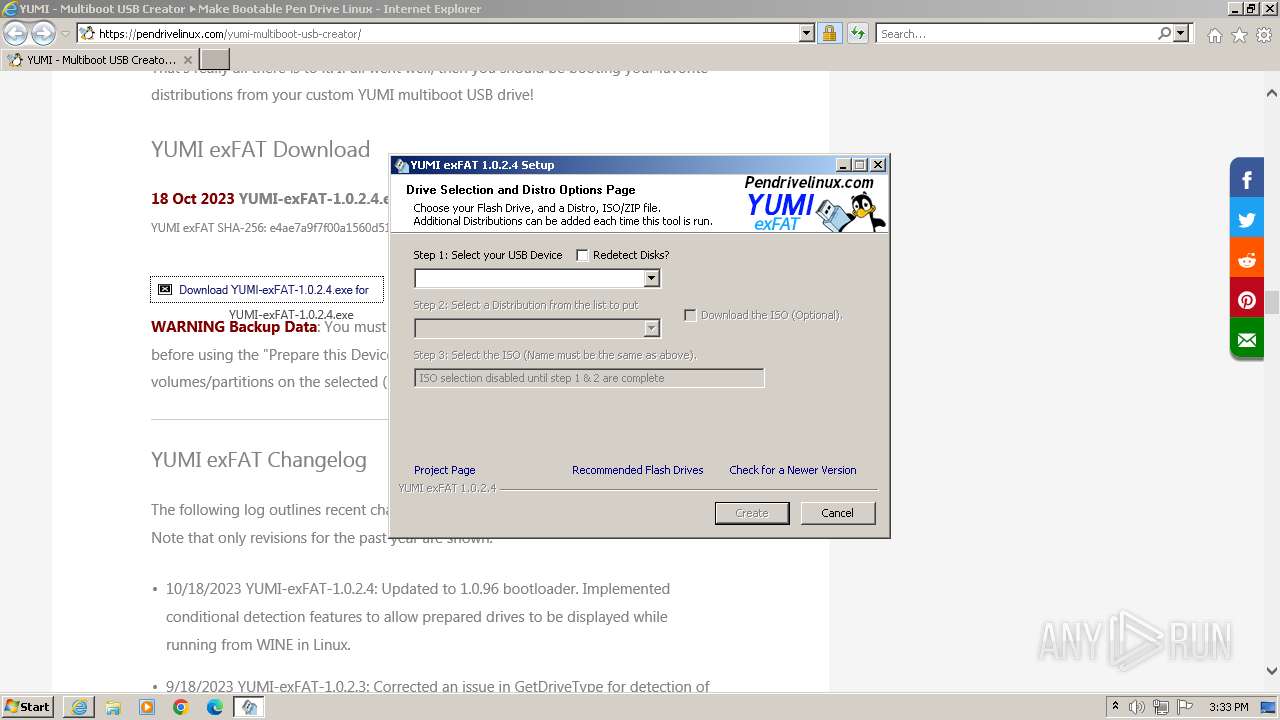
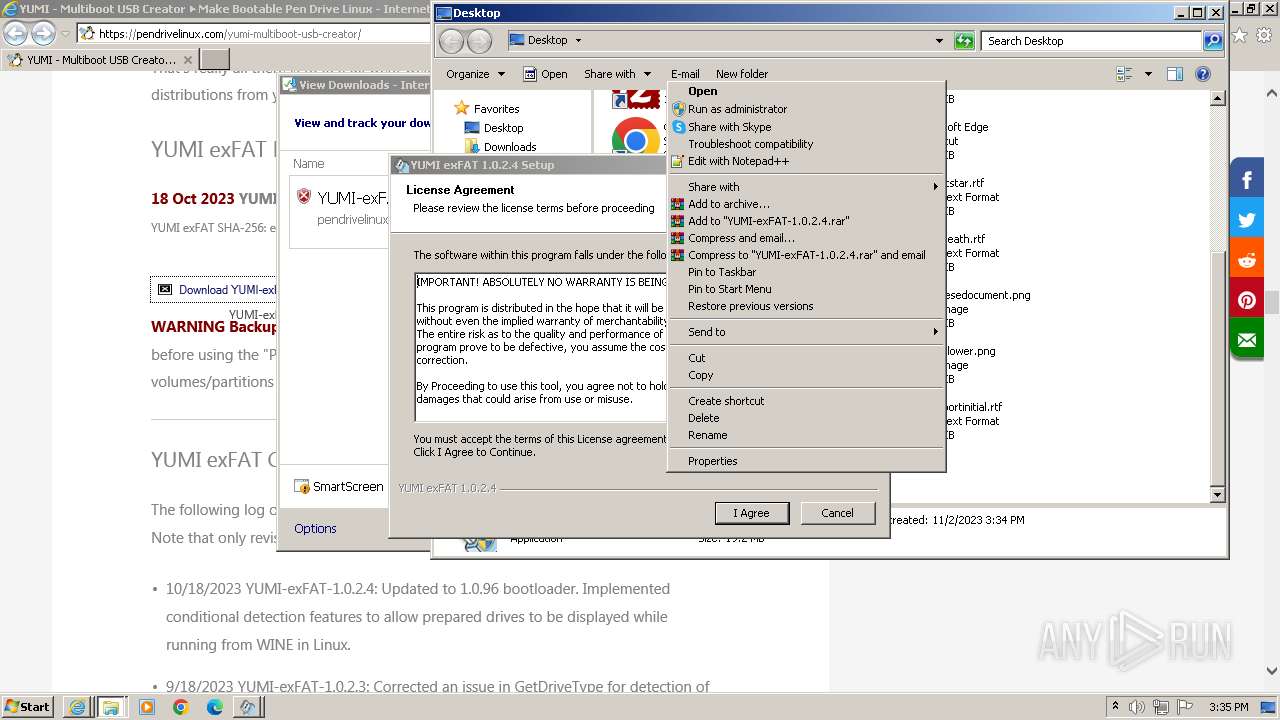
Drops the executable file immediately after the start
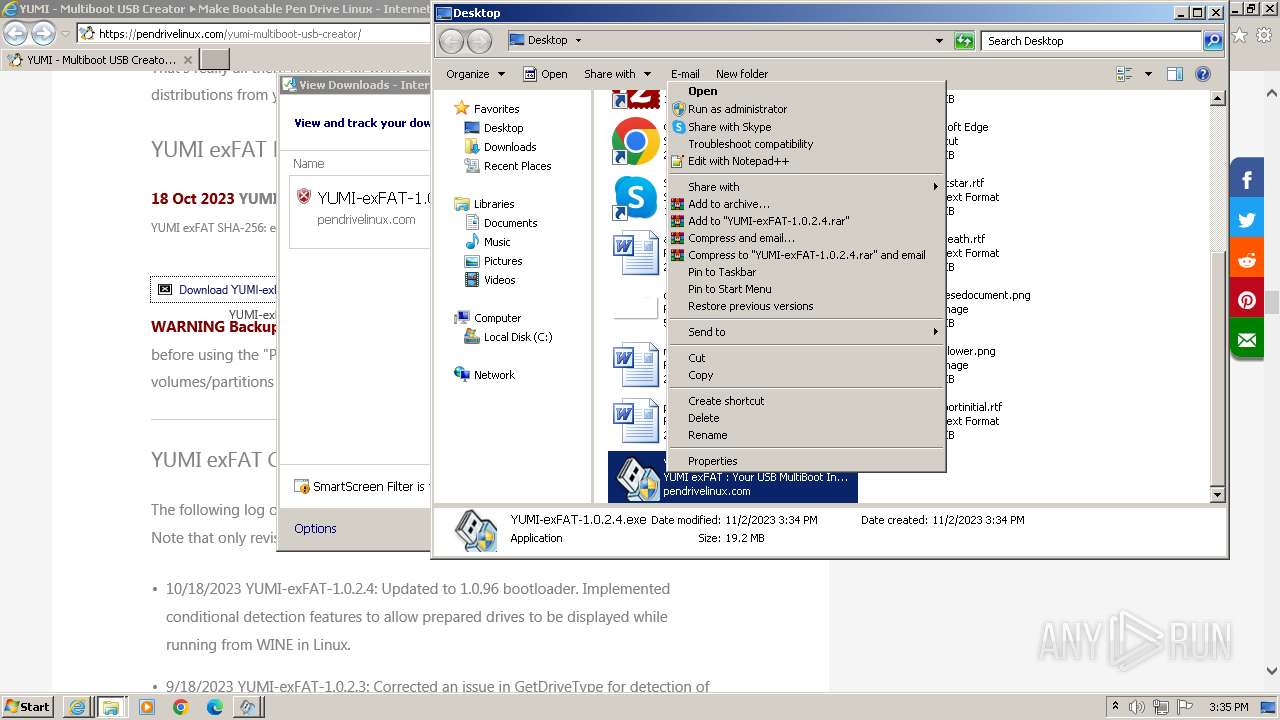
- YUMI-exFAT-1.0.2.4.exe (PID: 4032)
- YUMI-exFAT-1.0.2.4.exe (PID: 292)
- YUMI-exFAT-1.0.2.4.exe (PID: 3040)
SUSPICIOUS
The process creates files with name similar to system file names
- YUMI-exFAT-1.0.2.4.exe (PID: 4032)
- YUMI-exFAT-1.0.2.4.exe (PID: 292)
Malware-specific behavior (creating "System.dll" in Temp)
- YUMI-exFAT-1.0.2.4.exe (PID: 4032)
- YUMI-exFAT-1.0.2.4.exe (PID: 292)
Reads the Internet Settings
- YUMI-exFAT-1.0.2.4.exe (PID: 4032)
- YUMI-exFAT-1.0.2.4.exe (PID: 292)
- YUMI-exFAT-1.0.2.4.exe (PID: 3040)
Checks Windows Trust Settings
- YUMI-exFAT-1.0.2.4.exe (PID: 4032)
- YUMI-exFAT-1.0.2.4.exe (PID: 292)
- YUMI-exFAT-1.0.2.4.exe (PID: 3040)
Reads security settings of Internet Explorer
- YUMI-exFAT-1.0.2.4.exe (PID: 4032)
- YUMI-exFAT-1.0.2.4.exe (PID: 292)
- YUMI-exFAT-1.0.2.4.exe (PID: 3040)
Reads settings of System Certificates
- YUMI-exFAT-1.0.2.4.exe (PID: 4032)
- YUMI-exFAT-1.0.2.4.exe (PID: 292)
- YUMI-exFAT-1.0.2.4.exe (PID: 3040)
Adds/modifies Windows certificates
- iexplore.exe (PID: 3440)
Drops 7-zip archiver for unpacking
- YUMI-exFAT-1.0.2.4.exe (PID: 4032)
- YUMI-exFAT-1.0.2.4.exe (PID: 292)
- YUMI-exFAT-1.0.2.4.exe (PID: 3040)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3516)
- explorer.exe (PID: 788)
- YUMI-exFAT-1.0.2.4.exe (PID: 292)
- YUMI-exFAT-1.0.2.4.exe (PID: 3040)
Checks supported languages
- wmpnscfg.exe (PID: 3516)
- YUMI-exFAT-1.0.2.4.exe (PID: 4032)
- YUMI-exFAT-1.0.2.4.exe (PID: 3040)
- YUMI-exFAT-1.0.2.4.exe (PID: 292)
Reads the computer name
- wmpnscfg.exe (PID: 3516)
- YUMI-exFAT-1.0.2.4.exe (PID: 4032)
- YUMI-exFAT-1.0.2.4.exe (PID: 3040)
- YUMI-exFAT-1.0.2.4.exe (PID: 292)
Application launched itself
- iexplore.exe (PID: 3440)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3516)
- YUMI-exFAT-1.0.2.4.exe (PID: 4032)
- YUMI-exFAT-1.0.2.4.exe (PID: 292)
- YUMI-exFAT-1.0.2.4.exe (PID: 3040)
Create files in a temporary directory
- YUMI-exFAT-1.0.2.4.exe (PID: 4032)
- YUMI-exFAT-1.0.2.4.exe (PID: 3040)
- YUMI-exFAT-1.0.2.4.exe (PID: 292)
Checks proxy server information
- YUMI-exFAT-1.0.2.4.exe (PID: 4032)
- YUMI-exFAT-1.0.2.4.exe (PID: 292)
- YUMI-exFAT-1.0.2.4.exe (PID: 3040)
The process uses the downloaded file
- iexplore.exe (PID: 3440)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3440)
- iexplore.exe (PID: 3196)
Creates files or folders in the user directory
- YUMI-exFAT-1.0.2.4.exe (PID: 4032)
- YUMI-exFAT-1.0.2.4.exe (PID: 3040)
- YUMI-exFAT-1.0.2.4.exe (PID: 292)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
61
Monitored processes
8
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
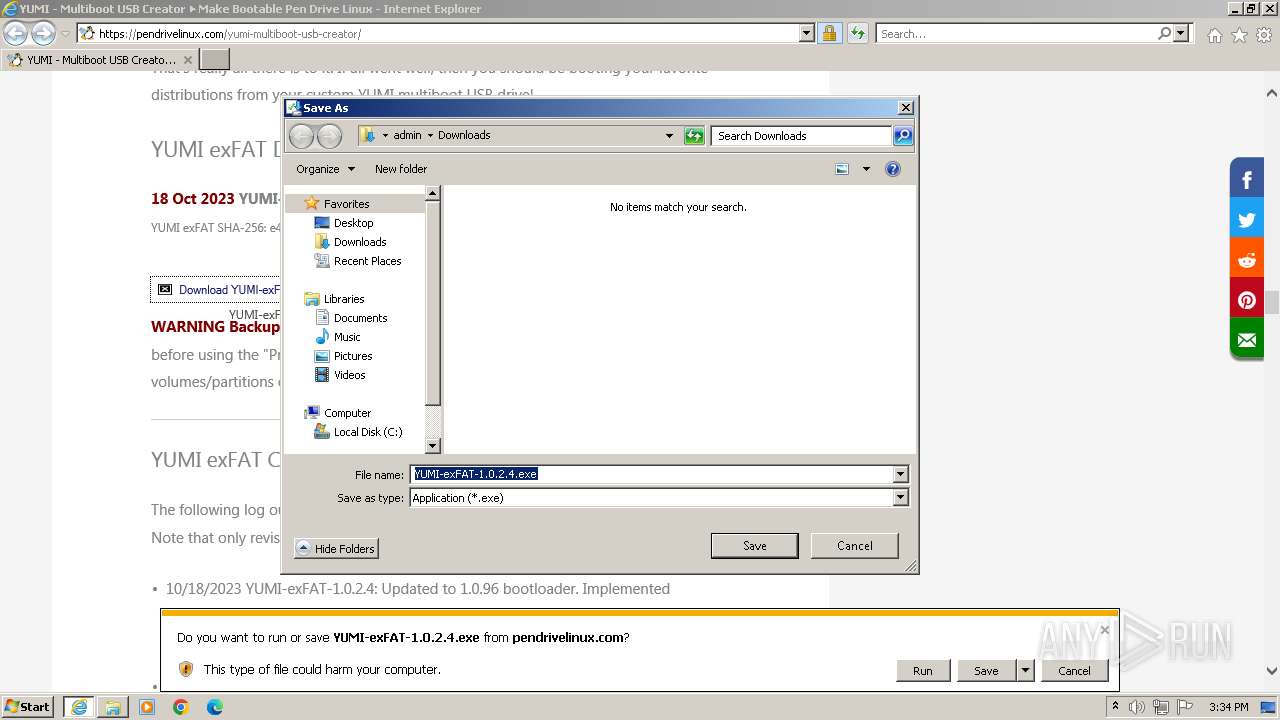
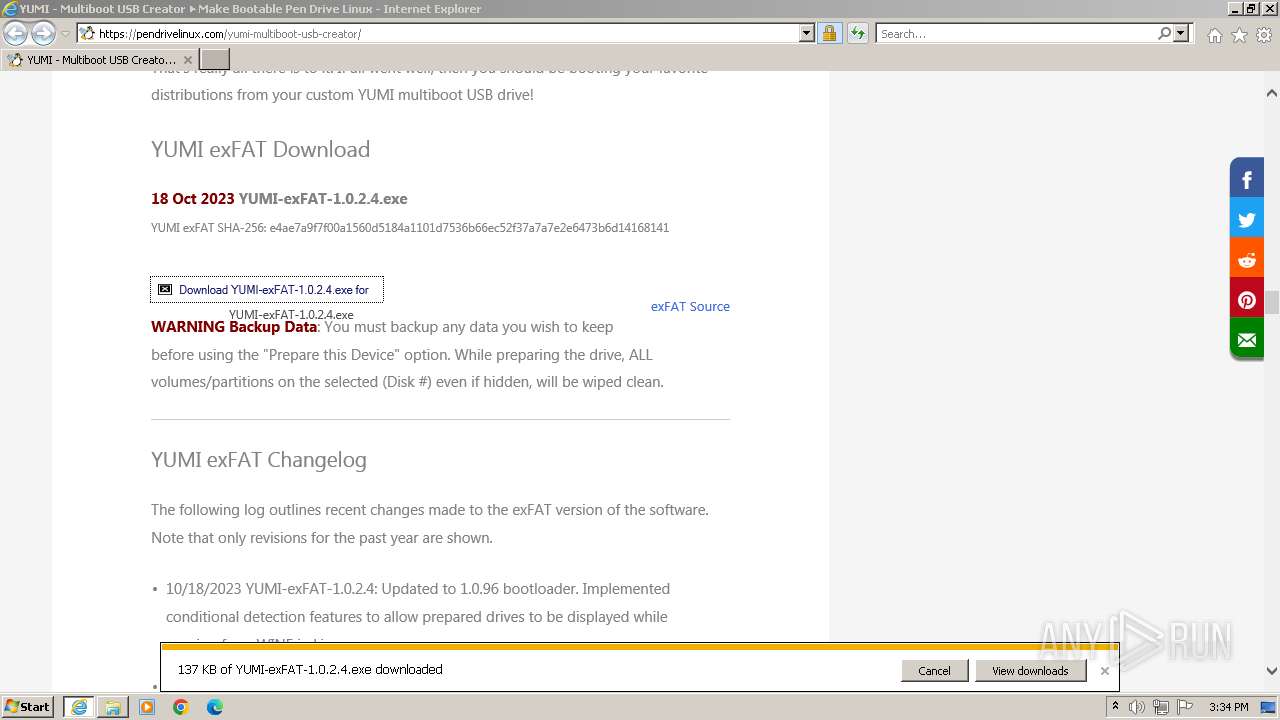
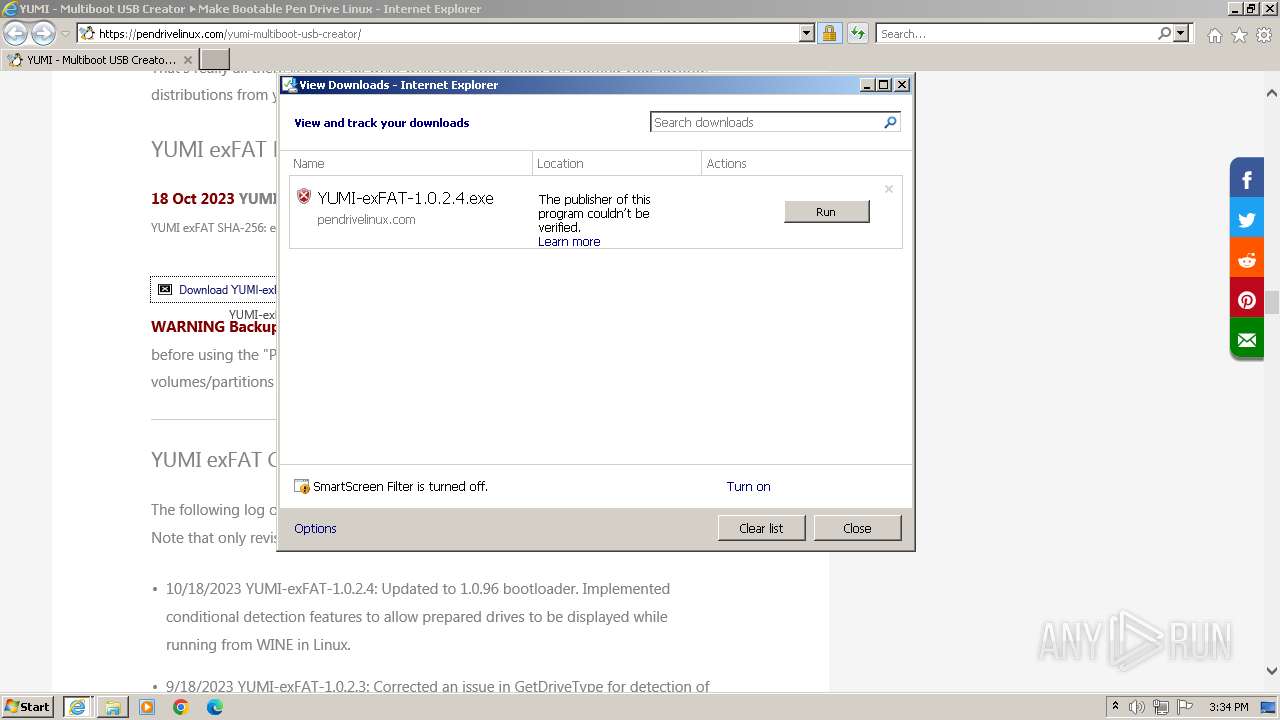
| 292 | "C:\Users\admin\Desktop\YUMI-exFAT-1.0.2.4.exe" | C:\Users\admin\Desktop\YUMI-exFAT-1.0.2.4.exe | explorer.exe | ||||||||||||
User: admin Company: pendrivelinux.com Integrity Level: HIGH Description: YUMI exFAT : Your USB MultiBoot Installer Exit code: 0 Version: 1.0.2.4 Modules
| |||||||||||||||
| 788 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3040 | "C:\Users\admin\Desktop\YUMI-exFAT-1.0.2.4.exe" | C:\Users\admin\Desktop\YUMI-exFAT-1.0.2.4.exe | explorer.exe | ||||||||||||
User: admin Company: pendrivelinux.com Integrity Level: HIGH Description: YUMI exFAT : Your USB MultiBoot Installer Exit code: 0 Version: 1.0.2.4 Modules
| |||||||||||||||
| 3196 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3440 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3440 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://pendrivelinux.com/yumi-multiboot-usb-creator/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3516 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4032 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\YUMI-exFAT-1.0.2.4.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\YUMI-exFAT-1.0.2.4.exe | iexplore.exe | ||||||||||||
User: admin Company: pendrivelinux.com Integrity Level: HIGH Description: YUMI exFAT : Your USB MultiBoot Installer Exit code: 1 Version: 1.0.2.4 Modules
| |||||||||||||||
| 4044 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\YUMI-exFAT-1.0.2.4.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\YUMI-exFAT-1.0.2.4.exe | — | iexplore.exe | |||||||||||
User: admin Company: pendrivelinux.com Integrity Level: MEDIUM Description: YUMI exFAT : Your USB MultiBoot Installer Exit code: 3221226540 Version: 1.0.2.4 Modules
| |||||||||||||||
Total events
34 936
Read events
34 702
Write events
227
Delete events
7
Modification events
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000059010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3440) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
28
Suspicious files
93
Text files
184
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3196 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:8BC01F1089F13556B64CBCF0926467D2 | SHA256:763EE0A0EEF83871043510C30CDC5106DF53DB613B6ECCA55EDB335C3D396500 | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab7EBA.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1B1495DD322A24490E2BF2FAABAE1C61 | binary | |
MD5:DEC6BBE308EB44937F77160A25EE32DB | SHA256:68A71DE28F488586C2B169F4652347E0A1FD632D48A6D6725393607BFA18BC7E | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar7EBB.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab7EDB.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:E4B4DD89A9640B56E4D97A256C322E13 | SHA256:AF2CB97DFF6AE9813EDD23C6430C466766E1B944817FCBC26969F5B75BF2D660 | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\67O6O40H.txt | text | |
MD5:BD4544F9A3540C514A1748772A30E25B | SHA256:F8AFCB28F4927CB64471F5CD11E0B64D7BB91C47D333BD9A7739F1FA3151C41B | |||
| 3196 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar7EDC.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
59
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3196 | iexplore.exe | GET | 200 | 8.241.123.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d6bb2ad0af14907d | unknown | compressed | 4.66 Kb | unknown |
3196 | iexplore.exe | GET | 200 | 8.241.123.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a3e161be64fd9a79 | unknown | compressed | 61.6 Kb | unknown |
3196 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDCjDk6BcP0YRJkTzSsQwBD | unknown | binary | 472 b | unknown |
3196 | iexplore.exe | GET | 200 | 23.197.120.82:80 | http://x2.c.lencr.org/ | unknown | binary | 300 b | unknown |
3196 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3196 | iexplore.exe | GET | 200 | 8.241.123.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?7f22e41b60d8fd96 | unknown | compressed | 61.6 Kb | unknown |
3196 | iexplore.exe | GET | 200 | 23.60.200.134:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3196 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDCNiwY2ODuiwnOV%2Bqn%2FArZ | unknown | binary | 472 b | unknown |
3196 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3196 | iexplore.exe | GET | 200 | 172.217.18.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3196 | iexplore.exe | 172.67.145.16:443 | pendrivelinux.com | CLOUDFLARENET | US | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3196 | iexplore.exe | 8.241.123.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
3196 | iexplore.exe | 23.60.200.134:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
3196 | iexplore.exe | 23.197.120.82:80 | x2.c.lencr.org | Akamai International B.V. | US | unknown |
3196 | iexplore.exe | 172.67.144.62:443 | privacy.gatekeeperconsent.com | CLOUDFLARENET | US | unknown |
3196 | iexplore.exe | 216.58.212.168:443 | www.googletagmanager.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pendrivelinux.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
privacy.gatekeeperconsent.com |
| unknown |
www.googletagmanager.com |
| whitelisted |
ezodn.com |
| whitelisted |
the.gatekeeperconsent.com |
| unknown |