| File name: | LB3.exe |
| Full analysis: | https://app.any.run/tasks/a3963e1f-6931-411b-987a-1c77ab808481 |
| Verdict: | Malicious activity |
| Threats: | LockBit, a ransomware variant, encrypts data on infected machines, demanding a ransom payment for decryption. Used in targeted attacks, It's a significant risk to organizations. |
| Analysis date: | April 09, 2025, 16:00:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | A40BBBDC17F188EB906DC09CB0556BC6 |
| SHA1: | 1F582C3BA3157202357D11A5A5EDE3A383D10D79 |
| SHA256: | 251297B055AA4DECDAB1A1D8E14EA1331BCBE00974515A647F55B0E0C23E29F5 |
| SSDEEP: | 3072:OmhXodguLLDzaJ/A7z7zT73cLLsXd6PbMS8IkUA9QyHVy:2fza6z7z8LXbYrU |
MALICIOUS
Known privilege escalation attack
- dllhost.exe (PID: 7692)
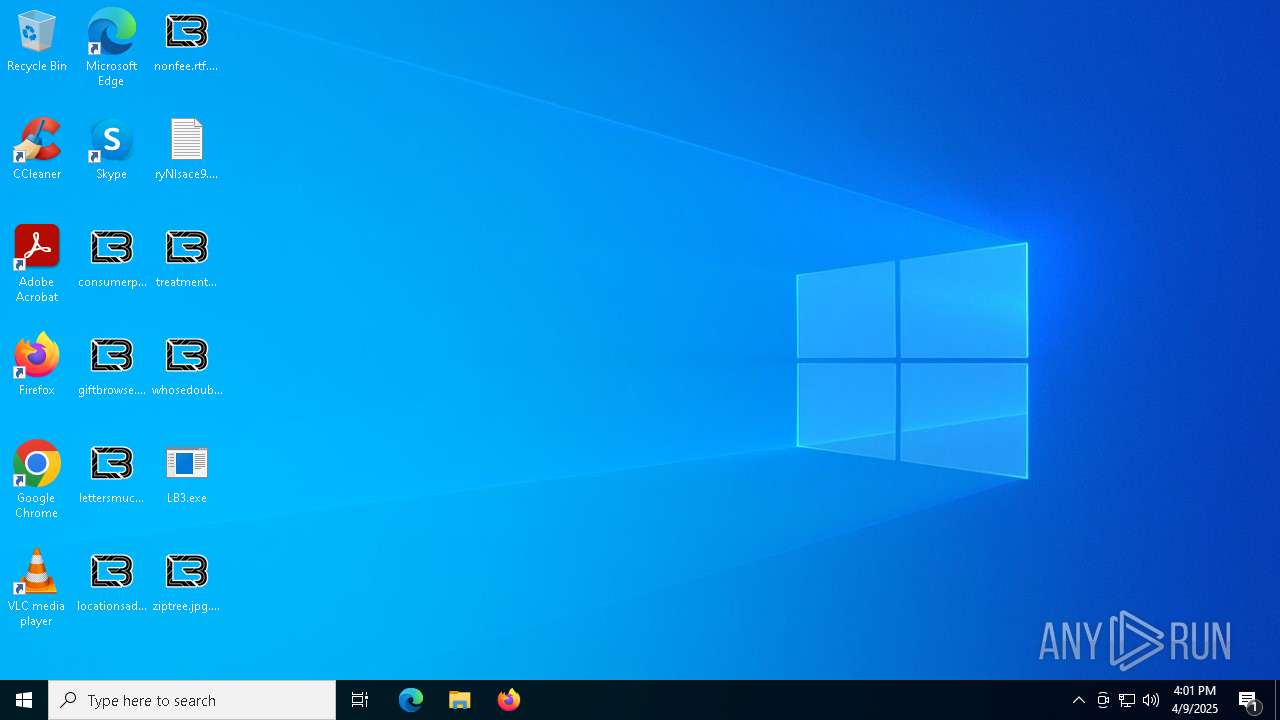
Renames files like ransomware
- LB3.exe (PID: 7764)
RANSOMWARE has been detected
- LB3.exe (PID: 7764)
Actions looks like stealing of personal data
- LB3.exe (PID: 7764)
[YARA] LockBit is detected
- LB3.exe (PID: 7764)
Steals credentials from Web Browsers
- LB3.exe (PID: 7764)
SUSPICIOUS
Write to the desktop.ini file (may be used to cloak folders)
- LB3.exe (PID: 7764)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 8028)
There is functionality for taking screenshot (YARA)
- LB3.exe (PID: 7764)
INFO
Reads the machine GUID from the registry
- LB3.exe (PID: 7524)
- SearchApp.exe (PID: 1056)
Checks supported languages
- LB3.exe (PID: 7524)
- LB3.exe (PID: 7764)
- ShellExperienceHost.exe (PID: 8028)
- SearchApp.exe (PID: 1056)
Reads the computer name
- LB3.exe (PID: 7524)
- LB3.exe (PID: 7764)
- ShellExperienceHost.exe (PID: 8028)
- SearchApp.exe (PID: 1056)
Creates files in the program directory
- LB3.exe (PID: 7764)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 7692)
- OpenWith.exe (PID: 7404)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 3888)
- OpenWith.exe (PID: 7404)
- OpenWith.exe (PID: 7384)
- OpenWith.exe (PID: 7176)
- OpenWith.exe (PID: 5864)
Manual execution by a user
- OpenWith.exe (PID: 5864)
- OpenWith.exe (PID: 3888)
- notepad.exe (PID: 1052)
- OpenWith.exe (PID: 7384)
- OpenWith.exe (PID: 7404)
- OpenWith.exe (PID: 7176)
Creates files or folders in the user directory
- LB3.exe (PID: 7764)
Create files in a temporary directory
- LB3.exe (PID: 7764)
Application launched itself
- AcroCEF.exe (PID: 1568)
- Acrobat.exe (PID: 4268)
Process checks computer location settings
- SearchApp.exe (PID: 1056)
Checks proxy server information
- SearchApp.exe (PID: 1056)
Reads the software policy settings
- SearchApp.exe (PID: 1056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (38.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (26.2) |
| .exe | | | Win16/32 Executable Delphi generic (12) |
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:09:13 23:30:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.12 |
| CodeSize: | 99328 |
| InitializedDataSize: | 50688 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1946f |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
150
Monitored processes
21
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1052 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Downloads\ryNlsace9.README.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2440 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1208 --field-trial-handle=1608,i,1143756365087369624,4421537699712626334,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
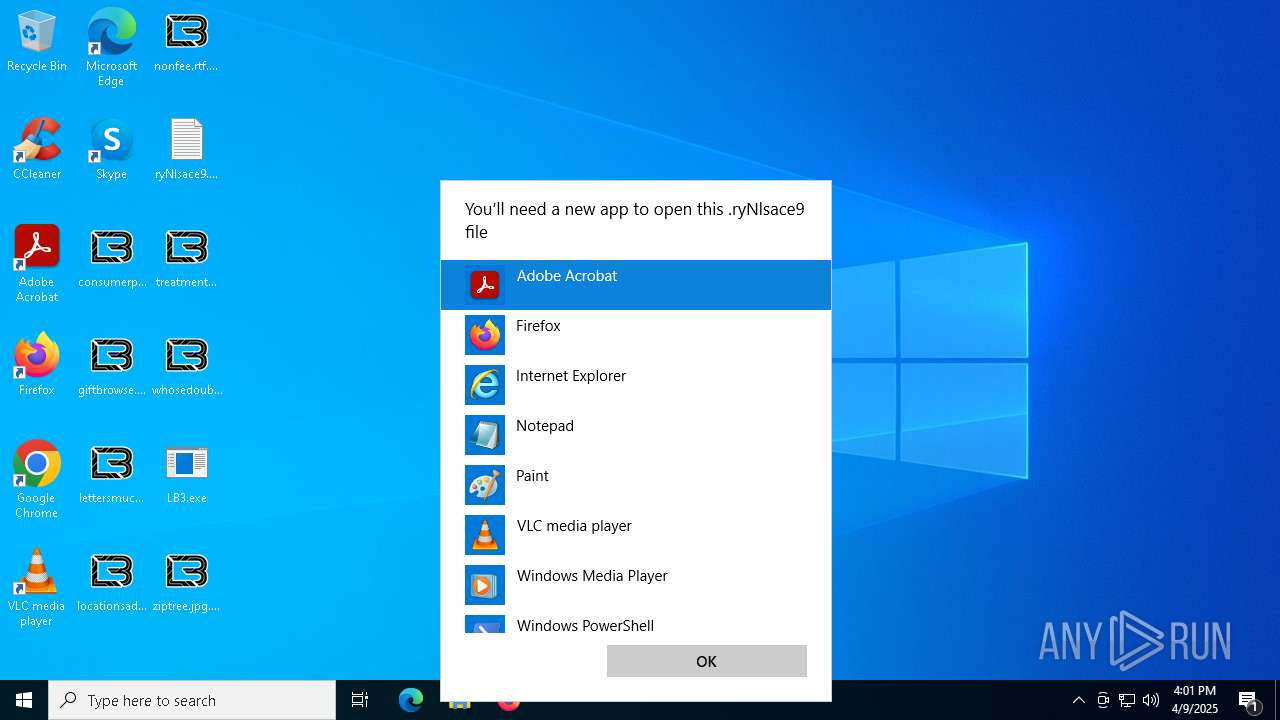
| 3888 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Downloads\wellterms.jpg.ryNlsace9 | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
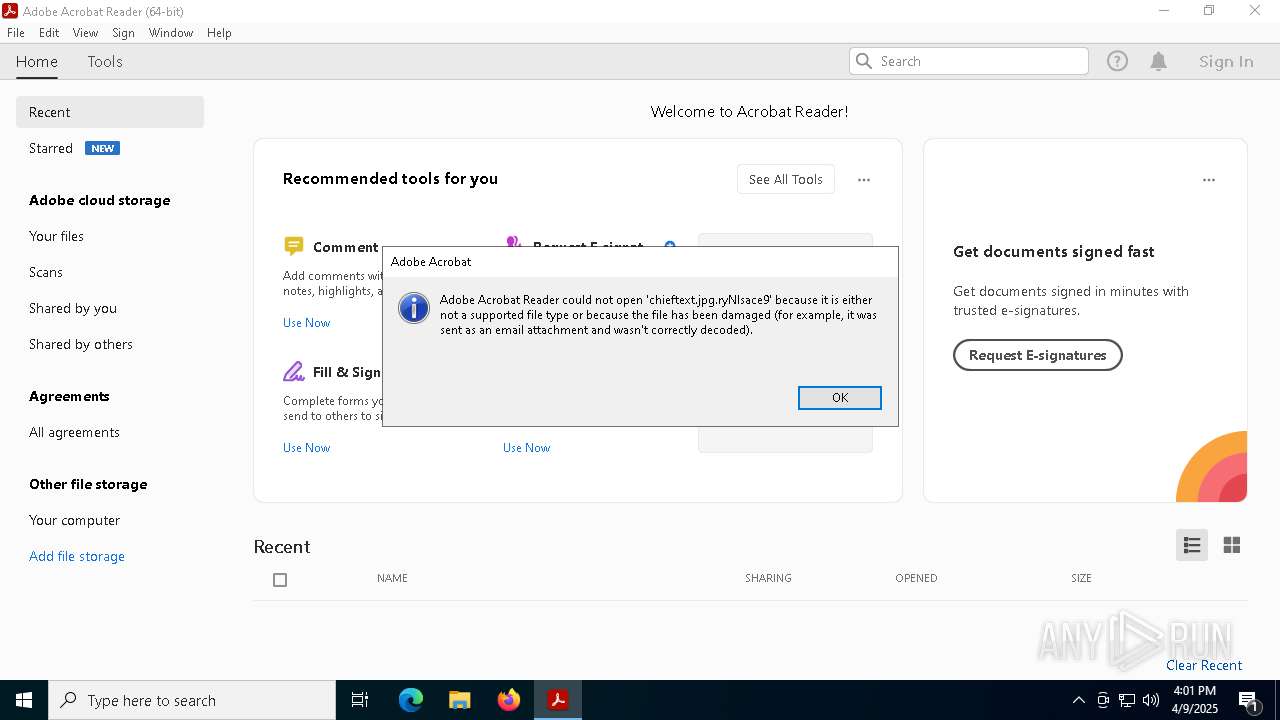
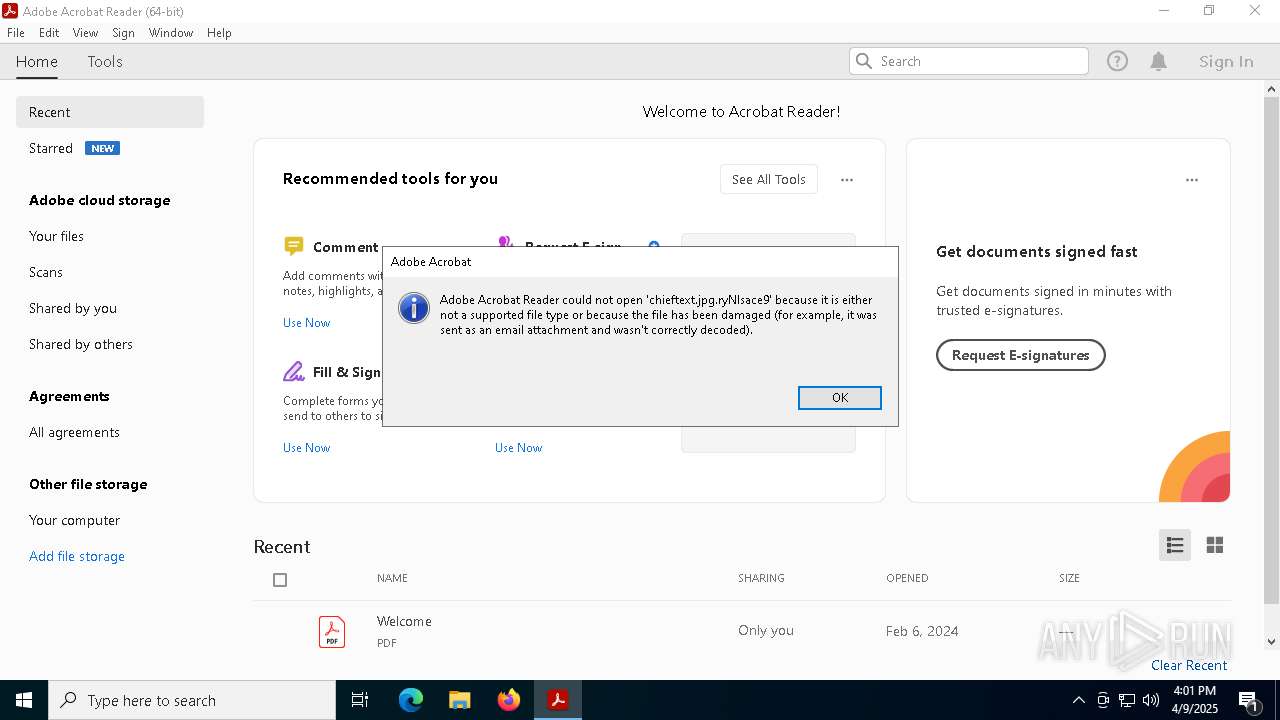
| 4268 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" "C:\Users\admin\Downloads\chieftext.jpg.ryNlsace9" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
| 4436 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1736 --field-trial-handle=1608,i,1143756365087369624,4421537699712626334,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 4736 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2848 --field-trial-handle=1608,i,1143756365087369624,4421537699712626334,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 5864 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Downloads\stockvegas.jpg.ryNlsace9 | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7176 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Downloads\setsoffers.png.ryNlsace9 | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 081
Read events
26 784
Write events
282
Delete events
15
Modification events
| (PID) Process: | (7692) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (8028) ShellExperienceHost.exe | Key: | \REGISTRY\A\{a5fa9160-2d57-759e-f46c-7f4d84b5026f}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D000000206A959268A9DB01 | |||
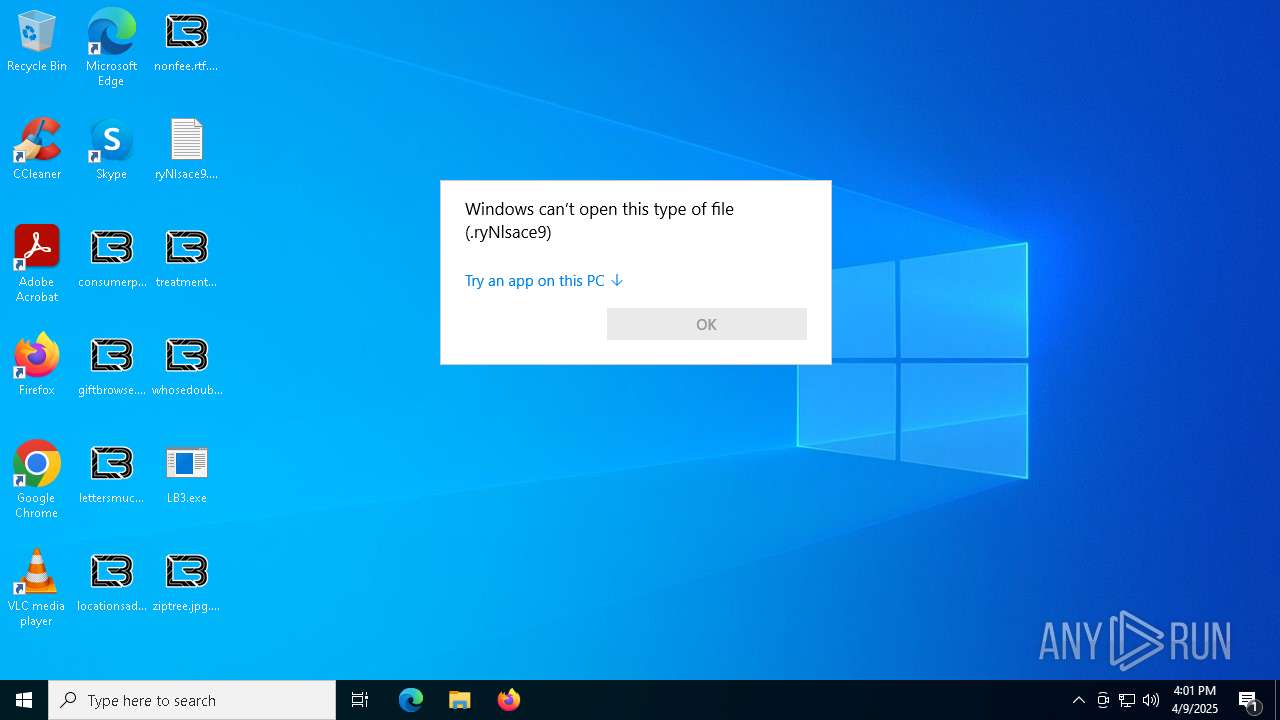
| (PID) Process: | (3888) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.ryNlsace9\OpenWithProgids |
| Operation: | write | Name: | ryNlsace9 |
Value: | |||
| (PID) Process: | (5864) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.ryNlsace9\OpenWithProgids |
| Operation: | write | Name: | ryNlsace9 |
Value: | |||
| (PID) Process: | (7176) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.ryNlsace9\OpenWithProgids |
| Operation: | write | Name: | ryNlsace9 |
Value: | |||
| (PID) Process: | (7384) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.ryNlsace9\OpenWithProgids |
| Operation: | write | Name: | ryNlsace9 |
Value: | |||
| (PID) Process: | (7404) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.ryNlsace9\OpenWithProgids |
| Operation: | write | Name: | ryNlsace9 |
Value: | |||
| (PID) Process: | (4268) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (7488) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (7488) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | bSynchronizeOPL |
Value: 0 | |||
Executable files
19
Suspicious files
1 798
Text files
1 759
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7764 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\IIIIIIIIIII | binary | |
MD5:43745B372AB27C298FBAEA730467F9CD | SHA256:ED1761B348194179DBF7E095ED348061CE128AA24C3B9E721CC181775FBDBA4C | |||
| 7764 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\JJJJJJJJJJJ | binary | |
MD5:43745B372AB27C298FBAEA730467F9CD | SHA256:ED1761B348194179DBF7E095ED348061CE128AA24C3B9E721CC181775FBDBA4C | |||
| 7764 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\FFFFFFFFFFF | binary | |
MD5:43745B372AB27C298FBAEA730467F9CD | SHA256:ED1761B348194179DBF7E095ED348061CE128AA24C3B9E721CC181775FBDBA4C | |||
| 7764 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\KKKKKKKKKKK | binary | |
MD5:43745B372AB27C298FBAEA730467F9CD | SHA256:ED1761B348194179DBF7E095ED348061CE128AA24C3B9E721CC181775FBDBA4C | |||
| 7764 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\GGGGGGGGGGG | binary | |
MD5:43745B372AB27C298FBAEA730467F9CD | SHA256:ED1761B348194179DBF7E095ED348061CE128AA24C3B9E721CC181775FBDBA4C | |||
| 7764 | LB3.exe | C:\ryNlsace9.README.txt | text | |
MD5:DD746ACE17E44ACE00885B91400F11D5 | SHA256:B27C3C8A30FAF7C76483B7E5D964AE85046A9713CAA46508EE7A1E31B7DC6272 | |||
| 7764 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\HHHHHHHHHHH | binary | |
MD5:43745B372AB27C298FBAEA730467F9CD | SHA256:ED1761B348194179DBF7E095ED348061CE128AA24C3B9E721CC181775FBDBA4C | |||
| 7764 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\BBBBBBBBBBB | binary | |
MD5:43745B372AB27C298FBAEA730467F9CD | SHA256:ED1761B348194179DBF7E095ED348061CE128AA24C3B9E721CC181775FBDBA4C | |||
| 7764 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\EEEEEEEEEEE | binary | |
MD5:43745B372AB27C298FBAEA730467F9CD | SHA256:ED1761B348194179DBF7E095ED348061CE128AA24C3B9E721CC181775FBDBA4C | |||
| 7764 | LB3.exe | C:\$Recycle.Bin\S-1-5-18\DDDDDDDDDDD | binary | |
MD5:43745B372AB27C298FBAEA730467F9CD | SHA256:ED1761B348194179DBF7E095ED348061CE128AA24C3B9E721CC181775FBDBA4C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
21
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | OPTIONS | 204 | 3.233.129.217:443 | https://p13n.adobe.io/psdk/v2/content?surfaceId=ACROBAT_READER_MASTER_SURFACEID&surfaceId=DC_READER_LAUNCH_CARD&surfaceId=DC_Reader_RHP_Banner&surfaceId=DC_Reader_RHP_Retention&surfaceId=Edit_InApp_Aug2020&surfaceId=DC_FirstMile_Right_Sec_Surface&surfaceId=DC_Reader_Upsell_Cards&surfaceId=DC_FirstMile_Home_View_Surface&surfaceId=DC_Reader_RHP_Intent_Banner&surfaceId=DC_Reader_Disc_LHP_Banner&surfaceId=DC_Reader_Edit_LHP_Banner&surfaceId=DC_Reader_Convert_LHP_Banner&surfaceId=DC_Reader_Sign_LHP_Banner&surfaceId=DC_Reader_More_LHP_Banner&surfaceId=DC_Reader_Disc_LHP_Retention&adcProductLanguage=en-us&adcVersion=23.1.20093&adcProductType=SingleClientMini&adcOSType=WIN&adcCountryCode=UA&adcXAPIClientID=api_reader_desktop_win_23.1.20093&encodingScheme=BASE_64 | unknown | — | — | unknown |
4208 | RUXIMICS.exe | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 92.123.104.32:443 | https://www.bing.com/rp/4BpQ1bD8vX1mXuJObN-gg9RqkyQ.br.js | unknown | binary | 950 b | whitelisted |
— | — | GET | 200 | 3.233.129.217:443 | https://p13n.adobe.io/psdk/v2/content?surfaceId=ACROBAT_READER_MASTER_SURFACEID&surfaceId=DC_READER_LAUNCH_CARD&surfaceId=DC_Reader_RHP_Banner&surfaceId=DC_Reader_RHP_Retention&surfaceId=Edit_InApp_Aug2020&surfaceId=DC_FirstMile_Right_Sec_Surface&surfaceId=DC_Reader_Upsell_Cards&surfaceId=DC_FirstMile_Home_View_Surface&surfaceId=DC_Reader_RHP_Intent_Banner&surfaceId=DC_Reader_Disc_LHP_Banner&surfaceId=DC_Reader_Edit_LHP_Banner&surfaceId=DC_Reader_Convert_LHP_Banner&surfaceId=DC_Reader_Sign_LHP_Banner&surfaceId=DC_Reader_More_LHP_Banner&surfaceId=DC_Reader_Disc_LHP_Retention&adcProductLanguage=en-us&adcVersion=23.1.20093&adcProductType=SingleClientMini&adcOSType=WIN&adcCountryCode=UA&adcXAPIClientID=api_reader_desktop_win_23.1.20093&encodingScheme=BASE_64 | unknown | binary | 187 b | whitelisted |
— | — | GET | 200 | 69.192.160.136:443 | https://geo2.adobe.com/ | unknown | text | 50 b | whitelisted |
— | — | GET | 200 | 92.123.104.24:443 | https://www.bing.com/rb/16/jnc,nj/pNXV2ymlrFEAOVLUgJkRBRwYFkY.js?bu=DicwgAGNAZQBlwGKAYMBhwHCAcUBMLoByAE&or=w | unknown | binary | 21.7 Kb | whitelisted |
— | — | GET | 200 | 92.123.104.20:443 | https://www.bing.com/manifest/threshold.appcache | unknown | text | 3.47 Kb | whitelisted |
— | — | GET | 200 | 92.123.104.33:443 | https://www.bing.com/rb/18/jnc,nj/6hU_LneafI_NFLeDvM367ebFaKQ.js?bu=DyIrb3t-gQF4cnWyAbUBK6UBK7gB&or=w | unknown | binary | 21.3 Kb | whitelisted |
— | — | POST | 204 | 92.123.104.14:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
— | — | GET | 200 | 92.123.104.26:443 | https://www.bing.com/rb/19/cir3,ortl,cc,nc/FgBbpIj0thGWZOh_xFnM9i4O7ek.css?bu=C6QK5QORBfYK3gnICb8HYWFhYQ&or=w | unknown | text | 19.8 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4208 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4208 | RUXIMICS.exe | 23.216.77.20:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7576 | AcroCEF.exe | 69.192.160.136:443 | geo2.adobe.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
www.bing.com |
| whitelisted |