| download: | /getfile |
| Full analysis: | https://app.any.run/tasks/78e33a10-81c5-44e1-be9b-909445bed611 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2024, 04:07:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
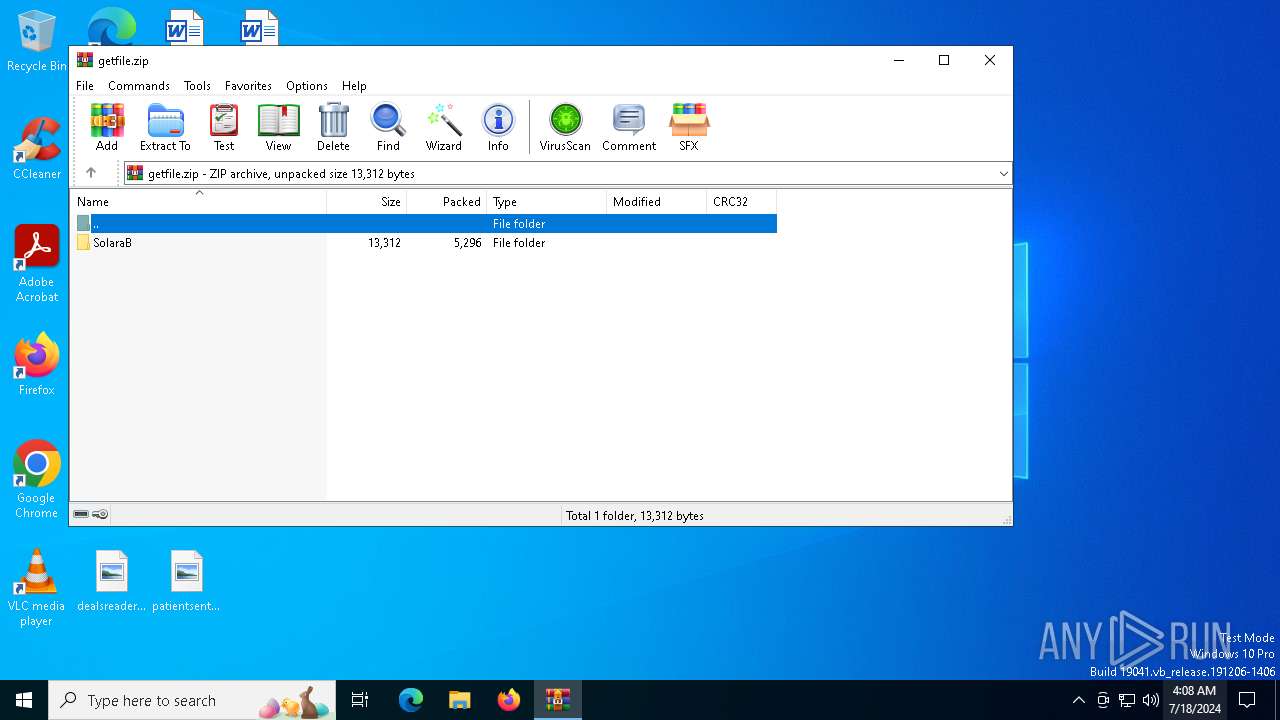
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 4EC8143B6DBE27870CF8333711FF5096 |
| SHA1: | 693D467EBEC348469011FFEF1BD370B113653147 |
| SHA256: | 2510BE907EC476E8375AC7B5431536AE9A32BF99FE77AB695A5100852B111B96 |
| SSDEEP: | 96:EUqjU52FPuD85CRbXQSQ4Bl1ZP5MaOS5ZTDCJvuB66EFscY7LO4ivJEzmqAZdXRD:EU+FuNQt6JP5GS5NGMYE7TogARskfl |
MALICIOUS
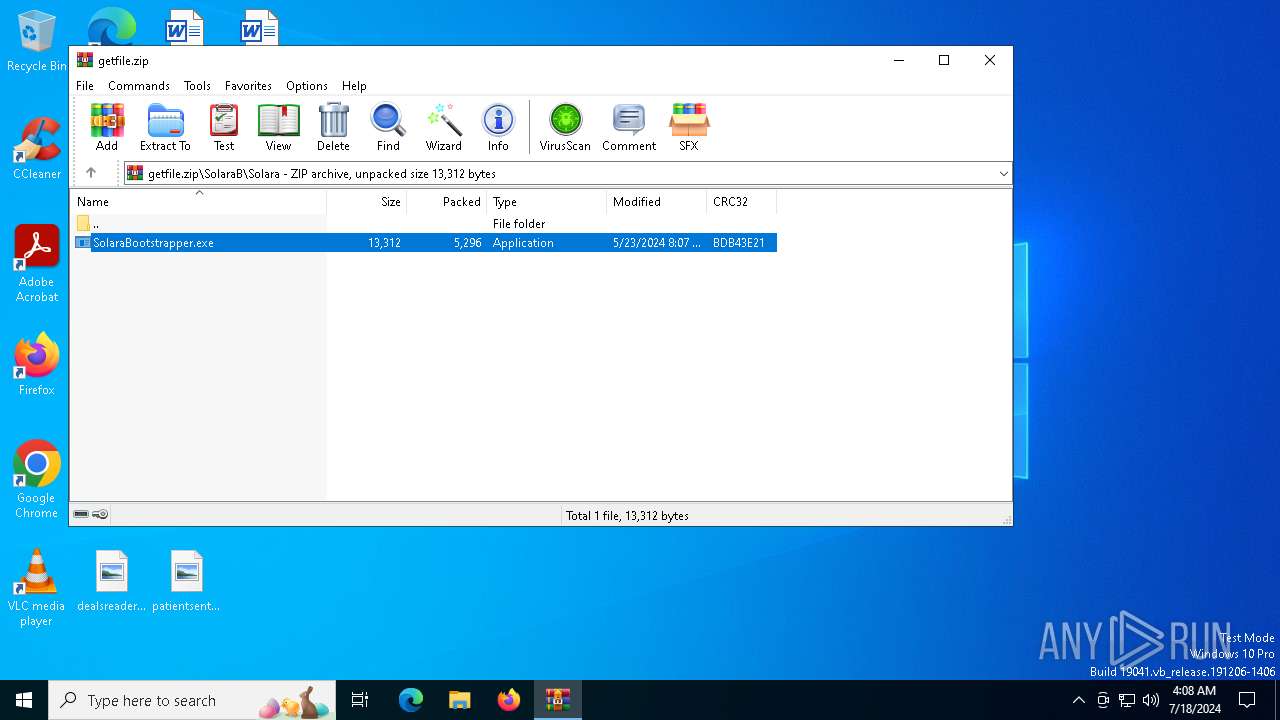
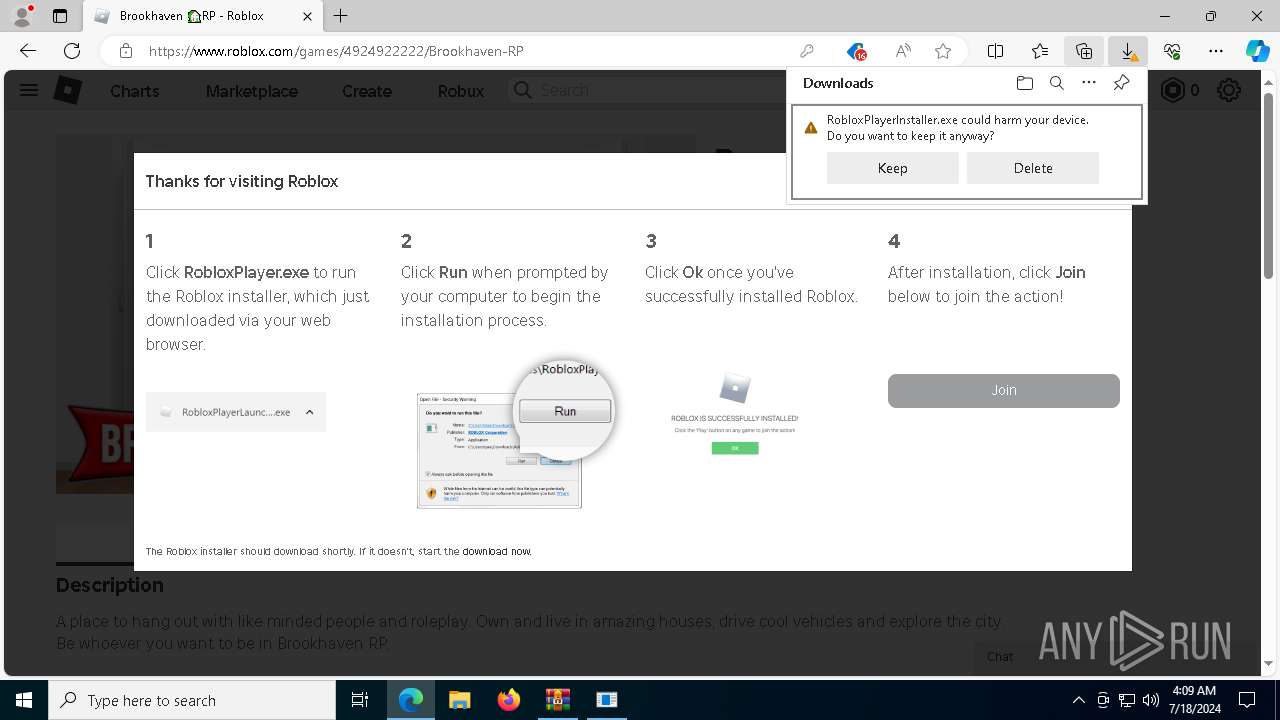
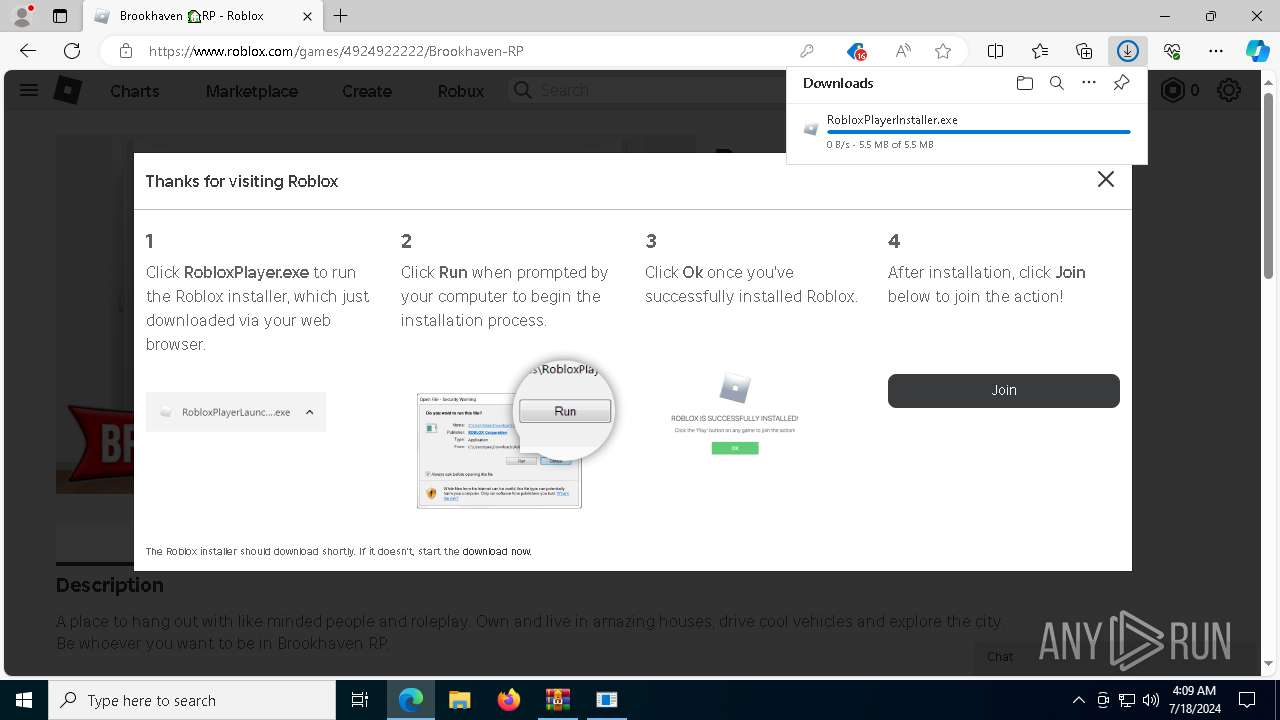
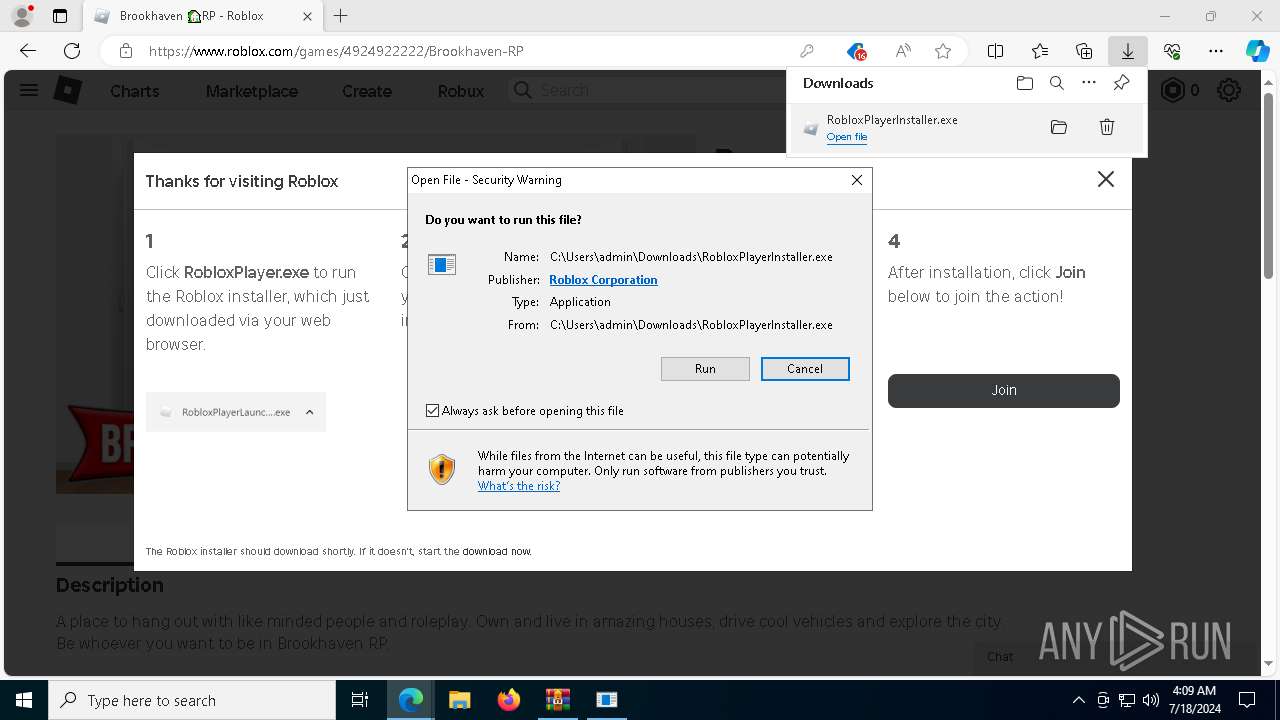
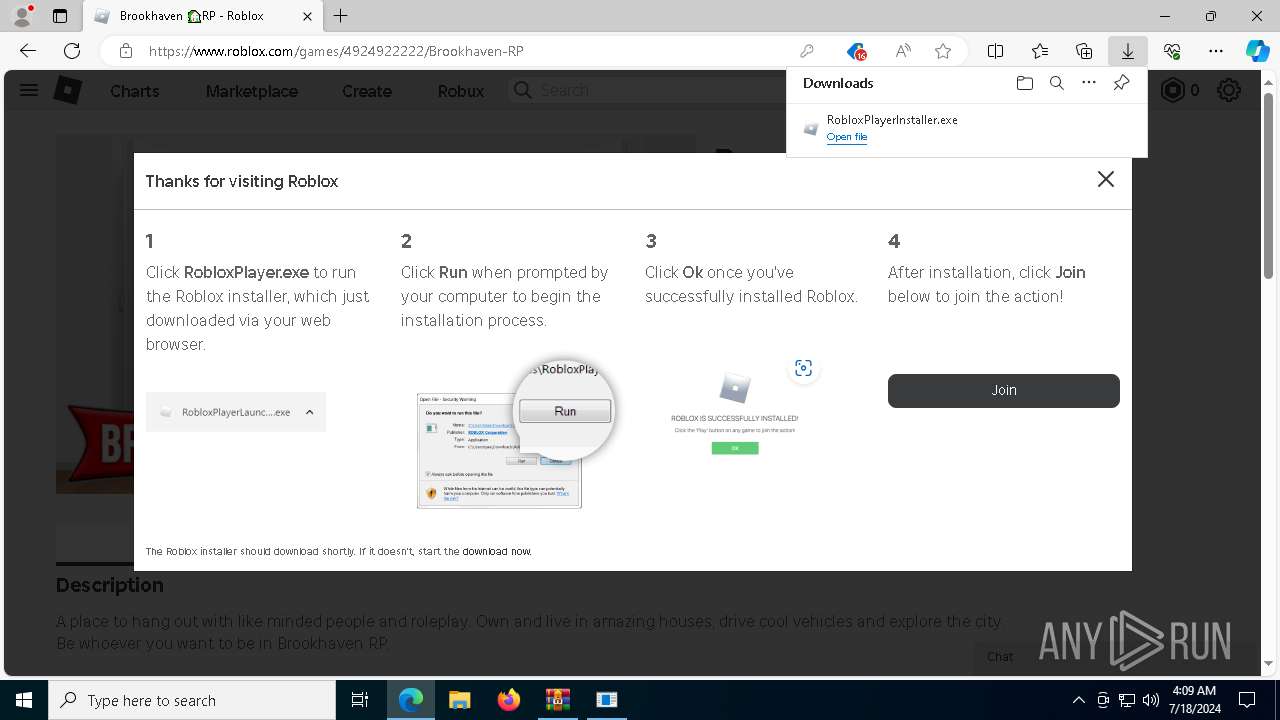
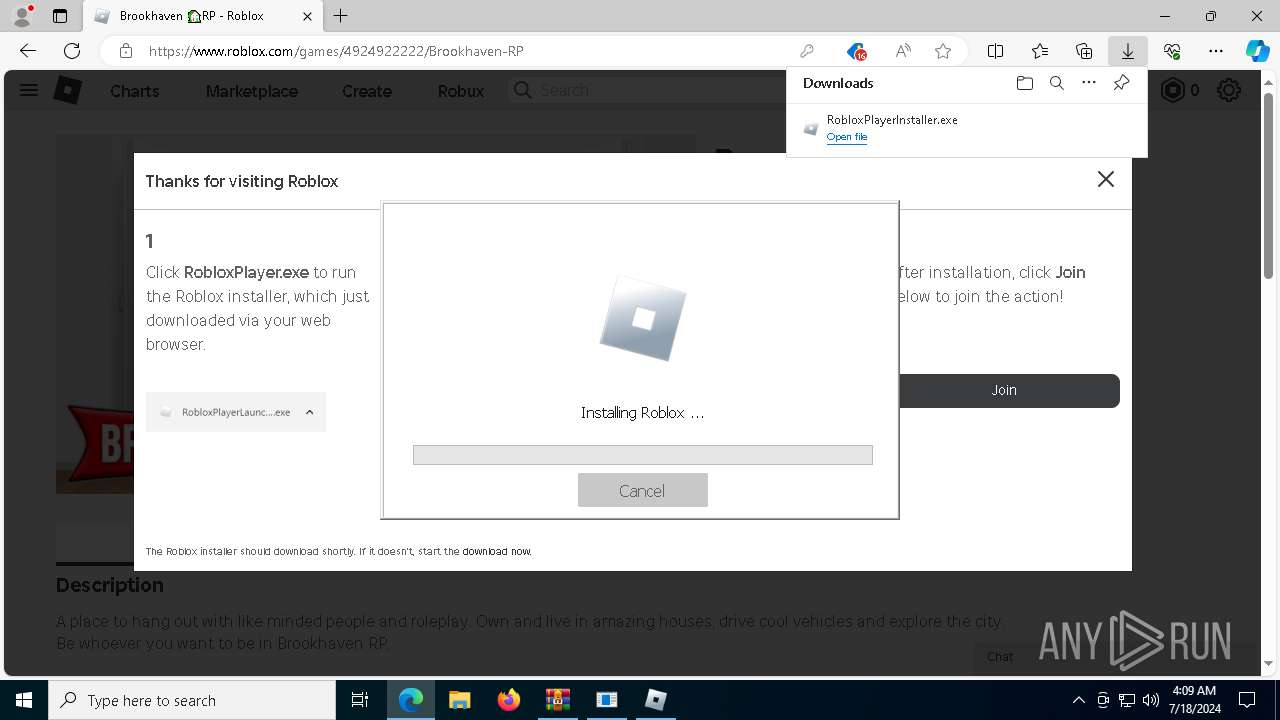
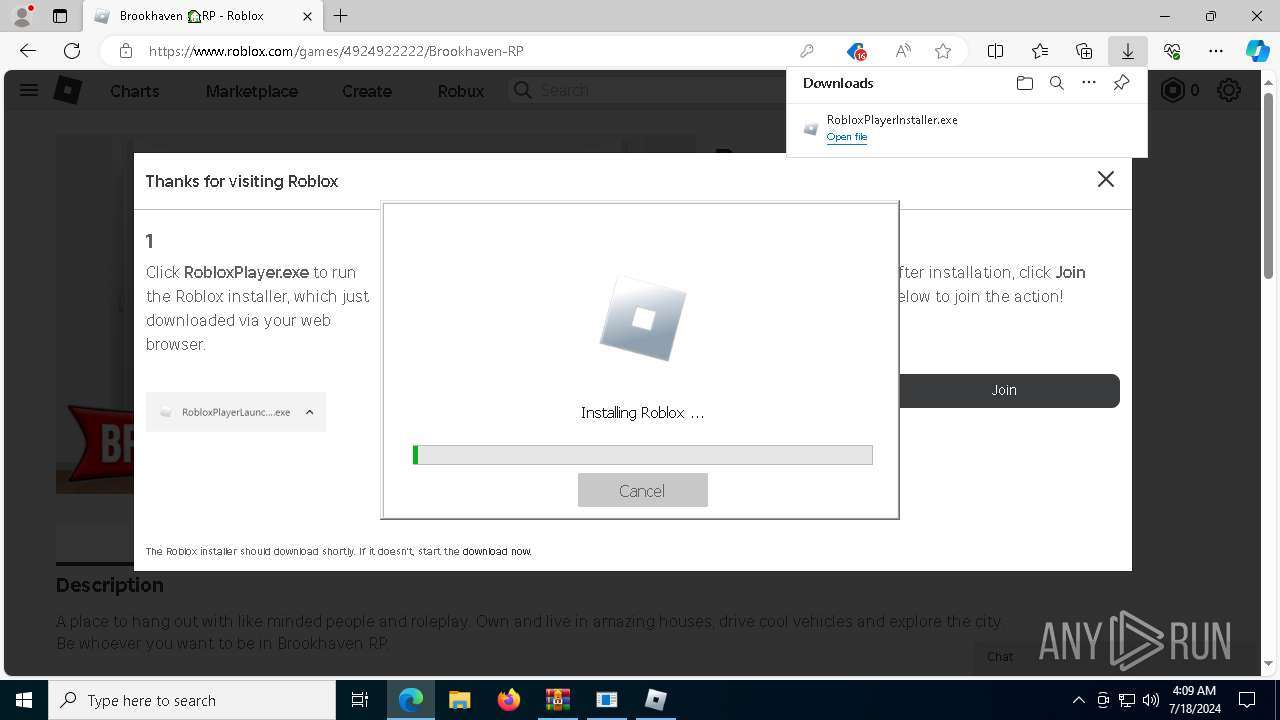
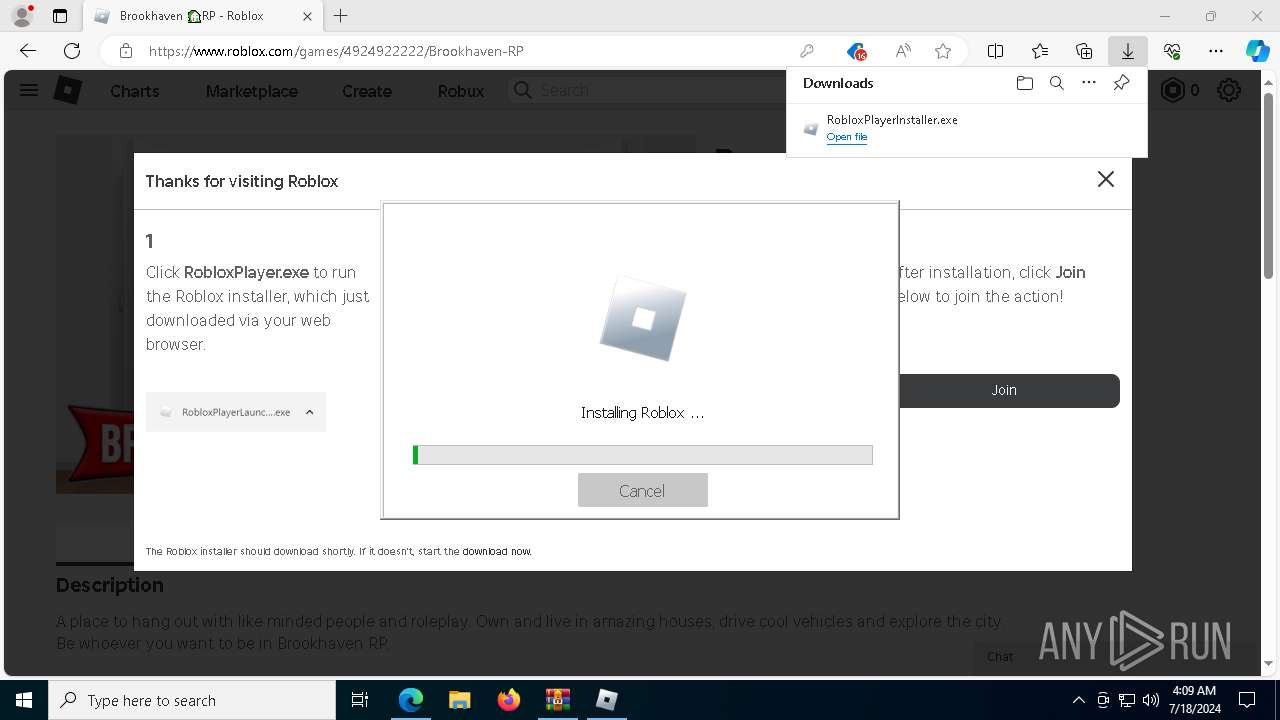
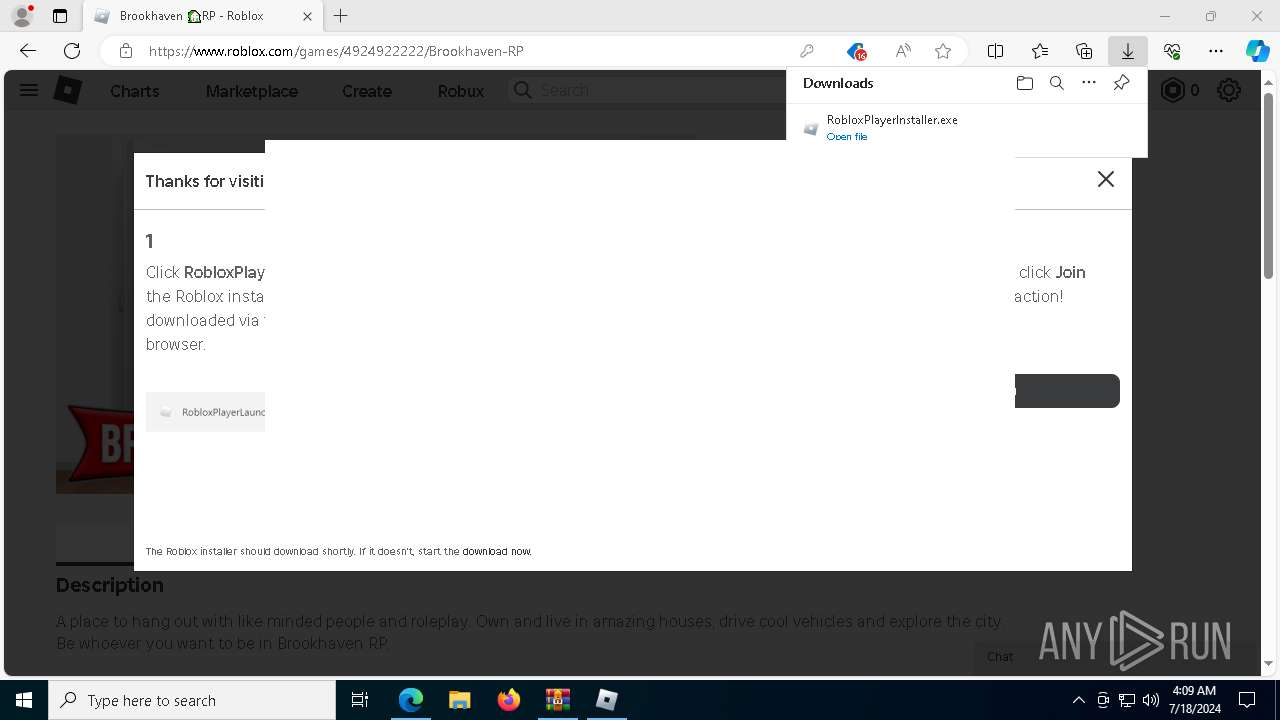
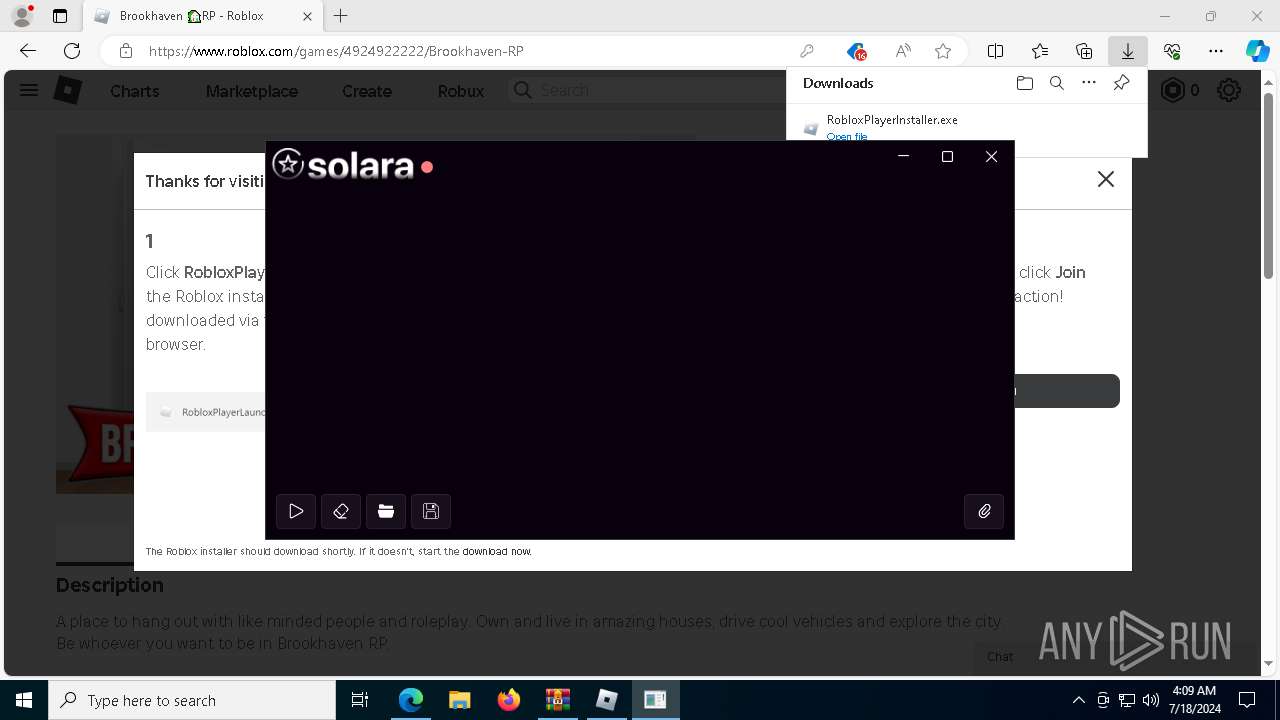
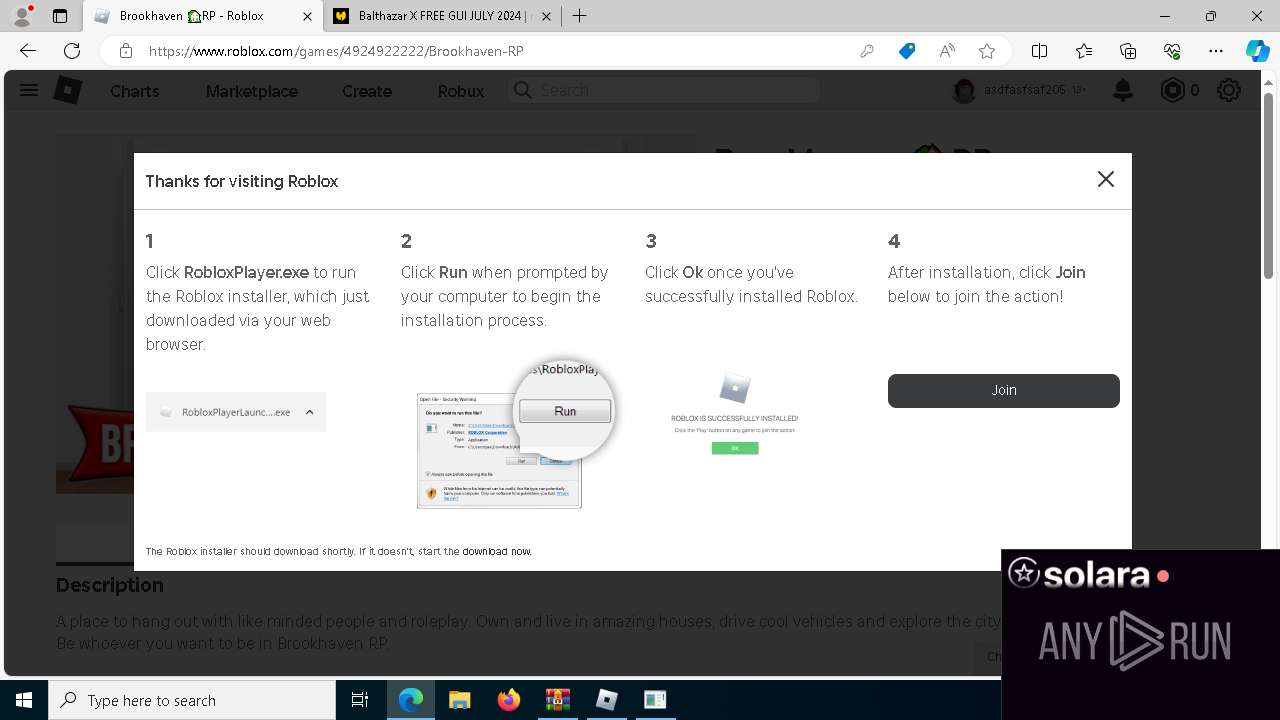
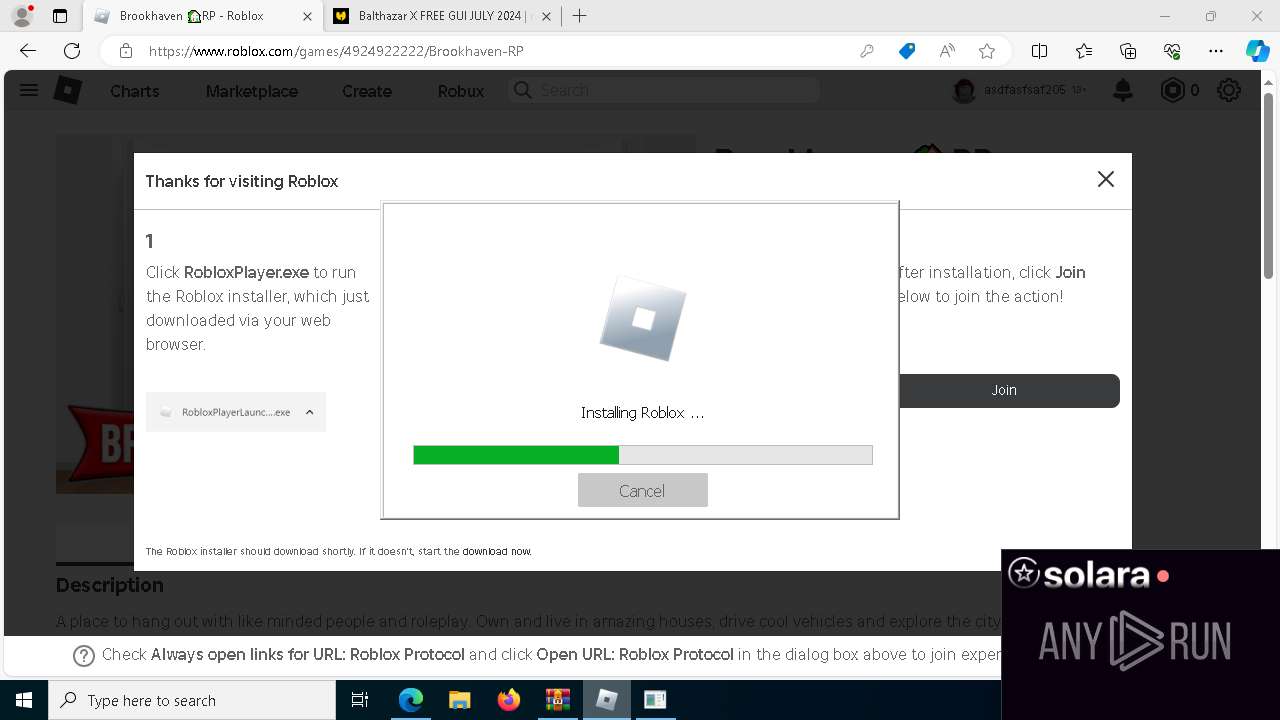
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1768)
- SolaraBootstrapper.exe (PID: 1300)
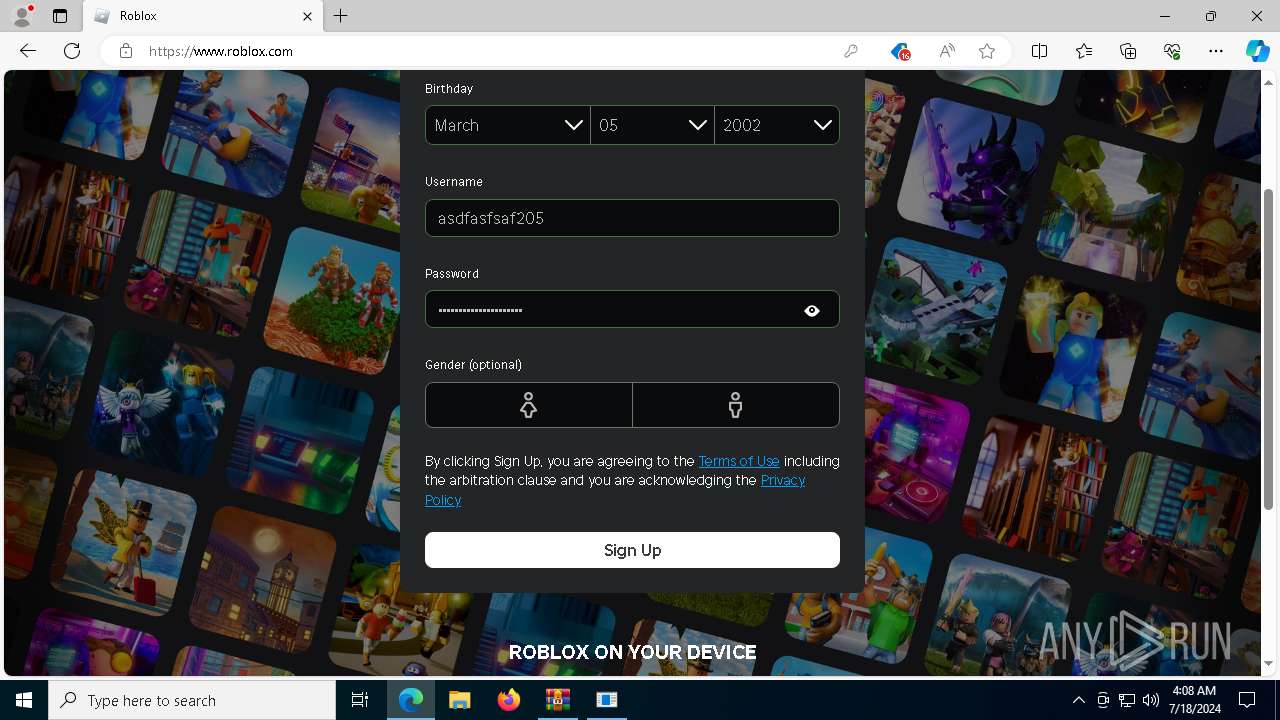
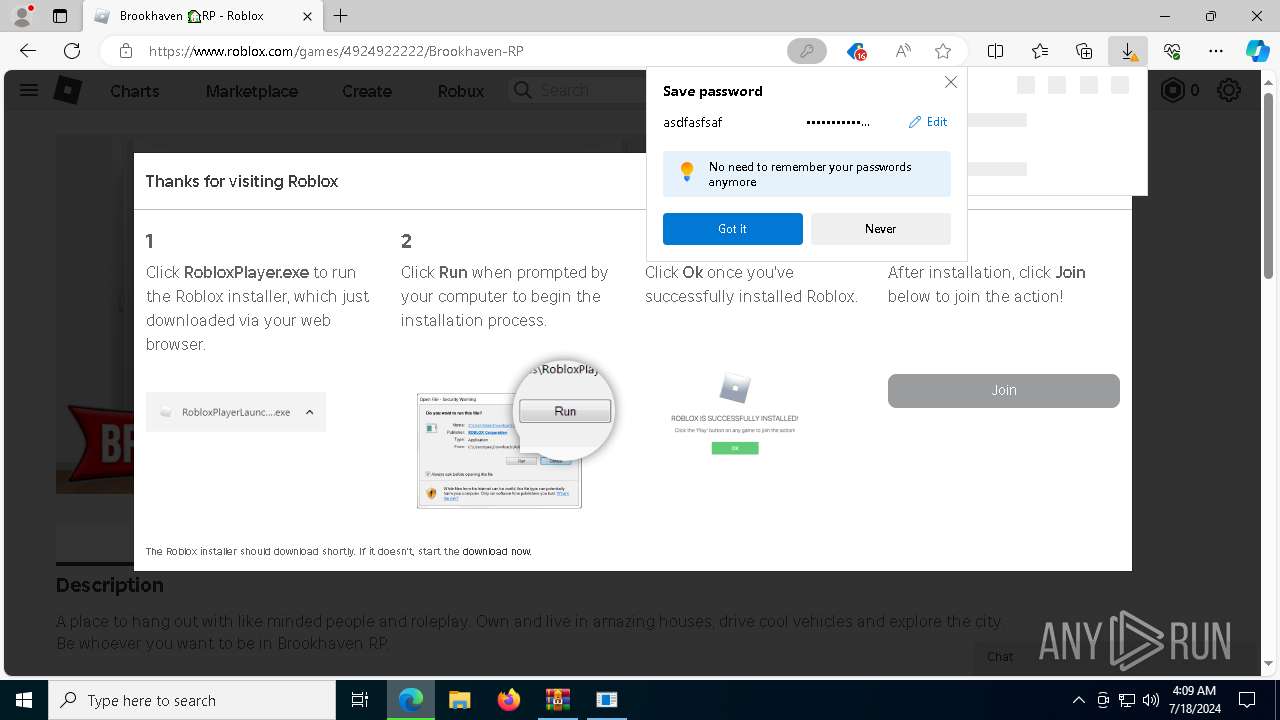
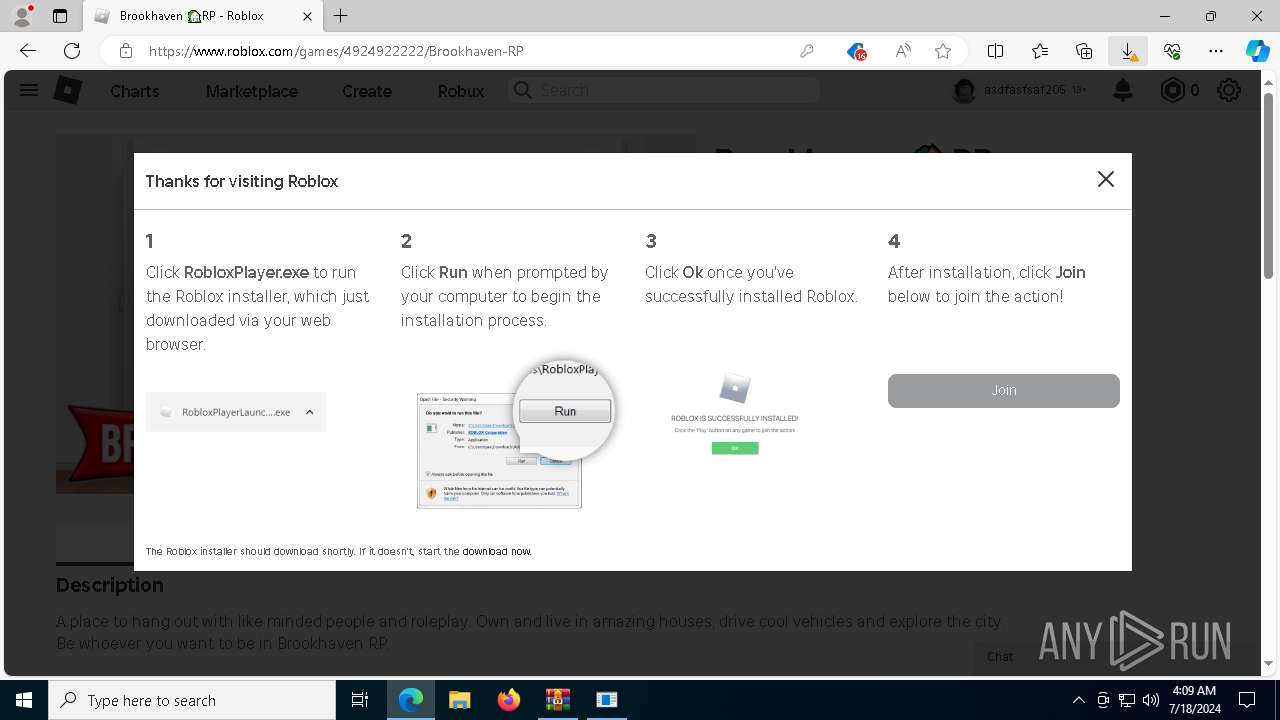
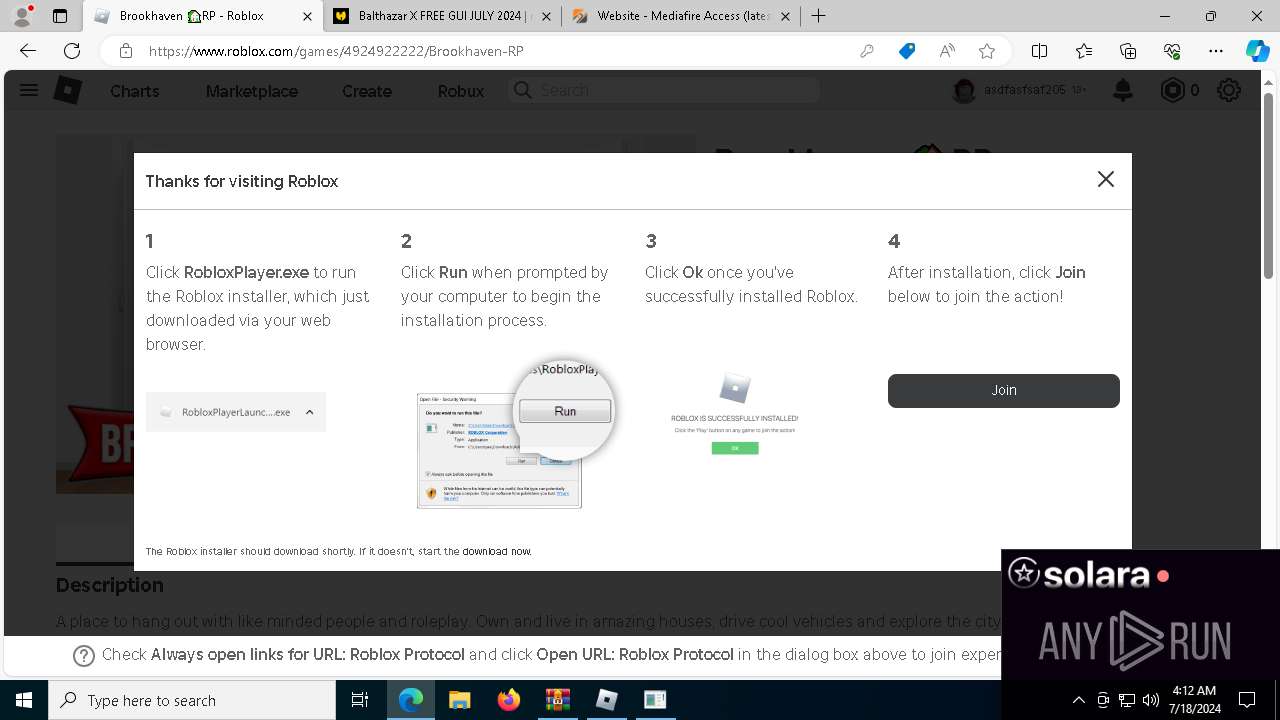
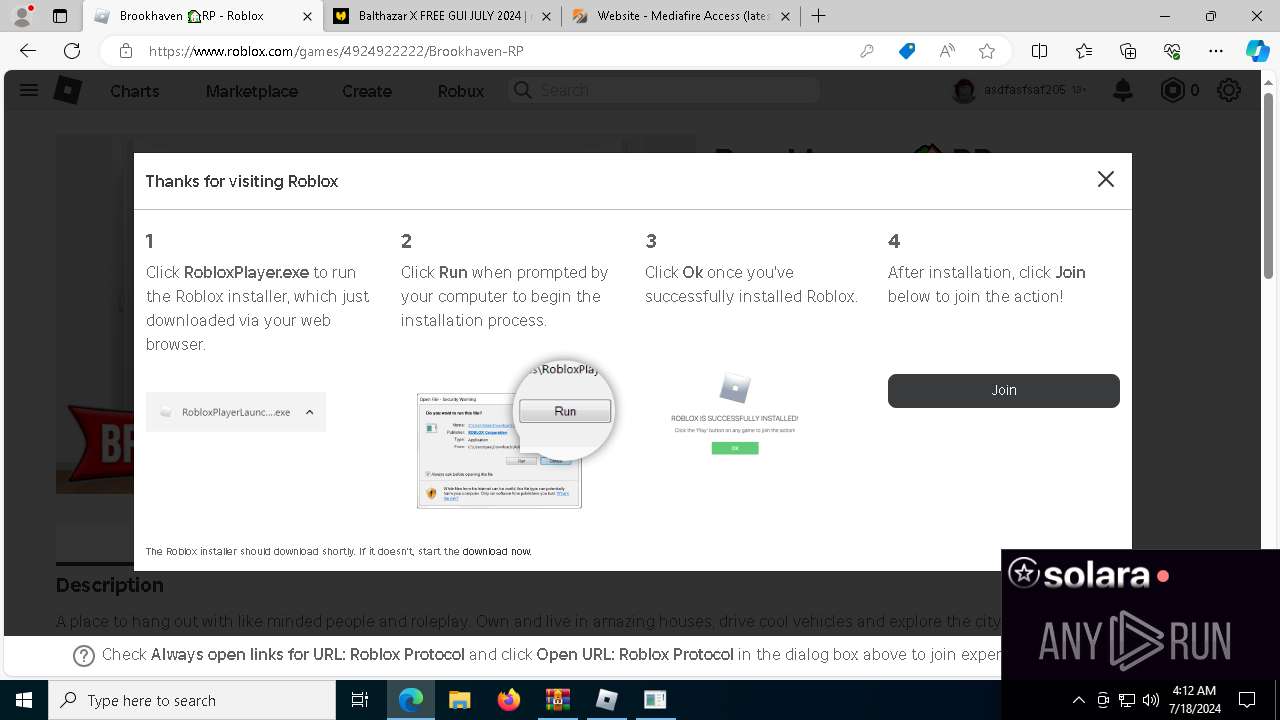
- RobloxPlayerInstaller.exe (PID: 7344)
- MicrosoftEdgeWebview2Setup.exe (PID: 6200)
- MicrosoftEdgeUpdate.exe (PID: 4452)
- MicrosoftEdge_X64_126.0.2592.102.exe (PID: 2056)
Actions looks like stealing of personal data
- RobloxPlayerInstaller.exe (PID: 7344)
Changes the autorun value in the registry
- MicrosoftEdgeUpdate.exe (PID: 4452)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1768)
- SolaraBootstrapper.exe (PID: 1300)
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 752)
- MicrosoftEdgeUpdate.exe (PID: 4452)
- MicrosoftEdgeUpdate.exe (PID: 6900)
Executable content was dropped or overwritten
- SolaraBootstrapper.exe (PID: 1300)
- RobloxPlayerInstaller.exe (PID: 7344)
- MicrosoftEdgeUpdate.exe (PID: 4452)
- MicrosoftEdgeWebview2Setup.exe (PID: 6200)
- MicrosoftEdge_X64_126.0.2592.102.exe (PID: 2056)
The process drops C-runtime libraries
- SolaraBootstrapper.exe (PID: 1300)
Process drops legitimate windows executable
- SolaraBootstrapper.exe (PID: 1300)
- RobloxPlayerInstaller.exe (PID: 7344)
- MicrosoftEdgeUpdate.exe (PID: 4452)
- MicrosoftEdgeWebview2Setup.exe (PID: 6200)
- MicrosoftEdge_X64_126.0.2592.102.exe (PID: 2056)
Reads the date of Windows installation
- SolaraBootstrapper.exe (PID: 1300)
- MicrosoftEdgeUpdate.exe (PID: 4452)
Changes default file association
- RobloxPlayerInstaller.exe (PID: 7344)
Reads the BIOS version
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 752)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 4452)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6644)
- MicrosoftEdgeUpdate.exe (PID: 6640)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6852)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 1972)
Starts a Microsoft application from unusual location
- MicrosoftEdgeUpdate.exe (PID: 4452)
Checks Windows Trust Settings
- MicrosoftEdgeUpdate.exe (PID: 6900)
Application launched itself
- setup.exe (PID: 7652)
INFO
Reads the computer name
- SolaraBootstrapper.exe (PID: 1300)
- identity_helper.exe (PID: 7612)
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 752)
- RobloxPlayerInstaller.exe (PID: 7344)
- MicrosoftEdgeUpdate.exe (PID: 6640)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6644)
- MicrosoftEdgeUpdate.exe (PID: 4452)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 1972)
- MicrosoftEdgeUpdate.exe (PID: 6856)
- MicrosoftEdgeUpdate.exe (PID: 6844)
- MicrosoftEdgeUpdate.exe (PID: 6900)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6852)
- MicrosoftEdge_X64_126.0.2592.102.exe (PID: 2056)
- setup.exe (PID: 7652)
Reads the machine GUID from the registry
- SolaraBootstrapper.exe (PID: 1300)
- RobloxPlayerInstaller.exe (PID: 7344)
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 752)
- MicrosoftEdgeUpdate.exe (PID: 6900)
Checks supported languages
- SolaraBootstrapper.exe (PID: 1300)
- identity_helper.exe (PID: 7612)
- RobloxPlayerInstaller.exe (PID: 7344)
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 752)
- MicrosoftEdgeWebview2Setup.exe (PID: 6200)
- MicrosoftEdgeUpdate.exe (PID: 6640)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6644)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6852)
- MicrosoftEdgeUpdate.exe (PID: 4452)
- MicrosoftEdgeUpdate.exe (PID: 6856)
- MicrosoftEdgeUpdate.exe (PID: 6844)
- MicrosoftEdgeUpdate.exe (PID: 6900)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 1972)
- MicrosoftEdge_X64_126.0.2592.102.exe (PID: 2056)
- setup.exe (PID: 7652)
- setup.exe (PID: 7044)
Disables trace logs
- SolaraBootstrapper.exe (PID: 1300)
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 752)
Checks proxy server information
- SolaraBootstrapper.exe (PID: 1300)
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 752)
- slui.exe (PID: 6892)
- MicrosoftEdgeUpdate.exe (PID: 6856)
- MicrosoftEdgeUpdate.exe (PID: 6900)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1768)
- msedge.exe (PID: 3168)
Reads Environment values
- SolaraBootstrapper.exe (PID: 1300)
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 752)
- MicrosoftEdgeUpdate.exe (PID: 6856)
Manual execution by a user
- msedge.exe (PID: 3168)
Reads Microsoft Office registry keys
- msedge.exe (PID: 3168)
Reads the software policy settings
- SolaraBootstrapper.exe (PID: 1300)
- cd57e4c171d6e8f5ea8b8f824a6a7316.exe (PID: 752)
- slui.exe (PID: 3656)
- slui.exe (PID: 6892)
- MicrosoftEdgeUpdate.exe (PID: 6856)
- MicrosoftEdgeUpdate.exe (PID: 6900)
Create files in a temporary directory
- SolaraBootstrapper.exe (PID: 1300)
- RobloxPlayerInstaller.exe (PID: 7344)
- MicrosoftEdgeWebview2Setup.exe (PID: 6200)
- MicrosoftEdgeUpdate.exe (PID: 4452)
Dropped object may contain TOR URL's
- SolaraBootstrapper.exe (PID: 1300)
Application launched itself
- msedge.exe (PID: 3168)
Drops the executable file immediately after the start
- msedge.exe (PID: 3168)
- msedge.exe (PID: 1848)
- msedge.exe (PID: 4152)
The process uses the downloaded file
- msedge.exe (PID: 3168)
- msedge.exe (PID: 8088)
Creates files or folders in the user directory
- RobloxPlayerInstaller.exe (PID: 7344)
- MicrosoftEdgeUpdate.exe (PID: 4452)
- MicrosoftEdgeUpdate.exe (PID: 6900)
- MicrosoftEdge_X64_126.0.2592.102.exe (PID: 2056)
- setup.exe (PID: 7652)
- setup.exe (PID: 7044)
Process checks computer location settings
- SolaraBootstrapper.exe (PID: 1300)
- MicrosoftEdgeUpdate.exe (PID: 4452)
Process checks whether UAC notifications are on
- RobloxPlayerInstaller.exe (PID: 7344)
Attempting to use instant messaging service
- msedge.exe (PID: 1848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:05:19 18:25:22 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
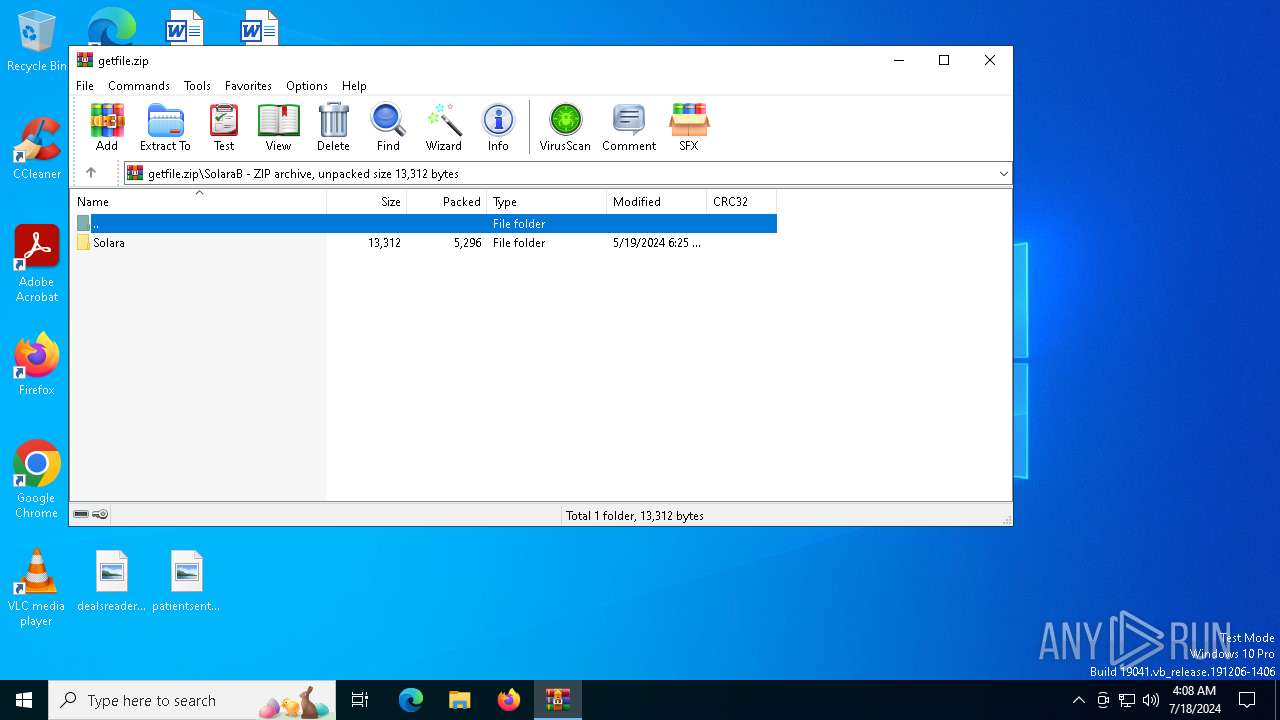
| ZipFileName: | SolaraB/Solara/ |
Total processes
259
Monitored processes
113
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 608 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=5888 --field-trial-handle=2436,i,16632872611704203952,2658074936895250651,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 608 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=71 --mojo-platform-channel-handle=9240 --field-trial-handle=2436,i,16632872611704203952,2658074936895250651,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 752 | "C:\Users\admin\AppData\Local\Temp\Solara.Dir\cd57e4c171d6e8f5ea8b8f824a6a7316.exe" | C:\Users\admin\AppData\Local\Temp\Solara.Dir\cd57e4c171d6e8f5ea8b8f824a6a7316.exe | SolaraBootstrapper.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: WpfApp1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1048 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3488 --field-trial-handle=2436,i,16632872611704203952,2658074936895250651,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1112 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=9400 --field-trial-handle=2436,i,16632872611704203952,2658074936895250651,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1188 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3644 --field-trial-handle=2436,i,16632872611704203952,2658074936895250651,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1280 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=49 --mojo-platform-channel-handle=3892 --field-trial-handle=2436,i,16632872611704203952,2658074936895250651,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
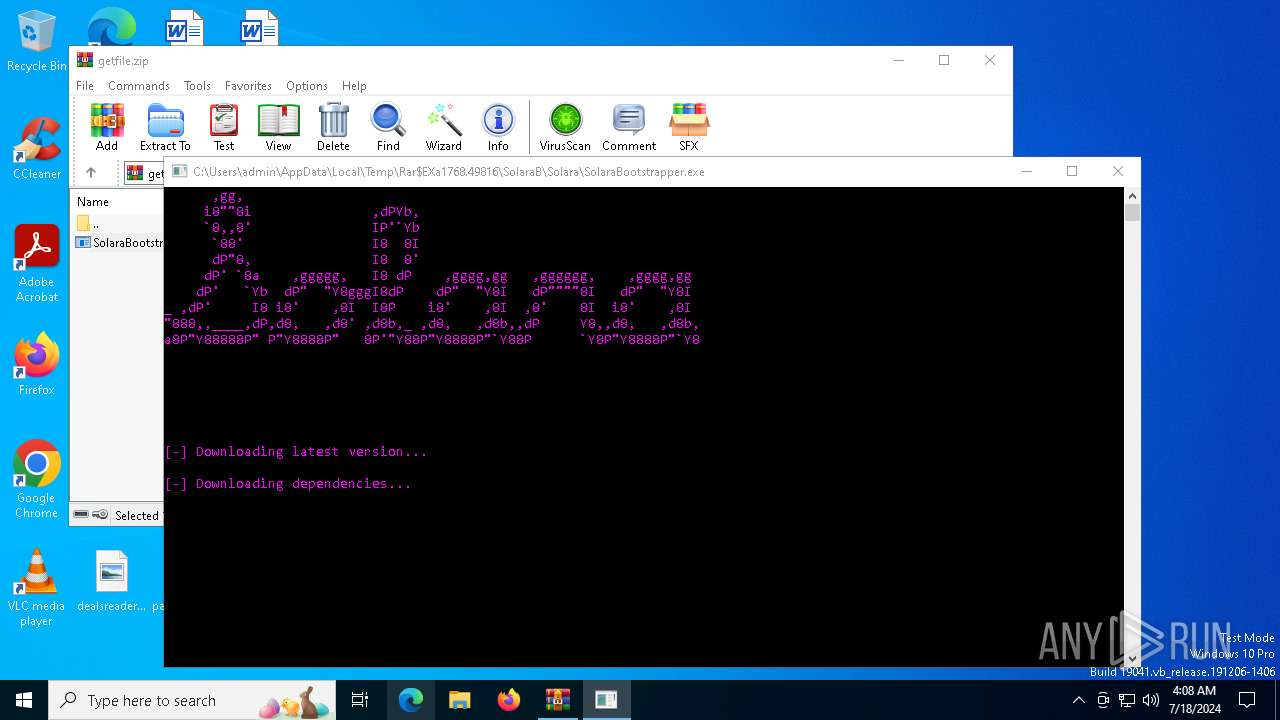
| 1300 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1768.49816\SolaraB\Solara\SolaraBootstrapper.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1768.49816\SolaraB\Solara\SolaraBootstrapper.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: SolaraBootstrapper Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1768 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\getfile.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1784 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=9600 --field-trial-handle=2436,i,16632872611704203952,2658074936895250651,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
47 260
Read events
43 532
Write events
3 678
Delete events
50
Modification events
| (PID) Process: | (1768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\getfile.zip | |||
| (PID) Process: | (1768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1768) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
239
Suspicious files
1 393
Text files
572
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1d258c.TMP | — | |
MD5:— | SHA256:— | |||
| 3168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1d258c.TMP | — | |
MD5:— | SHA256:— | |||
| 3168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1d258c.TMP | — | |
MD5:— | SHA256:— | |||
| 3168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1d258c.TMP | — | |
MD5:— | SHA256:— | |||
| 3168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1d259b.TMP | — | |
MD5:— | SHA256:— | |||
| 3168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3168 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
68
TCP/UDP connections
480
DNS requests
637
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
528 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
528 | svchost.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3944 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1848 | msedge.exe | GET | 304 | 72.246.169.163:80 | http://r3.i.lencr.org/ | unknown | — | — | whitelisted |
1848 | msedge.exe | GET | 304 | 72.246.169.163:80 | http://x1.i.lencr.org/ | unknown | — | — | whitelisted |
1848 | msedge.exe | GET | 304 | 195.138.255.24:80 | http://apps.identrust.com/roots/dstrootcax3.p7c | unknown | — | — | whitelisted |
6596 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5872 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5872 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6684 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
528 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4656 | SearchApp.exe | 2.23.209.189:443 | www.bing.com | Akamai International B.V. | GB | unknown |
4820 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
368 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 2.23.209.189:443 | www.bing.com | Akamai International B.V. | GB | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
528 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
528 | svchost.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
github.com |
| shared |
raw.githubusercontent.com |
| shared |
config.edge.skype.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
1848 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
1848 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
1848 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
1848 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
1848 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
1848 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
1848 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
1848 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
Process | Message |
|---|---|
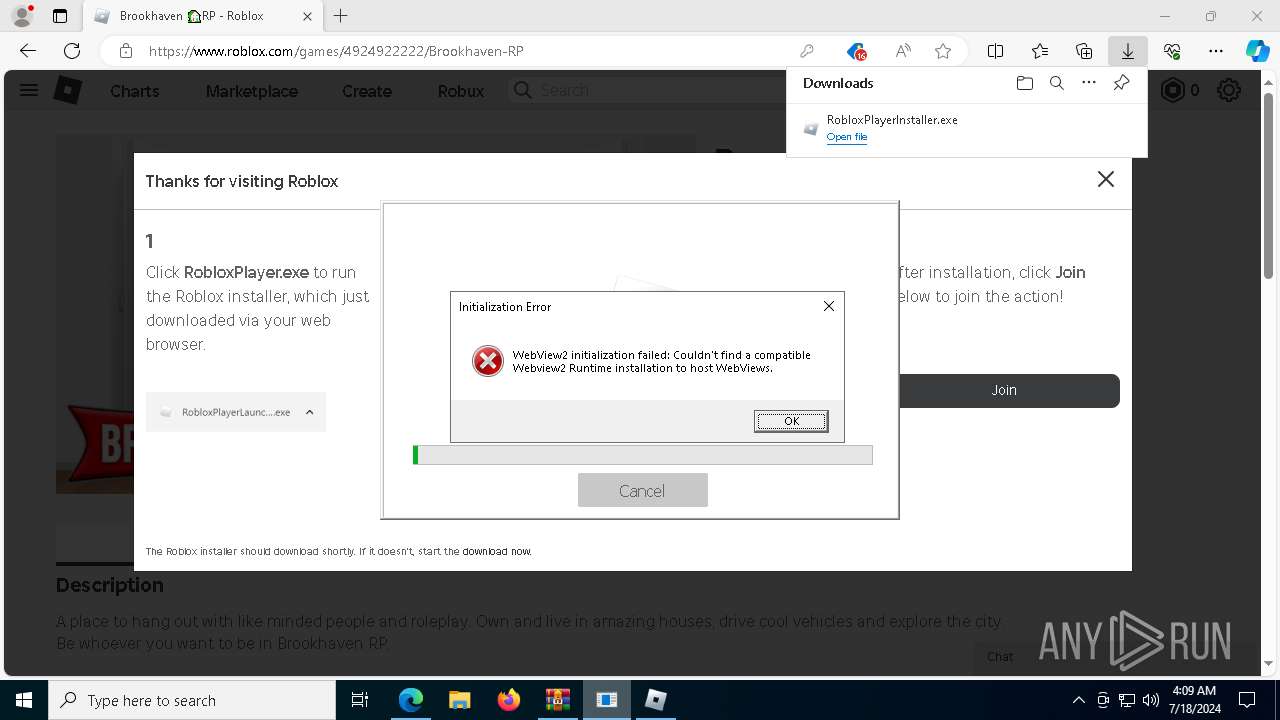
RobloxPlayerInstaller.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|