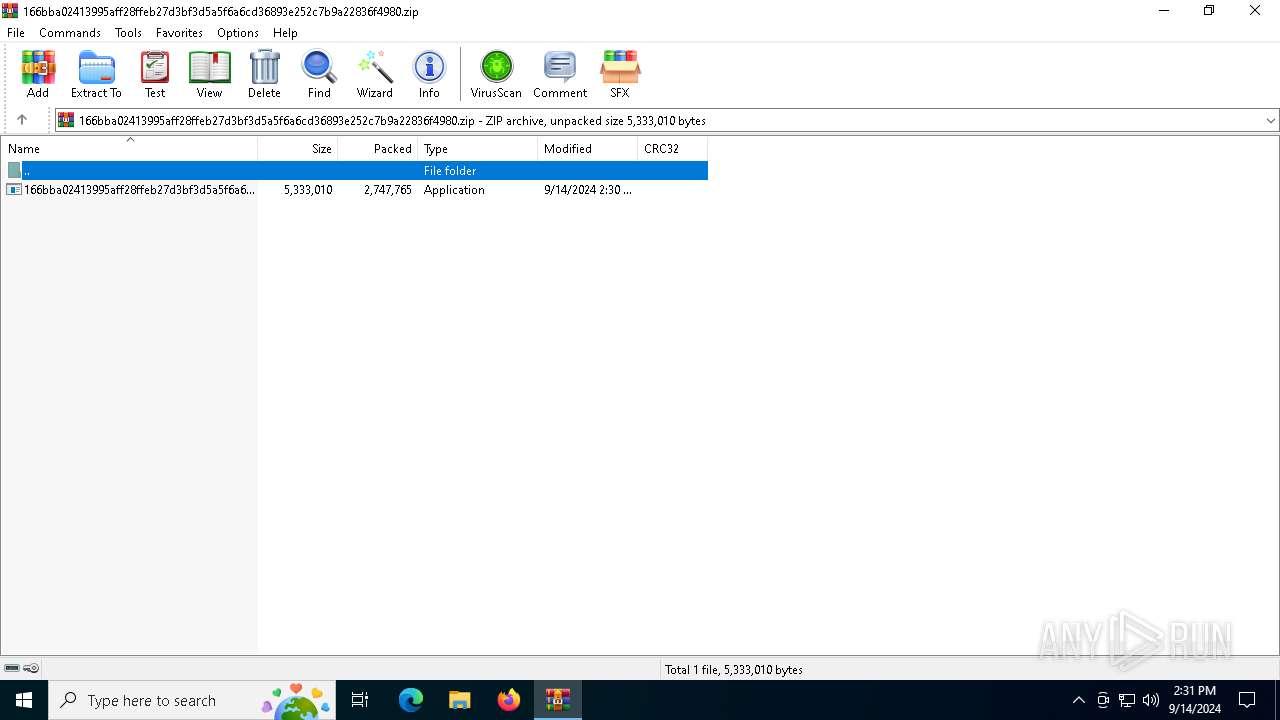
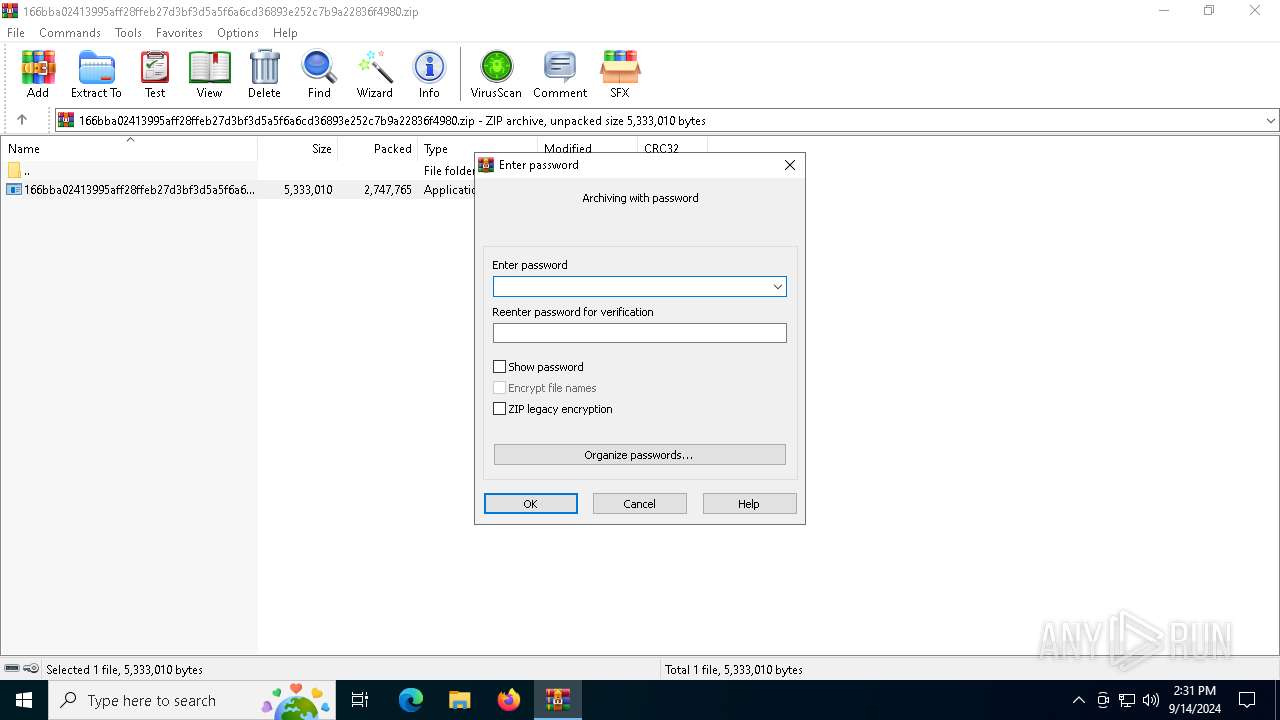
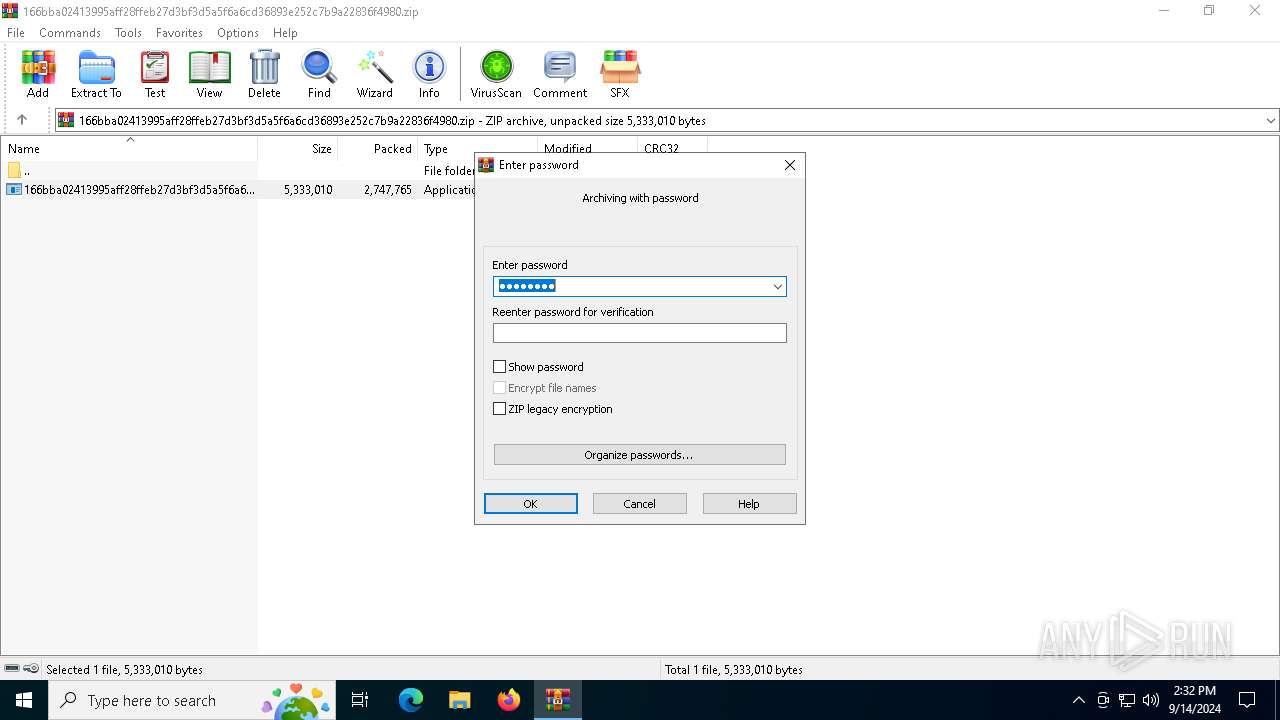
| File name: | 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.zip |
| Full analysis: | https://app.any.run/tasks/b905f88e-b416-45e4-ab2d-726480dcbff9 |
| Verdict: | Malicious activity |
| Analysis date: | September 14, 2024, 14:31:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | B33C0CCB43518CAB1CDC38D8440E19C7 |
| SHA1: | 59405CB357BE060E151F1B2ABDDBF3674857D250 |
| SHA256: | 24E21BBC6BB44459AEC17332F13AE8A27A2A628834BFD8F7B2875933F783AA66 |
| SSDEEP: | 98304:yYdkOcQkm46FYlZss01Njh6bvyNgM/nrhMY2fxpPba84ZGoKxRt5DPhnQPUDYfsp:YFGIuUsOLEO |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
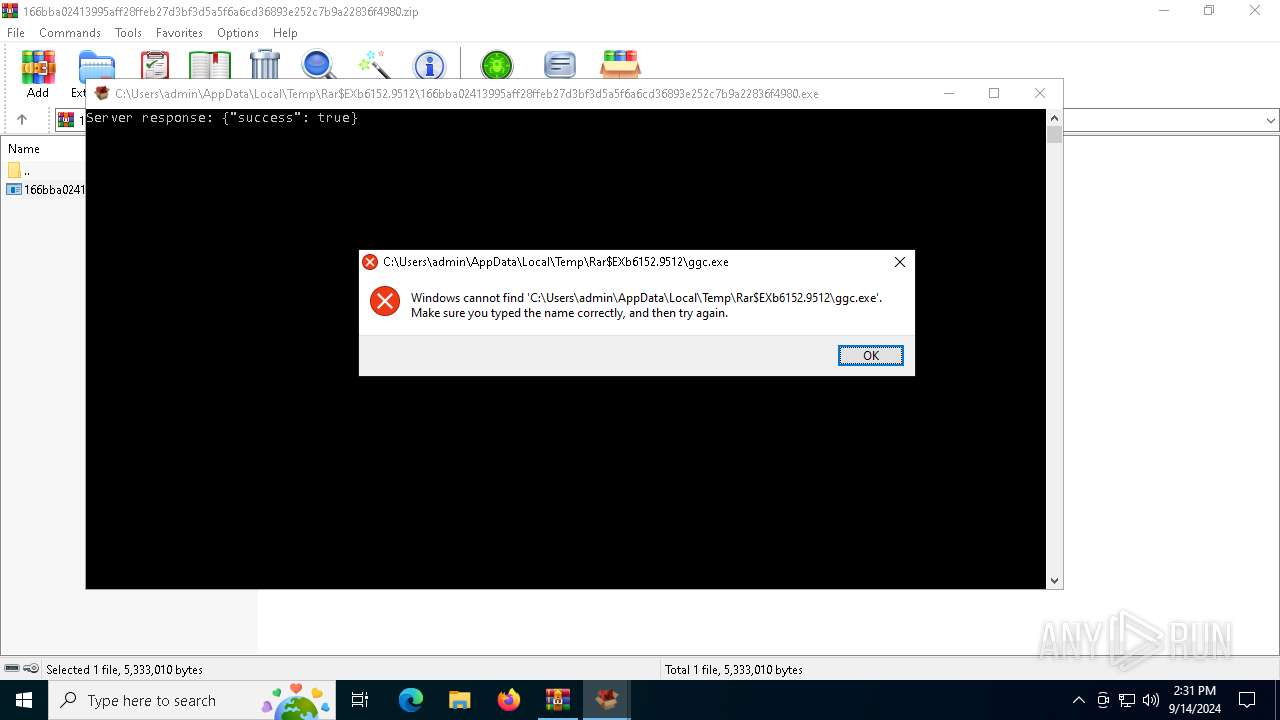
- WinRAR.exe (PID: 6152)
- 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe (PID: 5768)
Reads the date of Windows installation
- 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe (PID: 5768)
Checks Windows Trust Settings
- 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe (PID: 5768)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6152)
The process uses the downloaded file
- WinRAR.exe (PID: 6152)
- 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe (PID: 5768)
Reads the computer name
- 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe (PID: 5768)
Reads the machine GUID from the registry
- 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe (PID: 5768)
Create files in a temporary directory
- 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe (PID: 5768)
Reads the software policy settings
- 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe (PID: 5768)
Process checks computer location settings
- 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe (PID: 5768)
Checks proxy server information
- 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe (PID: 5768)
Checks supported languages
- 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe (PID: 5768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:09:14 14:30:12 |
| ZipCRC: | 0xc1ac975b |
| ZipCompressedSize: | 2747765 |
| ZipUncompressedSize: | 5333010 |
| ZipFileName: | 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe |
Total processes
127
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
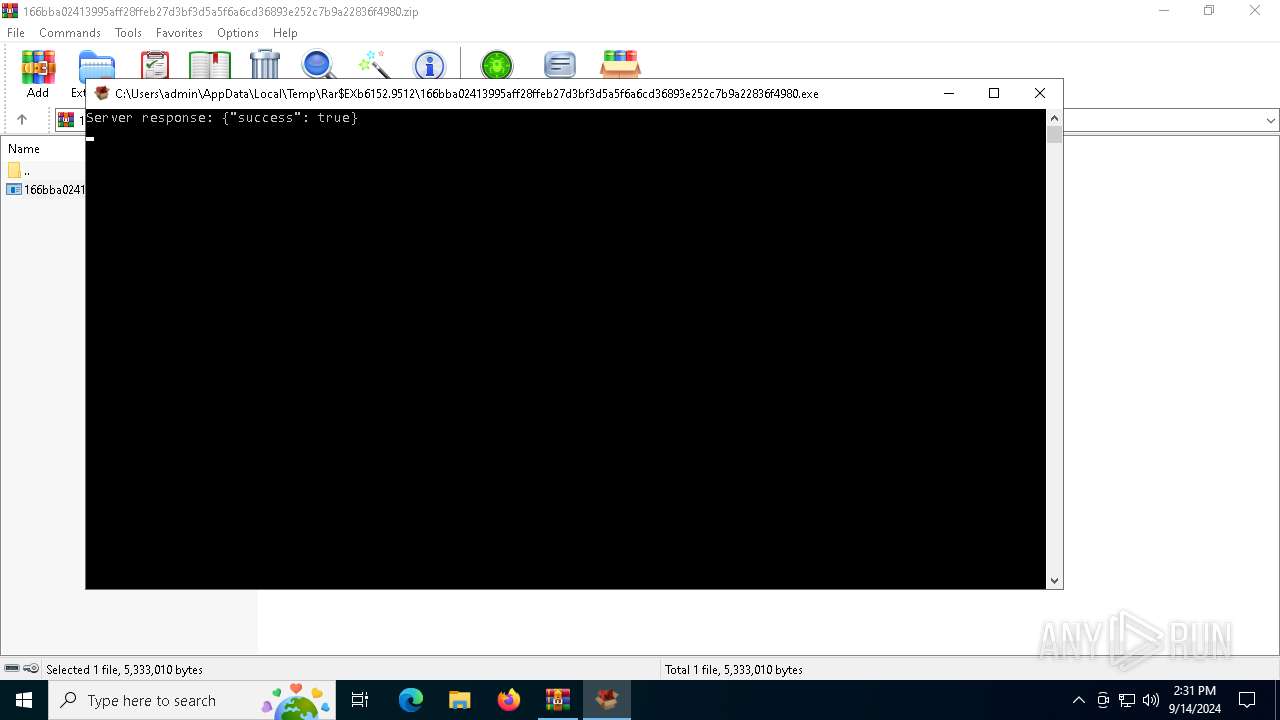
| 5768 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb6152.9512\166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb6152.9512\166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6152 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6884 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 955
Read events
2 944
Write events
11
Delete events
0
Modification events
| (PID) Process: | (6152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.zip | |||
| (PID) Process: | (6152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
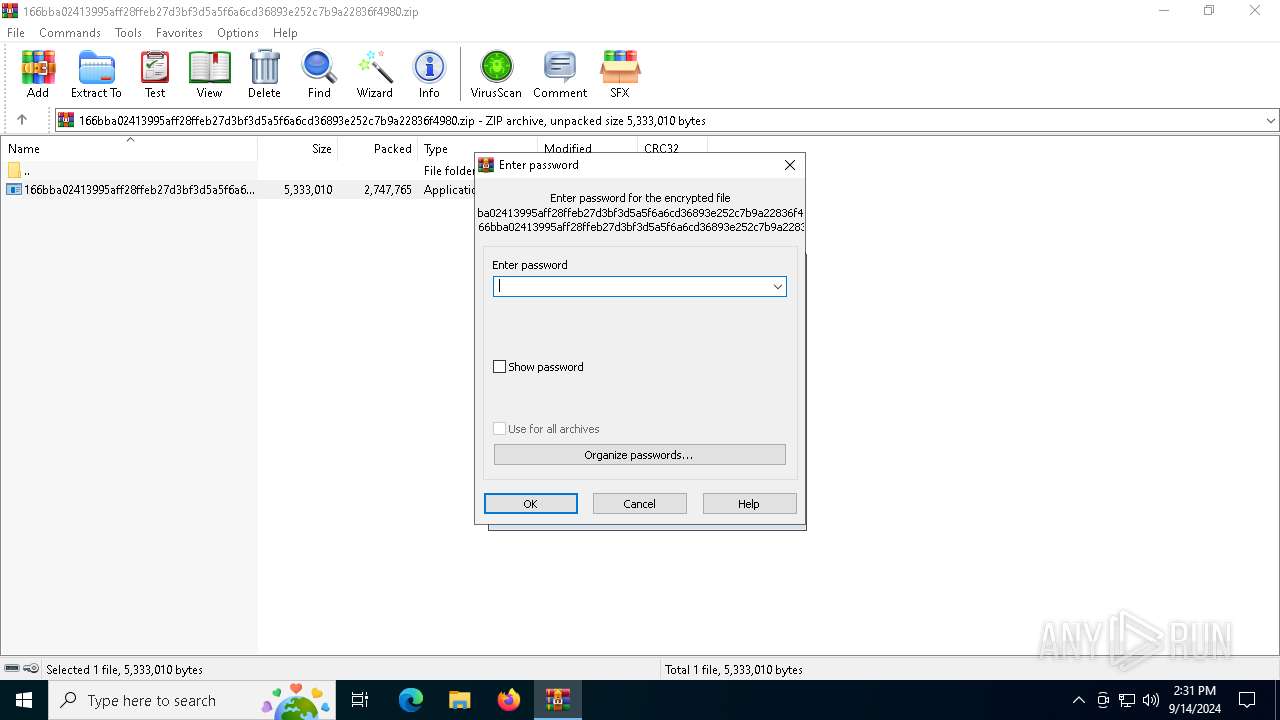
| (PID) Process: | (6152) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5768) 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5768) 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5768) 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
1
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5768 | 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:3DFCA46E00FFA4795C72A41375F159D3 | SHA256:DCBA1A505396539BAC40A7253C9F5DCCF06CBB79957E21D56305E1FC3AF5F40E | |||
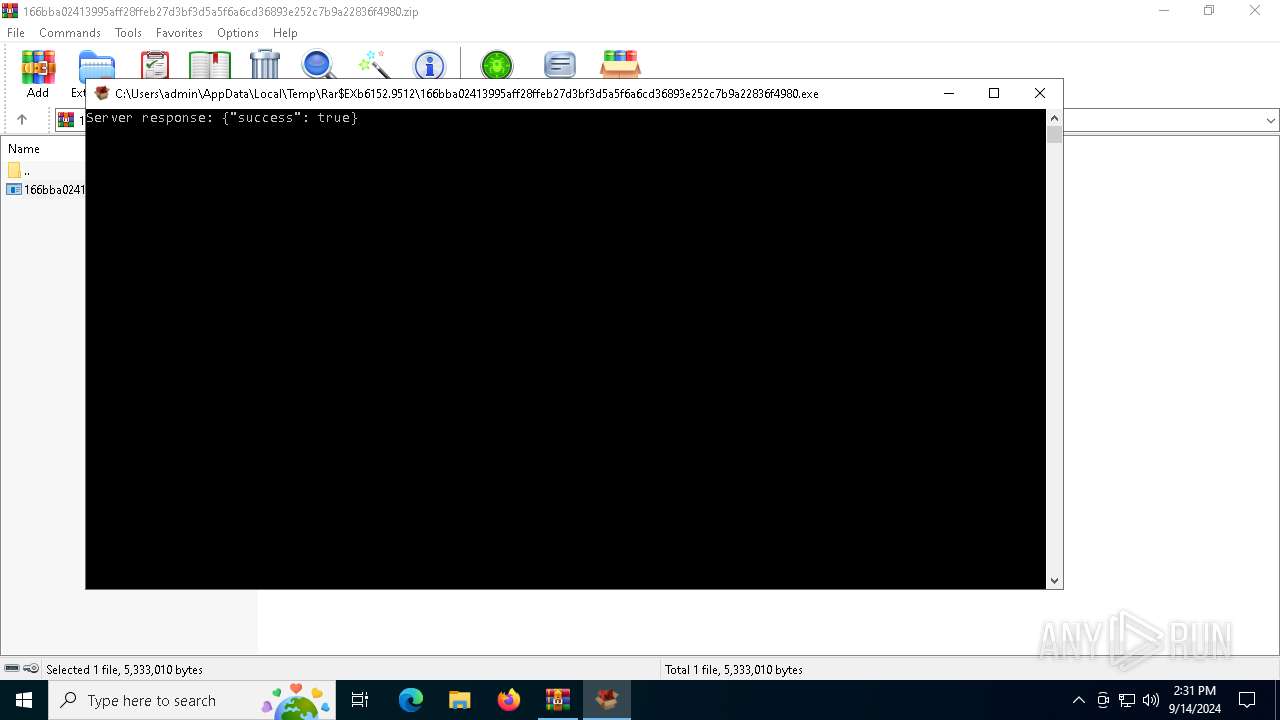
| 5768 | 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6152.9512\ggc.exe | text | |
MD5:CC1B29E9EE4DD33C08EDB1F55EB719DD | SHA256:8F998FFA9AC3628EFB50627E75CEF69156C7651D1E7B3B37AF6069E1104BCA04 | |||
| 6152 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb6152.9512\166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe | executable | |
MD5:BE8BF725892DDD7A200D0A1906B9387F | SHA256:166BBA02413995AFF28FFEB27D3BF3D5A5F6A6CD36893E252C7B9A22836F4980 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
32
DNS requests
17
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6876 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1440 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3908 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3908 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6876 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4132 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6876 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6876 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5768 | 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe | 198.49.23.144:443 | www.kenesrakishevinfo.com | SQUARESPACE | US | malicious |
5768 | 166bba02413995aff28ffeb27d3bf3d5a5f6a6cd36893e252c7b9a22836f4980.exe | 76.76.21.98:443 | master-repogen.vercel.app | AMAZON-02 | US | malicious |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.kenesrakishevinfo.com |
| malicious |
master-repogen.vercel.app |
| malicious |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Canva designs and to share platform (static .canva .com) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloud infrastructure to build app (vercel .app) |