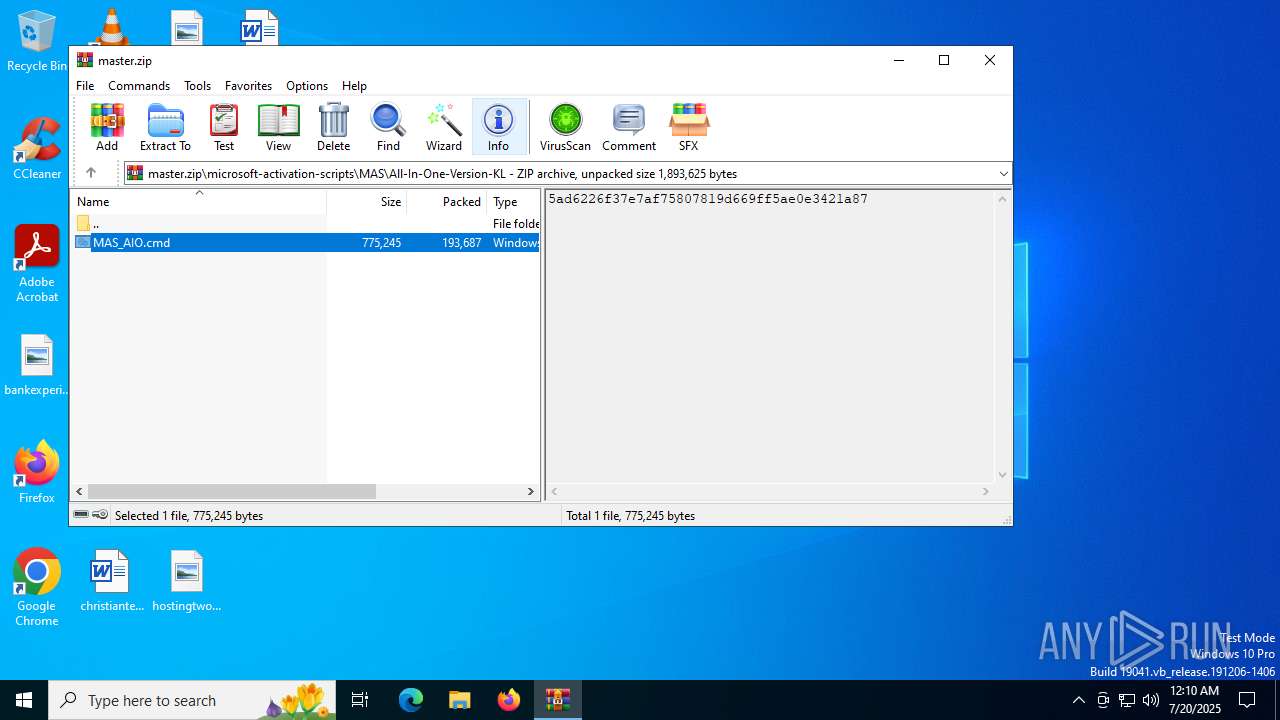
| download: | /massgrave/Microsoft-Activation-Scripts/archive/master.zip |
| Full analysis: | https://app.any.run/tasks/c7739a5a-043f-42b4-83ea-9e0768b3a04e |
| Verdict: | Malicious activity |
| Analysis date: | July 20, 2025, 00:09:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 735CBD090120D0435773356F78438B2A |
| SHA1: | 98659DA780E57AE466498548AC1CEB36996374E5 |
| SHA256: | 24E0B8CBB2734CA702515782F2EDAA4EA235D79F09EC0968F93B98862FF1B270 |
| SSDEEP: | 24576:dF5nJqS522wbbO/rvUezzyH61fqD818CCgDLBwK9tZ:dHnJqS522wbbO/rvUeX0AfqD818CC6L1 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3000)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3000)
Windows service management via SC.EXE
- sc.exe (PID: 1668)
Starts SC.EXE for service management
- cmd.exe (PID: 6724)
Executing commands from ".cmd" file
- WinRAR.exe (PID: 3000)
- cmd.exe (PID: 6724)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3000)
- cmd.exe (PID: 6724)
- cmd.exe (PID: 6732)
Application launched itself
- cmd.exe (PID: 6724)
- cmd.exe (PID: 6732)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6724)
INFO
Checks operating system version
- cmd.exe (PID: 6724)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:06:03 13:07:58 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | microsoft-activation-scripts/ |
Total processes
153
Monitored processes
17
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 892 | C:\WINDOWS\System32\cmd.exe /c ver | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1668 | sc query Null | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3000 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\master.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3392 | cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3656 | findstr /v "f7f81a39-5f63-5b42-9efd-1f13b5431005quot; "MAS_AIO.cmd" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3800 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3888 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4024 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "AMD64 " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4540 | find /i "RUNNING" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5084 | find /i "C:\Users\admin\AppData\Local\Temp" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 380
Read events
3 364
Write events
3
Delete events
13
Modification events
| (PID) Process: | (3000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (3000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (3000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (3000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
| (PID) Process: | (3000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 11 |
Value: | |||
| (PID) Process: | (3000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 10 |
Value: | |||
| (PID) Process: | (3000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 9 |
Value: | |||
| (PID) Process: | (3000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 8 |
Value: | |||
| (PID) Process: | (3000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 7 |
Value: | |||
| (PID) Process: | (3000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 6 |
Value: | |||
Executable files
0
Suspicious files
0
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\master\microsoft-activation-scripts\MAS\Separate-Files-Version\Activators\KMS38_Activation.cmd | text | |
MD5:A27233F975B0A862258850306428D8A8 | SHA256:FFF7663C7B60D04165DD9EFA1BD4A49C1DF22B9E30E0823CC1D162AA21216651 | |||
| 3000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\master\microsoft-activation-scripts\MAS\Separate-Files-Version\Change_Office_Edition.cmd | text | |
MD5:B1217CDA512BD1DC8B8CBAE24EC24F23 | SHA256:6478328076C5CBA9CA91CDCB4B4BE4A677EF390256E710DFD3B5B72FF9B07739 | |||
| 3000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\master\microsoft-activation-scripts\MAS\Separate-Files-Version\Activators\HWID_Activation.cmd | text | |
MD5:50F8BA713C1F0EC3E8C95BFD672B55D5 | SHA256:D4B919688492893AEAFF1B84A899FC246BF62488F3B8F49DAA5FDADEC6A4CD76 | |||
| 3000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\master\microsoft-activation-scripts\MAS\Separate-Files-Version\Activators\TSforge_Activation.cmd | text | |
MD5:2E401B2954C6F73E7374C2D67CB5CA36 | SHA256:CBB686EE731A732E5212BBC62955DFC61303391218973E786BAEE4AA1D096156 | |||
| 3000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\master\microsoft-activation-scripts\MAS\Separate-Files-Version\Activators\Ohook_Activation_AIO.cmd | text | |
MD5:CCC8625A469941C9D0B1C4D82137B1B8 | SHA256:D8D25D018A247BD382E17730A7F561D8B6EC7C8042F1AA94206408CA3CE038BB | |||
| 3000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\master\microsoft-activation-scripts\MAS\Separate-Files-Version\Activators\Online_KMS_Activation.cmd | text | |
MD5:FB98512A8983D2ED98A2C2123AF6C0BE | SHA256:080612B1AAF308FDE0608DB51D9B4B685AB85D4D2F6FF0CD542A72E0DE258FE5 | |||
| 3000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\master\microsoft-activation-scripts\LICENSE | text | |
MD5:1EBBD3E34237AF26DA5DC08A4E440464 | SHA256:3972DC9744F6499F0F9B2DBF76696F2AE7AD8AF9B23DDE66D6AF86C9DFB36986 | |||
| 3000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\master\microsoft-activation-scripts\MAS\All-In-One-Version-KL\MAS_AIO.cmd | text | |
MD5:B5A6AFF691AC3D6277C496C50F0A5DE1 | SHA256:EF2F705B9E8BE2816598E2E8B70BADB200733F2287B917D6C9666D95C63AFBF9 | |||
| 3000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\master\microsoft-activation-scripts\MAS\Separate-Files-Version\Change_Windows_Edition.cmd | text | |
MD5:ED1238F1D958E724AF8A716341ED0A5D | SHA256:0D05706E7D04970DD5C5E900B44EBB6440AB8CF095F6EF0981CEE7B1DD060BC2 | |||
| 3000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\master\microsoft-activation-scripts\MAS\Separate-Files-Version\Check_Activation_Status.cmd | text | |
MD5:8D85133114BEEAF31F14E95F53E77F92 | SHA256:0CCAB6D0453998A98620960513F98D9522DD61C52A69BBF5D4EEFB12BED79F3B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.55.110.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
592 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3556 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3556 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1156 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.55.110.211:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
592 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |