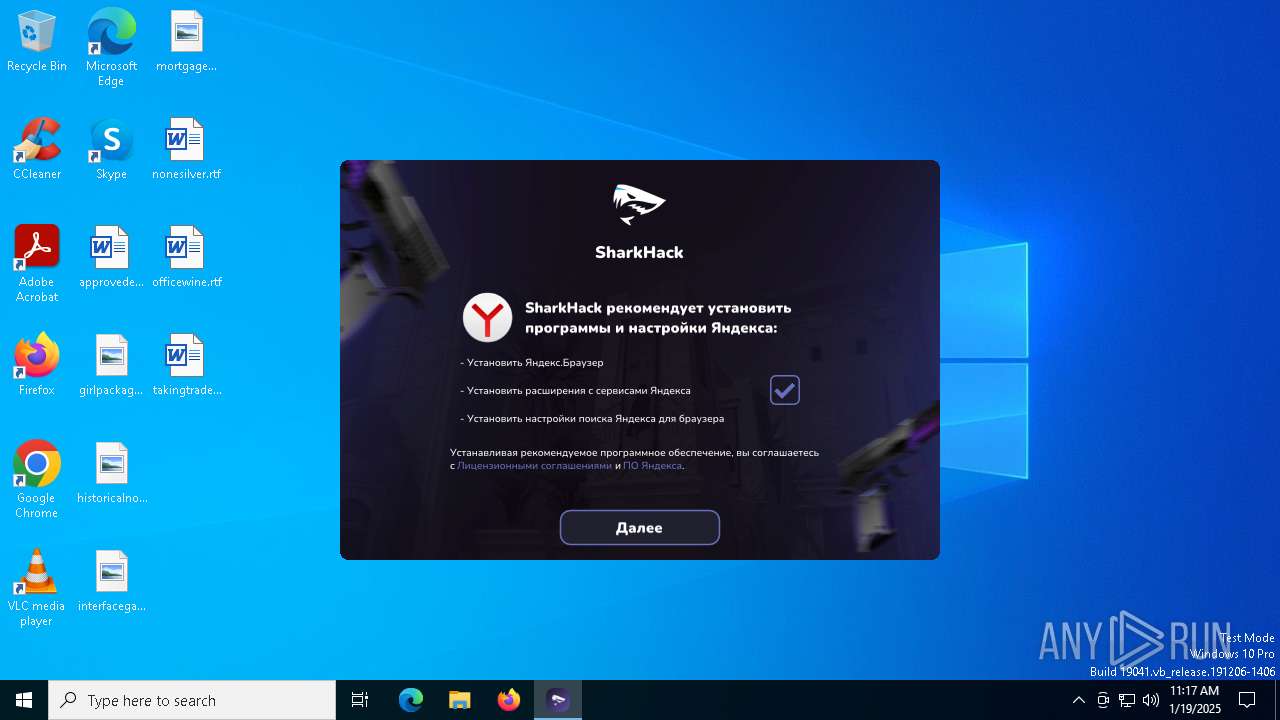
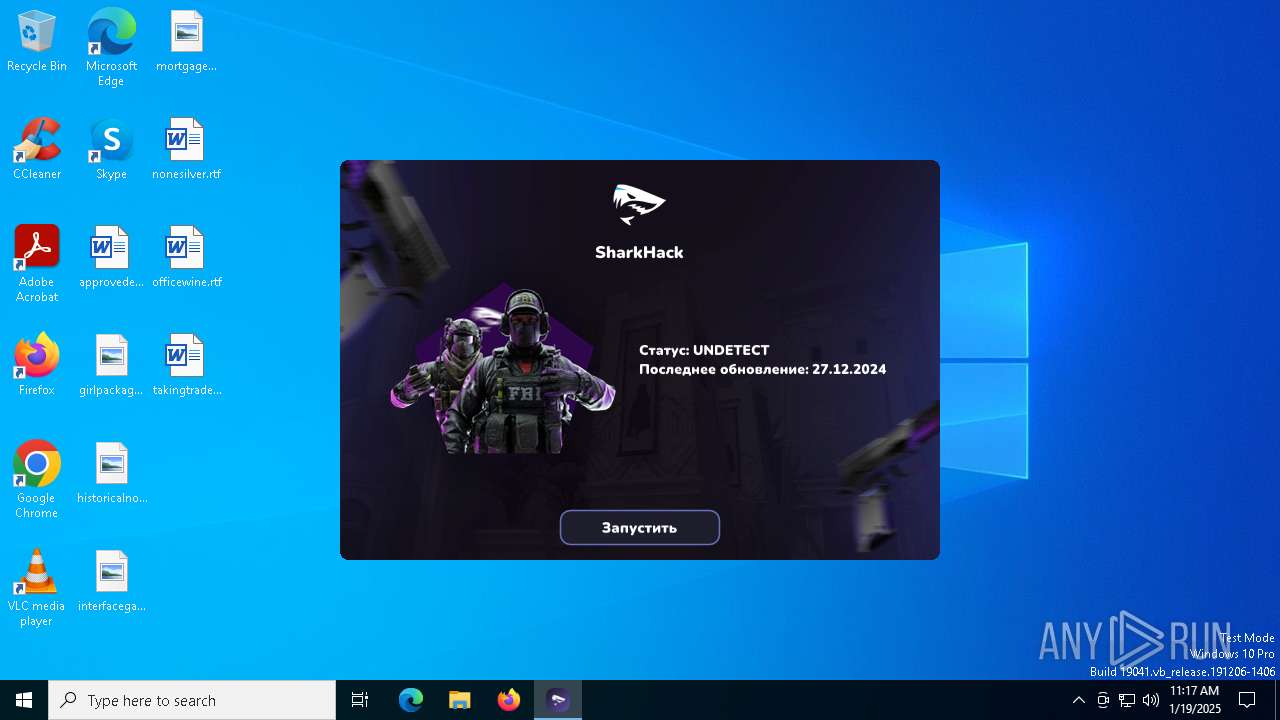
| File name: | SharkHack.exe |
| Full analysis: | https://app.any.run/tasks/7f812ea5-7074-419e-b4e5-be5994ead4fe |
| Verdict: | Malicious activity |
| Analysis date: | January 19, 2025, 11:17:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | DE1829AF1A22BBF3E19E47A95429801F |
| SHA1: | 42984734B1532E8EBD99DA16026ED225D1020B19 |
| SHA256: | 24DE9F578A10C496DBED85D9E01A1BAE955F317E93717988E39E9049CE4896C2 |
| SSDEEP: | 98304:GJ0Wa0jZAJ7O2YEHY+WAFJDT2f9kxo52m1Nw2wcDsWaeULnzDtHi7IyjIabltZsd:oKq6p |
MALICIOUS
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2192)
SUSPICIOUS
Reads security settings of Internet Explorer
- SharkHack.exe (PID: 6260)
Executable content was dropped or overwritten
- SharkHack.exe (PID: 6260)
Checks Windows Trust Settings
- SharkHack.exe (PID: 6260)
INFO
Reads the computer name
- SharkHack.exe (PID: 6260)
Checks supported languages
- SharkHack.exe (PID: 6260)
Checks proxy server information
- SharkHack.exe (PID: 6260)
Creates files or folders in the user directory
- SharkHack.exe (PID: 6260)
Reads the software policy settings
- SharkHack.exe (PID: 6260)
Reads the machine GUID from the registry
- SharkHack.exe (PID: 6260)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:01:05 18:59:52+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.42 |
| CodeSize: | 2664448 |
| InitializedDataSize: | 1439232 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1f6ee4 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
125
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6260 | "C:\Users\admin\AppData\Local\Temp\SharkHack.exe" | C:\Users\admin\AppData\Local\Temp\SharkHack.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
929
Read events
926
Write events
3
Delete events
0
Modification events
| (PID) Process: | (6260) SharkHack.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6260) SharkHack.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6260) SharkHack.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
2
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6260 | SharkHack.exe | C:\Users\admin\AppData\Roaming\OperaSetup.exe | executable | |
MD5:2033BABD0DEF2BE3CC4B21C764F1754A | SHA256:803802E34A8337B858DEBE051DD2A7EC6F552B8222CBA901829D7A900086C0FC | |||
| 6260 | SharkHack.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_B7ED31D77D311A56FDCB56A0083B3E0B | binary | |
MD5:918E52807D17A667887BA16E2E5A2619 | SHA256:9A3F3DEE8CF980B037F5DE028AE582B0119103B7028E6739EC99020AC4649A40 | |||
| 6260 | SharkHack.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_B7ED31D77D311A56FDCB56A0083B3E0B | der | |
MD5:8DB642DC1937B2F37E049E3AE64928CB | SHA256:7C03E5B3A2F6343BD1A6F879C1DD2840625AFE7C4B0614F9FB52FD204082F300 | |||
| 6260 | SharkHack.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\OperaSetup[1].exe | executable | |
MD5:2033BABD0DEF2BE3CC4B21C764F1754A | SHA256:803802E34A8337B858DEBE051DD2A7EC6F552B8222CBA901829D7A900086C0FC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
41
DNS requests
22
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2736 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2736 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 142.250.186.163:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 142.250.186.163:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
6260 | SharkHack.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAsA6S1NbXMfyjBZx8seGIY%3D | unknown | — | — | whitelisted |
4708 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6908 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2736 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2736 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.144:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
shark-software.ru |
| unknown |
c.pki.goog |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain (shark-software .ru) |