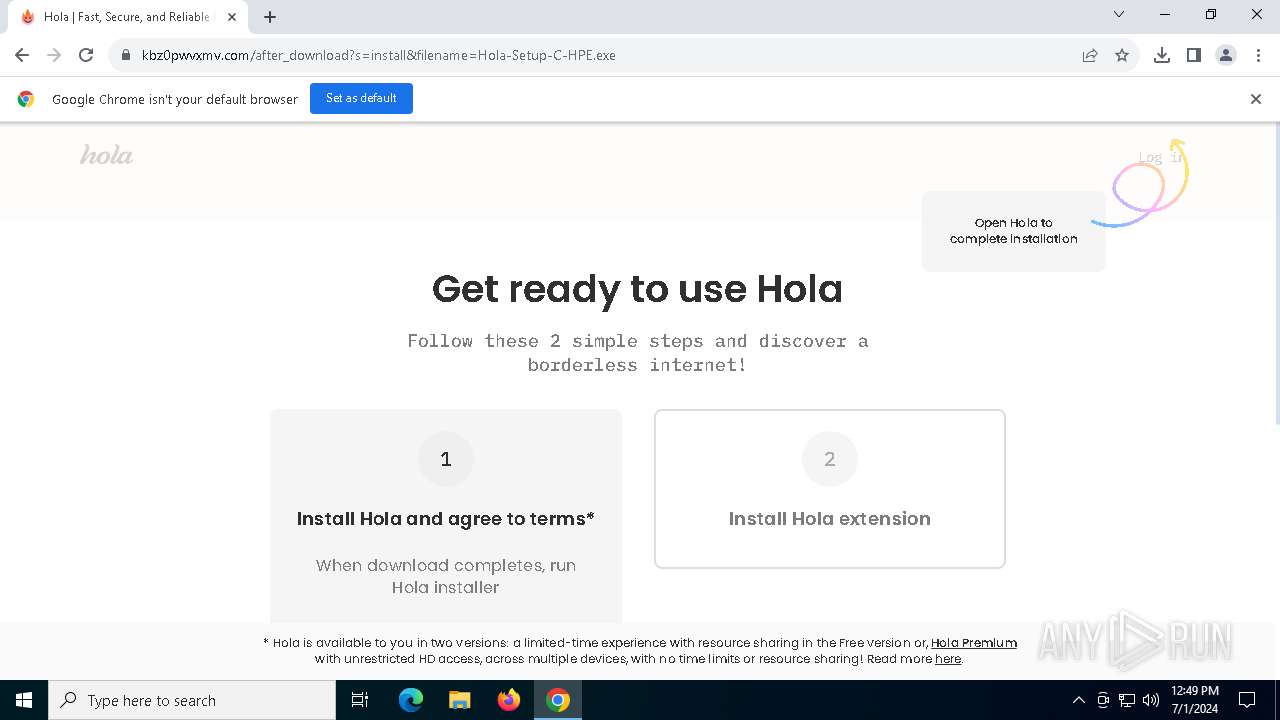
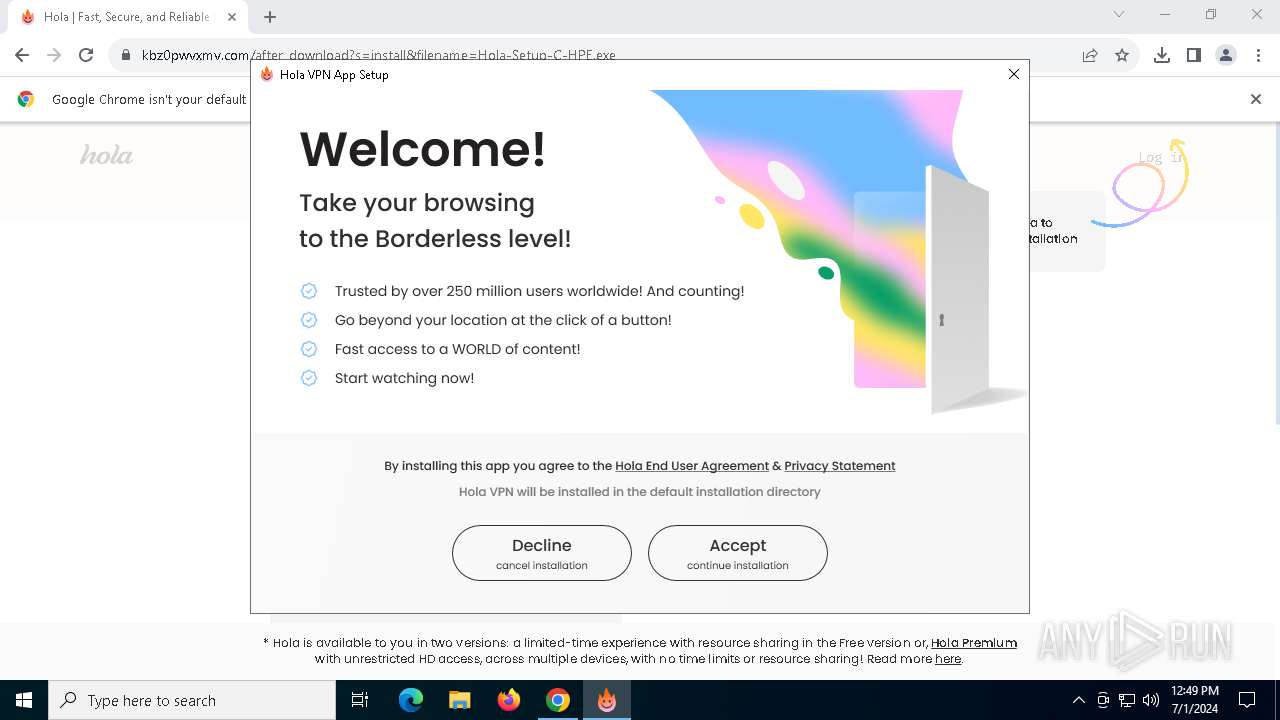
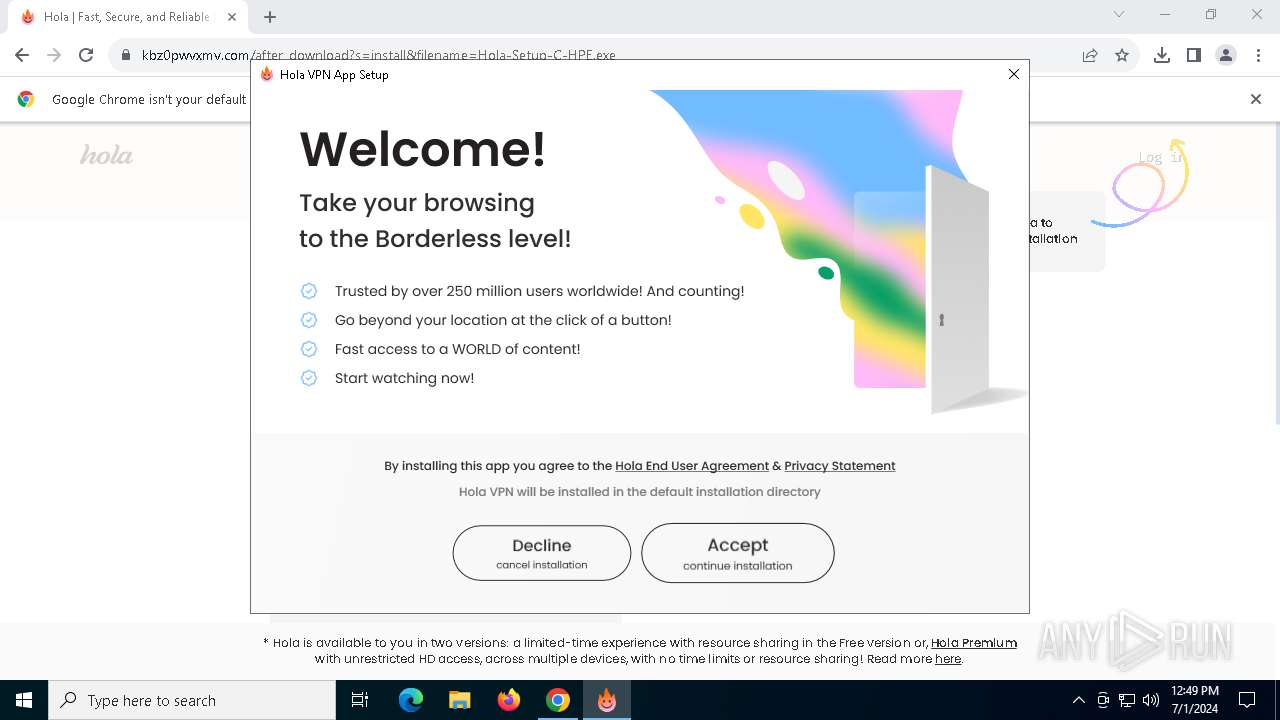
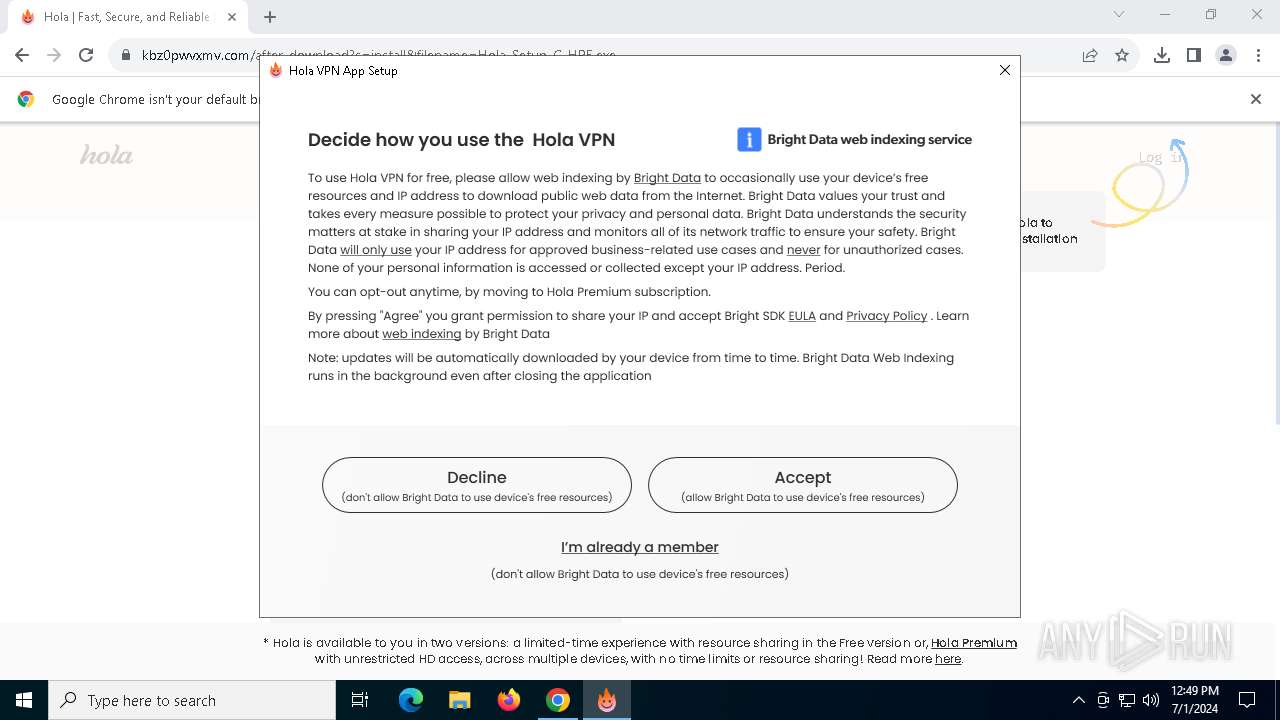
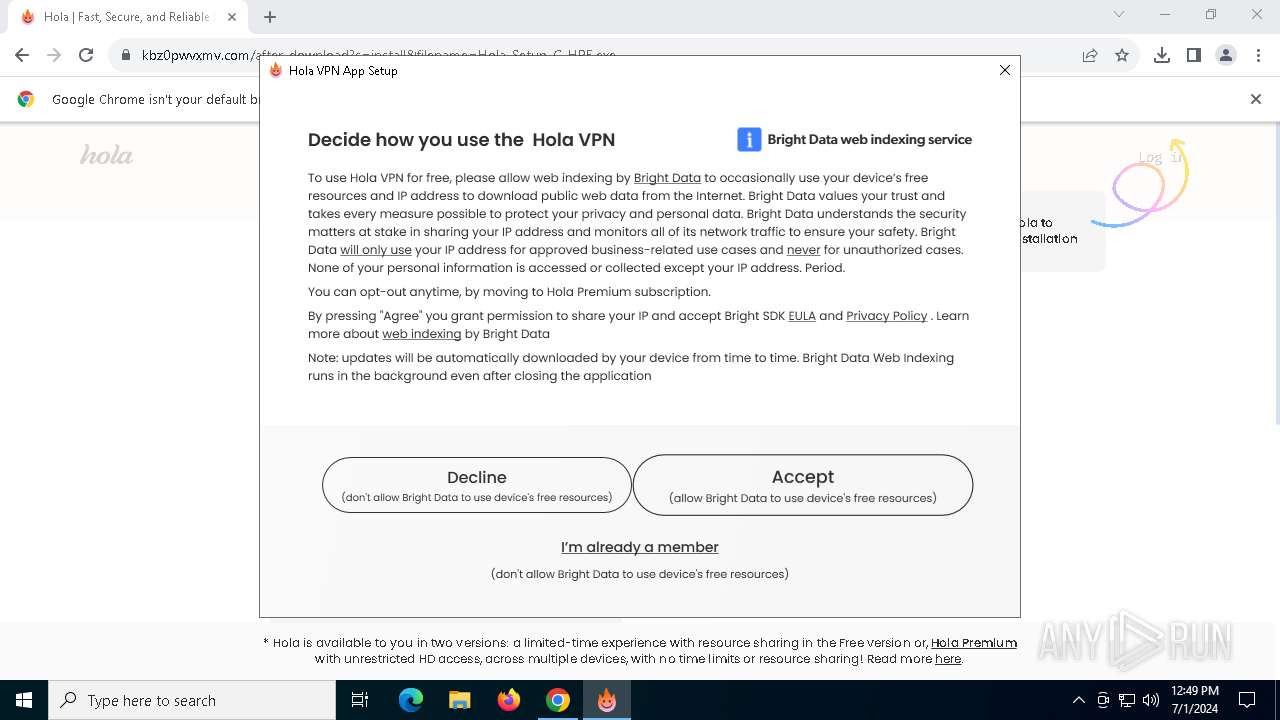
| URL: | kbz0pwvxmv.com |
| Full analysis: | https://app.any.run/tasks/4242e15c-edc4-4ca5-8ee0-275c6941fbc6 |
| Verdict: | Malicious activity |
| Analysis date: | July 01, 2024, 12:49:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 63E6BF2A5720E1187DB085ED2F28E886 |
| SHA1: | 9E963295FF068FC66DDE5C3F461618F79B9A9013 |
| SHA256: | 24CF53047673F751FDBC8235CA345384FBFCF174B44C68BC900841949334B871 |
| SSDEEP: | 3:F5n:F5n |
MALICIOUS
Drops the executable file immediately after the start
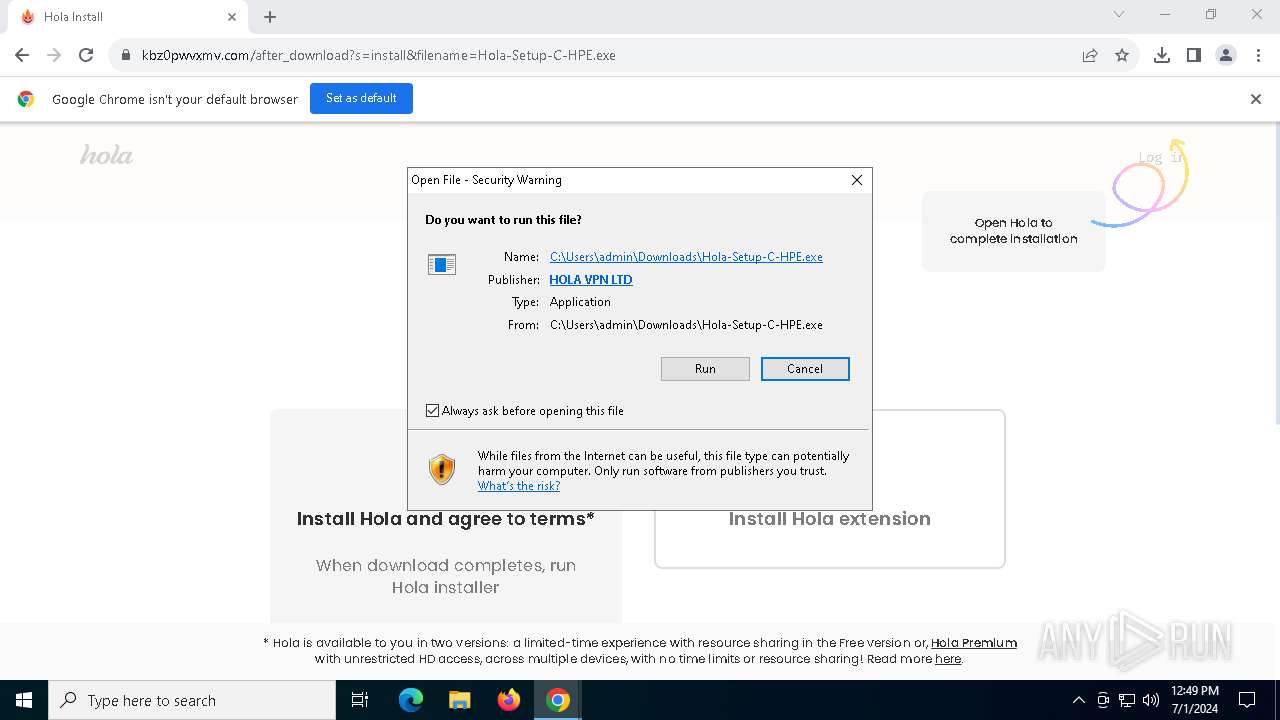
- Hola-Setup-C-HPE.exe (PID: 6204)
- Hola-Setup-x64-1.227.177.exe (PID: 4536)
- net_updater64.exe (PID: 1188)
- net_updater64.exe (PID: 3872)
- net_updater64.exe (PID: 6768)
- net_updater64.exe (PID: 6920)
- 7zr.exe (PID: 7712)
- Hola-Setup-x64-1.227.177.exe (PID: 7620)
- net_updater64.exe (PID: 1428)
Changes the autorun value in the registry
- Hola-Setup-x64-1.227.177.exe (PID: 4536)
Creates a writable file in the system directory
- net_updater64.exe (PID: 3872)
Actions looks like stealing of personal data
- Hola-Setup-x64-1.227.177.exe (PID: 7620)
- hola_svc.exe (PID: 1596)
- hola_cr.exe (PID: 9052)
- hola.exe (PID: 8936)
- hola_cr.exe (PID: 8308)
- 7zr.exe (PID: 7712)
- hola_cr.exe (PID: 5480)
- hola_cr.exe (PID: 6568)
- hola_cr.exe (PID: 8064)
- hola_cr.exe (PID: 6172)
- hola_cr.exe (PID: 8224)
- hola_cr.exe (PID: 8948)
- hola_cr.exe (PID: 7968)
- hola_cr.exe (PID: 8296)
- hola_cr.exe (PID: 8464)
- hola_cr.exe (PID: 2052)
- hola_cr.exe (PID: 6308)
- hola_cr.exe (PID: 8808)
- hola_cr.exe (PID: 8272)
- hola_cr.exe (PID: 8716)
- hola_cr.exe (PID: 7944)
- hola_cr.exe (PID: 7048)
- hola_cr.exe (PID: 8280)
- hola_cr.exe (PID: 7456)
- hola_cr.exe (PID: 7016)
- hola_cr.exe (PID: 7588)
- hola_cr.exe (PID: 8600)
- hola_cr.exe (PID: 8540)
- hola_cr.exe (PID: 8280)
- hola_cr.exe (PID: 6776)
- hola_cr.exe (PID: 7432)
- hola_cr.exe (PID: 7912)
- hola_cr.exe (PID: 7960)
SUSPICIOUS
Reads security settings of Internet Explorer
- Hola-Setup-C-HPE.exe (PID: 7048)
- Hola-Setup-C-HPE.exe (PID: 6204)
- net_updater64.exe (PID: 1188)
- net_updater64.exe (PID: 6768)
Application launched itself
- Hola-Setup-C-HPE.exe (PID: 6204)
- Hola-Setup-C-HPE.exe (PID: 7048)
- hola_svc.exe (PID: 1596)
- hola_cr.exe (PID: 9052)
- hola_cr.exe (PID: 7968)
Executable content was dropped or overwritten
- Hola-Setup-C-HPE.exe (PID: 6204)
- Hola-Setup-x64-1.227.177.exe (PID: 4536)
- net_updater64.exe (PID: 1188)
- net_updater64.exe (PID: 3872)
- net_updater64.exe (PID: 6768)
- net_updater64.exe (PID: 6920)
- net_updater64.exe (PID: 1428)
- 7zr.exe (PID: 7712)
- Hola-Setup-x64-1.227.177.exe (PID: 7620)
Reads the date of Windows installation
- Hola-Setup-C-HPE.exe (PID: 6204)
- Hola-Setup-C-HPE.exe (PID: 7048)
Drops 7-zip archiver for unpacking
- Hola-Setup-x64-1.227.177.exe (PID: 4536)
Drops a system driver (possible attempt to evade defenses)
- Hola-Setup-x64-1.227.177.exe (PID: 4536)
Creates a software uninstall entry
- Hola-Setup-x64-1.227.177.exe (PID: 4536)
Checks Windows Trust Settings
- net_updater64.exe (PID: 1188)
- net_updater64.exe (PID: 3872)
- net_updater64.exe (PID: 6768)
- net_updater64.exe (PID: 6920)
- net_updater64.exe (PID: 1428)
Process drops legitimate windows executable
- net_updater64.exe (PID: 1188)
The process drops C-runtime libraries
- net_updater64.exe (PID: 1188)
Executes as Windows Service
- net_updater64.exe (PID: 3872)
- hola_svc.exe (PID: 1596)
- WmiApSrv.exe (PID: 2860)
Detected use of alternative data streams (AltDS)
- net_updater64.exe (PID: 3872)
- net_updater64.exe (PID: 6768)
- net_updater64.exe (PID: 6920)
- net_updater64.exe (PID: 1428)
Creates file in the systems drive root
- hola_svc.exe (PID: 1596)
The process checks if it is being run in the virtual environment
- net_updater64.exe (PID: 3872)
- hola_cr.exe (PID: 7968)
Connects to unusual port
- hola_svc.exe (PID: 1596)
Starts SC.EXE for service management
- hola_svc.exe (PID: 1596)
Process requests binary or script from the Internet
- hola.exe (PID: 8936)
Patches Antimalware Scan Interface function (YARA)
- net_updater64.exe (PID: 3872)
INFO
Application launched itself
- chrome.exe (PID: 4852)
Drops the executable file immediately after the start
- chrome.exe (PID: 4852)
- chrome.exe (PID: 7776)
Reads the computer name
- Hola-Setup-C-HPE.exe (PID: 7048)
- Hola-Setup-C-HPE.exe (PID: 6388)
- Hola-Setup-x64-1.227.177.exe (PID: 4536)
- net_updater64.exe (PID: 1188)
- test_wpf.exe (PID: 6620)
- net_updater64.exe (PID: 3872)
- test_wpf.exe (PID: 7160)
- net_updater64.exe (PID: 6768)
- test_wpf.exe (PID: 6920)
- Hola-Setup-C-HPE.exe (PID: 6204)
- hola_svc.exe (PID: 1596)
- idle_report.exe (PID: 6644)
- net_updater64.exe (PID: 6920)
- test_wpf.exe (PID: 7040)
- net_updater64.exe (PID: 1428)
- Hola-Setup-x64-1.227.177.exe (PID: 7620)
- 7zr.exe (PID: 7712)
- test_wpf.exe (PID: 7960)
- Hola-Setup-x64-1.227.177.exe (PID: 7360)
- hola.exe (PID: 8936)
- hola_cr.exe (PID: 7968)
- hola_cr.exe (PID: 9052)
- hola_cr.exe (PID: 5480)
- hola_cr.exe (PID: 6568)
- hola_cr.exe (PID: 8064)
- hola_cr.exe (PID: 8280)
- hola_cr.exe (PID: 8600)
- idle_report.exe (PID: 6196)
- idle_report.exe (PID: 1736)
Checks supported languages
- Hola-Setup-C-HPE.exe (PID: 7048)
- Hola-Setup-C-HPE.exe (PID: 6388)
- Hola-Setup-x64-1.227.177.exe (PID: 4536)
- net_updater64.exe (PID: 1188)
- test_wpf.exe (PID: 6620)
- net_updater64.exe (PID: 3872)
- test_wpf.exe (PID: 7160)
- net_updater64.exe (PID: 6768)
- test_wpf.exe (PID: 6920)
- Hola-Setup-C-HPE.exe (PID: 6204)
- hola_svc.exe (PID: 1596)
- idle_report.exe (PID: 6644)
- net_updater64.exe (PID: 6920)
- test_wpf.exe (PID: 7040)
- Hola-Setup-x64-1.227.177.exe (PID: 7620)
- hola_svc.exe (PID: 7544)
- hola_svc.exe (PID: 6676)
- net_updater64.exe (PID: 1428)
- 7zr.exe (PID: 7712)
- Hola-Setup-x64-1.227.177.exe (PID: 7360)
- test_wpf.exe (PID: 7960)
- hola_cr.exe (PID: 7968)
- hola_cr.exe (PID: 9052)
- hola_cr.exe (PID: 8308)
- hola.exe (PID: 8936)
- hola_cr.exe (PID: 5480)
- hola_cr.exe (PID: 6568)
- hola_cr.exe (PID: 6172)
- hola_cr.exe (PID: 8948)
- hola_cr.exe (PID: 6308)
- hola_cr.exe (PID: 8296)
- hola_cr.exe (PID: 8464)
- hola_cr.exe (PID: 8064)
- hola_cr.exe (PID: 8224)
- hola_cr.exe (PID: 2052)
- hola_cr.exe (PID: 7944)
- hola_cr.exe (PID: 7048)
- hola_cr.exe (PID: 8808)
- hola_cr.exe (PID: 8272)
- hola_cr.exe (PID: 8716)
- hola_cr.exe (PID: 7016)
- hola_cr.exe (PID: 8280)
- hola_cr.exe (PID: 7456)
- hola_cr.exe (PID: 7588)
- hola_cr.exe (PID: 8600)
- hola_cr.exe (PID: 8540)
- idle_report.exe (PID: 6196)
- hola_cr.exe (PID: 8280)
- hola_cr.exe (PID: 6776)
- hola_svc.exe (PID: 6960)
- hola_cr.exe (PID: 7432)
- hola_cr.exe (PID: 7912)
- idle_report.exe (PID: 1736)
- hola_cr.exe (PID: 7960)
- hola_svc.exe (PID: 8044)
Disables trace logs
- Hola-Setup-C-HPE.exe (PID: 7048)
- Hola-Setup-C-HPE.exe (PID: 6204)
- Hola-Setup-C-HPE.exe (PID: 6388)
- net_updater64.exe (PID: 3872)
- rasdial.exe (PID: 1708)
- hola_svc.exe (PID: 1596)
- rasdial.exe (PID: 5324)
- rasdial.exe (PID: 8020)
- rasdial.exe (PID: 6504)
- rasdial.exe (PID: 8196)
- rasdial.exe (PID: 8384)
- rasdial.exe (PID: 6424)
- rasdial.exe (PID: 8412)
- rasdial.exe (PID: 5632)
- rasdial.exe (PID: 9160)
- rasdial.exe (PID: 6368)
- rasdial.exe (PID: 7692)
- rasdial.exe (PID: 8368)
- rasdial.exe (PID: 3104)
- rasdial.exe (PID: 8208)
- rasdial.exe (PID: 6512)
- rasdial.exe (PID: 8996)
- rasdial.exe (PID: 7744)
- rasdial.exe (PID: 6996)
- rasdial.exe (PID: 7916)
- rasdial.exe (PID: 2120)
- rasdial.exe (PID: 8260)
- rasdial.exe (PID: 8632)
- rasdial.exe (PID: 4208)
- rasdial.exe (PID: 8412)
- rasdial.exe (PID: 6240)
- rasdial.exe (PID: 6876)
- rasdial.exe (PID: 7764)
- rasdial.exe (PID: 2216)
- rasdial.exe (PID: 7668)
- rasdial.exe (PID: 8268)
- rasdial.exe (PID: 6356)
- rasdial.exe (PID: 3020)
- rasdial.exe (PID: 6308)
- rasdial.exe (PID: 8072)
- rasdial.exe (PID: 1452)
- rasdial.exe (PID: 8296)
- rasdial.exe (PID: 6036)
- rasdial.exe (PID: 8544)
- rasdial.exe (PID: 5656)
- rasdial.exe (PID: 1960)
- rasdial.exe (PID: 8688)
- rasdial.exe (PID: 6448)
- rasdial.exe (PID: 7852)
- rasdial.exe (PID: 6160)
- rasdial.exe (PID: 8208)
- rasdial.exe (PID: 4476)
- rasdial.exe (PID: 6748)
- rasdial.exe (PID: 7132)
- rasdial.exe (PID: 7696)
- rasdial.exe (PID: 7820)
- rasdial.exe (PID: 8984)
- rasdial.exe (PID: 8388)
- rasdial.exe (PID: 9176)
- rasdial.exe (PID: 8024)
- rasdial.exe (PID: 5344)
- rasdial.exe (PID: 7540)
- rasdial.exe (PID: 7412)
- rasdial.exe (PID: 7332)
- rasdial.exe (PID: 8960)
- rasdial.exe (PID: 4264)
- rasdial.exe (PID: 6404)
- rasdial.exe (PID: 2008)
- rasdial.exe (PID: 8168)
- rasdial.exe (PID: 6508)
- rasdial.exe (PID: 4084)
- rasdial.exe (PID: 1796)
- rasdial.exe (PID: 1088)
- rasdial.exe (PID: 8164)
- rasdial.exe (PID: 5596)
- rasdial.exe (PID: 6556)
- rasdial.exe (PID: 9200)
- rasdial.exe (PID: 5968)
- rasdial.exe (PID: 7632)
- rasdial.exe (PID: 5832)
- rasdial.exe (PID: 8096)
- rasdial.exe (PID: 9140)
- rasdial.exe (PID: 700)
- rasdial.exe (PID: 7152)
- rasdial.exe (PID: 9028)
- rasdial.exe (PID: 6216)
- rasdial.exe (PID: 7420)
- rasdial.exe (PID: 3884)
- rasdial.exe (PID: 8388)
- rasdial.exe (PID: 6436)
- rasdial.exe (PID: 8996)
- rasdial.exe (PID: 4732)
- rasdial.exe (PID: 6724)
- rasdial.exe (PID: 4688)
- rasdial.exe (PID: 7984)
- rasdial.exe (PID: 7992)
- rasdial.exe (PID: 1376)
- rasdial.exe (PID: 6452)
- rasdial.exe (PID: 6468)
- rasdial.exe (PID: 1920)
- rasdial.exe (PID: 6704)
- rasdial.exe (PID: 3848)
- rasdial.exe (PID: 8052)
- rasdial.exe (PID: 8180)
- rasdial.exe (PID: 8628)
- rasdial.exe (PID: 6352)
- rasdial.exe (PID: 5252)
- rasdial.exe (PID: 6424)
Reads the machine GUID from the registry
- Hola-Setup-C-HPE.exe (PID: 7048)
- Hola-Setup-C-HPE.exe (PID: 6388)
- Hola-Setup-C-HPE.exe (PID: 6204)
- net_updater64.exe (PID: 1188)
- test_wpf.exe (PID: 6620)
- net_updater64.exe (PID: 3872)
- test_wpf.exe (PID: 7160)
- net_updater64.exe (PID: 6768)
- test_wpf.exe (PID: 6920)
- idle_report.exe (PID: 6644)
- hola_svc.exe (PID: 1596)
- net_updater64.exe (PID: 6920)
- test_wpf.exe (PID: 7040)
- net_updater64.exe (PID: 1428)
- test_wpf.exe (PID: 7960)
- hola_cr.exe (PID: 7968)
- idle_report.exe (PID: 6196)
- idle_report.exe (PID: 1736)
Executable content was dropped or overwritten
- chrome.exe (PID: 4852)
- chrome.exe (PID: 7776)
Reads Environment values
- Hola-Setup-C-HPE.exe (PID: 7048)
- Hola-Setup-C-HPE.exe (PID: 6204)
- Hola-Setup-C-HPE.exe (PID: 6388)
- net_updater64.exe (PID: 1188)
- net_updater64.exe (PID: 3872)
- net_updater64.exe (PID: 6768)
- net_updater64.exe (PID: 6920)
- net_updater64.exe (PID: 1428)
- hola_cr.exe (PID: 9052)
The process uses the downloaded file
- chrome.exe (PID: 4852)
- chrome.exe (PID: 6924)
- Hola-Setup-C-HPE.exe (PID: 7048)
Create files in a temporary directory
- Hola-Setup-C-HPE.exe (PID: 7048)
- Hola-Setup-x64-1.227.177.exe (PID: 4536)
- Hola-Setup-C-HPE.exe (PID: 6204)
- Hola-Setup-x64-1.227.177.exe (PID: 7620)
- Hola-Setup-x64-1.227.177.exe (PID: 7360)
- hola_cr.exe (PID: 7968)
Checks proxy server information
- Hola-Setup-C-HPE.exe (PID: 7048)
- Hola-Setup-C-HPE.exe (PID: 6204)
- Hola-Setup-C-HPE.exe (PID: 6388)
- net_updater64.exe (PID: 1188)
- hola_cr.exe (PID: 7968)
Reads the software policy settings
- Hola-Setup-C-HPE.exe (PID: 6204)
- Hola-Setup-x64-1.227.177.exe (PID: 4536)
- Hola-Setup-C-HPE.exe (PID: 6388)
- net_updater64.exe (PID: 1188)
- net_updater64.exe (PID: 3872)
- net_updater64.exe (PID: 6768)
- Hola-Setup-C-HPE.exe (PID: 7048)
- net_updater64.exe (PID: 6920)
- net_updater64.exe (PID: 1428)
- Hola-Setup-x64-1.227.177.exe (PID: 7620)
- hola.exe (PID: 8936)
- Hola-Setup-x64-1.227.177.exe (PID: 7360)
Process checks computer location settings
- Hola-Setup-C-HPE.exe (PID: 6204)
- net_updater64.exe (PID: 1188)
- net_updater64.exe (PID: 3872)
- net_updater64.exe (PID: 6768)
- Hola-Setup-C-HPE.exe (PID: 7048)
- net_updater64.exe (PID: 6920)
- net_updater64.exe (PID: 1428)
- hola_cr.exe (PID: 7968)
- hola_cr.exe (PID: 8464)
- hola_cr.exe (PID: 7944)
- hola_cr.exe (PID: 7048)
- hola_cr.exe (PID: 8716)
- hola_cr.exe (PID: 2052)
- hola_cr.exe (PID: 8808)
- hola_cr.exe (PID: 7016)
- hola_cr.exe (PID: 7456)
- hola_cr.exe (PID: 8272)
- hola_cr.exe (PID: 7588)
Creates files in the program directory
- Hola-Setup-x64-1.227.177.exe (PID: 4536)
- net_updater64.exe (PID: 1188)
- net_updater64.exe (PID: 3872)
- net_updater64.exe (PID: 6768)
- hola_svc.exe (PID: 1596)
- net_updater64.exe (PID: 6920)
- net_updater64.exe (PID: 1428)
- 7zr.exe (PID: 7712)
- Hola-Setup-x64-1.227.177.exe (PID: 7620)
- Hola-Setup-x64-1.227.177.exe (PID: 7360)
- hola.exe (PID: 8936)
Creates files or folders in the user directory
- net_updater64.exe (PID: 1188)
- hola_cr.exe (PID: 7968)
- hola_cr.exe (PID: 6568)
- hola_cr.exe (PID: 9052)
Reads CPU info
- net_updater64.exe (PID: 3872)
Reads the time zone
- net_updater64.exe (PID: 3872)
Reads security settings of Internet Explorer
- explorer.exe (PID: 6664)
Reads Microsoft Office registry keys
- hola_cr.exe (PID: 7968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
561
Monitored processes
413
Malicious processes
43
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rasdial.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | sc query luminati_net_updater_com_hvpnmobile | C:\Windows\System32\sc.exe | — | hola_svc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 428 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2248 --field-trial-handle=1956,i,12962839455447776431,10999735610040446498,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 | |||||||||||||||
| 700 | rasdial | C:\Windows\System32\rasdial.exe | — | hola_svc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Remote Access Command Line Dial UI Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | sc query luminati_net_updater_win_hola_email_hola_org | C:\Windows\System32\sc.exe | — | hola_svc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | sc query luminati_net_updater_win_hola_sdk_hola_org | C:\Windows\System32\sc.exe | — | hola_svc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1060 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1088 | rasdial | C:\Windows\System32\rasdial.exe | — | hola_svc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Remote Access Command Line Dial UI Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1112 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rasdial.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rasdial.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
106 222
Read events
105 995
Write events
215
Delete events
12
Modification events
| (PID) Process: | (4852) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (6924) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6924) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6924) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6924) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6924) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\Component Categories64\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\Enum |
| Operation: | write | Name: | Implementing |
Value: 1C00000001000000E8070700010001000C0031001D001902010000001E768127E028094199FEB9D127C57AFE | |||
| (PID) Process: | (6924) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 010000000000000021C4E81CB5CBDA01 | |||
| (PID) Process: | (6924) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\Component Categories64\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\Enum |
| Operation: | write | Name: | Implementing |
Value: 1C00000001000000E8070700010001000C0031001D002202010000001E768127E028094199FEB9D127C57AFE | |||
| (PID) Process: | (4852) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4852) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
31
Suspicious files
557
Text files
97
Unknown types
27
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1ae1b6.TMP | — | |
MD5:— | SHA256:— | |||
| 4852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1ae1b6.TMP | — | |
MD5:— | SHA256:— | |||
| 4852 | chrome.exe | C:\USERS\ADMIN\APPDATA\LOCAL\GOOGLE\CHROME\USER DATA\LAST VERSION | text | |
MD5:FCE53E052E5CF7C20819320F374DEA88 | SHA256:CD95DE277E746E92CC2C53D9FC92A8F6F0C3EDFB7F1AD9A4E9259F927065BC89 | |||
| 4852 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:723783C35EAEEE1492EDB30847AE6750 | SHA256:C29323F784CF873BF34992E7A2B4630B19641BF42980109E31D5AF2D487DF6F8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
52
TCP/UDP connections
325
DNS requests
166
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4852 | chrome.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | unknown |
4852 | chrome.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAXrhBDPOQ2gaSPA09Ycq3A%3D | unknown | — | — | unknown |
5776 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4020 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
4424 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
4424 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
1188 | net_updater64.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4636 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 142.251.18.84:443 | accounts.google.com | GOOGLE | US | unknown |
— | — | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 54.225.121.9:443 | kbz0pwvxmv.com | AMAZON-AES | US | unknown |
— | — | 54.225.121.9:80 | kbz0pwvxmv.com | AMAZON-AES | US | unknown |
— | — | 34.96.102.137:443 | dev.visualwebsiteoptimizer.com | GOOGLE | US | unknown |
— | — | 142.250.184.195:443 | fonts.gstatic.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
kbz0pwvxmv.com |
| unknown |
accounts.google.com |
| shared |
cdn4.kbz0pwvxmv.com |
| unknown |
fonts.gstatic.com |
| whitelisted |
dev.visualwebsiteoptimizer.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
perr.kbz0pwvxmv.com |
| unknown |
www.google.com |
| whitelisted |
client.kbz0pwvxmv.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
hola_cr.exe | RecursiveDirectoryCreate( C:\\Users\\admin\\AppData\\Roaming\ directory exists )
|