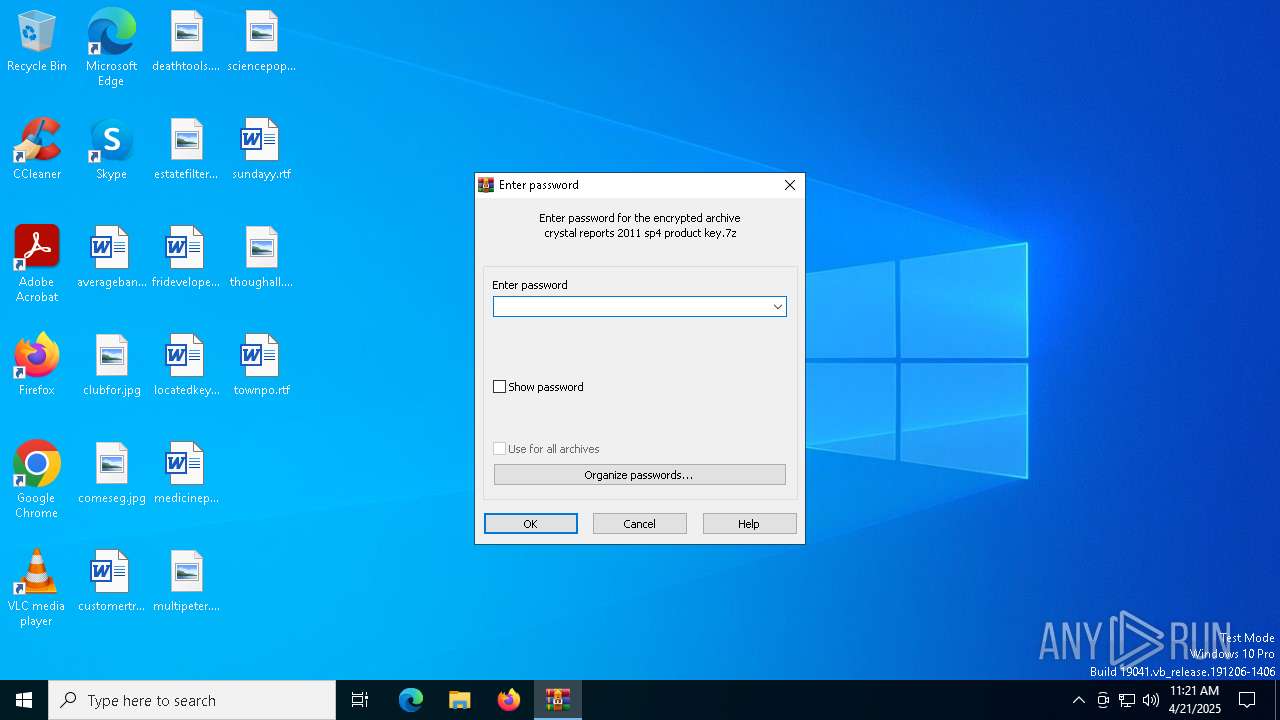
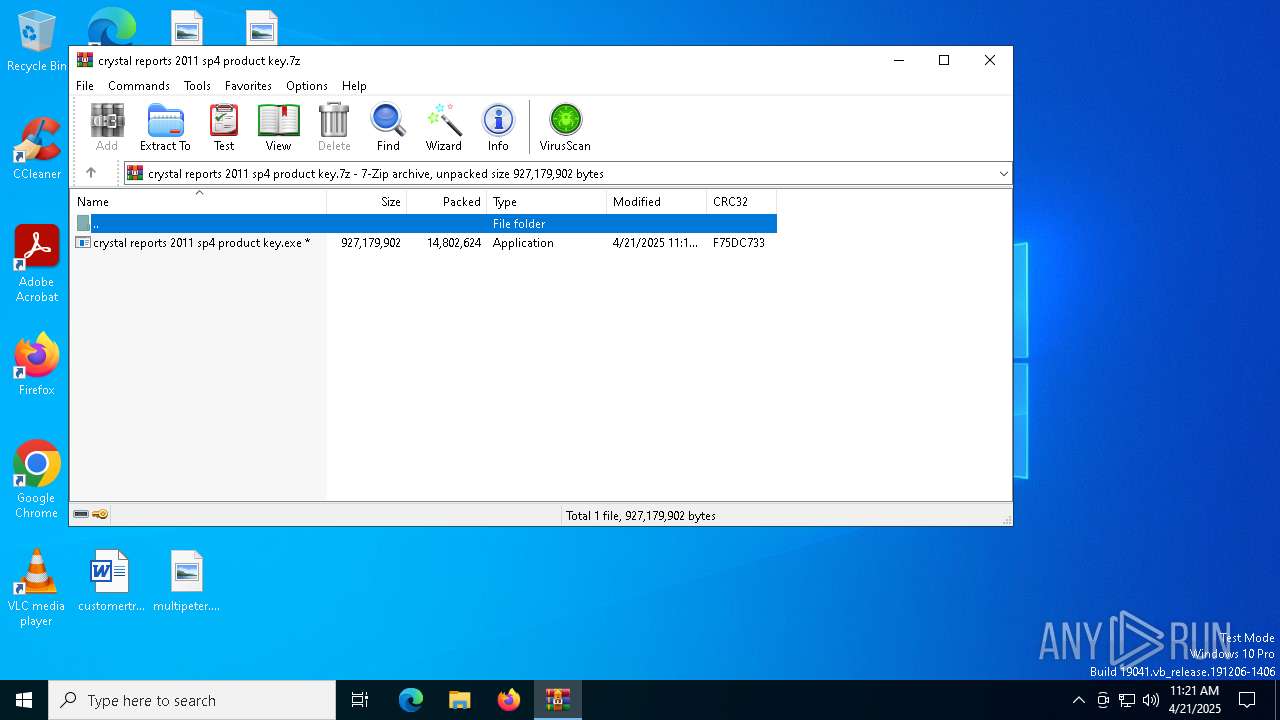
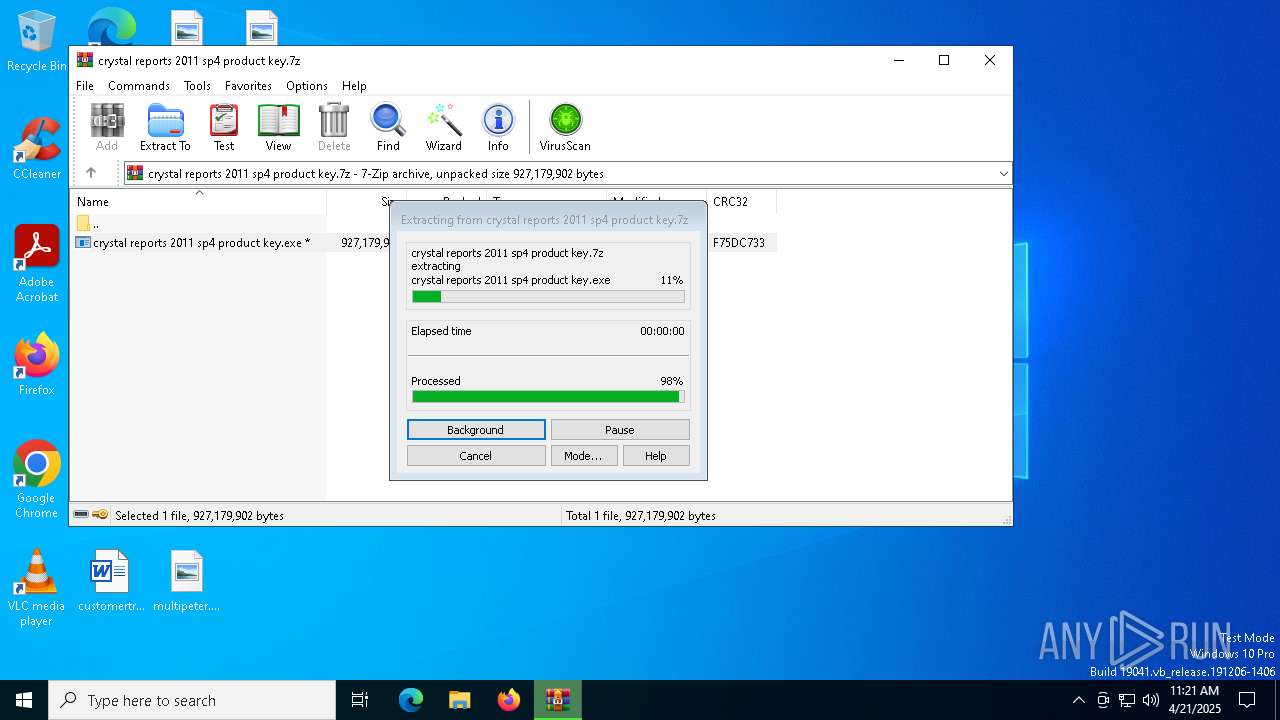
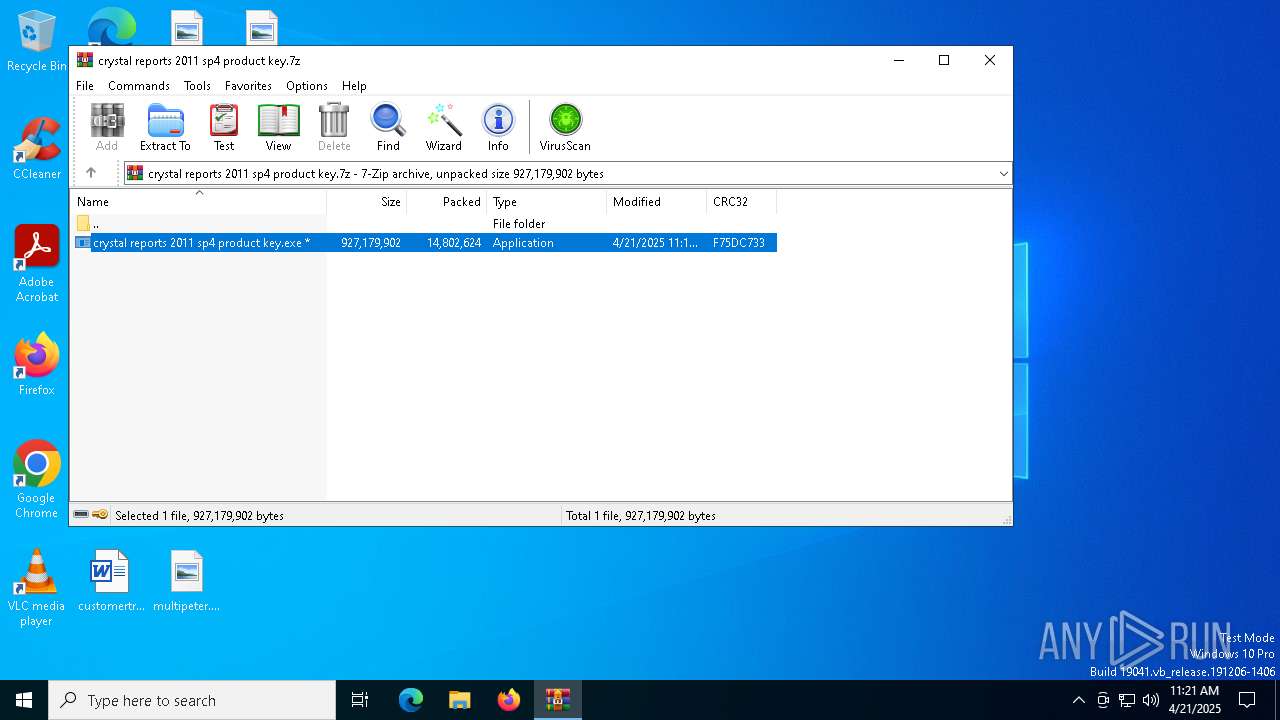
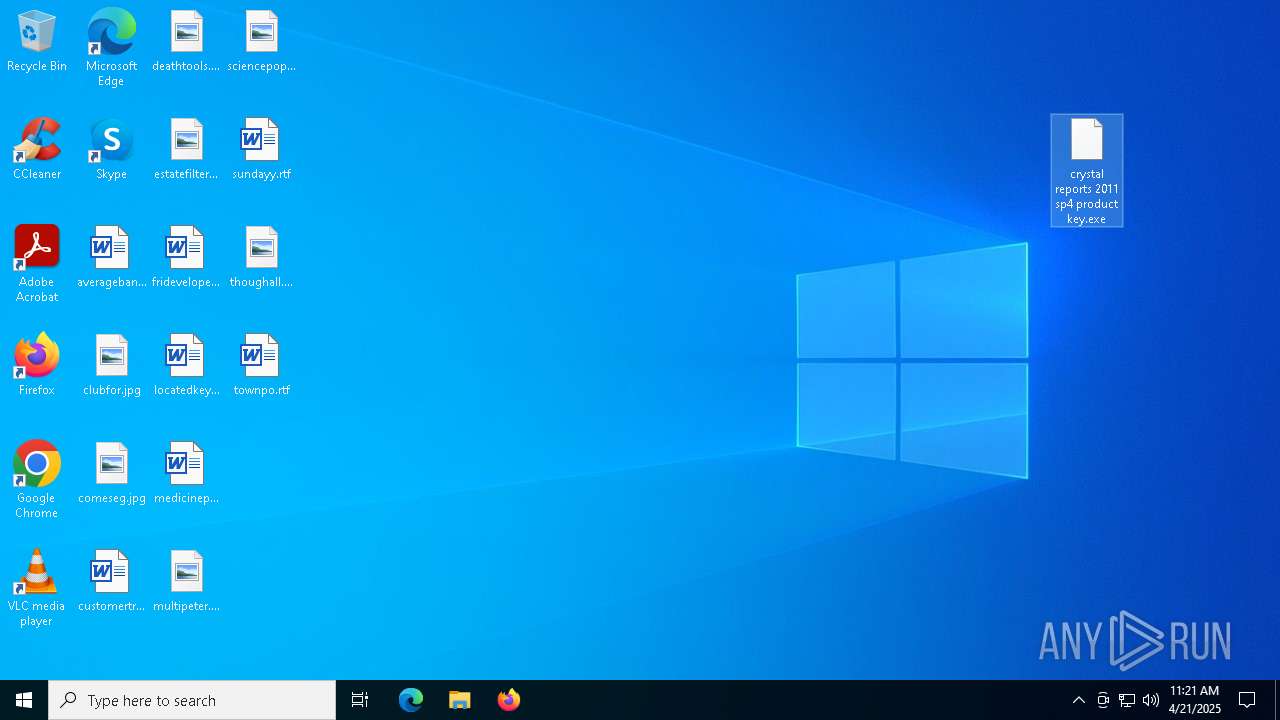
| File name: | crystal reports 2011 sp4 product key.7z |
| Full analysis: | https://app.any.run/tasks/7b7584ed-9397-4f73-8438-4e36e2b6035d |
| Verdict: | Malicious activity |
| Analysis date: | April 21, 2025, 11:21:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 8EC2B437E2A03B24A833A4919374A51D |
| SHA1: | 218731F3453483CD31139BAFD858833C3CD83D80 |
| SHA256: | 24CE970398616ADC2F30EA25893D5E376E7B5046DD1135770EE0FD9BAFFA6DB9 |
| SSDEEP: | 98304:OkqyFJVUCcLgza/CwpUd/Vpi9m9LGGId0eBaKt/pPlPXw/6oVEnGqS/X/qz5dc8K:0+4uAyYtfIF8hEofuDfwmqQK6d |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- crystal reports 2011 sp4 product key.exe (PID: 8004)
Executing commands from a ".bat" file
- crystal reports 2011 sp4 product key.exe (PID: 8004)
Starts CMD.EXE for commands execution
- crystal reports 2011 sp4 product key.exe (PID: 8004)
- cmd.exe (PID: 8060)
Get information on the list of running processes
- cmd.exe (PID: 8060)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 8060)
Application launched itself
- cmd.exe (PID: 8060)
Starts application with an unusual extension
- cmd.exe (PID: 8060)
Starts the AutoIt3 executable file
- cmd.exe (PID: 8060)
The executable file from the user directory is run by the CMD process
- Trust.com (PID: 4024)
INFO
Manual execution by a user
- crystal reports 2011 sp4 product key.exe (PID: 8004)
Create files in a temporary directory
- crystal reports 2011 sp4 product key.exe (PID: 8004)
- extrac32.exe (PID: 4220)
Process checks computer location settings
- crystal reports 2011 sp4 product key.exe (PID: 8004)
Checks supported languages
- crystal reports 2011 sp4 product key.exe (PID: 8004)
- extrac32.exe (PID: 4220)
- Trust.com (PID: 4024)
Reads the computer name
- crystal reports 2011 sp4 product key.exe (PID: 8004)
- extrac32.exe (PID: 4220)
- Trust.com (PID: 4024)
Creates a new folder
- cmd.exe (PID: 6516)
Reads mouse settings
- Trust.com (PID: 4024)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|
Total processes
146
Monitored processes
17
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4024 | Trust.com p | C:\Users\admin\AppData\Local\Temp\113445\Trust.com | — | cmd.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Version: 3, 3, 15, 5 Modules
| |||||||||||||||
| 4220 | extrac32 /Y /E Receivers.msi | C:\Windows\SysWOW64\extrac32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® CAB File Extract Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5072 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\crystal reports 2011 sp4 product key.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5544 | findstr /V "Result" Contributor | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5640 | choice /d y /t 5 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6516 | cmd /c md 113445 | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6800 | cmd /c copy /b 113445\Trust.com + Behavioral + Divided + Opera + Hughes + Accommodations + Faculty + Scanning + Plenty + Starsmerchant + Hosted 113445\Trust.com | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6988 | cmd /c copy /b ..\Lp.msi + ..\Protest.msi + ..\Tits.msi + ..\Twinks.msi + ..\Cooking.msi + ..\Likely.msi + ..\Larry.msi p | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7224 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7256 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 538
Read events
2 519
Write events
19
Delete events
0
Modification events
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\crystal reports 2011 sp4 product key.7z | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5072) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
0
Suspicious files
20
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5072 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5072.30309\crystal reports 2011 sp4 product key.exe | — | |
MD5:— | SHA256:— | |||
| 8004 | crystal reports 2011 sp4 product key.exe | C:\Users\admin\AppData\Local\Temp\Cooking.msi | binary | |
MD5:95ACB61938A32FB40023CDB233B7D401 | SHA256:6D86CCC7804F6C690D538F356399AD7F20AC8AA320105A8FDA7D628C02E727CF | |||
| 8004 | crystal reports 2011 sp4 product key.exe | C:\Users\admin\AppData\Local\Temp\Tits.msi | binary | |
MD5:5D662C0488C1E80DC10FCFF1877C1769 | SHA256:8A54FC01FE160D6F96A69C8245440A754FBEE5E99354D8059A775A57A855944A | |||
| 8004 | crystal reports 2011 sp4 product key.exe | C:\Users\admin\AppData\Local\Temp\Lp.msi | binary | |
MD5:2921329FDA4F2CEACB29083083093F40 | SHA256:65C7840A16DB42F4EC59C03EAF6D5E8F05A72CD0D813E33497784B837248847D | |||
| 8004 | crystal reports 2011 sp4 product key.exe | C:\Users\admin\AppData\Local\Temp\Protest.msi | binary | |
MD5:3EC5ABBB3FAE37C10FD9C92565C7847D | SHA256:8C330CED47F5E4E7BCFE0393FF2867B7BD4D368D2118FF88893EA554BE00C5F4 | |||
| 8004 | crystal reports 2011 sp4 product key.exe | C:\Users\admin\AppData\Local\Temp\Aging.msi | text | |
MD5:226100B77578E8BA2587F189D37DA9B9 | SHA256:E674CD0E75D891D6F95DB78CEAF99E918AD0563D63477CC1AA79E35CC6DF5F69 | |||
| 8004 | crystal reports 2011 sp4 product key.exe | C:\Users\admin\AppData\Local\Temp\Twinks.msi | binary | |
MD5:563A0C1A960B8D66B5D4E8647DD3BFA5 | SHA256:9CAA37BBF9D6B1E3AD26E168F793464F345384CF0550DF5AEBBB172B3E46C252 | |||
| 8004 | crystal reports 2011 sp4 product key.exe | C:\Users\admin\AppData\Local\Temp\Likely.msi | binary | |
MD5:D57BF1E897F117908A9542F1FEB73692 | SHA256:42E771D2469F12A6498DAE3E9C8869769B4B13B4F100D628E15C3491E0D9FEDB | |||
| 8004 | crystal reports 2011 sp4 product key.exe | C:\Users\admin\AppData\Local\Temp\Larry.msi | binary | |
MD5:466FB8D686703A90BDF3331C93B62B09 | SHA256:2122A2C851BB34DFBC063735B0544F4434ABC134192E9E7B5FE2CFE5A27E72D3 | |||
| 8004 | crystal reports 2011 sp4 product key.exe | C:\Users\admin\AppData\Local\Temp\Receivers.msi | compressed | |
MD5:BEEA6111DFB78010EE397DD813049987 | SHA256:0DC4C0F2F0B88B3DB1BE1D123AC736B3A7744F628879C2E798951B575D614D4B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.43:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7840 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7840 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6668 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.43:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
QQRWQKNbOuL.QQRWQKNbOuL |
| unknown |