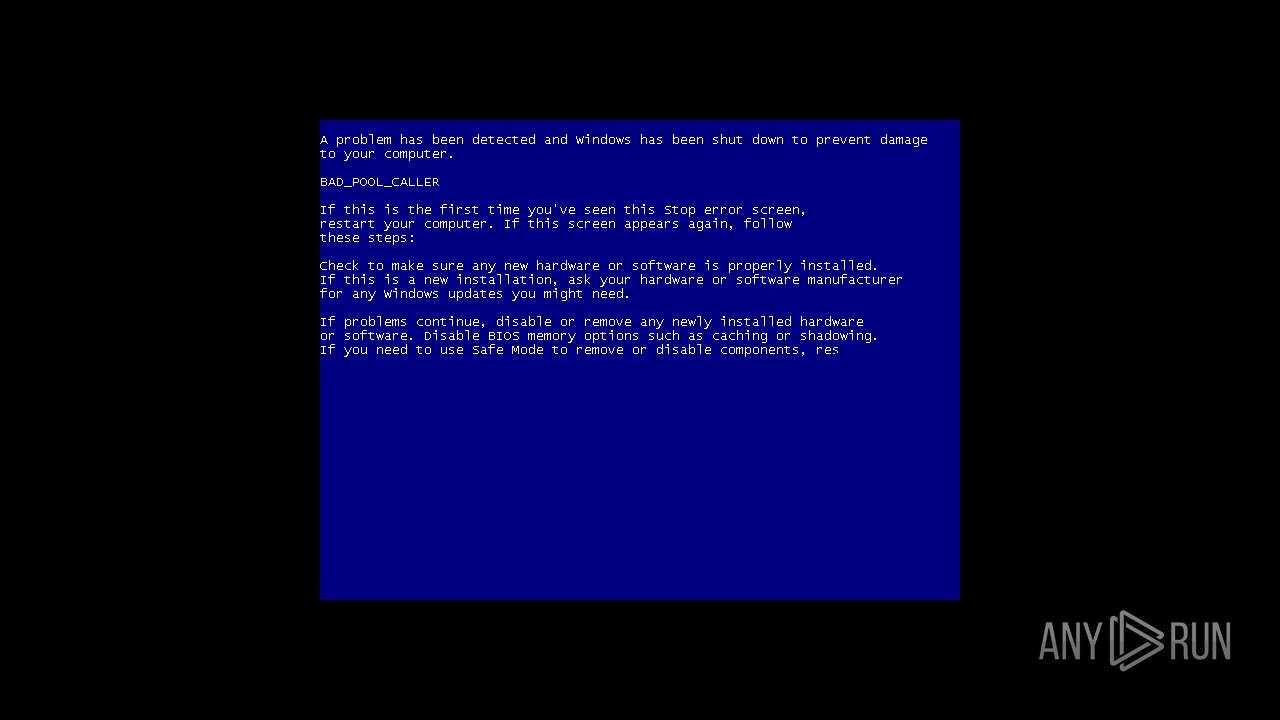
| File name: | WEXTRACT.exe |
| Full analysis: | https://app.any.run/tasks/638cd007-f49a-402a-8fe4-dc07809efba7 |
| Verdict: | Malicious activity |
| Analysis date: | December 28, 2023, 17:52:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 12382062C6ABC23EBDF6AEC25F383FA4 |
| SHA1: | 9834DC9A4FD1F037C574C27A932C96D68409C882 |
| SHA256: | 24B66C0D6F26F5DE09B4CB7A2496BF87AD0ED9D45E846870DEE70941B565BC3C |
| SSDEEP: | 49152:SLnemI4SBofQmk5fozRgpxdsFzIv8HqCTmU4ABHA+xskww4YmUvHLcL8bbtg8VWl:2n2CfQmktozRg7dsFzIv8HxTR40A2skD |
MALICIOUS
Changes the autorun value in the registry
- explothe.exe (PID: 584)
Uses Task Scheduler to run other applications
- explothe.exe (PID: 584)
SUSPICIOUS
Reads the Internet Settings
- 5NS8xD0.exe (PID: 1044)
- explothe.exe (PID: 584)
- cmd.exe (PID: 1820)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1592)
- explothe.exe (PID: 584)
- 7ct2pQ14.exe (PID: 764)
Executing commands from a ".bat" file
- 7ct2pQ14.exe (PID: 764)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 1592)
INFO
Create files in a temporary directory
- WEXTRACT.exe (PID: 120)
- Rw4YT03.exe (PID: 128)
- nf4rn60.exe (PID: 124)
- qP5Qb44.exe (PID: 1356)
- FJ4OU94.exe (PID: 1776)
- kK0yG24.exe (PID: 1432)
- 5NS8xD0.exe (PID: 1044)
- 7ct2pQ14.exe (PID: 764)
Drops the executable file immediately after the start
- WEXTRACT.exe (PID: 120)
- Rw4YT03.exe (PID: 128)
- nf4rn60.exe (PID: 124)
- qP5Qb44.exe (PID: 1356)
- FJ4OU94.exe (PID: 1776)
- kK0yG24.exe (PID: 1432)
- 5NS8xD0.exe (PID: 1044)
Checks supported languages
- WEXTRACT.exe (PID: 120)
- Rw4YT03.exe (PID: 128)
- nf4rn60.exe (PID: 124)
- qP5Qb44.exe (PID: 1356)
- 1rs14bk1.exe (PID: 1288)
- 2Ro9432.exe (PID: 324)
- 3Hm09Ej.exe (PID: 2016)
- AppLaunch.exe (PID: 1056)
- AppLaunch.exe (PID: 2420)
- FJ4OU94.exe (PID: 1776)
- kK0yG24.exe (PID: 1432)
- explothe.exe (PID: 584)
- 6dg6UC8.exe (PID: 1836)
- 4ew995pG.exe (PID: 268)
- AppLaunch.exe (PID: 668)
- 5NS8xD0.exe (PID: 1044)
- 7ct2pQ14.exe (PID: 764)
Process drops legitimate windows executable
- WEXTRACT.exe (PID: 120)
- Rw4YT03.exe (PID: 128)
- nf4rn60.exe (PID: 124)
- FJ4OU94.exe (PID: 1776)
- kK0yG24.exe (PID: 1432)
Reads the computer name
- AppLaunch.exe (PID: 1056)
- AppLaunch.exe (PID: 668)
- 5NS8xD0.exe (PID: 1044)
- explothe.exe (PID: 584)
Starts itself from another location
- 5NS8xD0.exe (PID: 1044)
Application launched itself
- msedge.exe (PID: 2192)
- msedge.exe (PID: 2312)
- cmd.exe (PID: 1592)
- msedge.exe (PID: 2320)
- msedge.exe (PID: 2296)
- msedge.exe (PID: 2328)
- msedge.exe (PID: 2736)
- msedge.exe (PID: 664)
- msedge.exe (PID: 1036)
- msedge.exe (PID: 2792)
- msedge.exe (PID: 2888)
Reads the machine GUID from the registry
- AppLaunch.exe (PID: 668)
- explothe.exe (PID: 584)
Checks proxy server information
- explothe.exe (PID: 584)
Connects to unusual port
- AppLaunch.exe (PID: 668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:05:25 00:49:06+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.13 |
| CodeSize: | 25600 |
| InitializedDataSize: | 1590784 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6a60 |
| OSVersion: | 10 |
| ImageVersion: | 10 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.17763.1 |
| ProductVersionNumber: | 11.0.17763.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Win32 Cabinet Self-Extractor |
| FileVersion: | 11.00.17763.1 (WinBuild.160101.0800) |
| InternalName: | Wextract |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | WEXTRACT.EXE .MUI |
| ProductName: | Internet Explorer |
| ProductVersion: | 11.00.17763.1 |
Total processes
109
Monitored processes
72
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Users\admin\Desktop\WEXTRACT.exe" | C:\Users\admin\Desktop\WEXTRACT.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 11.00.17763.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 124 | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\nf4rn60.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\nf4rn60.exe | — | Rw4YT03.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 11.00.17763.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 128 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\Rw4YT03.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\Rw4YT03.exe | — | WEXTRACT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 11.00.17763.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 268 | C:\Users\admin\AppData\Local\Temp\IXP003.TMP\4ew995pG.exe | C:\Users\admin\AppData\Local\Temp\IXP003.TMP\4ew995pG.exe | — | FJ4OU94.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 324 | C:\Users\admin\AppData\Local\Temp\IXP005.TMP\2Ro9432.exe | C:\Users\admin\AppData\Local\Temp\IXP005.TMP\2Ro9432.exe | — | qP5Qb44.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 584 | "C:\Users\admin\AppData\Local\Temp\fefffe8cea\explothe.exe" | C:\Users\admin\AppData\Local\Temp\fefffe8cea\explothe.exe | 5NS8xD0.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 664 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument https://steamcommunity.com/openid/loginform/ | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 668 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe | 4ew995pG.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET ClickOnce Launch Utility Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 764 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\7ct2pQ14.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\7ct2pQ14.exe | — | WEXTRACT.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 796 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0x178,0x17c,0x180,0x14c,0x188,0x6d63f598,0x6d63f5a8,0x6d63f5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
6 202
Read events
6 054
Write events
148
Delete events
0
Modification events
| (PID) Process: | (1044) 5NS8xD0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1044) 5NS8xD0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1044) 5NS8xD0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1044) 5NS8xD0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (584) explothe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders |
| Operation: | write | Name: | Startup |
Value: %USERPROFILE%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup | |||
| (PID) Process: | (584) explothe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (584) explothe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (584) explothe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (584) explothe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2296) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
Executable files
13
Suspicious files
12
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2636 | msedge.exe | — | ||
MD5:— | SHA256:— | |||
| 2052 | msedge.exe | — | ||
MD5:— | SHA256:— | |||
| 2660 | msedge.exe | — | ||
MD5:— | SHA256:— | |||
| 2324 | msedge.exe | — | ||
MD5:— | SHA256:— | |||
| 2672 | msedge.exe | — | ||
MD5:— | SHA256:— | |||
| 2900 | msedge.exe | — | ||
MD5:— | SHA256:— | |||
| 1220 | msedge.exe | — | ||
MD5:— | SHA256:— | |||
| 128 | Rw4YT03.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\6dg6UC8.exe | executable | |
MD5:738B51E076E429595BD12A2E4408DFDC | SHA256:82EC00E88797FF182391E628CB89C05954D10862180A51581D18E7B24FB11C70 | |||
| 120 | WEXTRACT.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\7ct2pQ14.exe | executable | |
MD5:EE1300A5DD8B53671D572AB4FBA80990 | SHA256:306246151C2AAA6C9136B1E5CBB778FE8FEFA79B0B6F6052A9D93654455748F2 | |||
| 120 | WEXTRACT.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\Rw4YT03.exe | executable | |
MD5:C21BFF299A662C17AF5E4E9730B3A464 | SHA256:735390B07D329A0474622E85810F58C274B467C311EA35D714EC26B324E7286D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
11
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 23.214.232.9:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133482596214840000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
584 | explothe.exe | 77.91.124.1:80 | — | Foton Telecom CJSC | RU | unknown |
668 | AppLaunch.exe | 77.91.124.86:19084 | — | Foton Telecom CJSC | RU | malicious |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
— | — | 23.214.232.9:80 | query.prod.cms.rt.microsoft.com | Reliance Jio Infocomm Limited | IN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |