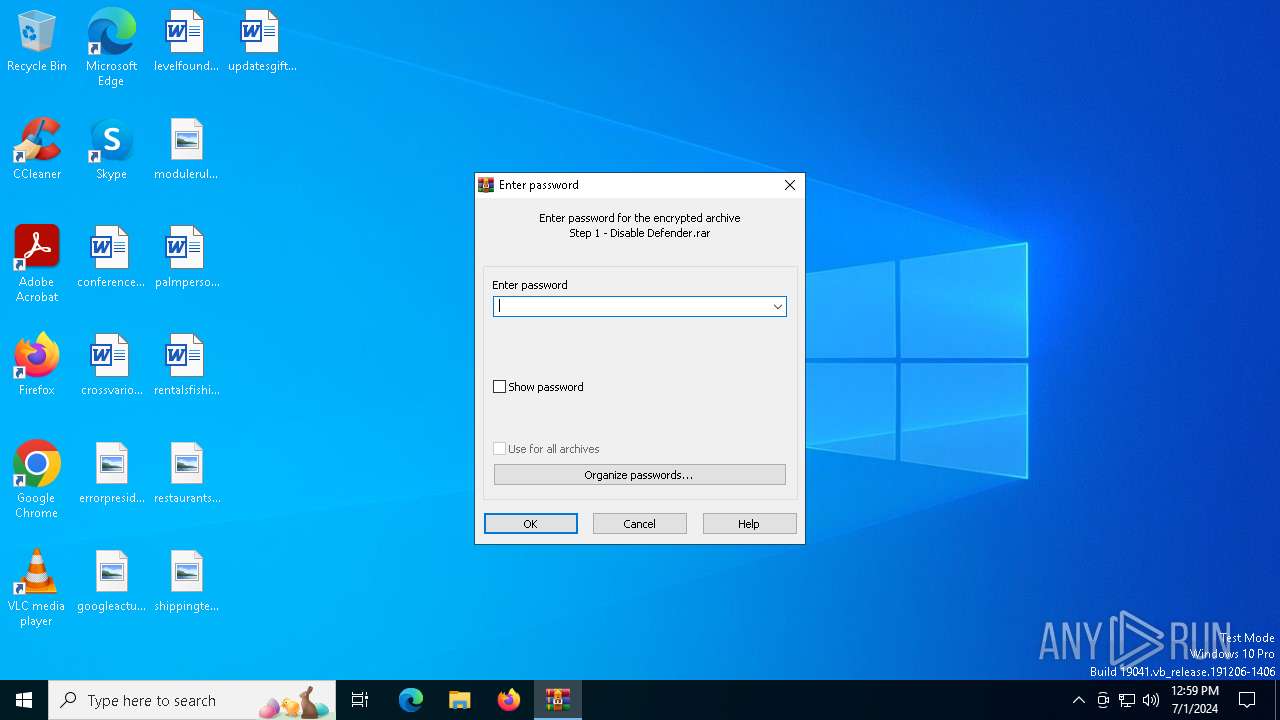
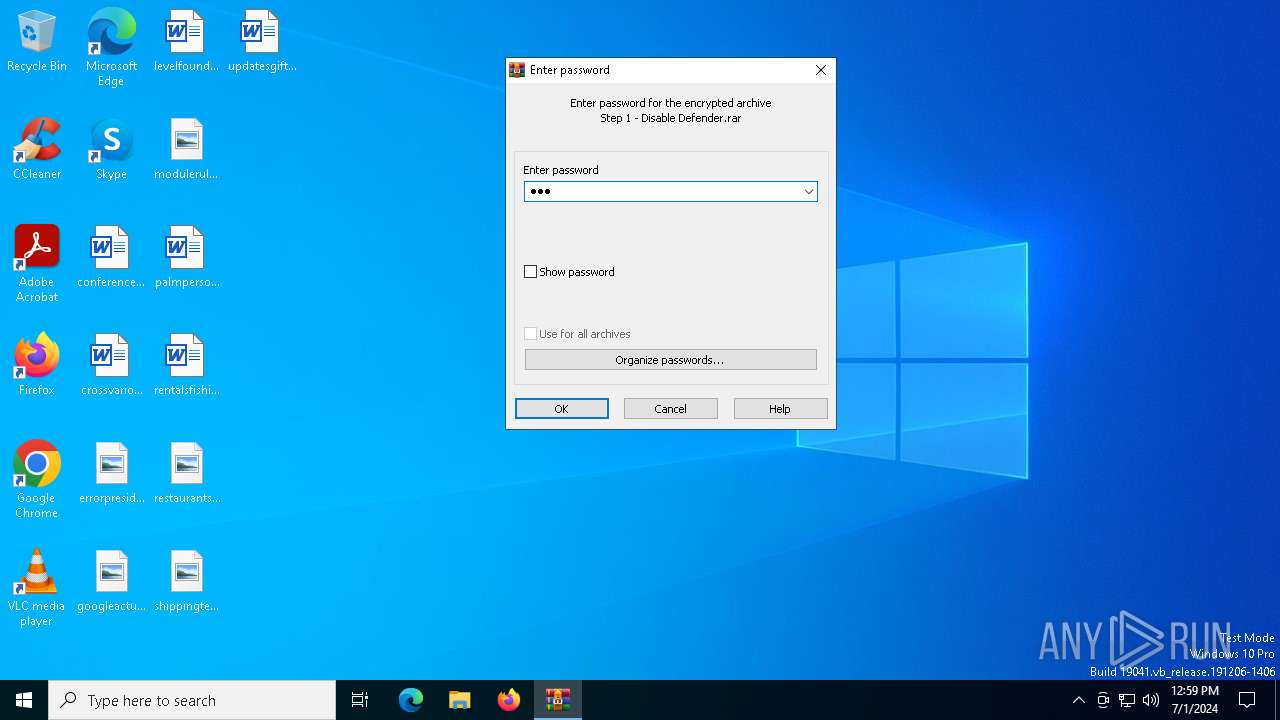
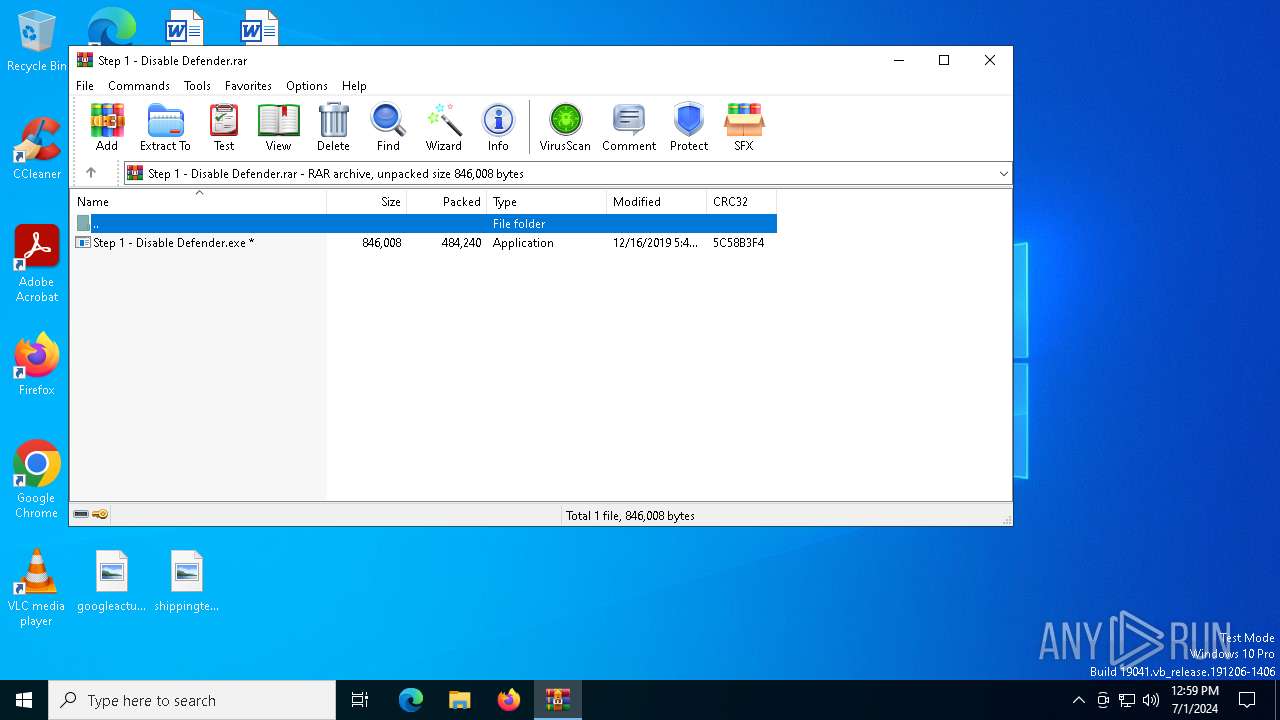
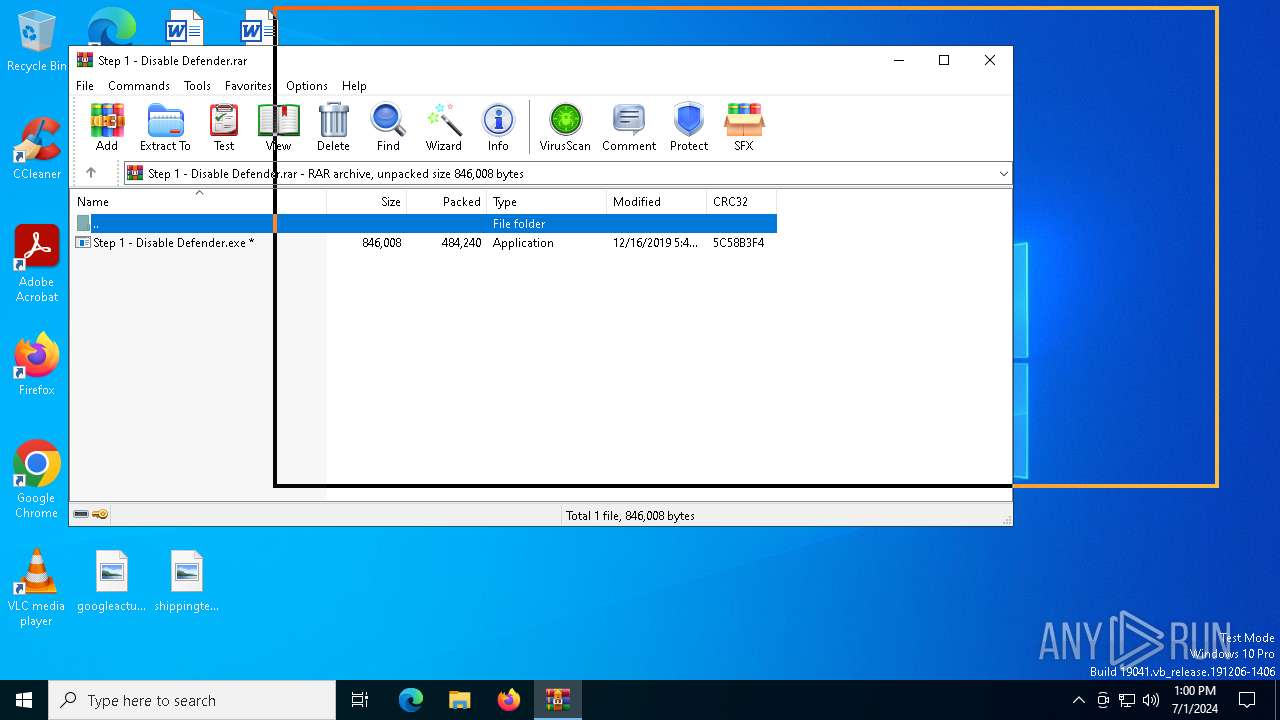
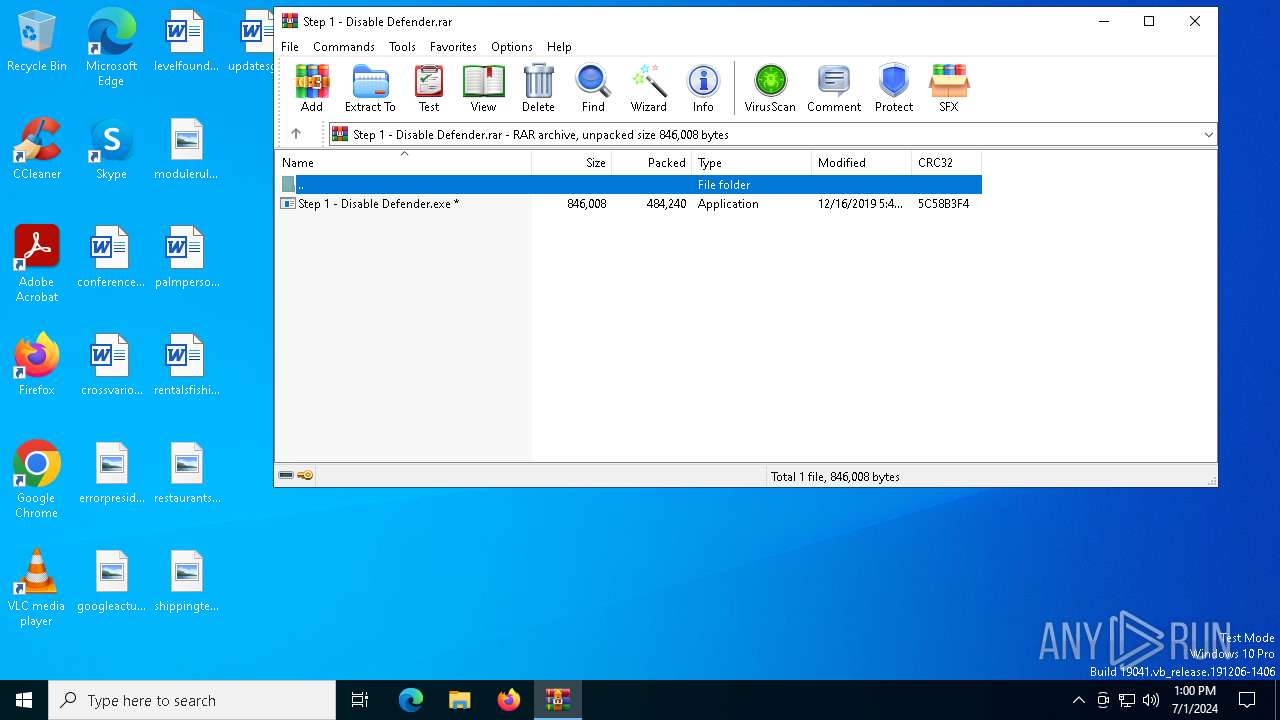
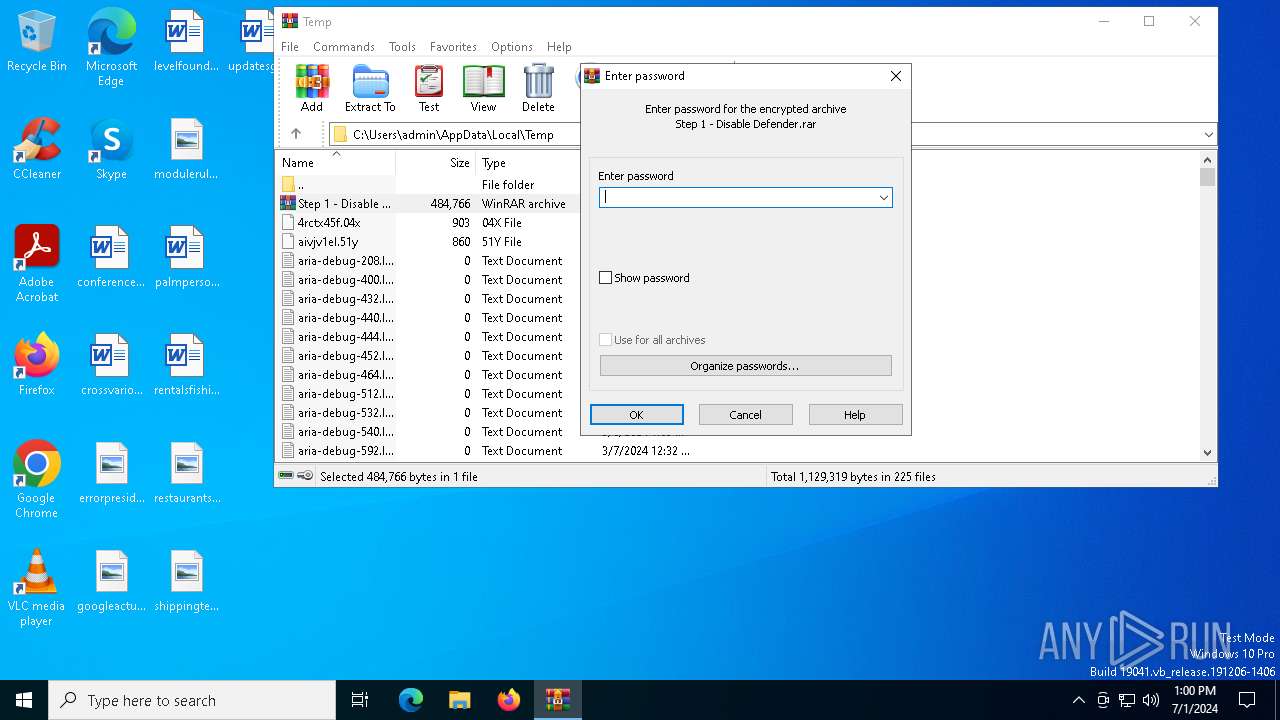
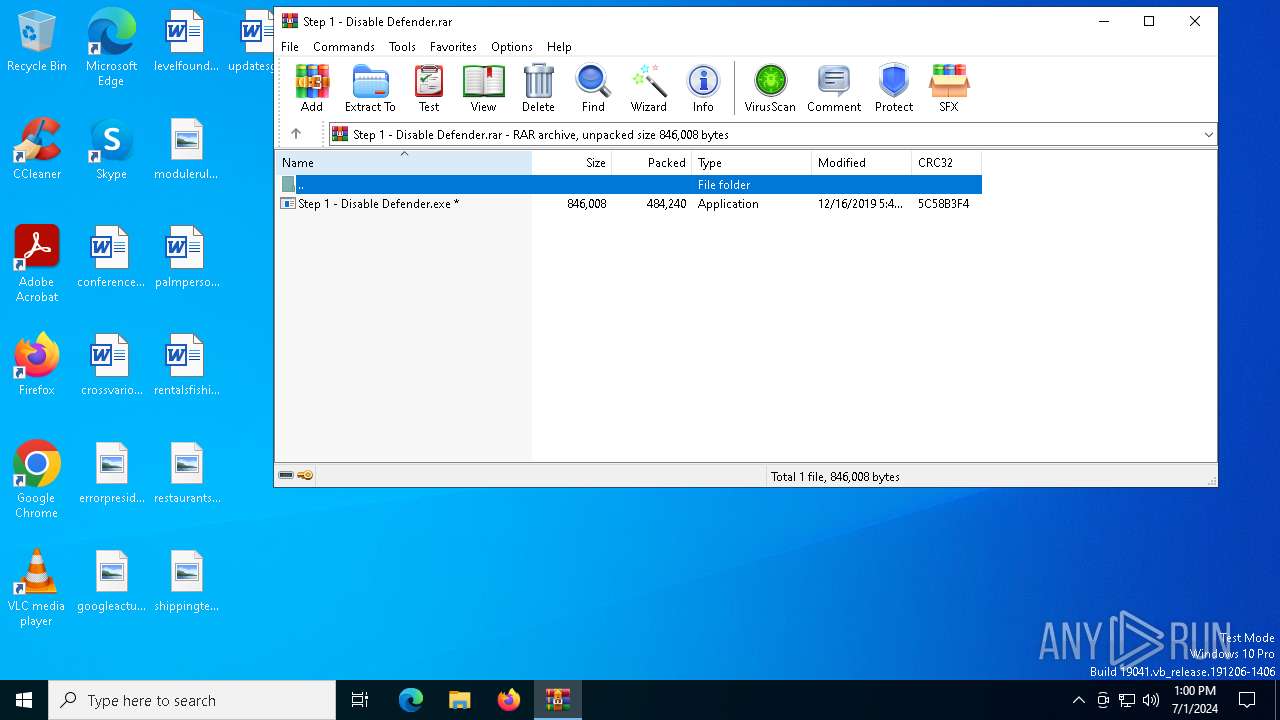
| File name: | Step 1 - Disable Defender.rar |
| Full analysis: | https://app.any.run/tasks/d10b914a-31c8-4f2b-876a-0f38c5bfaf7b |
| Verdict: | Malicious activity |
| Analysis date: | July 01, 2024, 12:59:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 9EFE8E6C7B341C6AC7BB9824CB2E3A10 |
| SHA1: | FC6D39D33CBD65EAE95F0C3E97194DF1E6B59B46 |
| SHA256: | 2491A416C86C1988905DF7A95B82C3CCF8FD97B9D0C959201FF316033CE61782 |
| SSDEEP: | 12288:4YCrAN1avQFqyQmohHyuS6+PGB1Cuu5C8xWbYvl/0Cc1oaYeEm:4YwDvQu9hHynPGS75NxWUp0Ccm5m |
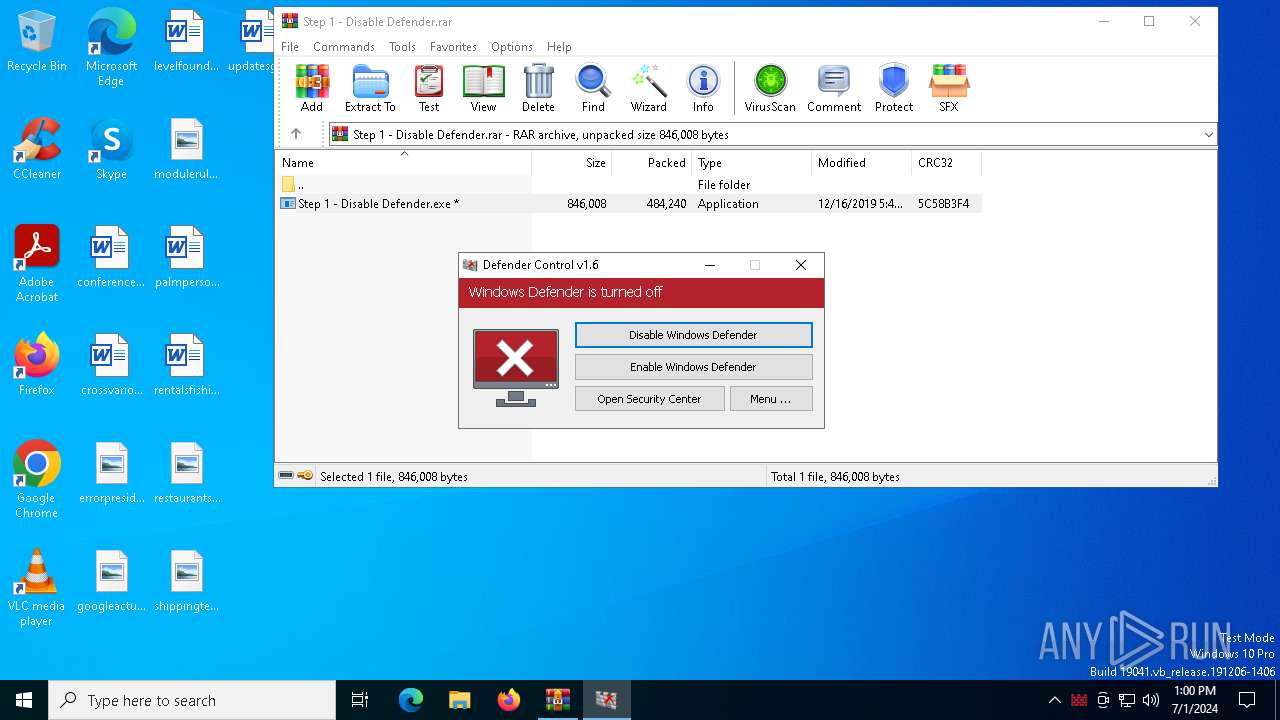
MALICIOUS
Disables Windows Defender
- Step 1 - Disable Defender.exe (PID: 1016)
- Step 1 - Disable Defender.exe (PID: 420)
- Step 1 - Disable Defender.exe (PID: 1672)
Creates or modifies Windows services
- Step 1 - Disable Defender.exe (PID: 420)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2416)
Application launched itself
- Step 1 - Disable Defender.exe (PID: 1672)
- Step 1 - Disable Defender.exe (PID: 1016)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2416)
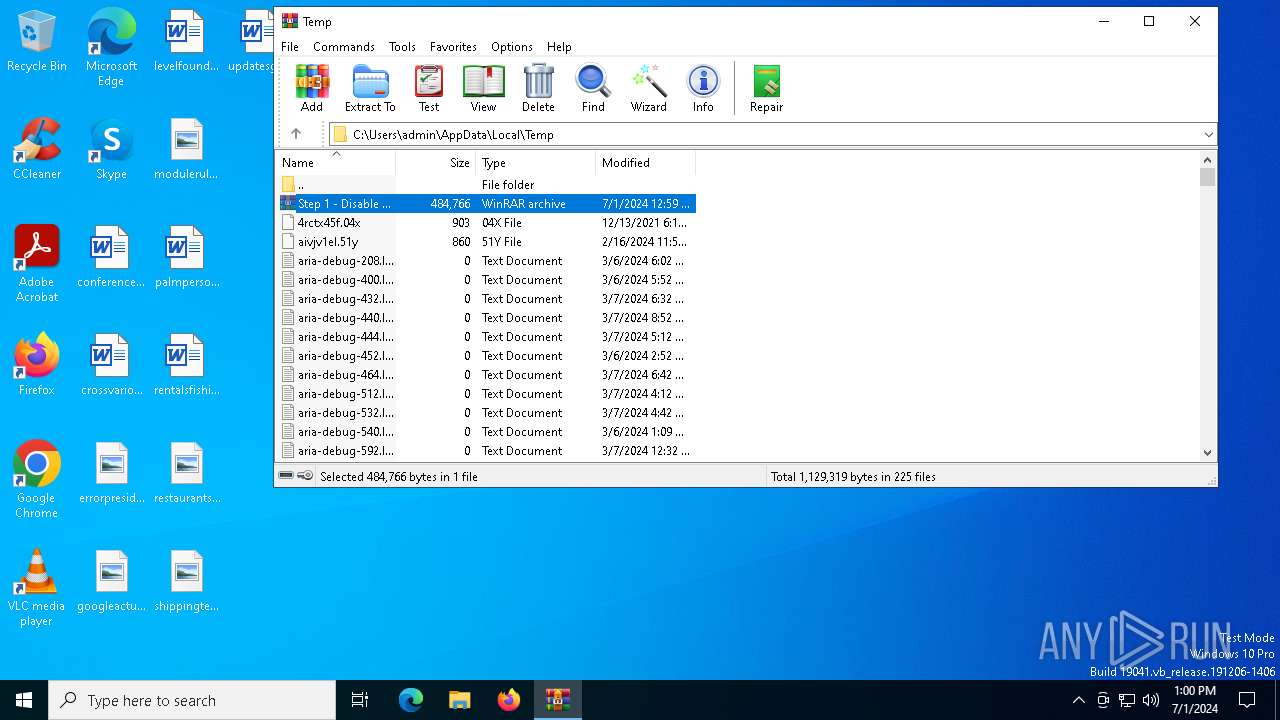
Create files in a temporary directory
- Step 1 - Disable Defender.exe (PID: 1016)
Reads mouse settings
- Step 1 - Disable Defender.exe (PID: 1016)
- Step 1 - Disable Defender.exe (PID: 1672)
- Step 1 - Disable Defender.exe (PID: 420)
Checks supported languages
- Step 1 - Disable Defender.exe (PID: 1672)
- Step 1 - Disable Defender.exe (PID: 420)
- Step 1 - Disable Defender.exe (PID: 1016)
Reads the computer name
- Step 1 - Disable Defender.exe (PID: 1016)
- Step 1 - Disable Defender.exe (PID: 1672)
- Step 1 - Disable Defender.exe (PID: 420)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2416)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
150
Monitored processes
5
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2416.12859\Step 1 - Disable Defender.exe" /TI 1 | C:\Users\admin\AppData\Local\Temp\Rar$EXb2416.12859\Step 1 - Disable Defender.exe | — | Step 1 - Disable Defender.exe | |||||||||||
User: SYSTEM Company: www.sordum.org Integrity Level: SYSTEM Description: Windows Defender Control Exit code: 0 Version: 1.6.0.0 Modules
| |||||||||||||||
| 1016 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2416.12859\Step 1 - Disable Defender.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2416.12859\Step 1 - Disable Defender.exe | WinRAR.exe | ||||||||||||
User: admin Company: www.sordum.org Integrity Level: HIGH Description: Windows Defender Control Version: 1.6.0.0 Modules
| |||||||||||||||
| 1672 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2416.12859\Step 1 - Disable Defender.exe" /SYS 1 | C:\Users\admin\AppData\Local\Temp\Rar$EXb2416.12859\Step 1 - Disable Defender.exe | Step 1 - Disable Defender.exe | ||||||||||||
User: SYSTEM Company: www.sordum.org Integrity Level: SYSTEM Description: Windows Defender Control Exit code: 0 Version: 1.6.0.0 Modules
| |||||||||||||||
| 2416 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Step 1 - Disable Defender.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4624 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2416.12859\Step 1 - Disable Defender.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2416.12859\Step 1 - Disable Defender.exe | — | WinRAR.exe | |||||||||||
User: admin Company: www.sordum.org Integrity Level: MEDIUM Description: Windows Defender Control Exit code: 3221226540 Version: 1.6.0.0 Modules
| |||||||||||||||
Total events
32 614
Read events
32 575
Write events
39
Delete events
0
Modification events
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Step 1 - Disable Defender.rar | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
1
Suspicious files
4
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1672 | Step 1 - Disable Defender.exe | C:\WINDOWS\TEMP\erwqdby | text | |
MD5:B9B96CDCEF855AB98EE55AF4EC32C96A | SHA256:2721F4949FDF46A89A1454E4EDBC3BC178F764F58955BEFA74BCBA57F7B0FA45 | |||
| 1016 | Step 1 - Disable Defender.exe | C:\WINDOWS\System32\GroupPolicy\gpt.ini | text | |
MD5:617078BCAAA2FF95E4438D83A49CE878 | SHA256:42EC7933F10ABA61202B3FC7D3C02D47CFD0C953A8F2CB0E39DF3069697F99EF | |||
| 1672 | Step 1 - Disable Defender.exe | C:\WINDOWS\TEMP\aut9AF4.tmp | binary | |
MD5:446A845A0963C84E6B7F1C6B648ADF62 | SHA256:950BD3BF22CA0BF4DAA3B12AF5EB6356F0810E93AE1E86FB419646C3AAB588DB | |||
| 1016 | Step 1 - Disable Defender.exe | C:\Users\admin\AppData\Local\Temp\rqeonyt | text | |
MD5:B9B96CDCEF855AB98EE55AF4EC32C96A | SHA256:2721F4949FDF46A89A1454E4EDBC3BC178F764F58955BEFA74BCBA57F7B0FA45 | |||
| 1016 | Step 1 - Disable Defender.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2416.12859\Step 1 - Disable Defender.ini | text | |
MD5:69866EAE7B3249210BEA54CF3D228309 | SHA256:5B744FEC9B03BCF71C84C6A43341AEB14D385D8F5F8EB6BC27A2C39087DF4CF1 | |||
| 2416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2416.12859\Step 1 - Disable Defender.exe | executable | |
MD5:3A24A7B7C1BA74A5AFA50F88BA81D550 | SHA256:A201F7F81277E28C0BDD680427B979AEE70E42E8A98C67F11E7C83D02F8FE7AE | |||
| 1016 | Step 1 - Disable Defender.exe | C:\Users\admin\AppData\Local\Temp\aut7AAB.tmp | binary | |
MD5:446A845A0963C84E6B7F1C6B648ADF62 | SHA256:950BD3BF22CA0BF4DAA3B12AF5EB6356F0810E93AE1E86FB419646C3AAB588DB | |||
| 420 | Step 1 - Disable Defender.exe | C:\WINDOWS\TEMP\ebldptx | text | |
MD5:B9B96CDCEF855AB98EE55AF4EC32C96A | SHA256:2721F4949FDF46A89A1454E4EDBC3BC178F764F58955BEFA74BCBA57F7B0FA45 | |||
| 1016 | Step 1 - Disable Defender.exe | C:\WINDOWS\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:A205A64883D657DE511B900BEC778255 | SHA256:02BD4DD91B5A9AA5EE58C09F66D1E79677AFCFED8756B483907B5AAC555CE06C | |||
| 420 | Step 1 - Disable Defender.exe | C:\WINDOWS\TEMP\aut9C6B.tmp | binary | |
MD5:446A845A0963C84E6B7F1C6B648ADF62 | SHA256:950BD3BF22CA0BF4DAA3B12AF5EB6356F0810E93AE1E86FB419646C3AAB588DB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
60
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2568 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2568 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
4680 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
1236 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
4680 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2568 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4656 | SearchApp.exe | 92.123.104.14:443 | — | Akamai International B.V. | DE | unknown |
3172 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2276 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2568 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2568 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3040 | OfficeClickToRun.exe | 13.69.116.109:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
r.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |