| File name: | BitDefender.exe |
| Full analysis: | https://app.any.run/tasks/411dfa73-6ef7-47a2-85a6-0a0c0e1f1afd |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2025, 11:41:41 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 5C39420363460DC4E1ED830666F679D1 |
| SHA1: | 1FBD10591C0AB6E633D4B2F2CE2EEFB3B9E5F2B8 |
| SHA256: | 248A36071B83F7F98F8F87EED5BEFF1F4828EAA065B7A1FE63F0A525CB46AC88 |
| SSDEEP: | 98304:7qfxOIRRTifp/VQc5c13Xf51rwxeT+fGUGDLWX8rjsdJkkwN25fJ8s9bkNOmLdnY:sHmUHlKF6 |
MALICIOUS
Executing a file with an untrusted certificate
- BitDefender.exe (PID: 3900)
Antivirus name has been found in the command line (generic signature)
- BitDefender.exe (PID: 3900)
- BitDefender.exe (PID: 4776)
SUSPICIOUS
Process drops legitimate windows executable
- BitDefender.exe (PID: 3900)
- WinRAR.exe (PID: 1452)
The process drops C-runtime libraries
- BitDefender.exe (PID: 3900)
Executable content was dropped or overwritten
- BitDefender.exe (PID: 3900)
Application launched itself
- BitDefender.exe (PID: 3900)
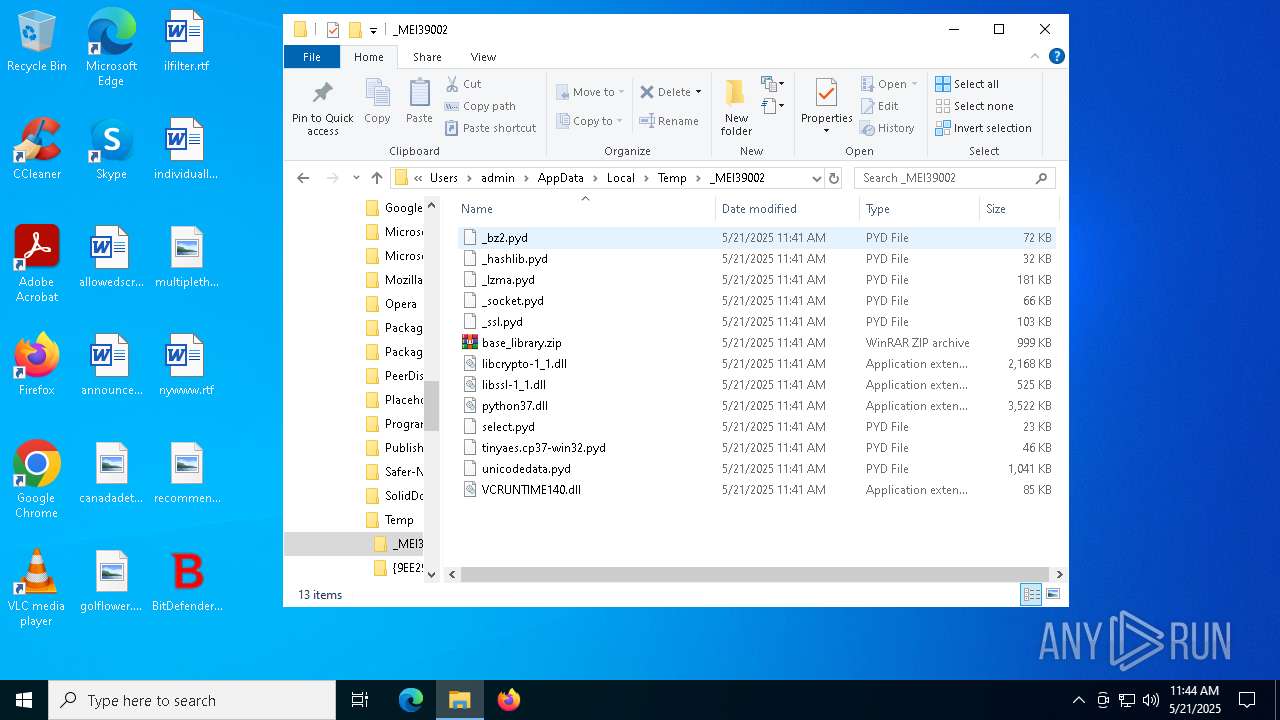
Process drops python dynamic module
- BitDefender.exe (PID: 3900)
Loads Python modules
- BitDefender.exe (PID: 4776)
Connects to unusual port
- BitDefender.exe (PID: 4776)
There is functionality for taking screenshot (YARA)
- BitDefender.exe (PID: 3900)
- BitDefender.exe (PID: 4776)
INFO
Checks supported languages
- BitDefender.exe (PID: 3900)
- BitDefender.exe (PID: 4776)
Reads the computer name
- BitDefender.exe (PID: 3900)
- BitDefender.exe (PID: 4776)
The sample compiled with english language support
- BitDefender.exe (PID: 3900)
- WinRAR.exe (PID: 1452)
Create files in a temporary directory
- BitDefender.exe (PID: 3900)
Reads the machine GUID from the registry
- BitDefender.exe (PID: 4776)
PyInstaller has been detected (YARA)
- BitDefender.exe (PID: 3900)
- BitDefender.exe (PID: 4776)
Checks proxy server information
- slui.exe (PID: 6652)
Manual execution by a user
- WinRAR.exe (PID: 1452)
Reads the software policy settings
- slui.exe (PID: 6652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:15 15:43:23+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.36 |
| CodeSize: | 151552 |
| InitializedDataSize: | 72192 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa510 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
154
Monitored processes
9
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1452 | "C:\Program Files\WinRAR\WinRAR.exe" a -ep1 -scul -r0 -iext -- _MEI39002.rar C:\Users\admin\AppData\Local\Temp\_MEI39002 | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2284 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 3760 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3900 | "C:\Users\admin\Desktop\BitDefender.exe" | C:\Users\admin\Desktop\BitDefender.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 4724 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 4776 | "C:\Users\admin\Desktop\BitDefender.exe" | C:\Users\admin\Desktop\BitDefender.exe | BitDefender.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6068 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6652 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6852 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 823
Read events
3 819
Write events
4
Delete events
0
Modification events
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1452) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
12
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
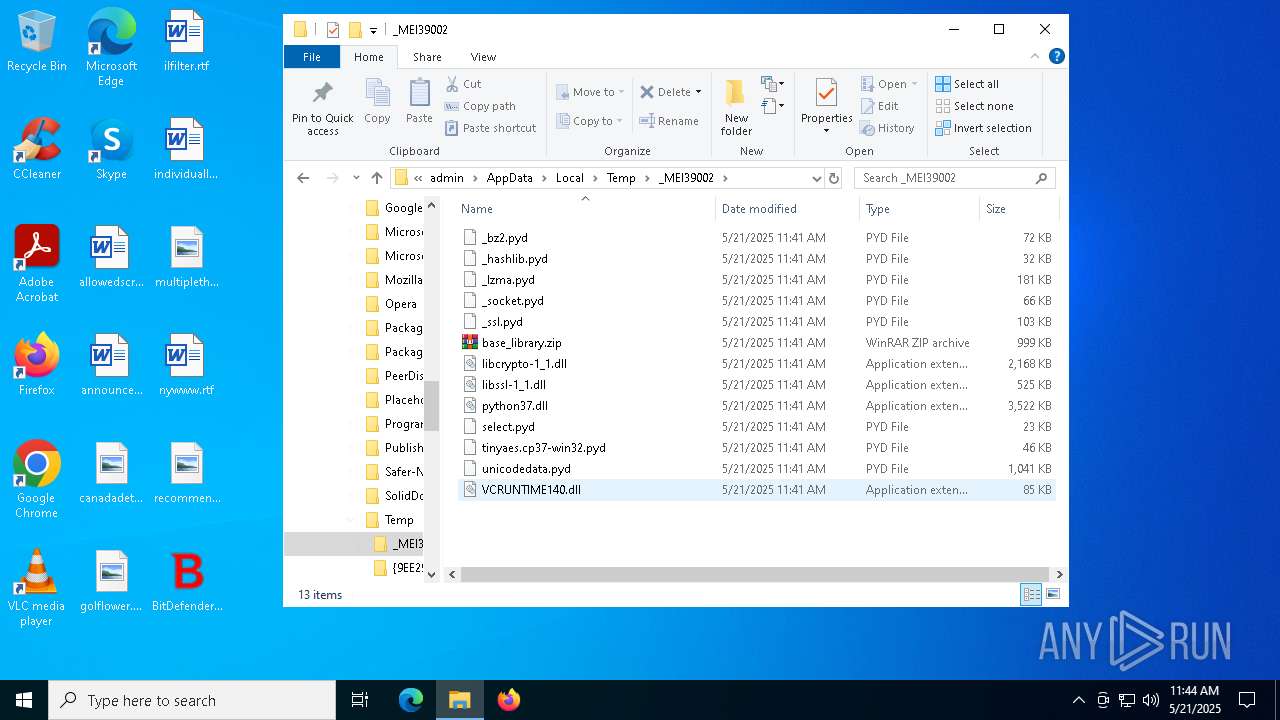
| 3900 | BitDefender.exe | C:\Users\admin\AppData\Local\Temp\_MEI39002\VCRUNTIME140.dll | executable | |
MD5:AE96651CFBD18991D186A029CBECB30C | SHA256:1B372F064EACB455A0351863706E6326CA31B08E779A70DE5DE986B5BE8069A1 | |||
| 3900 | BitDefender.exe | C:\Users\admin\AppData\Local\Temp\_MEI39002\_bz2.pyd | executable | |
MD5:FF5AC8FB724EDB1635E2AD985F98EE5B | SHA256:B94F64FCB49F40682ED794FA1940A1DC0C8A28F24A1768D3BFE774CF75F59B62 | |||
| 3900 | BitDefender.exe | C:\Users\admin\AppData\Local\Temp\_MEI39002\_lzma.pyd | executable | |
MD5:65880A33015AF2030A08987924CA737B | SHA256:A71366B95D89D1539A6EE751D48A969C1BCA1AA75116424CC5F905F32A625EEA | |||
| 3900 | BitDefender.exe | C:\Users\admin\AppData\Local\Temp\_MEI39002\_ssl.pyd | executable | |
MD5:CC5C8EB32ACB2261C42A7285D436CCA9 | SHA256:07EA50E536886F68473635FFEFCFCAA7266E63C478EF039BA100DDF02F88CE61 | |||
| 3900 | BitDefender.exe | C:\Users\admin\AppData\Local\Temp\_MEI39002\libcrypto-1_1.dll | executable | |
MD5:C0E55A25DD5C5447F15EED0CA6552AB7 | SHA256:9FEFBA93FA3300732B7E68FB3B4DBB57BF2726889772A1D0D6694A71820D71F3 | |||
| 3900 | BitDefender.exe | C:\Users\admin\AppData\Local\Temp\_MEI39002\libssl-1_1.dll | executable | |
MD5:5ADB49CC84ABD6D3C8F959CA5A146AD7 | SHA256:F4D5DF50BDF3E7304C67C81ACE83263C8D0F0E28087C6104C21150BFEDA86B8D | |||
| 3900 | BitDefender.exe | C:\Users\admin\AppData\Local\Temp\_MEI39002\python37.dll | executable | |
MD5:D49EAC0FAA510F2B2A8934A0F4E4A46F | SHA256:625CA7BB2D34A3986F77C0C5CE572A08FEBFCACF5050A986507E822FF694DCAA | |||
| 3900 | BitDefender.exe | C:\Users\admin\AppData\Local\Temp\_MEI39002\_socket.pyd | executable | |
MD5:A4BD8E0C0597A22C3F0601FE798668AA | SHA256:96B0A3CFC16E215F0EF5D1E206F0137B4255005052720E91A58BC98CDE8C898E | |||
| 3900 | BitDefender.exe | C:\Users\admin\AppData\Local\Temp\_MEI39002\_hashlib.pyd | executable | |
MD5:E84E1BA269371E439C2D52024ACA6535 | SHA256:2FCB297733E6080480AC24CF073FF5E239FB02A1CE9694313C5047F9C58D781B | |||
| 3900 | BitDefender.exe | C:\Users\admin\AppData\Local\Temp\_MEI39002\tinyaes.cp37-win32.pyd | executable | |
MD5:2EE4A5453D610134BE563564E0D832FA | SHA256:EDACA59C7081DD3355AD53830ED2153EB905EB72FF96750695DF51C7C508A957 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
89
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5512 | SIHClient.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5512 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5512 | SIHClient.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5512 | SIHClient.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
5512 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5512 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5512 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
5512 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4776 | BitDefender.exe | 185.170.154.197:7645 | — | Node4 Limited | GB | unknown |
6544 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5512 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
5512 | SIHClient.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |