| URL: | https://can01.safelinks.protection.outlook.com/?url=https%3A%2F%2Fu10704350.ct.sendgrid.net%2Fls%2Fclick%3Fupn%3Dn0I16x2JTvUQ5lBFUSFflE5RXCzViUzPnq9b1wKq9Nc0uHXWH-2FSiU3boqrP0TzkwUkk-2BtIRAYgmkiirvxnT85Jmi7VEffIEaPKTZ7vBf-2FgO2A2BOQvnjEhNz-2BhiKm9KRzeUiAp1T-2FHezuZ-2BA1ssW7g-3D-3D_YOS_uAGIKxVHnzoGVmPcnUwHmaU-2FnkoJkDSw4aHFiI-2B0y4Fhy58-2BRG59axtnosJJcUGv8X7JXZioX2JD6uR3gQZeHqpELfestL6V8E-2BR-2FLxVjVCIvADFiCk-2Fb75CxRZCcrmkH9U-2F873t8hRTbMuiEkpqZI1X7-2B1uAjkBOEu6MJIMi64iS8dhfVITYlBTFWg5lDn6UoPVFy-2B4CfTGgZ4Su65F-2FFxiEHnQdniJKwhGIWoe598-3D&data=05%7C01%7Cdaniel.thibault%40saaq.gouv.qc.ca%7C62ec7c6d83764198c20208da7bf2757d%7C4df32e45efd840c193ead0041b95d83b%7C0%7C0%7C637958578649493597%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C2000%7C%7C%7C&sdata=xYZMHHYWq4jIGfSMOm142iT%2FoOGCwXfebm5gEiCtR9s%3D&reserved=0 |
| Full analysis: | https://app.any.run/tasks/e257c856-35a3-476c-a51e-fe82b262121b |
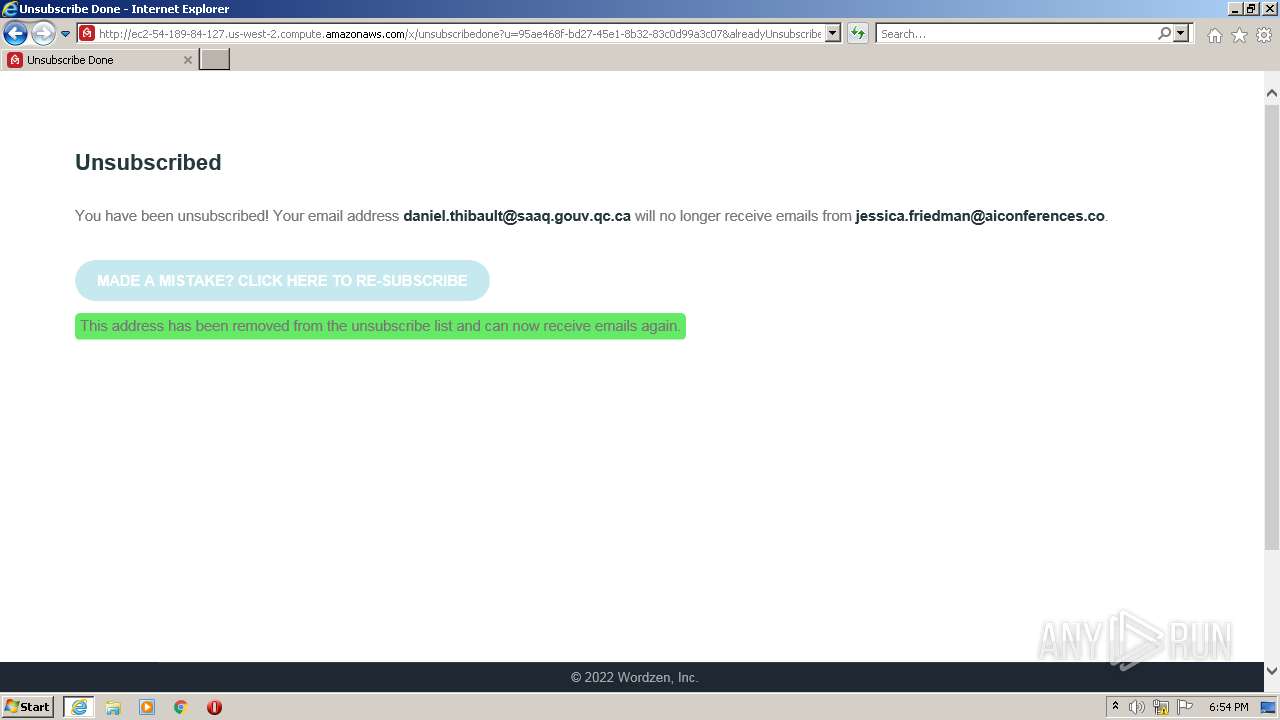
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 17:54:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | AFFE3F7E6EFE97D4FF1E565E6CC3F400 |
| SHA1: | DEFC65BB9D633CC8621CFBADC6E6C37DD59CABB7 |
| SHA256: | 248144831EBCB359AD5678B01EAB6DE55EB749A3967FBF1FF1A00F7B74792036 |
| SSDEEP: | 12:2G9qx9hjYvXYg8O39sJIqvQD8p0zkKp7zOmcgqjwud4L7HwDA5ZddCXtp0UKP7Rj:2aqxeoP2qvQ9k+iBjwuaV5ZddRHP7Qu |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 4020)
- iexplore.exe (PID: 2480)
INFO
Reads the computer name
- iexplore.exe (PID: 2480)
- iexplore.exe (PID: 4020)
Changes internet zones settings
- iexplore.exe (PID: 2480)
Checks supported languages
- iexplore.exe (PID: 4020)
- iexplore.exe (PID: 2480)
Application launched itself
- iexplore.exe (PID: 2480)
Reads settings of System Certificates
- iexplore.exe (PID: 4020)
- iexplore.exe (PID: 2480)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2480)
Checks Windows Trust Settings
- iexplore.exe (PID: 4020)
- iexplore.exe (PID: 2480)
Reads the date of Windows installation
- iexplore.exe (PID: 2480)
Reads internet explorer settings
- iexplore.exe (PID: 4020)
Changes settings of System certificates
- iexplore.exe (PID: 2480)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2480 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://can01.safelinks.protection.outlook.com/?url=https%3A%2F%2Fu10704350.ct.sendgrid.net%2Fls%2Fclick%3Fupn%3Dn0I16x2JTvUQ5lBFUSFflE5RXCzViUzPnq9b1wKq9Nc0uHXWH-2FSiU3boqrP0TzkwUkk-2BtIRAYgmkiirvxnT85Jmi7VEffIEaPKTZ7vBf-2FgO2A2BOQvnjEhNz-2BhiKm9KRzeUiAp1T-2FHezuZ-2BA1ssW7g-3D-3D_YOS_uAGIKxVHnzoGVmPcnUwHmaU-2FnkoJkDSw4aHFiI-2B0y4Fhy58-2BRG59axtnosJJcUGv8X7JXZioX2JD6uR3gQZeHqpELfestL6V8E-2BR-2FLxVjVCIvADFiCk-2Fb75CxRZCcrmkH9U-2F873t8hRTbMuiEkpqZI1X7-2B1uAjkBOEu6MJIMi64iS8dhfVITYlBTFWg5lDn6UoPVFy-2B4CfTGgZ4Su65F-2FFxiEHnQdniJKwhGIWoe598-3D&data=05%7C01%7Cdaniel.thibault%40saaq.gouv.qc.ca%7C62ec7c6d83764198c20208da7bf2757d%7C4df32e45efd840c193ead0041b95d83b%7C0%7C0%7C637958578649493597%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C2000%7C%7C%7C&sdata=xYZMHHYWq4jIGfSMOm142iT%2FoOGCwXfebm5gEiCtR9s%3D&reserved=0" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4020 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2480 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
14 788
Read events
14 636
Write events
149
Delete events
3
Modification events
| (PID) Process: | (2480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30977652 | |||
| (PID) Process: | (2480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30977652 | |||
| (PID) Process: | (2480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2480) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
26
Text files
24
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2480 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 4020 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2F23D0F5E4D72862517E1CB26A329742_F6FACC49395CFA949BCE851E73323C49 | binary | |
MD5:— | SHA256:— | |||
| 4020 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | binary | |
MD5:— | SHA256:— | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 2480 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 4020 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\unsubscribe[1].htm | html | |
MD5:— | SHA256:— | |||
| 4020 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | der | |
MD5:— | SHA256:— | |||
| 4020 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | binary | |
MD5:— | SHA256:— | |||
| 4020 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
39
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
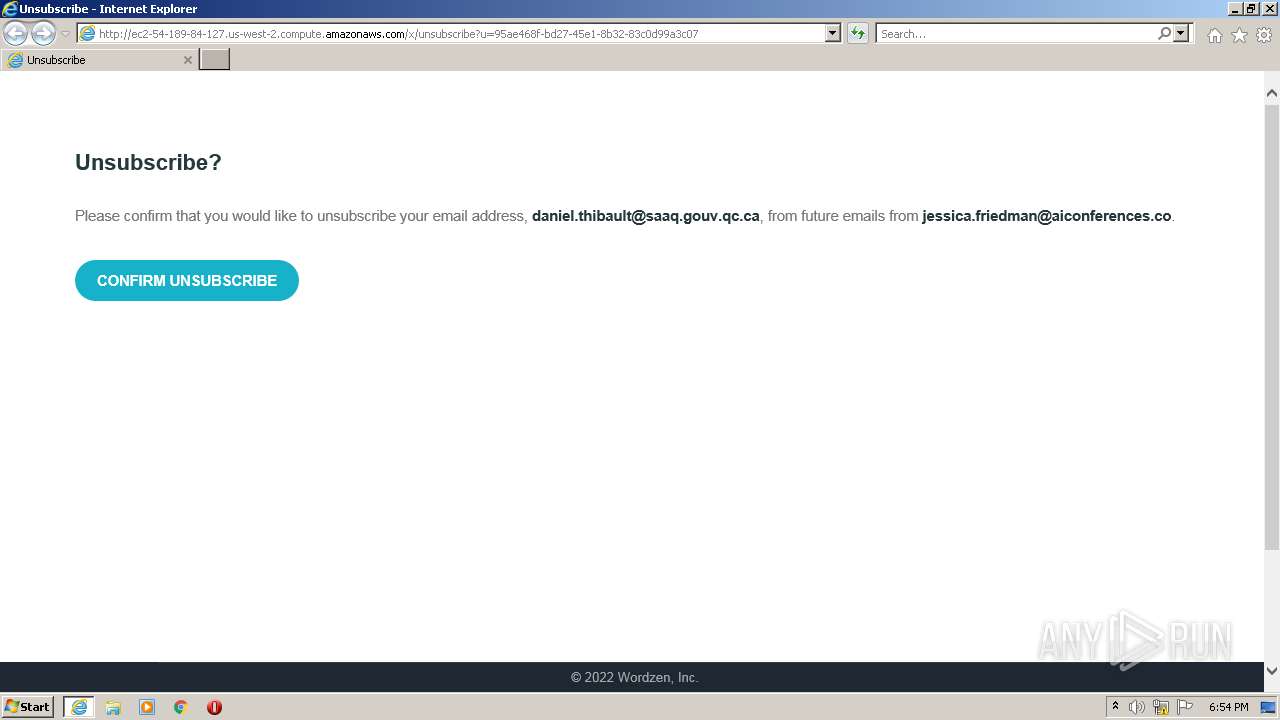
4020 | iexplore.exe | GET | — | 54.189.84.127:80 | http://ec2-54-189-84-127.us-west-2.compute.amazonaws.com/x/Unsubscribe?u=95ae468f-bd27-45e1-8b32-83c0d99a3c07&unsubscribe=True | US | — | — | shared |
4020 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAGewca9P1l7sgwzOOVR2Hc%3D | US | der | 471 b | whitelisted |
4020 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
4020 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDyjRAUcVc1IArKByftf8KS | US | der | 472 b | whitelisted |
4020 | iexplore.exe | GET | 302 | 54.189.84.127:80 | http://ec2-54-189-84-127.us-west-2.compute.amazonaws.com/x/unsubscribe?u=95ae468f-bd27-45e1-8b32-83c0d99a3c07&unsubscribe=True | US | html | 204 b | shared |
4020 | iexplore.exe | GET | 301 | 54.189.84.127:80 | http://ec2-54-189-84-127.us-west-2.compute.amazonaws.com/x/Unsubscribe?u=95ae468f-bd27-45e1-8b32-83c0d99a3c07&unsubscribe=True | US | compressed | 5.26 Kb | shared |
2480 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
4020 | iexplore.exe | GET | 200 | 192.124.249.36:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | US | der | 1.66 Kb | whitelisted |
4020 | iexplore.exe | GET | 200 | 192.124.249.36:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
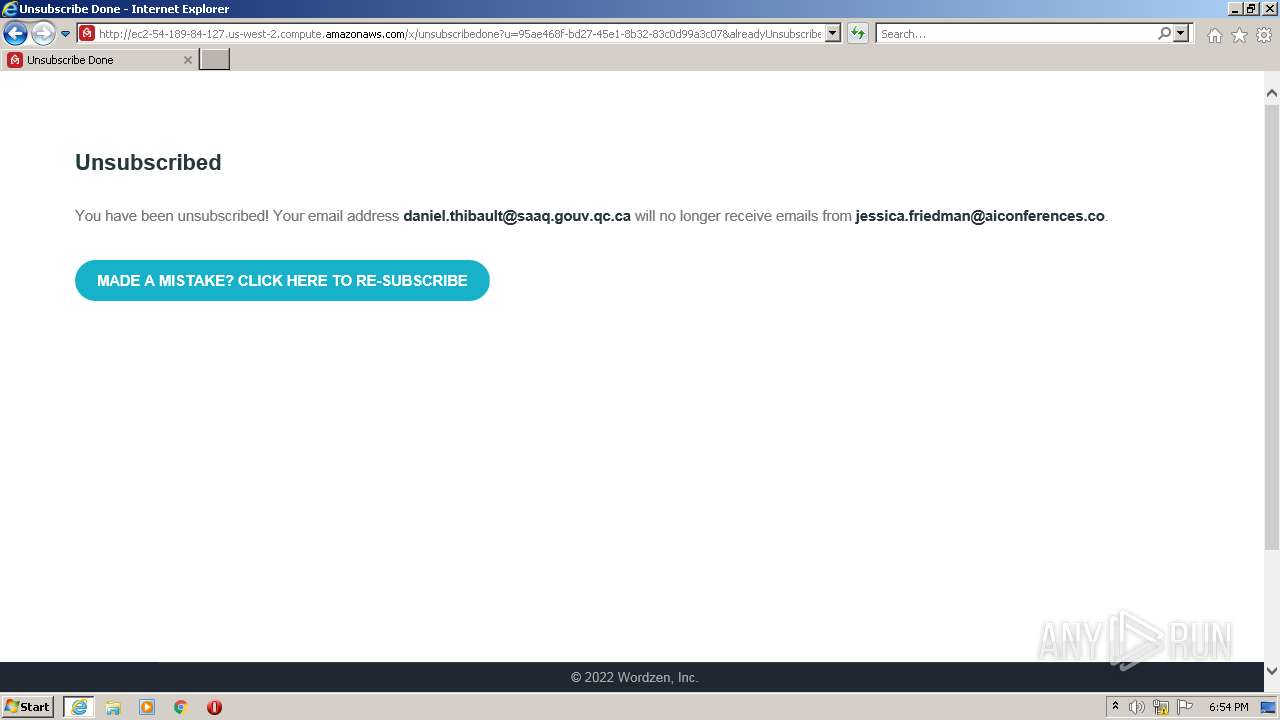
4020 | iexplore.exe | GET | 200 | 54.189.84.127:80 | http://ec2-54-189-84-127.us-west-2.compute.amazonaws.com/x/unsubscribe?u=95ae468f-bd27-45e1-8b32-83c0d99a3c07 | US | html | 3.25 Kb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2480 | iexplore.exe | 13.107.21.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
— | — | 13.107.21.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2480 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4020 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4020 | iexplore.exe | 192.124.249.36:80 | ocsp.godaddy.com | Sucuri | US | suspicious |
4020 | iexplore.exe | 54.189.84.127:80 | ec2-54-189-84-127.us-west-2.compute.amazonaws.com | Amazon.com, Inc. | US | shared |
4020 | iexplore.exe | 172.217.18.106:80 | ajax.googleapis.com | Google Inc. | US | whitelisted |
4020 | iexplore.exe | 142.250.186.35:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2480 | iexplore.exe | 54.189.84.127:80 | ec2-54-189-84-127.us-west-2.compute.amazonaws.com | Amazon.com, Inc. | US | shared |
2480 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
can01.safelinks.protection.outlook.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
u10704350.ct.sendgrid.net |
| malicious |
ocsp.godaddy.com |
| whitelisted |
ec2-54-189-84-127.us-west-2.compute.amazonaws.com |
| shared |
ajax.googleapis.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |