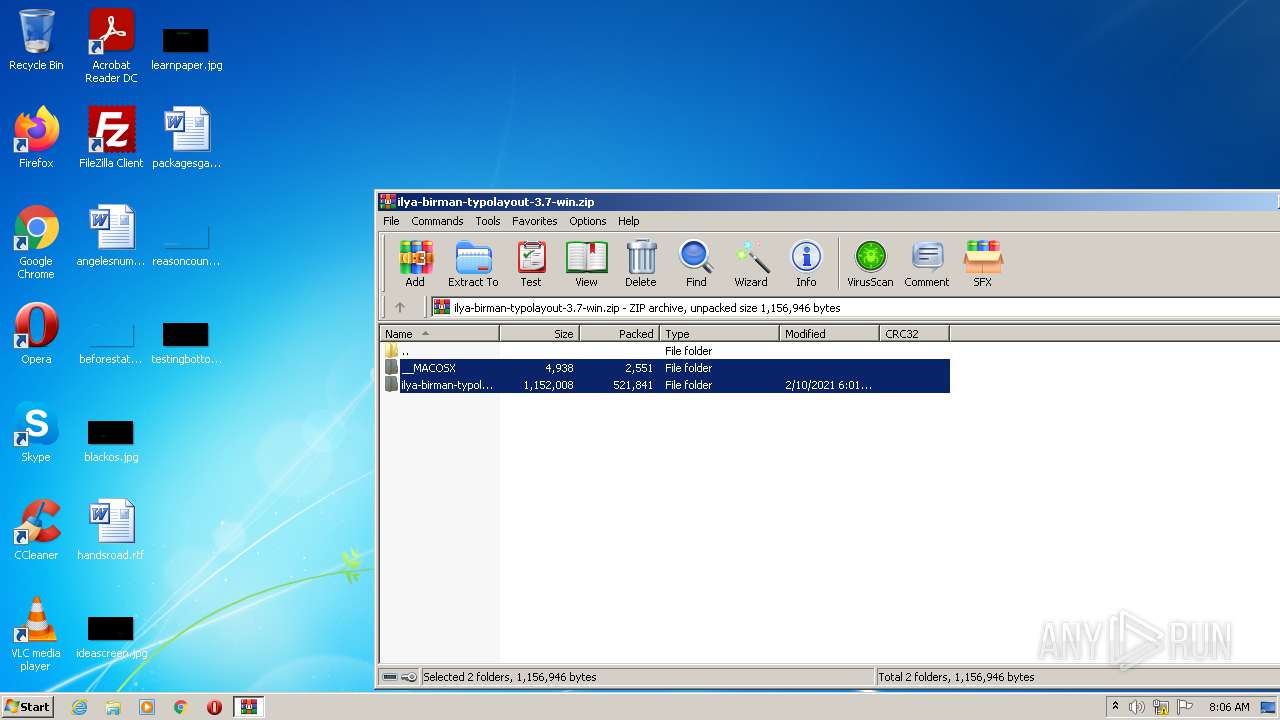
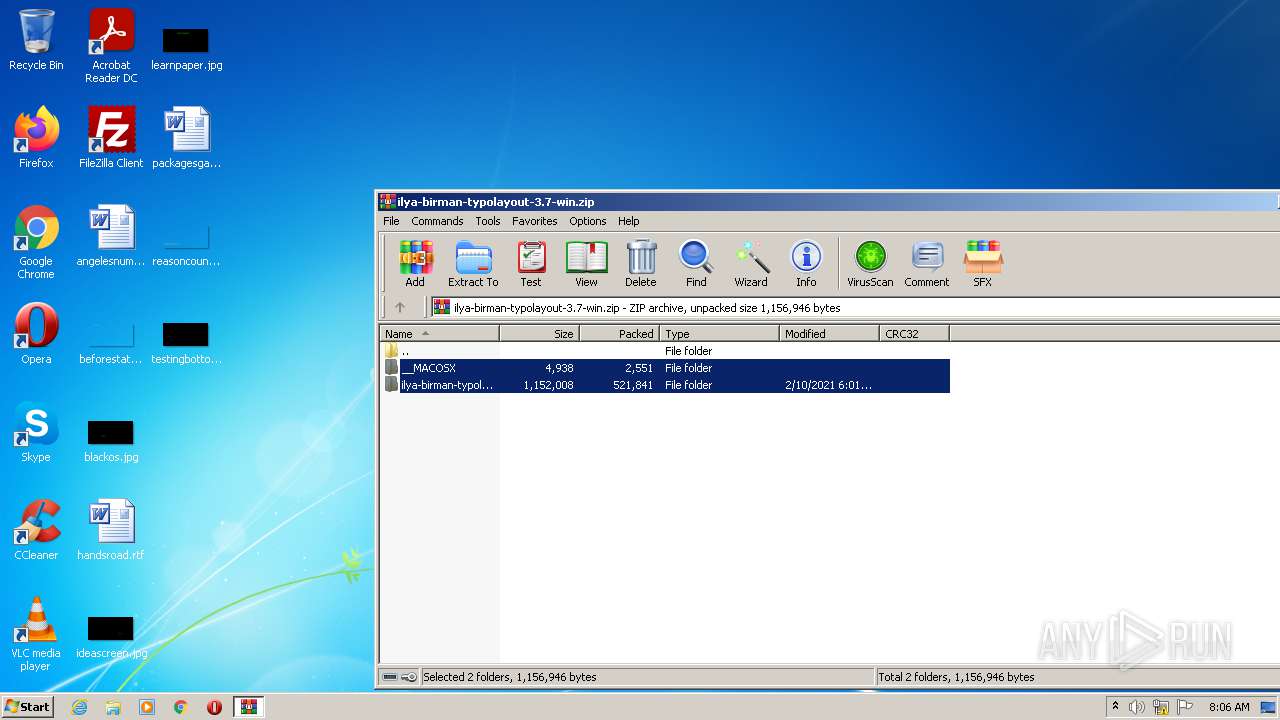
| File name: | ilya-birman-typolayout-3.7-win.zip |
| Full analysis: | https://app.any.run/tasks/178dbfcb-9ed6-4e77-b819-90f7dad37fb5 |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2021, 07:06:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | D05500A4BCA1E328309BE89056021964 |
| SHA1: | 3D92C8A3782D0B215591C8E70B7DE67CDAEFB984 |
| SHA256: | 247C4BE22ED038D703B4445D9B9A41A8BE49680B163ACDC42BEFE26E96371B87 |
| SSDEEP: | 12288:OMzIo/A3BBnmezSMBnf7KJi+owl1GL7lnuIAkHr:OMzZaBBfdVeL+7lnuIxr |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3692)
- MsiExec.exe (PID: 324)
- MsiExec.exe (PID: 1892)
Application was dropped or rewritten from another process
- setup.exe (PID: 3624)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 2252)
- setup.exe (PID: 3624)
Checks supported languages
- WinRAR.exe (PID: 2252)
- setup.exe (PID: 3624)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2252)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2252)
Drops a file with too old compile date
- WinRAR.exe (PID: 2252)
Executed as Windows Service
- msiexec.exe (PID: 4020)
- vssvc.exe (PID: 3496)
Reads Windows owner or organization settings
- setup.exe (PID: 3624)
Application launched itself
- msiexec.exe (PID: 4020)
Reads the Windows organization settings
- setup.exe (PID: 3624)
Searches for installed software
- msiexec.exe (PID: 4020)
Reads Environment values
- vssvc.exe (PID: 3496)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2252)
Manual execution by user
- setup.exe (PID: 3624)
Checks supported languages
- msiexec.exe (PID: 4020)
- vssvc.exe (PID: 3496)
Reads the computer name
- msiexec.exe (PID: 4020)
- vssvc.exe (PID: 3496)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | ilya-birman-typolayout-3.7-win/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2021:02:10 23:01:26 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
44
Monitored processes
7
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | C:\Windows\system32\MsiExec.exe -Embedding 9FDDB118F3525515A7C9A5810E858CCE | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1892 | C:\Windows\system32\MsiExec.exe -Embedding 495EA400435333CF055E2481DB8EC0E1 E Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2252 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\ilya-birman-typolayout-3.7-win.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3496 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft� Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3624 | "C:\Users\admin\Desktop\ilya-birman-typolayout-3.7-win\ibtl-rus\setup.exe" | C:\Users\admin\Desktop\ilya-birman-typolayout-3.7-win\ibtl-rus\setup.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Keyboard Layout Creator Bootstrap Exit code: 0 Version: 1.4.6000.2 (vbl_core_gift(michkap).061022-2037) Modules
| |||||||||||||||
| 3692 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 4020 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 917
Read events
5 266
Write events
617
Delete events
34
Modification events
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ilya-birman-typolayout-3.7-win.zip | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2252) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
32
Suspicious files
0
Text files
0
Unknown types
62
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ilya-birman-typolayout-3.7-win\__MACOSX\._ilya-birman-typolayout-3.7-win | ad | |
MD5:AD4C547221C2057D0157BDCFDCAF7618 | SHA256:C0B465A8F64BEB7B43344316BAC4DC46241AAA365F5B9258F091A333E34A57DD | |||
| 2252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ilya-birman-typolayout-3.7-win\ilya-birman-typolayout-3.7-win\ibtl-eng\setup.exe | executable | |
MD5:7F6655193E788A58248FEB230C4F5D3D | SHA256:3F3F7AFCCC638EC12E6065E79BFADBD7EC34F02525D73B07F6BFB70C2C698EE4 | |||
| 2252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ilya-birman-typolayout-3.7-win\__MACOSX\ilya-birman-typolayout-3.7-win\._ibtl-rus | ad | |
MD5:D496E9AA2FFEF9D8B4528350239CD202 | SHA256:24E6A3D8BE9E8743E95AF7A3453DD710A2FCA42436B0D2C45040CA8CE961C9E0 | |||
| 2252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ilya-birman-typolayout-3.7-win\__MACOSX\ilya-birman-typolayout-3.7-win\ibtl-eng\._IBTL-ENG_ia64.msi | ad | |
MD5:D496E9AA2FFEF9D8B4528350239CD202 | SHA256:24E6A3D8BE9E8743E95AF7A3453DD710A2FCA42436B0D2C45040CA8CE961C9E0 | |||
| 2252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ilya-birman-typolayout-3.7-win\__MACOSX\ilya-birman-typolayout-3.7-win\ibtl-eng\._ia64 | ad | |
MD5:D496E9AA2FFEF9D8B4528350239CD202 | SHA256:24E6A3D8BE9E8743E95AF7A3453DD710A2FCA42436B0D2C45040CA8CE961C9E0 | |||
| 2252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ilya-birman-typolayout-3.7-win\__MACOSX\ilya-birman-typolayout-3.7-win\ibtl-eng\._setup.exe | ad | |
MD5:D496E9AA2FFEF9D8B4528350239CD202 | SHA256:24E6A3D8BE9E8743E95AF7A3453DD710A2FCA42436B0D2C45040CA8CE961C9E0 | |||
| 2252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ilya-birman-typolayout-3.7-win\ilya-birman-typolayout-3.7-win\ibtl-eng\.DS_Store | ds_store | |
MD5:4B16A1694B646656A1A4469ABDE5660C | SHA256:A749B7D5EF662727C21B059DAF8D4119BFA77ECD799FA73CB659562C5C0B72F7 | |||
| 2252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ilya-birman-typolayout-3.7-win\__MACOSX\ilya-birman-typolayout-3.7-win\._ibtl-eng | ad | |
MD5:D496E9AA2FFEF9D8B4528350239CD202 | SHA256:24E6A3D8BE9E8743E95AF7A3453DD710A2FCA42436B0D2C45040CA8CE961C9E0 | |||
| 2252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ilya-birman-typolayout-3.7-win\ilya-birman-typolayout-3.7-win\ibtl-eng\IBTL-ENG_ia64.msi | executable | |
MD5:F57966858DD58FCAA1A3AA38BD03D0C3 | SHA256:7FB0AED26D1CD565B2CCC30F22FFF8B87BC8C61F2E61A42959626E66D1DBC910 | |||
| 2252 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\ilya-birman-typolayout-3.7-win\ilya-birman-typolayout-3.7-win\ibtl-eng\IBTL-ENG_i386.msi | executable | |
MD5:2A6103BC7509A785B596F2FECB144971 | SHA256:57A6060B8C474E3B58A97905D3DBC0BD920824ACD52311A787F3C6562EC67340 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report