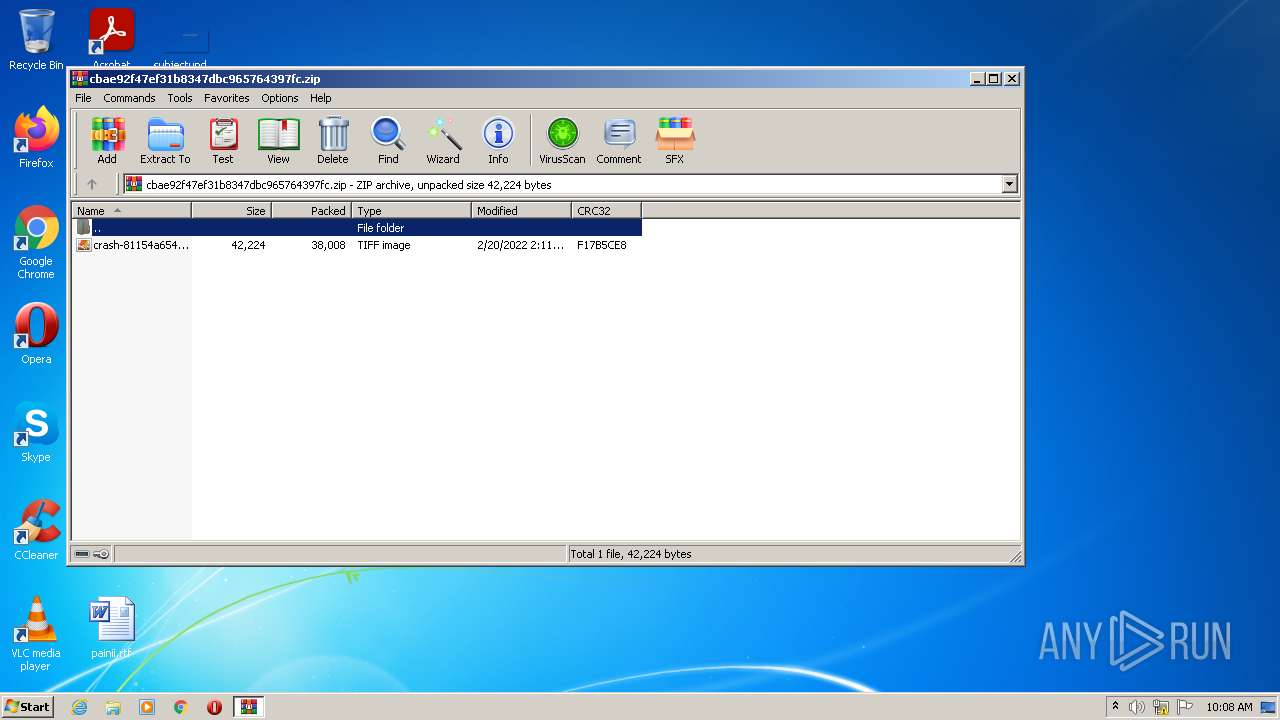
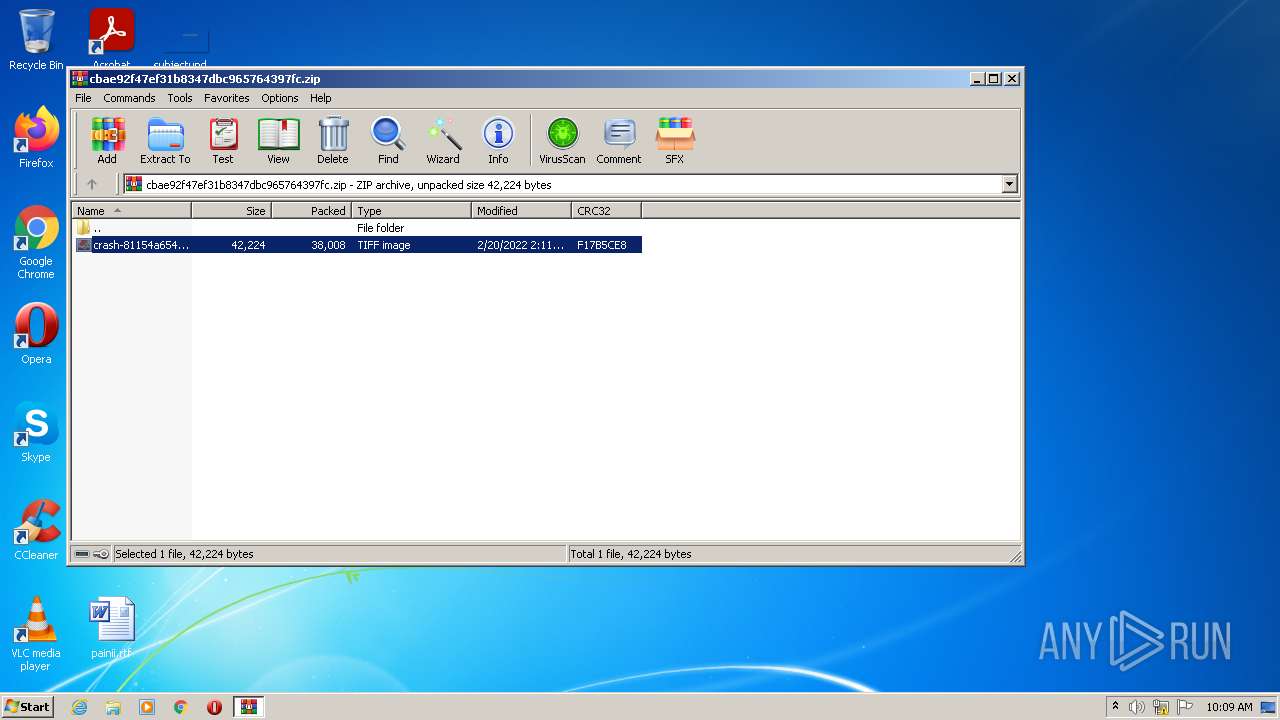
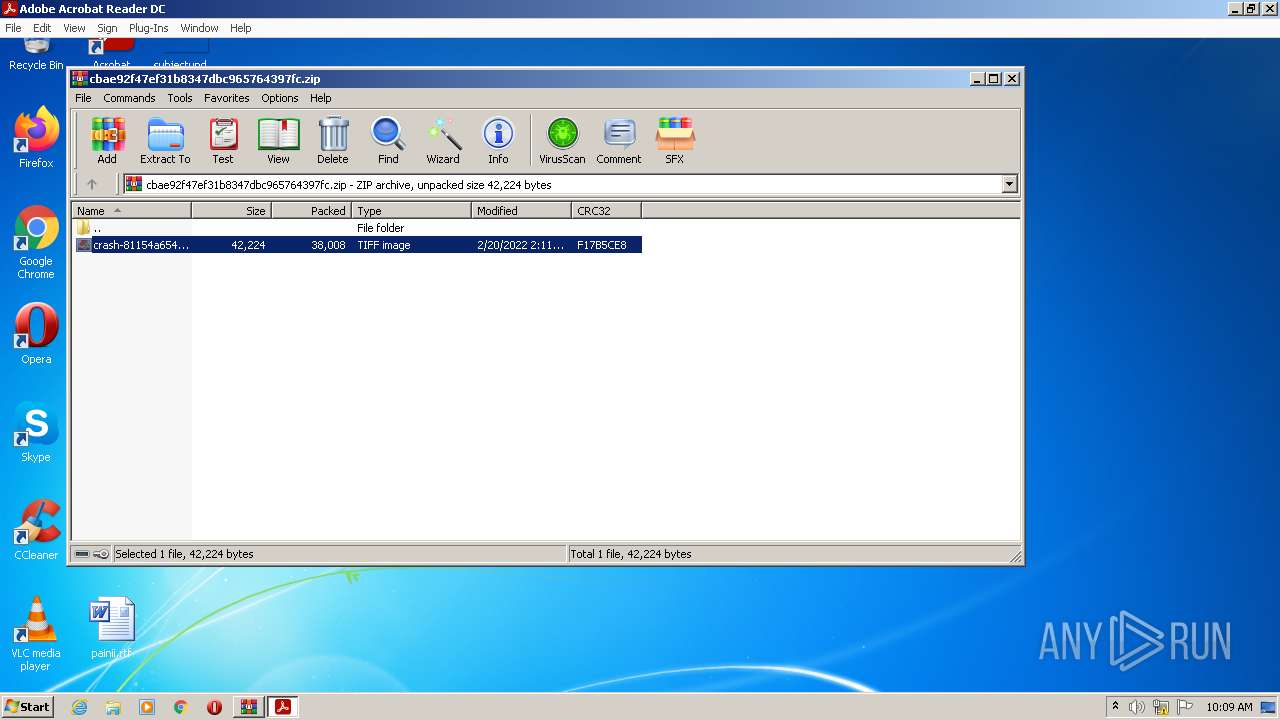
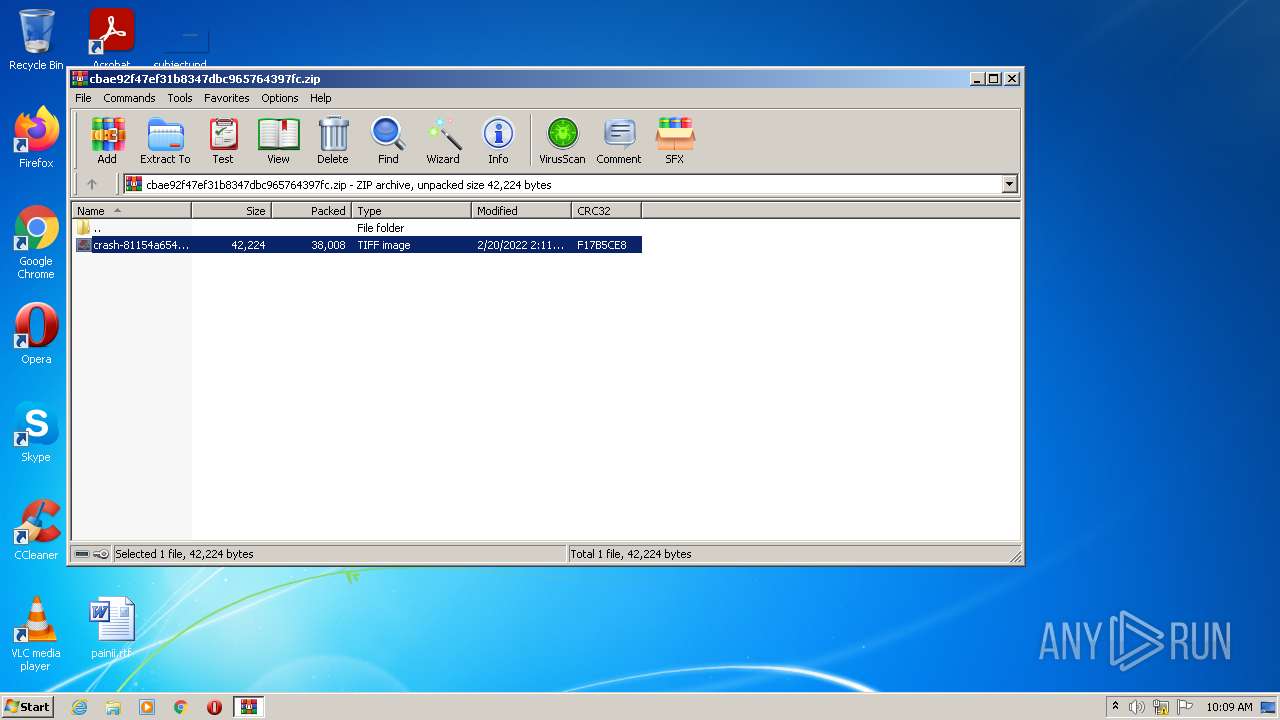
| File name: | cbae92f47ef31b8347dbc965764397fc.zip |
| Full analysis: | https://app.any.run/tasks/489ddd33-3206-4158-a02e-af7ac019127b |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 09:08:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 34F25C0D4CCED0216098DF6D0271C5B0 |
| SHA1: | 01D1196D99884BF5ACC2235D4EB2B53C7538D8B1 |
| SHA256: | 246B1467221ED13830AAFA8A167620CC055F8D7E1D274814AF59F72F444ED235 |
| SSDEEP: | 768:aPw3Uflz54K1/HtVy123EiPhCD2J0nlivjYOS/HxqE/1n2TjSMrj7E:AfjBy1XYJ0nw7Y//J2ZA |
MALICIOUS
Drops executable file immediately after starts
- RdrCEF.exe (PID: 3168)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 2836)
Reads the computer name
- WinRAR.exe (PID: 2836)
Reads default file associations for system extensions
- AcroRd32.exe (PID: 3376)
Drops a file with a compile date too recent
- RdrCEF.exe (PID: 3168)
Executed via COM
- DllHost.exe (PID: 2604)
INFO
Reads CPU info
- AcroRd32.exe (PID: 2328)
Reads settings of System Certificates
- AcroRd32.exe (PID: 3376)
- RdrCEF.exe (PID: 3168)
Searches for installed software
- AcroRd32.exe (PID: 3376)
- AcroRd32.exe (PID: 2328)
Reads the computer name
- AcroRd32.exe (PID: 3376)
- AcroRd32.exe (PID: 2328)
- RdrCEF.exe (PID: 3168)
- DllHost.exe (PID: 2604)
Application launched itself
- AcroRd32.exe (PID: 3376)
- RdrCEF.exe (PID: 3168)
Checks supported languages
- RdrCEF.exe (PID: 4008)
- AcroRd32.exe (PID: 2328)
- AcroRd32.exe (PID: 3376)
- RdrCEF.exe (PID: 3168)
- RdrCEF.exe (PID: 2784)
- RdrCEF.exe (PID: 1972)
- RdrCEF.exe (PID: 2172)
- RdrCEF.exe (PID: 2996)
- DllHost.exe (PID: 2604)
- RdrCEF.exe (PID: 2612)
Manual execution by user
- AcroRd32.exe (PID: 3376)
Reads the hosts file
- RdrCEF.exe (PID: 3168)
Checks Windows Trust Settings
- AcroRd32.exe (PID: 3376)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | crash-81154a65438ba5aaeca73fd502fa4850fbde60f8.tif |
|---|---|
| ZipUncompressedSize: | 42224 |
| ZipCompressedSize: | 38008 |
| ZipCRC: | 0xf17b5ce8 |
| ZipModifyDate: | 2022:02:20 02:11:09 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0001 |
| ZipRequiredVersion: | 20 |
Total processes
48
Monitored processes
11
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1972 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1176,3745731671552507276,13818964381929950695,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=690738302295747521 --mojo-platform-channel-handle=1260 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2172 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1176,3745731671552507276,13818964381929950695,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=3147957792802413281 --mojo-platform-channel-handle=1212 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2328 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2604 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2612 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1176,3745731671552507276,13818964381929950695,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7421792312292348048 --renderer-client-id=6 --mojo-platform-channel-handle=1456 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2784 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1176,3745731671552507276,13818964381929950695,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5116789611713404080 --renderer-client-id=2 --mojo-platform-channel-handle=1184 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2836 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\cbae92f47ef31b8347dbc965764397fc.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2996 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1176,3745731671552507276,13818964381929950695,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13260308477373662127 --renderer-client-id=7 --mojo-platform-channel-handle=1944 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 3168 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 3221225547 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 3376 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | Explorer.EXE | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
Total events
13 369
Read events
13 169
Write events
194
Delete events
6
Modification events
| (PID) Process: | (2836) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2836) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2836) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2836) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2836) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2836) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\cbae92f47ef31b8347dbc965764397fc.zip | |||
| (PID) Process: | (2836) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2836) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2836) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2836) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
124
Text files
6
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
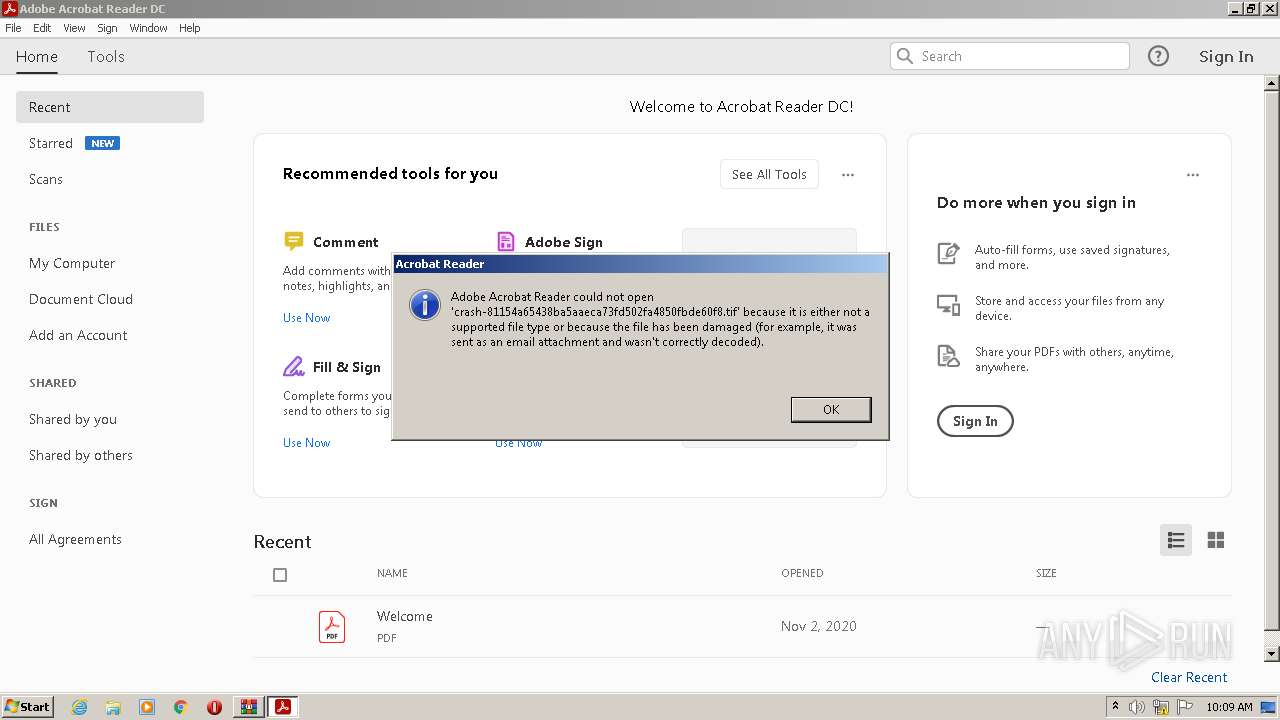
| 2836 | WinRAR.exe | C:\Users\admin\Pictures\crash-81154a65438ba5aaeca73fd502fa4850fbde60f8.tif | image | |
MD5:— | SHA256:— | |||
| 3168 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\86b8040b7132b608_0 | binary | |
MD5:— | SHA256:— | |||
| 3168 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\983b7a3da8f39a46_0 | binary | |
MD5:— | SHA256:— | |||
| 3168 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\bba29d2e6197e2f4_0 | binary | |
MD5:— | SHA256:— | |||
| 3168 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\72d9f526d2e2e7c8_0 | binary | |
MD5:— | SHA256:— | |||
| 3168 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\2a426f11fd8ebe18_0 | binary | |
MD5:— | SHA256:— | |||
| 3168 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:— | SHA256:— | |||
| 3168 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\8c84d92a9dbce3e0_0 | binary | |
MD5:— | SHA256:— | |||
| 3168 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\0786087c3c360803_0 | binary | |
MD5:— | SHA256:— | |||
| 3168 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\8c159cc5880890bc_0 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
13
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3376 | AcroRd32.exe | 23.48.23.34:443 | acroipm2.adobe.com | TRUE INTERNET Co.,Ltd. | US | suspicious |
3168 | RdrCEF.exe | 184.30.20.134:443 | armmf.adobe.com | GTT Communications Inc. | US | suspicious |
3168 | RdrCEF.exe | 23.35.236.137:443 | geo2.adobe.com | Zayo Bandwidth Inc | US | suspicious |
3168 | RdrCEF.exe | 54.144.73.197:443 | p13n.adobe.io | Amazon.com, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |