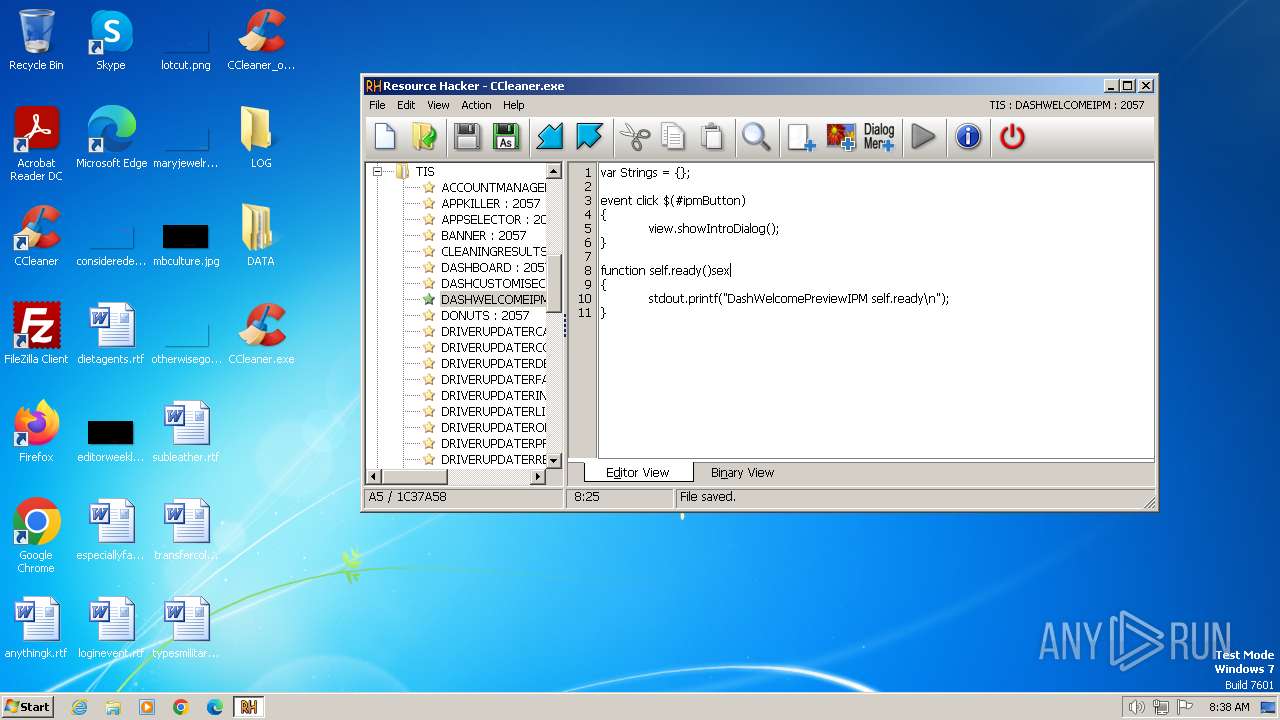
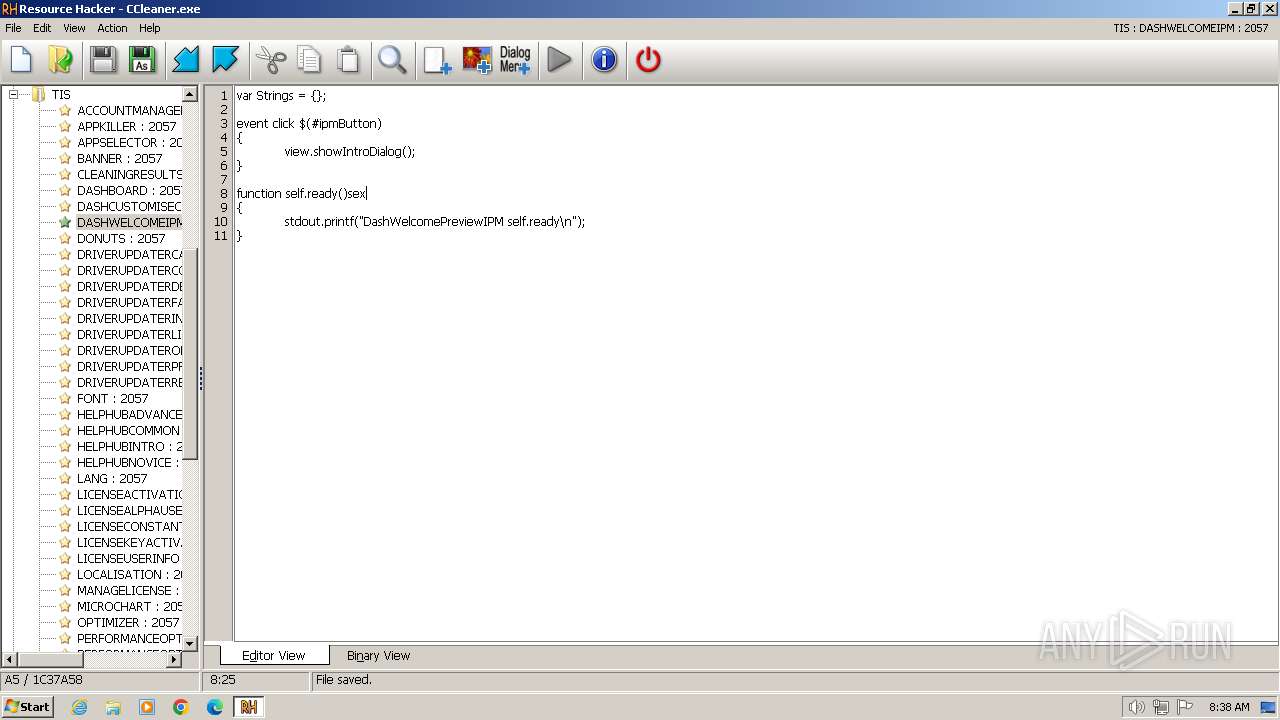
| File name: | reshacker_setup.exe |
| Full analysis: | https://app.any.run/tasks/410f0e7a-5309-442f-9ea1-df1f870c2e1b |
| Verdict: | Malicious activity |
| Analysis date: | February 18, 2024, 08:36:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 02EB693DCFB90A696D191BADBCF314CE |
| SHA1: | B1D0352C35D7DA251E2FA19ECBE8C1E5286F898F |
| SHA256: | 246457363396DCEA4CC3D19CE2A431897BAC948AE1694D3E87CC0EBAF2EA39F5 |
| SSDEEP: | 98304:A+QQm6RjZApvR6Br62Bow/DZyZAght2rOBFw4P6Ab2SN1bG37nh1brbgICjfa/xz:52WOQqw5 |
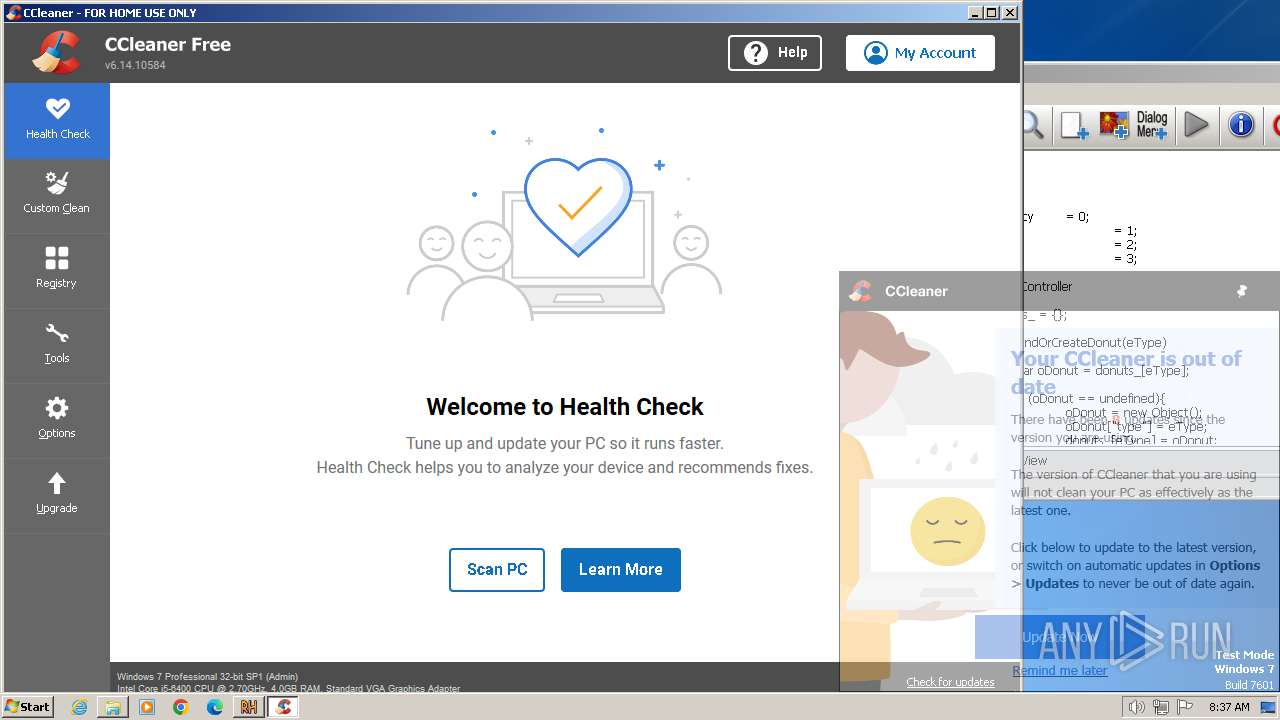
MALICIOUS
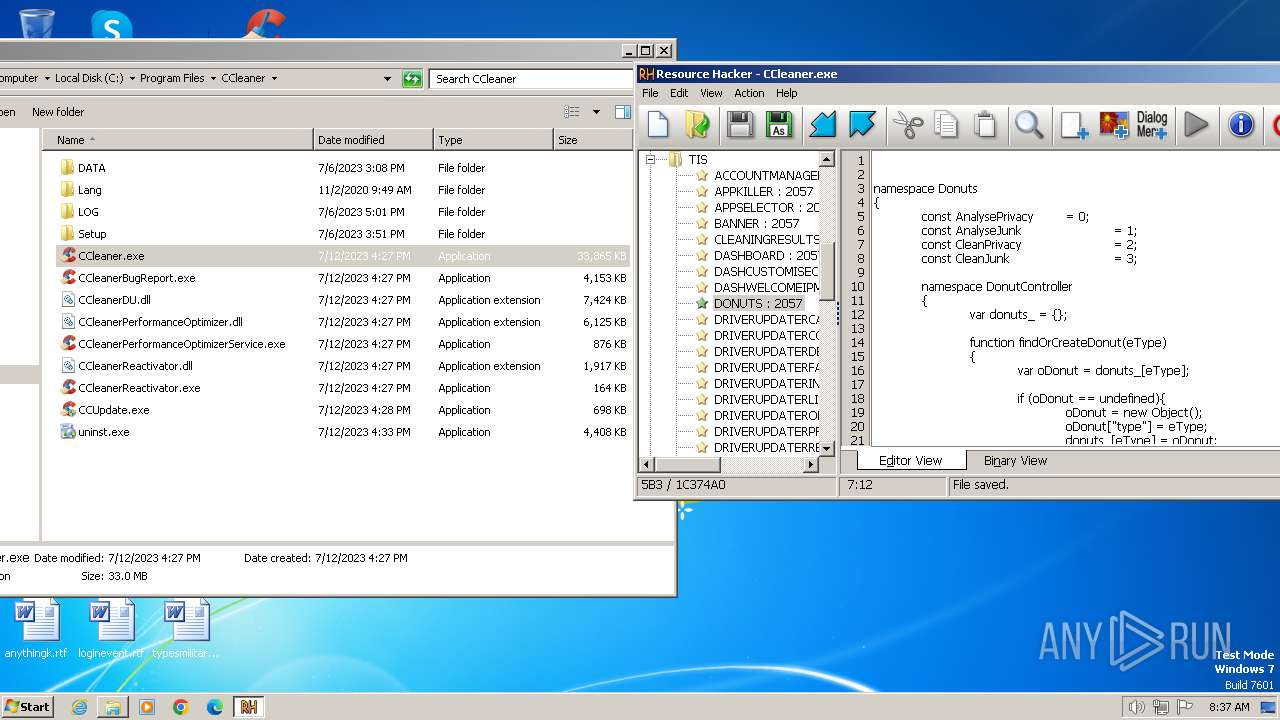
Drops the executable file immediately after the start
- reshacker_setup.exe (PID: 3700)
- reshacker_setup.exe (PID: 3944)
- reshacker_setup.tmp (PID: 3228)
- CCleaner.exe (PID: 1860)
Actions looks like stealing of personal data
- CCleaner.exe (PID: 1860)
Steals credentials from Web Browsers
- CCleaner.exe (PID: 1860)
SUSPICIOUS
Executable content was dropped or overwritten
- reshacker_setup.exe (PID: 3700)
- reshacker_setup.tmp (PID: 3228)
- reshacker_setup.exe (PID: 3944)
- CCleaner.exe (PID: 1860)
Reads the Windows owner or organization settings
- reshacker_setup.tmp (PID: 3228)
Start notepad (likely ransomware note)
- reshacker_setup.tmp (PID: 3656)
Reads the Internet Settings
- ResourceHacker.exe (PID: 4060)
- CCleaner.exe (PID: 2256)
- CCleaner.exe (PID: 1860)
Reads security settings of Internet Explorer
- CCleaner.exe (PID: 2256)
- CCleaner.exe (PID: 1860)
Application launched itself
- CCleaner.exe (PID: 2256)
Reads Internet Explorer settings
- CCleaner.exe (PID: 1860)
Searches for installed software
- CCleaner.exe (PID: 1860)
Reads settings of System Certificates
- CCleaner.exe (PID: 1860)
Reads the date of Windows installation
- CCleaner.exe (PID: 1860)
Checks Windows Trust Settings
- CCleaner.exe (PID: 1860)
Reads Microsoft Outlook installation path
- CCleaner.exe (PID: 1860)
INFO
Reads the computer name
- reshacker_setup.tmp (PID: 3656)
- reshacker_setup.tmp (PID: 3228)
- ResourceHacker.exe (PID: 4060)
- CCleaner.exe (PID: 2256)
- CCleaner.exe (PID: 1860)
Checks supported languages
- reshacker_setup.exe (PID: 3700)
- reshacker_setup.tmp (PID: 3656)
- reshacker_setup.exe (PID: 3944)
- reshacker_setup.tmp (PID: 3228)
- ResourceHacker.exe (PID: 4060)
- CCleaner.exe (PID: 2256)
- CCleaner.exe (PID: 1860)
Create files in a temporary directory
- reshacker_setup.exe (PID: 3700)
- reshacker_setup.exe (PID: 3944)
Creates files in the program directory
- reshacker_setup.tmp (PID: 3228)
Creates a software uninstall entry
- reshacker_setup.tmp (PID: 3228)
Reads the machine GUID from the registry
- ResourceHacker.exe (PID: 4060)
- CCleaner.exe (PID: 1860)
Manual execution by a user
- CCleaner.exe (PID: 2256)
Reads Environment values
- CCleaner.exe (PID: 2256)
- CCleaner.exe (PID: 1860)
Reads CPU info
- CCleaner.exe (PID: 1860)
Reads the software policy settings
- CCleaner.exe (PID: 1860)
Reads product name
- CCleaner.exe (PID: 1860)
Checks proxy server information
- CCleaner.exe (PID: 1860)
Creates files or folders in the user directory
- CCleaner.exe (PID: 1860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:05:21 05:56:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741376 |
| InitializedDataSize: | 128000 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Angus Johnson |
| FileDescription: | Resource Hacker Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Resource Hacker |
| ProductVersion: | 5.2.6 |
Total processes
57
Monitored processes
8
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1860 | "C:\Users\admin\Desktop\CCleaner.exe" /uac | C:\Users\admin\Desktop\CCleaner.exe | CCleaner.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 6.14.0.10584 Modules
| |||||||||||||||
| 2256 | "C:\Users\admin\Desktop\CCleaner.exe" | C:\Users\admin\Desktop\CCleaner.exe | — | explorer.exe | |||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 6.14.0.10584 Modules
| |||||||||||||||
| 3228 | "C:\Users\admin\AppData\Local\Temp\is-F5MH1.tmp\reshacker_setup.tmp" /SL5="$100130,3504386,870400,C:\Users\admin\AppData\Local\Temp\reshacker_setup.exe" /SPAWNWND=$18013E /NOTIFYWND=$E0170 | C:\Users\admin\AppData\Local\Temp\is-F5MH1.tmp\reshacker_setup.tmp | reshacker_setup.exe | ||||||||||||
User: admin Company: Angus Johnson Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3428 | "C:\Windows\system32\NOTEPAD.EXE" C:\Program Files\Resource Hacker\ReadMe.txt | C:\Windows\System32\notepad.exe | — | reshacker_setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3656 | "C:\Users\admin\AppData\Local\Temp\is-18QRN.tmp\reshacker_setup.tmp" /SL5="$E0170,3504386,870400,C:\Users\admin\AppData\Local\Temp\reshacker_setup.exe" | C:\Users\admin\AppData\Local\Temp\is-18QRN.tmp\reshacker_setup.tmp | — | reshacker_setup.exe | |||||||||||
User: admin Company: Angus Johnson Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3700 | "C:\Users\admin\AppData\Local\Temp\reshacker_setup.exe" | C:\Users\admin\AppData\Local\Temp\reshacker_setup.exe | explorer.exe | ||||||||||||
User: admin Company: Angus Johnson Integrity Level: MEDIUM Description: Resource Hacker Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3944 | "C:\Users\admin\AppData\Local\Temp\reshacker_setup.exe" /SPAWNWND=$18013E /NOTIFYWND=$E0170 | C:\Users\admin\AppData\Local\Temp\reshacker_setup.exe | reshacker_setup.tmp | ||||||||||||
User: admin Company: Angus Johnson Integrity Level: HIGH Description: Resource Hacker Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 4060 | "C:\Program Files\Resource Hacker\ResourceHacker.exe" | C:\Program Files\Resource Hacker\ResourceHacker.exe | — | reshacker_setup.tmp | |||||||||||
User: admin Company: Angus Johnson Integrity Level: MEDIUM Description: Resource viewer, decompiler & recompiler Exit code: 0 Version: 5.2.6.425 Modules
| |||||||||||||||
Total events
29 338
Read events
28 960
Write events
280
Delete events
98
Modification events
| (PID) Process: | (3228) reshacker_setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 9C0C0000E0194F974562DA01 | |||
| (PID) Process: | (3228) reshacker_setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 3CB4C6137CCC8594B57E880AE9A01F1CF51E3F8C9F54A9A958CAB4395ACAEAF6 | |||
| (PID) Process: | (3228) reshacker_setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3228) reshacker_setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\Resource Hacker\ResourceHacker.exe | |||
| (PID) Process: | (3228) reshacker_setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 3D92BE349D9E8137D41EF675B714B7A8F874DB97C18ADC0B04E75AE608206BE0 | |||
| (PID) Process: | (3228) reshacker_setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{A10FDE4A-B9BB-4427-A4A2-843A960D99FA}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.0.5 (u) | |||
| (PID) Process: | (3228) reshacker_setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{A10FDE4A-B9BB-4427-A4A2-843A960D99FA}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\Resource Hacker | |||
| (PID) Process: | (3228) reshacker_setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{A10FDE4A-B9BB-4427-A4A2-843A960D99FA}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\Resource Hacker\ | |||
| (PID) Process: | (3228) reshacker_setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{A10FDE4A-B9BB-4427-A4A2-843A960D99FA}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: (Default) | |||
| (PID) Process: | (3228) reshacker_setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{A10FDE4A-B9BB-4427-A4A2-843A960D99FA}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
10
Suspicious files
21
Text files
38
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3228 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\is-269II.tmp | executable | |
MD5:263B8A401528B440657BBDFFC64C6487 | SHA256:1227E484F32C34F026F311E60F1ABAE065E00F203153DBF0623152DEDF5CAFBD | |||
| 3228 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\ResourceHacker.exe | executable | |
MD5:263B8A401528B440657BBDFFC64C6487 | SHA256:1227E484F32C34F026F311E60F1ABAE065E00F203153DBF0623152DEDF5CAFBD | |||
| 3228 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\changes.txt | text | |
MD5:5D00DE639AEA86E57534B4D575B44C35 | SHA256:364674887A684CFA8FE5981F06D6A3B2B06AA7B5C53F158C6B4A405613F18966 | |||
| 3228 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\is-PHF7M.tmp | executable | |
MD5:55ABBAA40E0EAEACAABAD31EAF9692A0 | SHA256:120CFAFB05CAC4650CB299F05A38422580F0ED6B15BD495D46CF40216C8200F2 | |||
| 3228 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\is-HSD8O.tmp | image | |
MD5:0513C11177A2EDE618D8FC375F9C3767 | SHA256:55826A6FD5E1056F3CD85110EFAC33EABF28364E1B2E3370CF565793DC0FBB26 | |||
| 3228 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\is-R2L4I.tmp | image | |
MD5:B6577C2A048E6F9FA588994345A21400 | SHA256:0BB5001274535E7BD4A88E95FA5497D28507313BD8C9C5FE6D16E763DA5F8B25 | |||
| 3228 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\rh_dlg_ctrl.png | image | |
MD5:1DDEE97A31B52AF6E8A5E718B5B02C08 | SHA256:B4692A3BE299443A39350B0AF56A966F655EF06F140F3C142BC458FDA9BD9459 | |||
| 3228 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\rh_dlg_edit.png | image | |
MD5:B6577C2A048E6F9FA588994345A21400 | SHA256:0BB5001274535E7BD4A88E95FA5497D28507313BD8C9C5FE6D16E763DA5F8B25 | |||
| 3228 | reshacker_setup.tmp | C:\Program Files\Resource Hacker\unins000.exe | executable | |
MD5:55ABBAA40E0EAEACAABAD31EAF9692A0 | SHA256:120CFAFB05CAC4650CB299F05A38422580F0ED6B15BD495D46CF40216C8200F2 | |||
| 3700 | reshacker_setup.exe | C:\Users\admin\AppData\Local\Temp\is-18QRN.tmp\reshacker_setup.tmp | executable | |
MD5:C5CAC19A48B63987B767C8CE36A09282 | SHA256:9AEC7890B56A86F175957B7A99FE57CE6234D16995E019D3008A5D599FDF8E28 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
22
DNS requests
11
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1860 | CCleaner.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bc287f3b19cf8fe0 | unknown | — | — | unknown |
1860 | CCleaner.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
1860 | CCleaner.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d8b1dda1a525c312 | unknown | — | — | unknown |
1860 | CCleaner.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
1860 | CCleaner.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6d0c5b125d543b00 | unknown | — | — | unknown |
1860 | CCleaner.exe | GET | 200 | 104.124.11.73:80 | http://ncc.avast.com/ncc.txt | unknown | text | 26 b | unknown |
1860 | CCleaner.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?20f7867851d324b1 | unknown | — | — | unknown |
1860 | CCleaner.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/s/gts1d4/dKa2DF3Ws7g/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICEQCirF%2F66XssownTCQRm1ZB%2F | unknown | binary | 472 b | unknown |
1860 | CCleaner.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/s/gts1d4/t0jeL7ceLrY/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICEQDRSW2avX2yRQo3SfbomPuF | unknown | binary | 472 b | unknown |
1860 | CCleaner.exe | GET | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1860 | CCleaner.exe | 104.124.11.73:80 | ncc.avast.com | Akamai International B.V. | DE | unknown |
1860 | CCleaner.exe | 34.117.223.223:443 | analytics.ff.avast.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
1860 | CCleaner.exe | 34.160.176.28:443 | shepherd.ff.avast.com | GOOGLE | US | unknown |
1860 | CCleaner.exe | 34.149.149.62:443 | ip-info.ff.avast.com | GOOGLE | US | unknown |
1860 | CCleaner.exe | 23.211.8.159:443 | www.ccleaner.com | AKAMAI-AS | DE | unknown |
1860 | CCleaner.exe | 34.111.24.1:443 | ipm-provider.ff.avast.com | GOOGLE | US | unknown |
1860 | CCleaner.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ncc.avast.com |
| whitelisted |
analytics.ff.avast.com |
| whitelisted |
ip-info.ff.avast.com |
| whitelisted |
shepherd.ff.avast.com |
| whitelisted |
ipm-provider.ff.avast.com |
| whitelisted |
www.ccleaner.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ipmcdn.avast.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
1860 | CCleaner.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
Process | Message |
|---|---|
CCleaner.exe | [2024-02-18 08:37:46.650] [error ] [settings ] [ 1860: 3308] [6000C4: 356] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner.exe | Failed to open log file 'C:\Users\admin\Desktop' |
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | startCheckingLicense()
|
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | observing CurrentIndex changed - 0
|
CCleaner.exe | observing currentResultDetails changed - None
|
CCleaner.exe | SetStrings - Live Region updated: ,
|