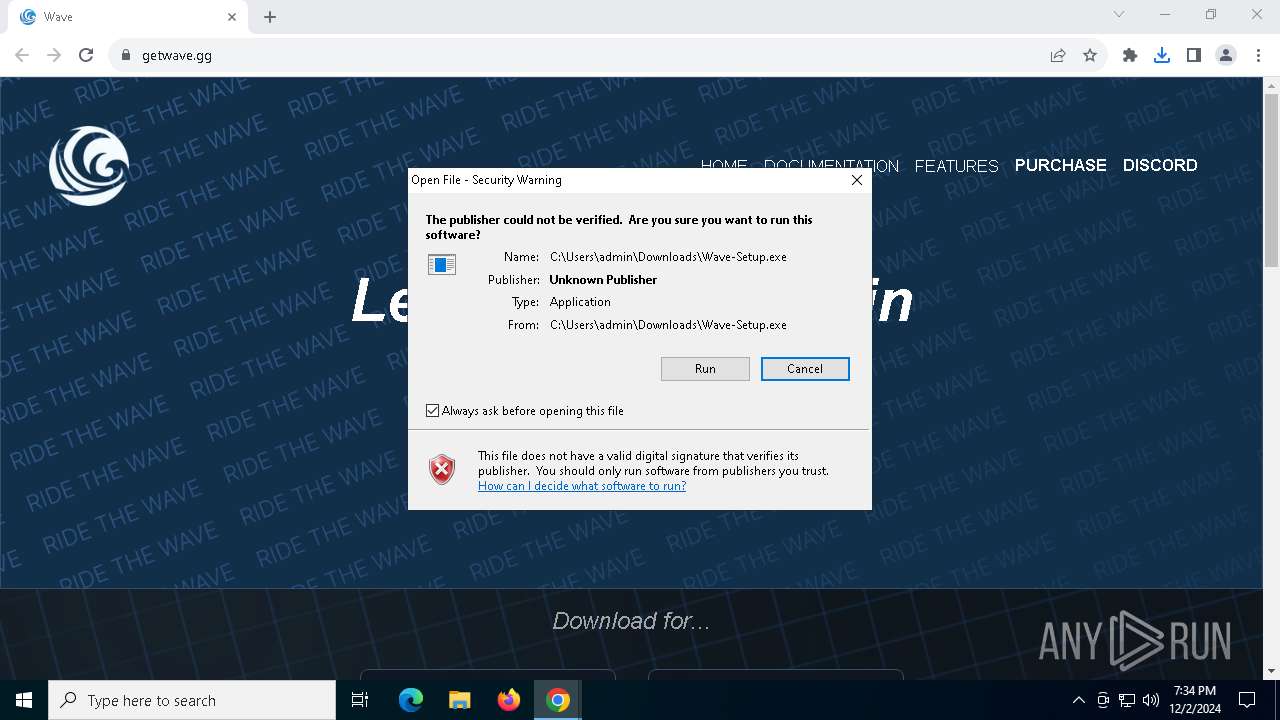
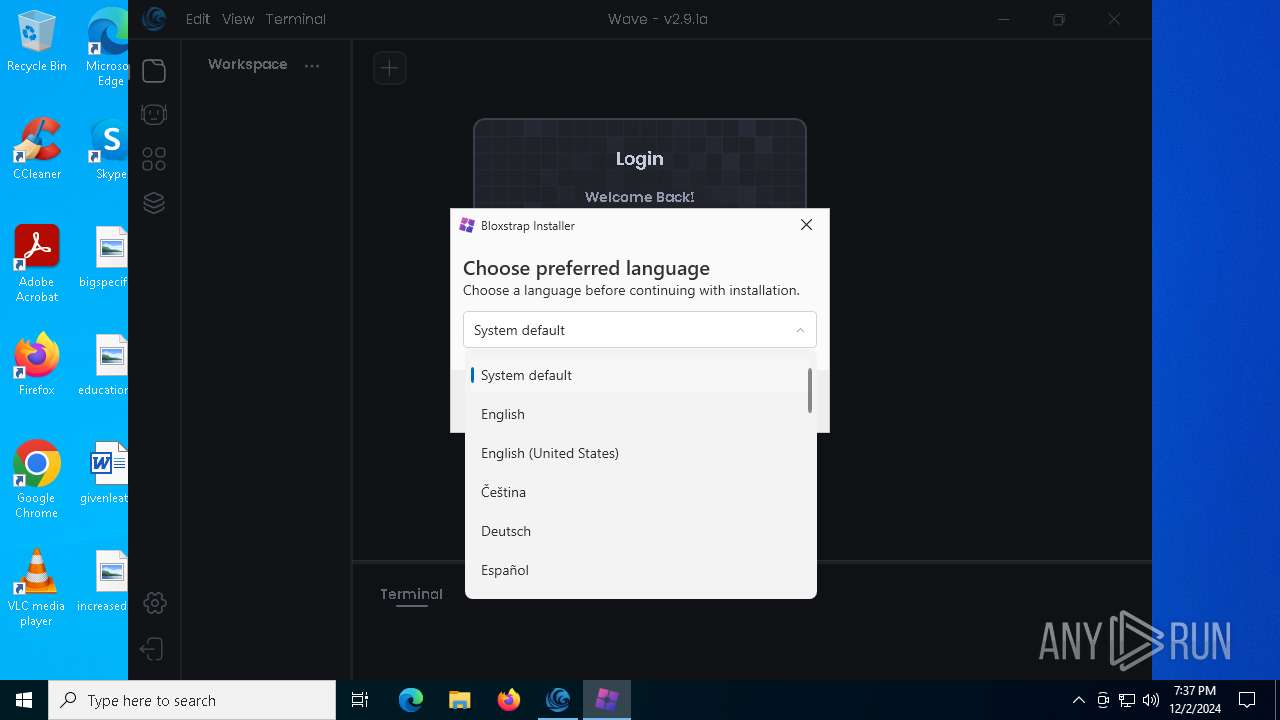
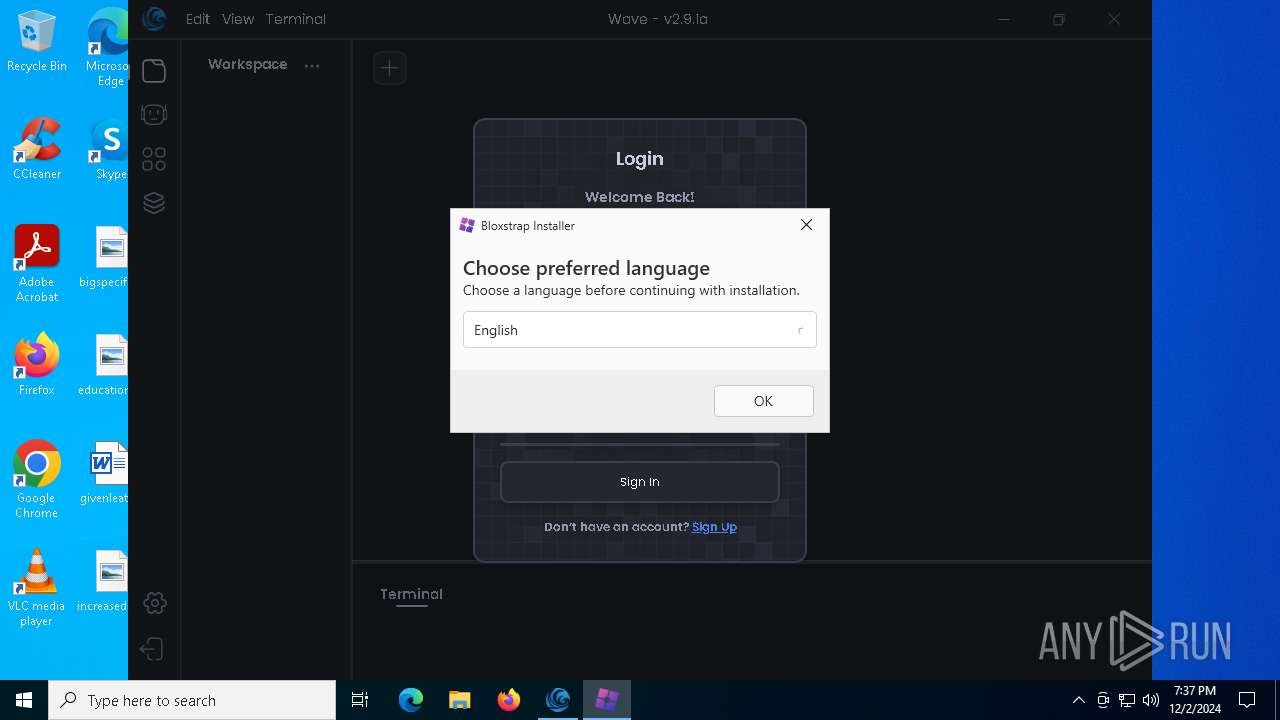
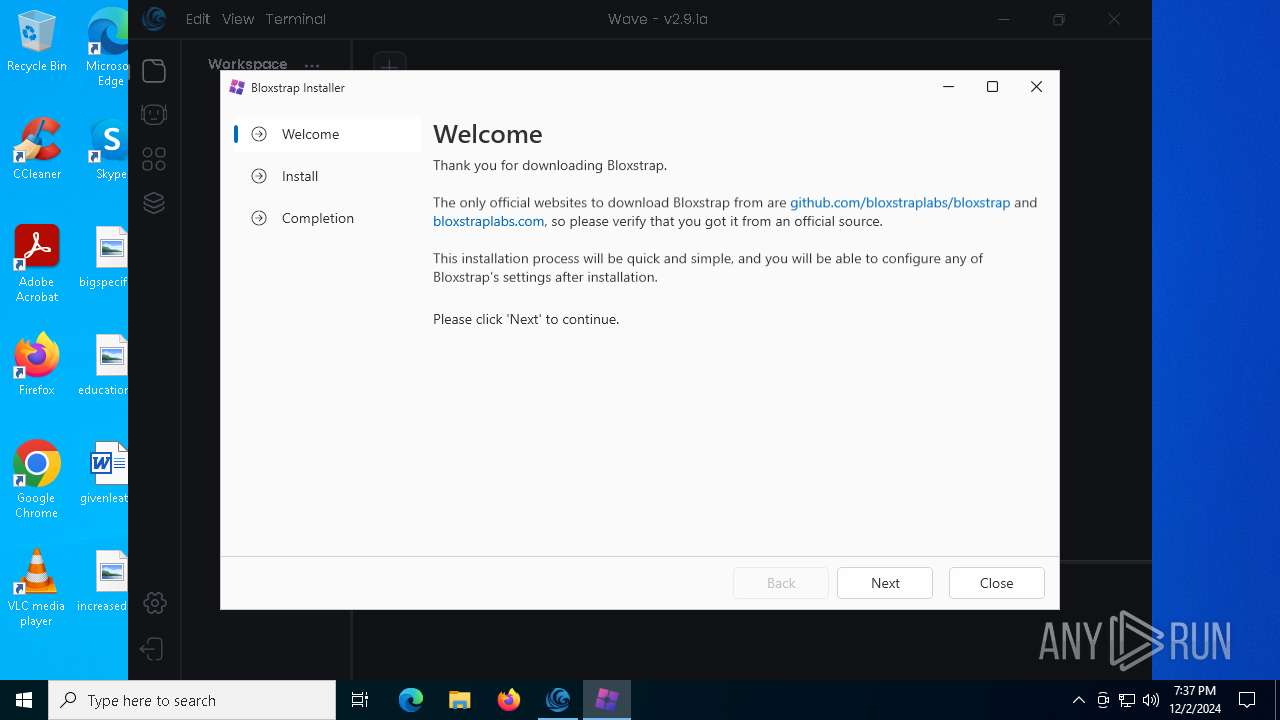
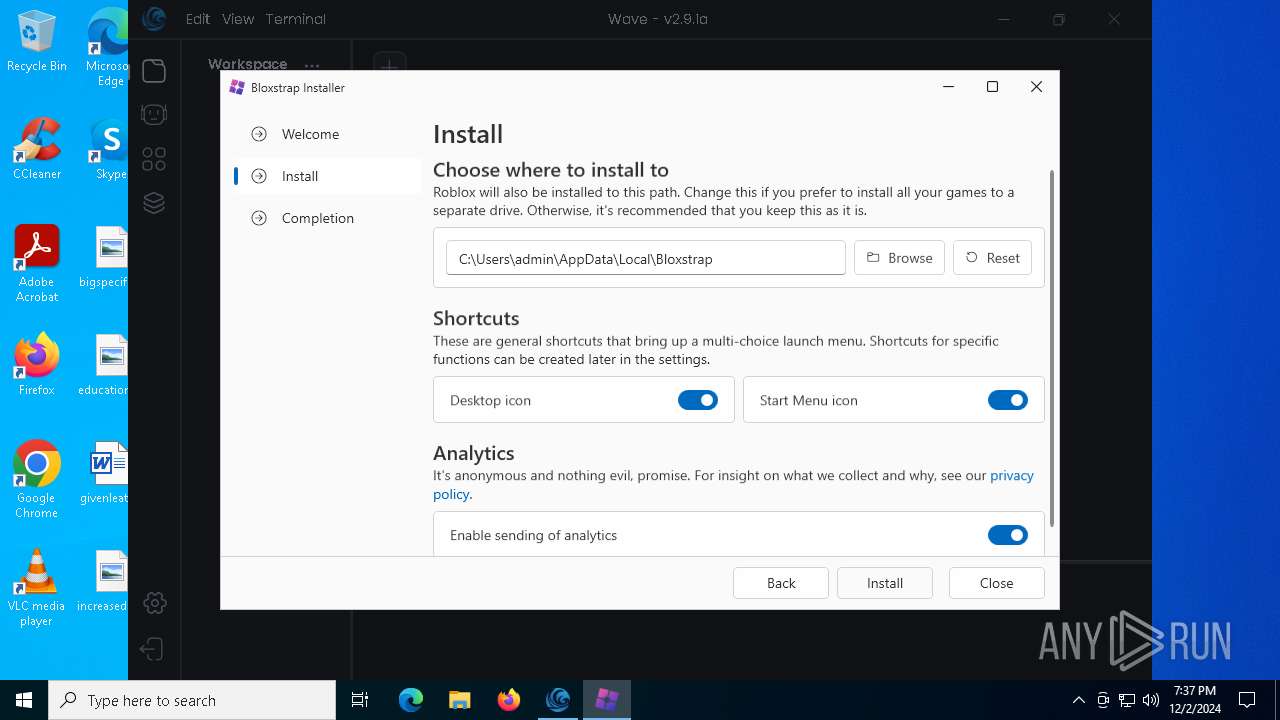
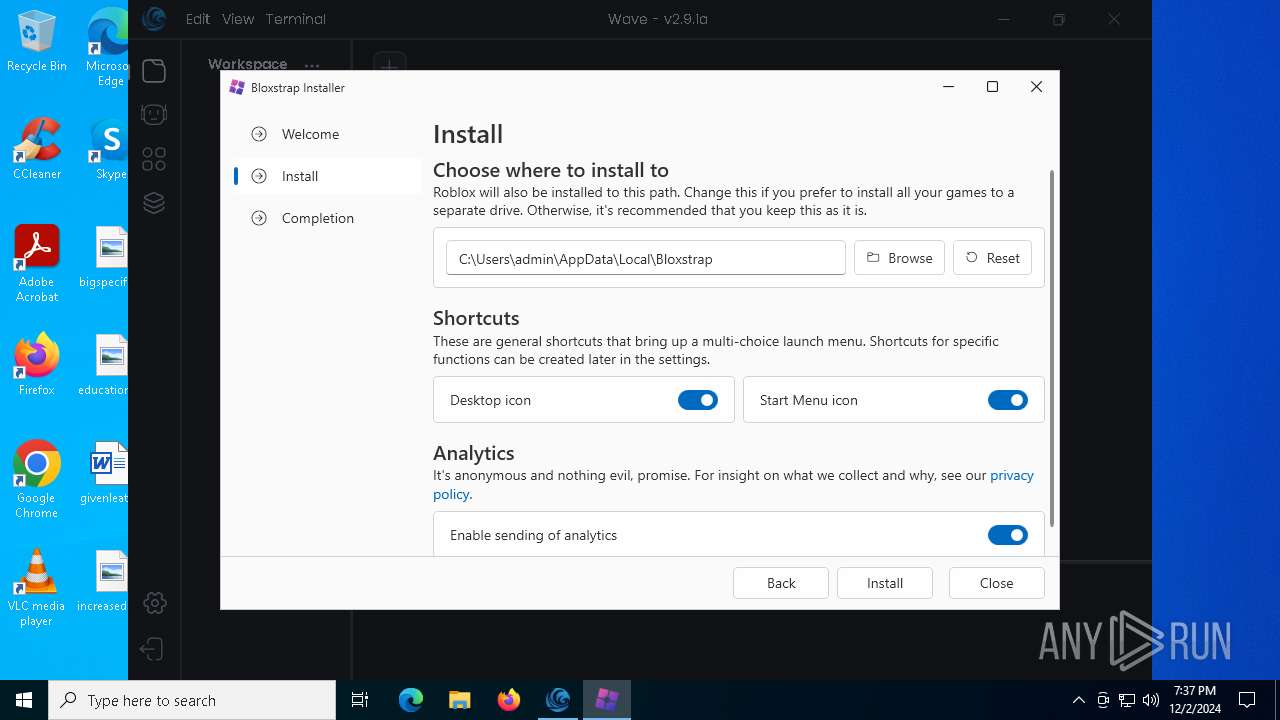
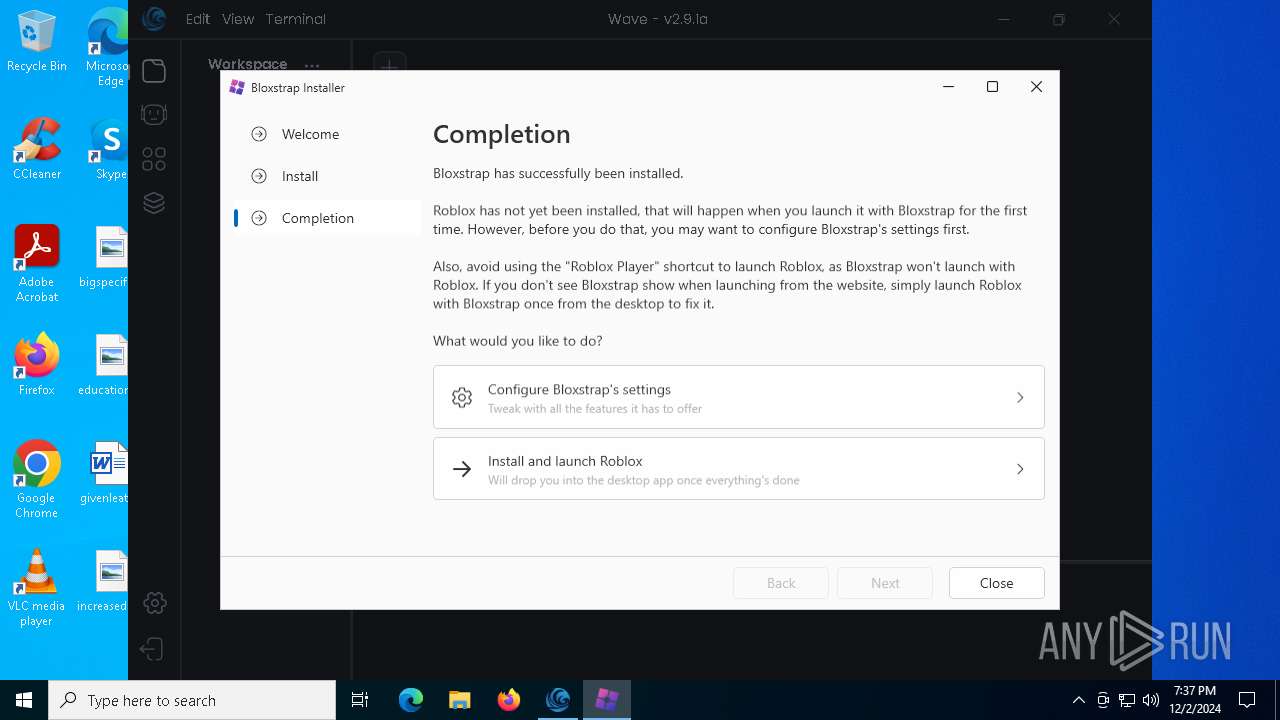
| URL: | https://getwave.gg/ |
| Full analysis: | https://app.any.run/tasks/103a408c-b15a-4302-af4c-08c1297048df |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2024, 19:33:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | CE3B30FB315819A69E70DD1F8B4E3B00 |
| SHA1: | 994B6DE099D67A03253C6D678F1793A3818BBD1B |
| SHA256: | 245FB4AFC200F78B505CF1795AB9AE23C4FAABF0432BF8C14AC088215CC68301 |
| SSDEEP: | 3:N8h9TA2Jn:2cQ |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 6720)
- powershell.exe (PID: 396)
SUSPICIOUS
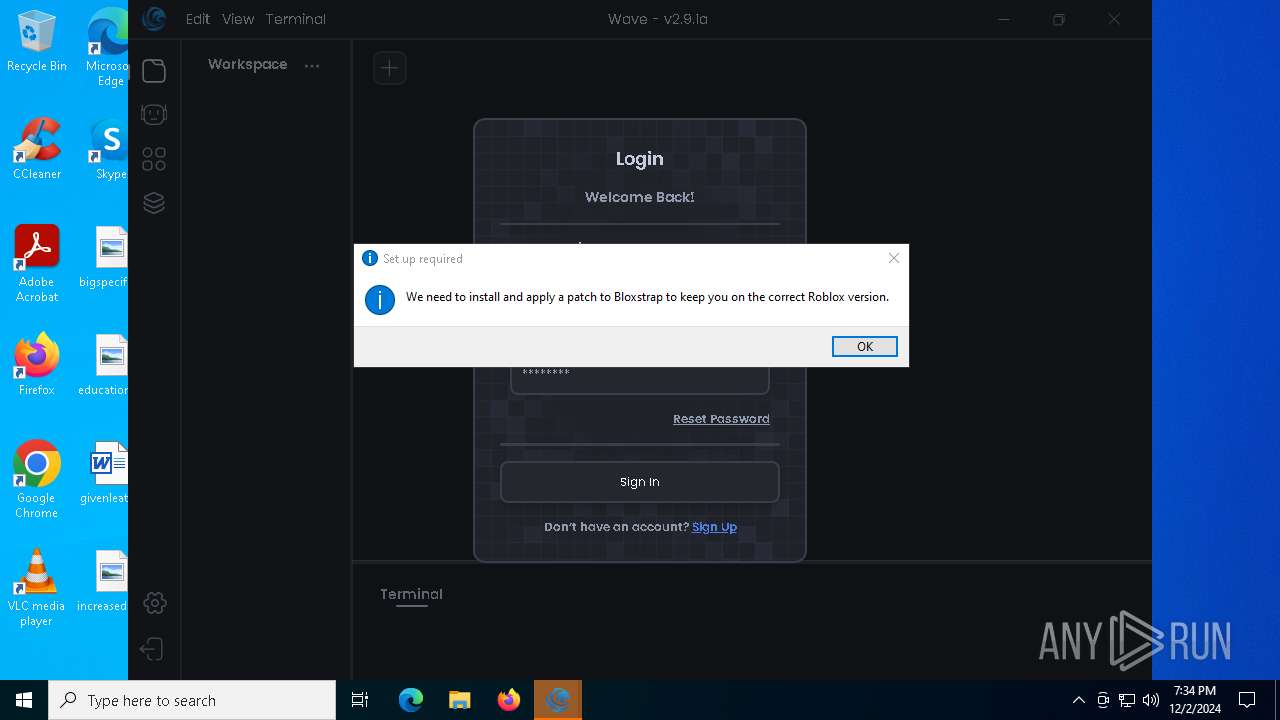
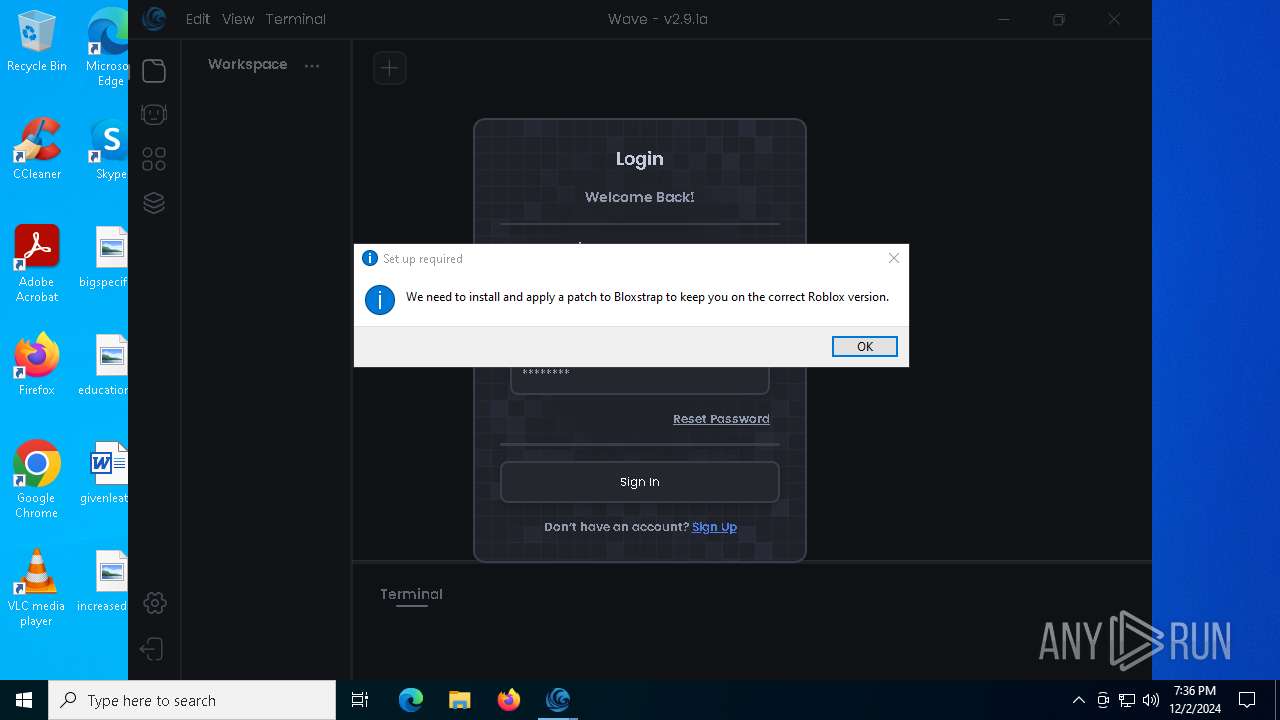
Malware-specific behavior (creating "System.dll" in Temp)
- Wave-Setup.exe (PID: 6300)
Starts CMD.EXE for commands execution
- Wave-Setup.exe (PID: 6300)
- Wave.exe (PID: 5916)
- powershell.exe (PID: 6720)
- Wave.exe (PID: 6424)
- Wave.exe (PID: 7044)
- powershell.exe (PID: 396)
- Wave.exe (PID: 6768)
Executable content was dropped or overwritten
- Wave-Setup.exe (PID: 6300)
- Wave.exe (PID: 6424)
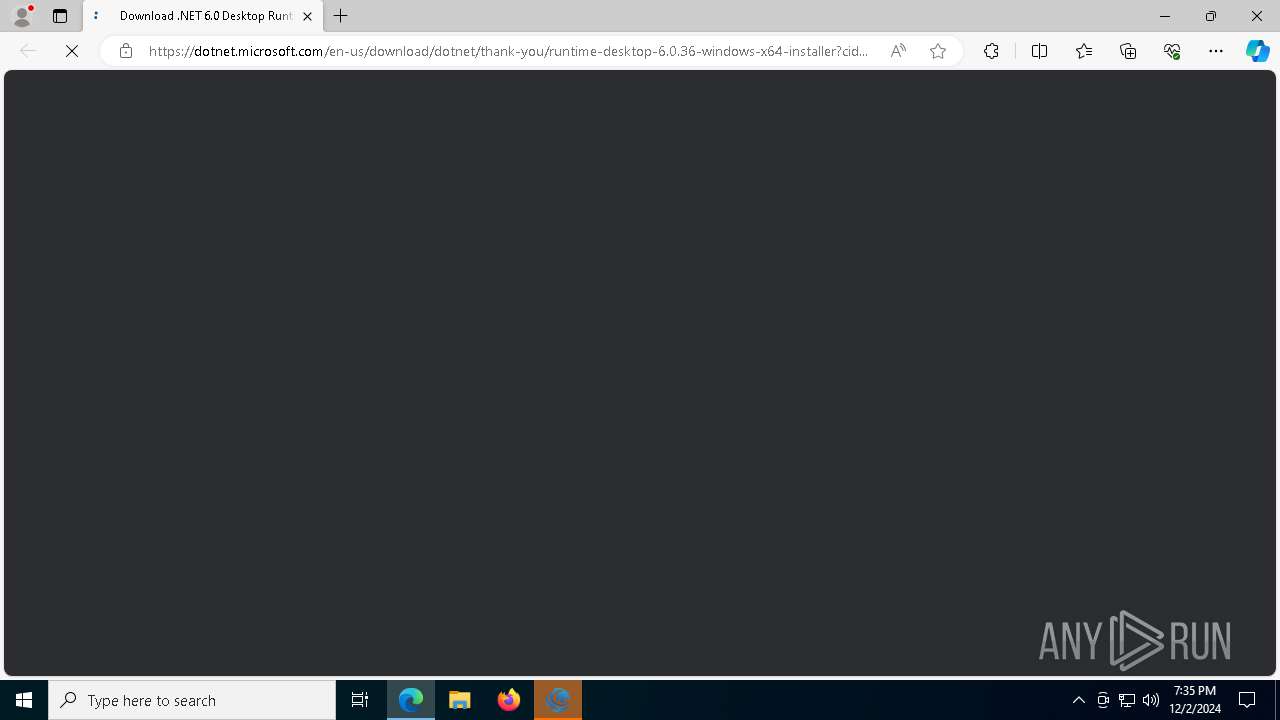
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 4428)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 1576)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 3656)
- Wave.exe (PID: 6768)
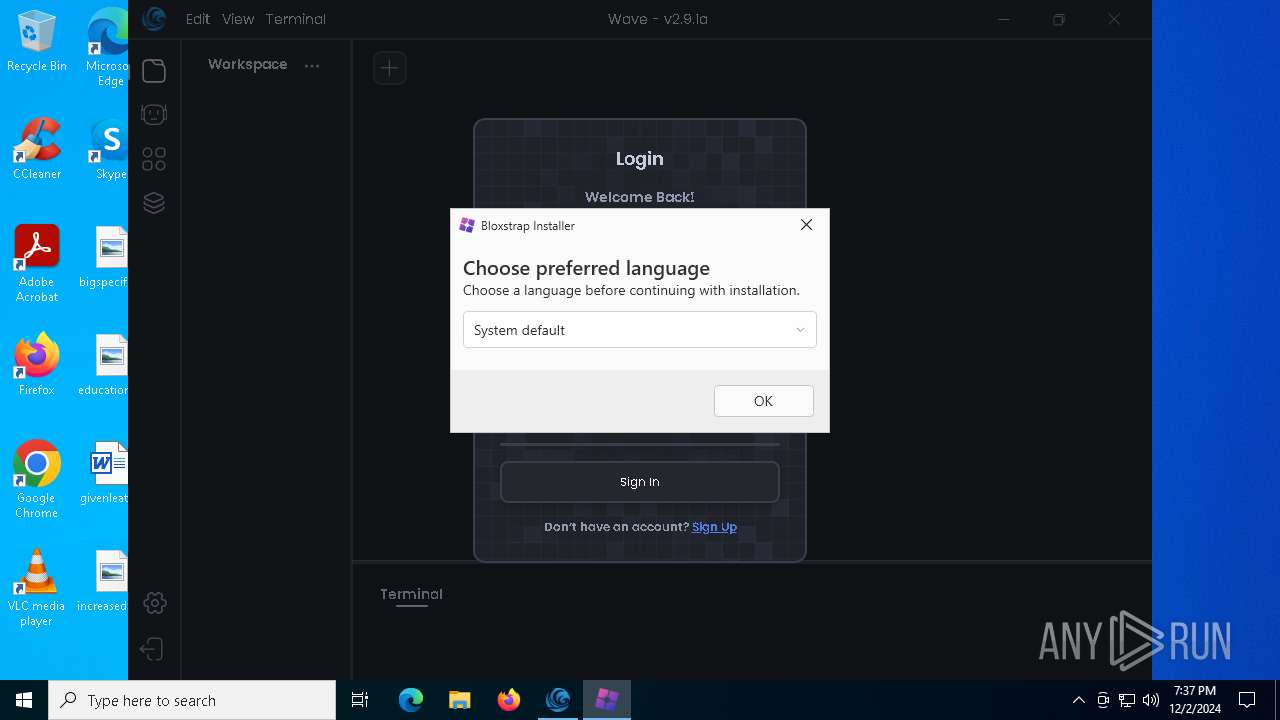
- Bloxstrap.exe (PID: 1172)
Get information on the list of running processes
- Wave-Setup.exe (PID: 6300)
- cmd.exe (PID: 3224)
Drops 7-zip archiver for unpacking
- Wave-Setup.exe (PID: 6300)
Process drops legitimate windows executable
- Wave-Setup.exe (PID: 6300)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 4428)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 3656)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 1576)
- msiexec.exe (PID: 6500)
Executing commands from a ".bat" file
- Wave.exe (PID: 5916)
- powershell.exe (PID: 6720)
- Wave.exe (PID: 7044)
- powershell.exe (PID: 396)
Application launched itself
- Wave.exe (PID: 5916)
- Wave.exe (PID: 6424)
- Wave.exe (PID: 7044)
- Wave.exe (PID: 6768)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6652)
- cmd.exe (PID: 132)
Starts process via Powershell
- powershell.exe (PID: 6720)
- powershell.exe (PID: 396)
Starts application with an unusual extension
- cmd.exe (PID: 6524)
- cmd.exe (PID: 1296)
The executable file from the user directory is run by the CMD process
- Wave.exe (PID: 6424)
- Wave.exe (PID: 6768)
The process deletes folder without confirmation
- Wave.exe (PID: 5916)
Starts a Microsoft application from unusual location
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 3656)
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 1576)
Starts itself from another location
- windowsdesktop-runtime-6.0.36-win-x64.exe (PID: 3656)
The process drops C-runtime libraries
- msiexec.exe (PID: 6500)
INFO
Application launched itself
- chrome.exe (PID: 2956)
- msedge.exe (PID: 6368)
- msedge.exe (PID: 6584)
- msedge.exe (PID: 4672)
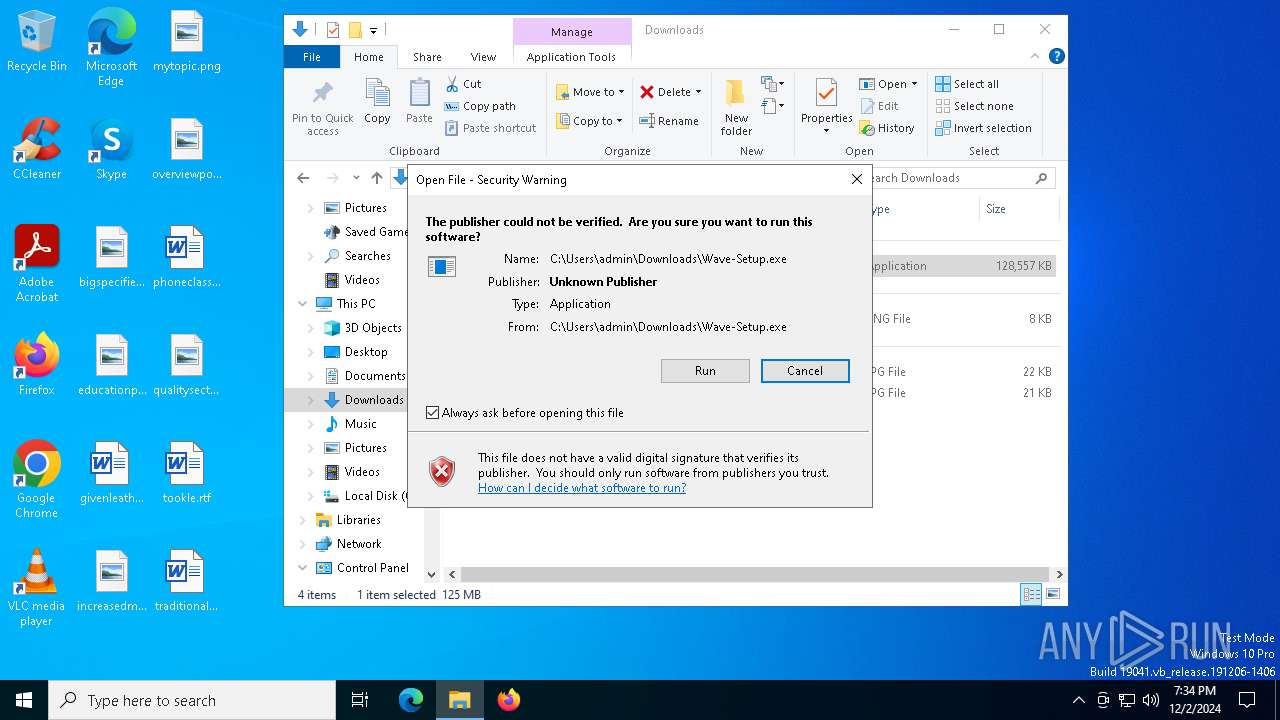
Manual execution by a user
- Wave-Setup.exe (PID: 6300)
- Wave.exe (PID: 5916)
- msedge.exe (PID: 6584)
- Wave.exe (PID: 7044)
Executable content was dropped or overwritten
- chrome.exe (PID: 2956)
- msedge.exe (PID: 6584)
- msiexec.exe (PID: 6500)
Changes the display of characters in the console
- cmd.exe (PID: 6524)
- cmd.exe (PID: 1296)
Node.js compiler has been detected
- Wave.exe (PID: 5916)
Attempting to use instant messaging service
- msedge.exe (PID: 3824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
289
Monitored processes
142
Malicious processes
3
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | C:\WINDOWS\system32\cmd.exe /d /s /c "powershell.exe Start-Process -FilePath "'C:\Users\admin\AppData\Local\Temp\39b110712191dae729dd41d37aae5a10\execute.bat'" -WindowStyle hidden -Verb runAs" | C:\Windows\System32\cmd.exe | — | Wave.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 396 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5268 --field-trial-handle=2332,i,2682333483964724530,3105097841356373329,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 396 | powershell.exe Start-Process -FilePath "'C:\Users\admin\AppData\Local\Temp\39b110712191dae729dd41d37aae5a10\execute.bat'" -WindowStyle hidden -Verb runAs | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 628 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 628 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4272 --field-trial-handle=2376,i,8655759176222163982,10157465641918129267,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 900 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=5424 --field-trial-handle=2332,i,2682333483964724530,3105097841356373329,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 1076 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3780 --field-trial-handle=2332,i,2682333483964724530,3105097841356373329,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1076 | fsutil dirty query C: | C:\Windows\System32\fsutil.exe | — | Wave.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: fsutil.exe Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1144 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2676 --field-trial-handle=2332,i,2682333483964724530,3105097841356373329,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
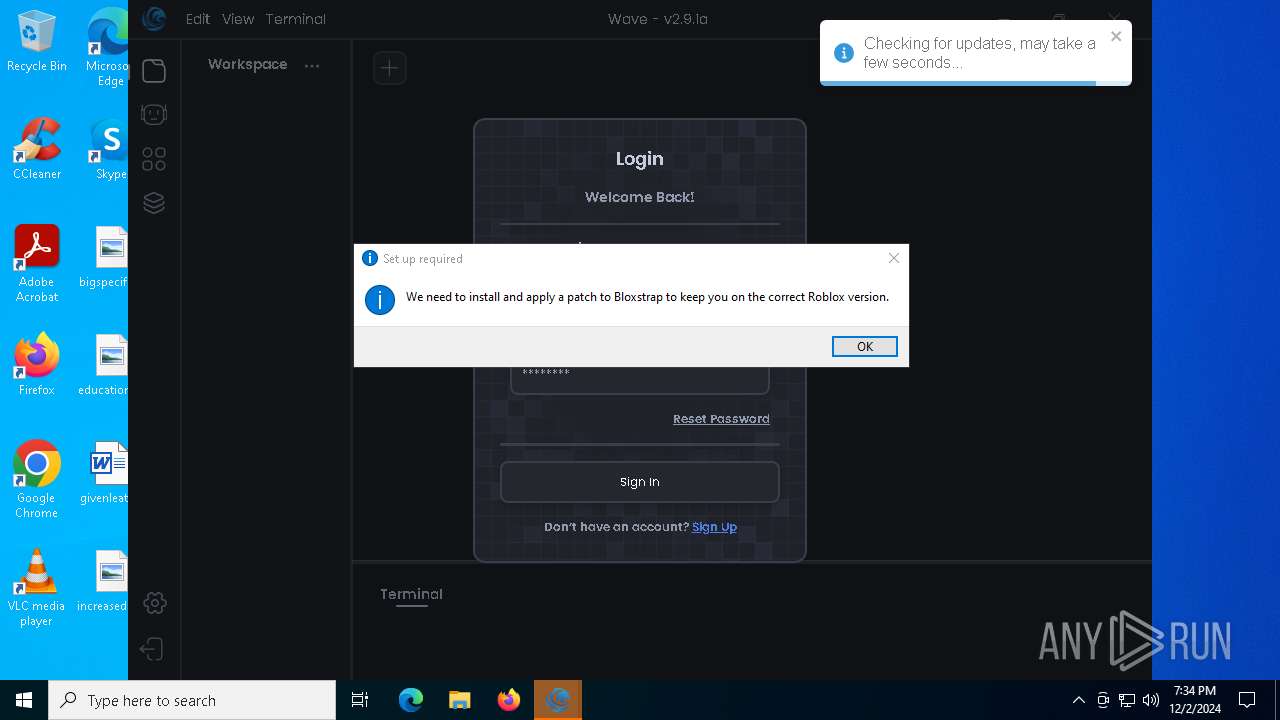
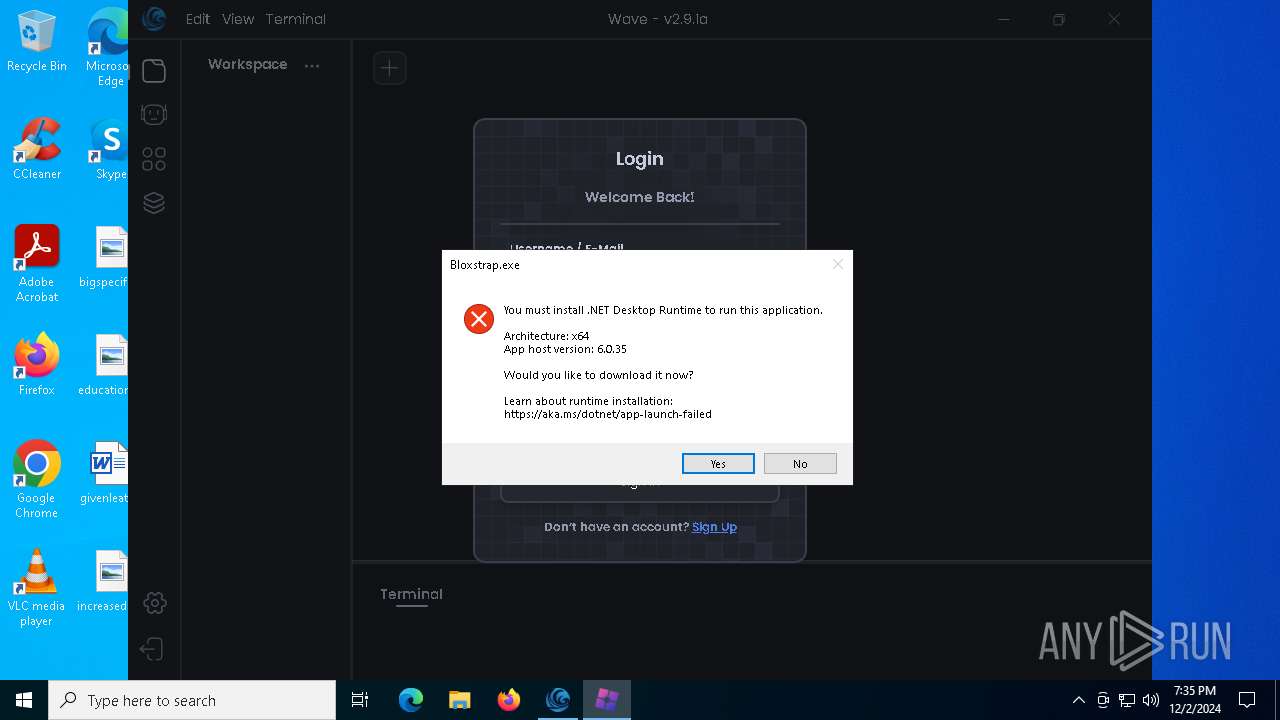
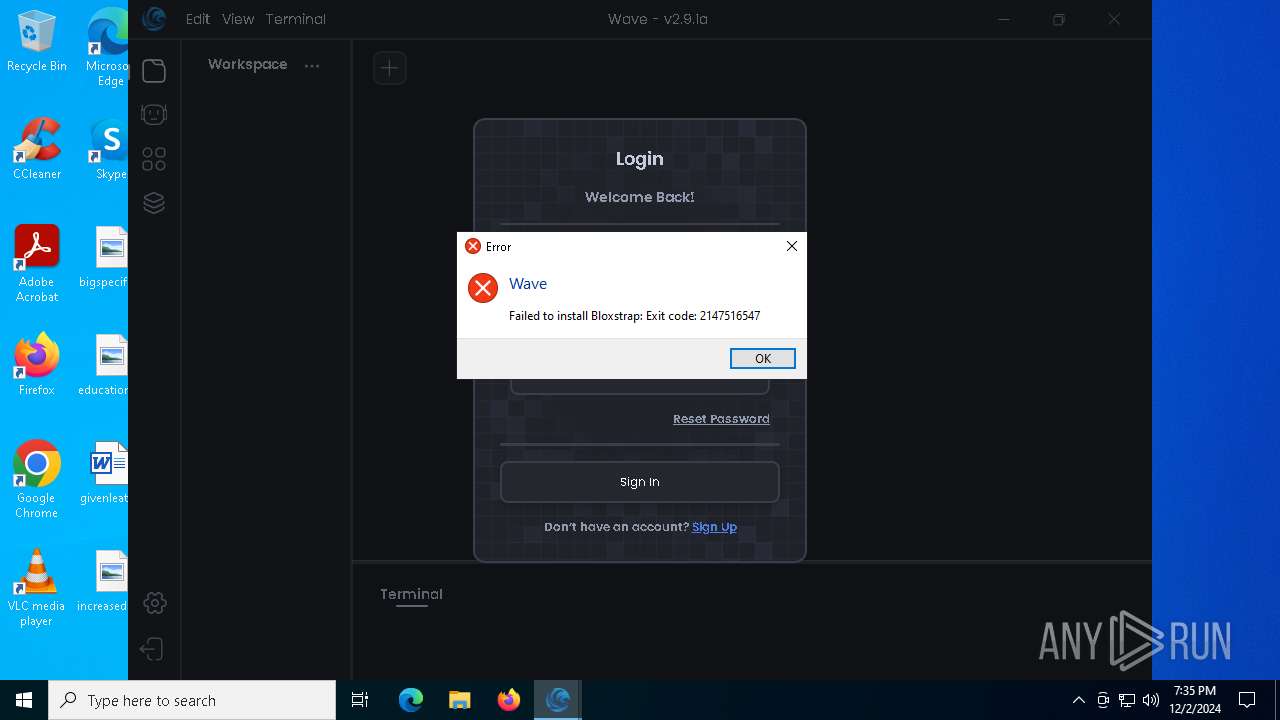
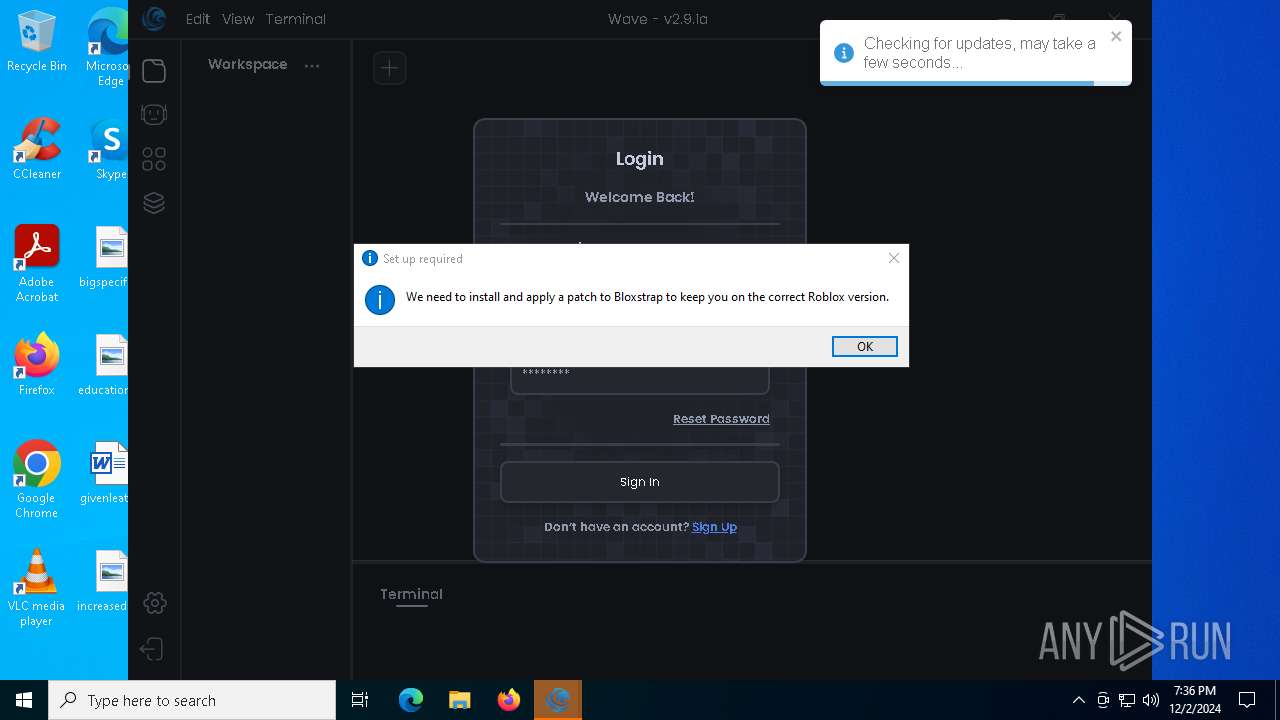
| 1172 | C:\Users\admin\AppData\Local\Programs\Wave\bin\Bloxstrap.exe | C:\Users\admin\AppData\Local\Programs\Wave\bin\Bloxstrap.exe | Wave.exe | ||||||||||||
User: admin Company: Bloxstrap Integrity Level: HIGH Description: Bloxstrap Exit code: 1223 Version: 4.2.1 | |||||||||||||||
Total events
38 824
Read events
37 774
Write events
986
Delete events
64
Modification events
| (PID) Process: | (2956) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2956) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2956) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2956) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2956) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (5572) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 01000000000000004B44FA28F144DB01 | |||
| (PID) Process: | (2956) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (2956) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | GoogleChromeAutoLaunch_A822CA3D40D4B8944864CFEA751D8D57 |
Value: | |||
| (PID) Process: | (6300) Wave-Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\66920116-fd5e-58eb-8cdb-b4525ae2cfc1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\Programs\Wave | |||
| (PID) Process: | (6300) Wave-Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\66920116-fd5e-58eb-8cdb-b4525ae2cfc1 |
| Operation: | write | Name: | KeepShortcuts |
Value: true | |||
Executable files
563
Suspicious files
606
Text files
197
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2956 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF136881.TMP | — | |
MD5:— | SHA256:— | |||
| 2956 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2956 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF136881.TMP | — | |
MD5:— | SHA256:— | |||
| 2956 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2956 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF136881.TMP | — | |
MD5:— | SHA256:— | |||
| 2956 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF136891.TMP | — | |
MD5:— | SHA256:— | |||
| 2956 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2956 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2956 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF136891.TMP | — | |
MD5:— | SHA256:— | |||
| 2956 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF136881.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
115
DNS requests
120
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4328 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6584 | msedge.exe | GET | 200 | 2.16.164.16:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6204 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1733661611&P2=404&P3=2&P4=E31jRUPO3k5bujOwzVcJYOwUgzrpBM2nZTaXM8bs0TS6pIX9bTC%2bgr4sG%2bo%2foUI0VTAuQKQlESoEgezGlDwPjA%3d%3d | unknown | — | — | whitelisted |
6584 | msedge.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
— | — | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1733661611&P2=404&P3=2&P4=E31jRUPO3k5bujOwzVcJYOwUgzrpBM2nZTaXM8bs0TS6pIX9bTC%2bgr4sG%2bo%2foUI0VTAuQKQlESoEgezGlDwPjA%3d%3d | unknown | — | — | whitelisted |
— | — | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1733661611&P2=404&P3=2&P4=E31jRUPO3k5bujOwzVcJYOwUgzrpBM2nZTaXM8bs0TS6pIX9bTC%2bgr4sG%2bo%2foUI0VTAuQKQlESoEgezGlDwPjA%3d%3d | unknown | — | — | whitelisted |
1684 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c5b4d902-2dfd-449f-82ac-4dda5d3a938a?P1=1733733279&P2=404&P3=2&P4=QNN5qaXNEHfVNu05npp4vDChMfUEdMdzgGxFYF9zfBCM2T%2fJNrWi7ghLVA9R9yNNu5pMjXMAOTRjHR%2fjBKjO%2fA%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/c5b4d902-2dfd-449f-82ac-4dda5d3a938a?P1=1733733279&P2=404&P3=2&P4=QNN5qaXNEHfVNu05npp4vDChMfUEdMdzgGxFYF9zfBCM2T%2fJNrWi7ghLVA9R9yNNu5pMjXMAOTRjHR%2fjBKjO%2fA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 104.126.37.177:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1684 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1684 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 23.52.181.141:443 | go.microsoft.com | Akamai International B.V. | US | whitelisted |
2956 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
getwave.gg |
| unknown |
accounts.google.com |
| whitelisted |
a.nel.cloudflare.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6432 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6432 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
3824 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
3824 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
3824 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
3824 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
3824 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
3824 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
3824 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
3824 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
Process | Message |
|---|---|
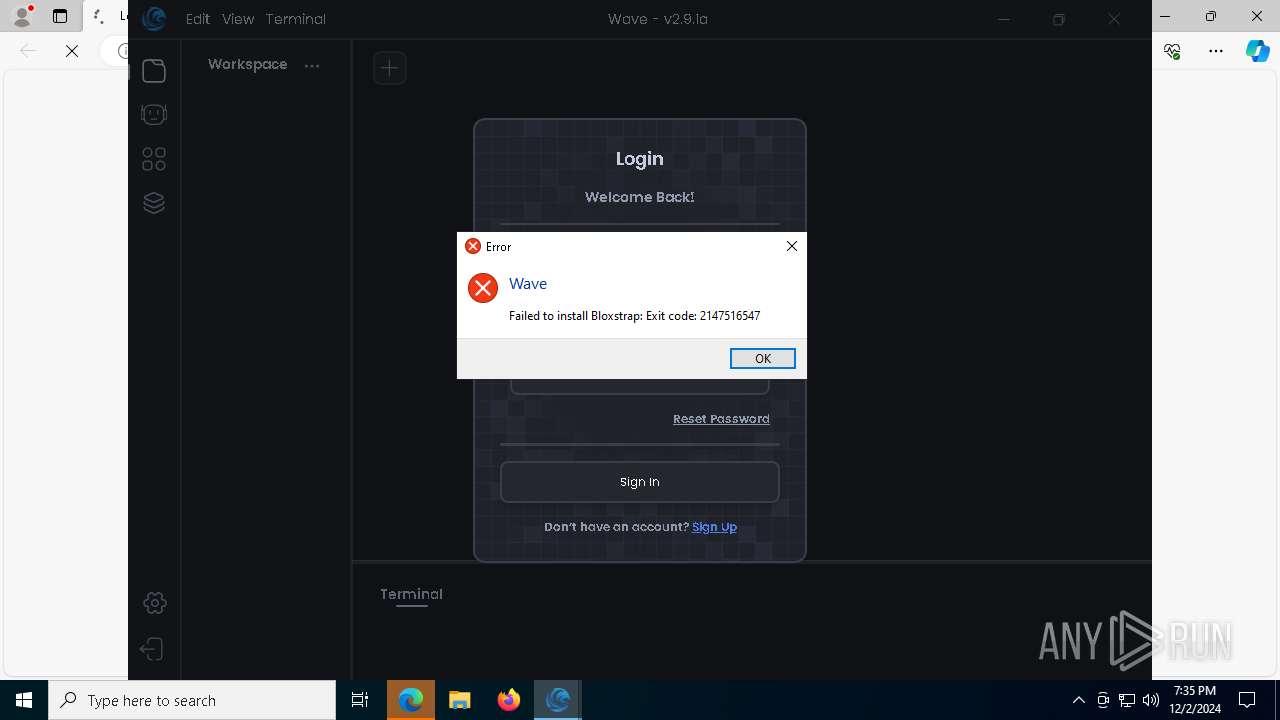
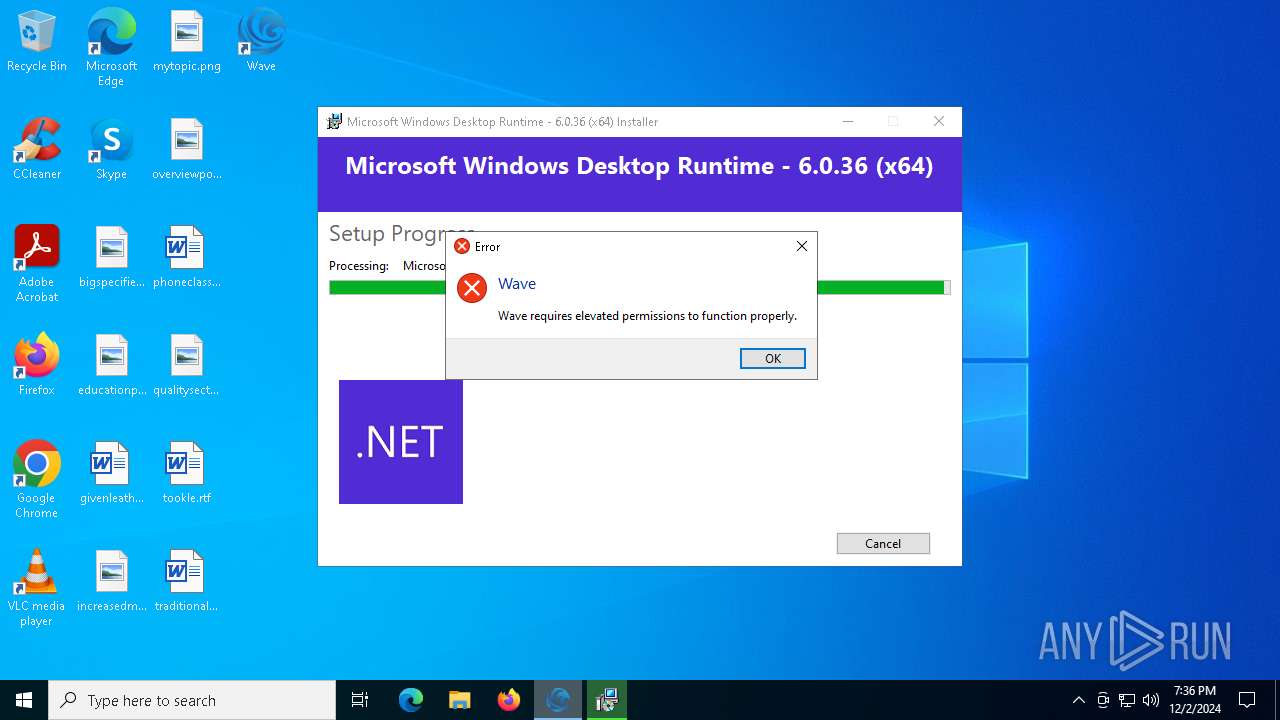
Bloxstrap.exe | You must install .NET to run this application.
App: C:\Users\admin\AppData\Local\Programs\Wave\bin\Bloxstrap.exe
Architecture: x64
App host version: 6.0.35
.NET location: Not found
Learn about runtime installation:
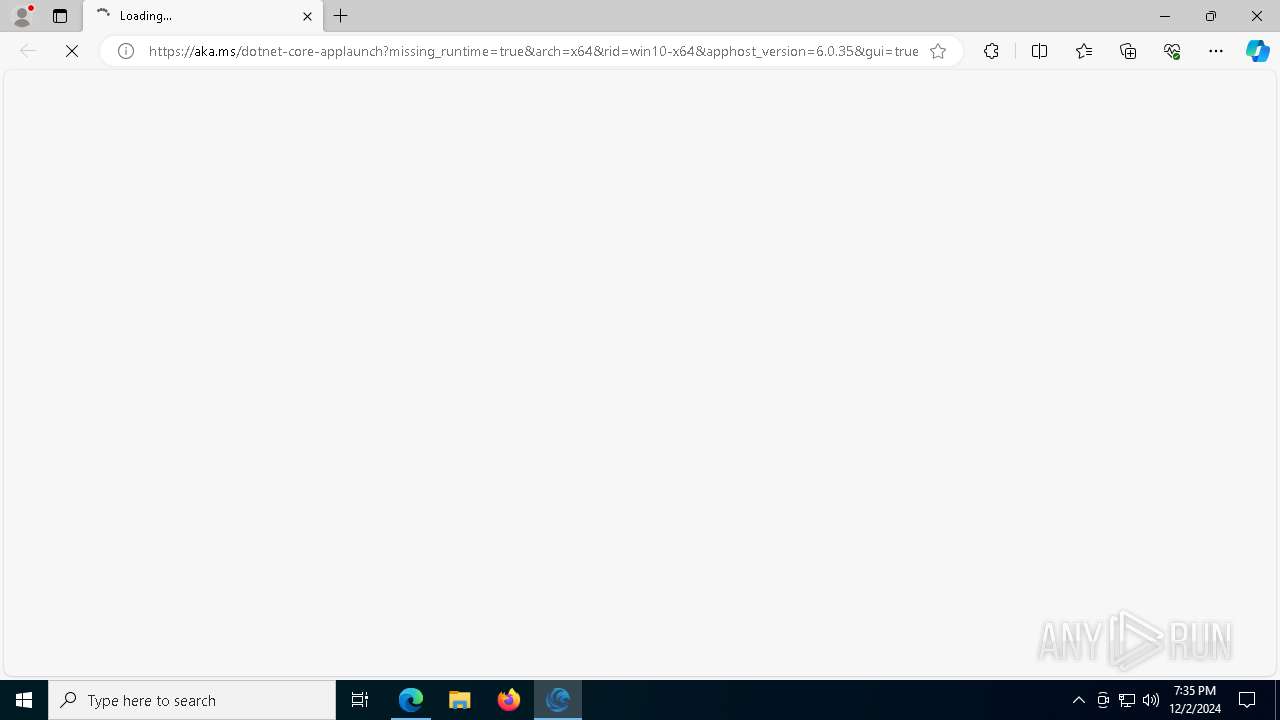
https://aka.ms/dotnet/app-launch-failed
Download the .NET runtime:
https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x64&rid=win10-x64&apphost_version=6.0.35 |