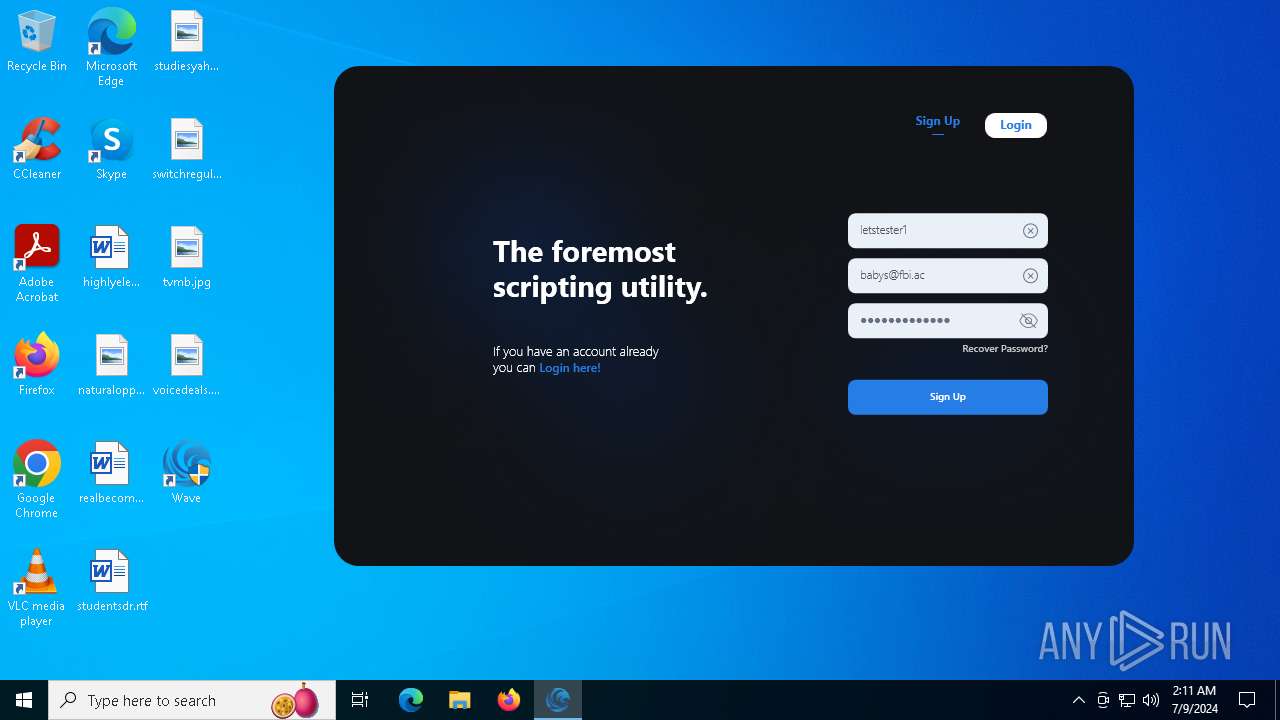
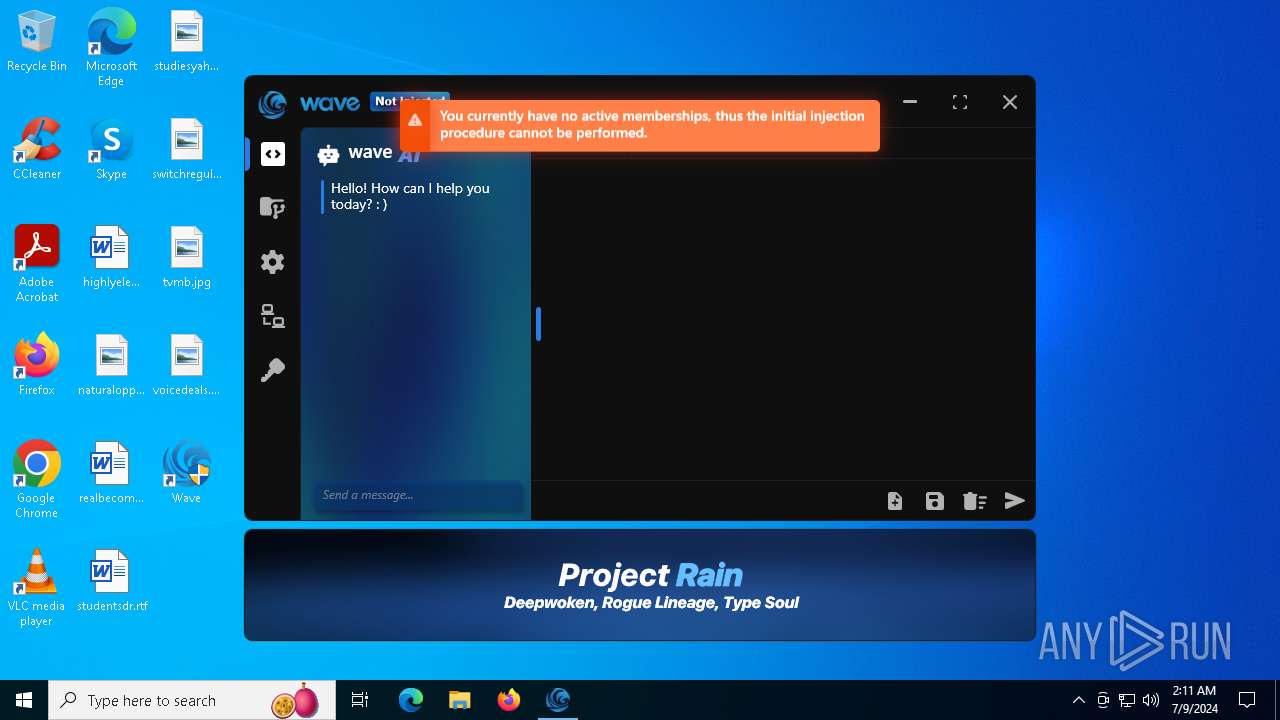
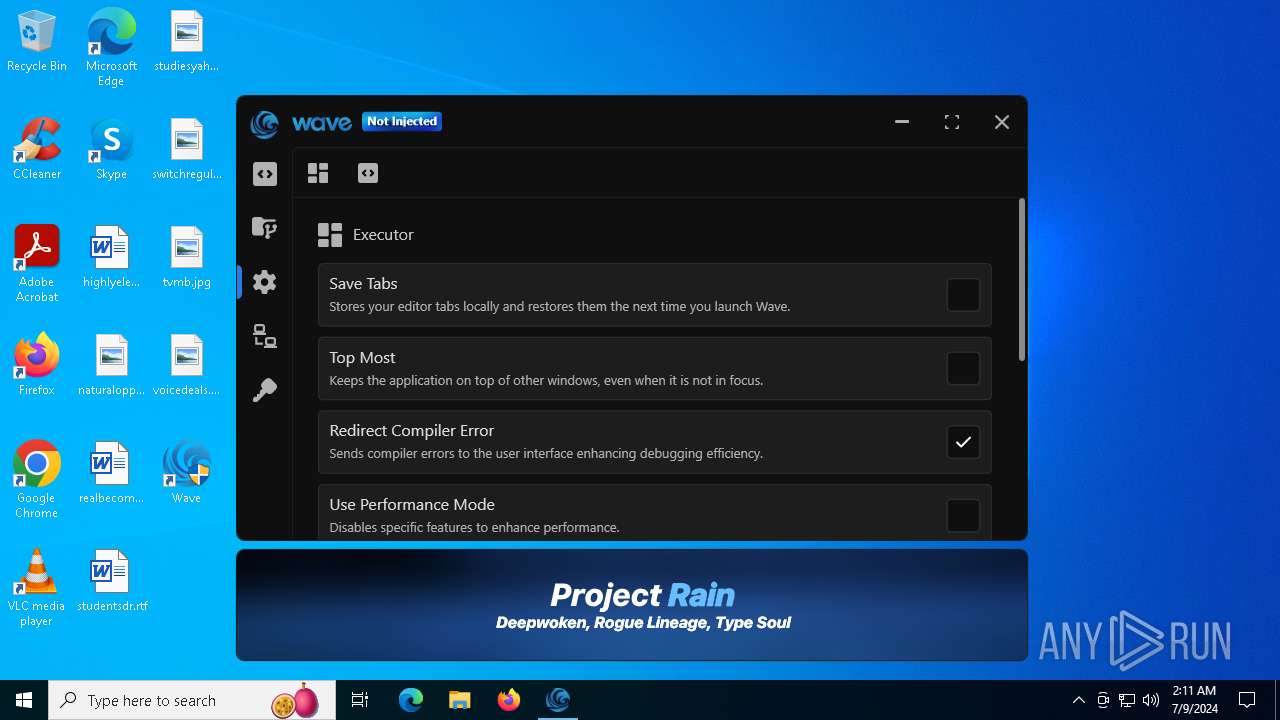
| URL: | https://getwave.gg/ |
| Full analysis: | https://app.any.run/tasks/087e15d2-cde2-46ee-9bfe-bfec208186b6 |
| Verdict: | Malicious activity |
| Analysis date: | July 09, 2024, 02:06:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | CE3B30FB315819A69E70DD1F8B4E3B00 |
| SHA1: | 994B6DE099D67A03253C6D678F1793A3818BBD1B |
| SHA256: | 245FB4AFC200F78B505CF1795AB9AE23C4FAABF0432BF8C14AC088215CC68301 |
| SSDEEP: | 3:N8h9TA2Jn:2cQ |
MALICIOUS
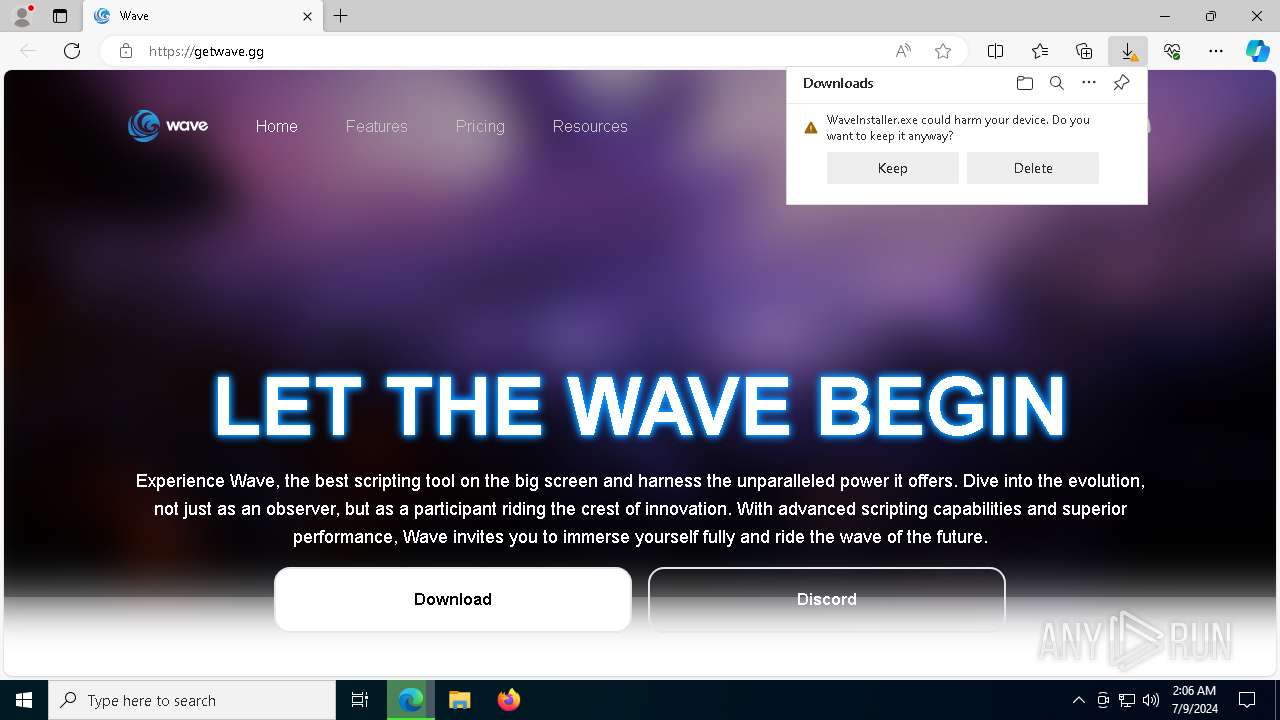
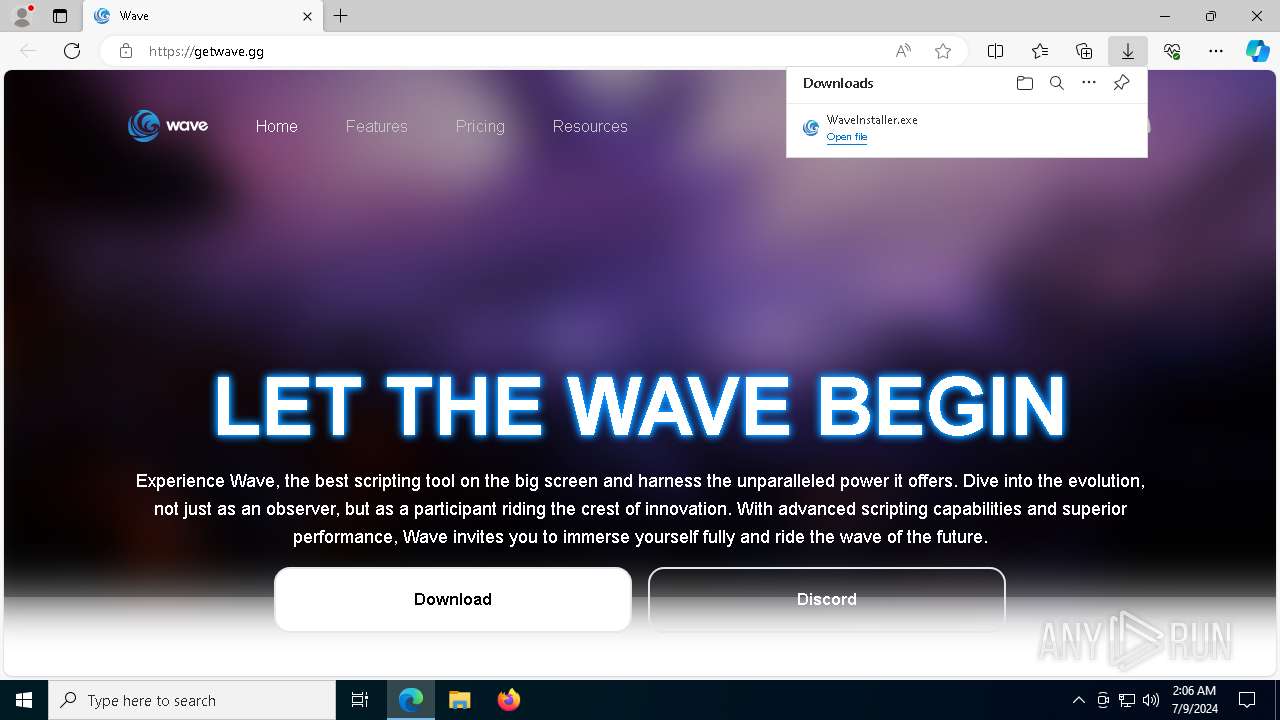
Drops the executable file immediately after the start
- WaveInstaller.exe (PID: 8044)
- WaveWindows.exe (PID: 7900)
SUSPICIOUS
Reads security settings of Internet Explorer
- WaveInstaller.exe (PID: 8044)
- WaveBootstrapper.exe (PID: 7396)
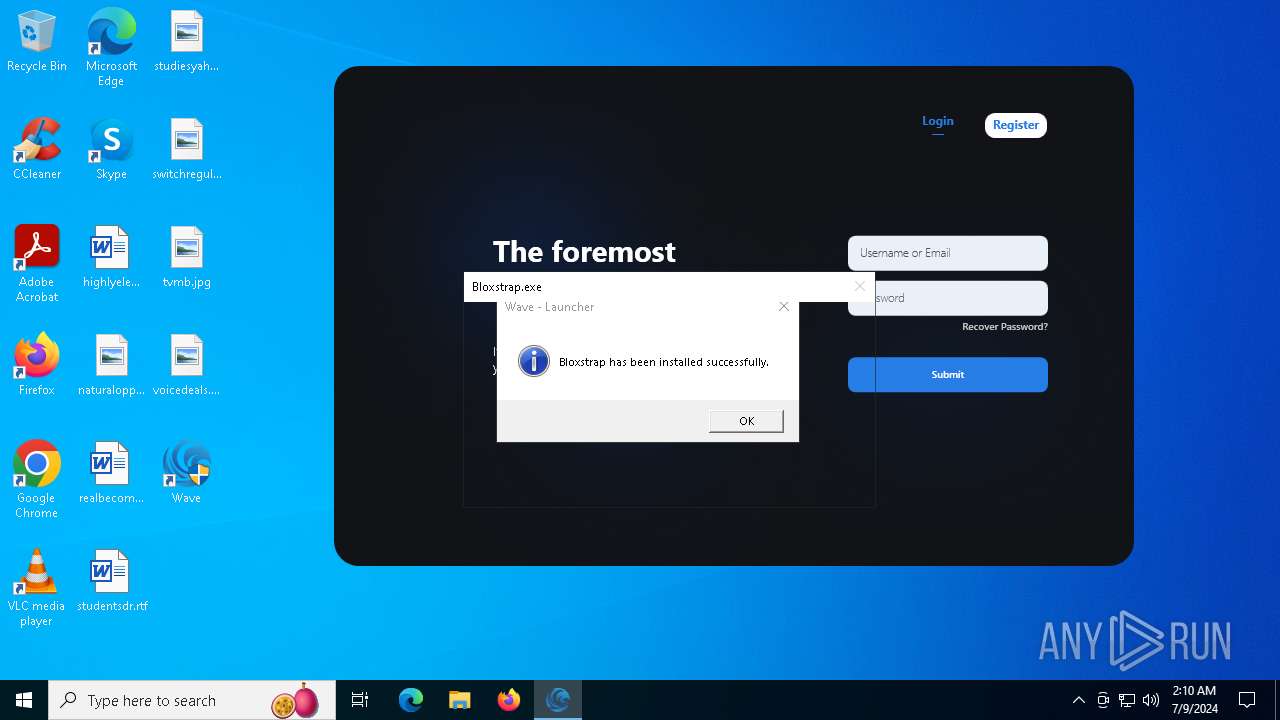
- Bloxstrap.exe (PID: 4976)
- WaveWindows.exe (PID: 7900)
Process drops legitimate windows executable
- WaveInstaller.exe (PID: 8044)
Executable content was dropped or overwritten
- WaveInstaller.exe (PID: 8044)
- WaveWindows.exe (PID: 7900)
Reads the date of Windows installation
- WaveInstaller.exe (PID: 8044)
- WaveBootstrapper.exe (PID: 7396)
- WaveWindows.exe (PID: 7900)
Detected use of alternative data streams (AltDS)
- wave-luau.exe (PID: 7320)
INFO
Application launched itself
- msedge.exe (PID: 3068)
- msedge.exe (PID: 7384)
- msedge.exe (PID: 6836)
Reads Microsoft Office registry keys
- msedge.exe (PID: 3068)
- msedge.exe (PID: 7384)
- Bloxstrap.exe (PID: 4976)
- msedge.exe (PID: 6836)
Executable content was dropped or overwritten
- msedge.exe (PID: 3624)
- msedge.exe (PID: 3068)
Drops the executable file immediately after the start
- msedge.exe (PID: 3624)
- msedge.exe (PID: 3068)
Checks supported languages
- identity_helper.exe (PID: 6476)
- WaveInstaller.exe (PID: 8044)
- identity_helper.exe (PID: 692)
- WaveBootstrapper.exe (PID: 7396)
- WaveWindows.exe (PID: 7900)
- node.exe (PID: 7648)
- identity_helper.exe (PID: 7156)
- CefSharp.BrowserSubprocess.exe (PID: 6980)
- CefSharp.BrowserSubprocess.exe (PID: 1324)
- CefSharp.BrowserSubprocess.exe (PID: 1220)
- CefSharp.BrowserSubprocess.exe (PID: 8032)
- CefSharp.BrowserSubprocess.exe (PID: 5908)
- Bloxstrap.exe (PID: 4976)
- CefSharp.BrowserSubprocess.exe (PID: 8040)
- CefSharp.BrowserSubprocess.exe (PID: 7740)
- wave-luau.exe (PID: 7320)
Reads the computer name
- identity_helper.exe (PID: 6476)
- WaveInstaller.exe (PID: 8044)
- identity_helper.exe (PID: 692)
- WaveBootstrapper.exe (PID: 7396)
- WaveWindows.exe (PID: 7900)
- Bloxstrap.exe (PID: 4976)
- identity_helper.exe (PID: 7156)
- CefSharp.BrowserSubprocess.exe (PID: 6980)
- CefSharp.BrowserSubprocess.exe (PID: 1324)
- CefSharp.BrowserSubprocess.exe (PID: 1220)
- CefSharp.BrowserSubprocess.exe (PID: 8032)
- CefSharp.BrowserSubprocess.exe (PID: 7740)
- CefSharp.BrowserSubprocess.exe (PID: 8040)
- CefSharp.BrowserSubprocess.exe (PID: 5908)
The process uses the downloaded file
- msedge.exe (PID: 3068)
- msedge.exe (PID: 7708)
Reads the machine GUID from the registry
- WaveInstaller.exe (PID: 8044)
- WaveBootstrapper.exe (PID: 7396)
- WaveWindows.exe (PID: 7900)
- CefSharp.BrowserSubprocess.exe (PID: 1324)
- CefSharp.BrowserSubprocess.exe (PID: 8032)
- CefSharp.BrowserSubprocess.exe (PID: 1220)
- CefSharp.BrowserSubprocess.exe (PID: 7740)
- CefSharp.BrowserSubprocess.exe (PID: 5908)
- CefSharp.BrowserSubprocess.exe (PID: 8040)
- CefSharp.BrowserSubprocess.exe (PID: 6980)
Creates files in the program directory
- WaveInstaller.exe (PID: 8044)
- WaveBootstrapper.exe (PID: 7396)
- WaveWindows.exe (PID: 7900)
Reads Environment values
- WaveInstaller.exe (PID: 8044)
- WaveBootstrapper.exe (PID: 7396)
- node.exe (PID: 7648)
- WaveWindows.exe (PID: 7900)
Checks proxy server information
- WaveInstaller.exe (PID: 8044)
- slui.exe (PID: 5624)
- WaveBootstrapper.exe (PID: 7396)
- WaveWindows.exe (PID: 7900)
Reads the software policy settings
- slui.exe (PID: 7416)
- slui.exe (PID: 5624)
- WaveBootstrapper.exe (PID: 7396)
- WaveWindows.exe (PID: 7900)
- WaveInstaller.exe (PID: 8044)
Creates files or folders in the user directory
- WaveInstaller.exe (PID: 8044)
- WaveWindows.exe (PID: 7900)
Process checks computer location settings
- WaveInstaller.exe (PID: 8044)
- WaveBootstrapper.exe (PID: 7396)
- WaveWindows.exe (PID: 7900)
- node.exe (PID: 7648)
- CefSharp.BrowserSubprocess.exe (PID: 5908)
- CefSharp.BrowserSubprocess.exe (PID: 1220)
Disables trace logs
- WaveBootstrapper.exe (PID: 7396)
- WaveWindows.exe (PID: 7900)
- WaveInstaller.exe (PID: 8044)
Checks for the presence of KasperskyLab
- WaveWindows.exe (PID: 7900)
Reads product name
- node.exe (PID: 7648)
Create files in a temporary directory
- WaveWindows.exe (PID: 7900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
254
Monitored processes
102
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 692 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=3320 --field-trial-handle=2228,i,15051762683127444209,3079899189302900488,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 836 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3280 --field-trial-handle=2228,i,15051762683127444209,3079899189302900488,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 884 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=21 --mojo-platform-channel-handle=5360 --field-trial-handle=2316,i,11840467186088719742,11129535436603108854,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1064 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3724 --field-trial-handle=2316,i,8149325105625651031,1360052420262780611,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1164 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=3720 --field-trial-handle=2316,i,8149325105625651031,1360052420262780611,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1220 | "C:\Users\admin\AppData\Local\Wave\CefSharp.BrowserSubprocess.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Local\CEF\User Data" --cefsharpexitsub --no-sandbox --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --field-trial-handle=7368,i,10562019025336091780,4746190827423615951,262144 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,DocumentPictureInPictureAPI --variations-seed-version --enable-logging=handle --log-file=7380 --mojo-platform-channel-handle=7360 --host-process-id=7900 /prefetch:1 | C:\Users\admin\AppData\Local\Wave\CefSharp.BrowserSubprocess.exe | WaveWindows.exe | ||||||||||||
User: admin Company: The CefSharp Authors Integrity Level: HIGH Description: CefSharp.BrowserSubprocess Version: 124.3.80.0 Modules
| |||||||||||||||
| 1324 | "C:\Users\admin\AppData\Local\Wave\CefSharp.BrowserSubprocess.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-sandbox --lang=en-US --user-data-dir="C:\Users\admin\AppData\Local\CEF\User Data" --cefsharpexitsub --field-trial-handle=6780,i,10562019025336091780,4746190827423615951,262144 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,DocumentPictureInPictureAPI --variations-seed-version --enable-logging=handle --log-file=6784 --mojo-platform-channel-handle=6776 /prefetch:3 --host-process-id=7900 | C:\Users\admin\AppData\Local\Wave\CefSharp.BrowserSubprocess.exe | — | WaveWindows.exe | |||||||||||
User: admin Company: The CefSharp Authors Integrity Level: HIGH Description: CefSharp.BrowserSubprocess Version: 124.3.80.0 Modules
| |||||||||||||||
| 1328 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4540 --field-trial-handle=2228,i,15051762683127444209,3079899189302900488,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1708 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=4824 --field-trial-handle=2228,i,15051762683127444209,3079899189302900488,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1908 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=3692 --field-trial-handle=2316,i,11840467186088719742,11129535436603108854,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
44 633
Read events
44 311
Write events
316
Delete events
6
Modification events
| (PID) Process: | (3068) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3068) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3068) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3068) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3068) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3068) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3068) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3068) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (3068) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3068) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 0 | |||
Executable files
33
Suspicious files
408
Text files
196
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1ce75a.TMP | — | |
MD5:— | SHA256:— | |||
| 3068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1ce75a.TMP | — | |
MD5:— | SHA256:— | |||
| 3068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1ce76a.TMP | — | |
MD5:— | SHA256:— | |||
| 3068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1ce76a.TMP | — | |
MD5:— | SHA256:— | |||
| 3068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1ce76a.TMP | — | |
MD5:— | SHA256:— | |||
| 3068 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
148
DNS requests
103
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1832 | svchost.exe | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
4632 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
452 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
1832 | svchost.exe | GET | 200 | 104.79.89.142:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
6768 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
5080 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
452 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
7300 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/cea6d764-36bf-4144-a357-ec91013ddbf5?P1=1720569934&P2=404&P3=2&P4=JuIWClBA%2bI3ZTX7vARsCY9R%2bbjPtK0yQzrY8y53MybnVlM665IgIDg8Qs3mAlhi%2ftHo%2bjnVhWiQVxTNSStj6mw%3d%3d | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1832 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3868 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1776 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3624 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3068 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3624 | msedge.exe | 172.67.73.56:443 | getwave.gg | CLOUDFLARENET | US | unknown |
3624 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3624 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
getwave.gg |
| unknown |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| unknown |
bzib.nelreports.net |
| whitelisted |
www.bing.com |
| whitelisted |
xpaywalletcdn.azureedge.net |
| unknown |
cdn.getwave.gg |
| unknown |
update.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
Process | Message |
|---|---|
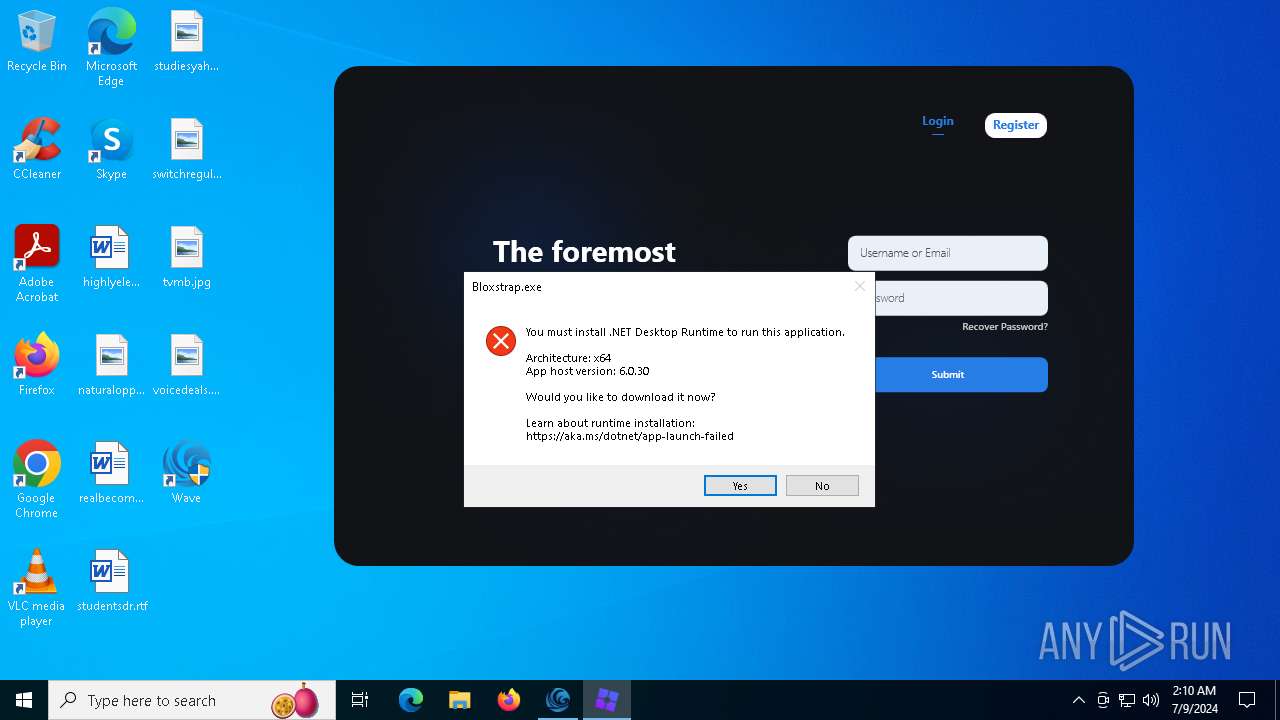
Bloxstrap.exe | You must install .NET to run this application.
App: C:\Users\admin\AppData\Local\Bloxstrap\Bloxstrap.exe
Architecture: x64
App host version: 6.0.30
.NET location: Not found
Learn about runtime installation:
https://aka.ms/dotnet/app-launch-failed
Download the .NET runtime:
https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x64&rid=win10-x64&apphost_version=6.0.30 |
WaveWindows.exe | [0709/021129.297:WARNING:resource_util.cc(94)] Please customize CefSettings.root_cache_path for your application. Use of the default value may lead to unintended process singleton behavior.
|
CefSharp.BrowserSubprocess.exe | [0709/021129.489:ERROR:angle_platform_impl.cc(44)] Display.cpp:1086 (initialize): ANGLE Display::initialize error 0: Internal Vulkan error (-3): Initialization of an object could not be completed for implementation-specific reasons, in ..\..\third_party\angle\src\libANGLE\renderer\vulkan\RendererVk.cpp, initialize:1715.
|
CefSharp.BrowserSubprocess.exe | [0709/021129.489:ERROR:gl_display.cc(515)] EGL Driver message (Critical) eglInitialize: Internal Vulkan error (-3): Initialization of an object could not be completed for implementation-specific reasons, in ..\..\third_party\angle\src\libANGLE\renderer\vulkan\RendererVk.cpp, initialize:1715.
|
CefSharp.BrowserSubprocess.exe | [0709/021129.491:ERROR:gl_display.cc(786)] eglInitialize SwANGLE failed with error EGL_NOT_INITIALIZED
|
CefSharp.BrowserSubprocess.exe | [0709/021129.491:ERROR:gl_display.cc(820)] Initialization of all EGL display types failed.
|
CefSharp.BrowserSubprocess.exe | [0709/021129.492:ERROR:gl_initializer_win.cc(135)] GLDisplayEGL::Initialize failed.
|
CefSharp.BrowserSubprocess.exe | [0709/021129.492:ERROR:angle_platform_impl.cc(44)] Display.cpp:1086 (initialize): ANGLE Display::initialize error 0: Internal Vulkan error (-3): Initialization of an object could not be completed for implementation-specific reasons, in ..\..\third_party\angle\src\libANGLE\renderer\vulkan\RendererVk.cpp, initialize:1715.
|
CefSharp.BrowserSubprocess.exe | [0709/021129.492:ERROR:gl_display.cc(515)] EGL Driver message (Critical) eglInitialize: Internal Vulkan error (-3): Initialization of an object could not be completed for implementation-specific reasons, in ..\..\third_party\angle\src\libANGLE\renderer\vulkan\RendererVk.cpp, initialize:1715.
|
CefSharp.BrowserSubprocess.exe | [0709/021129.492:ERROR:gl_display.cc(786)] eglInitialize SwANGLE failed with error EGL_NOT_INITIALIZED
|