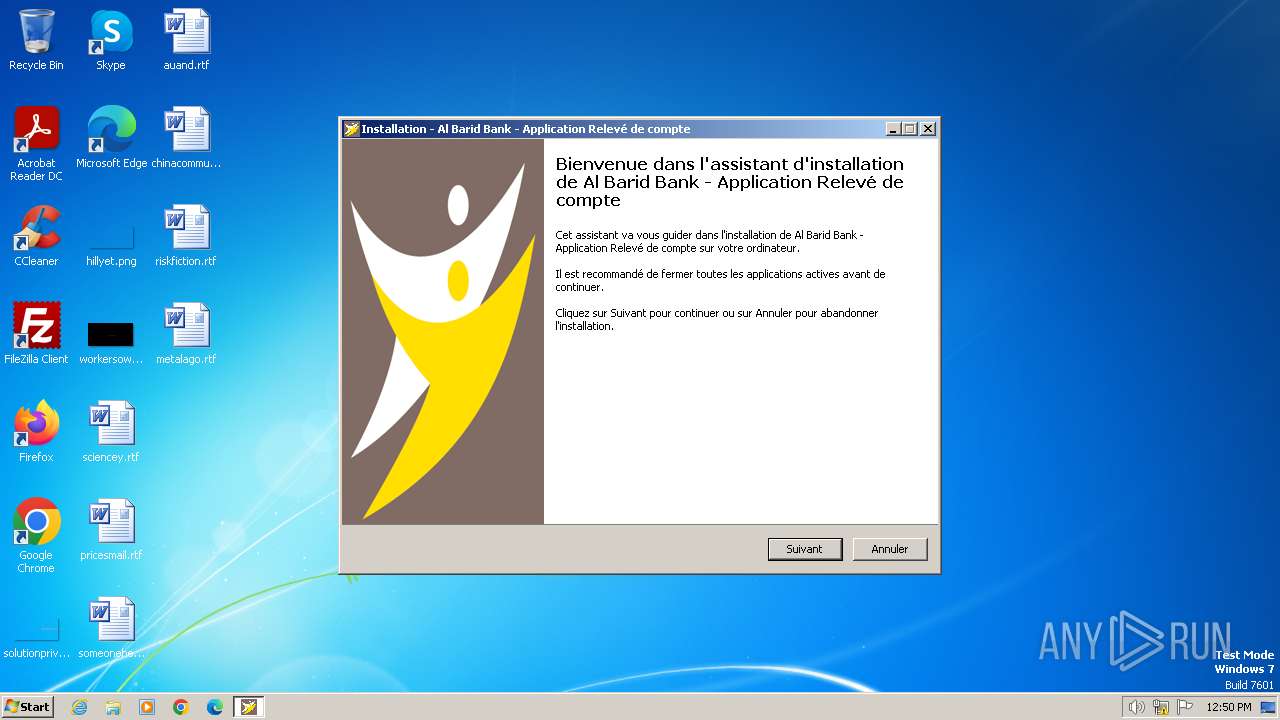
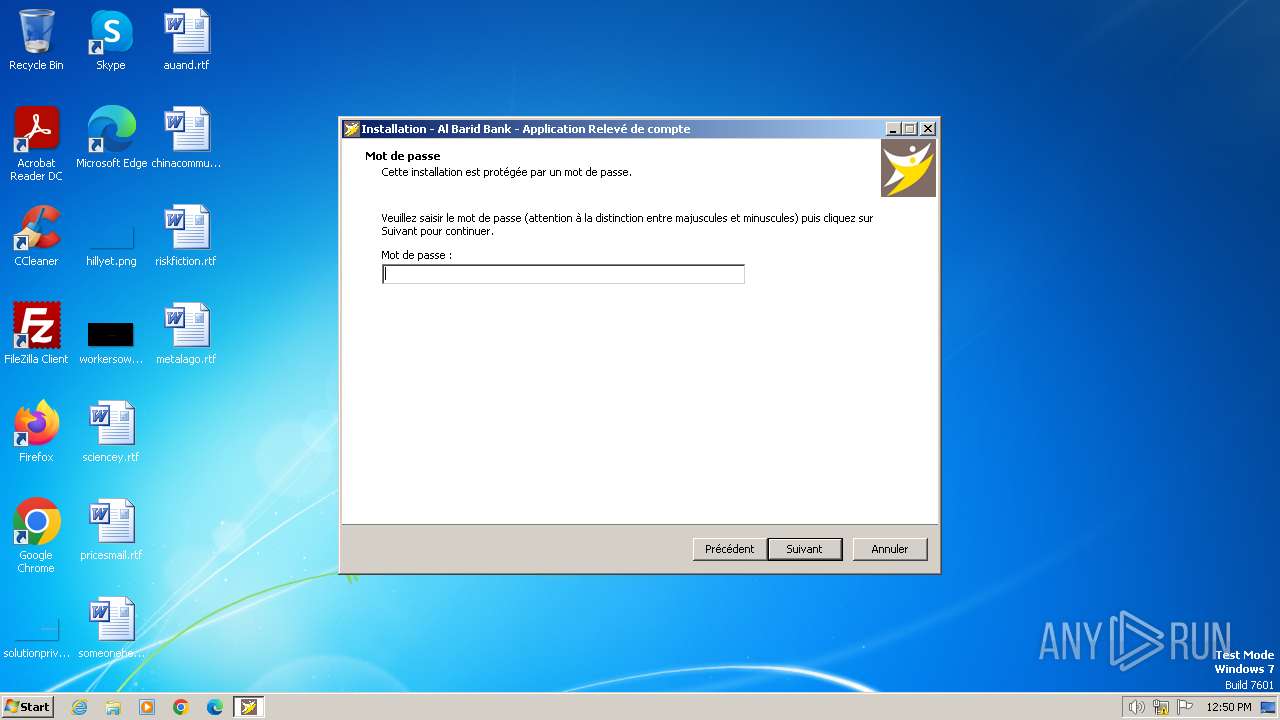
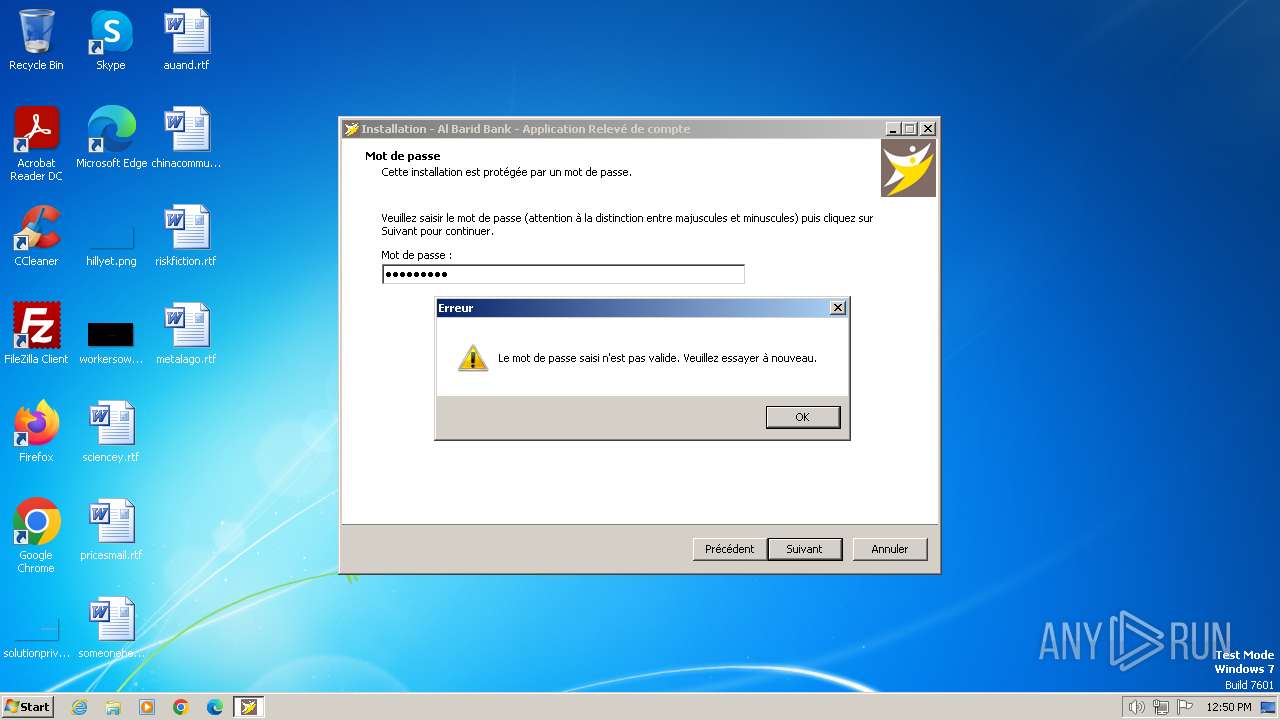
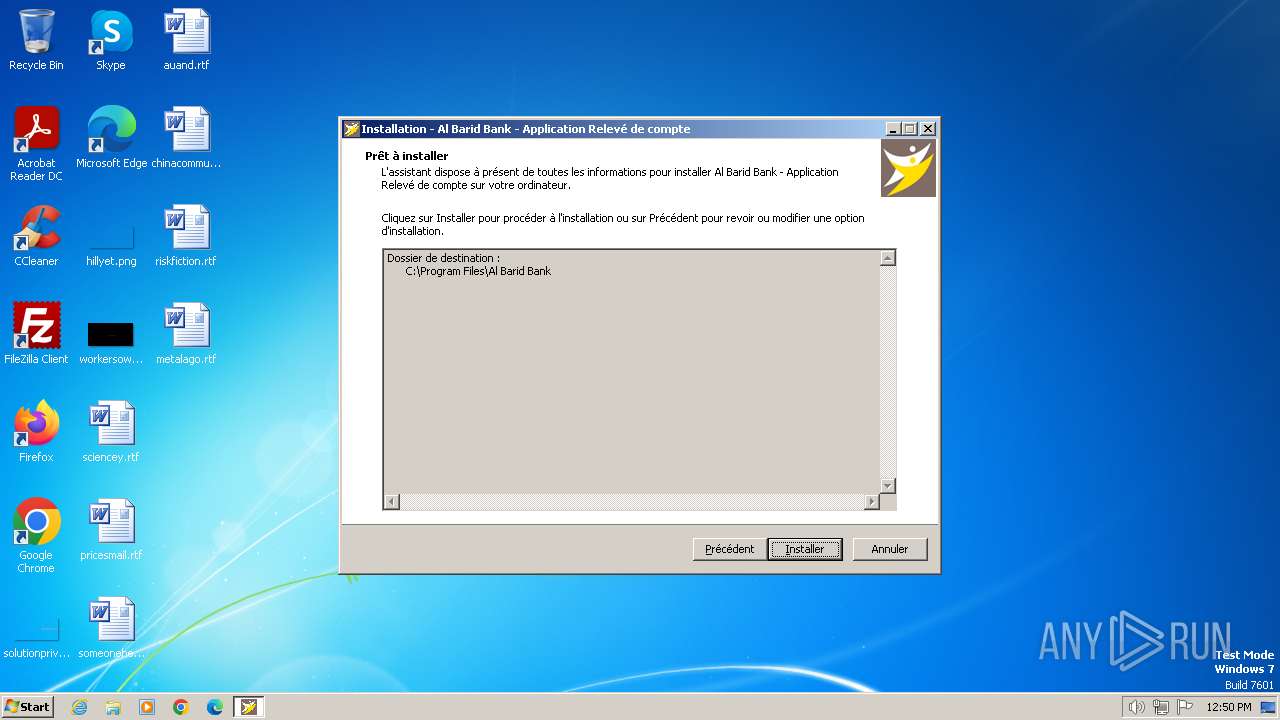
| File name: | Al Barid Bank Relevé de compte_Setup.exe |
| Full analysis: | https://app.any.run/tasks/e248152a-5adc-429b-9737-118509085104 |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2024, 11:49:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 95A5A5117656C75F3F9B679936255EE1 |
| SHA1: | D52E1FE99B9E9F03D85996476FEE404E013044D5 |
| SHA256: | 241BDE54C54268F4D3398F2B8D8C501EB50D11BDF3F72F39F137B4379EEED92D |
| SSDEEP: | 98304:m+cD4dnm0QhcpjdPokcVAcegYnzJaSLWu22l2+UDNm5E2ERHeTsxRbMuxhGstKVV:ZK4KoCit |
MALICIOUS
Drops the executable file immediately after the start
- Al Barid Bank Relevé de compte_Setup.exe (PID: 2260)
- Al Barid Bank Relevé de compte_Setup.exe (PID: 2088)
- Al Barid Bank Relevé de compte_Setup.tmp (PID: 3448)
- admin_microsoft_account.exe (PID: 3736)
Bypass execution policy to execute commands
- powershell.exe (PID: 2552)
- powershell.exe (PID: 4080)
Adds path to the Windows Defender exclusion list
- Al Barid Bank Relevé de compte_Setup.tmp (PID: 3448)
- admin_microsoft_account.exe (PID: 3736)
Changes powershell execution policy (Bypass)
- Al Barid Bank Relevé de compte_Setup.tmp (PID: 3448)
- admin_microsoft_account.exe (PID: 3736)
Uses Task Scheduler to run other applications
- admin_microsoft_account.exe (PID: 3736)
UAC/LUA settings modification
- reg.exe (PID: 2156)
Changes the autorun value in the registry
- admin_microsoft_account.exe (PID: 3736)
SUSPICIOUS
Executable content was dropped or overwritten
- Al Barid Bank Relevé de compte_Setup.exe (PID: 2260)
- Al Barid Bank Relevé de compte_Setup.exe (PID: 2088)
- Al Barid Bank Relevé de compte_Setup.tmp (PID: 3448)
- admin_microsoft_account.exe (PID: 3736)
Reads the Windows owner or organization settings
- Al Barid Bank Relevé de compte_Setup.tmp (PID: 3448)
Starts POWERSHELL.EXE for commands execution
- Al Barid Bank Relevé de compte_Setup.tmp (PID: 3448)
- admin_microsoft_account.exe (PID: 3736)
Script adds exclusion path to Windows Defender
- Al Barid Bank Relevé de compte_Setup.tmp (PID: 3448)
- admin_microsoft_account.exe (PID: 3736)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 2552)
- powershell.exe (PID: 4080)
Reads the Internet Settings
- powershell.exe (PID: 2552)
- powershell.exe (PID: 4080)
Starts CMD.EXE for commands execution
- Al Barid Bank Relevé de compte_Setup.tmp (PID: 3448)
The process executes via Task Scheduler
- admin_microsoft_account.exe (PID: 3748)
The process drops C-runtime libraries
- admin_microsoft_account.exe (PID: 3736)
Process drops legitimate windows executable
- admin_microsoft_account.exe (PID: 3736)
Uses TASKKILL.EXE to kill process
- admin_microsoft_account.exe (PID: 3736)
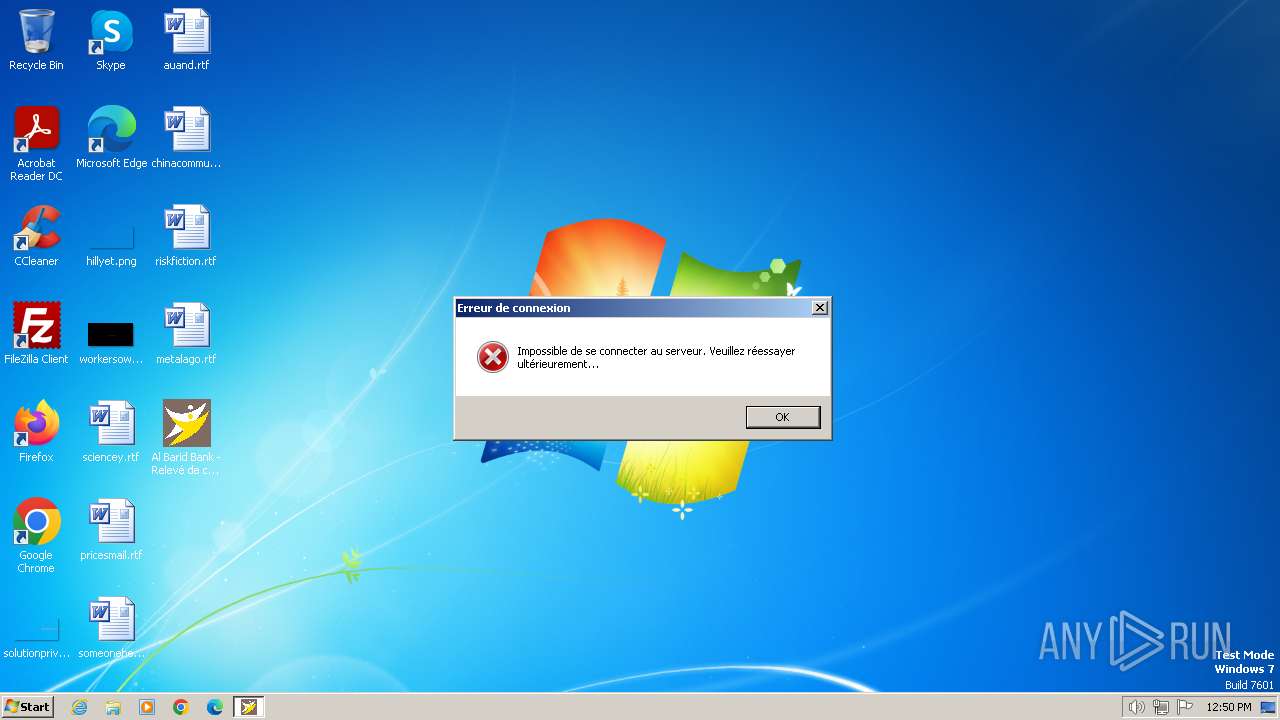
Connects to unusual port
- AlBaridBank_Relevé.exe (PID: 3672)
- admin_microsoft_account.exe (PID: 3736)
- Al Barid Bank - Relevé de compte.exe (PID: 2136)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 1060)
Uses REG/REGEDIT.EXE to modify registry
- admin_microsoft_account.exe (PID: 3736)
INFO
Checks supported languages
- Al Barid Bank Relevé de compte_Setup.exe (PID: 2260)
- Al Barid Bank Relevé de compte_Setup.tmp (PID: 536)
- Al Barid Bank Relevé de compte_Setup.exe (PID: 2088)
- Al Barid Bank Relevé de compte_Setup.tmp (PID: 3448)
- admin_microsoft_account.exe (PID: 3736)
- wmpnscfg.exe (PID: 2632)
- admin_microsoft_account.exe (PID: 3748)
- AlBaridBank_Relevé.exe (PID: 3672)
- Al Barid Bank - Relevé de compte.exe (PID: 2136)
Reads the computer name
- Al Barid Bank Relevé de compte_Setup.tmp (PID: 536)
- Al Barid Bank Relevé de compte_Setup.tmp (PID: 3448)
- wmpnscfg.exe (PID: 2632)
- admin_microsoft_account.exe (PID: 3736)
- AlBaridBank_Relevé.exe (PID: 3672)
- Al Barid Bank - Relevé de compte.exe (PID: 2136)
Create files in a temporary directory
- Al Barid Bank Relevé de compte_Setup.exe (PID: 2260)
- Al Barid Bank Relevé de compte_Setup.exe (PID: 2088)
- Al Barid Bank Relevé de compte_Setup.tmp (PID: 3448)
Manual execution by a user
- wmpnscfg.exe (PID: 2632)
- Al Barid Bank - Relevé de compte.exe (PID: 2136)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2552)
- powershell.exe (PID: 4080)
Creates a software uninstall entry
- Al Barid Bank Relevé de compte_Setup.tmp (PID: 3448)
Creates files in the program directory
- Al Barid Bank Relevé de compte_Setup.tmp (PID: 3448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (65.1) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (24.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.9) |
| .exe | | | Win32 Executable (generic) (2.6) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 52224 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Al Barid Bank |
| FileDescription: | Al Barid Bank - Application Relevé de compte Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Al Barid Bank - Application Relevé de compte |
| ProductVersion: |
Total processes
64
Monitored processes
17
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\Users\admin\AppData\Local\Temp\is-KMGDT.tmp\Al Barid Bank Relevé de compte_Setup.tmp" /SL5="$30214,3687585,795136,C:\Users\admin\AppData\Local\Temp\Al Barid Bank Relevé de compte_Setup.exe" | C:\Users\admin\AppData\Local\Temp\is-KMGDT.tmp\Al Barid Bank Relevé de compte_Setup.tmp | — | Al Barid Bank Relevé de compte_Setup.exe | |||||||||||
User: admin Company: Al Barid Bank Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1060 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1076 | "taskkill" /f /im securitysvc.exe | C:\Windows\System32\taskkill.exe | — | admin_microsoft_account.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2088 | "C:\Users\admin\AppData\Local\Temp\Al Barid Bank Relevé de compte_Setup.exe" /SPAWNWND=$D016C /NOTIFYWND=$30214 | C:\Users\admin\AppData\Local\Temp\Al Barid Bank Relevé de compte_Setup.exe | Al Barid Bank Relevé de compte_Setup.tmp | ||||||||||||
User: admin Company: Al Barid Bank Integrity Level: HIGH Description: Al Barid Bank - Application Relevé de compte Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2136 | "C:\Users\admin\Desktop\Al Barid Bank - Relevé de compte.exe" | C:\Users\admin\Desktop\Al Barid Bank - Relevé de compte.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2156 | "REG" ADD HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | admin_microsoft_account.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2260 | "C:\Users\admin\AppData\Local\Temp\Al Barid Bank Relevé de compte_Setup.exe" | C:\Users\admin\AppData\Local\Temp\Al Barid Bank Relevé de compte_Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Al Barid Bank Integrity Level: MEDIUM Description: Al Barid Bank - Application Relevé de compte Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2552 | "powershell" -ex bypass -C "Add-MpPreference -ExclusionPath 'C:\Windows\Security\updateagent','c:','d:','e:','f:','g:','h:','i:'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Al Barid Bank Relevé de compte_Setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2632 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3260 | "cmd.exe" /c mklink /h "C:\Users\admin\Desktop\Al Barid Bank - Relevé de compte.exe" "C:\Program Files\Al Barid Bank\AlBaridBank_Relevé.exe" | C:\Windows\System32\cmd.exe | — | Al Barid Bank Relevé de compte_Setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
7 955
Read events
7 851
Write events
98
Delete events
6
Modification events
| (PID) Process: | (3448) Al Barid Bank Relevé de compte_Setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 780D0000B64D8B1C89E9DA01 | |||
| (PID) Process: | (3448) Al Barid Bank Relevé de compte_Setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: CE709383BD970BAE23833272983F06D3E2A6A6C3340C04C5A0B6B59E96C1A9FB | |||
| (PID) Process: | (3448) Al Barid Bank Relevé de compte_Setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2552) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2552) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2552) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2552) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1060) svchost.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\SystemCertificates\AuthRoot\AutoUpdate |
| Operation: | write | Name: | DisallowedCertLastSyncTime |
Value: 7229492689E9DA01 | |||
| (PID) Process: | (3448) Al Barid Bank Relevé de compte_Setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\Al Barid Bank\AlBaridBank_Relevé.exe | |||
| (PID) Process: | (3448) Al Barid Bank Relevé de compte_Setup.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 1097E513B566A0406EA925168A23E432EC07F5DF5BDA9524F209DA8AC9E330E4 | |||
Executable files
11
Suspicious files
10
Text files
2
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2552 | powershell.exe | C:\Users\admin\AppData\Local\Temp\404uwrkq.u1u.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3448 | Al Barid Bank Relevé de compte_Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-RDOL3.tmp\_isetup\_iscrypt.dll | executable | |
MD5:A69559718AB506675E907FE49DEB71E9 | SHA256:2F6294F9AA09F59A574B5DCD33BE54E16B39377984F3D5658CDA44950FA0F8FC | |||
| 2552 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ufsho0vy.5ih.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1060 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\Tar6935.tmp | cat | |
MD5:78785956AB4E54D6116D673C3491EDFF | SHA256:C514DBDBB13632CBB378C59086C1EBB0BC9B25FFB0A349F2B052B065C0D913E6 | |||
| 1060 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\Cab6934.tmp | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2552 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | dbf | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 3448 | Al Barid Bank Relevé de compte_Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-RDOL3.tmp\agent.exe | executable | |
MD5:4C168C3E04B0C0F73ABB3FA2A2A95104 | SHA256:9D28AB1200BA8C2B2C80C56AEB4FA0D57E1999BACB58532D141D93906752AC8A | |||
| 3448 | Al Barid Bank Relevé de compte_Setup.tmp | C:\Program Files\Al Barid Bank\unins000.exe | executable | |
MD5:DFBCA5D052F104BBF4DE4B2E1A0E47E1 | SHA256:60A0C146278A70C175BE0C42AF374B91F649F3530DD50164CE4F756EFE99AB55 | |||
| 3448 | Al Barid Bank Relevé de compte_Setup.tmp | C:\Windows\security\updateagent\admin_microsoft_account.exe | executable | |
MD5:4C168C3E04B0C0F73ABB3FA2A2A95104 | SHA256:9D28AB1200BA8C2B2C80C56AEB4FA0D57E1999BACB58532D141D93906752AC8A | |||
| 3448 | Al Barid Bank Relevé de compte_Setup.tmp | C:\Program Files\Al Barid Bank\AlBaridBank_Relevé.exe | executable | |
MD5:E20F08657989DBE260EAE2428447A20F | SHA256:1F8DB92E2C3238D13C3E361F6CC4DD3FB895D84AFD6BB9B28635BFF9DED4BA42 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
19
DNS requests
7
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8f69642324cc87bd | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1372 | svchost.exe | 23.50.131.200:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
albaridbank.freedynamicdns.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.freedynamicdns .org |
2 ETPRO signatures available at the full report