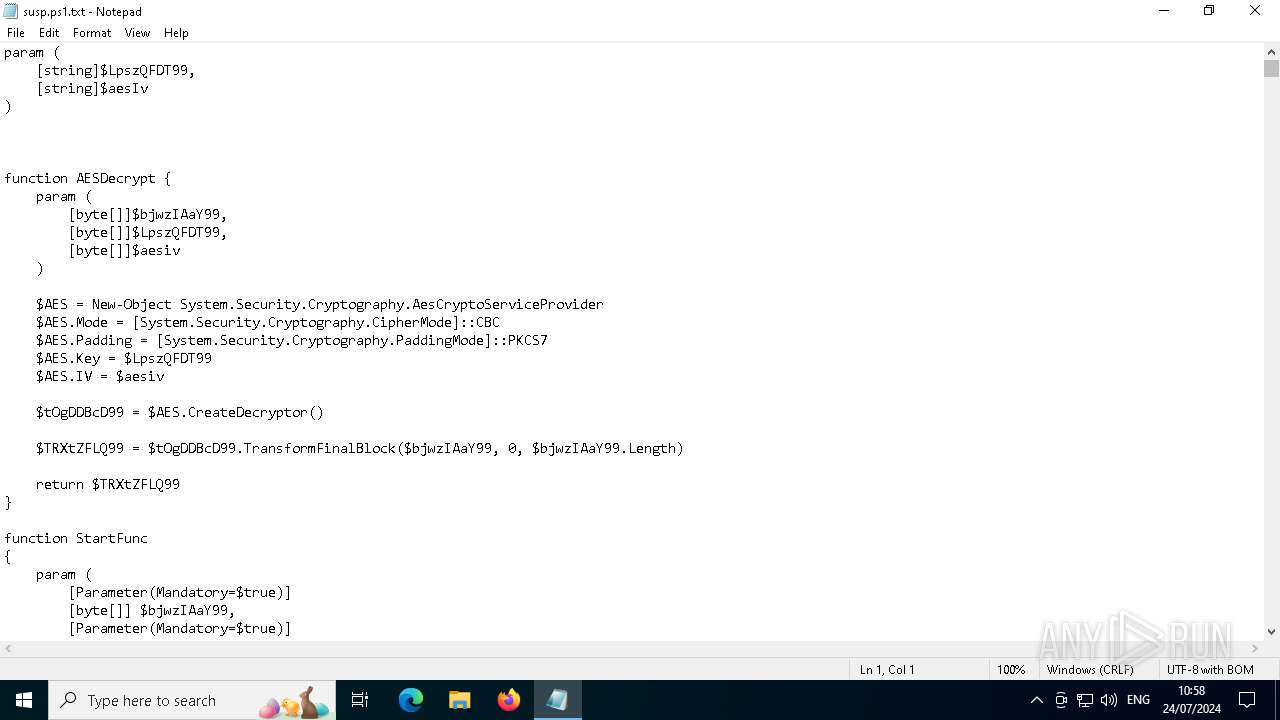
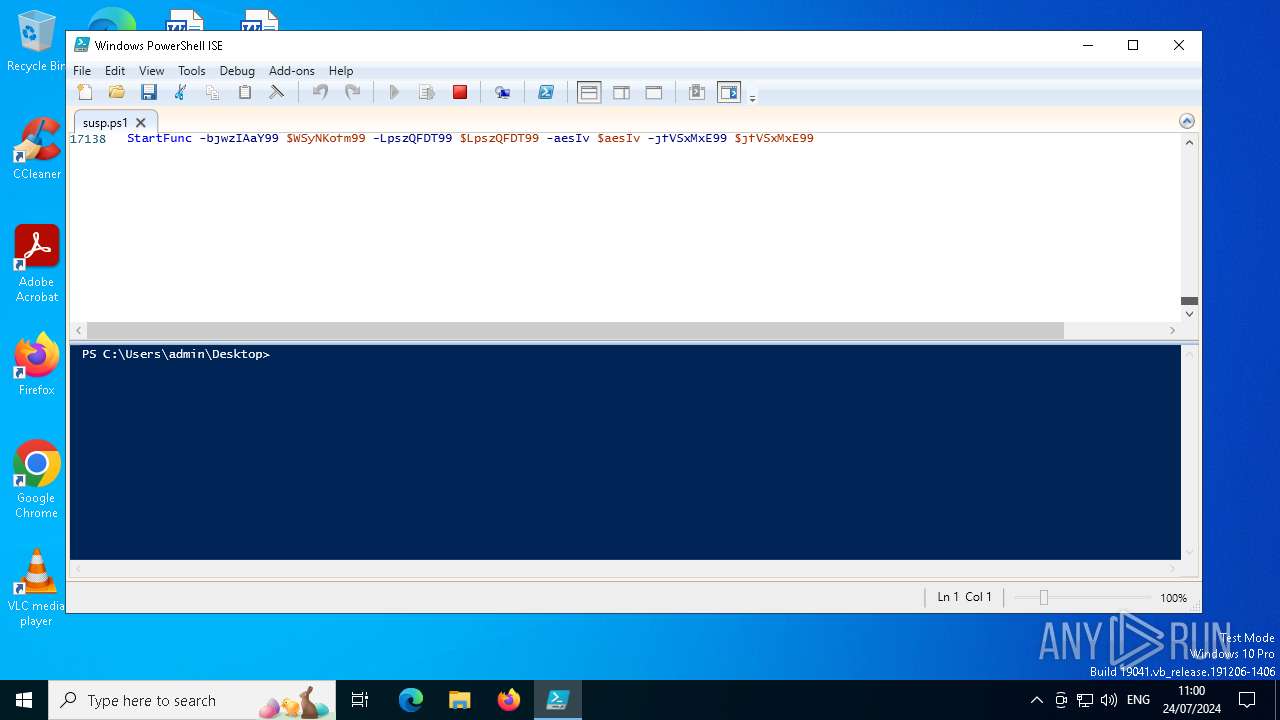
| File name: | susp.ps1 |
| Full analysis: | https://app.any.run/tasks/99ad902c-9d0e-48b0-b298-0546ac793e8a |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2024, 09:58:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 (with BOM) text, with CRLF line terminators |
| MD5: | FC11D5A9E8C047FE9D7E22797B15F461 |
| SHA1: | 0269D42CC98669955F0306D531E87130D4D06B12 |
| SHA256: | 241719892A747862CA98F44BBE4B22336FABBAFE0CAE7E3A8B30D2A9290C48DE |
| SSDEEP: | 12288:a/tJK3GrvlbSmDi0jNvhRScyjcZX65HSrsQhpAvH8dmqHBxTP:y |
MALICIOUS
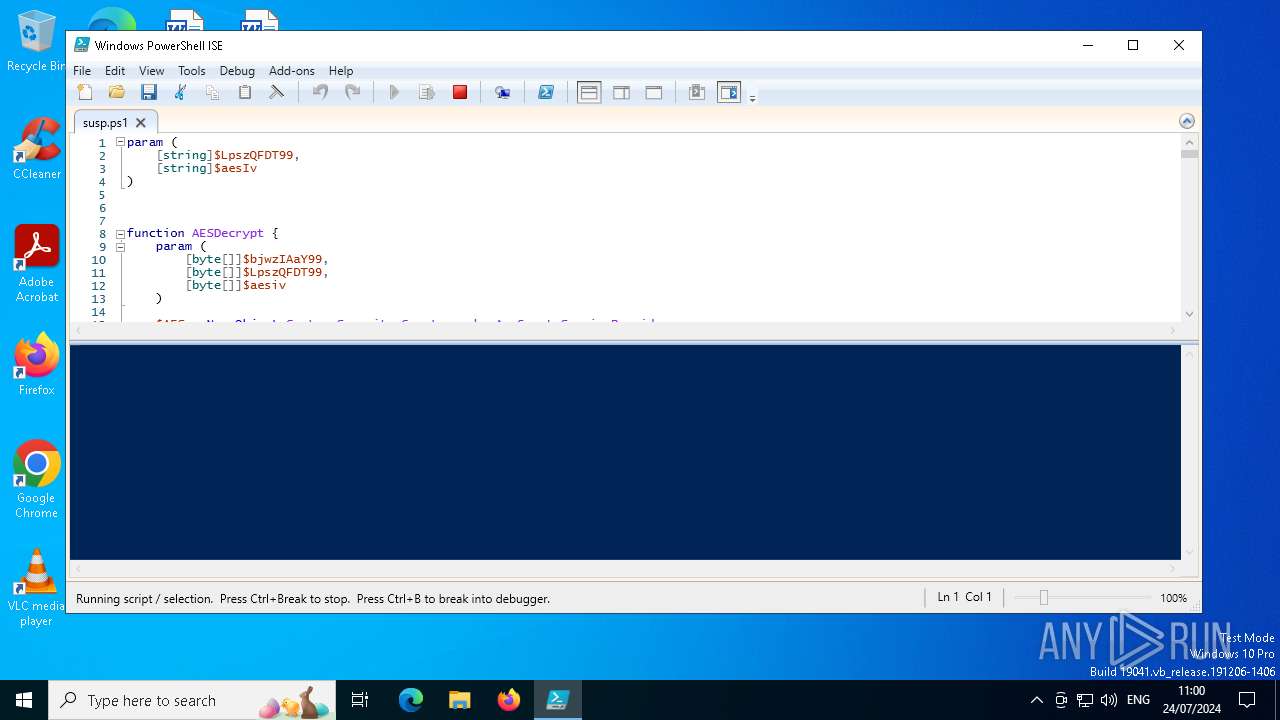
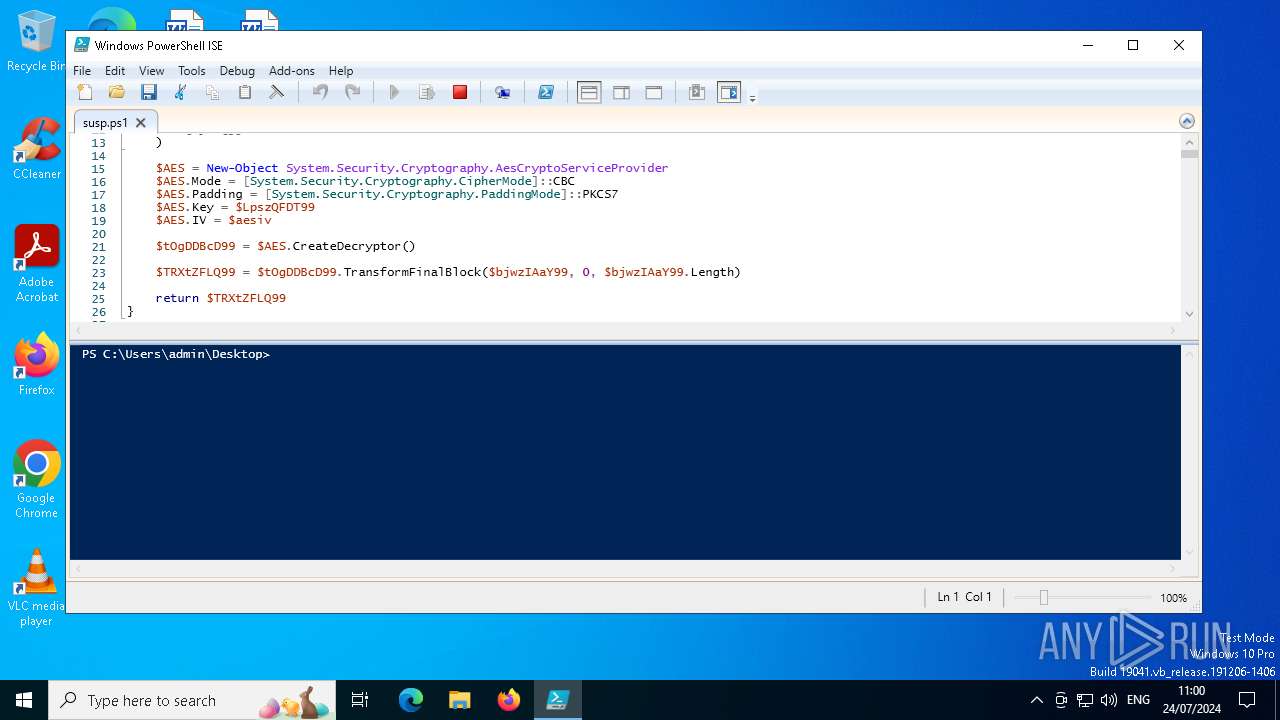
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 1252)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 1252)
Bypass execution policy to execute commands
- powershell.exe (PID: 1252)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 1252)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 1252)
SUSPICIOUS
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 1252)
Converts a string into array of characters (POWERSHELL)
- powershell.exe (PID: 1252)
INFO
Reads the computer name
- TextInputHost.exe (PID: 7096)
Reads security settings of Internet Explorer
- notepad.exe (PID: 5960)
- certutil.exe (PID: 4044)
Gets data length (POWERSHELL)
- powershell.exe (PID: 1252)
Manual execution by a user
- powershell.exe (PID: 1252)
- powershell_ise.exe (PID: 2256)
Checks supported languages
- TextInputHost.exe (PID: 7096)
Checks proxy server information
- certutil.exe (PID: 4044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-8 encoded (100) |
|---|
Total processes
129
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1252 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\Desktop\susp.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 2256 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe" "C:\Users\admin\Desktop\susp.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell ISE Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 4044 | C:\Windows\System32\certutil.exe | C:\Windows\System32\certutil.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 5052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 5304 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 5960 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\susp.ps1.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7096 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
Total events
47
Read events
47
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
6
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1252 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0upjt1l5.oum.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2256 | powershell_ise.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_spugfqar.3of.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1252 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RFe7ab9.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 1252 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mqkj24ni.gjz.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1252 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:F08B89D583626E198E95C0C9E7C12856 | SHA256:7DB5B5C505C30DCDE21C78D9A3C04586904C0B62BBBCB73AD316B5A4756E4098 | |||
| 2256 | powershell_ise.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_k2cghuvn.q0a.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2256 | powershell_ise.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FB64A9EBEDF48D3895381D5B7D80743D | SHA256:EA21D495930AD76F267A33A0F593DBF0C7EA75E457FCAE49A29DAAD8BD920F42 | |||
| 2256 | powershell_ise.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fsiqdz5q.2rf.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2256 | powershell_ise.exe | C:\Users\admin\AppData\Local\Microsoft_Corporation\powershell_ise.exe_StrongName_lw2v2vm3wmtzzpebq33gybmeoxukb04w\3.0.0.0\fnvylmis.newcfg | xml | |
MD5:528B41A963F374FFD257A706613A9712 | SHA256:B7146B989803CA62EB796DE31DF82C0CB6915AC103FF7C871C8AE194CB979C9B | |||
| 2256 | powershell_ise.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_iavjjwmm.co1.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
19
DNS requests
30
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | — | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
— | — | POST | 401 | 4.209.33.156:443 | https://licensing.mp.microsoft.com/v7.0/licenses/content | unknown | binary | 340 b | unknown |
— | — | POST | 200 | 20.44.10.122:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4288 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3380 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 92.123.104.6:443 | — | Akamai International B.V. | DE | unknown |
6012 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4204 | svchost.exe | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3380 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
licensing.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
haileigh-oakes.com |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |