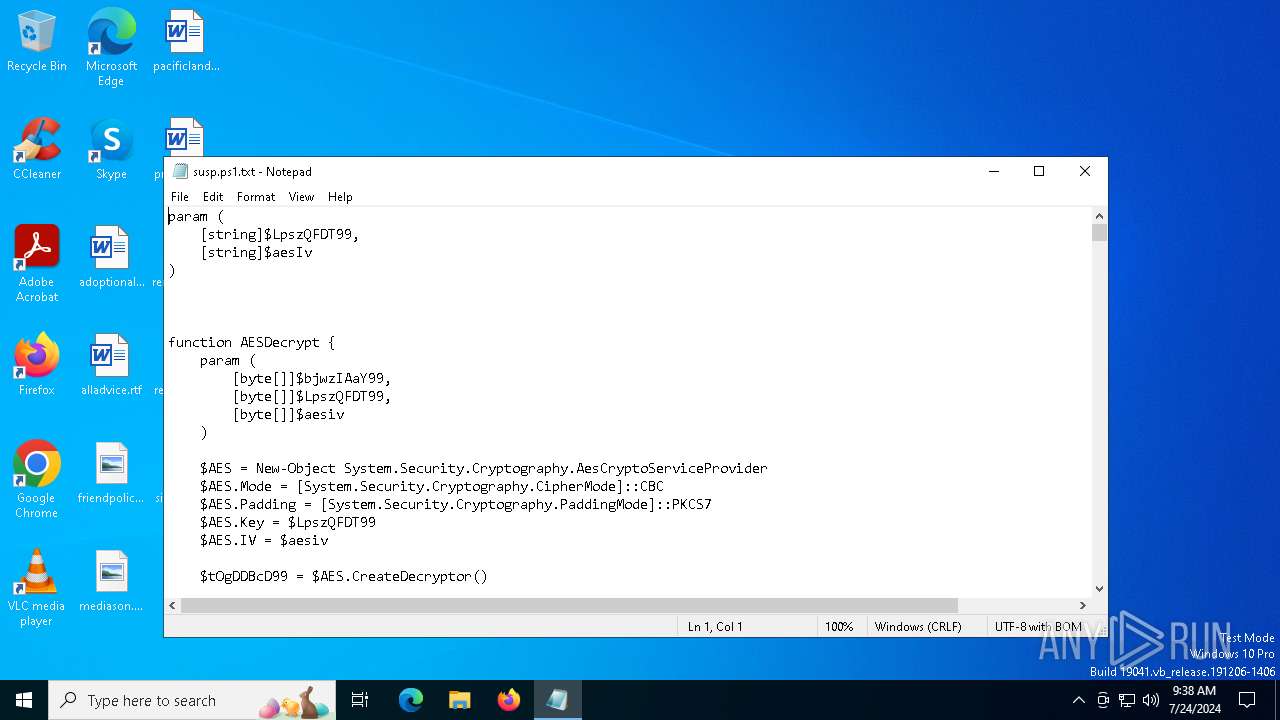
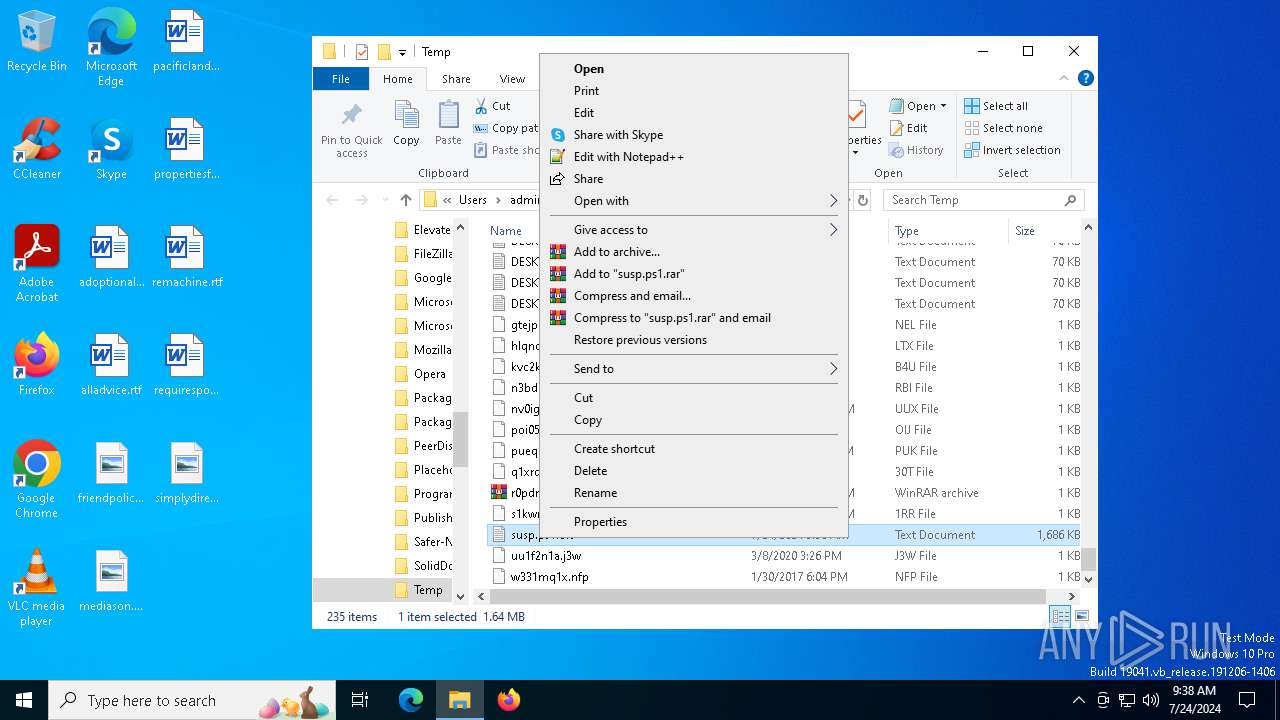
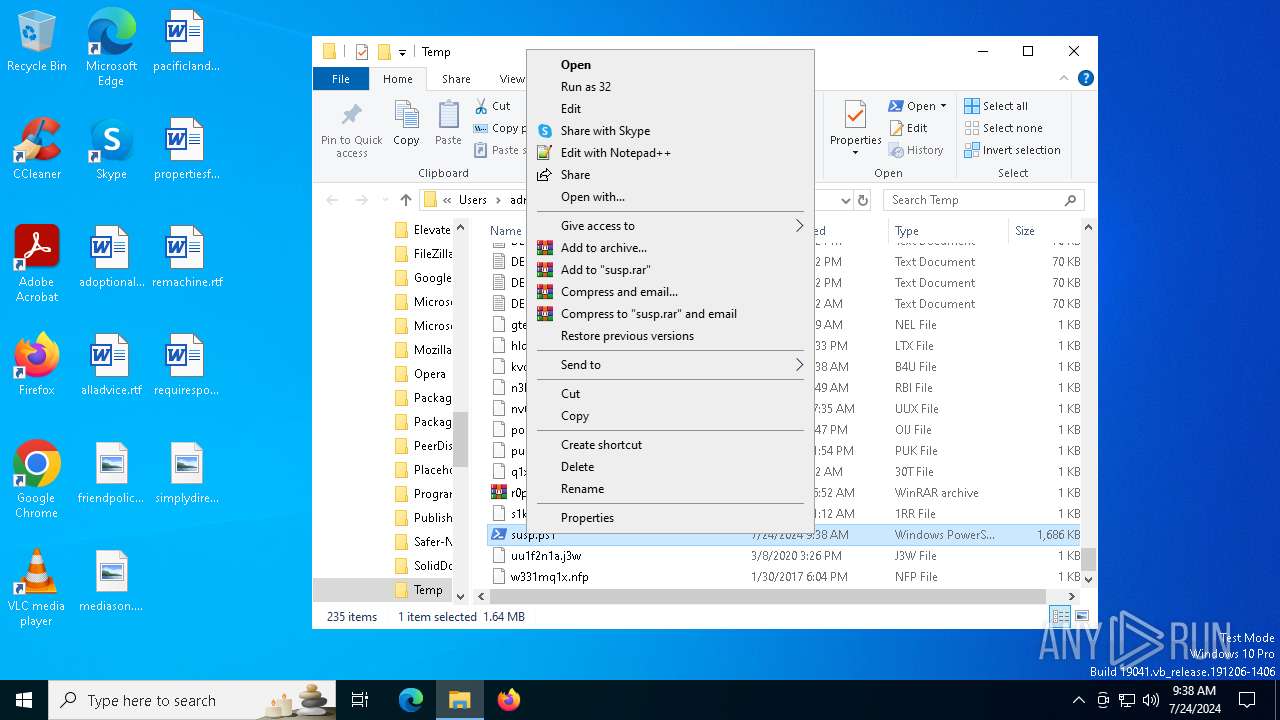
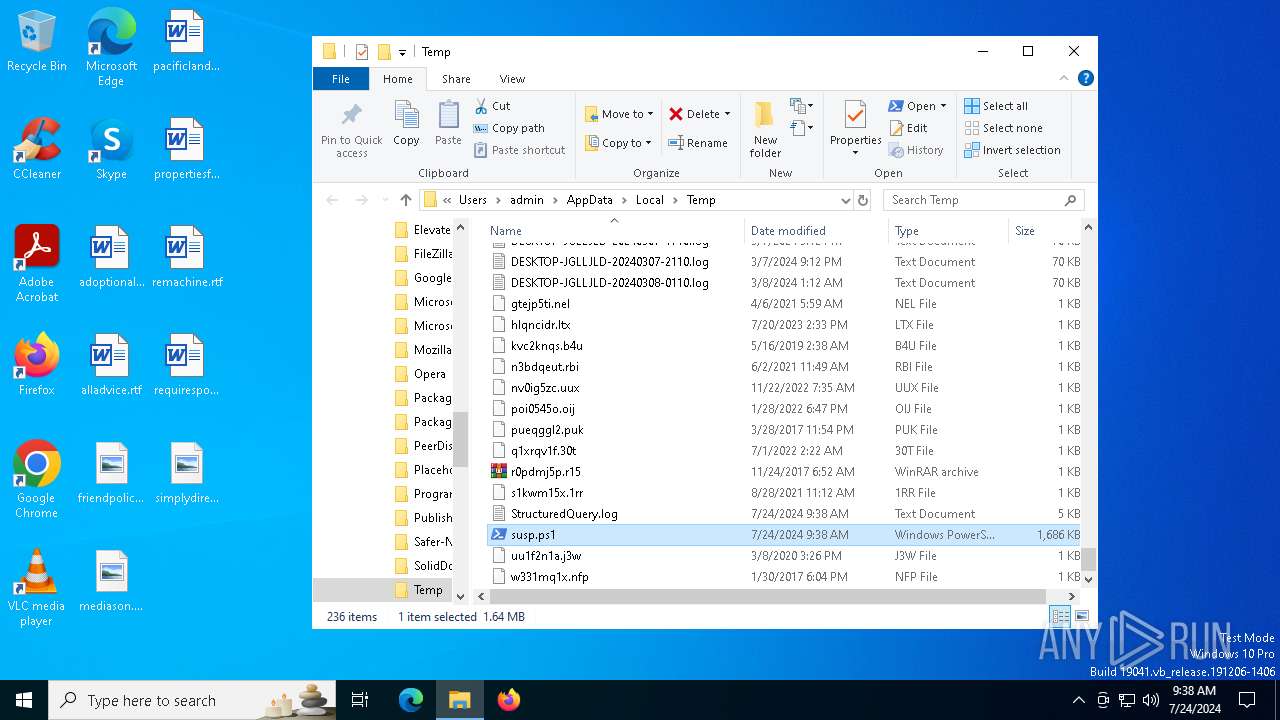
| File name: | susp.ps1 |
| Full analysis: | https://app.any.run/tasks/9956d7dd-ebab-49e2-b6a1-24df15634fca |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2024, 09:38:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 (with BOM) text, with CRLF line terminators |
| MD5: | FC11D5A9E8C047FE9D7E22797B15F461 |
| SHA1: | 0269D42CC98669955F0306D531E87130D4D06B12 |
| SHA256: | 241719892A747862CA98F44BBE4B22336FABBAFE0CAE7E3A8B30D2A9290C48DE |
| SSDEEP: | 12288:a/tJK3GrvlbSmDi0jNvhRScyjcZX65HSrsQhpAvH8dmqHBxTP:y |
MALICIOUS
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 7072)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 7072)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 7072)
Bypass execution policy to execute commands
- powershell.exe (PID: 7072)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 7072)
SUSPICIOUS
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7072)
Converts a string into array of characters (POWERSHELL)
- powershell.exe (PID: 7072)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 1328)
- certutil.exe (PID: 4932)
Checks supported languages
- TextInputHost.exe (PID: 4452)
Manual execution by a user
- powershell.exe (PID: 7072)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7072)
Reads the computer name
- TextInputHost.exe (PID: 4452)
Checks proxy server information
- certutil.exe (PID: 4932)
- slui.exe (PID: 1992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-8 encoded (100) |
|---|
Total processes
145
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | ||
|---|---|---|---|---|---|---|
| 1328 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\susp.ps1.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | ||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||||
| 1992 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | |||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||||
| 4052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | ||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||||
| 4452 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | ||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| ||||||
| 4932 | C:\Windows\System32\certutil.exe | C:\Windows\System32\certutil.exe | — | powershell.exe | ||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||||
| 5004 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certutil.exe | ||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||||
| 7008 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | ||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||||
| 7072 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\AppData\Local\Temp\susp.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | ||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||||
Total events
23
Read events
23
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
4
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7072 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RFe781a.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 7072 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kkbiph0h.v2d.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7072 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:EAD53ABD84C8983D0C21F18B3A581367 | SHA256:C814C5413D378225AF8C5687AB4DC34D81E2ABD16236DB1DE345A686DC139CE0 | |||
| 7072 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\5N8G7QYHOJXWCZEX4NSI.temp | binary | |
MD5:6EDF634E1B220714AFD58C0FC968B06C | SHA256:BADCEC8940E254C6DB781BA6931B8BBB9C70B3C1CFF13ACA028D62ACB0D8D455 | |||
| 7072 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ybip1uyr.0mx.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7072 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:6EDF634E1B220714AFD58C0FC968B06C | SHA256:BADCEC8940E254C6DB781BA6931B8BBB9C70B3C1CFF13ACA028D62ACB0D8D455 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
57
DNS requests
61
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6196 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
512 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3212 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3008 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4204 | svchost.exe | 4.208.221.206:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5368 | SearchApp.exe | 92.123.104.63:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5368 | SearchApp.exe | 92.123.104.65:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5368 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
s-ring.msedge.net |
| unknown |
fp-afd.azureedge.us |
| unknown |
61c7815e16e8b33b698eac69583ec7de.clo.footprintdns.com |
| whitelisted |