| File name: | UltraSearch-Setup.exe |
| Full analysis: | https://app.any.run/tasks/063f0c26-a9ef-4367-bdb3-caad8cc3e467 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 20:11:50 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | B26D0F9227D869C7DD4B2DE138313192 |
| SHA1: | C4FEC320A907154115C946D340745E3F92446B07 |
| SHA256: | 240F91F6AD0457390B477AB23C4A2CAC077B0AA816D2020C76D140647ABD4430 |
| SSDEEP: | 98304:Mrq3Bdwen2yFS/qoM0YpdJH/tc+gM8+3YXw80N+d91AjdJCSJE/S2JU2CaoM+vio:uO1P6oLMqzLlPZVKR0wn0tZcXMncClzR |
MALICIOUS
Adds process to the Windows Defender exclusion list
- UltraSearch-Setup.tmp (PID: 7052)
- powershell.exe (PID: 6768)
Changes powershell execution policy (Bypass)
- UltraSearch-Setup.tmp (PID: 7052)
- powershell.exe (PID: 6768)
Changes Windows Defender settings
- UltraSearch-Setup.tmp (PID: 7052)
- powershell.exe (PID: 6768)
Bypass execution policy to execute commands
- powershell.exe (PID: 6768)
- powershell.exe (PID: 5384)
Create files in the Startup directory
- UltraSearch.exe (PID: 900)
SUSPICIOUS
Executable content was dropped or overwritten
- UltraSearch-Setup.exe (PID: 1280)
- UltraSearch-Setup.exe (PID: 1452)
- UltraSearch-Setup.tmp (PID: 7052)
Reads security settings of Internet Explorer
- UltraSearch-Setup.tmp (PID: 4988)
- UltraSearch.exe (PID: 5756)
- UltraSearch.exe (PID: 4784)
- UltraSearch.exe (PID: 900)
- UltraSearch.exe (PID: 1088)
- UltraSearch.exe (PID: 2240)
Reads the Windows owner or organization settings
- UltraSearch-Setup.tmp (PID: 7052)
Script adds exclusion process to Windows Defender
- UltraSearch-Setup.tmp (PID: 7052)
- powershell.exe (PID: 6768)
Starts POWERSHELL.EXE for commands execution
- UltraSearch-Setup.tmp (PID: 7052)
- powershell.exe (PID: 6768)
Process drops legitimate windows executable
- UltraSearch-Setup.tmp (PID: 7052)
Application launched itself
- powershell.exe (PID: 6768)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 6768)
Adds/modifies Windows certificates
- UltraSearch.exe (PID: 5756)
- powershell.exe (PID: 5384)
Starts process via Powershell
- powershell.exe (PID: 6768)
Reads Internet Explorer settings
- hh.exe (PID: 2984)
Reads Microsoft Outlook installation path
- hh.exe (PID: 2984)
There is functionality for taking screenshot (YARA)
- UltraSearch.exe (PID: 2240)
There is functionality for communication over UDP network (YARA)
- UltraSearch.exe (PID: 2240)
INFO
Create files in a temporary directory
- UltraSearch-Setup.exe (PID: 1280)
- UltraSearch-Setup.exe (PID: 1452)
- UltraSearch-Setup.tmp (PID: 7052)
- LicenseManager.exe (PID: 3240)
- UltraSearch.exe (PID: 5756)
- UltraSearch.exe (PID: 4784)
- UltraSearch.exe (PID: 1088)
- UltraSearch.exe (PID: 900)
- hh.exe (PID: 2984)
- UltraSearch.exe (PID: 2240)
Checks supported languages
- UltraSearch-Setup.exe (PID: 1280)
- UltraSearch-Setup.tmp (PID: 4988)
- UltraSearch-Setup.tmp (PID: 7052)
- UltraSearch-Setup.exe (PID: 1452)
- LicenseManager.exe (PID: 3240)
- LicenseManager.exe (PID: 3268)
- UltraSearch.exe (PID: 5756)
- UltraSearch.exe (PID: 900)
- UltraSearch.exe (PID: 1088)
- UltraSearch.exe (PID: 4784)
- UltraSearch.exe (PID: 2240)
Reads the computer name
- UltraSearch-Setup.tmp (PID: 4988)
- UltraSearch-Setup.exe (PID: 1452)
- UltraSearch-Setup.tmp (PID: 7052)
- LicenseManager.exe (PID: 3240)
- LicenseManager.exe (PID: 3268)
- UltraSearch.exe (PID: 5756)
- UltraSearch.exe (PID: 1088)
- UltraSearch.exe (PID: 4784)
- UltraSearch.exe (PID: 900)
- UltraSearch.exe (PID: 2240)
Process checks computer location settings
- UltraSearch-Setup.tmp (PID: 4988)
Reads Environment values
- UltraSearch-Setup.tmp (PID: 7052)
- UltraSearch.exe (PID: 5756)
- UltraSearch.exe (PID: 900)
- UltraSearch.exe (PID: 4784)
- UltraSearch.exe (PID: 1088)
- UltraSearch.exe (PID: 2240)
Compiled with Borland Delphi (YARA)
- UltraSearch-Setup.exe (PID: 1280)
- UltraSearch-Setup.tmp (PID: 4988)
- UltraSearch-Setup.exe (PID: 1452)
- UltraSearch-Setup.tmp (PID: 7052)
- UltraSearch.exe (PID: 2240)
Detects InnoSetup installer (YARA)
- UltraSearch-Setup.exe (PID: 1280)
- UltraSearch-Setup.tmp (PID: 4988)
- UltraSearch-Setup.exe (PID: 1452)
- UltraSearch-Setup.tmp (PID: 7052)
Reads the machine GUID from the registry
- LicenseManager.exe (PID: 3240)
- LicenseManager.exe (PID: 3268)
- UltraSearch.exe (PID: 5756)
- UltraSearch.exe (PID: 900)
- UltraSearch.exe (PID: 4784)
- UltraSearch.exe (PID: 1088)
- UltraSearch.exe (PID: 2240)
Creates files in the program directory
- LicenseManager.exe (PID: 3240)
- UltraSearch-Setup.tmp (PID: 7052)
Creates a software uninstall entry
- UltraSearch-Setup.tmp (PID: 7052)
Reads CPU info
- UltraSearch.exe (PID: 5756)
- UltraSearch.exe (PID: 1088)
- UltraSearch.exe (PID: 900)
- UltraSearch.exe (PID: 4784)
- UltraSearch.exe (PID: 2240)
The sample compiled with english language support
- UltraSearch-Setup.tmp (PID: 7052)
Reads the software policy settings
- UltraSearch.exe (PID: 5756)
- UltraSearch.exe (PID: 1088)
- UltraSearch.exe (PID: 4784)
- UltraSearch.exe (PID: 900)
- UltraSearch.exe (PID: 2240)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5384)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5384)
Auto-launch of the file from Startup directory
- UltraSearch.exe (PID: 900)
Creates files or folders in the user directory
- UltraSearch.exe (PID: 1088)
- UltraSearch.exe (PID: 900)
- hh.exe (PID: 2984)
Reads security settings of Internet Explorer
- hh.exe (PID: 2984)
Checks proxy server information
- hh.exe (PID: 2984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:06:28 08:29:25+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 685056 |
| InitializedDataSize: | 115712 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa83bc |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.7.0.1164 |
| ProductVersionNumber: | 4.7.0.1164 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
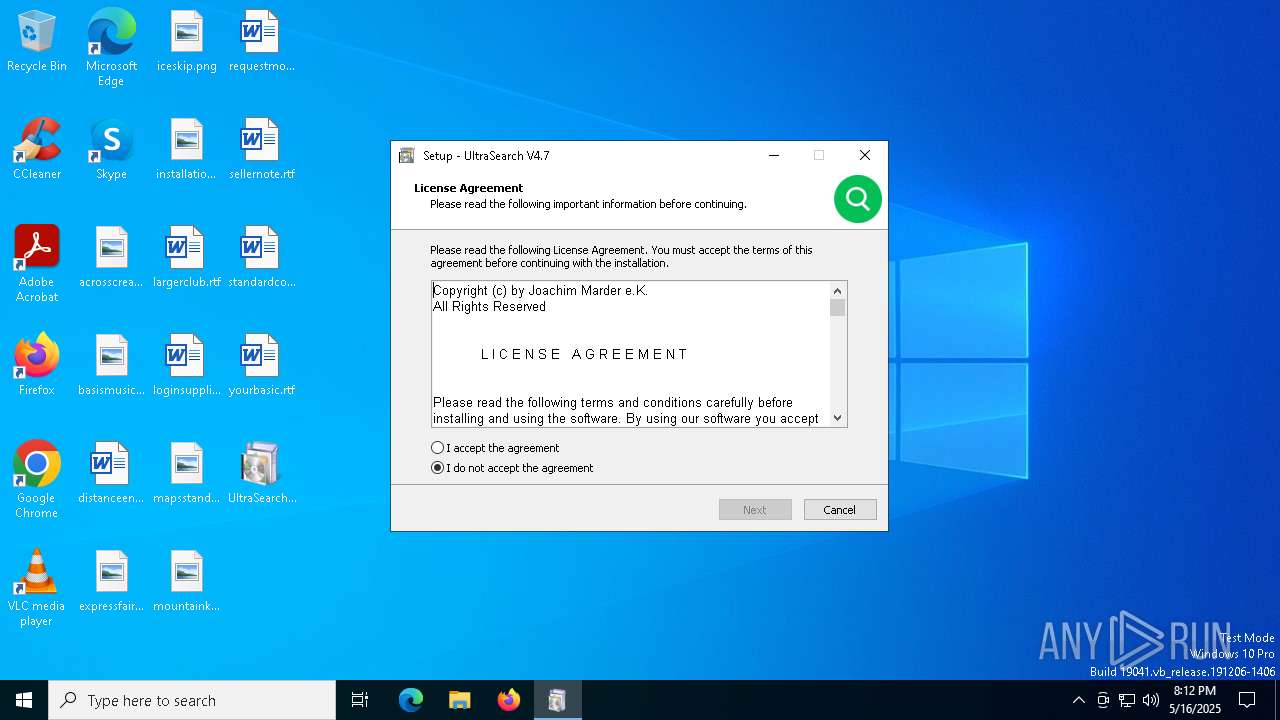
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | JAM Software |
| FileDescription: | UltraSearch Setup |
| FileVersion: | 4.7.0.1164 |
| LegalCopyright: | © 1996-2025 by Joachim Marder e.K. |
| OriginalFileName: | |
| ProductName: | UltraSearch |
| ProductVersion: | 4.7 |
Total processes
143
Monitored processes
16
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 900 | "C:\Program Files\JAM Software\UltraSearch\UltraSearch.exe" /NOGUI /NOTRAY /INSTALL /INSTALL_AUTOSTART /INSTALL_CONTEXTMENU | C:\Program Files\JAM Software\UltraSearch\UltraSearch.exe | UltraSearch-Setup.tmp | ||||||||||||
User: admin Company: JAM Software Integrity Level: MEDIUM Description: UltraSearch - Your Ultimate Tool For Ultra-Fast File Search Exit code: 0 Version: 4.7.0.1164 Modules
| |||||||||||||||
| 1088 | "C:\Program Files\JAM Software\UltraSearch\UltraSearch.exe" /NOGUI /NOTRAY /INSTALL /REGISTERPACKAGE /SAVESETTINGS /Language "en" | C:\Program Files\JAM Software\UltraSearch\UltraSearch.exe | — | UltraSearch-Setup.tmp | |||||||||||
User: admin Company: JAM Software Integrity Level: HIGH Description: UltraSearch - Your Ultimate Tool For Ultra-Fast File Search Exit code: 0 Version: 4.7.0.1164 Modules
| |||||||||||||||
| 1280 | "C:\Users\admin\Desktop\UltraSearch-Setup.exe" | C:\Users\admin\Desktop\UltraSearch-Setup.exe | explorer.exe | ||||||||||||
User: admin Company: JAM Software Integrity Level: MEDIUM Description: UltraSearch Setup Exit code: 0 Version: 4.7.0.1164 Modules
| |||||||||||||||
| 1452 | "C:\Users\admin\Desktop\UltraSearch-Setup.exe" /SPAWNWND=$4028A /NOTIFYWND=$80350 | C:\Users\admin\Desktop\UltraSearch-Setup.exe | UltraSearch-Setup.tmp | ||||||||||||
User: admin Company: JAM Software Integrity Level: HIGH Description: UltraSearch Setup Exit code: 0 Version: 4.7.0.1164 Modules
| |||||||||||||||
| 2240 | "C:\Program Files\JAM Software\UltraSearch\UltraSearch.exe" | C:\Program Files\JAM Software\UltraSearch\UltraSearch.exe | — | UltraSearch-Setup.tmp | |||||||||||
User: admin Company: JAM Software Integrity Level: MEDIUM Description: UltraSearch - Your Ultimate Tool For Ultra-Fast File Search Version: 4.7.0.1164 Modules
| |||||||||||||||
| 2984 | "C:\WINDOWS\hh.exe" C:\Program Files\JAM Software\UltraSearch\UltraSearch.chm | C:\Windows\hh.exe | — | UltraSearch-Setup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3240 | "C:\Users\admin\AppData\Local\Temp\is-4HNSS.tmp\LicenseManager.exe" license install --language en --useInnoSetupStyleDialog --dialogTitle " Setup - UltraSearch V4.7" --parentWindowIdentifier 459482 --suppressDialogs | C:\Users\admin\AppData\Local\Temp\is-4HNSS.tmp\LicenseManager.exe | — | UltraSearch-Setup.tmp | |||||||||||
User: admin Company: JAM Software Integrity Level: HIGH Description: LicenseManager Exit code: 0 Version: 5.1.2.173 Modules
| |||||||||||||||
| 3268 | "C:\Users\admin\AppData\Local\Temp\is-4HNSS.tmp\LicenseManager.exe" license getType | C:\Users\admin\AppData\Local\Temp\is-4HNSS.tmp\LicenseManager.exe | — | UltraSearch-Setup.tmp | |||||||||||
User: admin Company: JAM Software Integrity Level: HIGH Description: LicenseManager Exit code: 0 Version: 5.1.2.173 Modules
| |||||||||||||||
| 3304 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4784 | "C:\Program Files\JAM Software\UltraSearch\UltraSearch.exe" /NOGUI /NOTRAY /INSTALL /SL5="$6034A,19691664,801792,C:\Users\admin\Desktop\UltraSearch-Setup.exe" /SPAWNWND=$4028A /NOTIFYWND=$80350 | C:\Program Files\JAM Software\UltraSearch\UltraSearch.exe | — | UltraSearch-Setup.tmp | |||||||||||
User: admin Company: JAM Software Integrity Level: HIGH Description: UltraSearch - Your Ultimate Tool For Ultra-Fast File Search Exit code: 0 Version: 4.7.0.1164 Modules
| |||||||||||||||
Total events
45 807
Read events
45 723
Write events
60
Delete events
24
Modification events
| (PID) Process: | (3240) LicenseManager.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\EventLog\Application\Jam.License.Validation |
| Operation: | write | Name: | EventMessageFile |
Value: C:\Windows\Microsoft.NET\Framework64\v4.0.30319\EventLogMessages.dll | |||
| (PID) Process: | (7052) UltraSearch-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JAM Software\UltraSearch |
| Operation: | delete value | Name: | FullVersion |
Value: | |||
| (PID) Process: | (7052) UltraSearch-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JAM Software\UltraSearch |
| Operation: | write | Name: | FullVersion |
Value: 4.7 | |||
| (PID) Process: | (7052) UltraSearch-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\CodeGear\Locales |
| Operation: | write | Name: | C:\Program Files\JAM Software\UltraSearch\UltraSearch.exe |
Value: EN | |||
| (PID) Process: | (7052) UltraSearch-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\UltraSearch_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.3.2 | |||
| (PID) Process: | (7052) UltraSearch-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\UltraSearch_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\JAM Software\UltraSearch | |||
| (PID) Process: | (7052) UltraSearch-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\UltraSearch_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\JAM Software\UltraSearch\ | |||
| (PID) Process: | (7052) UltraSearch-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\UltraSearch_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: UltraSearch | |||
| (PID) Process: | (7052) UltraSearch-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\UltraSearch_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (7052) UltraSearch-Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\UltraSearch_is1 |
| Operation: | write | Name: | Inno Setup: Selected Tasks |
Value: desktopicon,desktopicon\common,shellcontextmenu,startmenu,autostartentry | |||
Executable files
22
Suspicious files
16
Text files
46
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7052 | UltraSearch-Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-4HNSS.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 1280 | UltraSearch-Setup.exe | C:\Users\admin\AppData\Local\Temp\is-R0P1R.tmp\UltraSearch-Setup.tmp | executable | |
MD5:89A098BF8393521F810FDDA2929B7F81 | SHA256:EFA01C87B67B861743FB2C07ED751E98EC2A1B734519DD73A05B729D15D62D2C | |||
| 1452 | UltraSearch-Setup.exe | C:\Users\admin\AppData\Local\Temp\is-4TKPQ.tmp\UltraSearch-Setup.tmp | executable | |
MD5:89A098BF8393521F810FDDA2929B7F81 | SHA256:EFA01C87B67B861743FB2C07ED751E98EC2A1B734519DD73A05B729D15D62D2C | |||
| 7052 | UltraSearch-Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-4HNSS.tmp\LicenseManager.exe | executable | |
MD5:967F81A2450F13F969255DD50C0AEBAA | SHA256:ECFCCAD10FA2C0567492BB20FFDC0E3657F86CDC5AA6572062D5863DBC0AA961 | |||
| 7052 | UltraSearch-Setup.tmp | C:\Program Files\JAM Software\UltraSearch\is-MG3CB.tmp | xml | |
MD5:EC0F31F8AF93BE5DB09EA45749E1A58B | SHA256:CF7AFF47F8F455A7AD8AA0A608DDBAB0225CF4BD3B26FEB0511C57E80F51B19D | |||
| 7052 | UltraSearch-Setup.tmp | C:\Program Files\JAM Software\UltraSearch\is-RS1DQ.tmp | text | |
MD5:8E037E19ADB723F0440520F750FF2EC3 | SHA256:105CBC0948A44C22F00D35E48F97EB79CD4D25C22C3A28CB75FC3D4BD944CBFC | |||
| 7052 | UltraSearch-Setup.tmp | C:\Program Files\JAM Software\UltraSearch\LicenseFiles\Inno Setup\LICENSE.txt | text | |
MD5:F960CFC0C8310C487633F5A0B945C987 | SHA256:D022EE9A38EA46EA445AD5370EE2B8AC75303D96A6FDBB30F50292F78A04D3D8 | |||
| 7052 | UltraSearch-Setup.tmp | C:\Program Files\JAM Software\UltraSearch\unins000.exe | executable | |
MD5:89A098BF8393521F810FDDA2929B7F81 | SHA256:EFA01C87B67B861743FB2C07ED751E98EC2A1B734519DD73A05B729D15D62D2C | |||
| 7052 | UltraSearch-Setup.tmp | C:\Program Files\JAM Software\UltraSearch\License.rtf | text | |
MD5:8E037E19ADB723F0440520F750FF2EC3 | SHA256:105CBC0948A44C22F00D35E48F97EB79CD4D25C22C3A28CB75FC3D4BD944CBFC | |||
| 7052 | UltraSearch-Setup.tmp | C:\Program Files\JAM Software\UltraSearch\LicenseFiles\Inno Setup\is-54ROE.tmp | text | |
MD5:F960CFC0C8310C487633F5A0B945C987 | SHA256:D022EE9A38EA46EA445AD5370EE2B8AC75303D96A6FDBB30F50292F78A04D3D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
23
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.48.23.181:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 23.48.23.181:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6620 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3304 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |