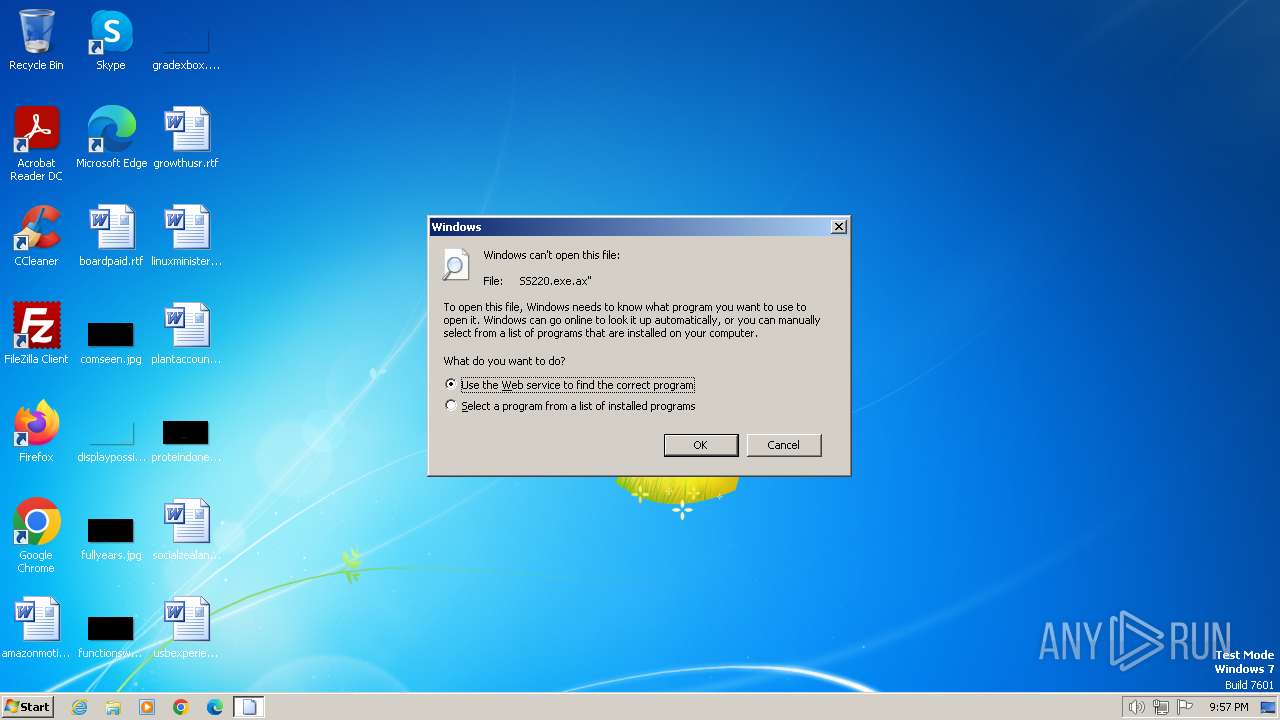
| File name: | SS220.exe |
| Full analysis: | https://app.any.run/tasks/4ed16d39-6ff2-41d2-9ab8-d5fffc335245 |
| Verdict: | Malicious activity |
| Analysis date: | January 07, 2024, 21:57:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9FCC1EB42F30F523C39980EB5051A385 |
| SHA1: | F8F397FAC336DD49A40AE2E4F2F793BD697DE3E3 |
| SHA256: | 240F25A7852321AE3E2864614FEF41BEAB82DDEEBEE57C064DD65C6260A65BD1 |
| SSDEEP: | 98304:oRa7UpgMkRkNgx4bgOtgZTp/xjbJCrpKqnDpKq4pKqTIRpKqsEszDeupKqCMupKT:MbQUa8G8OxrJbhlTcy |
MALICIOUS
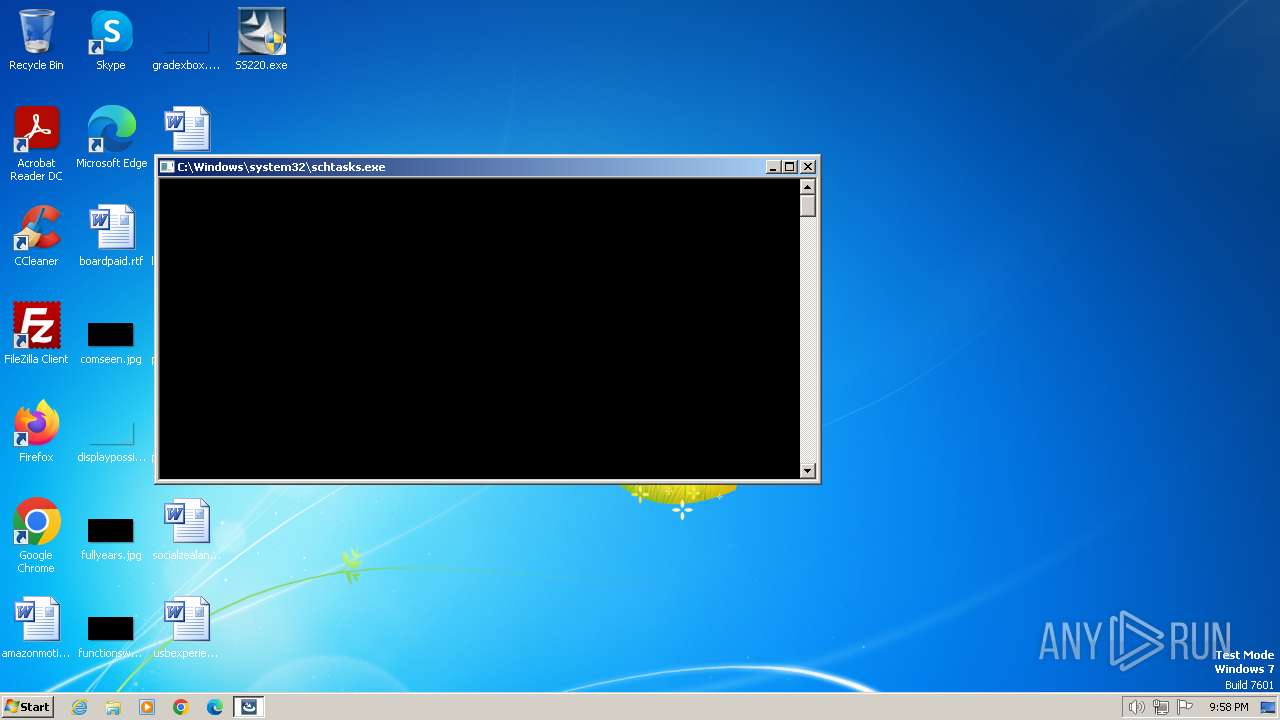
Uses Task Scheduler to run other applications
- SS220.exe (PID: 2056)
SUSPICIOUS
Reads the Windows owner or organization settings
- SS220.exe (PID: 2056)
Searches for installed software
- SS220.exe (PID: 2056)
- dllhost.exe (PID: 2584)
INFO
Reads the computer name
- SS220.exe (PID: 2056)
- mHotkey.exe (PID: 2916)
Manual execution by a user
- SS220.exe (PID: 1792)
- SS220.exe (PID: 2056)
- explorer.exe (PID: 908)
- SSConfig.exe (PID: 3124)
- msinfo32.exe (PID: 3368)
Drops the executable file immediately after the start
- rundll32.exe (PID: 2044)
- SS220.exe (PID: 2056)
Checks supported languages
- SS220.exe (PID: 2056)
- mHotkey.exe (PID: 2916)
- ChiFuncExt.exe (PID: 2524)
- SSConfig.exe (PID: 2956)
- SSConfig.exe (PID: 3124)
Create files in a temporary directory
- SS220.exe (PID: 2056)
Reads the machine GUID from the registry
- SS220.exe (PID: 2056)
Creates files or folders in the user directory
- SS220.exe (PID: 2056)
Executes as Windows Service
- VSSVC.exe (PID: 2328)
Creates files in the program directory
- SS220.exe (PID: 2056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .ax | | | DirectShow filter (40.7) |
|---|---|---|
| .exe | | | InstallShield setup (8.6) |
| .exe | | | Win32 Executable MS Visual C++ (generic) (6.3) |
| .exe | | | Win64 Executable (generic) (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:01:20 06:07:04+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 282624 |
| InitializedDataSize: | 172032 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x22d69 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 12.0.0.58849 |
| ProductVersionNumber: | 12.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Macrovision Corporation |
| FileDescription: | Setup.exe |
| FileVersion: | 12.0.58849 |
| InternalName: | Setup |
| OriginalFileName: | Setup.exe |
| LegalCopyright: | Copyright (C) 2006 Macrovision Corporation |
| ProductName: | InstallShield |
| ProductVersion: | 12 |
| OLESelfRegister: | - |
Total processes
55
Monitored processes
12
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 908 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 920 | schtasks.exe /Create /XML C:\Windows\MHotkey.XML /TN MHotkey | C:\Windows\System32\schtasks.exe | — | SS220.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1792 | "C:\Users\admin\Desktop\SS220.exe" | C:\Users\admin\Desktop\SS220.exe | — | explorer.exe | |||||||||||
User: admin Company: Macrovision Corporation Integrity Level: MEDIUM Description: Setup.exe Exit code: 3221226540 Version: 12.0.58849 Modules
| |||||||||||||||
| 2044 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL "C:\Users\admin\AppData\Local\Temp\SS220.exe.ax" | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2056 | "C:\Users\admin\Desktop\SS220.exe" | C:\Users\admin\Desktop\SS220.exe | explorer.exe | ||||||||||||
User: admin Company: Macrovision Corporation Integrity Level: HIGH Description: Setup.exe Exit code: 0 Version: 12.0.58849 Modules
| |||||||||||||||
| 2328 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2524 | C:\Windows\ChiFuncExt.exe | C:\Windows\ChiFuncExt.exe | — | mHotkey.exe | |||||||||||
User: admin Company: Chicony Integrity Level: HIGH Description: Input Assistant Software Kernel Exit code: 0 Version: 1, 0, 0, 0 Modules
| |||||||||||||||
| 2584 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2916 | C:\Windows\mHotkey.exe | C:\Windows\mHotkey.exe | — | SS220.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Multimedia Keyboard Driver Exit code: 0 Version: 3, 0, 0, 15 Modules
| |||||||||||||||
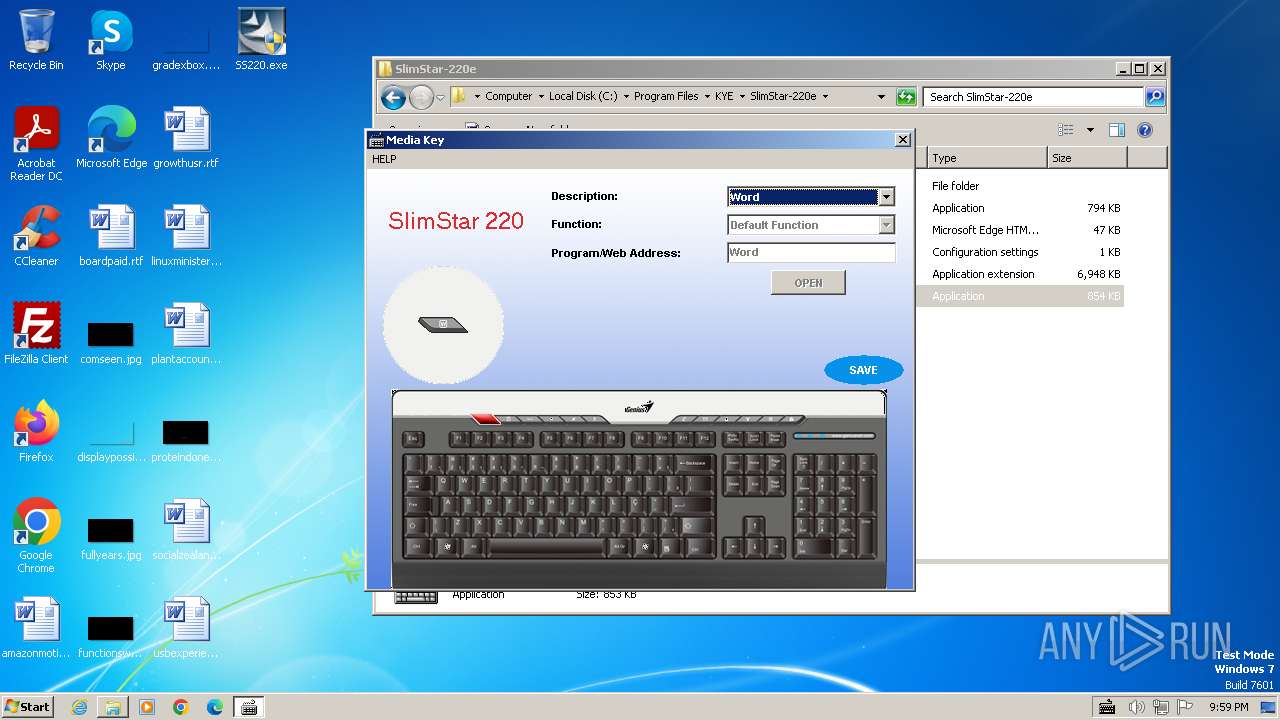
| 2956 | "C:\Program Files\KYE\SlimStar-220e\SSConfig.exe" | C:\Program Files\KYE\SlimStar-220e\SSConfig.exe | — | mHotkey.exe | |||||||||||
User: admin Company: CHICONY Integrity Level: HIGH Description: Media Key Exit code: 0 Version: 1.0.5.0 Modules
| |||||||||||||||
Total events
2 426
Read events
2 347
Write events
79
Delete events
0
Modification events
| (PID) Process: | (2056) SS220.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000009F5A7BD72FB0D90164030000840D0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2056) SS220.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 40000000000000009F5A7BD72FB0D90164030000840D0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2056) SS220.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 73 | |||
| (PID) Process: | (2056) SS220.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000008543C5D72FB0D90164030000840D0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2056) SS220.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 4000000000000000D1ABF1D82FB0D90164030000840D0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2056) SS220.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Leave) |
Value: 4000000000000000E57701DA2FB0D90164030000840D0000D0070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2056) SS220.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Leave) |
Value: 4000000000000000E57701DA2FB0D90164030000840D0000D5070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2056) SS220.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000002EA545A9B441DA0108080000C8080000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2584) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 40000000000000002EA545A9B441DA0108080000C8080000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2584) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 74 | |||
Executable files
33
Suspicious files
21
Text files
98
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2056 | SS220.exe | C:\Users\admin\AppData\Local\Temp\{189DCABE-0892-486C-B808-715B57747B58}\Disk1\data1.cab | compressed | |
MD5:E12B57992F74AEF6418B613954E7E948 | SHA256:C3083AAEAFE5650E1698976FC659170A0FD70465B7D08229B3BE1440E00268DD | |||
| 2056 | SS220.exe | C:\Users\admin\AppData\Local\Temp\{189DCABE-0892-486C-B808-715B57747B58}\Disk1\ISSetup.dll | executable | |
MD5:ABA37CD7FE50EE3D51BBA1884AB32011 | SHA256:7DEB4C7E37FE9429E64B0EB3D17BEB711B16876C5DAC90EBF057802F69F40C3C | |||
| 2056 | SS220.exe | C:\Users\admin\AppData\Local\Temp\{189DCABE-0892-486C-B808-715B57747B58}\_ispackdel.ini | text | |
MD5:11B233B7EBC4D7AA3E725A7F46106656 | SHA256:D54FEC18168B9E780636D62371AFA299504F17F402F6159310963922C1BB8FD4 | |||
| 2056 | SS220.exe | C:\Users\admin\AppData\Local\Temp\{189DCABE-0892-486C-B808-715B57747B58}\Disk1\layout.bin | binary | |
MD5:3064EB5F00ACF0654B2547036F8CC620 | SHA256:554DCE2F9EF1BC5500393A8204C36A78C4BAF64FE34831E55021F8AEE6384F3E | |||
| 2056 | SS220.exe | C:\Users\admin\AppData\Local\Temp\{189DCABE-0892-486C-B808-715B57747B58}\Disk1\_Setup.dll | executable | |
MD5:2985A79020EC96AFC2D1C8AB318B866F | SHA256:F9A007B9EC4A20FECFC004662028226E11ADA038BE69EAB586C03A903C73FBAD | |||
| 2056 | SS220.exe | C:\Users\admin\AppData\Local\Temp\{189DCABE-0892-486C-B808-715B57747B58}\setup.ini | text | |
MD5:64F8DB1C507DDAA1A4BC1CF19D550CBE | SHA256:12BFD9F1AE2793235BD4D443C9492D8E6837C888D50492CAD8475FE3C9AF762F | |||
| 2056 | SS220.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\4c85601bcbb53e7dc3880e8413b41fd4_90059c37-1320-41a4-b58d-2b75a9850d2f | binary | |
MD5:2A3A52DC633BD2E8E7187E9192350FDF | SHA256:BA39D2798AD84AFB8EE7D5A82B3C664B82BB98AB98AA8D7C8D9D471B16653115 | |||
| 2056 | SS220.exe | C:\Users\admin\AppData\Local\Temp\{189DCABE-0892-486C-B808-715B57747B58}\Disk1\setup.exe | executable | |
MD5:1108B166160D6023AF76435B074052B6 | SHA256:52B032521B4CD24A4268472BCFF3BE42FD8166A5CC5993B89F79575AA0279666 | |||
| 2056 | SS220.exe | C:\Users\admin\AppData\Local\Temp\{189DCABE-0892-486C-B808-715B57747B58}\Disk1\data1.hdr | compressed | |
MD5:230DC010EC2D76A676B9F3408DC66AC5 | SHA256:FF795C80CF8947F46254314348D808E065FE439D99B22E02CBD660BB86C85314 | |||
| 2056 | SS220.exe | C:\Users\admin\AppData\Local\Temp\{5EC62BFC-E019-4B61-B6AB-58D9B2E06CDF}\corecomp.ini | text | |
MD5:09D38CECA6A012F4CE5B54F03DB9B21A | SHA256:F6D7BC8CA6550662166F34407968C7D3669613E50E98A4E40BEC1589E74FF5D1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |