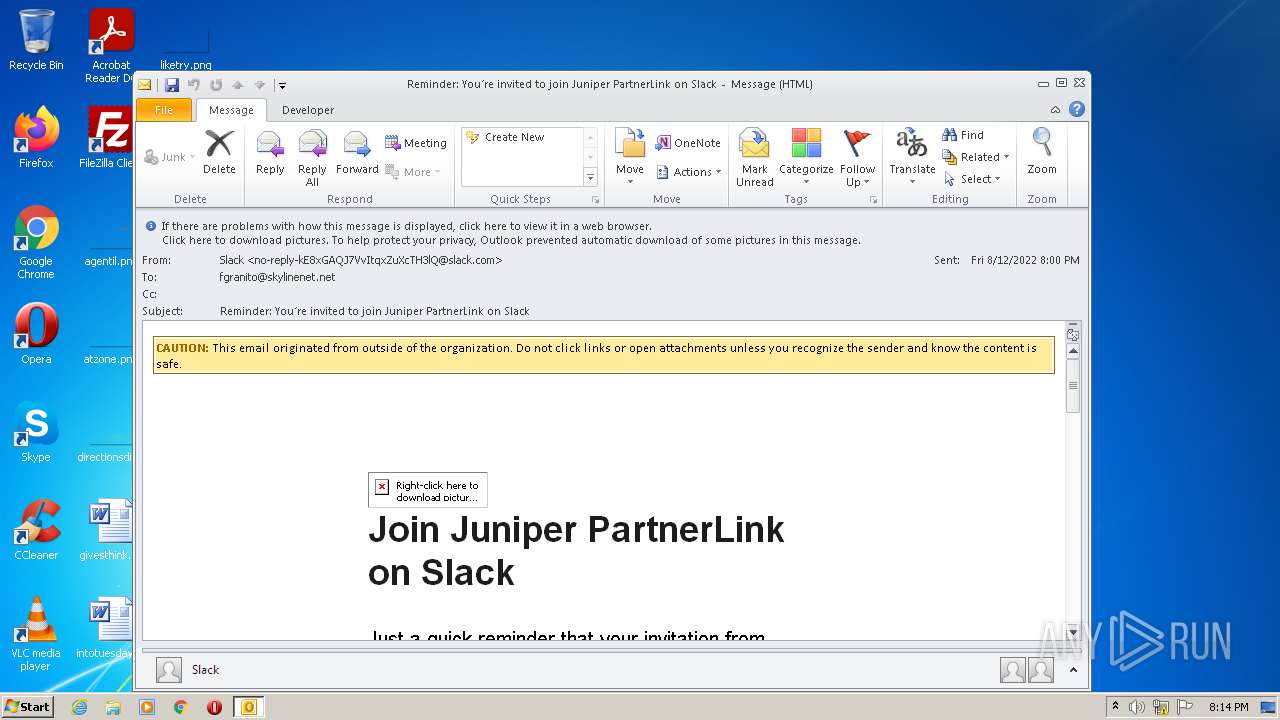
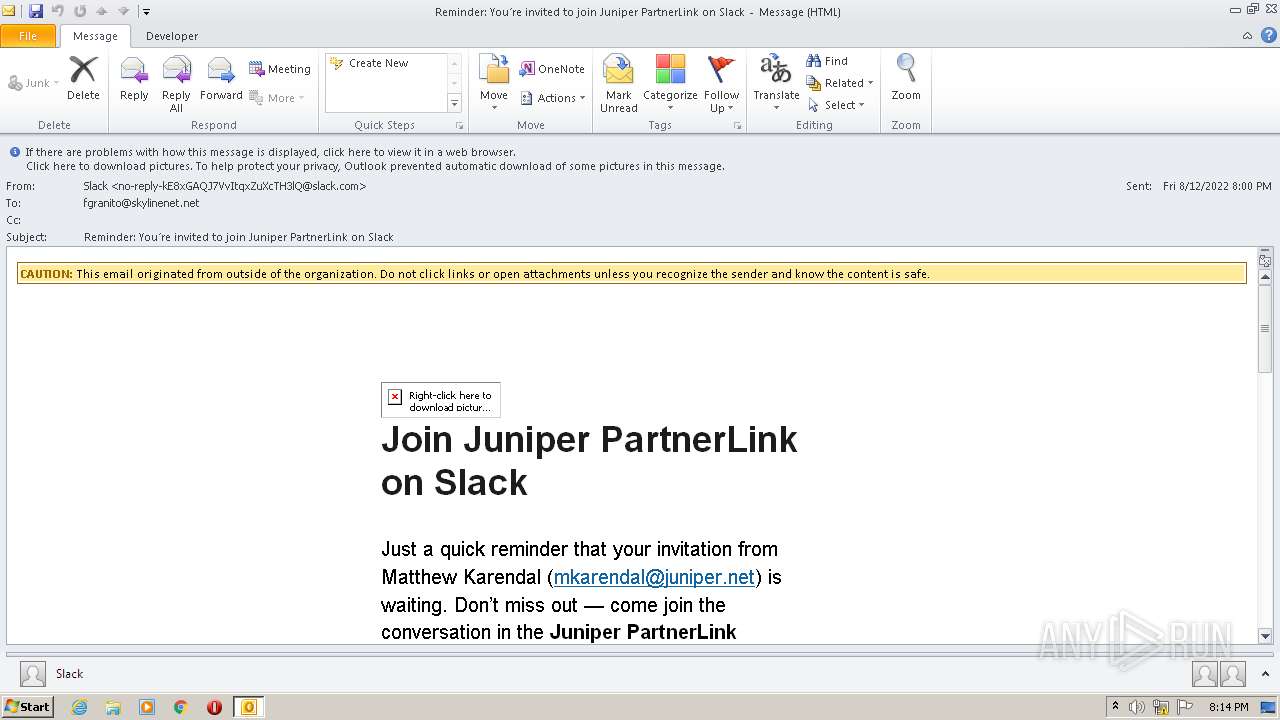
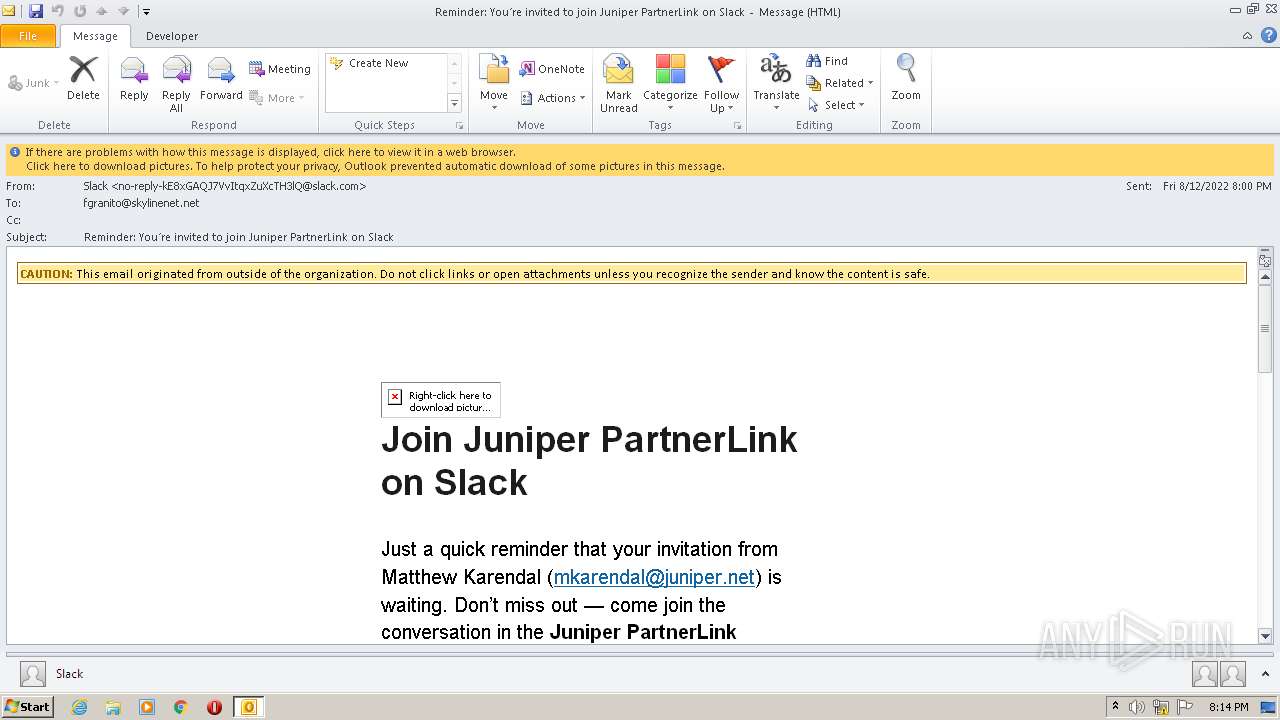
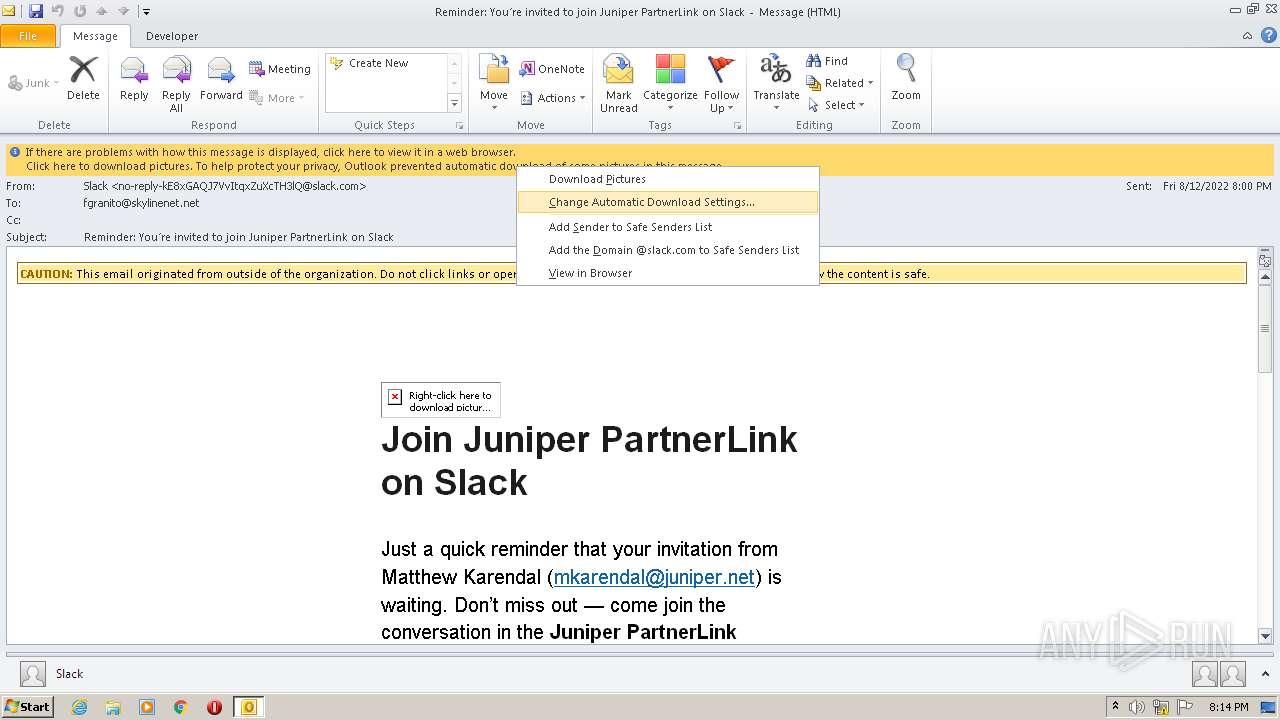
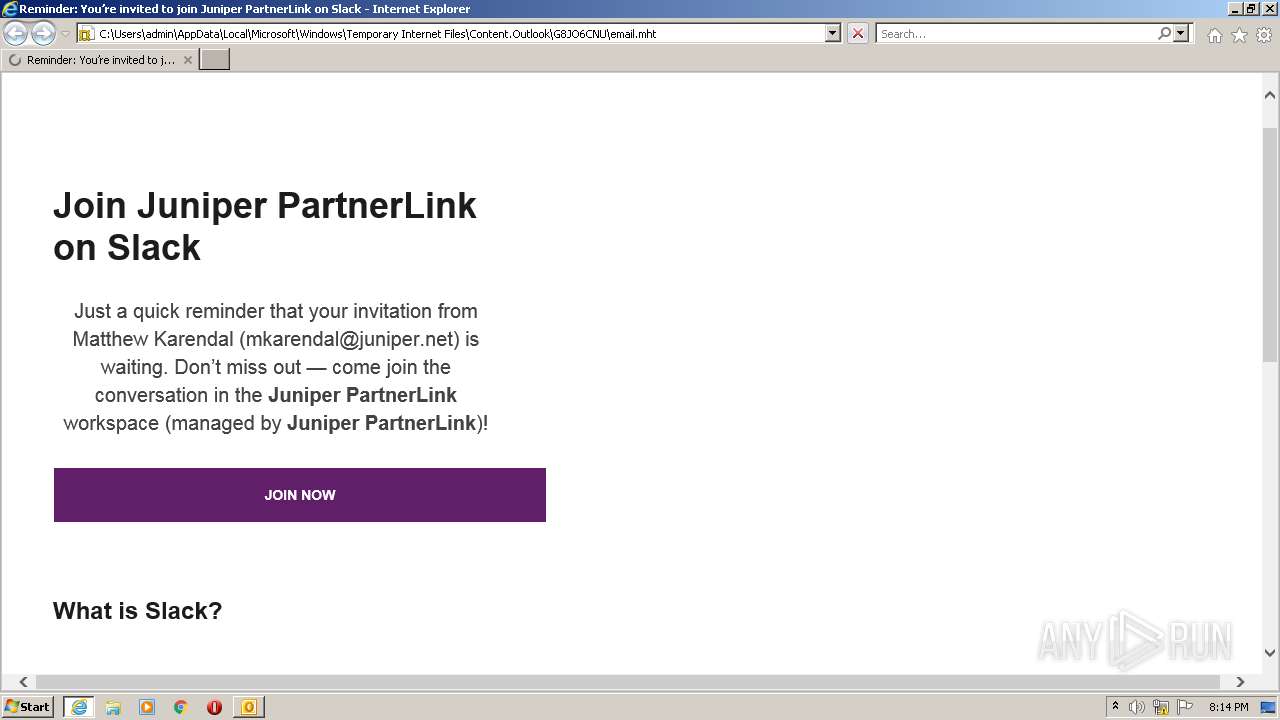
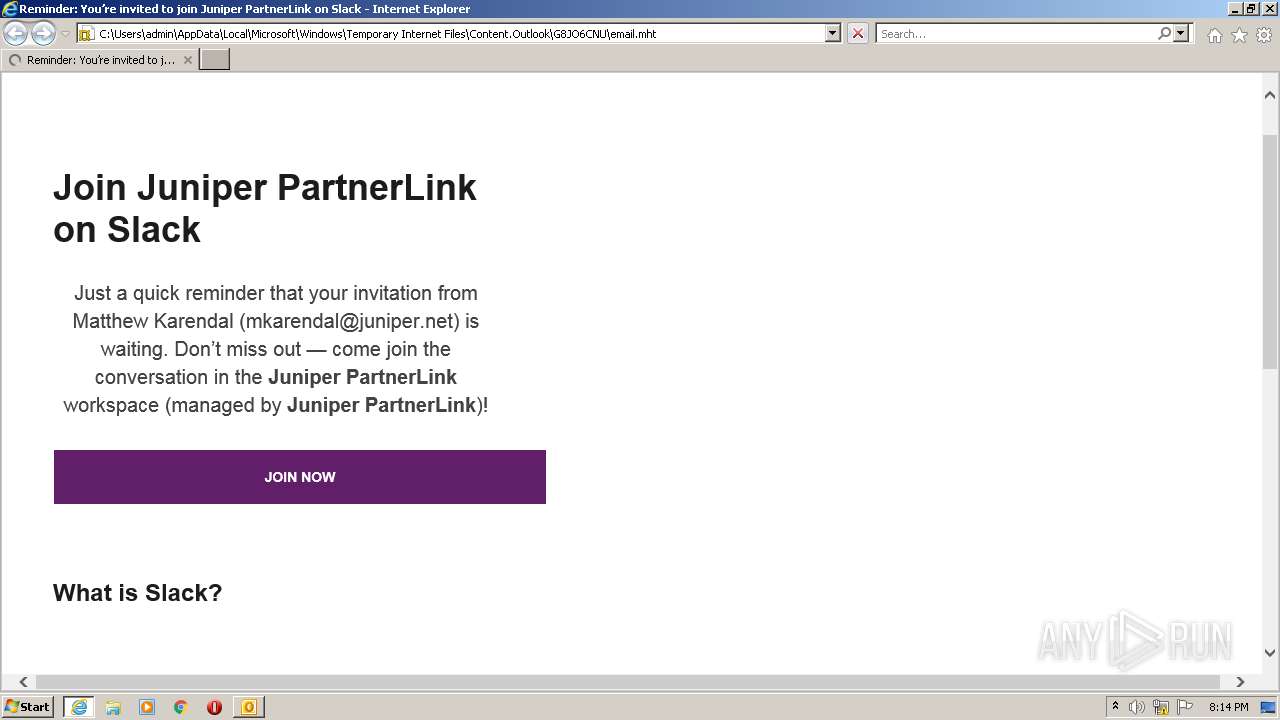
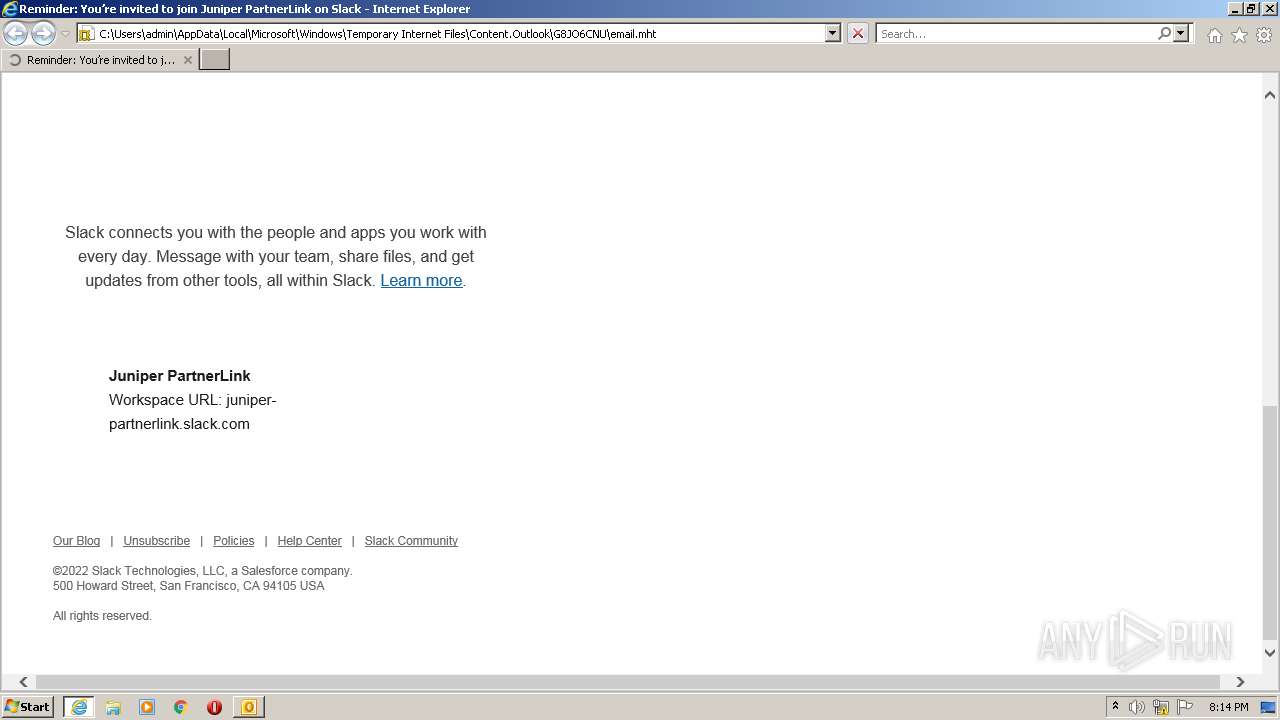
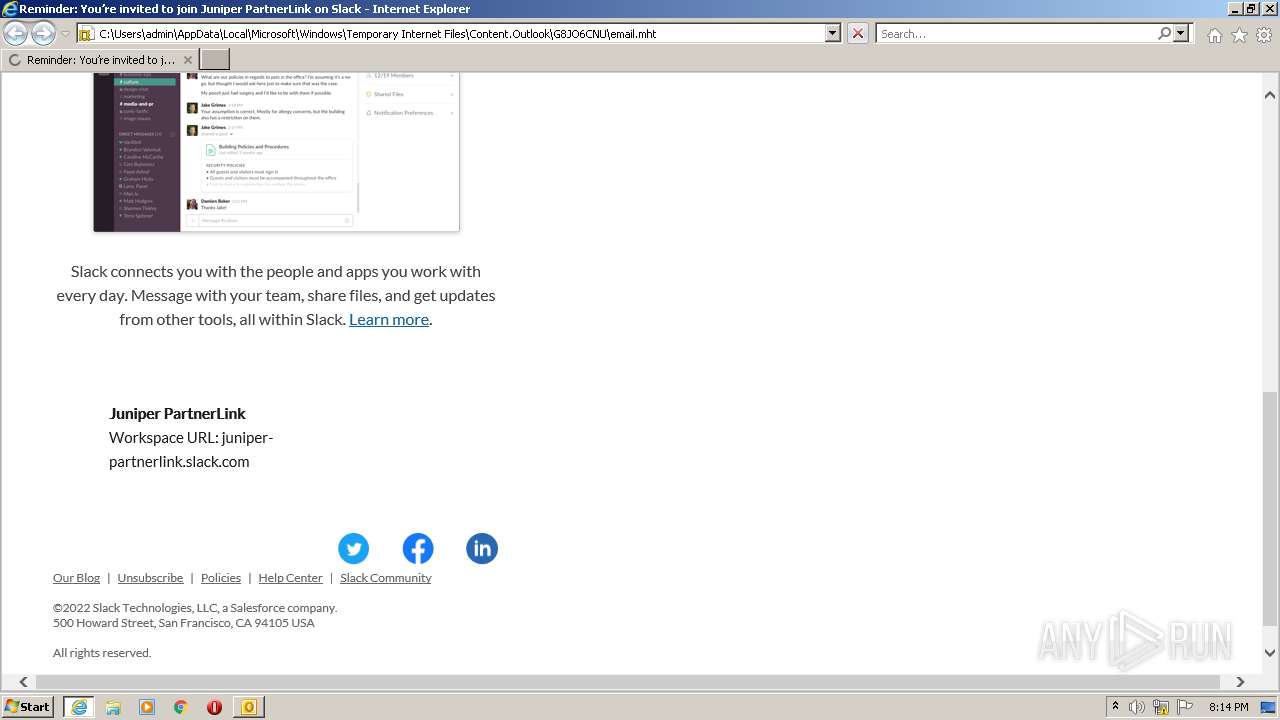
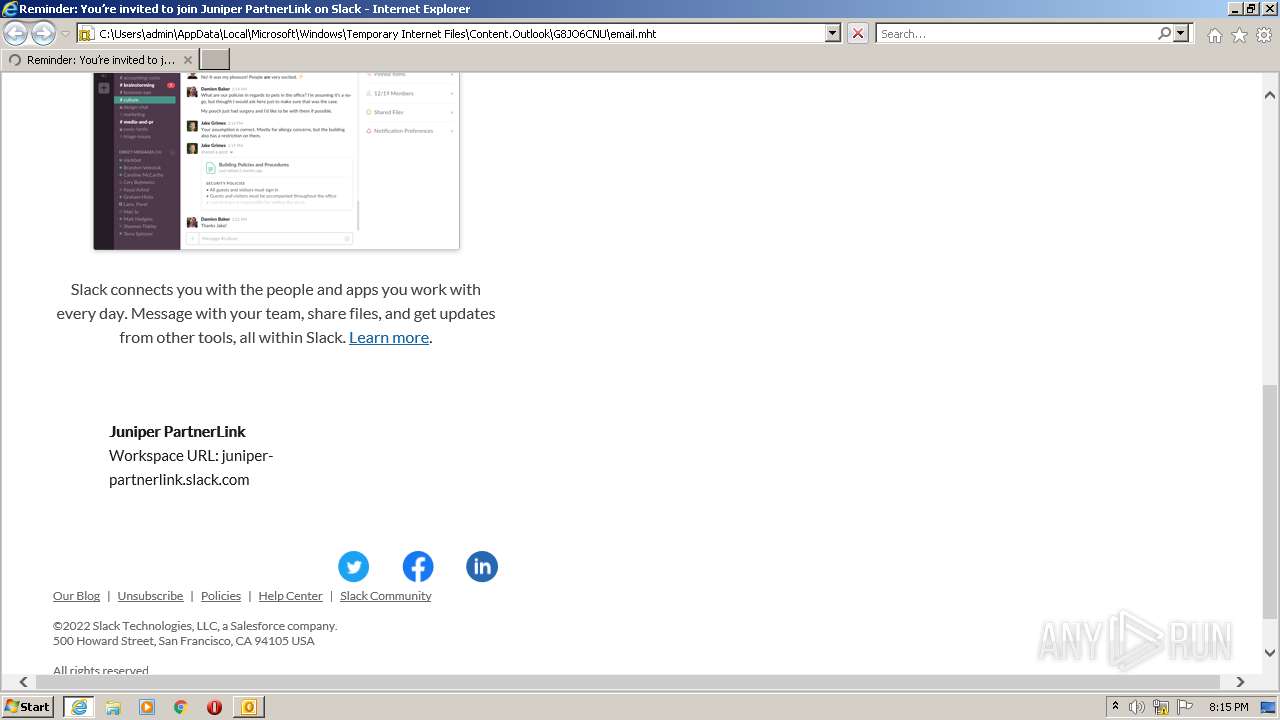
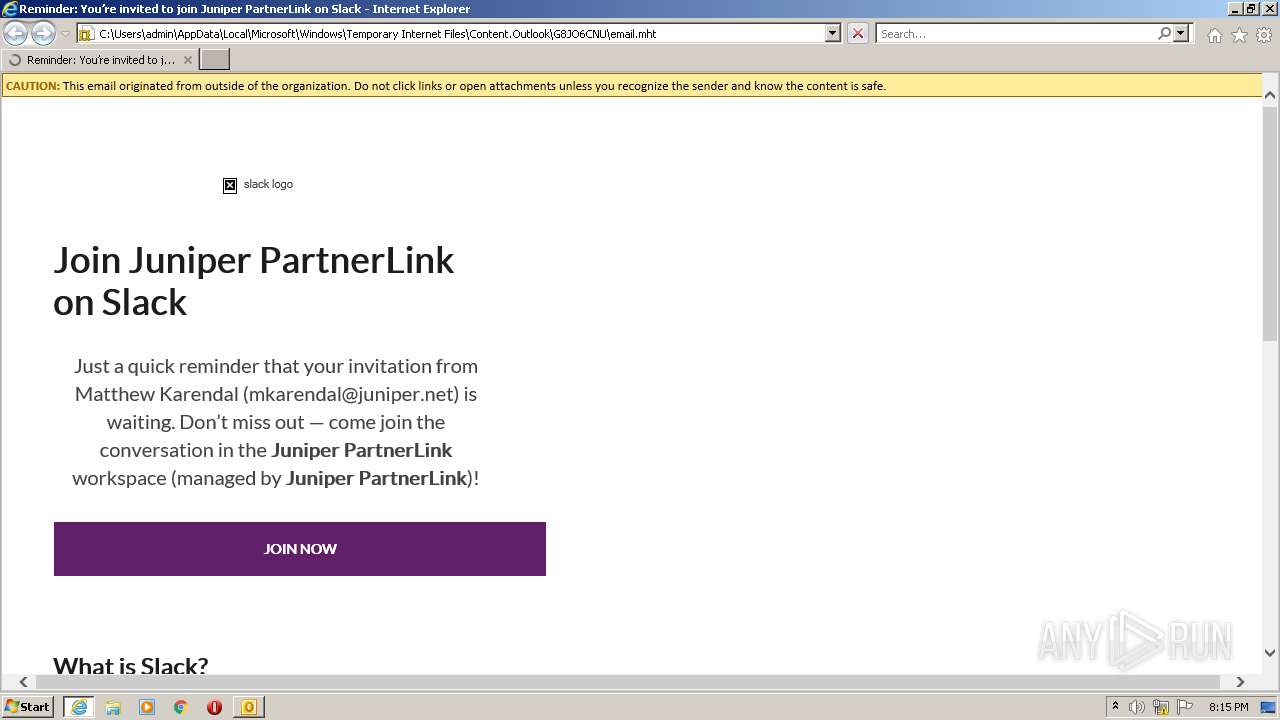
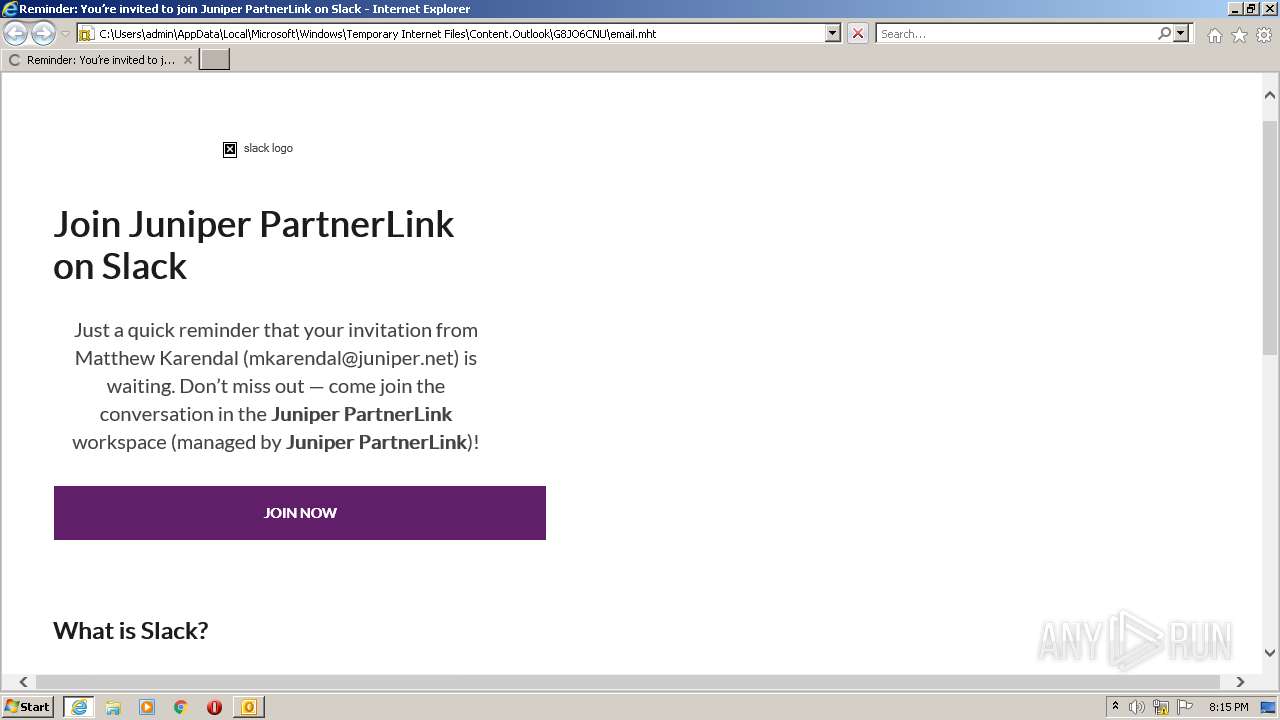
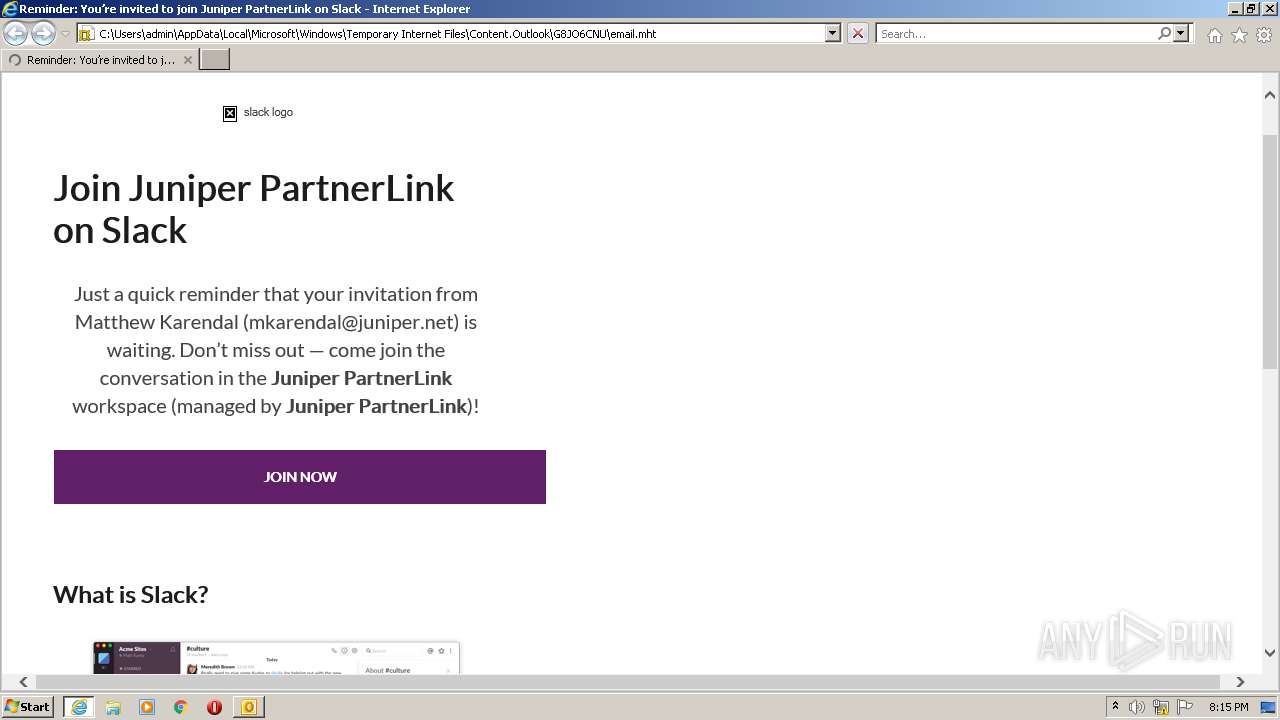
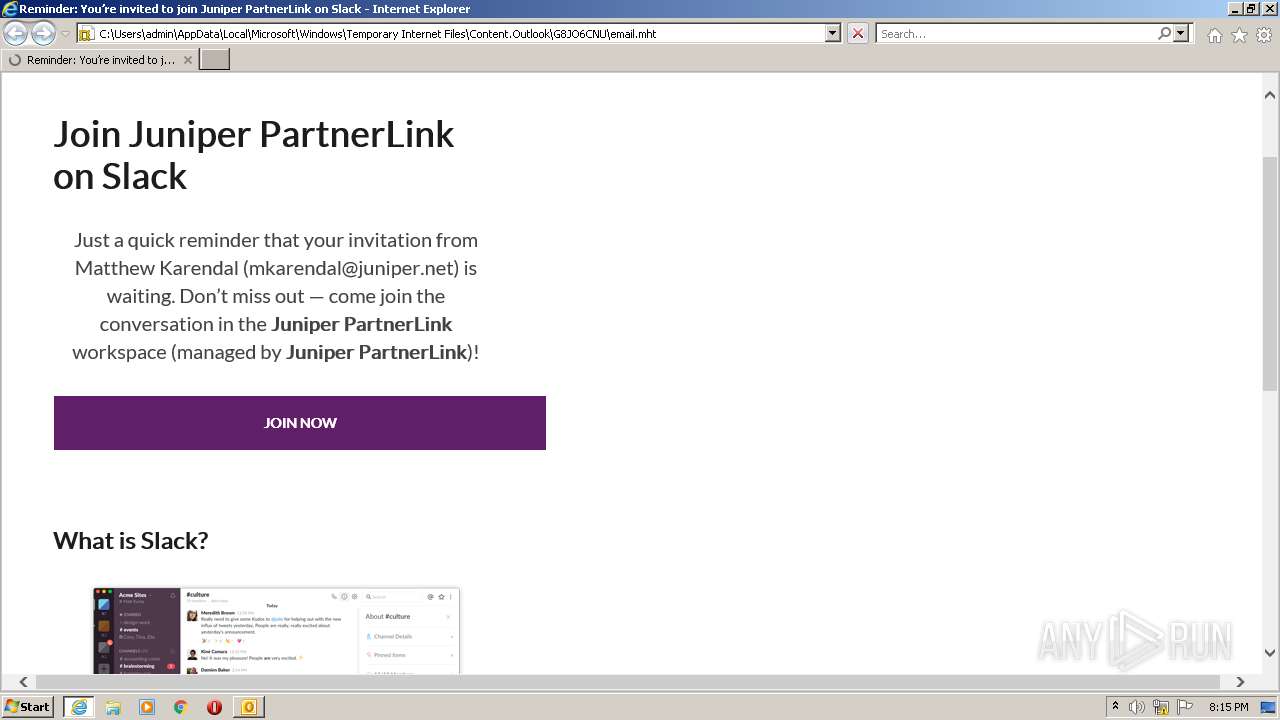
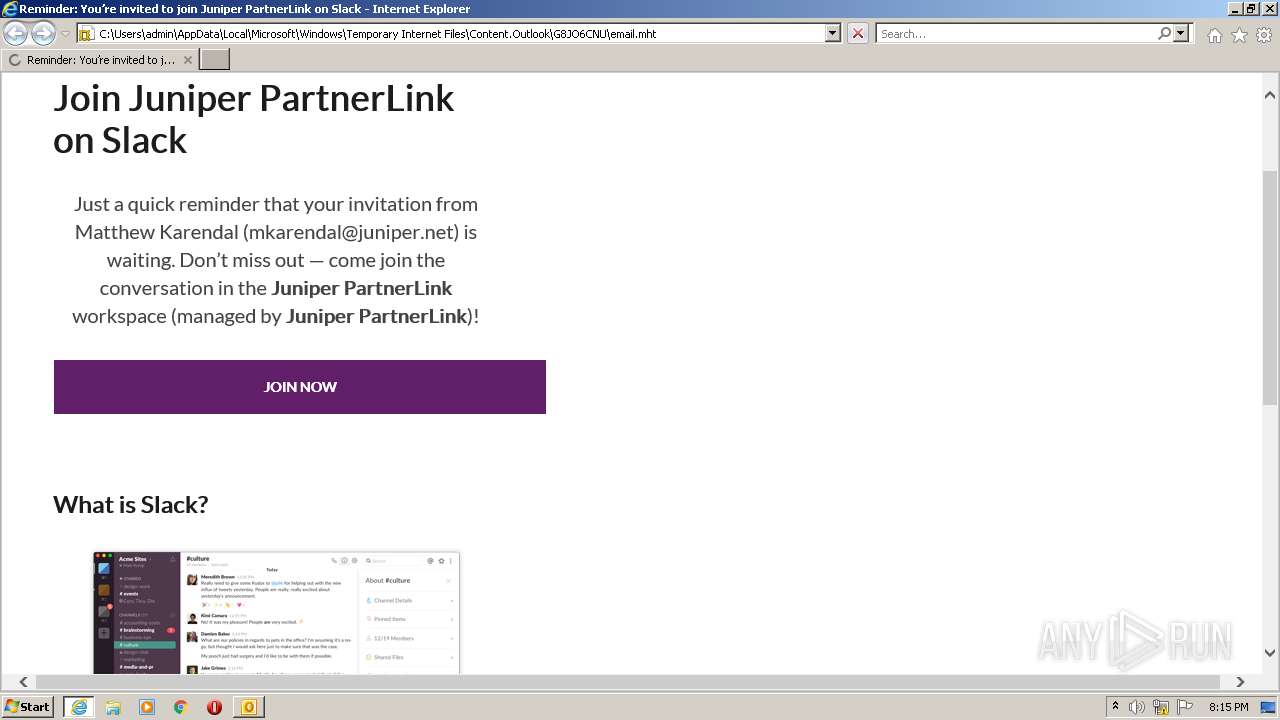
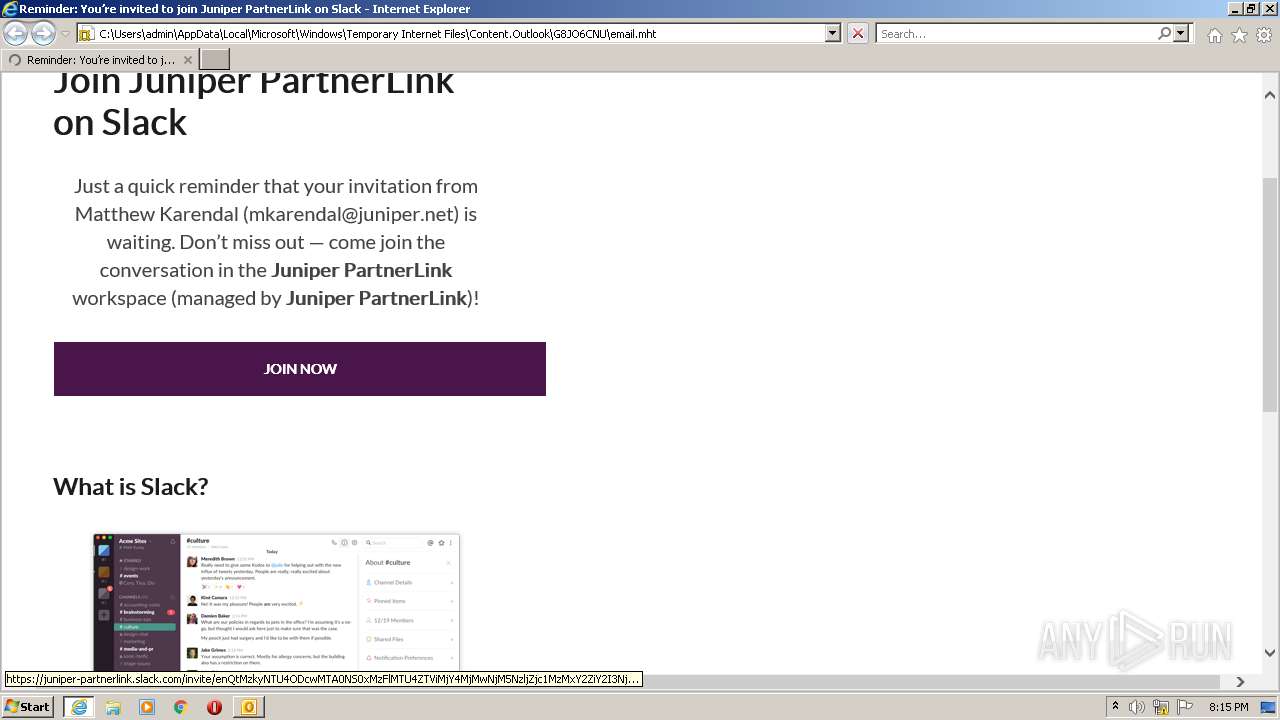
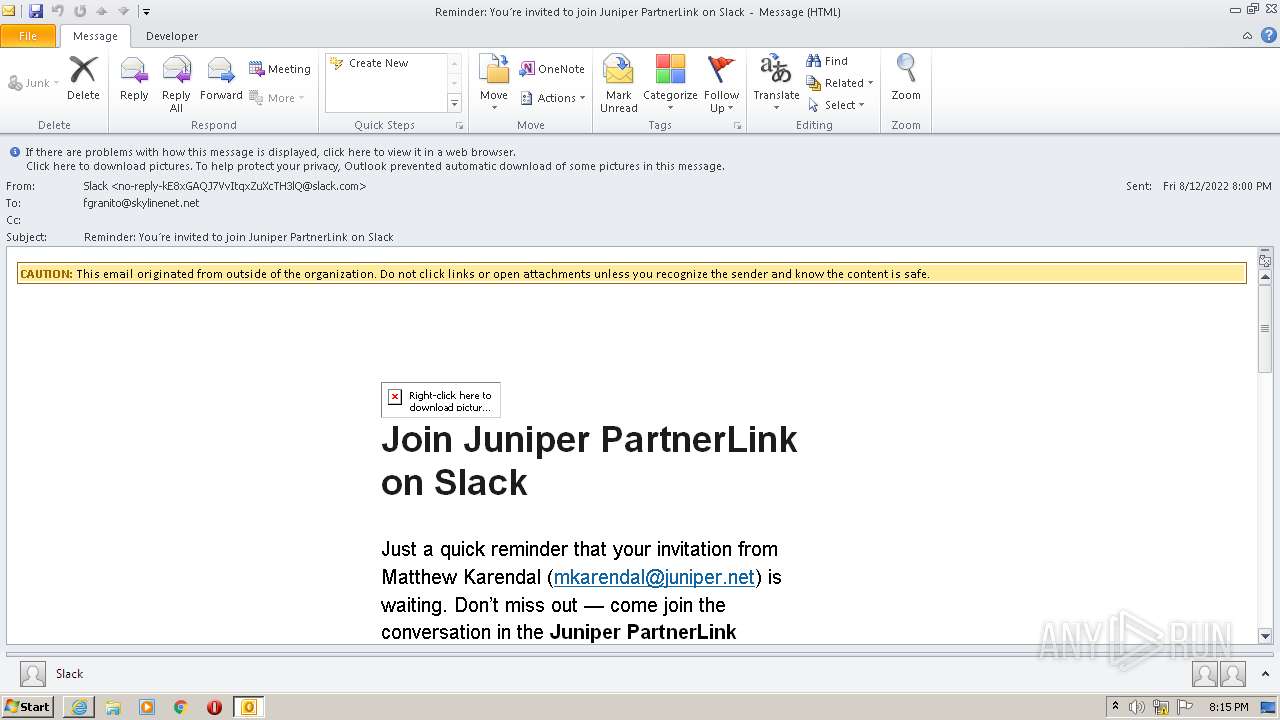
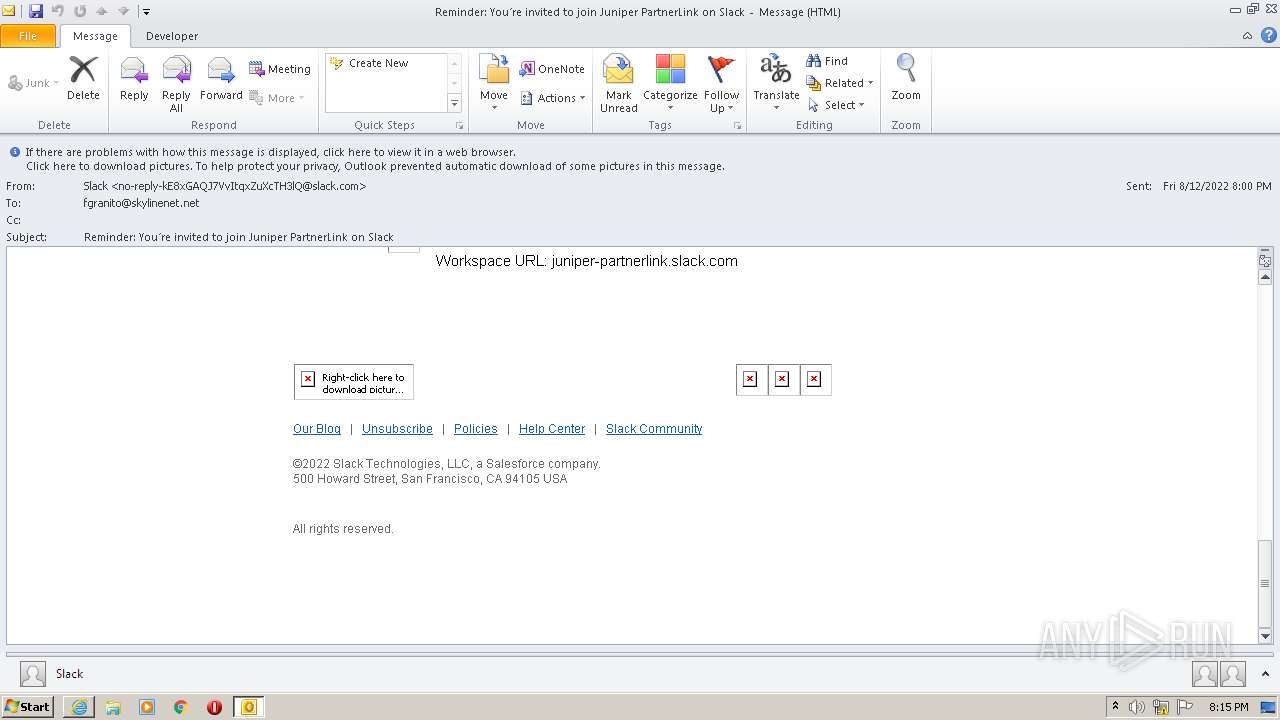
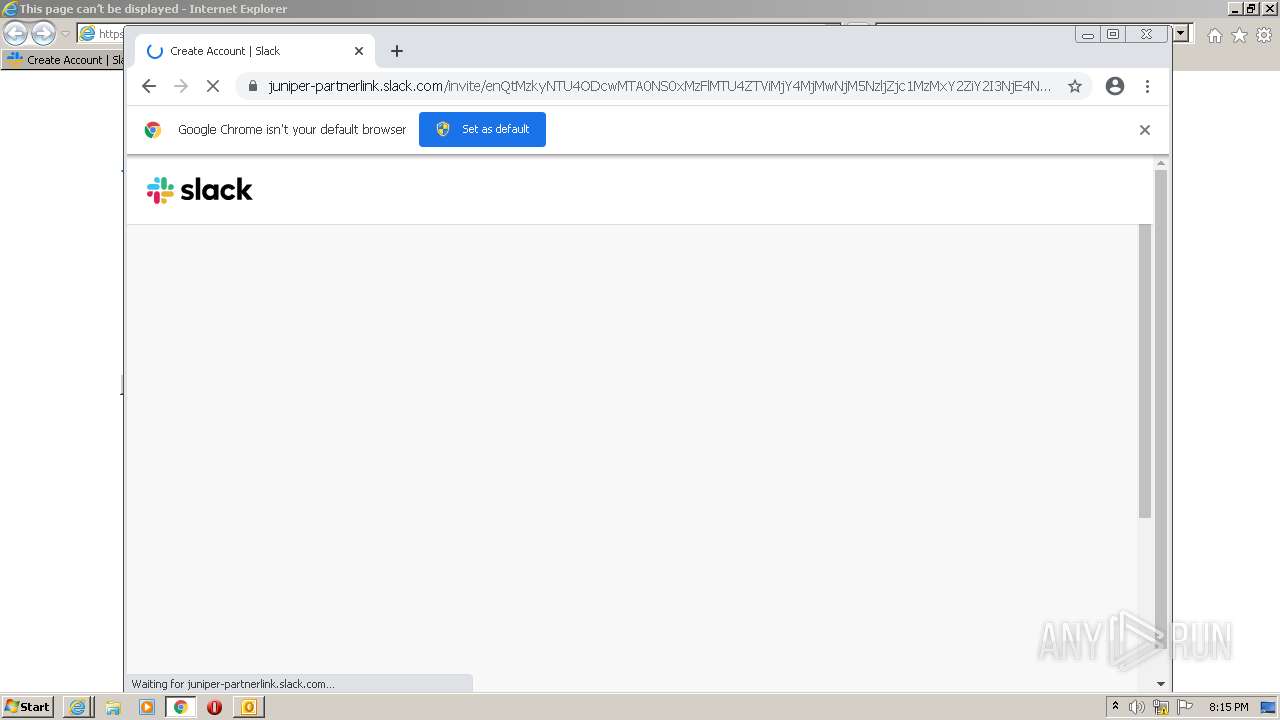
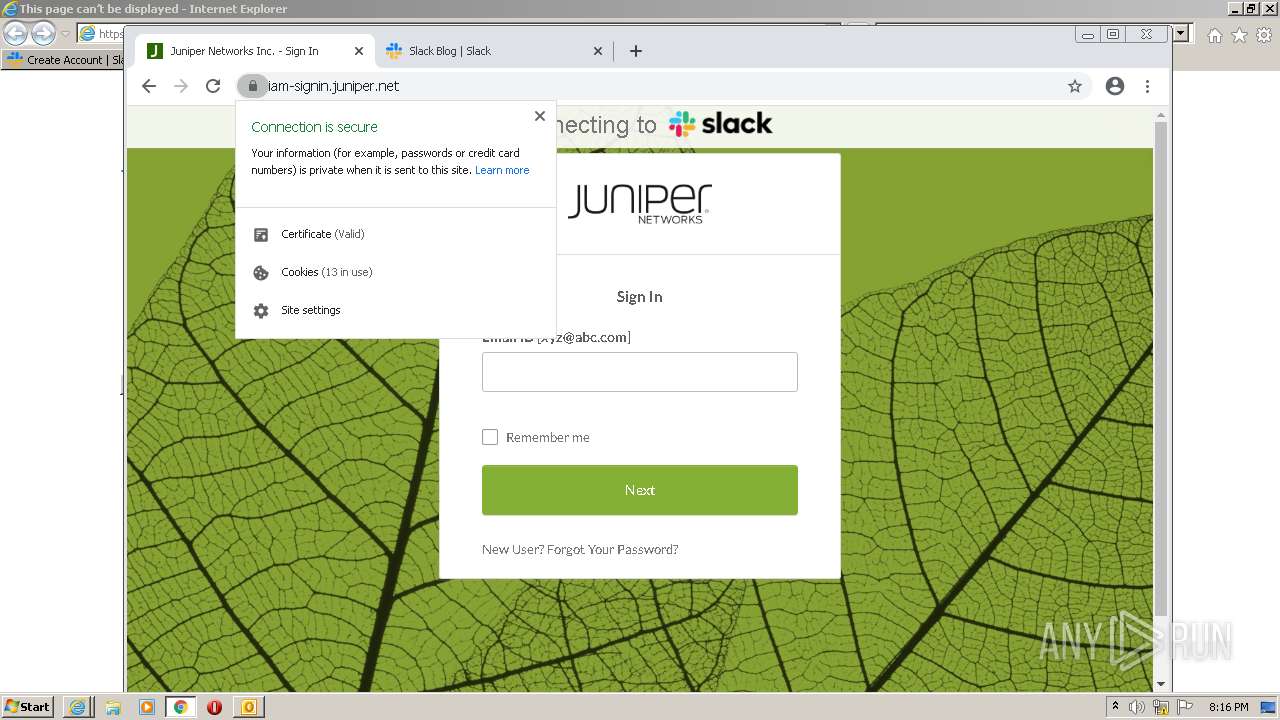
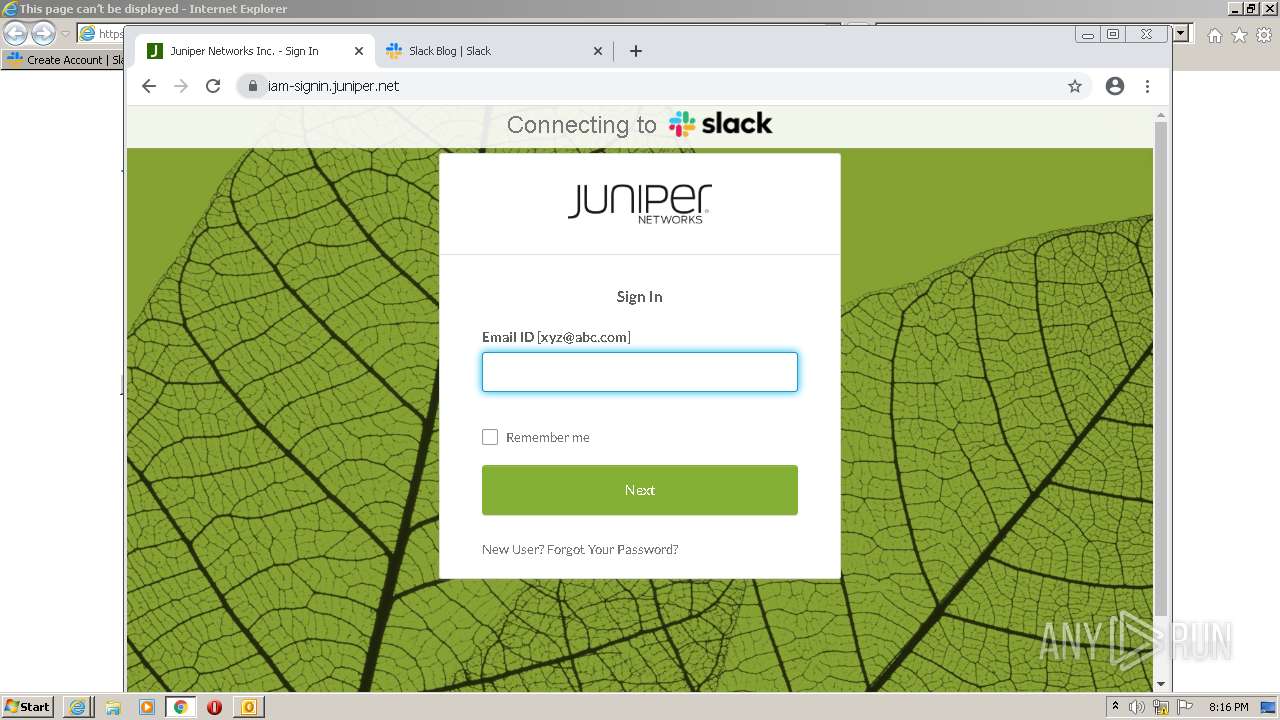
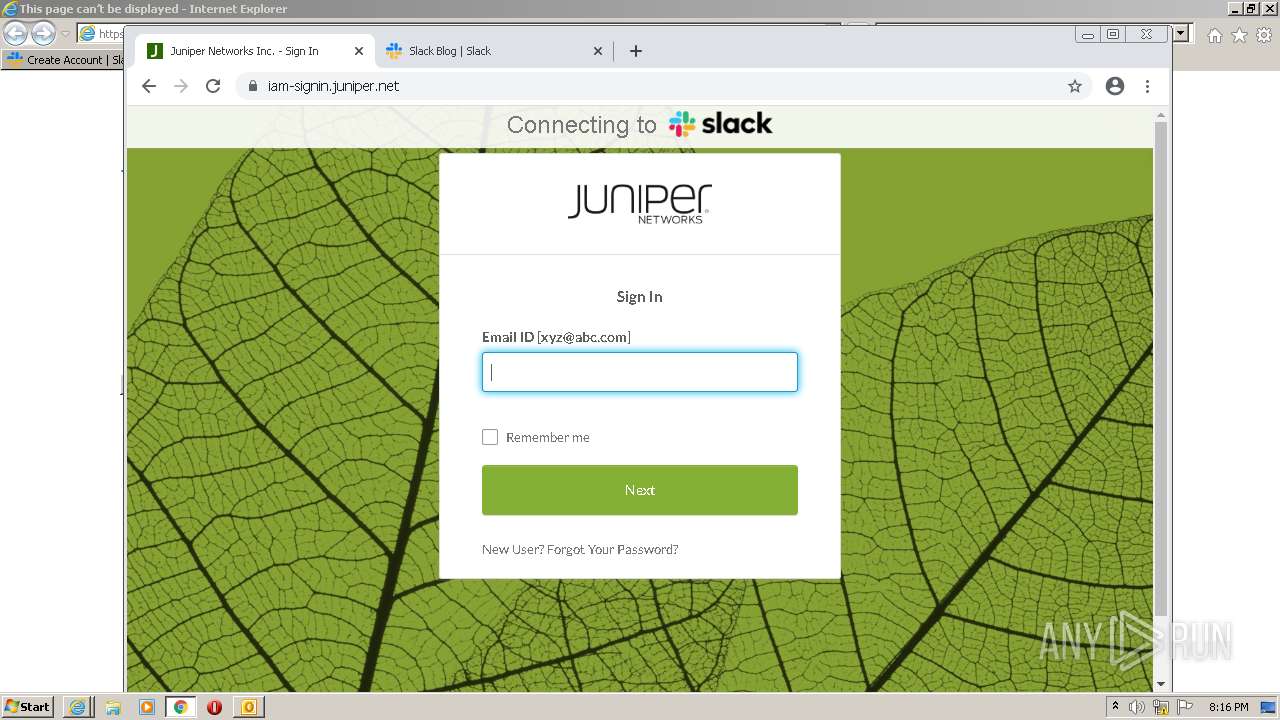
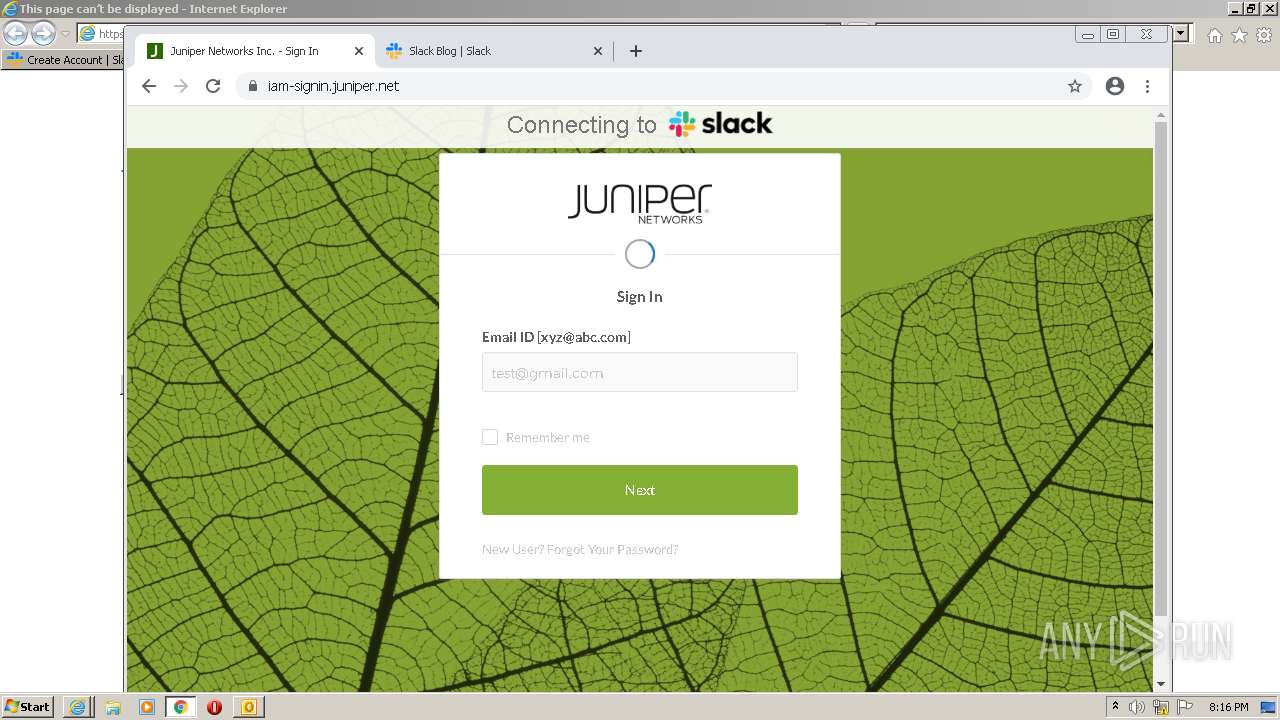
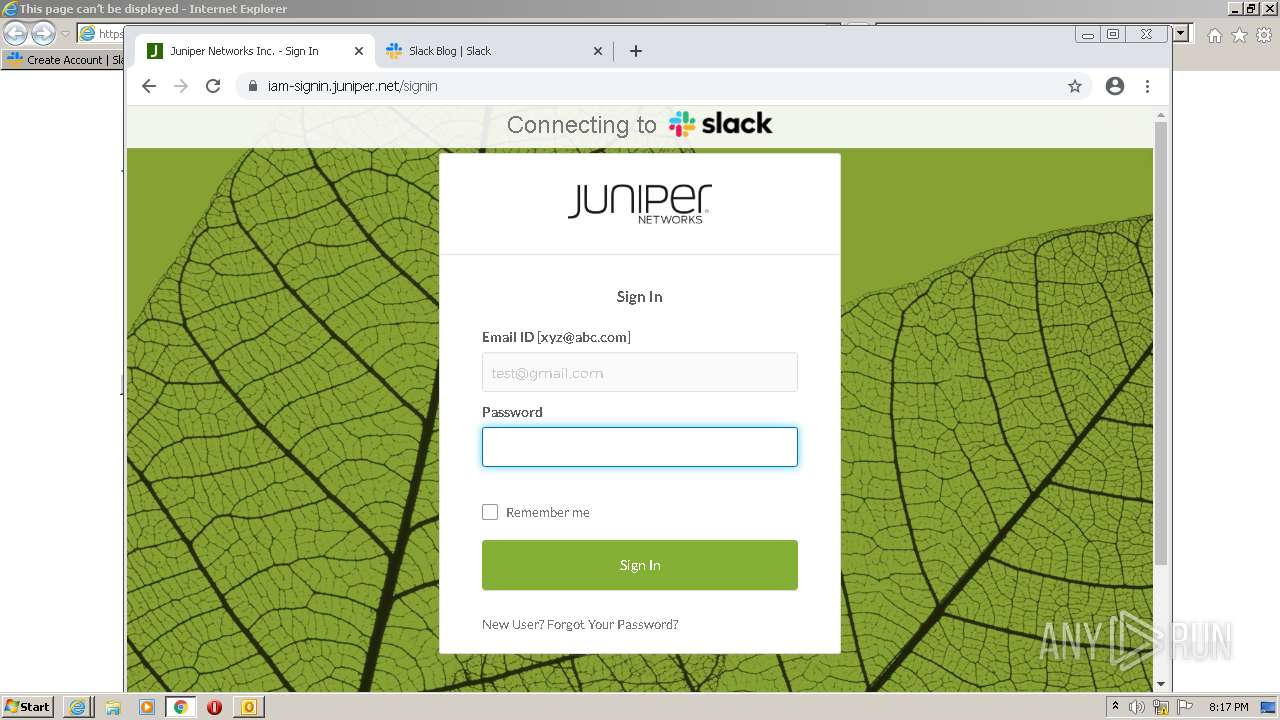
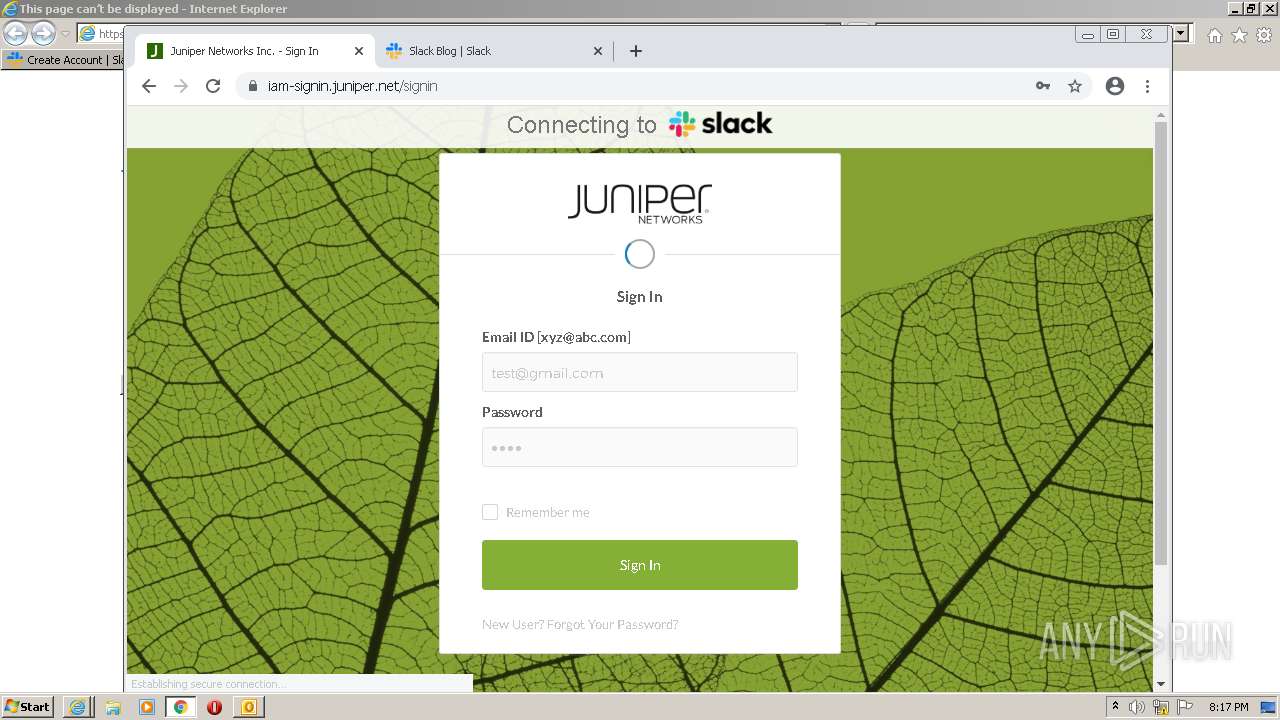
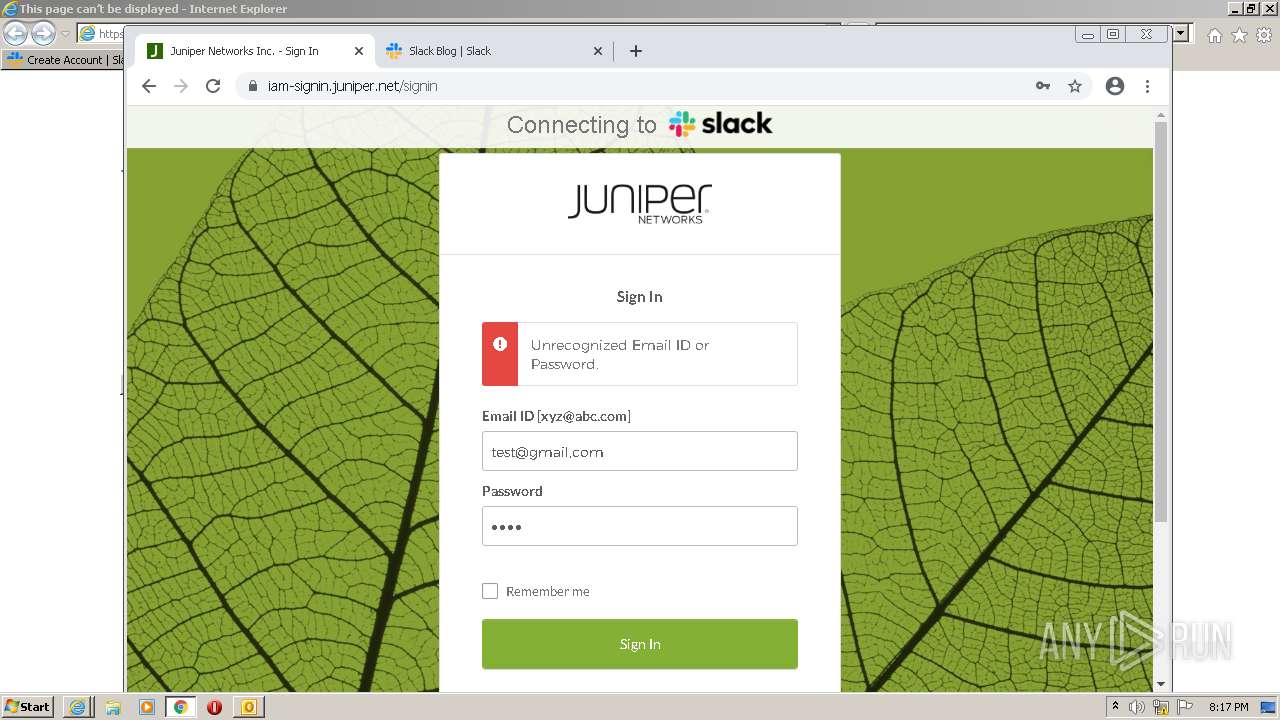
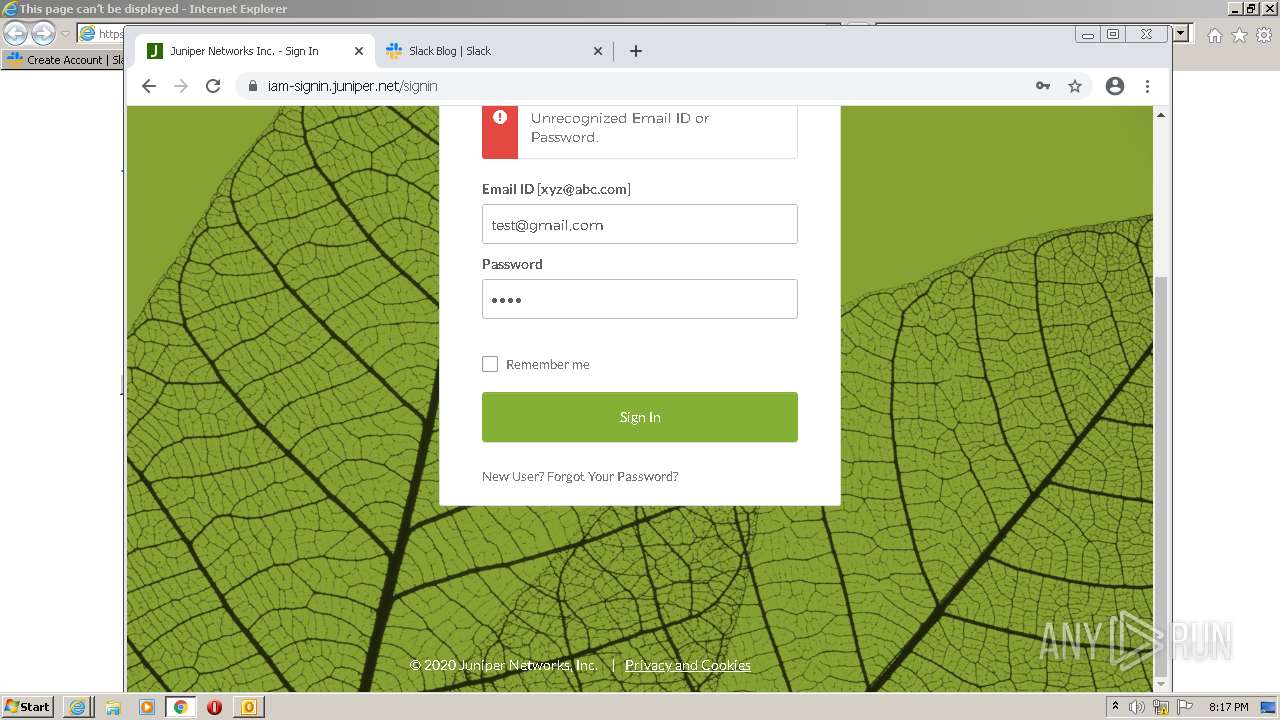
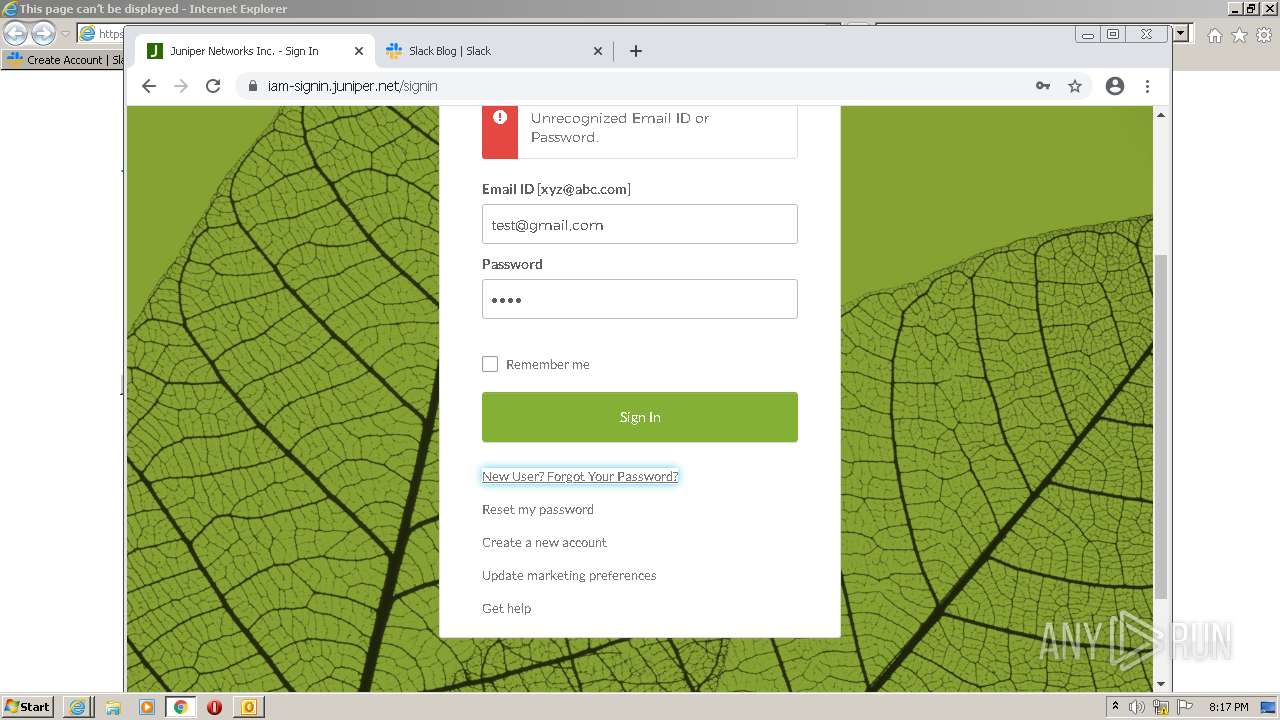
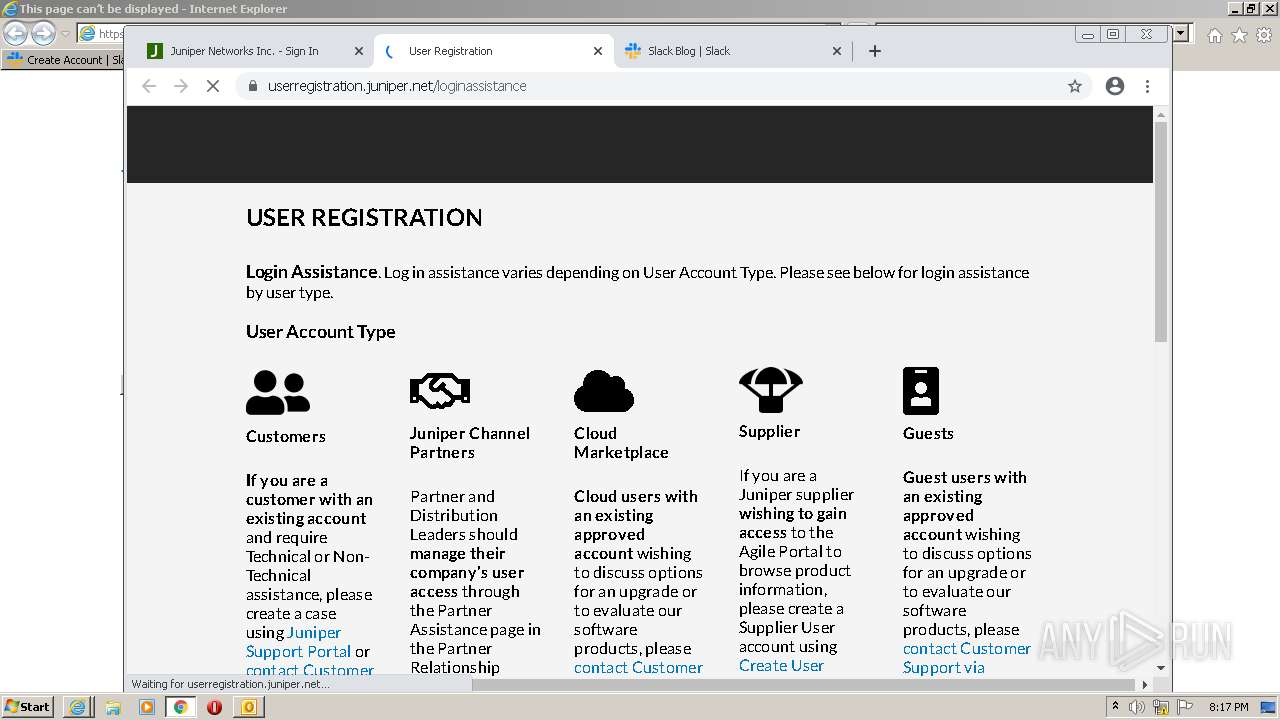
| File name: | phish_alert_sp2_2.0.0.0 (7).eml |
| Full analysis: | https://app.any.run/tasks/cd7591d6-d157-470b-a322-e10b275a93bd |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 19:14:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 000E4135D99B441E36BE5869A1A6835D |
| SHA1: | C13C8F7803378C2E1DE1D0A01E04955D4224C24F |
| SHA256: | 24028B46E5578511008CE251773CC6216D5EBD222D77AB9D0F41FD1C088A1375 |
| SSDEEP: | 384:GXd+Jct8ZBs/Qu+0lIQhxCJelK+YdxCJBUQVYxX7HIy8+tsIJtJau1f9j:RhWQu/RlwEgNIy8yJauh9j |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the computer name
- OUTLOOK.EXE (PID: 1520)
Searches for installed software
- OUTLOOK.EXE (PID: 1520)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 4044)
- iexplore.exe (PID: 3720)
Checks supported languages
- OUTLOOK.EXE (PID: 1520)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3888)
INFO
Reads the computer name
- iexplore.exe (PID: 3232)
- iexplore.exe (PID: 4044)
- iexplore.exe (PID: 3720)
- chrome.exe (PID: 3888)
- chrome.exe (PID: 4016)
- chrome.exe (PID: 4052)
- chrome.exe (PID: 284)
- chrome.exe (PID: 1088)
- chrome.exe (PID: 2288)
- chrome.exe (PID: 1448)
- chrome.exe (PID: 664)
- chrome.exe (PID: 3228)
Reads settings of System Certificates
- iexplore.exe (PID: 3232)
- iexplore.exe (PID: 4044)
- iexplore.exe (PID: 3720)
- chrome.exe (PID: 4016)
Checks supported languages
- iexplore.exe (PID: 3720)
- iexplore.exe (PID: 3232)
- iexplore.exe (PID: 4044)
- chrome.exe (PID: 3888)
- chrome.exe (PID: 3252)
- chrome.exe (PID: 4016)
- chrome.exe (PID: 4052)
- chrome.exe (PID: 3492)
- chrome.exe (PID: 3700)
- chrome.exe (PID: 2440)
- chrome.exe (PID: 904)
- chrome.exe (PID: 2972)
- chrome.exe (PID: 1088)
- chrome.exe (PID: 284)
- chrome.exe (PID: 2956)
- chrome.exe (PID: 2668)
- chrome.exe (PID: 892)
- chrome.exe (PID: 1788)
- chrome.exe (PID: 1264)
- chrome.exe (PID: 660)
- chrome.exe (PID: 2288)
- chrome.exe (PID: 3160)
- chrome.exe (PID: 3140)
- chrome.exe (PID: 2288)
- chrome.exe (PID: 1932)
- chrome.exe (PID: 3916)
- chrome.exe (PID: 3380)
- chrome.exe (PID: 1448)
- chrome.exe (PID: 3228)
- chrome.exe (PID: 664)
- chrome.exe (PID: 1504)
- chrome.exe (PID: 120)
- chrome.exe (PID: 3312)
- chrome.exe (PID: 3676)
- chrome.exe (PID: 1524)
Changes internet zones settings
- iexplore.exe (PID: 3232)
Application launched itself
- iexplore.exe (PID: 3232)
- chrome.exe (PID: 3888)
Checks Windows Trust Settings
- iexplore.exe (PID: 4044)
- iexplore.exe (PID: 3720)
- iexplore.exe (PID: 3232)
Reads internet explorer settings
- iexplore.exe (PID: 4044)
- iexplore.exe (PID: 3720)
Manual execution by user
- chrome.exe (PID: 3888)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 1520)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3232)
Changes settings of System certificates
- iexplore.exe (PID: 3232)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3232)
Reads the date of Windows installation
- chrome.exe (PID: 1448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
76
Monitored processes
36
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1252,12373162446714489170,8904404264810606057,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=30 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=668 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 284 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1252,12373162446714489170,8904404264810606057,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3532 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 660 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1252,12373162446714489170,8904404264810606057,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3660 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 664 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1252,12373162446714489170,8904404264810606057,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3132 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 892 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1252,12373162446714489170,8904404264810606057,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=19 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2900 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 904 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1252,12373162446714489170,8904404264810606057,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2932 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1088 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1252,12373162446714489170,8904404264810606057,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2924 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1264 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1252,12373162446714489170,8904404264810606057,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3516 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1448 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1252,12373162446714489170,8904404264810606057,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1996 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1504 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1252,12373162446714489170,8904404264810606057,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=536 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
39 315
Read events
38 381
Write events
903
Delete events
31
Modification events
| (PID) Process: | (1520) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1520) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1520) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1520) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1520) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1520) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1520) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1520) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1520) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (1520) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
242
Text files
208
Unknown types
47
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1520 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR97BC.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1520 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 1520 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1520 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
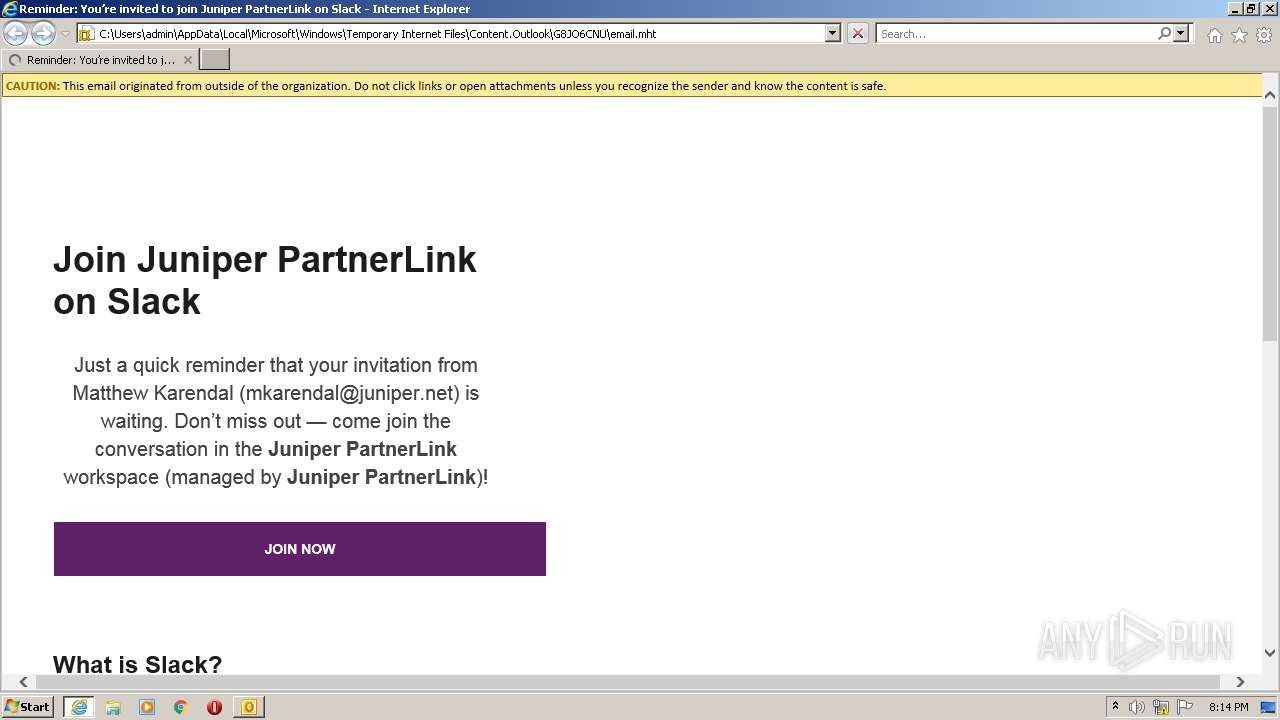
| 1520 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\G8JO6CNU\email.mht | html | |
MD5:— | SHA256:— | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\wbkC11F.tmp | html | |
MD5:— | SHA256:— | |||
| 4044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 1520 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_WorkHours_1_69916B1317A90744AF5276B3D43BE51B.dat | xml | |
MD5:807EF0FC900FEB3DA82927990083D6E7 | SHA256:4411E7DC978011222764943081500FFF0E43CBF7CCD44264BD1AB6306CA68913 | |||
| 3232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
141
DNS requests
72
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1520 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
4044 | iexplore.exe | GET | 200 | 172.217.23.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDyjRAUcVc1IArKByftf8KS | US | der | 472 b | whitelisted |
4044 | iexplore.exe | GET | 200 | 13.225.84.49:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
4044 | iexplore.exe | GET | 200 | 172.217.23.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
4044 | iexplore.exe | GET | 200 | 13.225.84.104:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEAUP3qKPs2fO6o794AObYqk%3D | US | der | 471 b | whitelisted |
3232 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
4044 | iexplore.exe | GET | 200 | 172.217.23.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3232 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3720 | iexplore.exe | GET | 200 | 13.107.4.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?3c4d590e4d71801a | US | compressed | 60.2 Kb | whitelisted |
3232 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4044 | iexplore.exe | 142.250.186.67:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
1520 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
4044 | iexplore.exe | 216.58.214.10:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
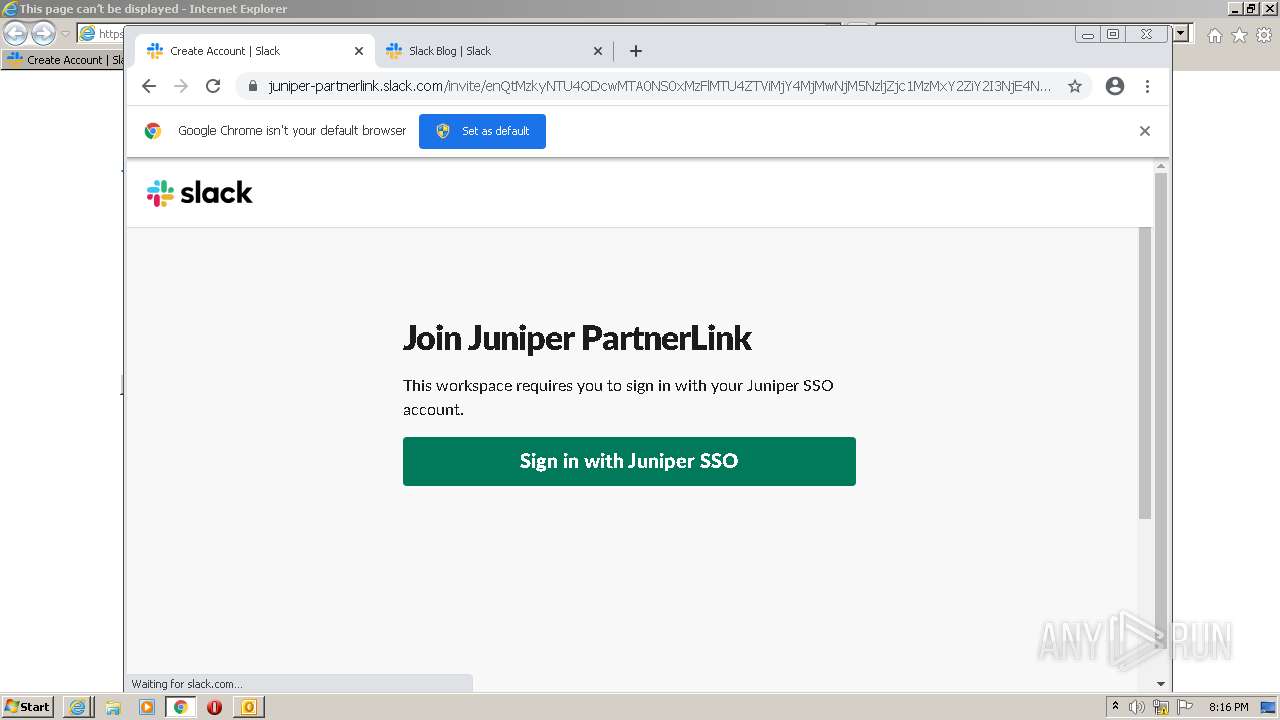
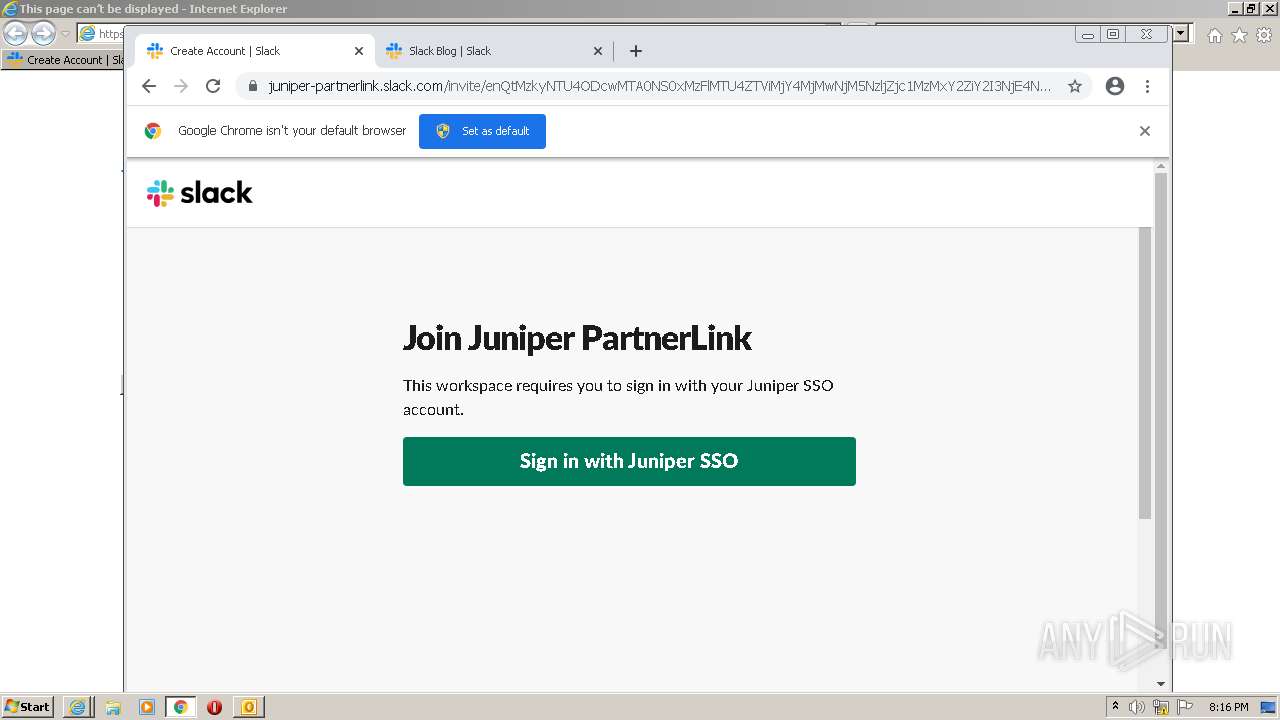
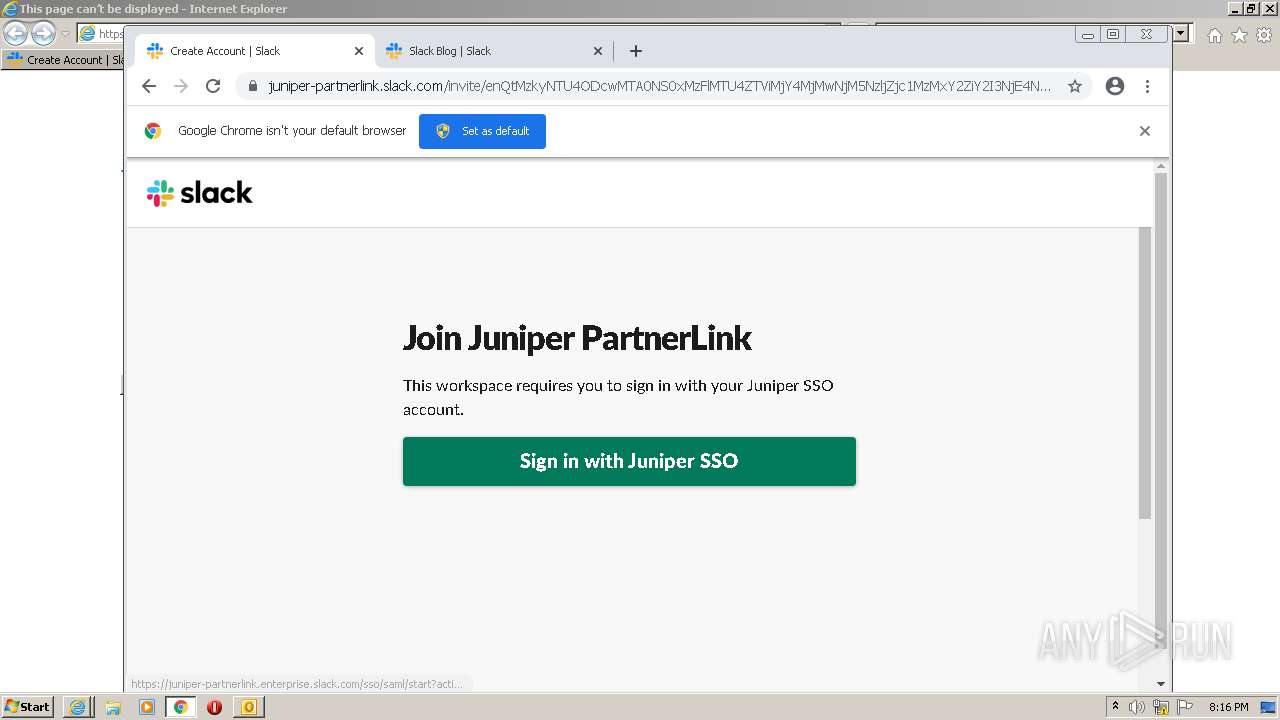
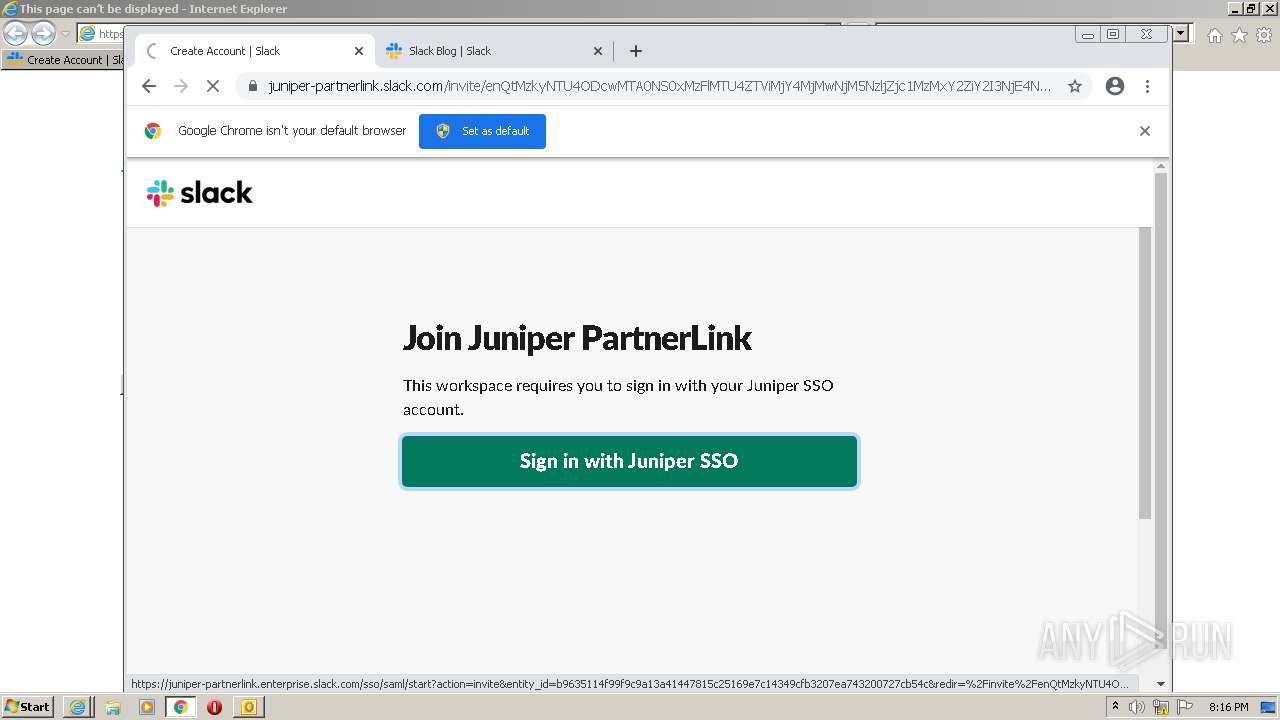
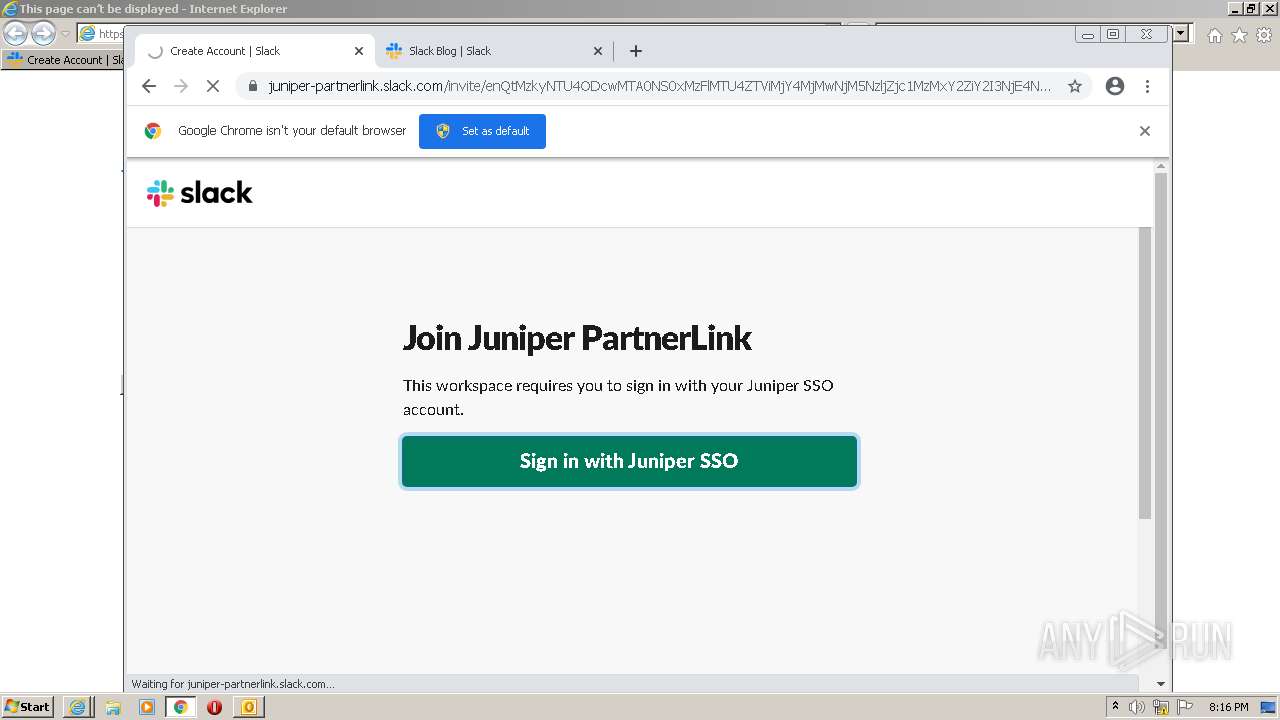
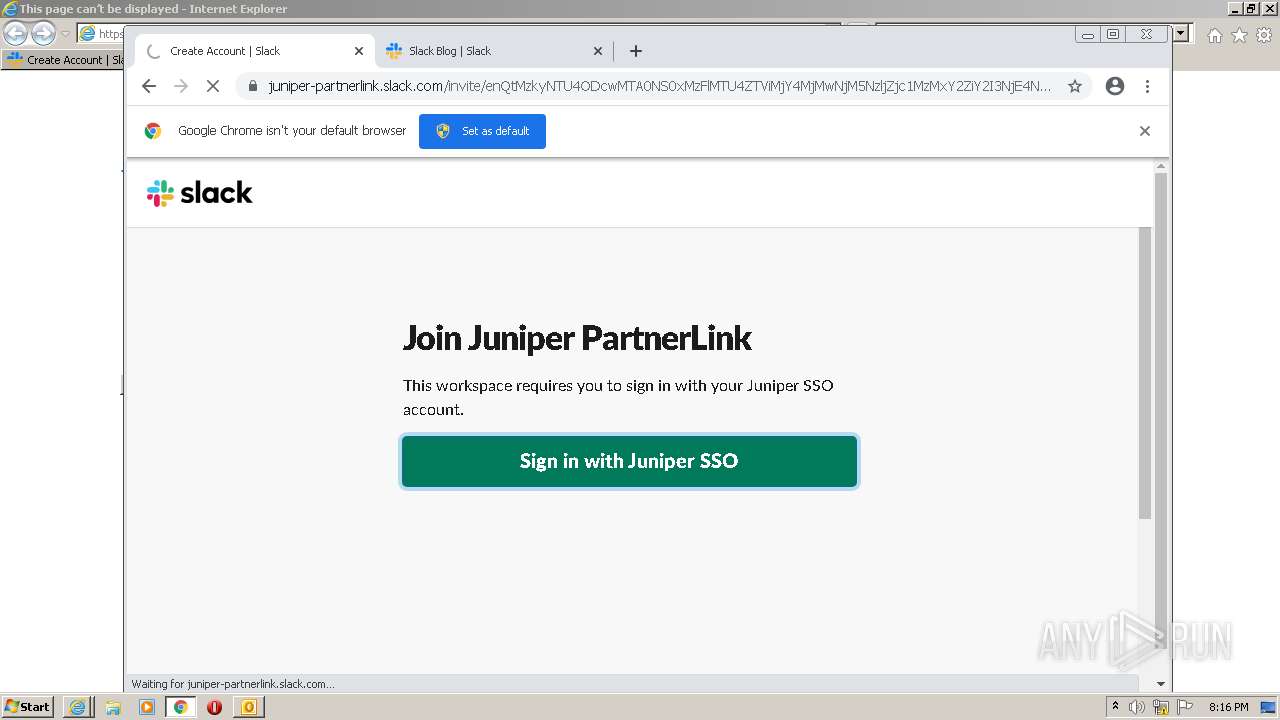
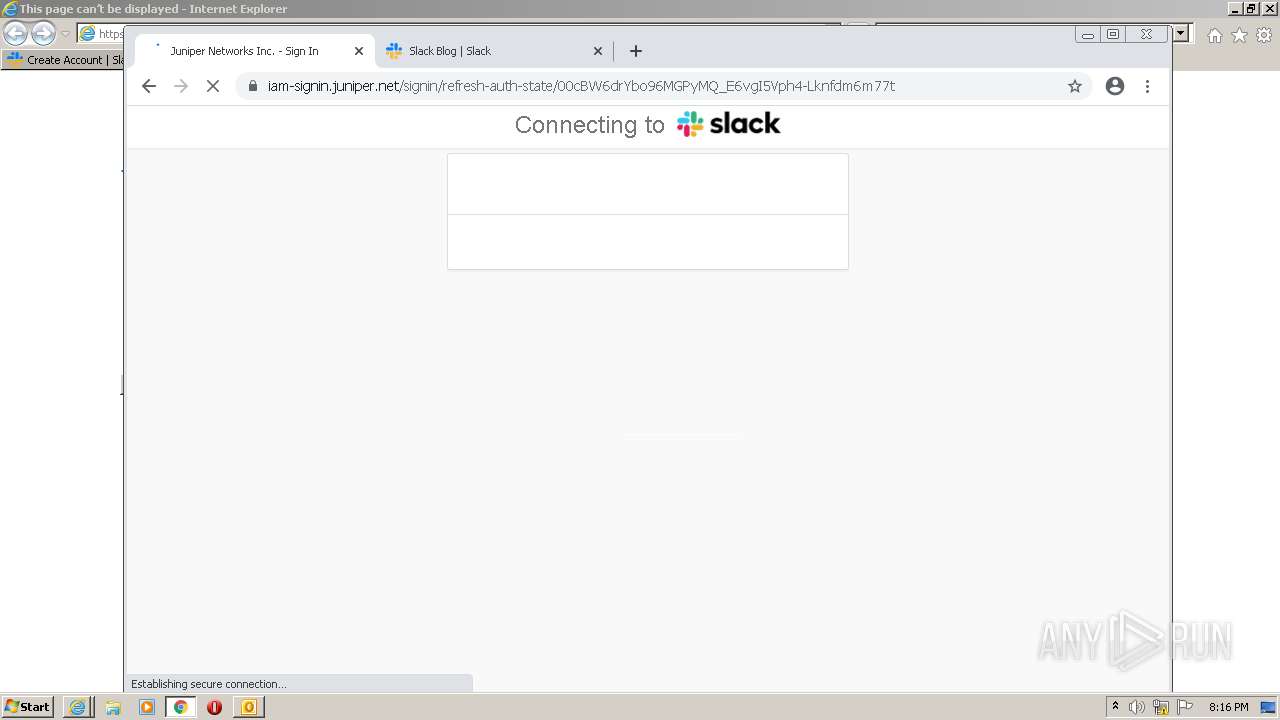
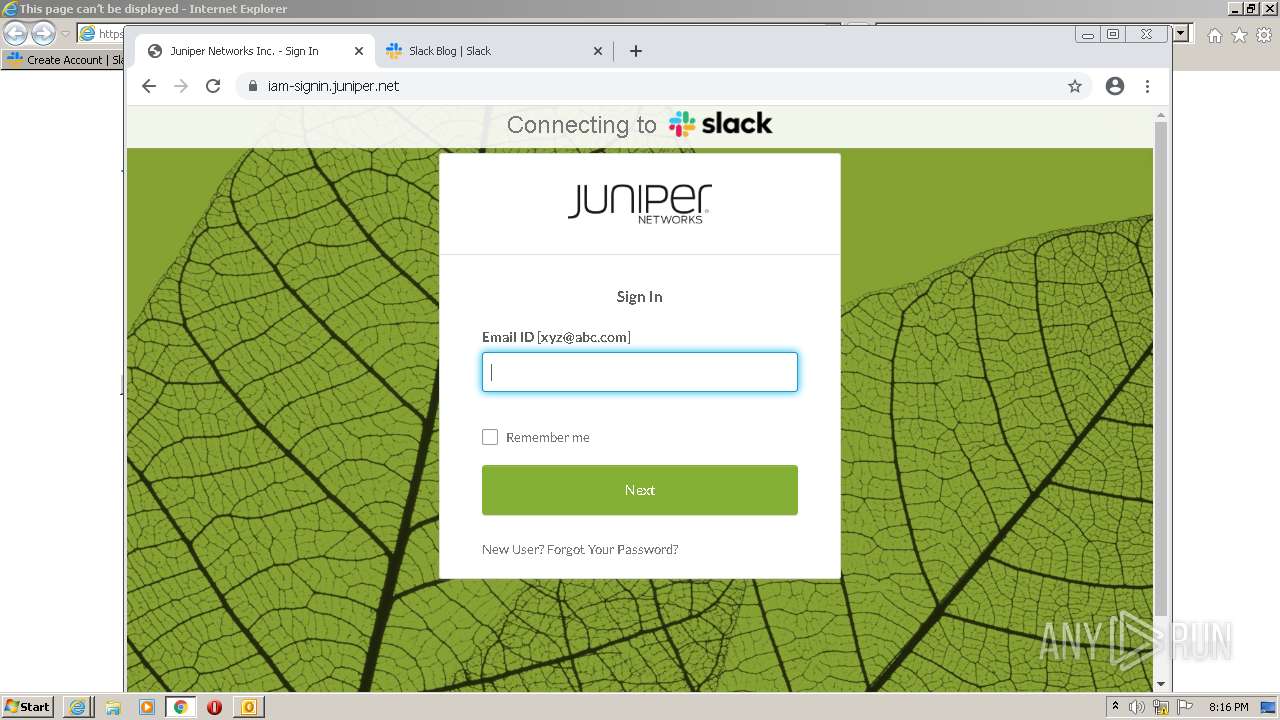
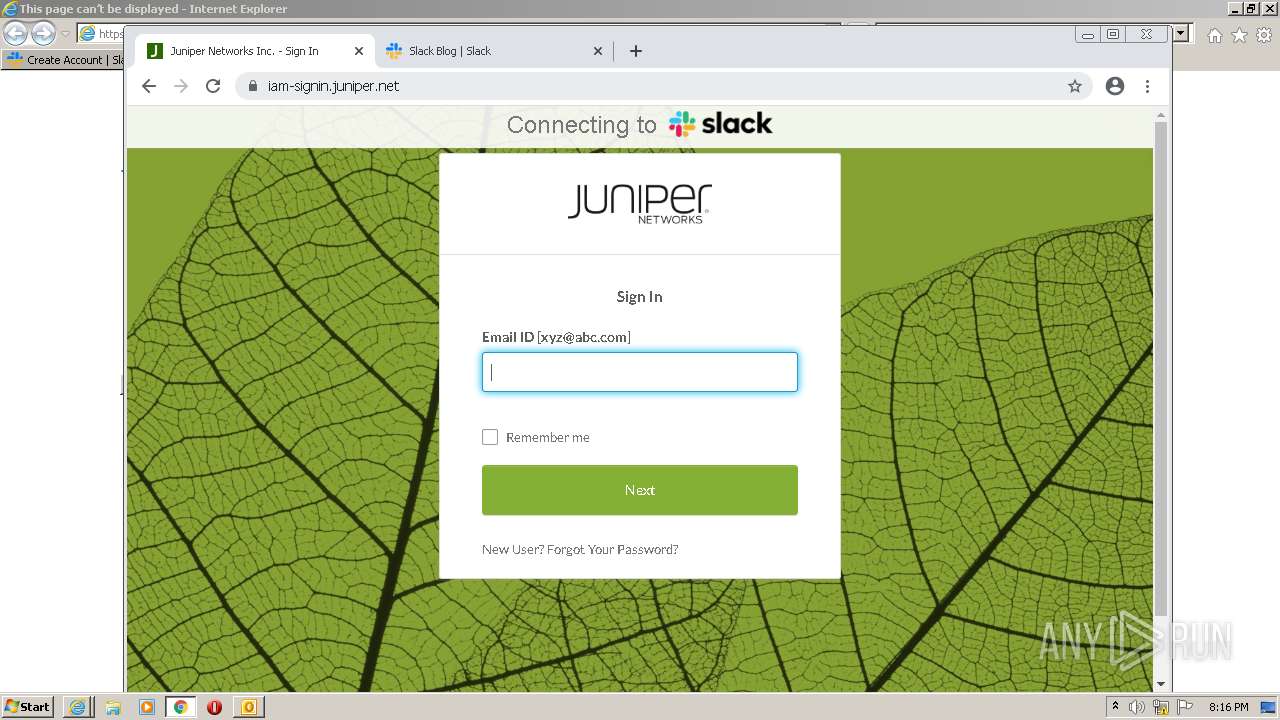
4044 | iexplore.exe | 3.68.124.168:443 | juniper-partnerlink.slack.com | — | US | unknown |
3232 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4044 | iexplore.exe | 13.224.189.39:443 | a.slack-edge.com | — | US | suspicious |
4044 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3232 | iexplore.exe | 13.107.21.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
4044 | iexplore.exe | 18.159.197.225:443 | juniper-partnerlink.slack.com | Massachusetts Institute of Technology | US | unknown |
4044 | iexplore.exe | 13.225.84.13:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
juniper-partnerlink.slack.com |
| unknown |
a.slack-edge.com |
| whitelisted |