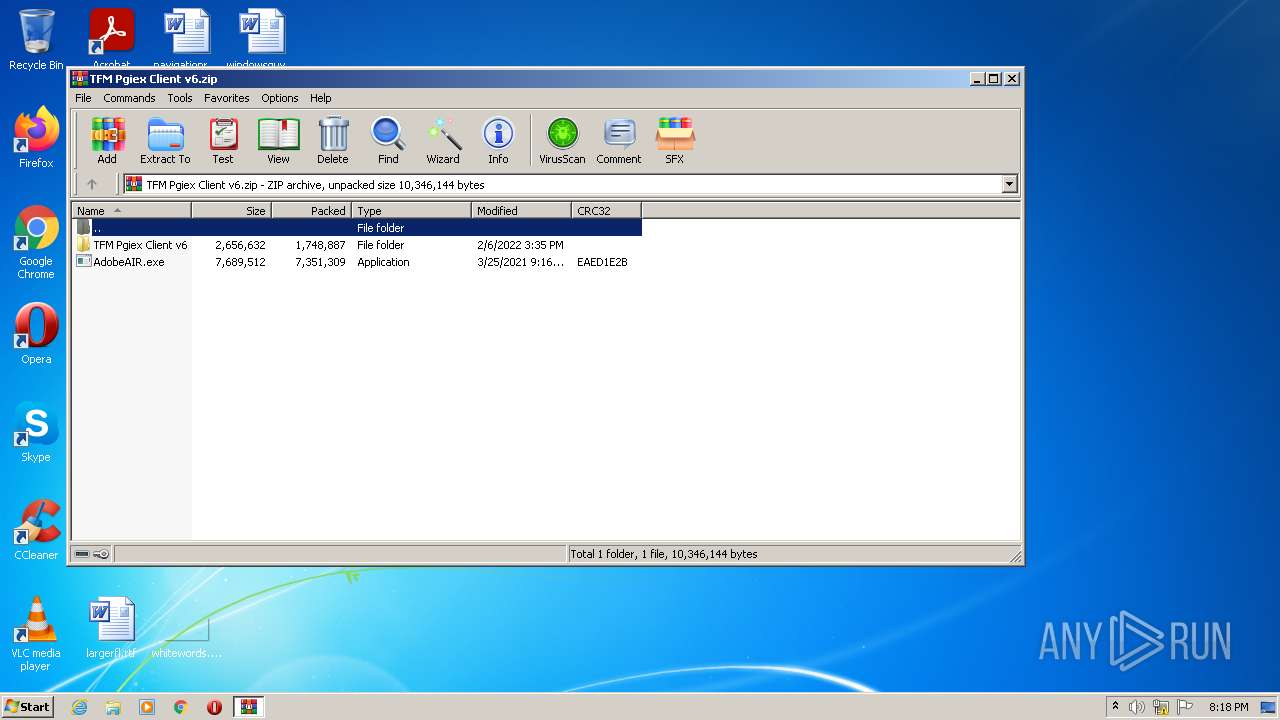
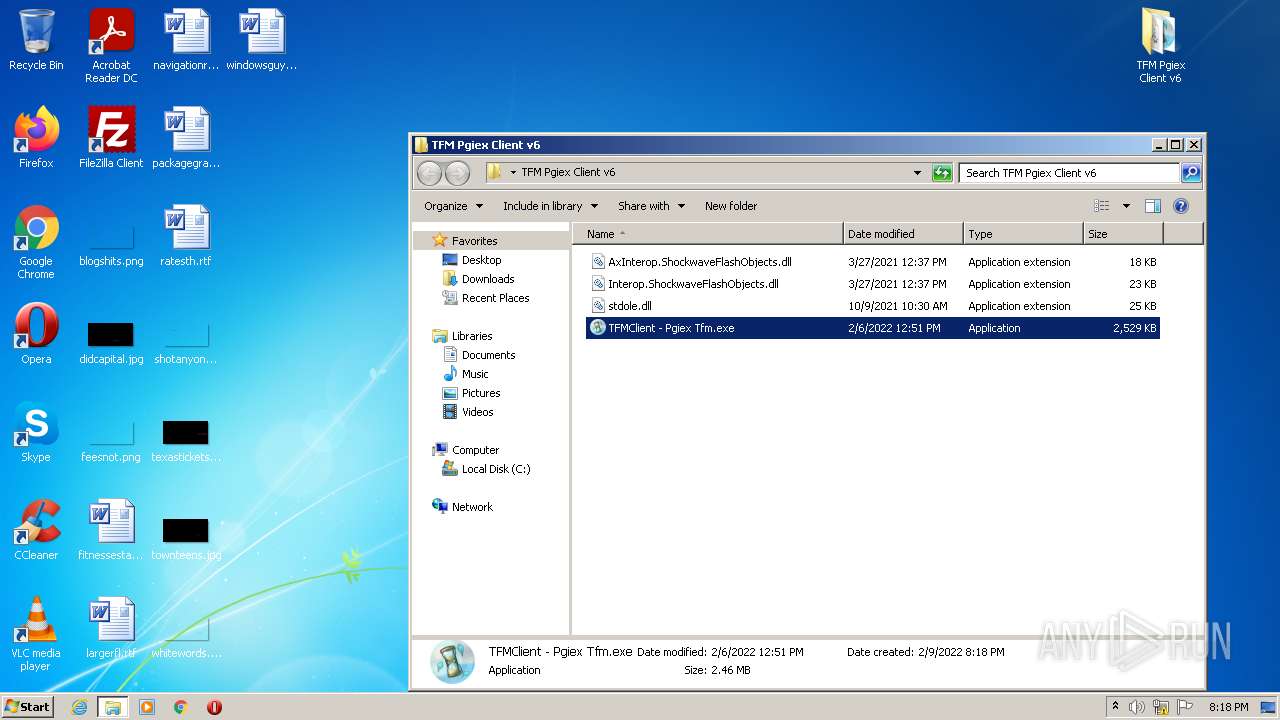
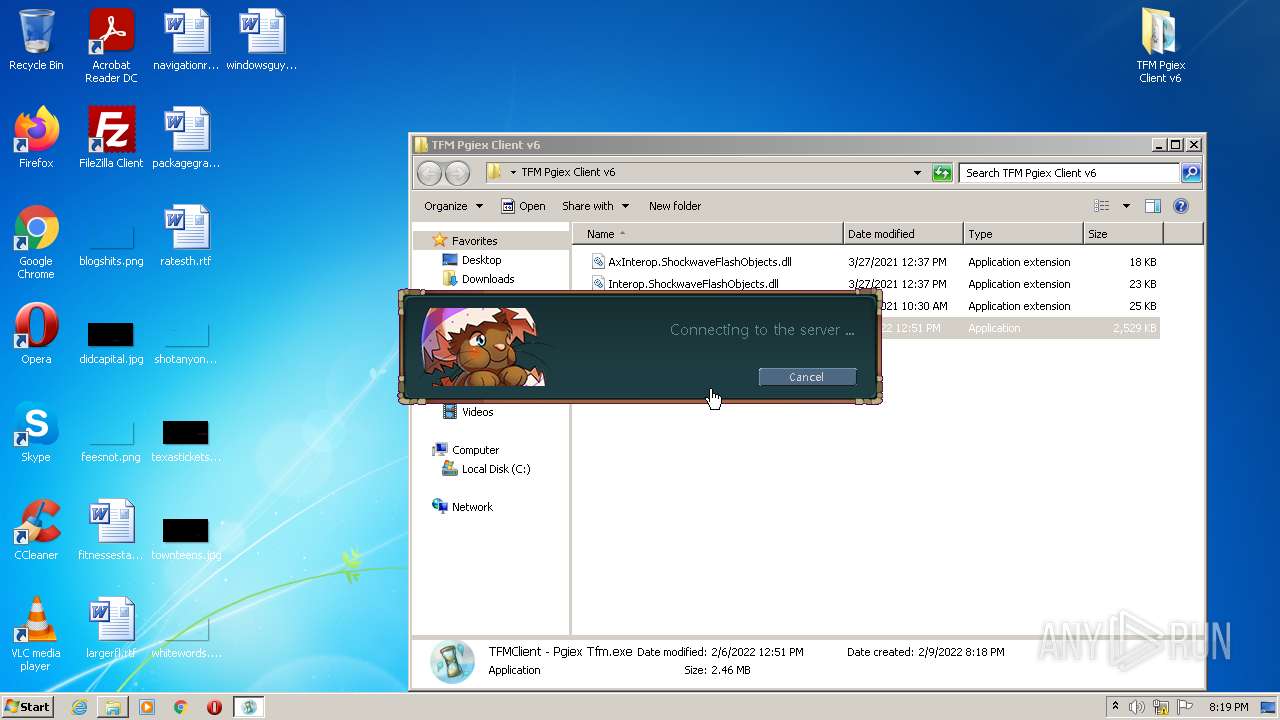
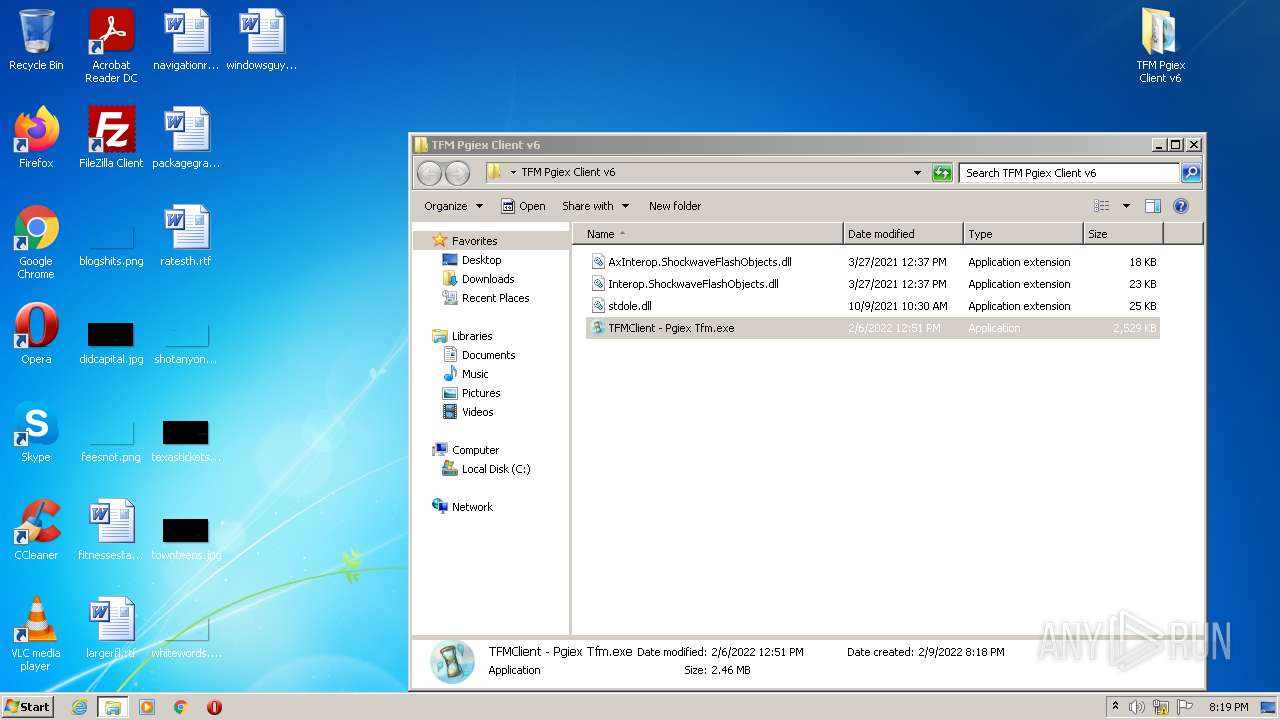
| File name: | TFM Pgiex Client v6.zip |
| Full analysis: | https://app.any.run/tasks/07190481-4117-4fbe-b42a-4733ff81d40e |
| Verdict: | Malicious activity |
| Analysis date: | February 09, 2022, 20:18:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | CDBB36E31429222672198D13FA2ECF09 |
| SHA1: | 77310F77ACF474E8A2A2BFD55461EA4C7F6BAF32 |
| SHA256: | 23F9B243882F95EB2FB6EEA5DE1E63658F2395823F927568D50AAC8AEA8ACF35 |
| SSDEEP: | 196608:K6fZOUWT7cKSUFP94Vntzu2FT6Brx/33R4ikdV/20kRsgLlYRKCnnnphKlb3WZa5:KD7nSUFUnRpFeB9p4ljlktLlYQ6gWZuv |
MALICIOUS
Application was dropped or rewritten from another process
- TFMClient - Pgiex Tfm.exe (PID: 1028)
- TFMClient - Pgiex Tfm.exe (PID: 4056)
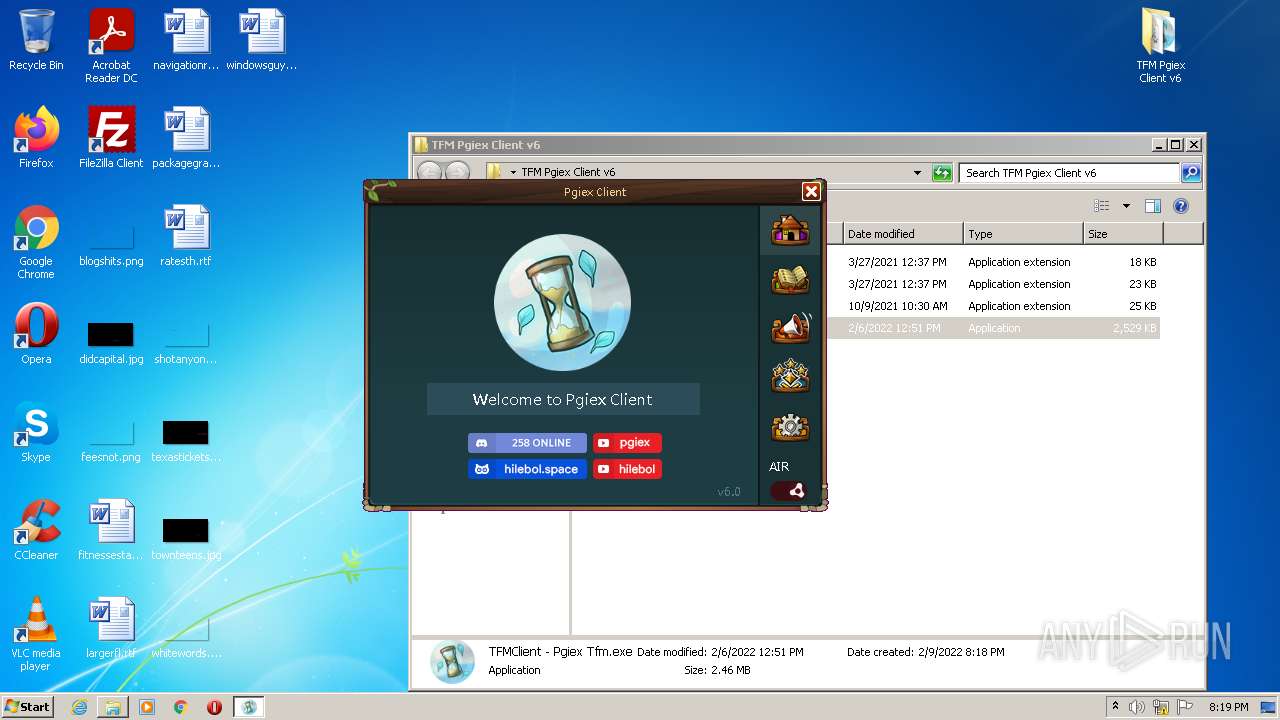
- Pgiex - Transformice SWF Updater.exe (PID: 2200)
Loads dropped or rewritten executable
- TFMClient - Pgiex Tfm.exe (PID: 1028)
- TFMClient - Pgiex Tfm.exe (PID: 4056)
- SearchProtocolHost.exe (PID: 3912)
SUSPICIOUS
Reads the computer name
- TFMClient - Pgiex Tfm.exe (PID: 1028)
- WinRAR.exe (PID: 3860)
- TFMClient - Pgiex Tfm.exe (PID: 4056)
- Pgiex - Transformice SWF Updater.exe (PID: 2200)
Application launched itself
- TFMClient - Pgiex Tfm.exe (PID: 4056)
Reads Environment values
- TFMClient - Pgiex Tfm.exe (PID: 4056)
- TFMClient - Pgiex Tfm.exe (PID: 1028)
- Pgiex - Transformice SWF Updater.exe (PID: 2200)
Checks supported languages
- TFMClient - Pgiex Tfm.exe (PID: 4056)
- TFMClient - Pgiex Tfm.exe (PID: 1028)
- WinRAR.exe (PID: 3860)
- Pgiex - Transformice SWF Updater.exe (PID: 2200)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3860)
Drops a file with too old compile date
- WinRAR.exe (PID: 3860)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3860)
- TFMClient - Pgiex Tfm.exe (PID: 1028)
Drops a file that was compiled in debug mode
- TFMClient - Pgiex Tfm.exe (PID: 1028)
INFO
Manual execution by user
- TFMClient - Pgiex Tfm.exe (PID: 4056)
Reads settings of System Certificates
- TFMClient - Pgiex Tfm.exe (PID: 1028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | AdobeAIR.exe |
|---|---|
| ZipUncompressedSize: | 7689512 |
| ZipCompressedSize: | 7351309 |
| ZipCRC: | 0xeaed1e2b |
| ZipModifyDate: | 2021:03:25 12:16:14 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
38
Monitored processes
5
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
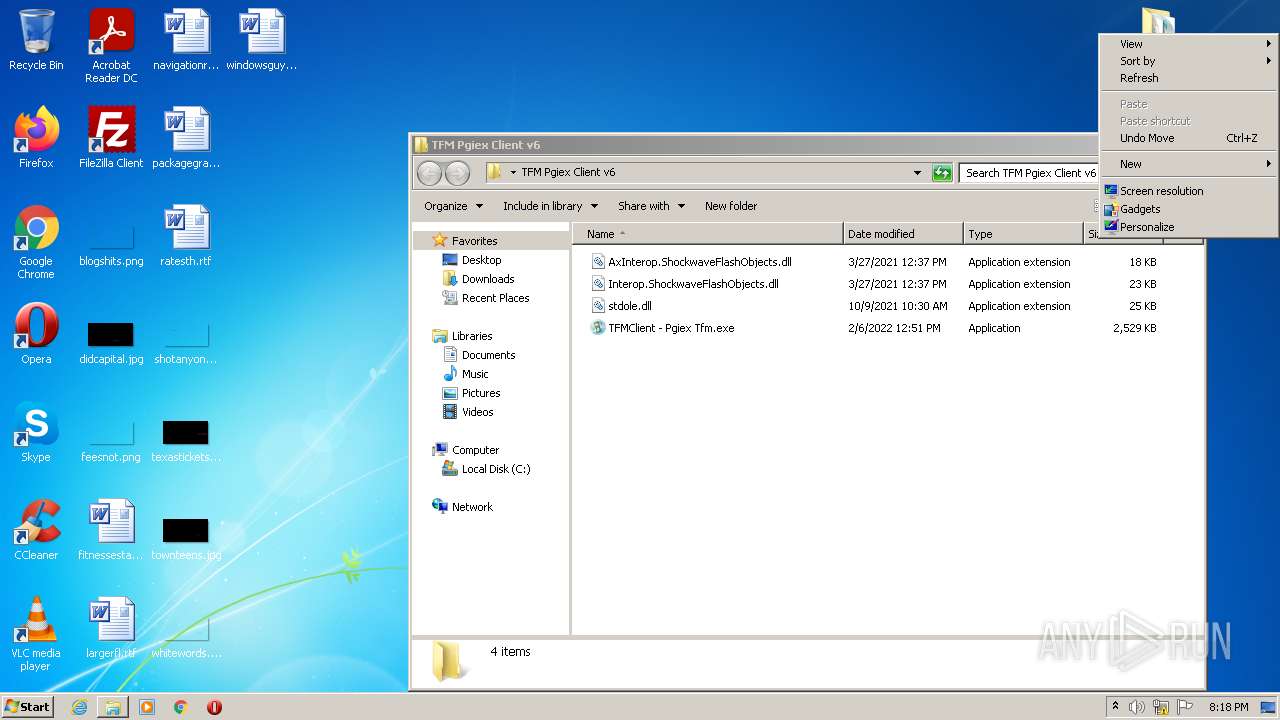
| 1028 | "C:\Users\admin\Desktop\TFM Pgiex Client v6\TFMClient - Pgiex Tfm.exe" | C:\Users\admin\Desktop\TFM Pgiex Client v6\TFMClient - Pgiex Tfm.exe | TFMClient - Pgiex Tfm.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: TFMClient - Pgiex Tfm Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2200 | "C:\0464a1aa-c46e-4971-b372-e53b0d85ac22\Pgiex - Transformice SWF Updater.exe" | C:\0464a1aa-c46e-4971-b372-e53b0d85ac22\Pgiex - Transformice SWF Updater.exe | TFMClient - Pgiex Tfm.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Pgiex - Transformice SWF Updater Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3860 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\TFM Pgiex Client v6.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3912 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 4056 | "C:\Users\admin\Desktop\TFM Pgiex Client v6\TFMClient - Pgiex Tfm.exe" | C:\Users\admin\Desktop\TFM Pgiex Client v6\TFMClient - Pgiex Tfm.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Description: TFMClient - Pgiex Tfm Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
7 261
Read events
7 182
Write events
79
Delete events
0
Modification events
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\TFM Pgiex Client v6.zip | |||
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3860) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
6
Suspicious files
3
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1028 | TFMClient - Pgiex Tfm.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 1028 | TFMClient - Pgiex Tfm.exe | C:\Users\admin\AppData\Local\Beds-Protector-rown-Fox??\TFMClient_-_Pgiex_Tfm.exe_Url_5sycvndflsf4lpm5vusrhru4htisfras\1.0.0.0\wqtec4e5.newcfg | xml | |
MD5:— | SHA256:— | |||
| 1028 | TFMClient - Pgiex Tfm.exe | C:\Users\admin\AppData\Local\Beds-Protector-rown-Fox??\TFMClient_-_Pgiex_Tfm.exe_Url_5sycvndflsf4lpm5vusrhru4htisfras\1.0.0.0\user.config | xml | |
MD5:— | SHA256:— | |||
| 3860 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3860.9040\TFM Pgiex Client v6\stdole.dll | executable | |
MD5:09AB7545A93B78612AE74D806CF9A07C | SHA256:DA76CB7FF44B8560547A3E578C18F158FBBABB19B82AE41B282F47801277EF49 | |||
| 3860 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3860.9040\TFM Pgiex Client v6\AxInterop.ShockwaveFlashObjects.dll | executable | |
MD5:FC5755937BEFDD2E722983245E9E20F4 | SHA256:1593EEB11FA3CC777E4357EFD0BB2BE65C74A54DAAA499BBA651AEFE221579F1 | |||
| 1028 | TFMClient - Pgiex Tfm.exe | C:\Users\admin\AppData\Local\Temp\Tar5AF5.tmp | cat | |
MD5:D99661D0893A52A0700B8AE68457351A | SHA256:BDD5111162A6FA25682E18FA74E37E676D49CAFCB5B7207E98E5256D1EF0D003 | |||
| 1028 | TFMClient - Pgiex Tfm.exe | C:\Users\admin\AppData\Local\Temp\Cab5AF4.tmp | compressed | |
MD5:ACAEDA60C79C6BCAC925EEB3653F45E0 | SHA256:6B0CECCF0103AFD89844761417C1D23ACC41F8AEBF3B7230765209B61EEE5658 | |||
| 1028 | TFMClient - Pgiex Tfm.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:ACAEDA60C79C6BCAC925EEB3653F45E0 | SHA256:6B0CECCF0103AFD89844761417C1D23ACC41F8AEBF3B7230765209B61EEE5658 | |||
| 3860 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3860.9040\TFM Pgiex Client v6\Interop.ShockwaveFlashObjects.dll | executable | |
MD5:06A3F066769840D59803A363E4085C18 | SHA256:71F163FDCBF8E488F27005B4AEF2667F94EB6528BEF549B90AB215F50672F3B3 | |||
| 1028 | TFMClient - Pgiex Tfm.exe | C:\0464a1aa-c46e-4971-b372-e53b0d85ac22\Pgiex - Transformice SWF Updater.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
9
DNS requests
6
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1028 | TFMClient - Pgiex Tfm.exe | GET | 200 | 2.16.106.233:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?c0087de96361d0f6 | unknown | compressed | 59.9 Kb | whitelisted |
1028 | TFMClient - Pgiex Tfm.exe | GET | 204 | 172.217.23.110:80 | http://google.com/generate_204 | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2200 | Pgiex - Transformice SWF Updater.exe | 140.82.36.185:443 | bolcorp.icu | — | US | suspicious |
1028 | TFMClient - Pgiex Tfm.exe | 162.159.133.233:443 | discordapp.com | Cloudflare Inc | — | shared |
1028 | TFMClient - Pgiex Tfm.exe | 2.16.106.233:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | whitelisted |
1028 | TFMClient - Pgiex Tfm.exe | 140.82.36.185:443 | bolcorp.icu | — | US | suspicious |
1028 | TFMClient - Pgiex Tfm.exe | 172.217.23.110:80 | google.com | Google Inc. | US | whitelisted |
4056 | TFMClient - Pgiex Tfm.exe | 172.217.23.110:80 | google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| malicious |
dns.msftncsi.com |
| shared |
bolcorp.icu |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
transformice.bolcorp.icu |
| suspicious |
discordapp.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .icu Domain |
1028 | TFMClient - Pgiex Tfm.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.icu) in TLS SNI |
1028 | TFMClient - Pgiex Tfm.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.icu) |
1028 | TFMClient - Pgiex Tfm.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.icu) |
1028 | TFMClient - Pgiex Tfm.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.icu) |