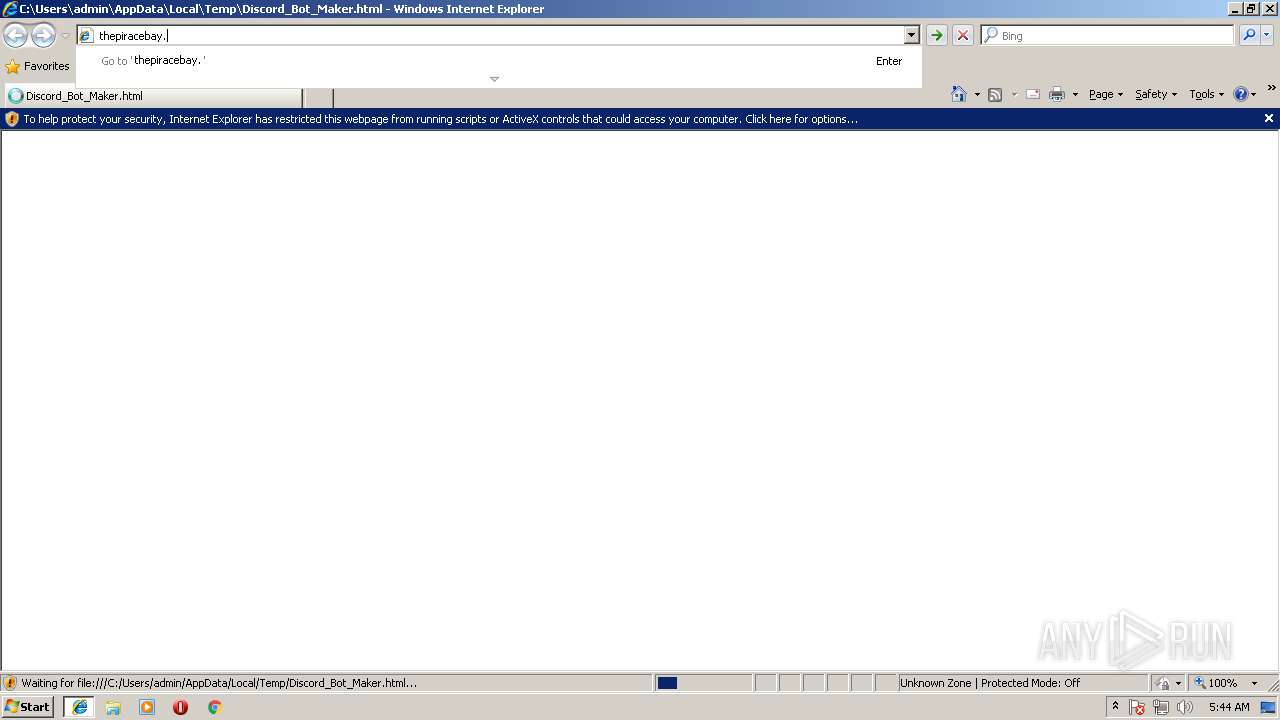
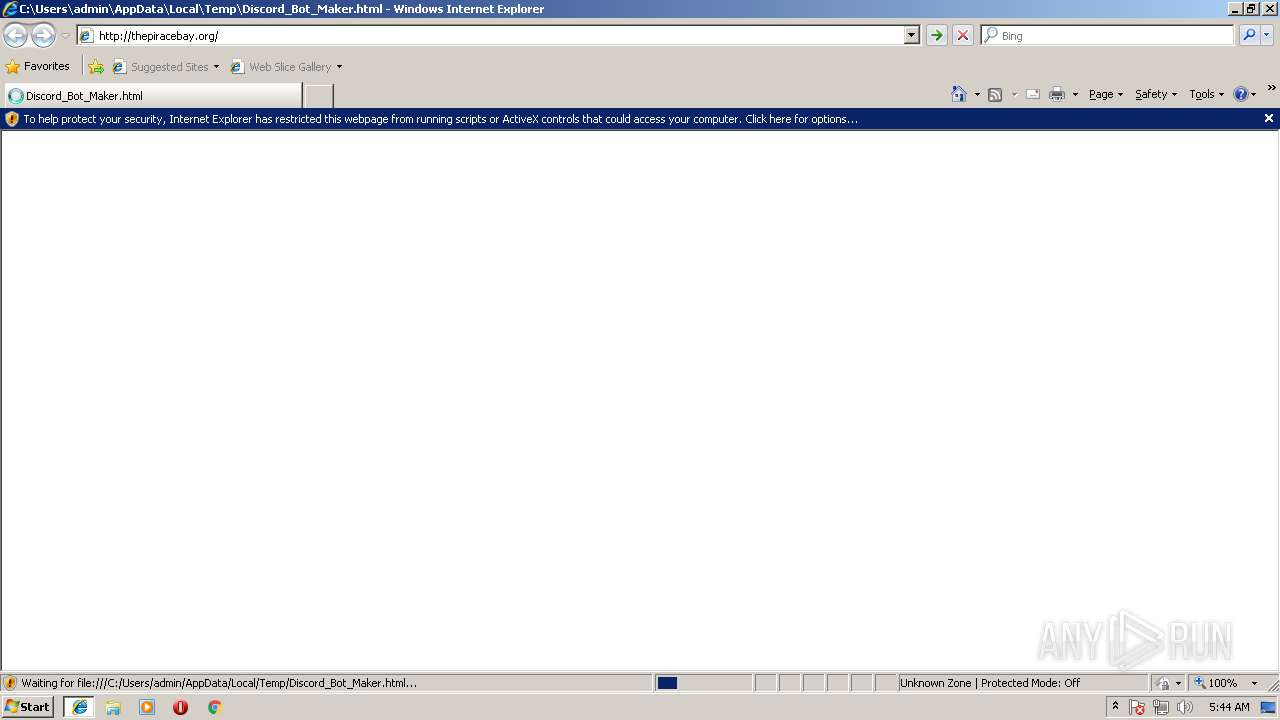
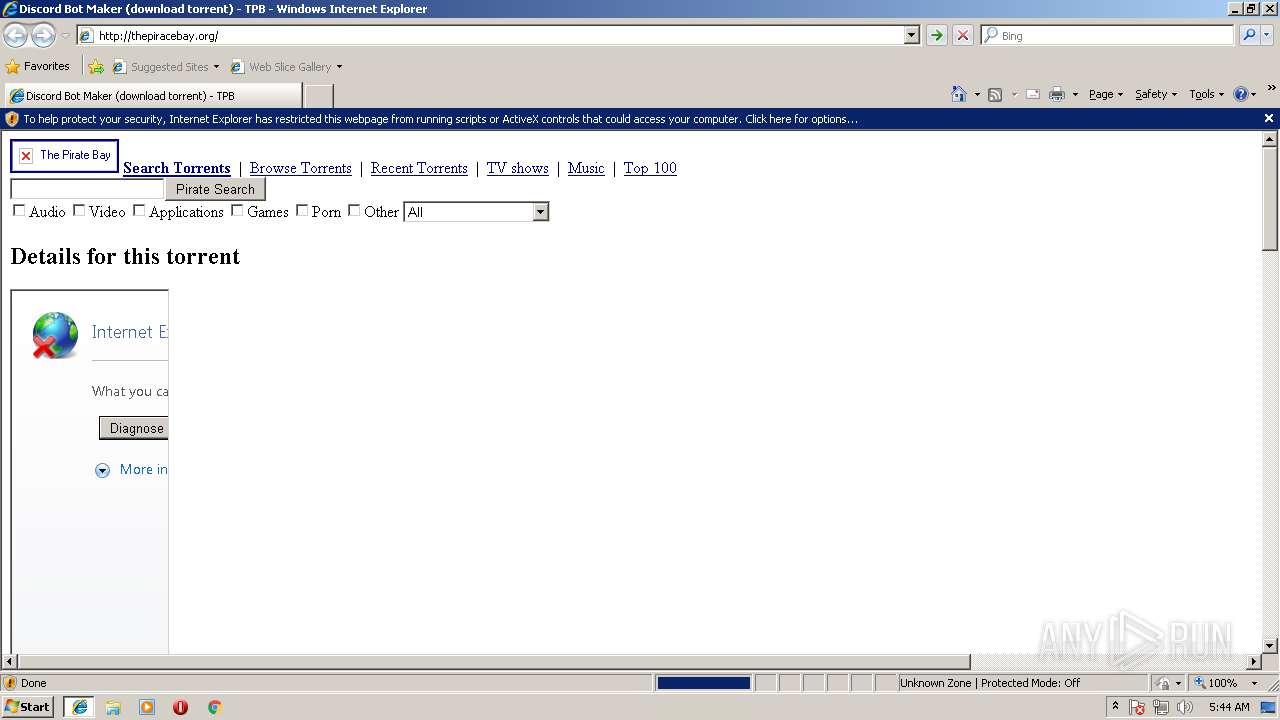
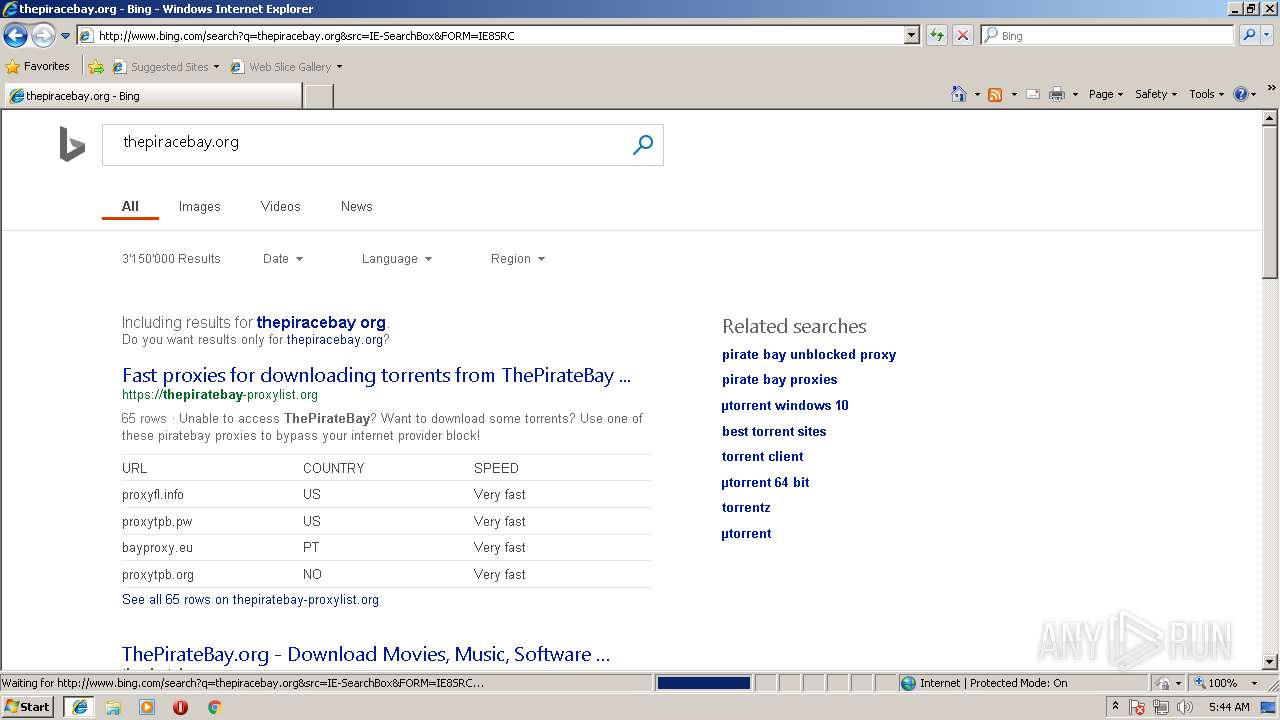
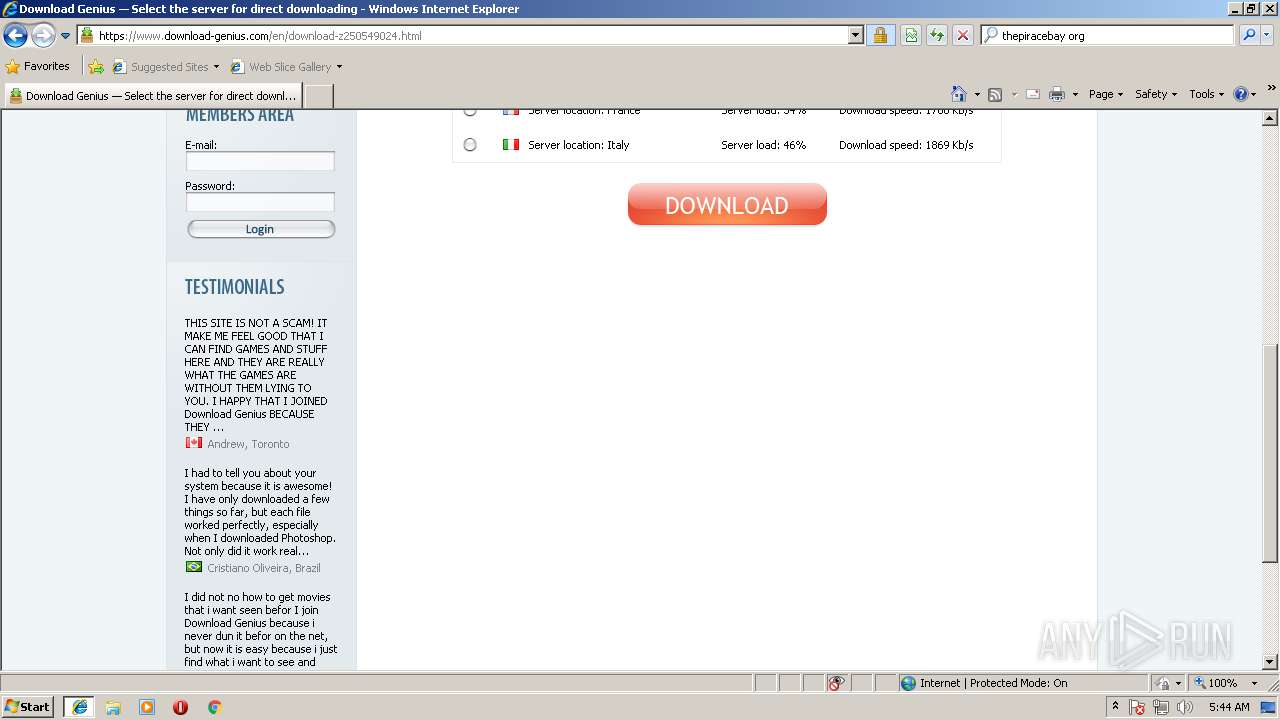
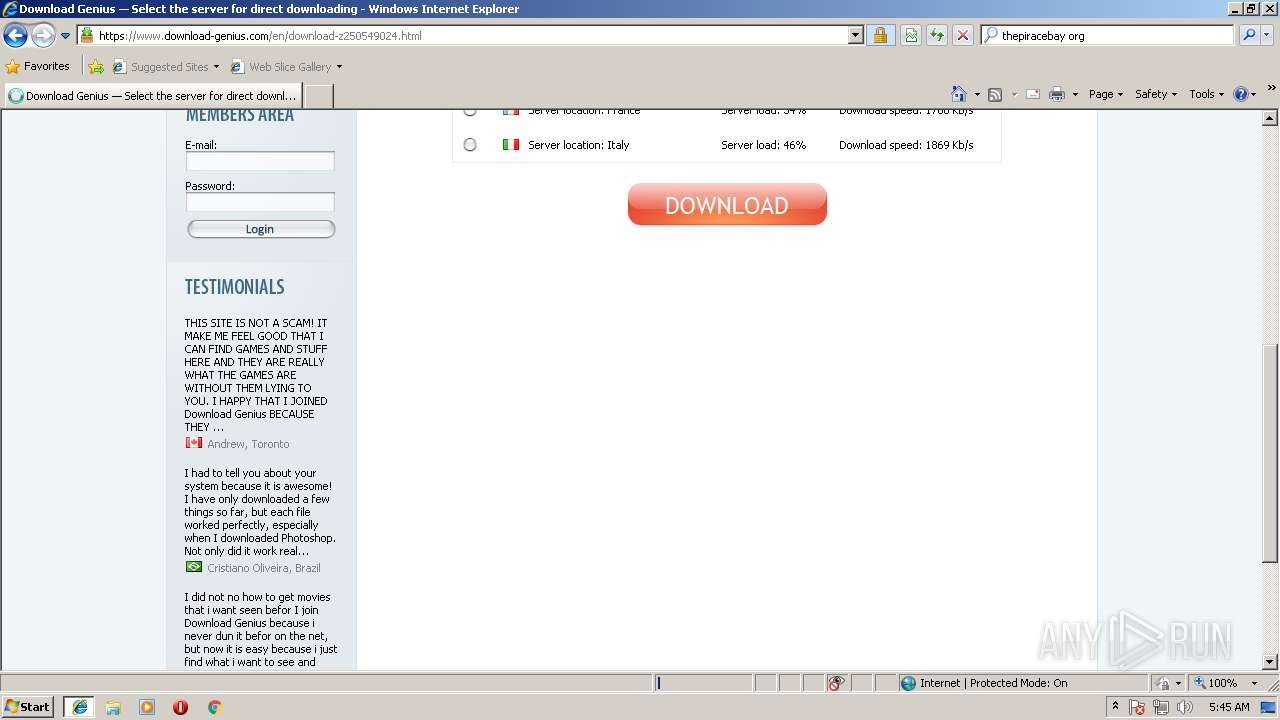
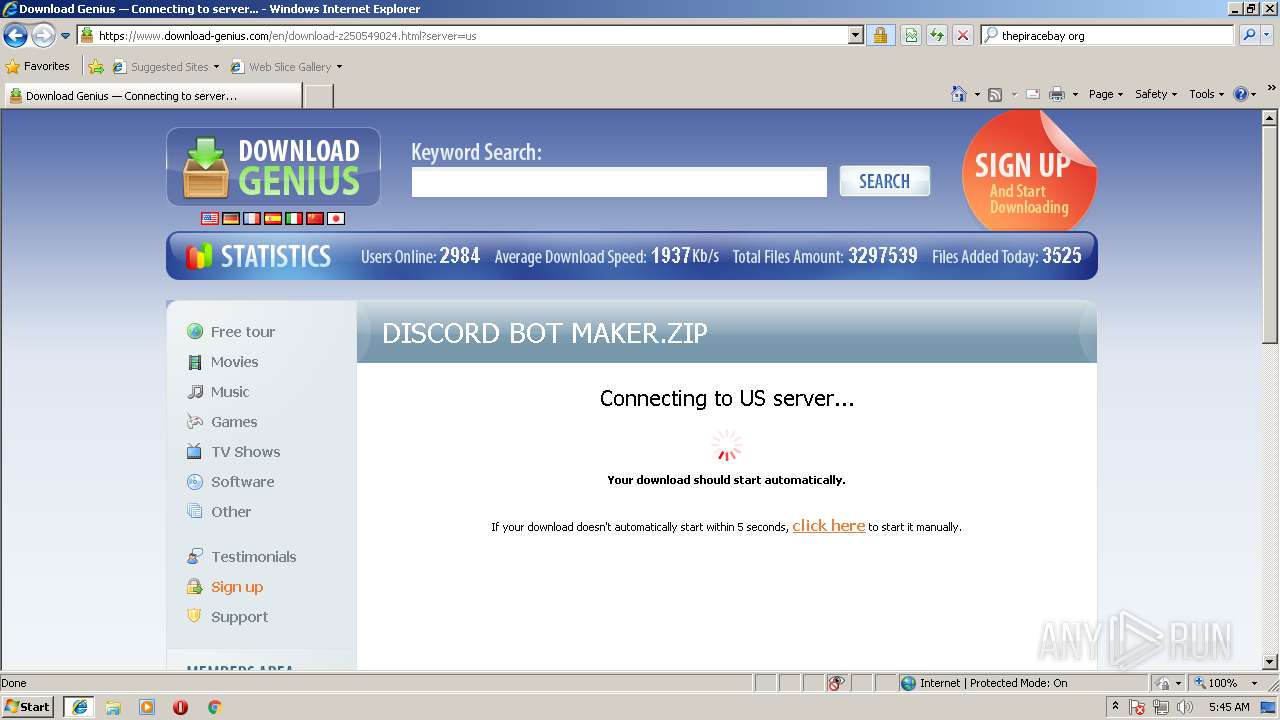
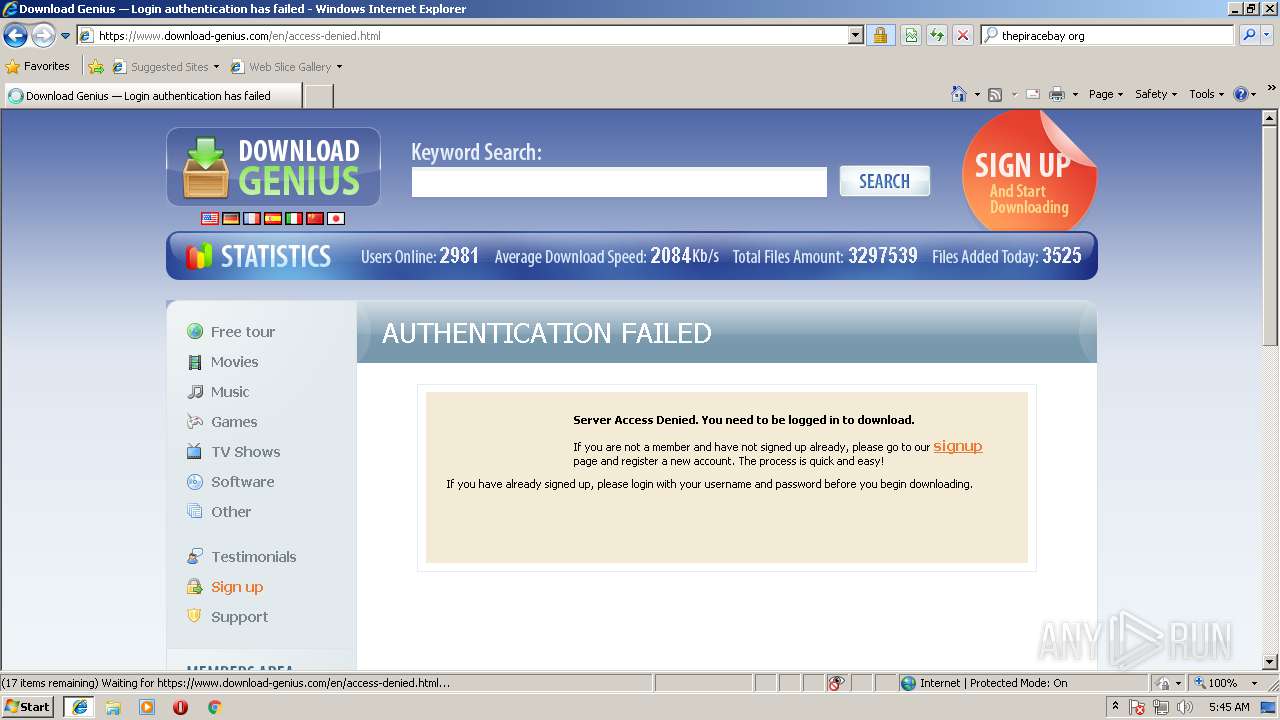
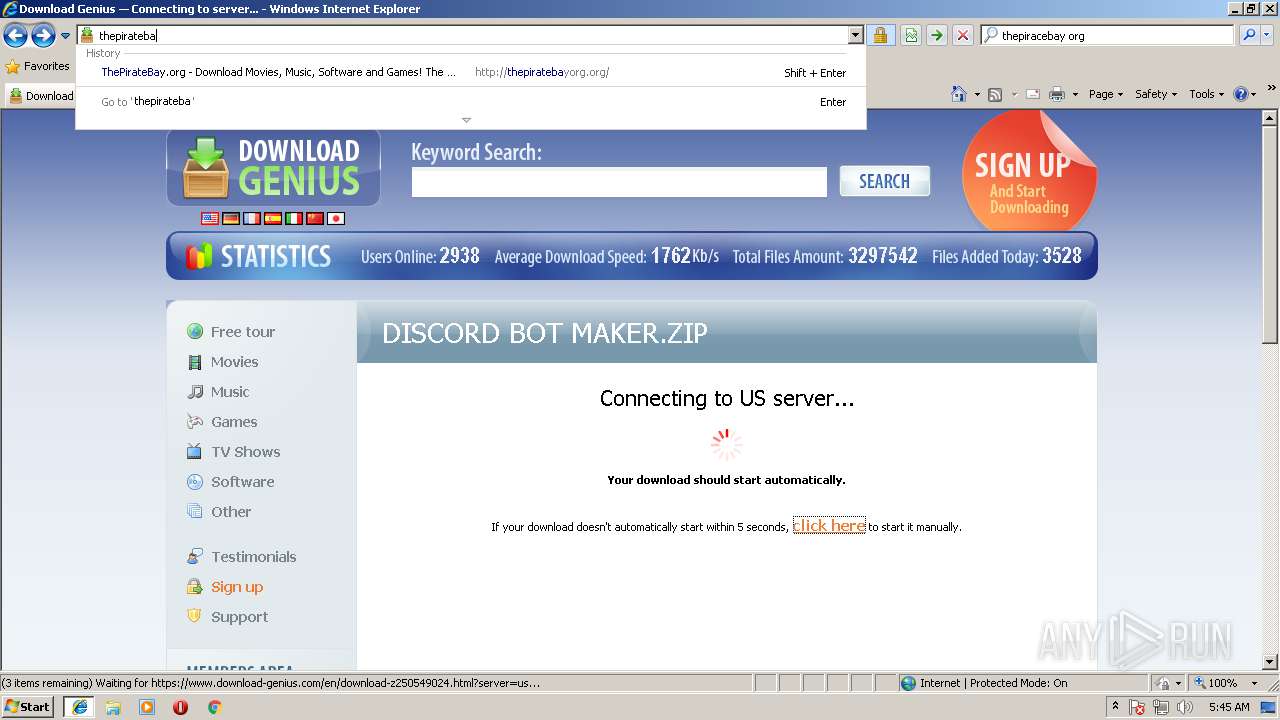
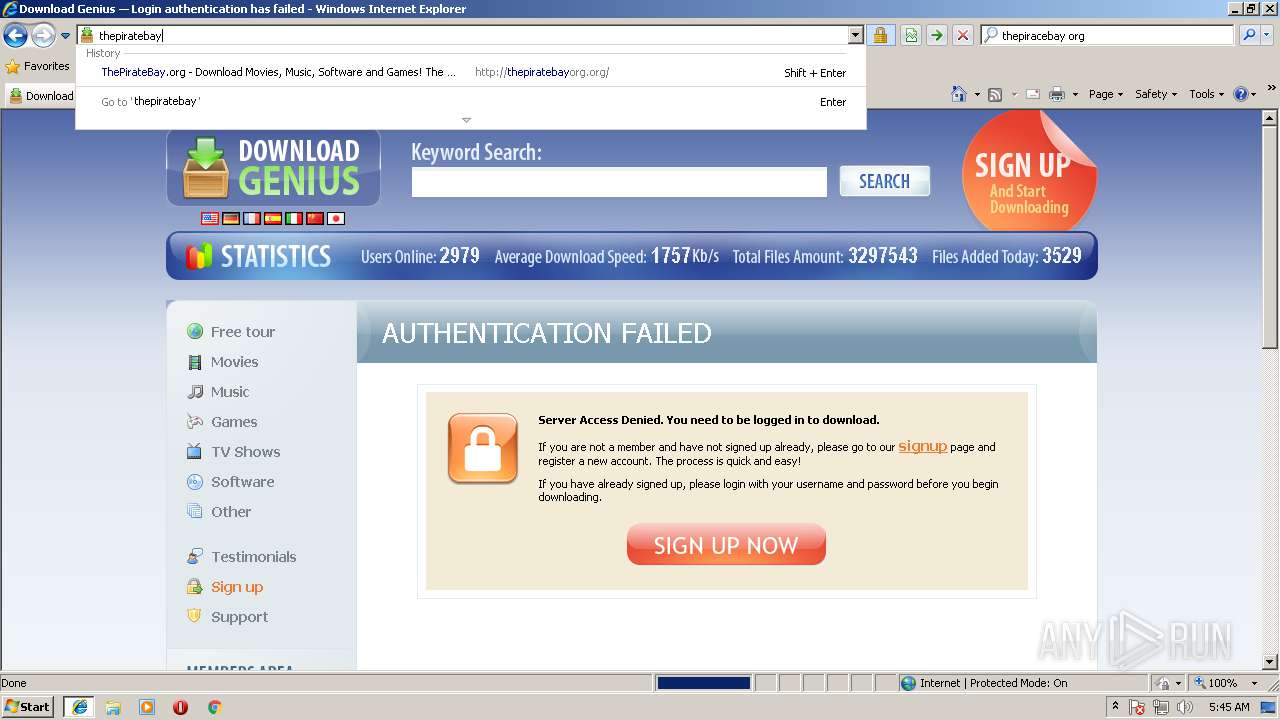
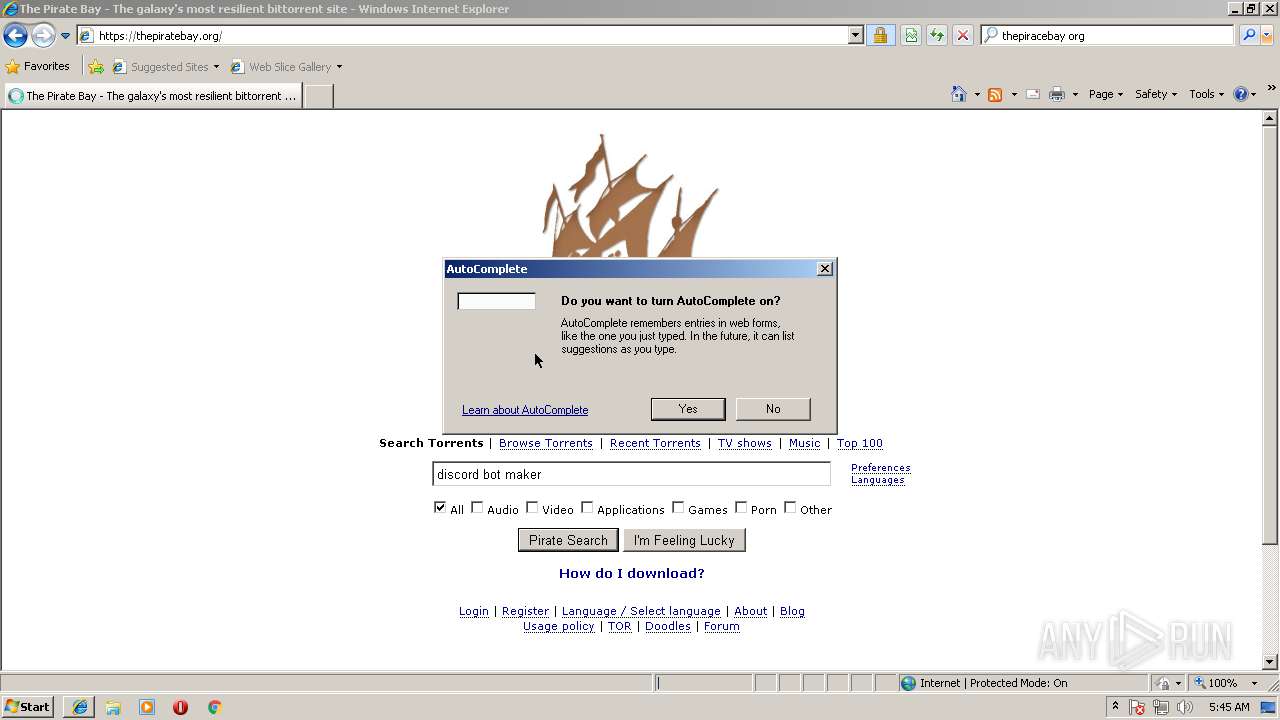
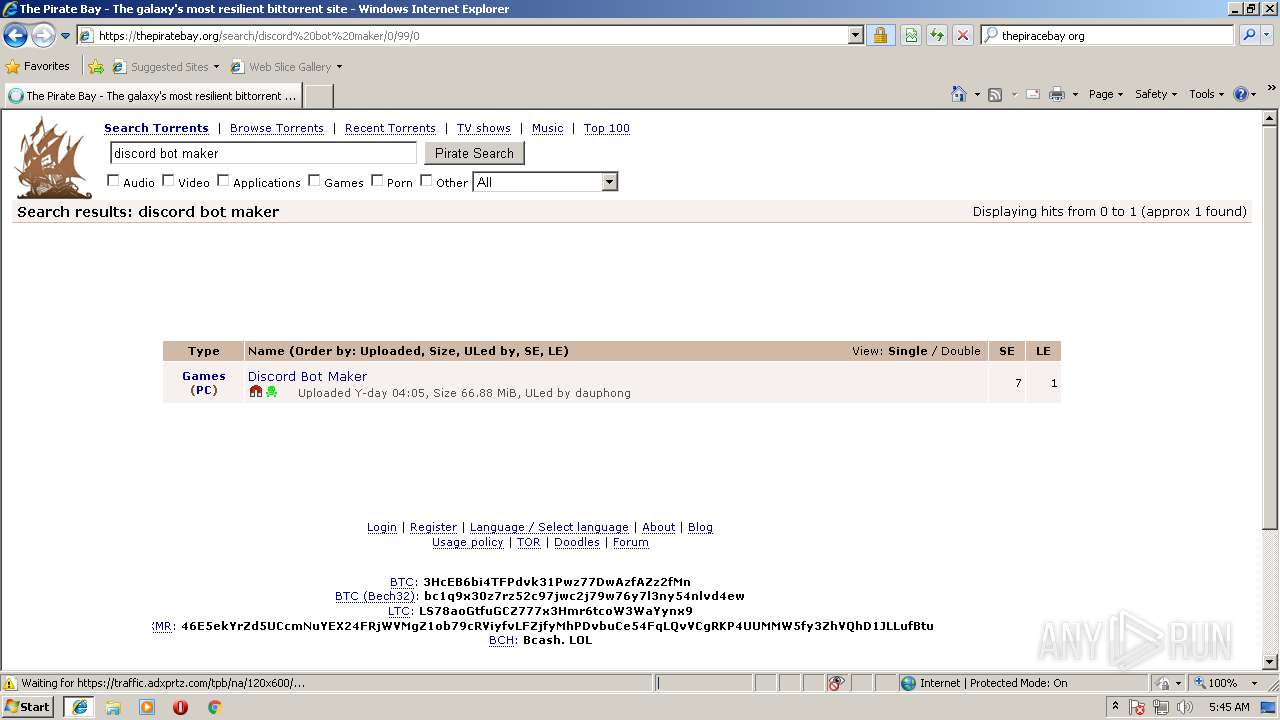
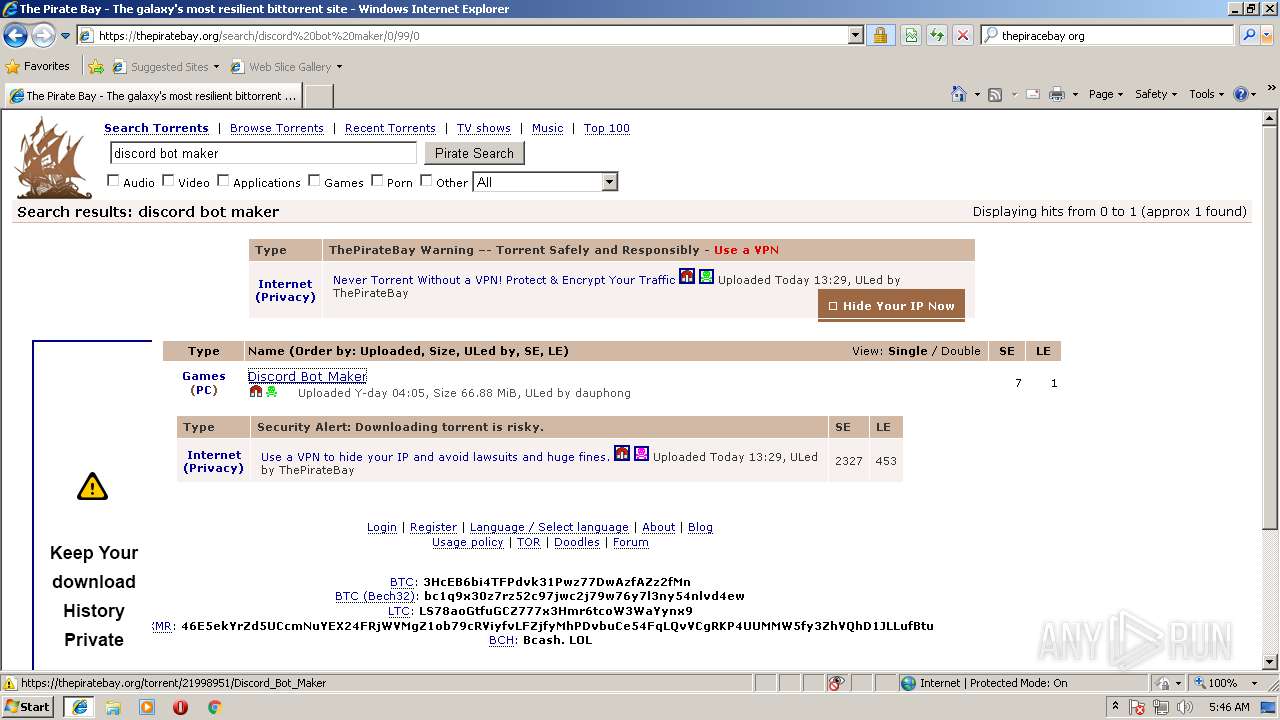
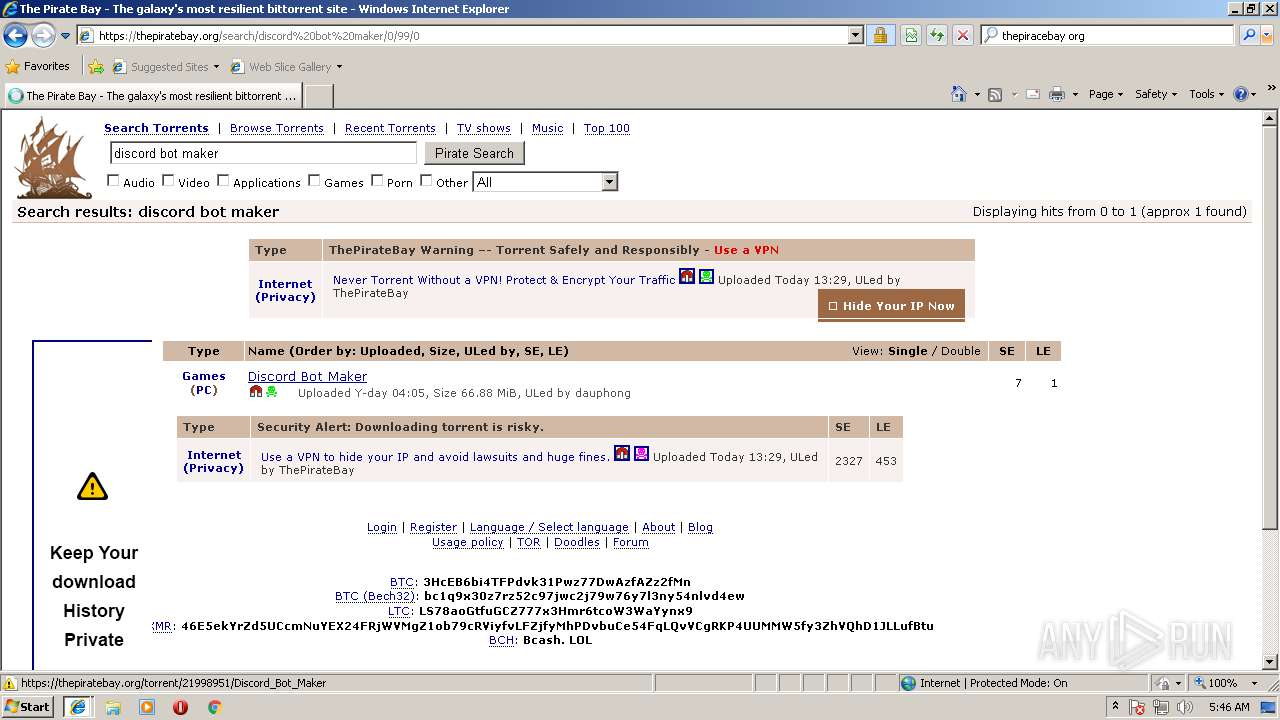
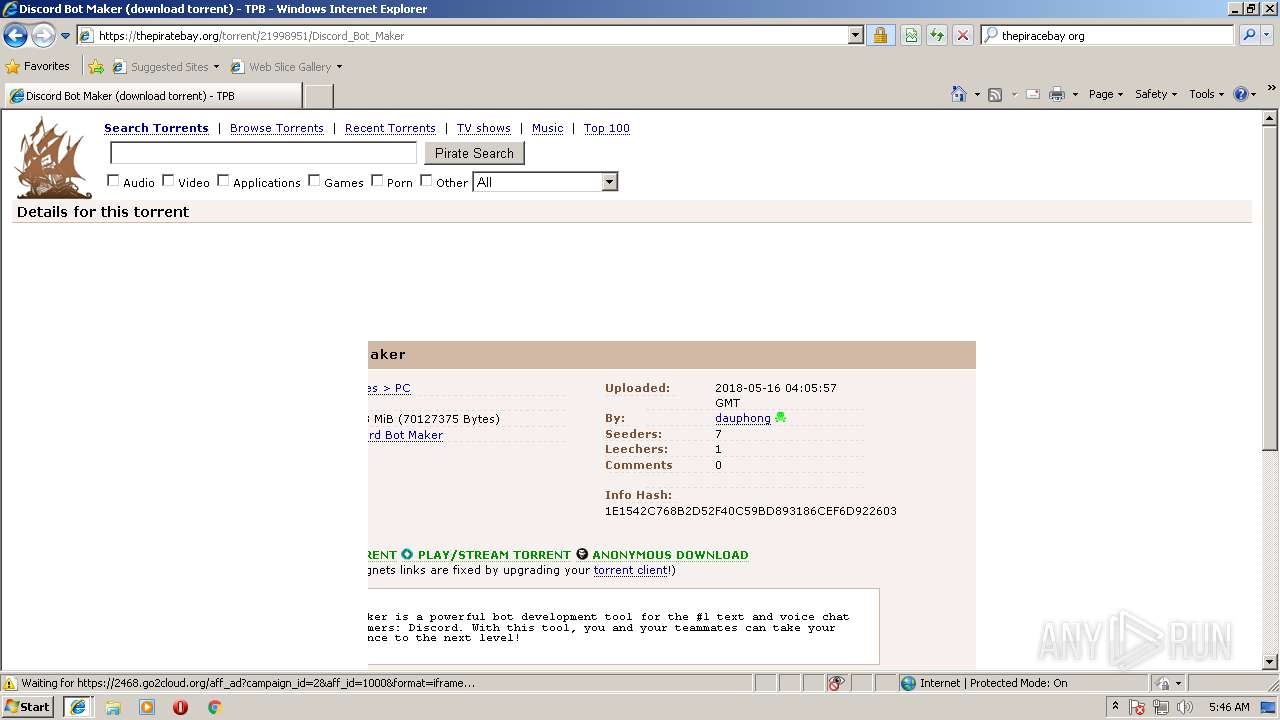
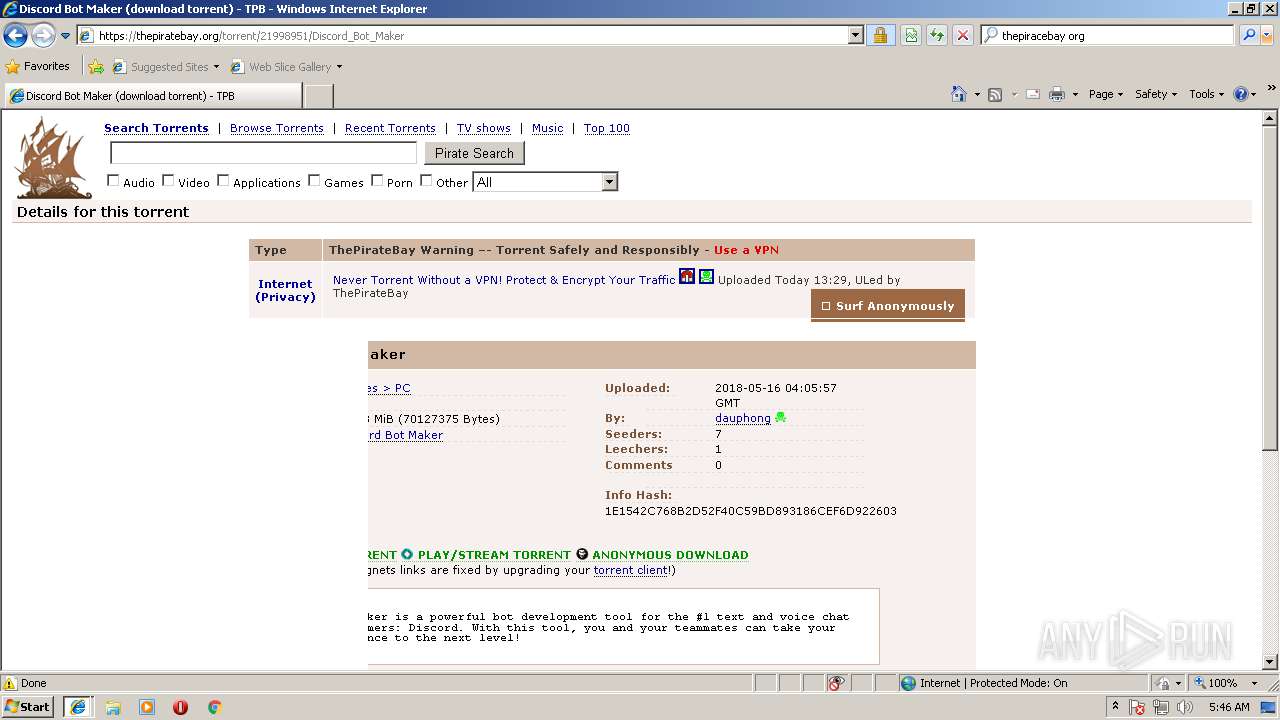
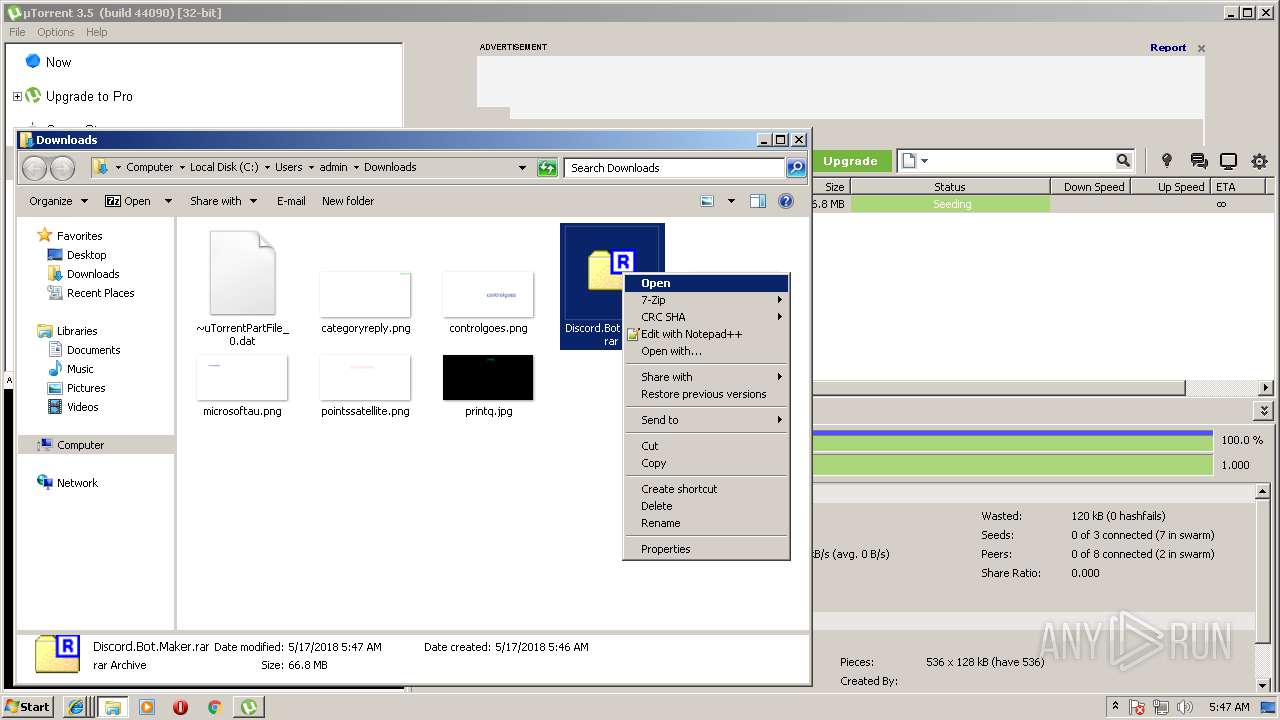
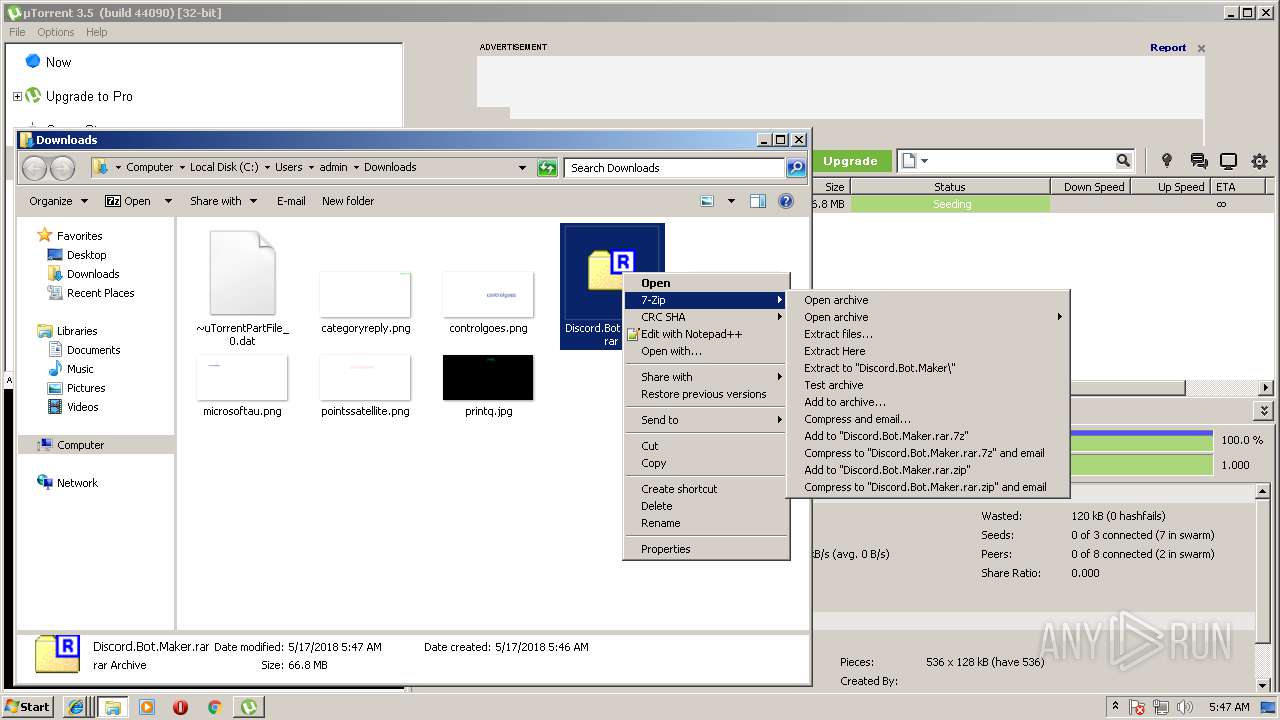
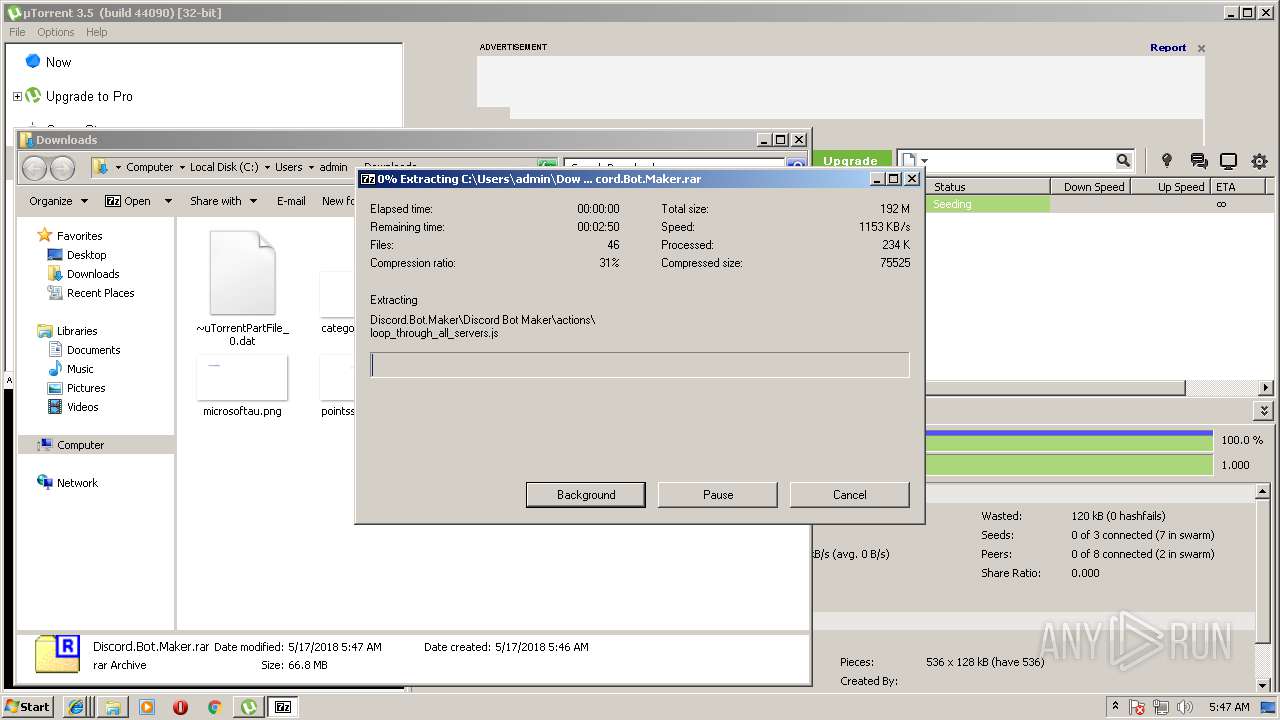
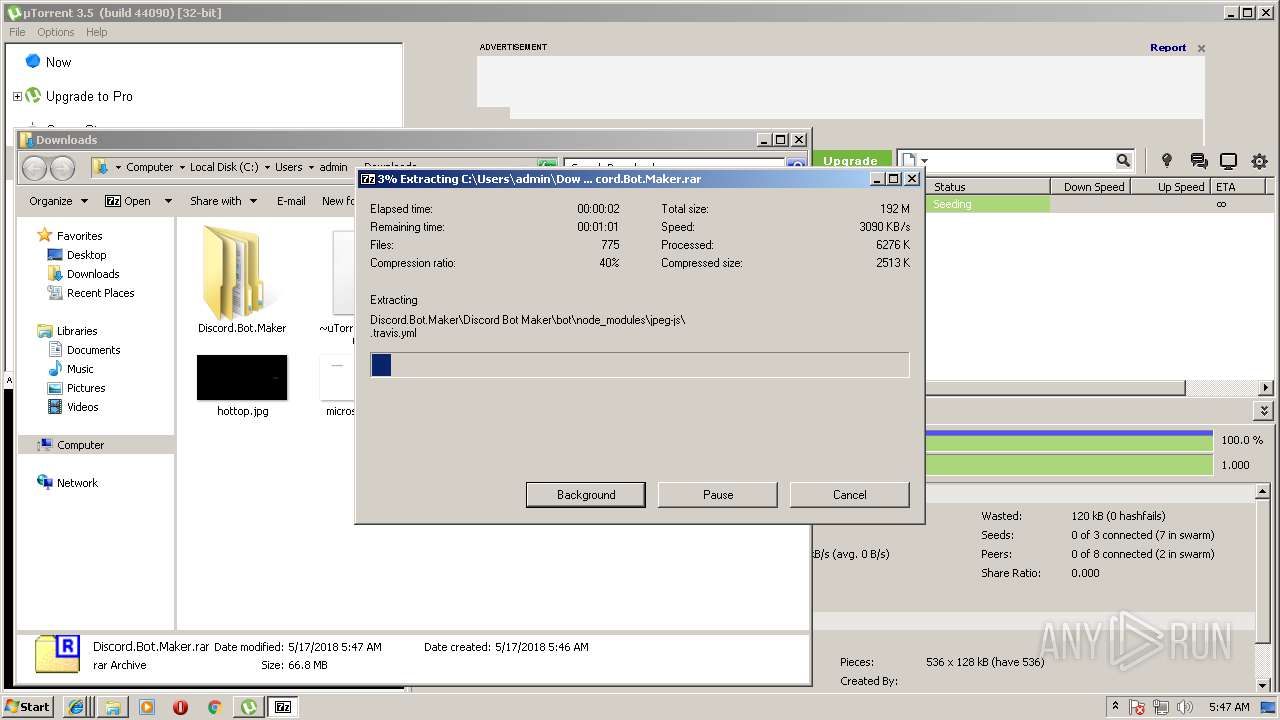
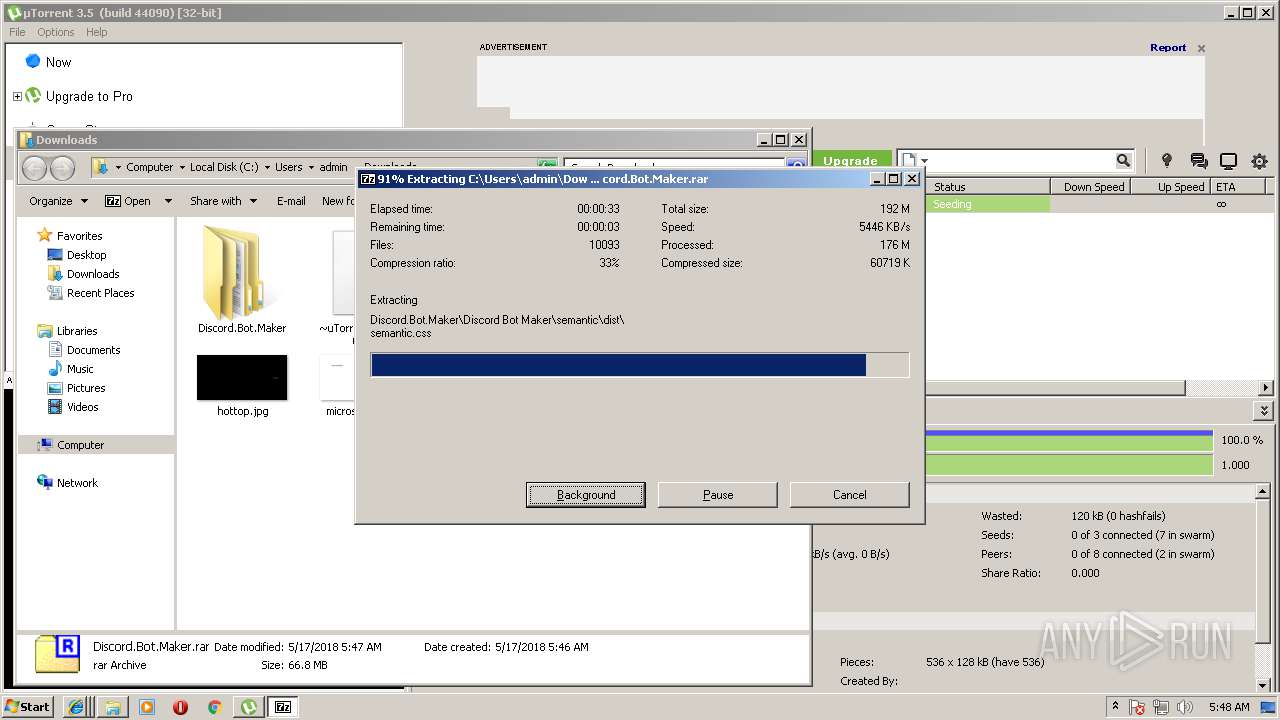
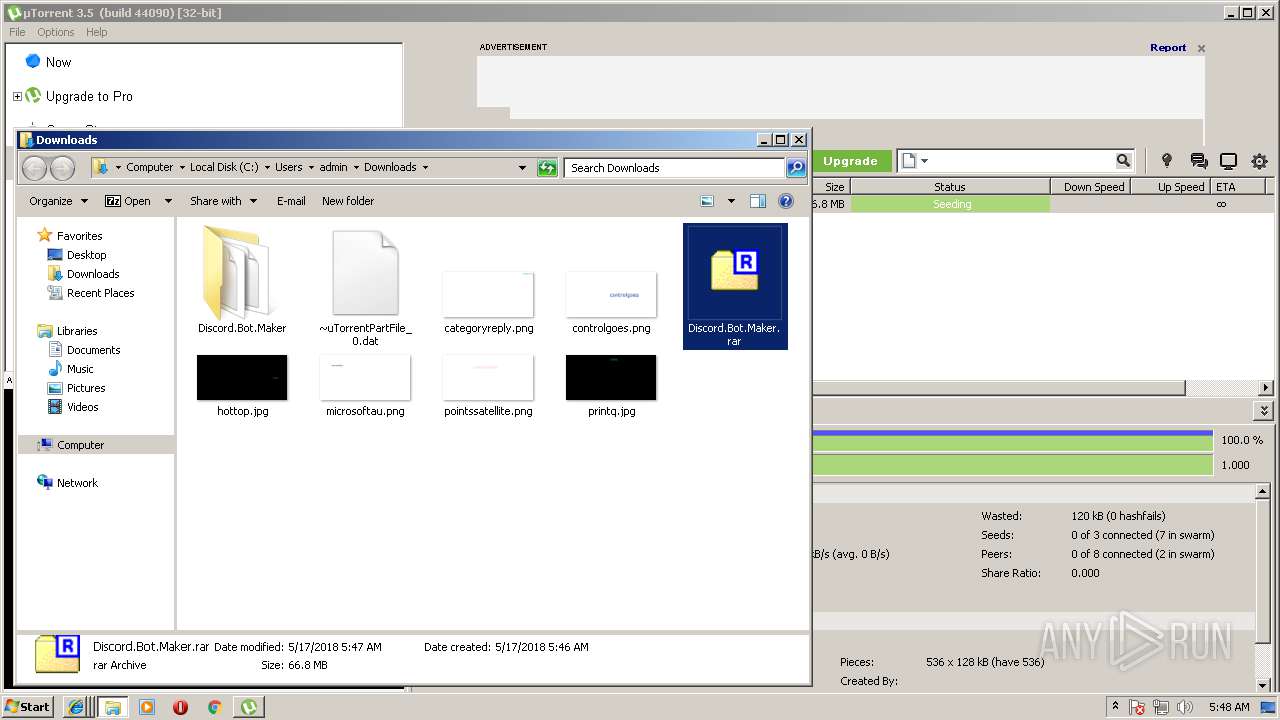
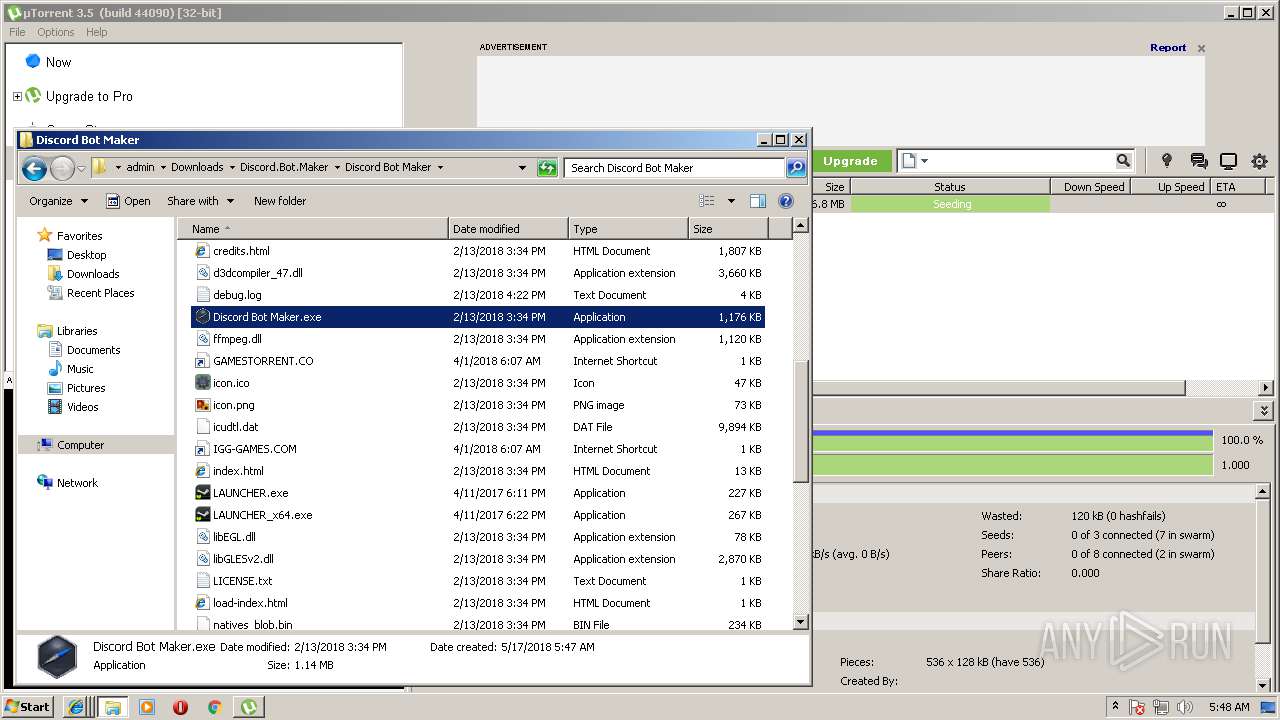
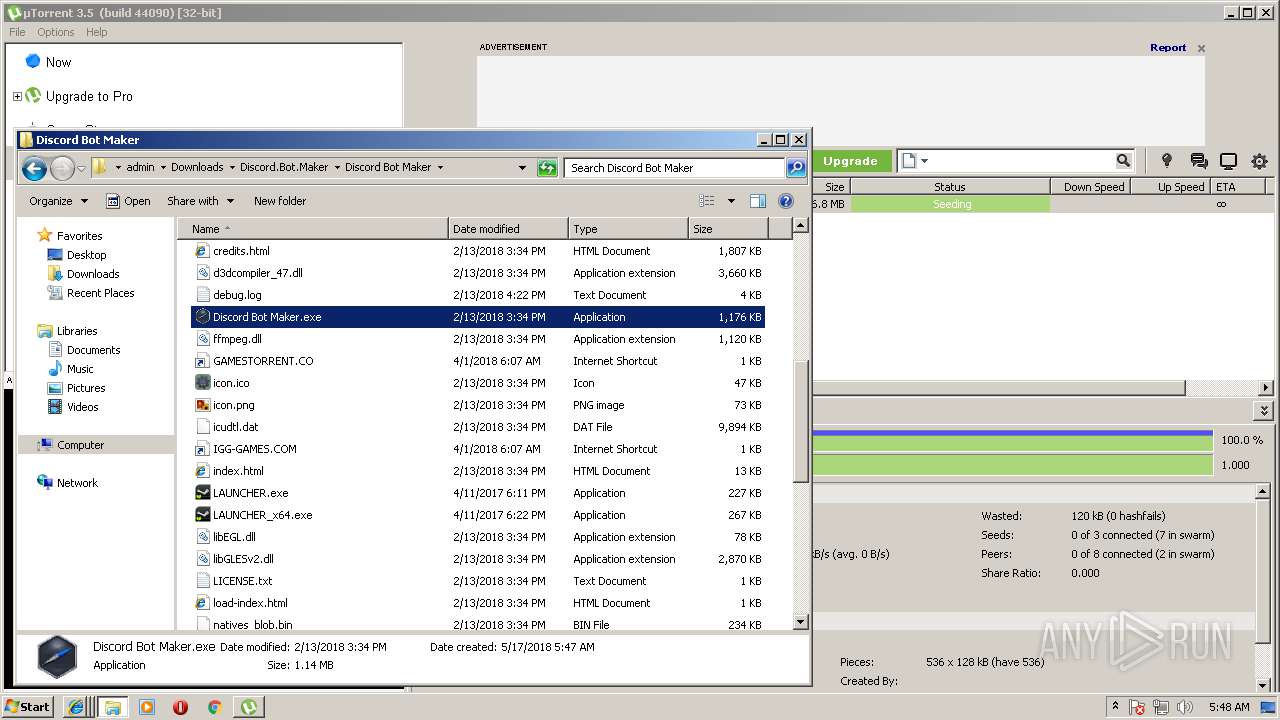
| download: | Discord_Bot_Maker |
| Full analysis: | https://app.any.run/tasks/9ef3bfd5-363e-48ce-99ac-5fbacf4da5da |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2018, 04:43:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines |
| MD5: | 38938D0CA62D13538BCA0B549F176EAF |
| SHA1: | 1C7C399DA5FFD121E3873847942BF1D92D0DC926 |
| SHA256: | 23DFD1A861CD6BC03BF0EA3EB914BA25F69E729AE0458EAEE1F9DECE59E3DEA4 |
| SSDEEP: | 768:qvOm/x9NV90iO0YiwBcjQV1Vv8HgceZGtii/iYiii1i4iQi3iYkUd:Dm/WilYi231BZGhqN3wtVS9Ud |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- FlashUtil32_26_0_0_137_ActiveX.exe (PID: 1380)
- uTorrent.exe (PID: 2072)
- utorrentie.exe (PID: 2144)
Reads Internet Cache Settings
- utorrentie.exe (PID: 2096)
- utorrentie.exe (PID: 2144)
Reads internet explorer settings
- utorrentie.exe (PID: 2096)
- utorrentie.exe (PID: 2144)
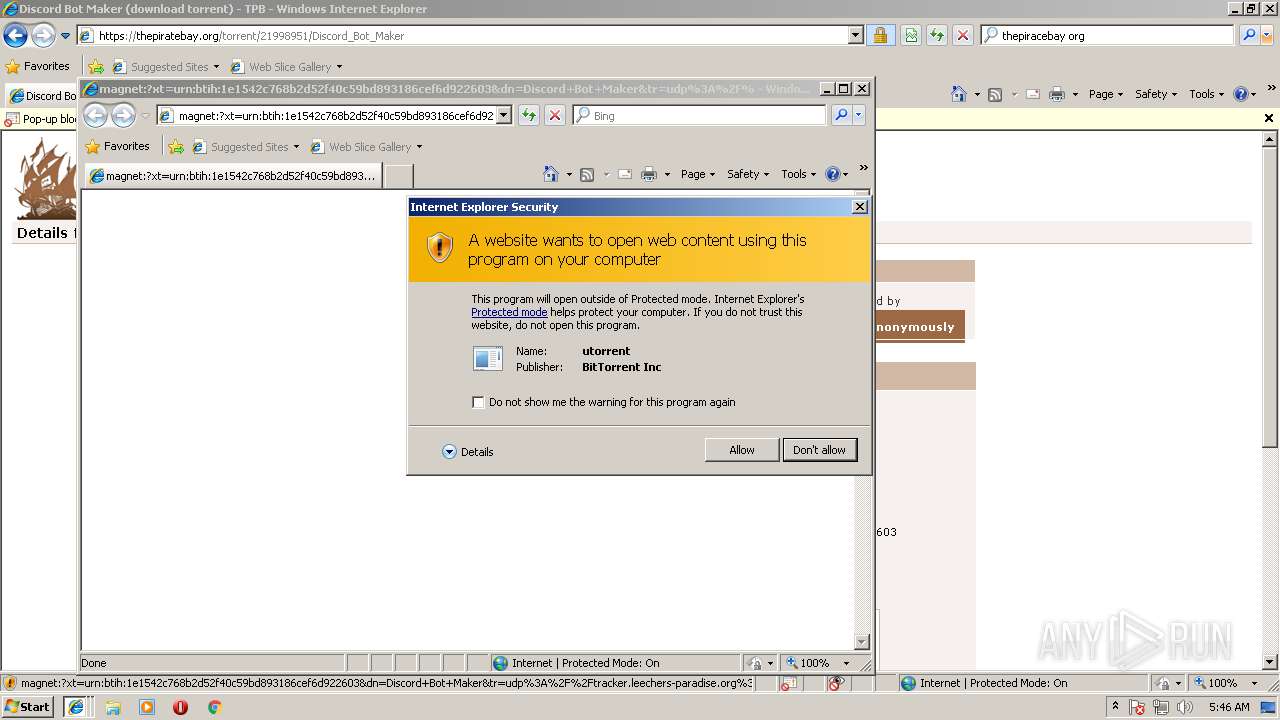
Changes IE settings (feature browser emulation)
- uTorrent.exe (PID: 2072)
Connects to unusual port
- uTorrent.exe (PID: 2072)
Executable content was dropped or overwritten
- 7zG.exe (PID: 3908)
INFO
Application launched itself
- iexplore.exe (PID: 3284)
Changes internet zones settings
- iexplore.exe (PID: 3284)
Creates files in the user directory
- iexplore.exe (PID: 3664)
- iexplore.exe (PID: 2844)
- iexplore.exe (PID: 3284)
- iexplore.exe (PID: 2504)
- iexplore.exe (PID: 4020)
Dropped object may contain URL's
- iexplore.exe (PID: 3664)
- iexplore.exe (PID: 3284)
- iexplore.exe (PID: 4020)
- uTorrent.exe (PID: 2072)
- iexplore.exe (PID: 2844)
- utorrentie.exe (PID: 2096)
- iexplore.exe (PID: 2504)
- utorrentie.exe (PID: 2144)
- 7zG.exe (PID: 3908)
Reads internet explorer settings
- iexplore.exe (PID: 3664)
- iexplore.exe (PID: 2844)
- iexplore.exe (PID: 2504)
- iexplore.exe (PID: 4020)
Reads Internet Cache Settings
- iexplore.exe (PID: 2844)
- iexplore.exe (PID: 3284)
- iexplore.exe (PID: 2504)
- iexplore.exe (PID: 4020)
Changes settings of System certificates
- iexplore.exe (PID: 3284)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 2504)
- iexplore.exe (PID: 2844)
- utorrentie.exe (PID: 2144)
- 7zG.exe (PID: 3908)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3284)
Dropped object may contain TOR URL's
- iexplore.exe (PID: 2844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
EXIF
HTML
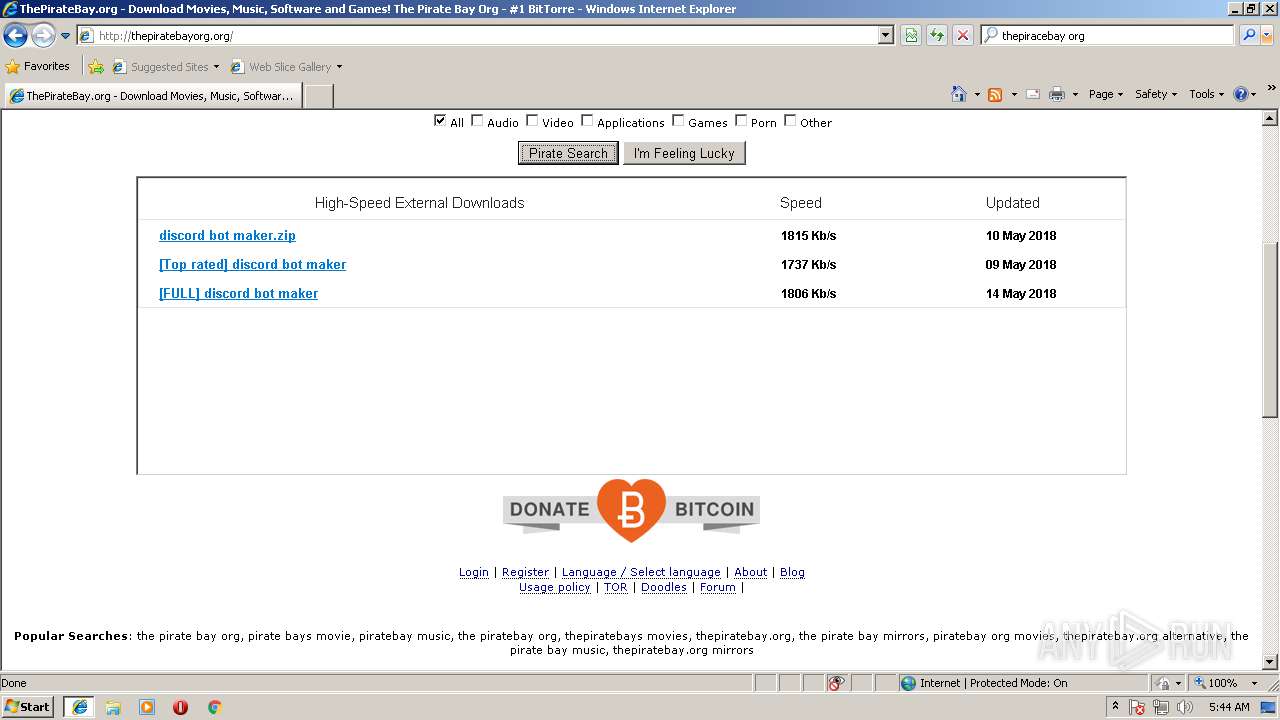
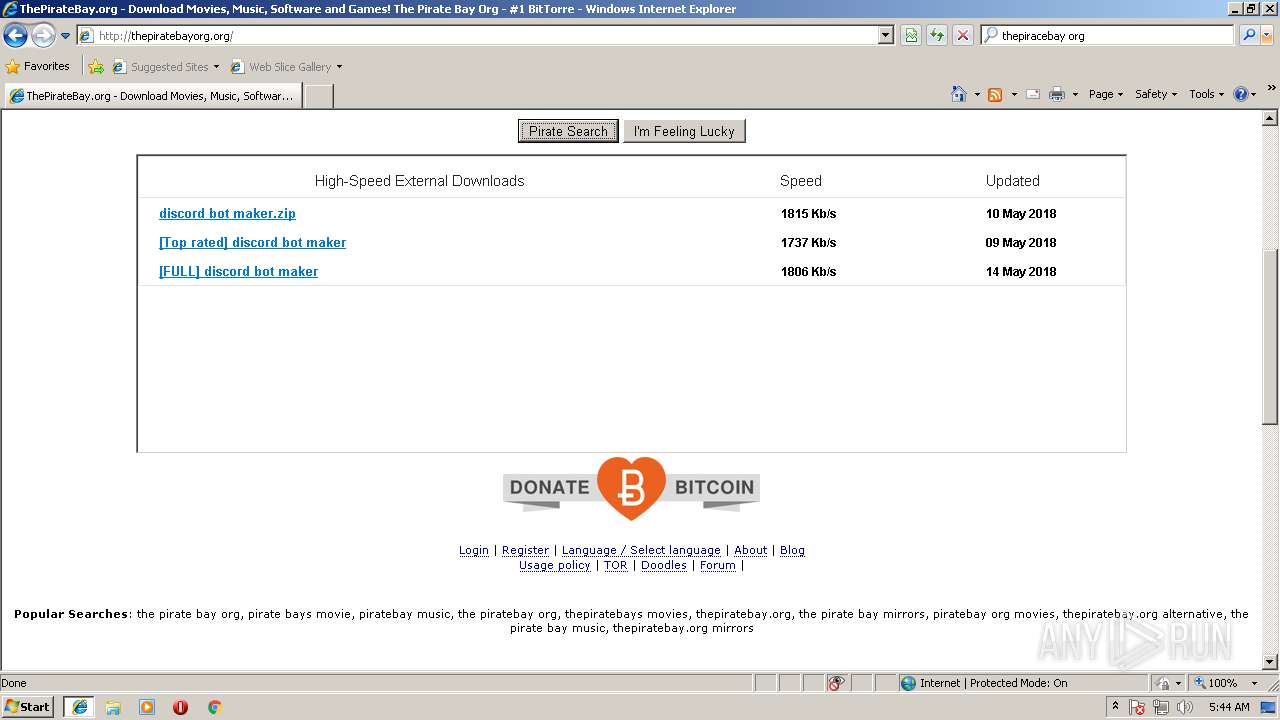
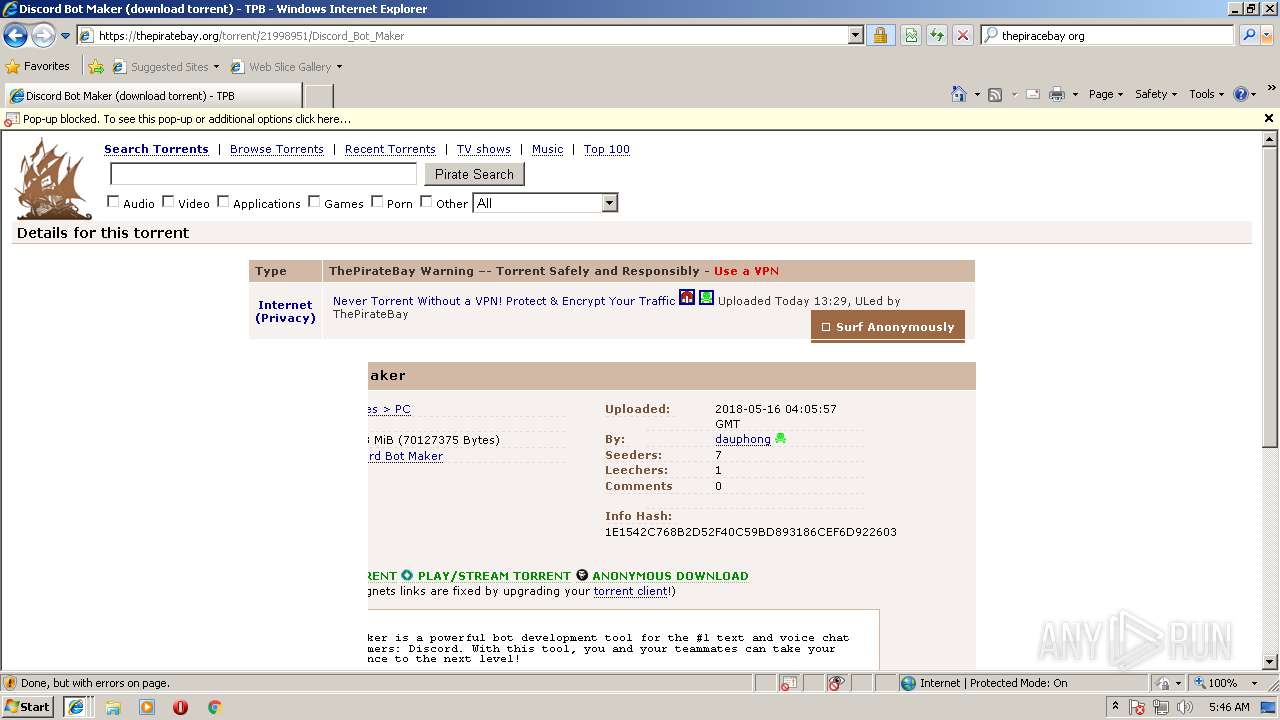
| Title: | Discord Bot Maker (download torrent) - TPB |
|---|---|
| ContentType: | text/html; charset=utf-8 |
| Description: | Download Discord Bot Maker torrent or any other torrent from the Games PC. Direct download via magnet link. |
| Keywords: | Discord Bot Maker Games PC Direct download torrent magnet |
Total processes
53
Monitored processes
12
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 808 | "C:\Users\admin\Downloads\Discord.Bot.Maker\Discord Bot Maker\Discord Bot Maker.exe" | C:\Users\admin\Downloads\Discord.Bot.Maker\Discord Bot Maker\Discord Bot Maker.exe | — | explorer.exe | |||||||||||
User: admin Company: The NWJS Community Integrity Level: MEDIUM Description: nwjs Exit code: 0 | |||||||||||||||
| 1380 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_137_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_137_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,137 Modules
| |||||||||||||||
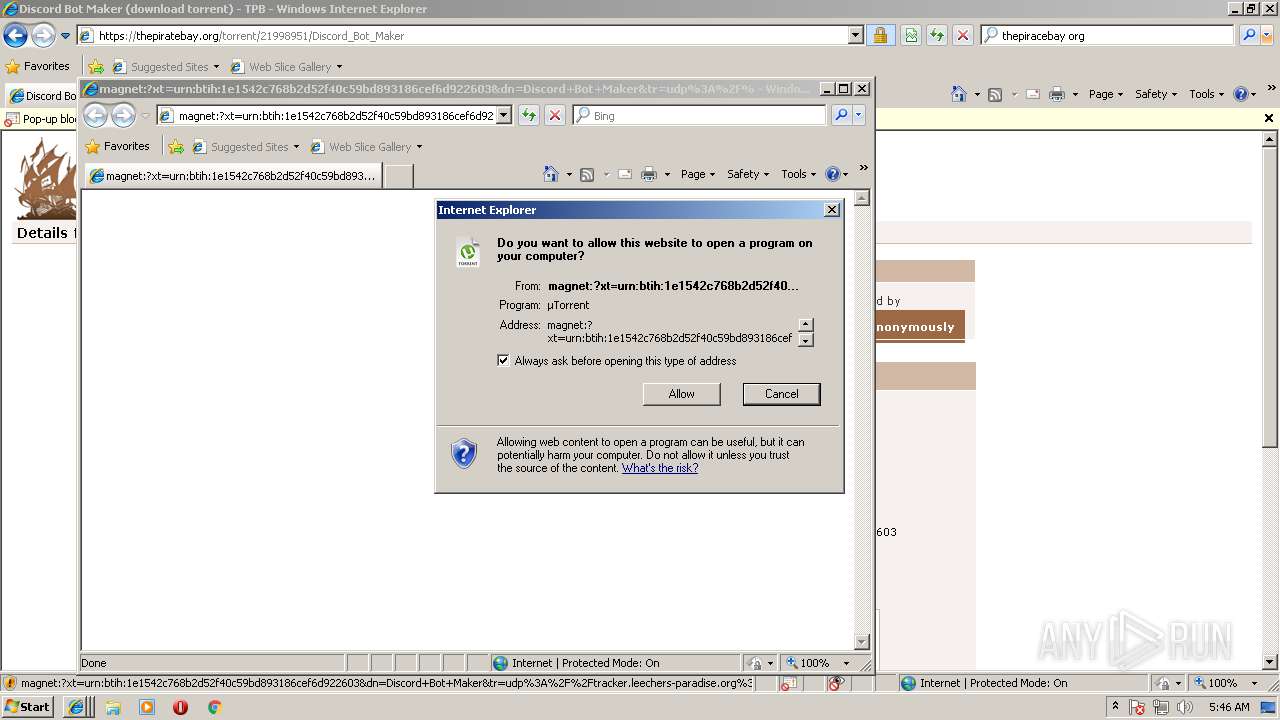
| 2072 | "C:\Users\admin\AppData\Roaming\uTorrent\uTorrent.exe" "magnet:?xt=urn:btih:1e1542c768b2d52f40c59bd893186cef6d922603&dn=Discord+Bot+Maker&tr=udp://tracker.leechers-paradise.org:6969&tr=udp://zer0day.ch:1337&tr=udp://open.demonii.com:1337&tr=udp://tracker.coppersurfer.tk:6969&tr=udp://exodus.desync.com:6969" /SHELLASSOC | C:\Users\admin\AppData\Roaming\uTorrent\uTorrent.exe | iexplore.exe | ||||||||||||
User: admin Company: BitTorrent Inc. Integrity Level: MEDIUM Description: µTorrent Exit code: 0 Version: 3.5.0.44090 Modules
| |||||||||||||||
| 2096 | "C:\Users\admin\AppData\Roaming\uTorrent\updates\3.5.0_44090\utorrentie.exe" uTorrent_2072_024870F8_1690830097 µTorrent4823DF041B09 uTorrent | C:\Users\admin\AppData\Roaming\uTorrent\updates\3.5.0_44090\utorrentie.exe | uTorrent.exe | ||||||||||||
User: admin Company: BitTorrent Inc. Integrity Level: LOW Description: WebHelper Exit code: 0 Version: 1.0.0 Modules
| |||||||||||||||
| 2144 | "C:\Users\admin\AppData\Roaming\uTorrent\updates\3.5.0_44090\utorrentie.exe" uTorrent_2072_02486FC8_174501290 µTorrent4823DF041B09 uTorrent | C:\Users\admin\AppData\Roaming\uTorrent\updates\3.5.0_44090\utorrentie.exe | uTorrent.exe | ||||||||||||
User: admin Company: BitTorrent Inc. Integrity Level: LOW Description: WebHelper Exit code: 0 Version: 1.0.0 Modules
| |||||||||||||||
| 2348 | "C:\Users\admin\AppData\Roaming\uTorrent\uTorrent.exe" "magnet:?xt=urn:btih:1e1542c768b2d52f40c59bd893186cef6d922603&dn=Discord+Bot+Maker&tr=udp://tracker.leechers-paradise.org:6969&tr=udp://zer0day.ch:1337&tr=udp://open.demonii.com:1337&tr=udp://tracker.coppersurfer.tk:6969&tr=udp://exodus.desync.com:6969" /SHELLASSOC | C:\Users\admin\AppData\Roaming\uTorrent\uTorrent.exe | — | iexplore.exe | |||||||||||
User: admin Company: BitTorrent Inc. Integrity Level: LOW Description: µTorrent Exit code: 0 Version: 3.5.0.44090 Modules
| |||||||||||||||
| 2504 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3284 CREDAT:203010 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2844 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3284 CREDAT:203009 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
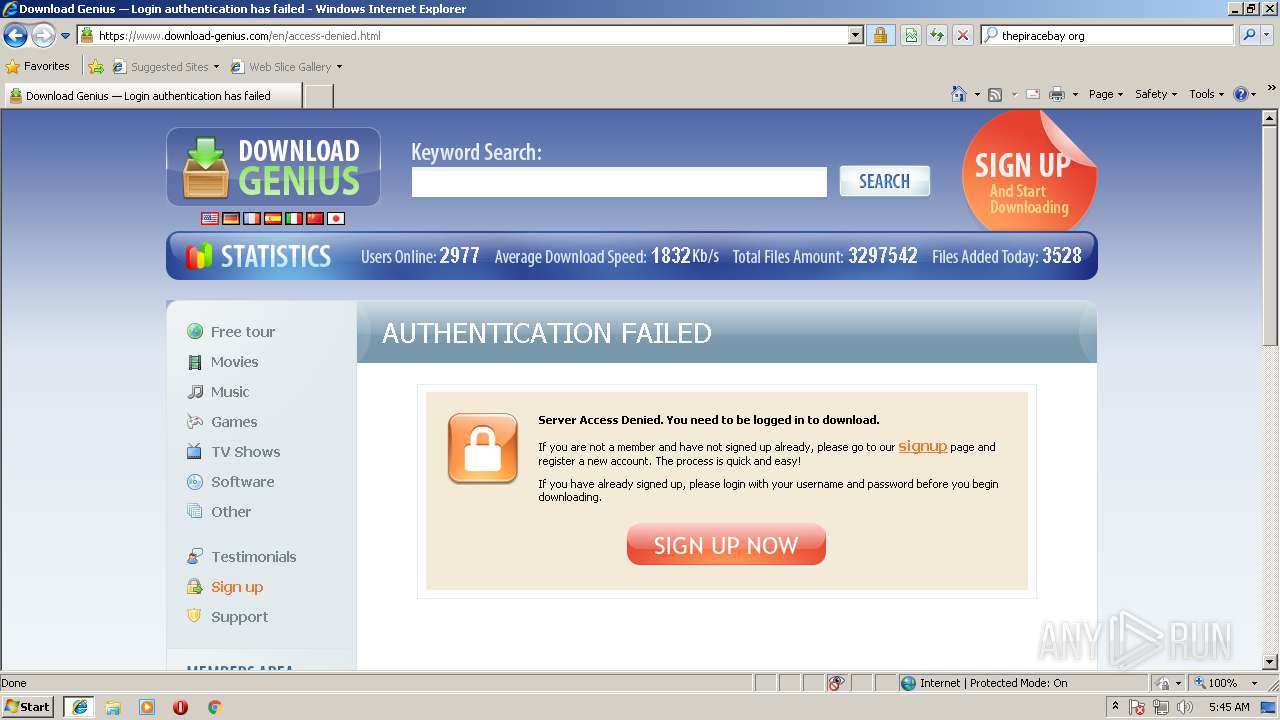
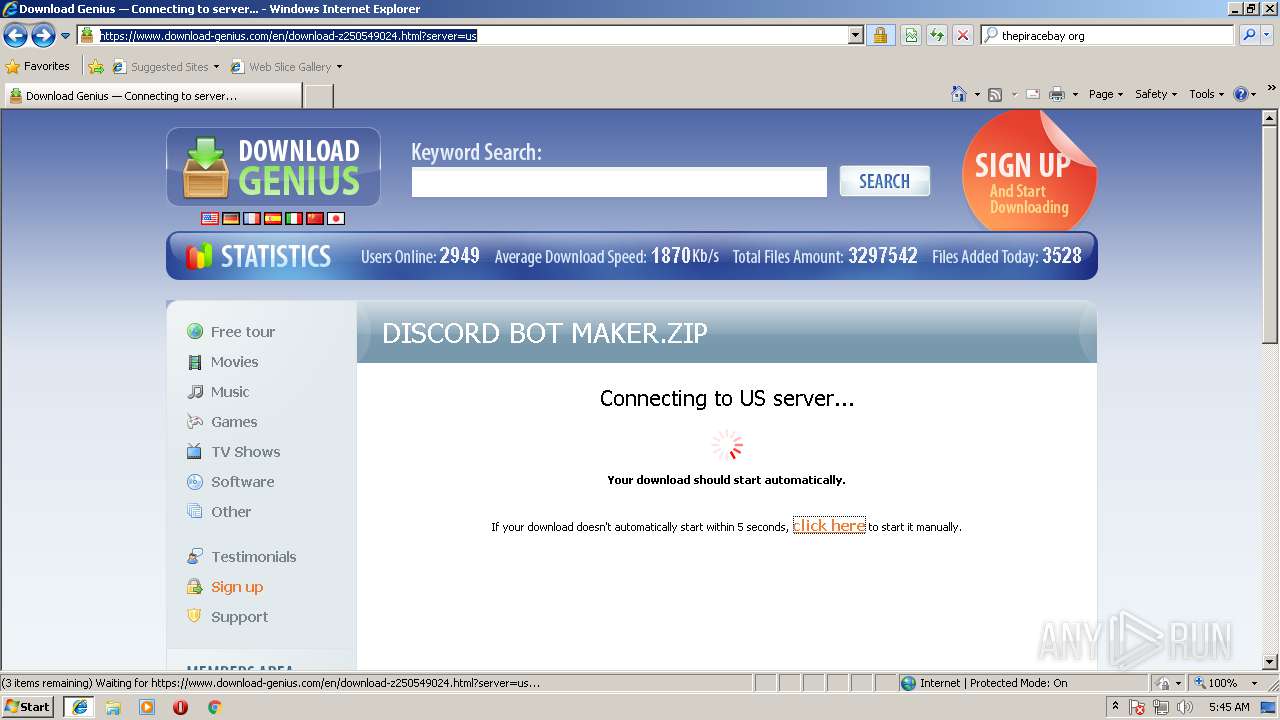
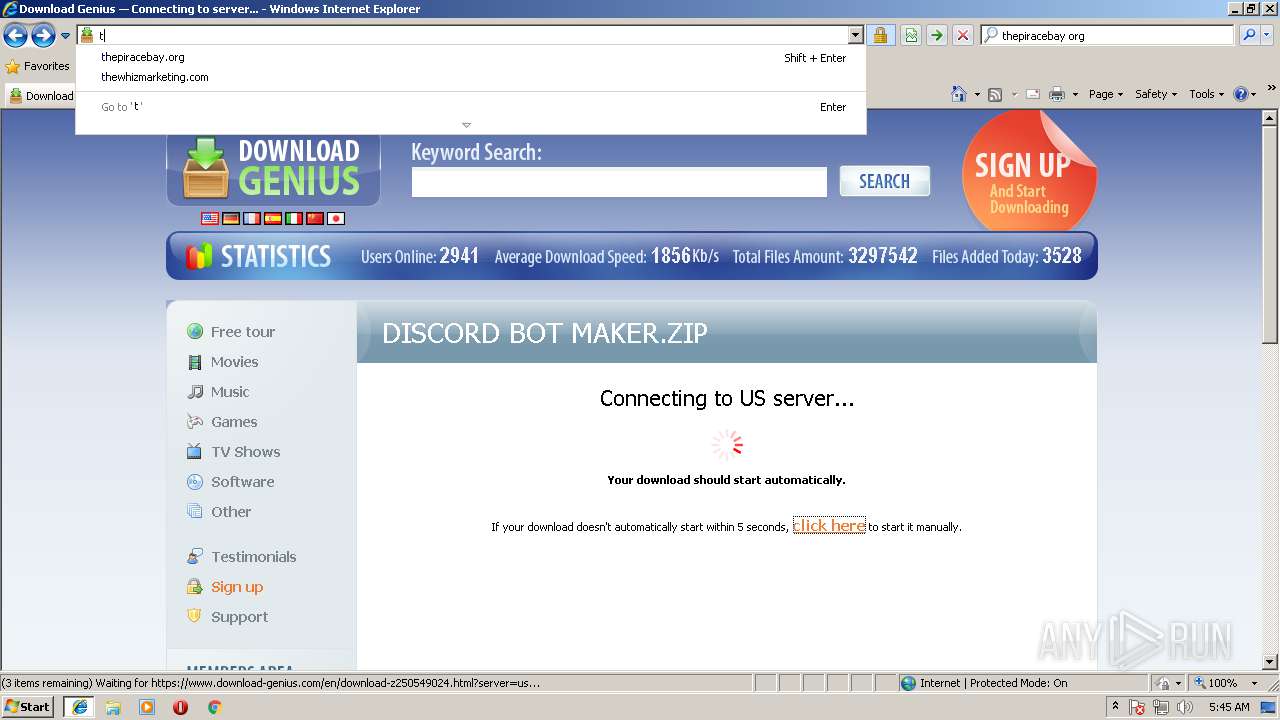
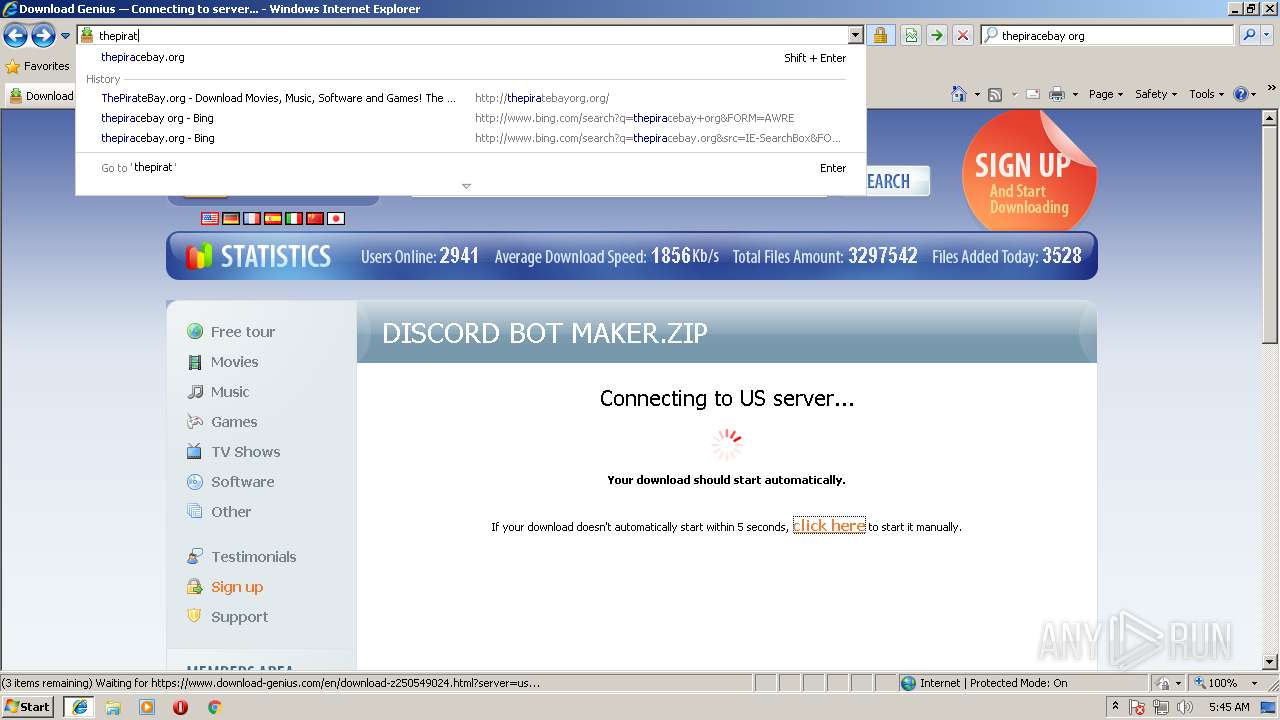
| 3284 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\Discord_Bot_Maker.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3664 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3284 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 137
Read events
1 807
Write events
324
Delete events
6
Modification events
| (PID) Process: | (3284) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3284) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3284) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3284) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3284) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3284) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000006B000000010000000000000000000000000000000000000000000000400C35B347C7D301000000000000000000000000020000001700000000000000FE80000000000000D45917EAB3ED3D860B000000000000001700000000000000FE80000000000000D45917EAB3ED3D860B000000000000001C00000000000000000000000000000000000000000000000000000000000000170000000000000000000000000000000000FFFFC0A8640B000000000000000002000000C0A801640000000000000000000000000000000000000000000000000C00000C37D0000010A73800D8703600000000000000000000000000000000000000000000000000000000000000000000000000000000000000000081F800009000230090002300380023000000000000702C000A00000000000000F8412C00 | |||
| (PID) Process: | (3284) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {E4C23E11-598C-11E8-B27F-5254004AAD21} |
Value: 0 | |||
| (PID) Process: | (3284) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3284) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 5 | |||
| (PID) Process: | (3284) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E20705000400110004002B0033008602 | |||
Executable files
18
Suspicious files
106
Text files
7 908
Unknown types
57
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3284 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2LKO8ICX\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3284 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab4D24.tmp | — | |
MD5:— | SHA256:— | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar4D25.tmp | — | |
MD5:— | SHA256:— | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab4D46.tmp | — | |
MD5:— | SHA256:— | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar4D47.tmp | — | |
MD5:— | SHA256:— | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab4DE4.tmp | — | |
MD5:— | SHA256:— | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar4DE5.tmp | — | |
MD5:— | SHA256:— | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LM4BD81N\dnserror[1] | — | |
MD5:— | SHA256:— | |||
| 3664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\2LKO8ICX\dnserror[1] | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
122
TCP/UDP connections
474
DNS requests
79
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3664 | iexplore.exe | OPTIONS | 301 | 104.27.216.28:80 | http://thepiratebay.org/ | US | — | — | whitelisted |
984 | svchost.exe | OPTIONS | 301 | 104.27.216.28:80 | http://thepiratebay.org/static | US | — | — | whitelisted |
2844 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rms/rms%20answers%20SegmentFilters%20Blue$GenericDropDownModernCalendar/cj,nj/dba278f5/46045091.js | US | text | 2.75 Kb | whitelisted |
2844 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rms/rms%20answers%20WebResult%20Blue$WebResultToolboxBlue/cj,nj/57324345/ae00a169.js | US | text | 1.72 Kb | whitelisted |
2844 | iexplore.exe | POST | 204 | 204.79.197.200:80 | http://www.bing.com/fd/ls/lsp.aspx | US | compressed | 2.75 Kb | whitelisted |
2844 | iexplore.exe | GET | 204 | 204.79.197.200:80 | http://www.bing.com/fd/ls/l?IG=E24A2D40A7FC4479A150012E9AE80908&CID=0BBF01EFD724668D052A0A1DD6D567B6&Type=Event.CPT&DATA={"pp":{"S":"L","FC":234,"BC":265,"SE":-1,"TC":-1,"H":328,"BP":437,"CT":453,"IL":3},"ad":[-1,-1,1260,560,1260,498,0]}&P=SERP&DA=DB5 | US | image | 7.91 Kb | whitelisted |
2844 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rms/rms%20answers%20Identity%20Blue$BlueIdentityDropdownBootStrap_Redirect/cj,nj/1946cd5d/345843dc.js | US | text | 753 b | whitelisted |
2844 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rms/BingCore.Bundle/cj,nj/7bd0f601/48d809c9.js?bu=rms+answers+Shared+BingCore%24ClientInstV2%24DuplicateXlsDefaultConfig%2cBingCore%24ClientInstV2%24SharedLocalStorageConfigDefault%2cBingCore%24shared%2cBingCore%24env.override%2cEmpty%2cBingCore%24event.custom.fix%2cBingCore%24event.native%2cBingCore%24onHTML%2cBingCore%24dom%2cBingCore%24cookies%2cBingCore%24rmsajax%2cBingCore%24ClientInstV2%24LogUploadCapFeatureDisabled%2cBingCore%24ClientInstV2%24ClientInstConfigSeparateOfflineQueue%2cBingCore%24clientinst%2cBingCore%24replay%2cBingCore%24Animation%2cBingCore%24fadeAnimation%2cBingCore%24framework | US | text | 4.92 Kb | whitelisted |
2844 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rms/rms%20answers%20Identity%20Blue$BlueIdentityHeader/cj,nj/4c7364c5/40e1b425.js | US | text | 816 b | whitelisted |
2844 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rms/rms%20answers%20Identity%20SnrWindowsLiveConnectBootstrap/cj,nj/bf587ad6/f1d86b5a.js | US | text | 181 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 104.24.120.216:139 | traffic.adxprtz.com | Cloudflare Inc | US | shared |
4 | System | 104.27.216.28:445 | thepiratebay.org | Cloudflare Inc | US | shared |
3284 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
4 | System | 104.27.217.28:445 | thepiratebay.org | Cloudflare Inc | US | shared |
— | — | 104.27.217.28:137 | thepiratebay.org | Cloudflare Inc | US | shared |
3664 | iexplore.exe | 104.27.216.28:80 | thepiratebay.org | Cloudflare Inc | US | shared |
3664 | iexplore.exe | 104.27.216.28:443 | thepiratebay.org | Cloudflare Inc | US | shared |
3664 | iexplore.exe | 68.232.34.240:80 | www.download.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
984 | svchost.exe | 104.27.216.28:80 | thepiratebay.org | Cloudflare Inc | US | shared |
2844 | iexplore.exe | 131.253.61.70:443 | login.live.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
thepiratebay.org |
| whitelisted |
www.bing.com |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
traffic.adxprtz.com |
| malicious |
thepiracebay.org |
| unknown |
login.live.com |
| whitelisted |
e60b7c55af6602676d072f846658d968.clo.footprintdns.com |
| unknown |
58d3a1bebf8aff95803b3709c356b78e.clo.footprintdns.com |
| unknown |
ee9e37e2e00c27b2e310c7f2a4ee94c3.clo.footprintdns.com |
| unknown |
fp.msedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2072 | uTorrent.exe | Potential Corporate Privacy Violation | ET P2P BTWebClient UA uTorrent in use |
2072 | uTorrent.exe | Potential Corporate Privacy Violation | ET P2P BTWebClient UA uTorrent in use |
2072 | uTorrent.exe | Potential Corporate Privacy Violation | ET P2P BTWebClient UA uTorrent in use |
2072 | uTorrent.exe | Potential Corporate Privacy Violation | ET P2P BTWebClient UA uTorrent in use |
2072 | uTorrent.exe | Potential Corporate Privacy Violation | ET P2P BTWebClient UA uTorrent in use |
2072 | uTorrent.exe | Potential Corporate Privacy Violation | ET P2P BitTorrent DHT ping request |
2072 | uTorrent.exe | Potential Corporate Privacy Violation | ET P2P BTWebClient UA uTorrent in use |
— | — | Misc Attack | ET CINS Active Threat Intelligence Poor Reputation IP group 89 |
— | — | Misc Attack | ET CINS Active Threat Intelligence Poor Reputation IP group 36 |
— | — | Potential Corporate Privacy Violation | ET P2P Vuze BT UDP Connection (5) |