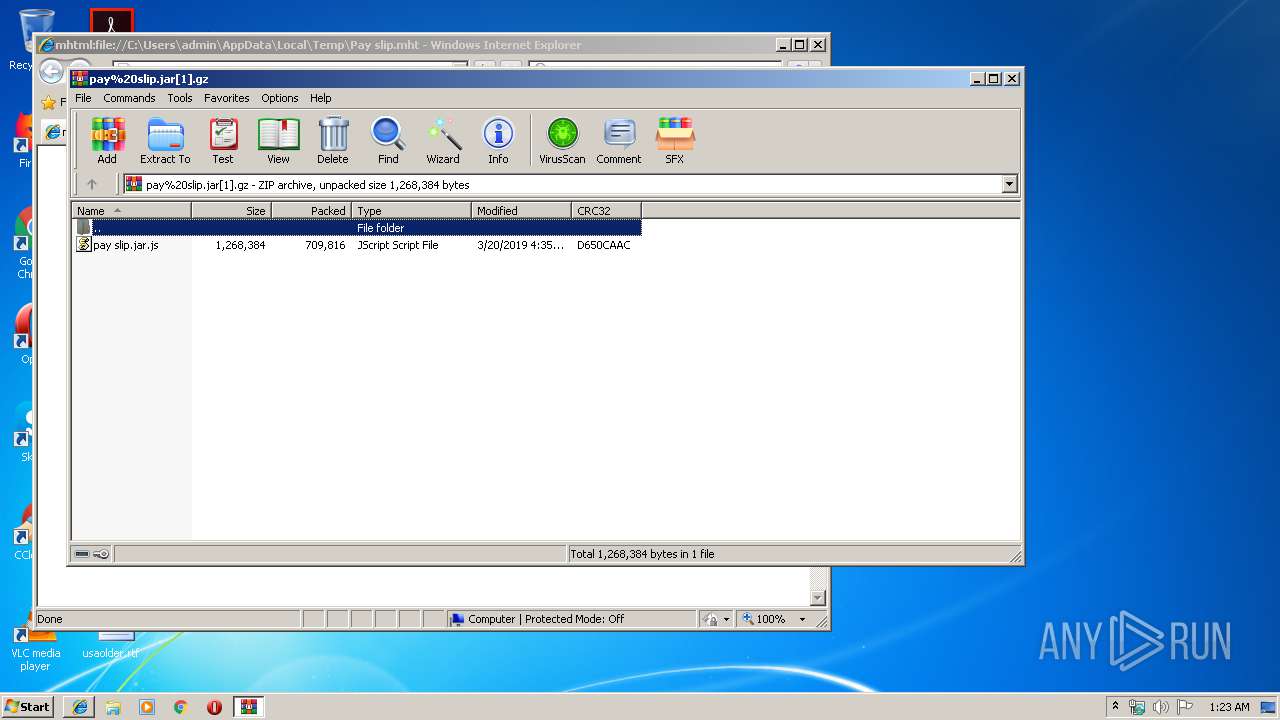
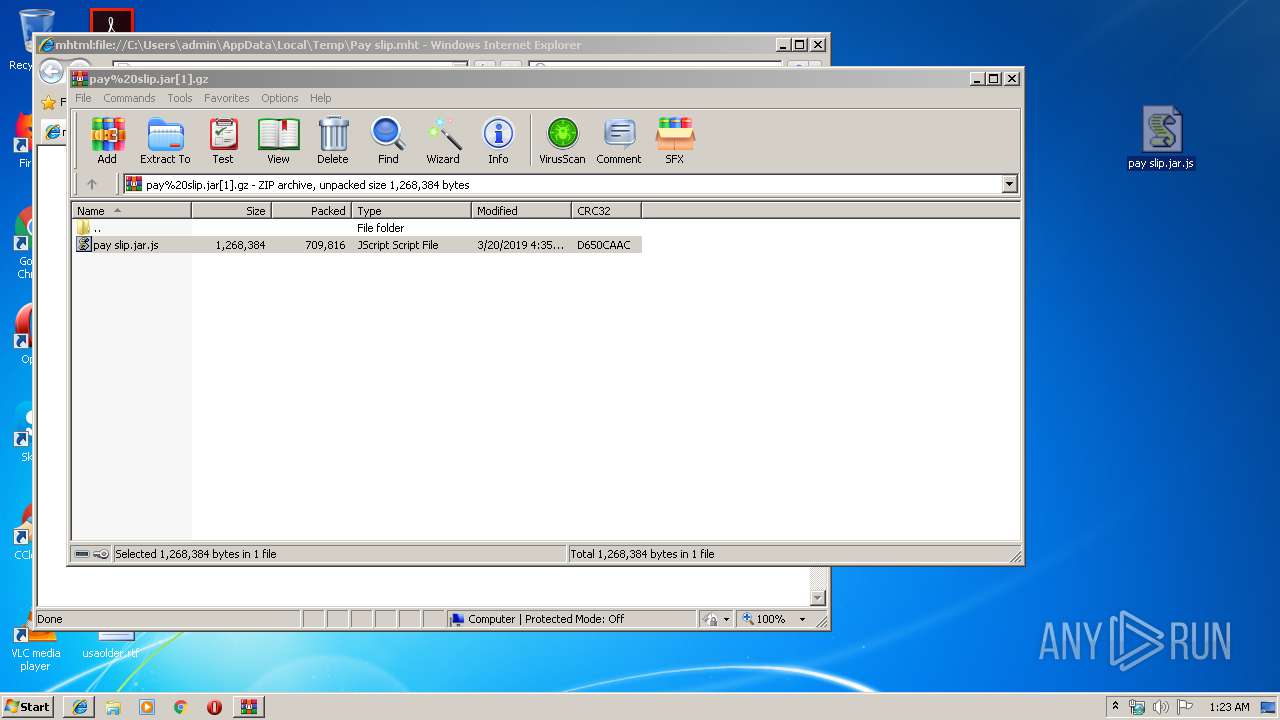
| File name: | Pay slip.mht |
| Full analysis: | https://app.any.run/tasks/04e0f98c-7348-436b-9db1-d786fbec9425 |
| Verdict: | Malicious activity |
| Analysis date: | March 22, 2019, 01:22:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF, CR line terminators |
| MD5: | 21A207995F80F95F717D74361B266090 |
| SHA1: | 5D03889A07816BDDB2E40437935746B8C802A021 |
| SHA256: | 23DAA64BB64553555FAC725EEF4B6103875C1E3FE8CC5FC2DE71183EA5A81476 |
| SSDEEP: | 6:4Q0kJQQ8a0NNEXW0Yfcvj3VTfCQ9MfS2yKiVOlAscSL7Wrn7f:4Q0AQQYf2j3VTr9eStKggWX |
MALICIOUS
Uses Task Scheduler to run other applications
- WScript.exe (PID: 2384)
- WScript.exe (PID: 2688)
Changes the autorun value in the registry
- javaw.exe (PID: 2732)
- WScript.exe (PID: 2384)
- WScript.exe (PID: 2688)
- javaw.exe (PID: 2436)
- WScript.exe (PID: 3904)
- WScript.exe (PID: 3052)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2876)
- schtasks.exe (PID: 1180)
Writes to a start menu file
- WScript.exe (PID: 2384)
- WScript.exe (PID: 2688)
SUSPICIOUS
Creates files in the user directory
- WScript.exe (PID: 2252)
- WScript.exe (PID: 3052)
- javaw.exe (PID: 2732)
- WScript.exe (PID: 2384)
- WScript.exe (PID: 4000)
- WScript.exe (PID: 3904)
- javaw.exe (PID: 2436)
Application launched itself
- WScript.exe (PID: 2252)
- javaw.exe (PID: 2732)
- WScript.exe (PID: 4000)
- WScript.exe (PID: 3904)
- javaw.exe (PID: 2436)
- WScript.exe (PID: 3052)
Executes JAVA applets
- WScript.exe (PID: 2252)
- javaw.exe (PID: 2732)
- WScript.exe (PID: 4000)
- WScript.exe (PID: 3904)
- javaw.exe (PID: 2436)
- WScript.exe (PID: 3052)
Executes scripts
- WScript.exe (PID: 2252)
- WScript.exe (PID: 3052)
- WScript.exe (PID: 4000)
- WScript.exe (PID: 3904)
Connects to unusual port
- WScript.exe (PID: 2384)
- javaw.exe (PID: 948)
- javaw.exe (PID: 1528)
- WScript.exe (PID: 2688)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2640)
- iexplore.exe (PID: 516)
- iexplore.exe (PID: 2180)
Changes internet zones settings
- iexplore.exe (PID: 516)
Reads internet explorer settings
- iexplore.exe (PID: 2640)
Application launched itself
- iexplore.exe (PID: 516)
Reads Microsoft Office registry keys
- iexplore.exe (PID: 516)
Creates files in the user directory
- iexplore.exe (PID: 2180)
Changes settings of System certificates
- iexplore.exe (PID: 516)
Reads settings of System Certificates
- iexplore.exe (PID: 516)
Adds / modifies Windows certificates
- iexplore.exe (PID: 516)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
52
Monitored processes
18
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\Pay slip.mht | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 948 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw" -jar "C:\Users\admin\AppData\RoamingServer1918697851.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | javaw.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 1180 | "C:\Windows\System32\schtasks.exe" /create /sc minute /mo 30 /tn Skype /tr "C:\Users\admin\AppData\Roaming\IyFfaseYOW.js | C:\Windows\System32\schtasks.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1528 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw" -jar "C:\Users\admin\AppData\RoamingServer-1082199189.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | javaw.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2068 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\AppData\Roaming\uslxjbpbxx.txt" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | WScript.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2180 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:516 CREDAT:137473 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2252 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\pay slip.jar.js" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2384 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\IyFfaseYOW.js" | C:\Windows\System32\WScript.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2436 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\AppData\Roaming\dgmjljnjmu.txt" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | WScript.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
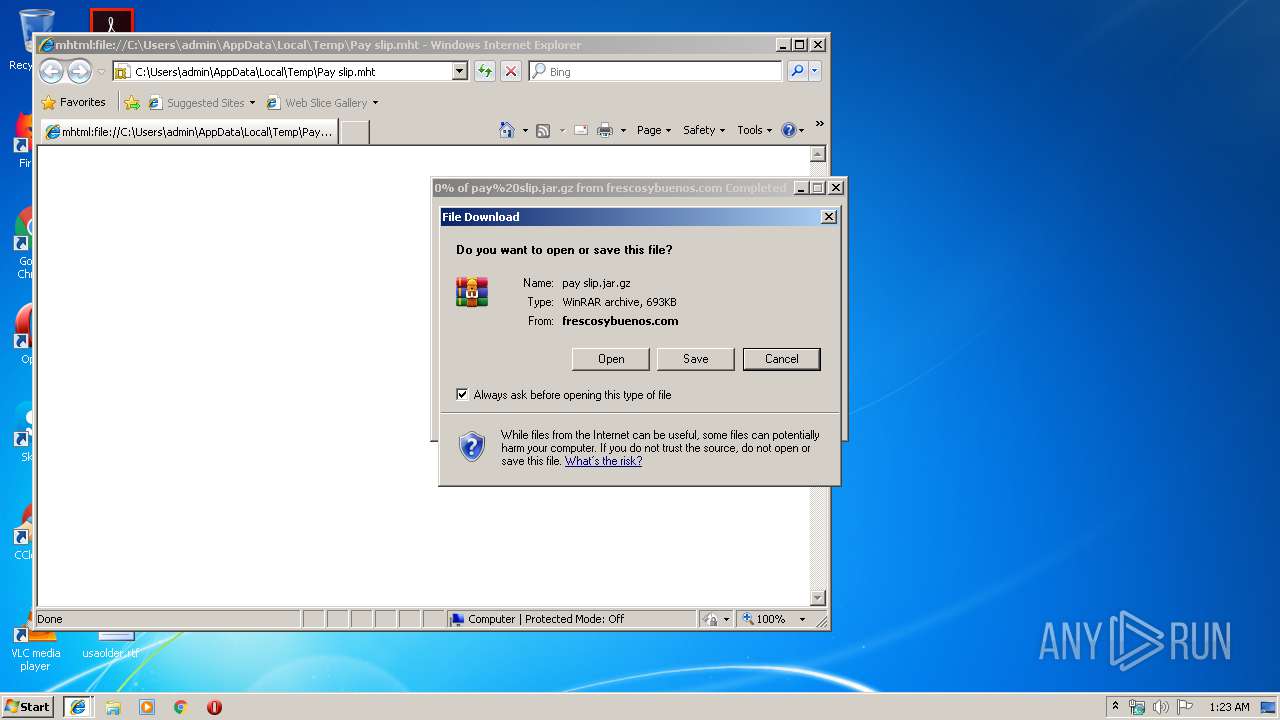
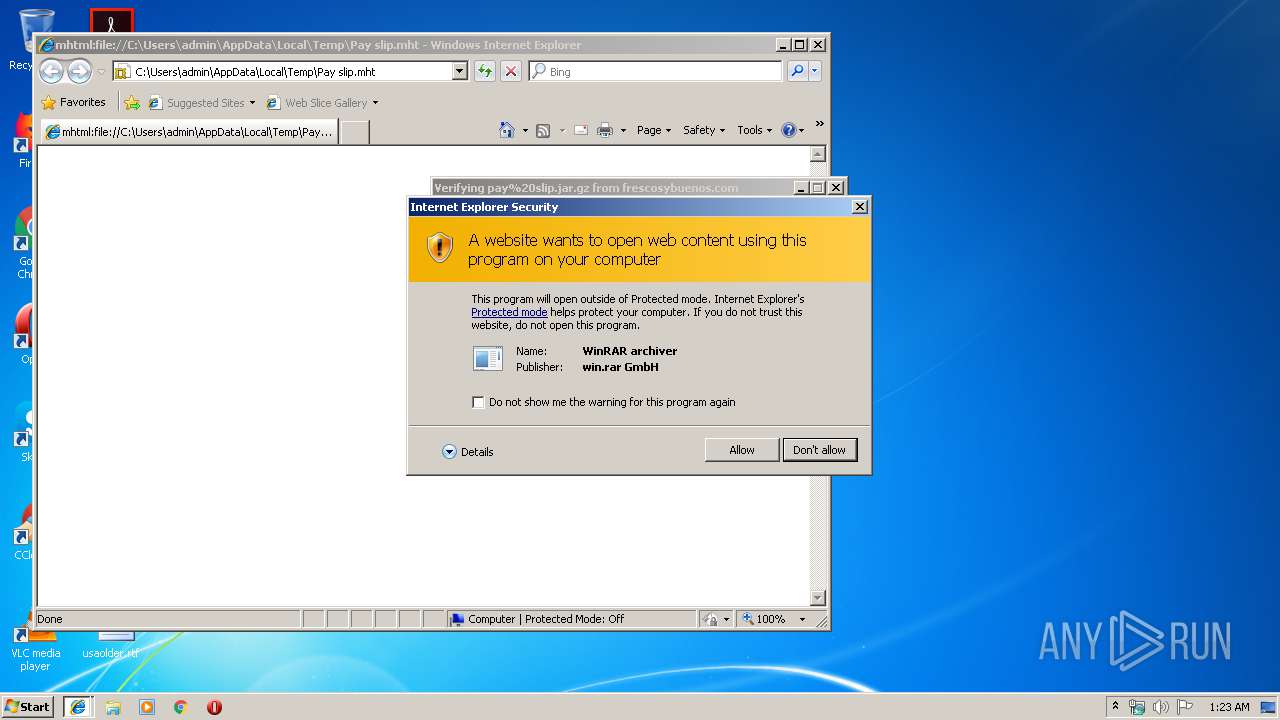
| 2636 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PM2354IV\pay%20slip.jar[1].gz" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
3 019
Read events
2 861
Write events
155
Delete events
3
Modification events
| (PID) Process: | (516) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (516) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (516) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (516) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (516) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (516) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000006E000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (516) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {10BF0975-4C41-11E9-A302-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (516) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (516) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (516) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307030005001600010017001000A401 | |||
Executable files
0
Suspicious files
8
Text files
24
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 516 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFF0BC9463E9178DB4.TMP | — | |
MD5:— | SHA256:— | |||
| 516 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 516 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2636 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2636.32291\pay slip.jar.js | — | |
MD5:— | SHA256:— | |||
| 2180 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012019032220190323\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2640 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\wbk934F.tmp | text | |
MD5:— | SHA256:— | |||
| 516 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{10BF0977-4C41-11E9-A302-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 2180 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2180 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2640 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\wbk9535.tmp | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
40
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
516 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
516 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
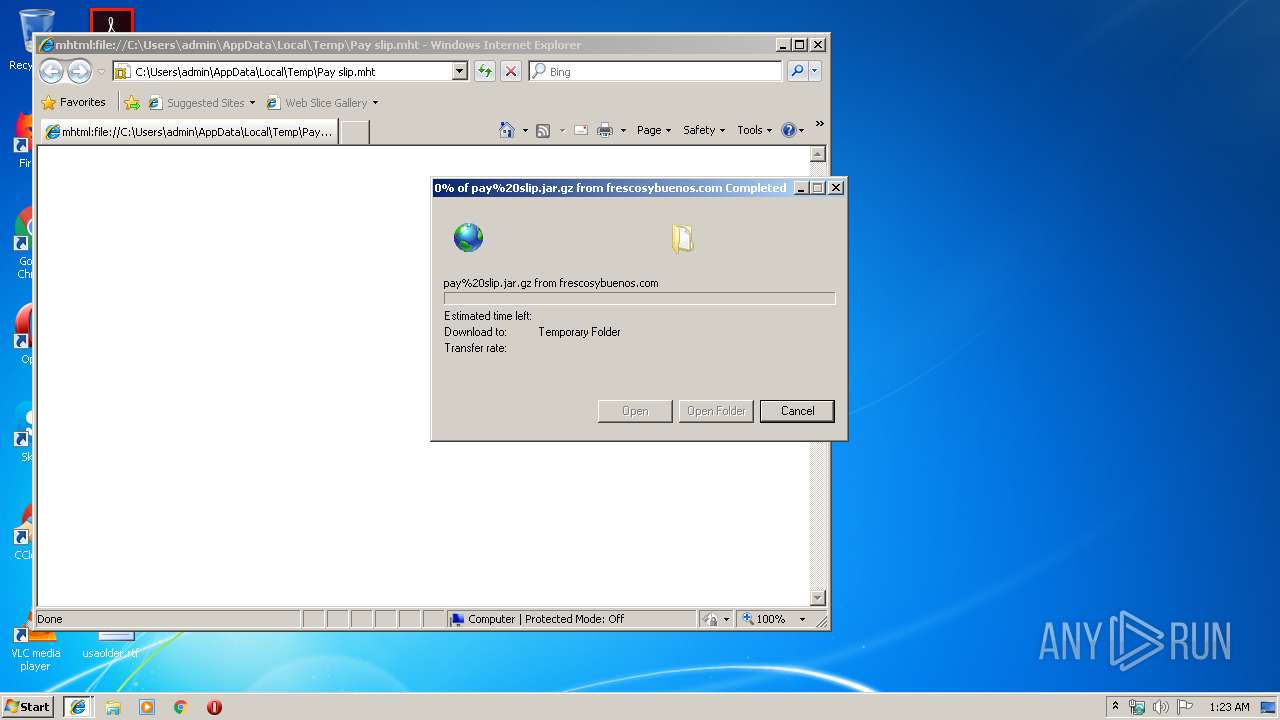
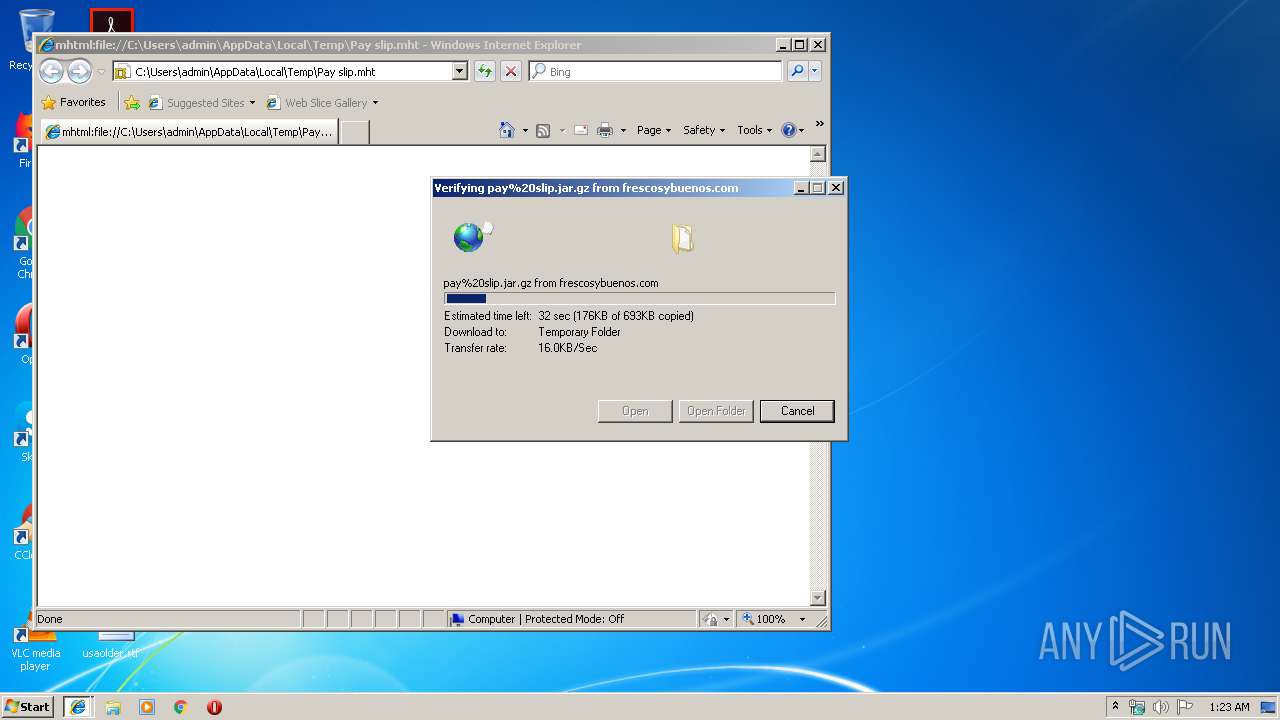
2180 | iexplore.exe | 198.50.154.4:443 | frescosybuenos.com | OVH SAS | US | unknown |
516 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2384 | WScript.exe | 41.217.38.155:7755 | unknownsoft.hopto.org | Spectranet | NG | unknown |
948 | javaw.exe | 41.217.38.155:7744 | unknownsoft.hopto.org | Spectranet | NG | unknown |
1528 | javaw.exe | 41.217.38.155:7744 | unknownsoft.hopto.org | Spectranet | NG | unknown |
2688 | WScript.exe | 41.217.38.155:7755 | unknownsoft.hopto.org | Spectranet | NG | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
frescosybuenos.com |
| unknown |
unknownsoft.hopto.org |
| malicious |
dns.msftncsi.com |
| shared |