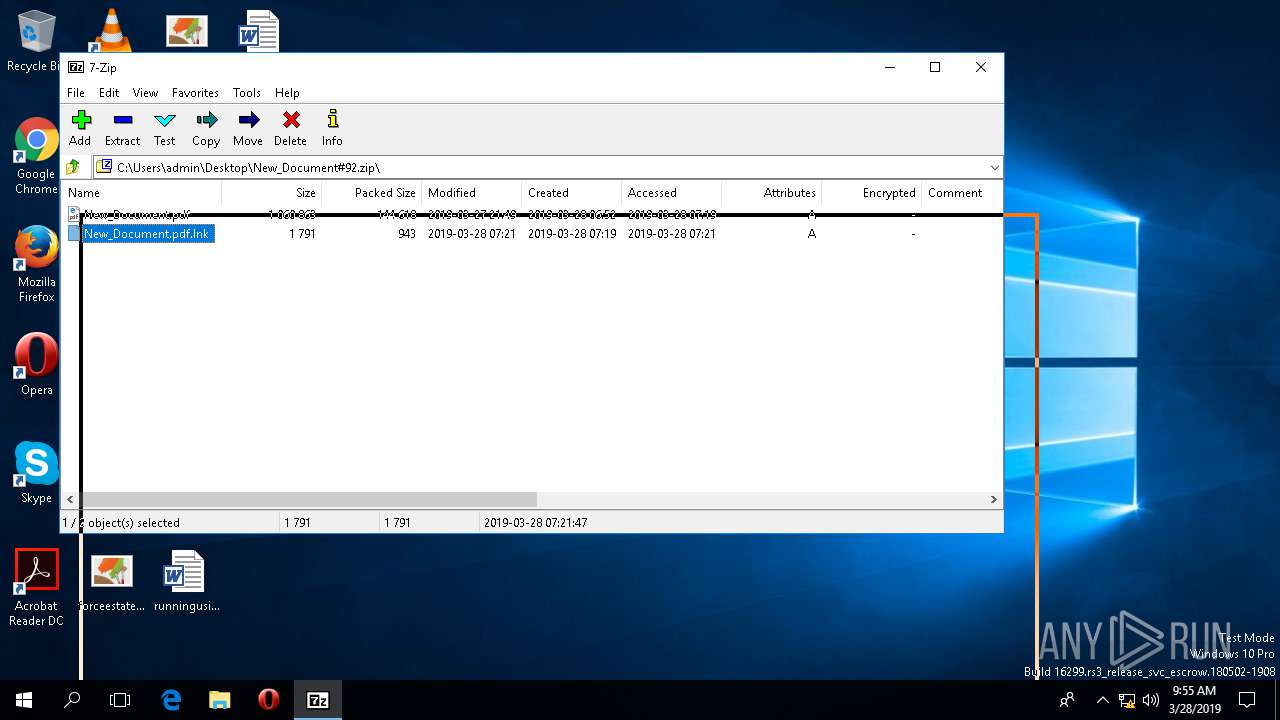
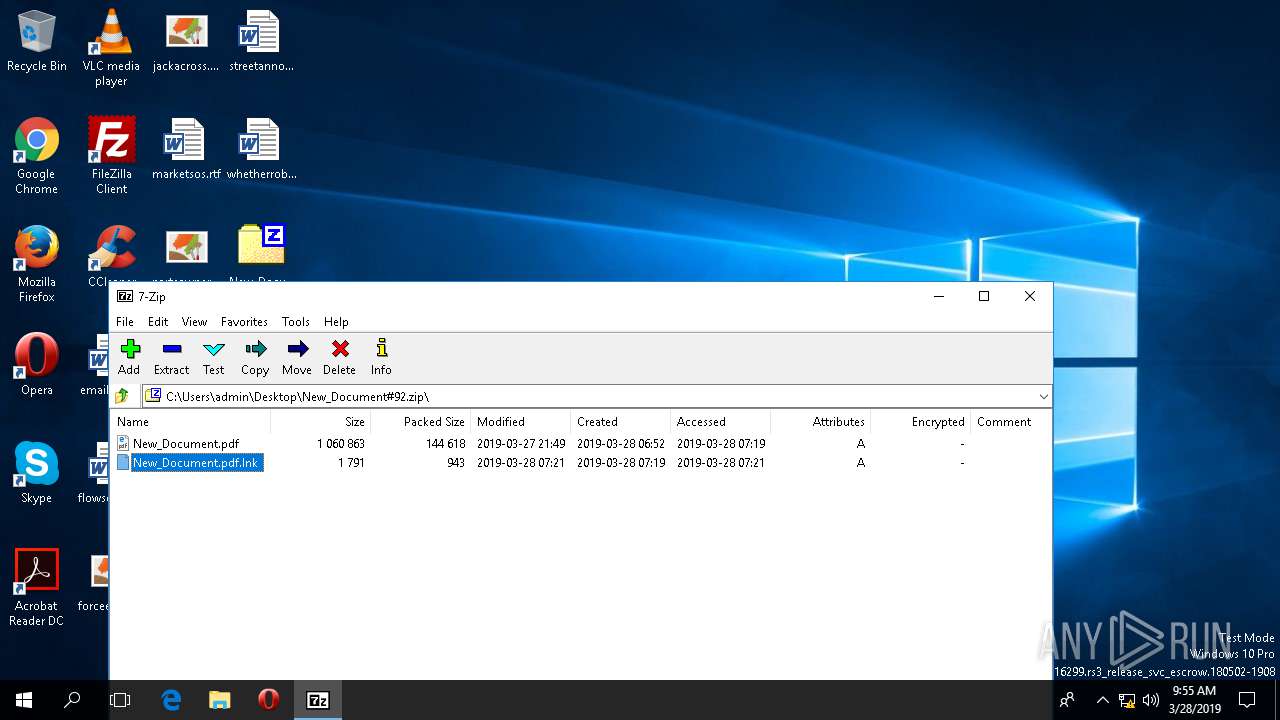
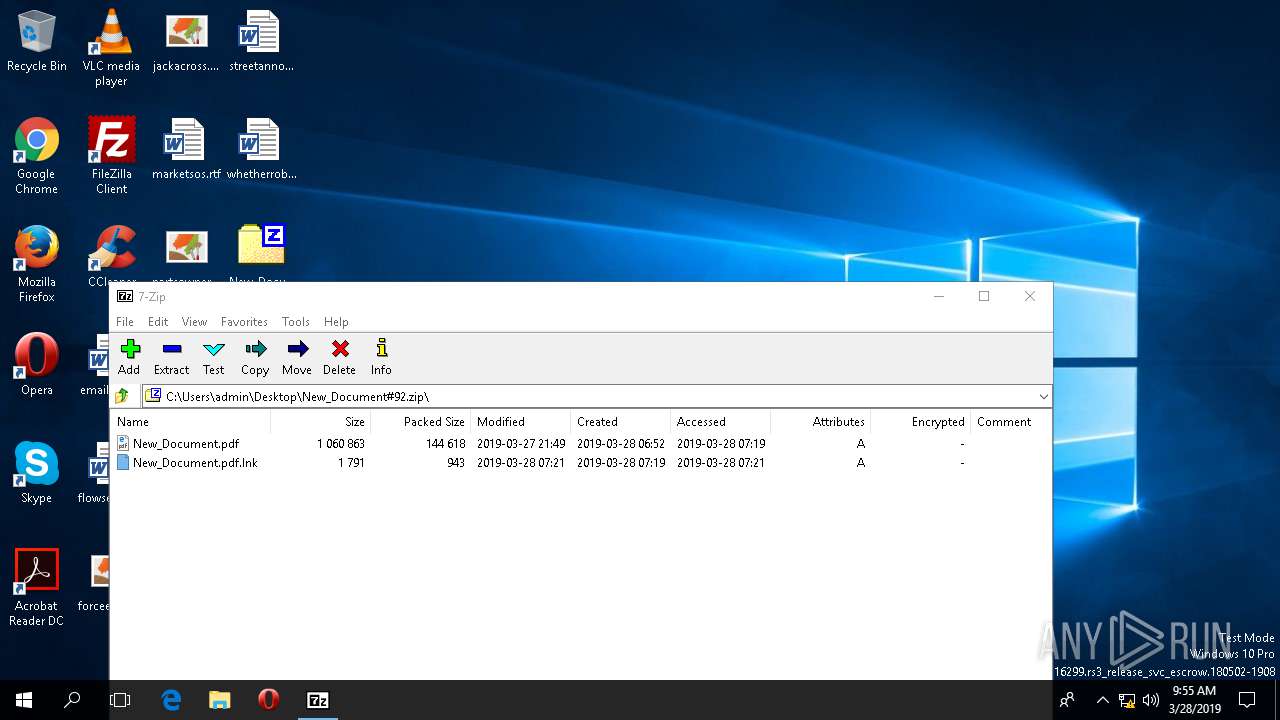
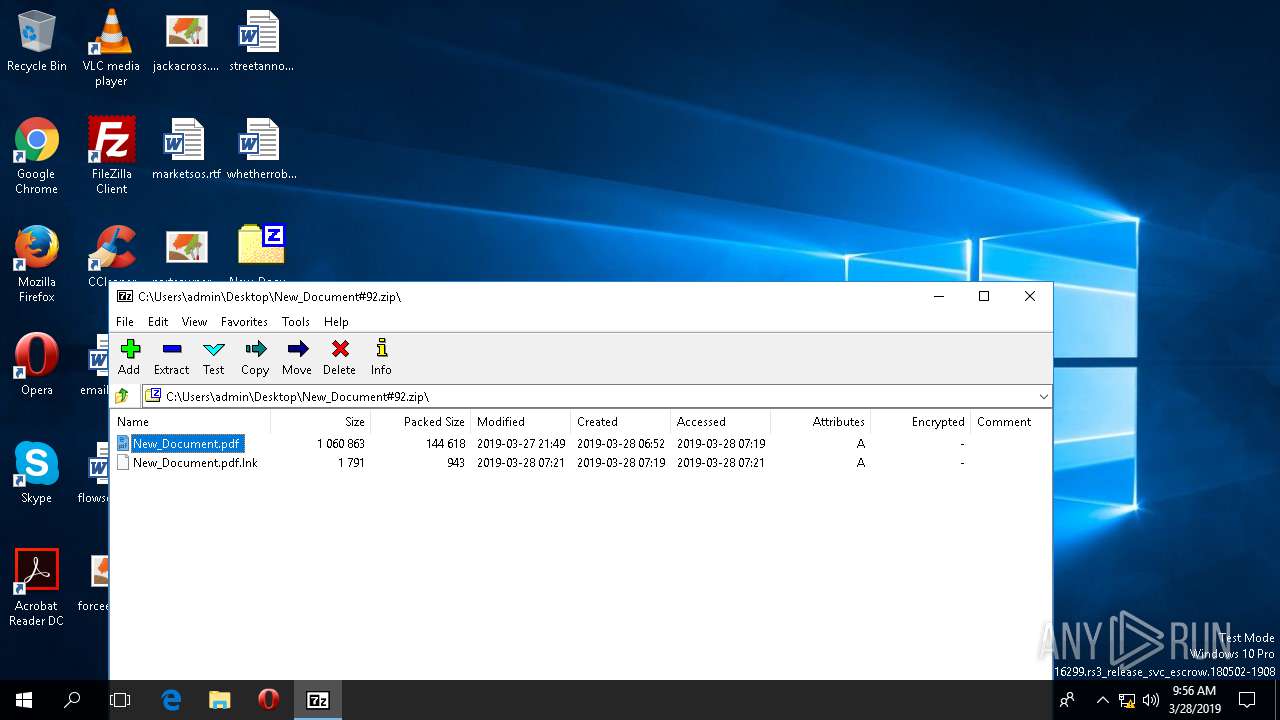
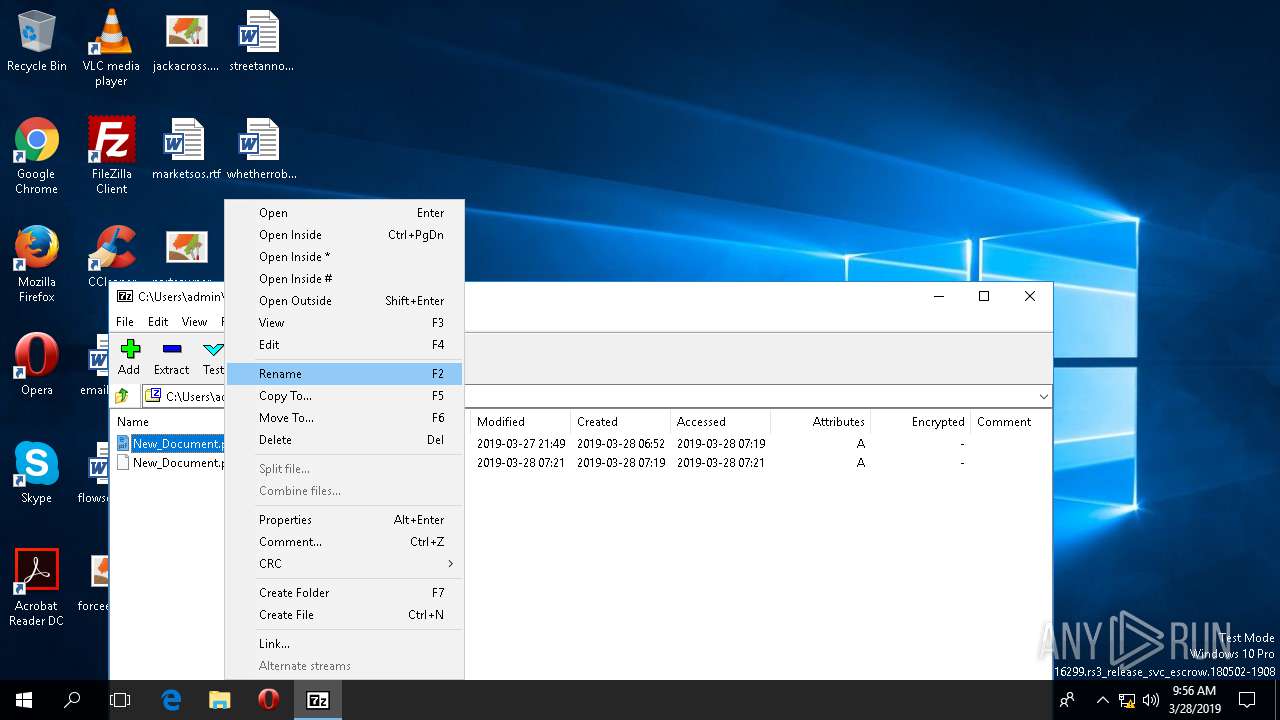
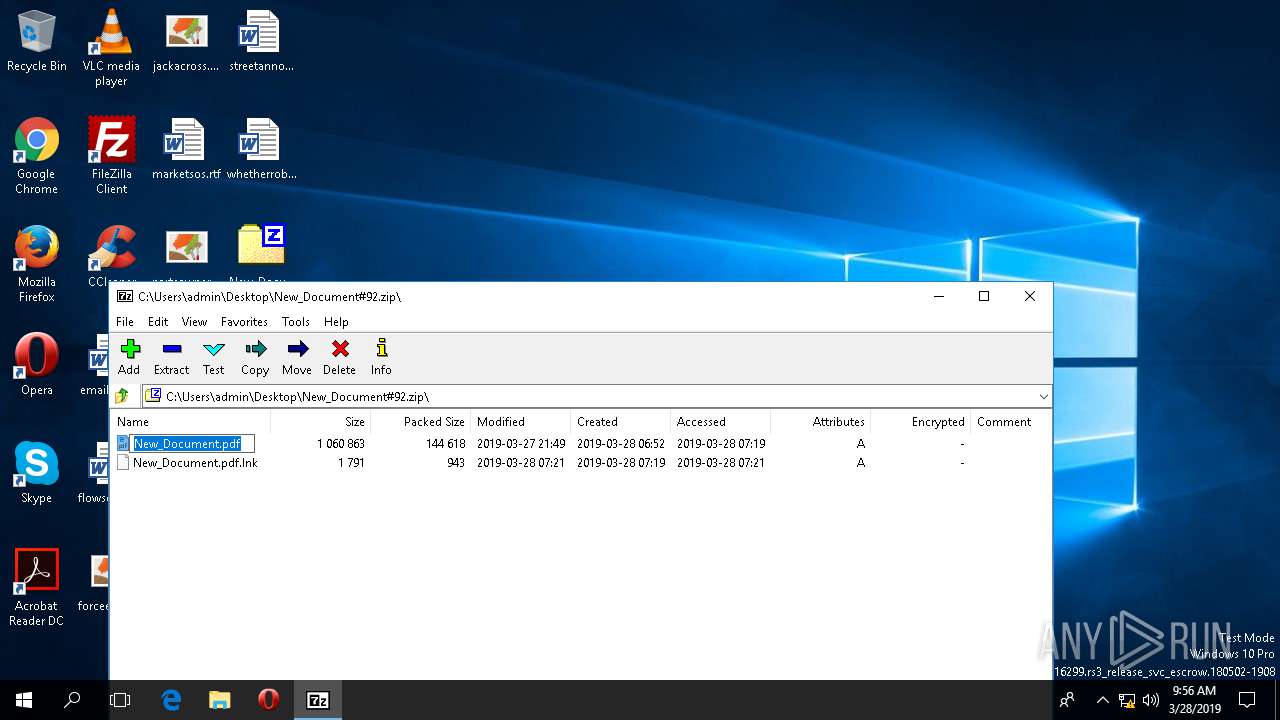
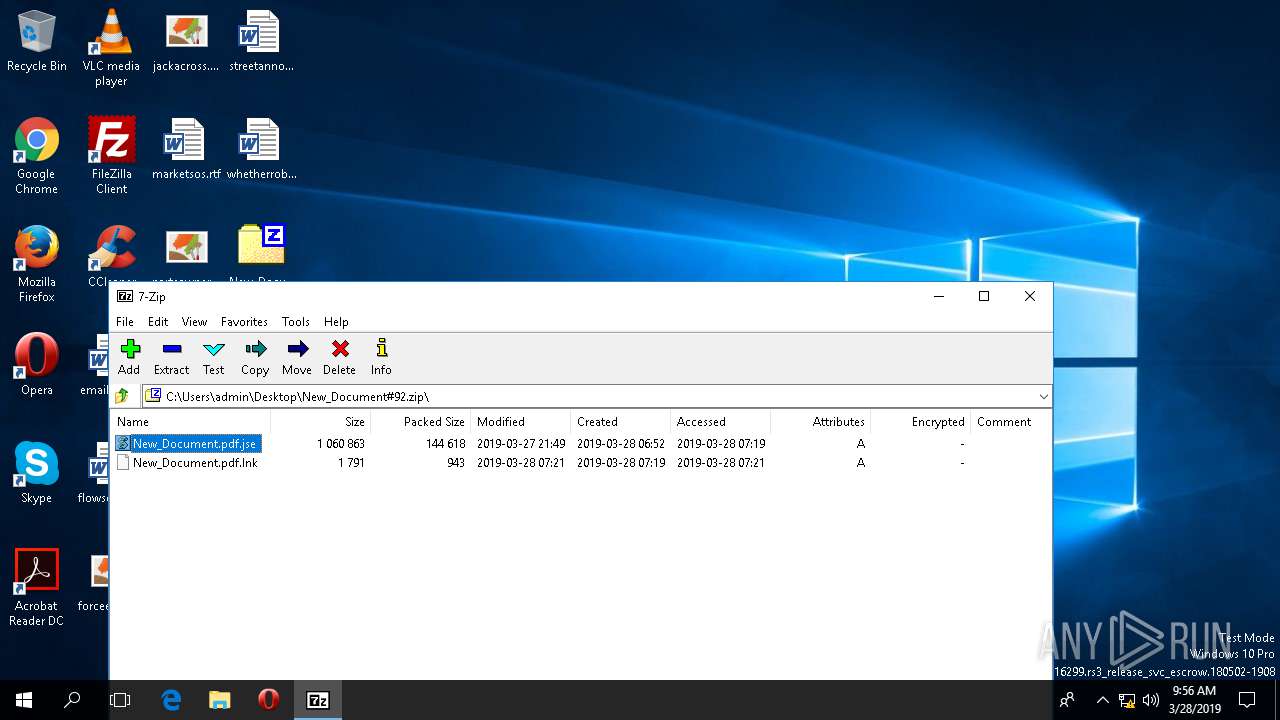
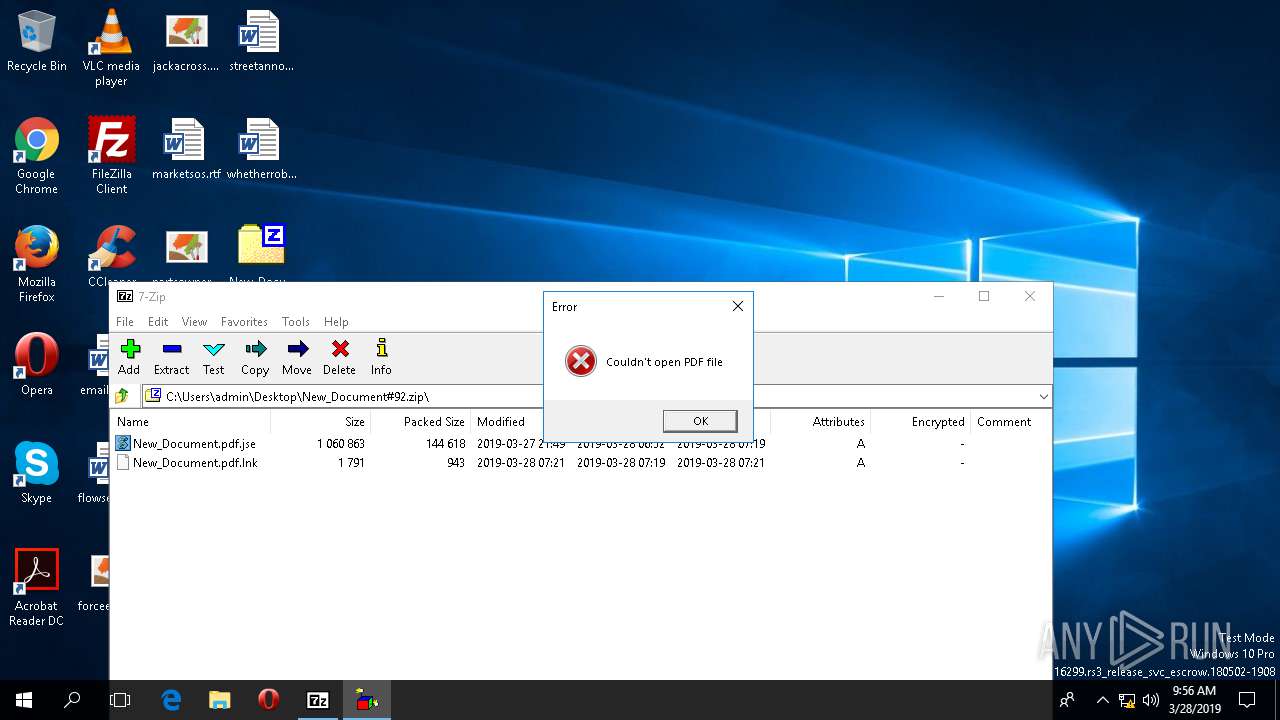
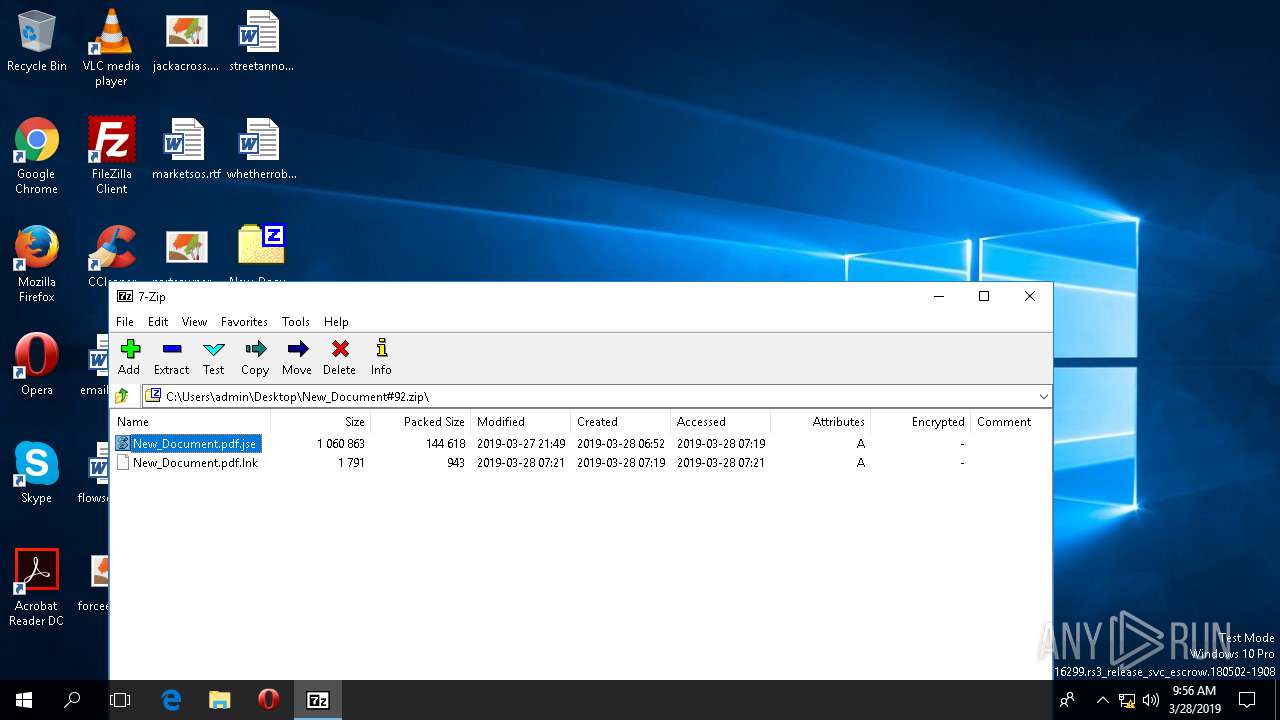
| File name: | New_Document#92.zip |
| Full analysis: | https://app.any.run/tasks/5874f2eb-eb4b-4112-849e-c4a556fccd8f |
| Verdict: | Suspicious activity |
| Analysis date: | March 28, 2019, 09:54:55 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | ABE5E33578FEDF84EADA2115B899C732 |
| SHA1: | 1EB39E64EBB6C9F4C10E02B5F5EA80E3F8E6C364 |
| SHA256: | 23BB1F450FBDEF779F383B414F5649299174837F6704401EE7F4BC8B276D0F1A |
| SSDEEP: | 3072:YRQPdvgVgqytidrJ8TKnxYuvQGHE/9h+ksMH9bImh:YkdL1yJ8TKxHouEVU6H93 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Application launched itself
- cmd.exe (PID: 5040)
- software_reporter_tool.exe (PID: 1208)
Checks supported languages
- OpenWith.exe (PID: 4156)
Starts CMD.EXE for commands execution
- 7zFM.exe (PID: 480)
- cmd.exe (PID: 5040)
Reads the time zone
- chrome.exe (PID: 724)
- chrome.exe (PID: 3348)
- chrome.exe (PID: 848)
Reads the machine GUID from the registry
- software_reporter_tool.exe (PID: 1208)
- WScript.exe (PID: 272)
Executes scripts
- 7zFM.exe (PID: 480)
INFO
Application launched itself
- chrome.exe (PID: 4724)
Reads the machine GUID from the registry
- chrome.exe (PID: 4724)
Reads the software policy settings
- chrome.exe (PID: 4724)
Reads settings of System Certificates
- chrome.exe (PID: 4724)
Loads the Task Scheduler COM API
- software_reporter_tool.exe (PID: 1208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
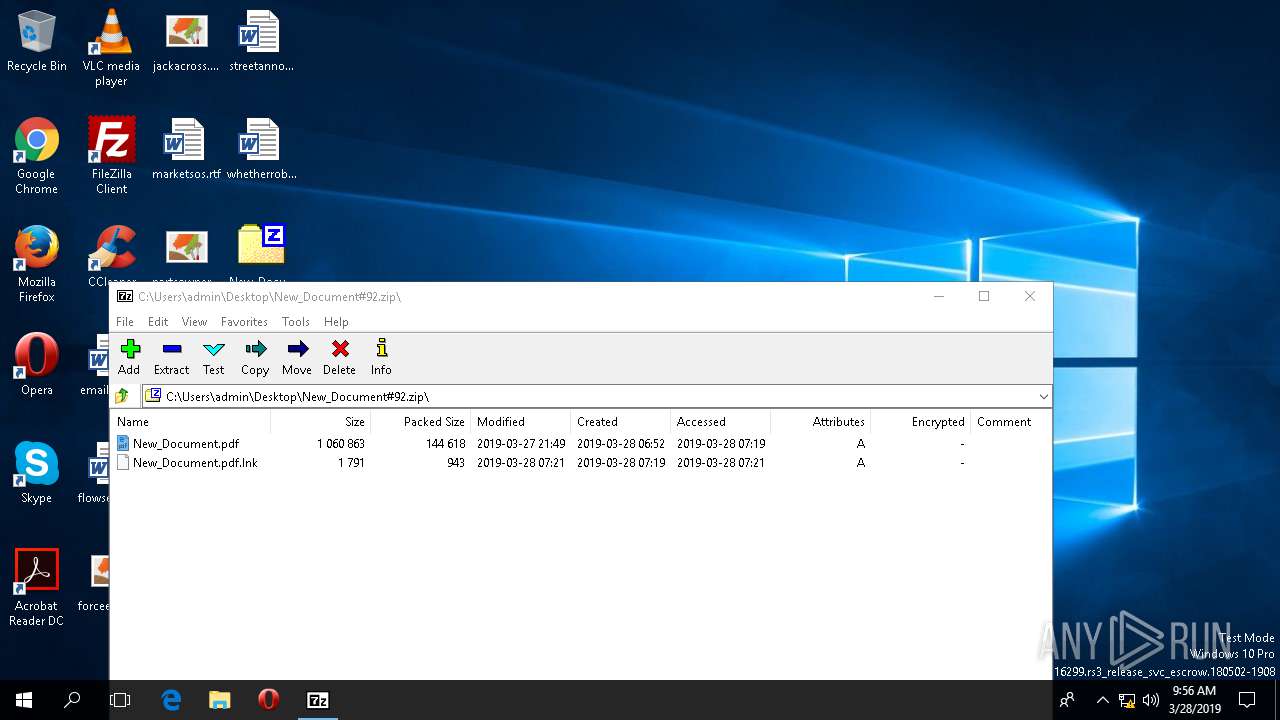
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:03:27 23:49:10 |
| ZipCRC: | 0x0dd1ccde |
| ZipCompressedSize: | 144618 |
| ZipUncompressedSize: | 1060863 |
| ZipFileName: | New_Document.pdf |
Total processes
101
Monitored processes
16
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\7zO0E119589\New_Document.pdf.jse" | C:\Windows\System32\WScript.exe | — | 7zFM.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 480 | "C:\Program Files\7-Zip\7zFM.exe" "C:\Users\admin\Desktop\New_Document#92.zip" | C:\Program Files\7-Zip\7zFM.exe | — | explorer.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 18.01 Modules
| |||||||||||||||
| 724 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1328,12043054571602874643,11027256193928253411,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=BDA10631B6DEC7555F4458E26F285E01 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --enable-compositor-image-animations --service-request-channel-token=BDA10631B6DEC7555F4458E26F285E01 --renderer-client-id=5 --mojo-platform-channel-handle=4076 /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 66.0.3359.181 Modules
| |||||||||||||||
| 848 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1328,12043054571602874643,11027256193928253411,131072 --enable-features=PasswordImport --service-pipe-token=7E4B8DAAFF2A6F9B7F85E80692748CB4 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --enable-compositor-image-animations --service-request-channel-token=7E4B8DAAFF2A6F9B7F85E80692748CB4 --renderer-client-id=3 --mojo-platform-channel-handle=2988 /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 66.0.3359.181 Modules
| |||||||||||||||
| 1176 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=964 --on-initialized-event-handle=660 --parent-handle=664 /prefetch:6 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 66.0.3359.181 Modules
| |||||||||||||||
| 1208 | "C:\Users\admin\AppData\Local\Google\Chrome\User Data\SwReporter\33.171.200\software_reporter_tool.exe" --session-id=MERpsaggtvs3J0icPUBBbvIVIorHG4mEfY0xu0S/ --registry-suffix=URZA | C:\Users\admin\AppData\Local\Google\Chrome\User Data\SwReporter\33.171.200\software_reporter_tool.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Integrity Level: MEDIUM Description: Software Reporter Tool Exit code: 2 Version: 33.171.200 Modules
| |||||||||||||||
| 1512 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=ppapi --field-trial-handle=1328,12043054571602874643,11027256193928253411,131072 --enable-features=PasswordImport --ppapi-flash-args --lang=en-US --device-scale-factor=1 --ppapi-antialiased-text-enabled=0 --ppapi-subpixel-rendering-setting=0 --service-request-channel-token=F2AEF6095B4FF18612B24467BBAB29A8 --mojo-platform-channel-handle=4928 --ignored=" --type=renderer " /prefetch:3 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 66.0.3359.181 Modules
| |||||||||||||||
| 1588 | "c:\users\admin\appdata\local\google\chrome\user data\swreporter\33.171.200\software_reporter_tool.exe" --crash-handler "--database=c:\users\admin\appdata\local\Google\Software Reporter Tool" --url=https://clients2.google.com/cr/report --annotation=plat=Win32 --annotation=prod=ChromeFoil --annotation=ver=33.171.200 --initial-client-data=0x25c,0x260,0x264,0x24c,0x268,0x7ff6e463c2b0,0x7ff6e463c2c0,0x7ff6e463c2d0 | c:\users\admin\appdata\local\google\chrome\user data\swreporter\33.171.200\software_reporter_tool.exe | — | software_reporter_tool.exe | |||||||||||
User: admin Company: Google Integrity Level: MEDIUM Description: Software Reporter Tool Exit code: 0 Version: 33.171.200 Modules
| |||||||||||||||
| 3156 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1328,12043054571602874643,11027256193928253411,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwCAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=72387D3A6000AEC8E5AEFF68B21FDD1C --mojo-platform-channel-handle=1344 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 66.0.3359.181 Modules
| |||||||||||||||
| 3348 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1328,12043054571602874643,11027256193928253411,131072 --enable-features=PasswordImport --service-pipe-token=F0E21636EB426F56AFABA8CD0B60AE97 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --enable-compositor-image-animations --service-request-channel-token=F0E21636EB426F56AFABA8CD0B60AE97 --renderer-client-id=4 --mojo-platform-channel-handle=2504 /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 66.0.3359.181 Modules
| |||||||||||||||
Total events
2 967
Read events
2 776
Write events
187
Delete events
4
Modification events
| (PID) Process: | (480) 7zFM.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MrtCache\C:%5CWindows%5CSystemApps%5CMicrosoft.MicrosoftEdge_8wekyb3d8bbwe%5Cresources.pri\1d3d4f12be32f10\f19bf2c3 |
| Operation: | write | Name: | LanguageList |
Value: _en-US;en_standard_100_US_16_LTR_dark_Desktop | |||
| (PID) Process: | (480) 7zFM.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MrtCache\C:%5CWindows%5CSystemApps%5CMicrosoft.MicrosoftEdge_8wekyb3d8bbwe%5Cresources.pri\1d3d4f12be32f10\f19bf2c3 |
| Operation: | write | Name: | @{microsoft.microsoftedge_41.16299.402.0_neutral__8wekyb3d8bbwe?ms-resource://microsoft.microsoftedge/files/assets/microsoftedgepdf.png} |
Value: C:\WINDOWS\SystemApps\Microsoft.MicrosoftEdge_8wekyb3d8bbwe\Assets\MicrosoftEdgePDF.targetsize-16.png | |||
| (PID) Process: | (480) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (480) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (480) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (480) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
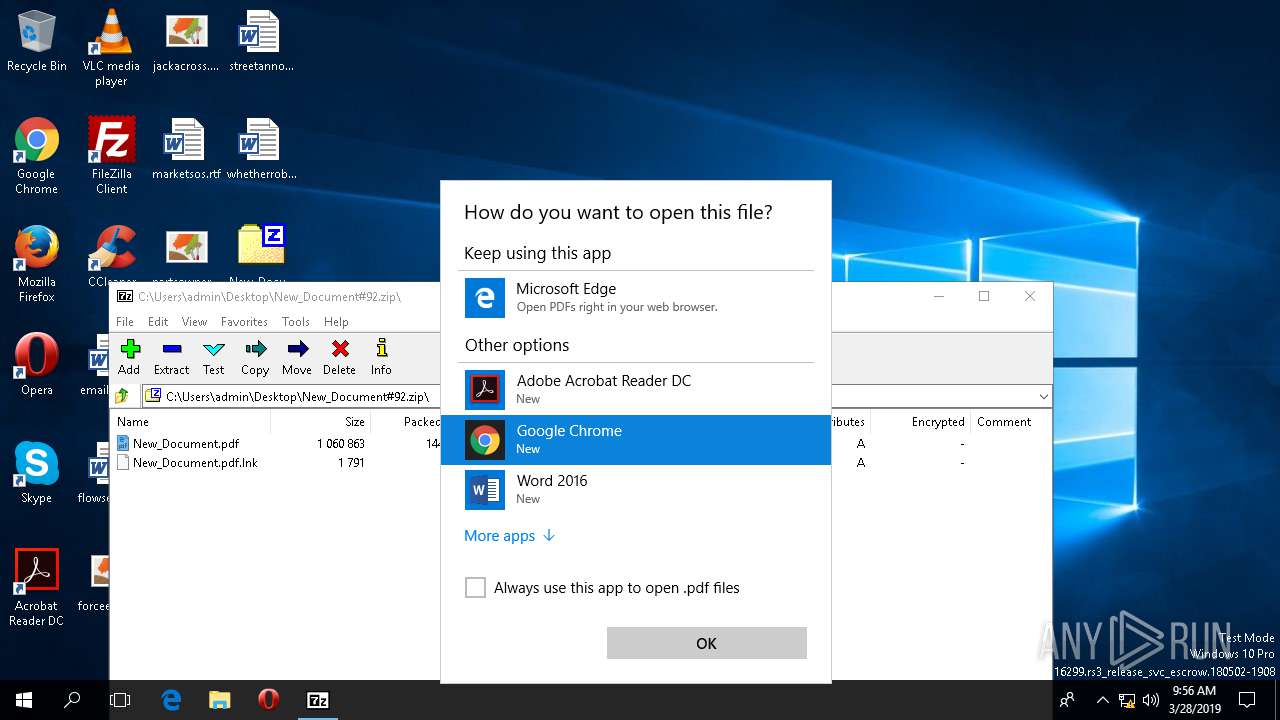
| (PID) Process: | (480) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.pdf\OpenWithProgids |
| Operation: | write | Name: | AcroExch.Document.DC |
Value: | |||
| (PID) Process: | (480) 7zFM.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe.FriendlyAppName |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (480) 7zFM.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe.ApplicationCompany |
Value: Adobe Systems Incorporated | |||
| (PID) Process: | (480) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {E44E9428-BDBC-4987-A099-40DC8FD255E7} {7F9185B0-CB92-43C5-80A9-92277A4F7B54} 0xFFFF |
Value: 010000000000000071EA61774CE5D401 | |||
Executable files
0
Suspicious files
14
Text files
27
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000012.dbtmp | — | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\8ac805cb-d924-40cc-b114-c36dfd6c4dcf.tmp | — | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Login Data-journal | — | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\History-journal | — | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Thumbnails\LOG.old | text | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\fe2841c8-19ab-4ba9-85d8-3674fd711051.tmp | — | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 4724 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4724 | chrome.exe | GET | 200 | 172.217.23.131:443 | https://clientservices.googleapis.com/chrome-variations/seed?osname=win&channel=stable&milestone=66 | US | compressed | 37.7 Kb | whitelisted |
4724 | chrome.exe | GET | 200 | 172.217.16.138:443 | https://translate.googleapis.com/translate_a/l?client=chrome&hl=en&key=AIzaSyBOti4mM-6x9WDnZIjIeyEU21OpBXqWBgw | US | text | 3.18 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4724 | chrome.exe | 172.217.16.138:443 | translate.googleapis.com | Google Inc. | US | whitelisted |
4724 | chrome.exe | 172.217.23.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
apis.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.google.de |
| whitelisted |
www.gstatic.com |
| whitelisted |
translate.googleapis.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
Threats
Process | Message |
|---|---|
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |