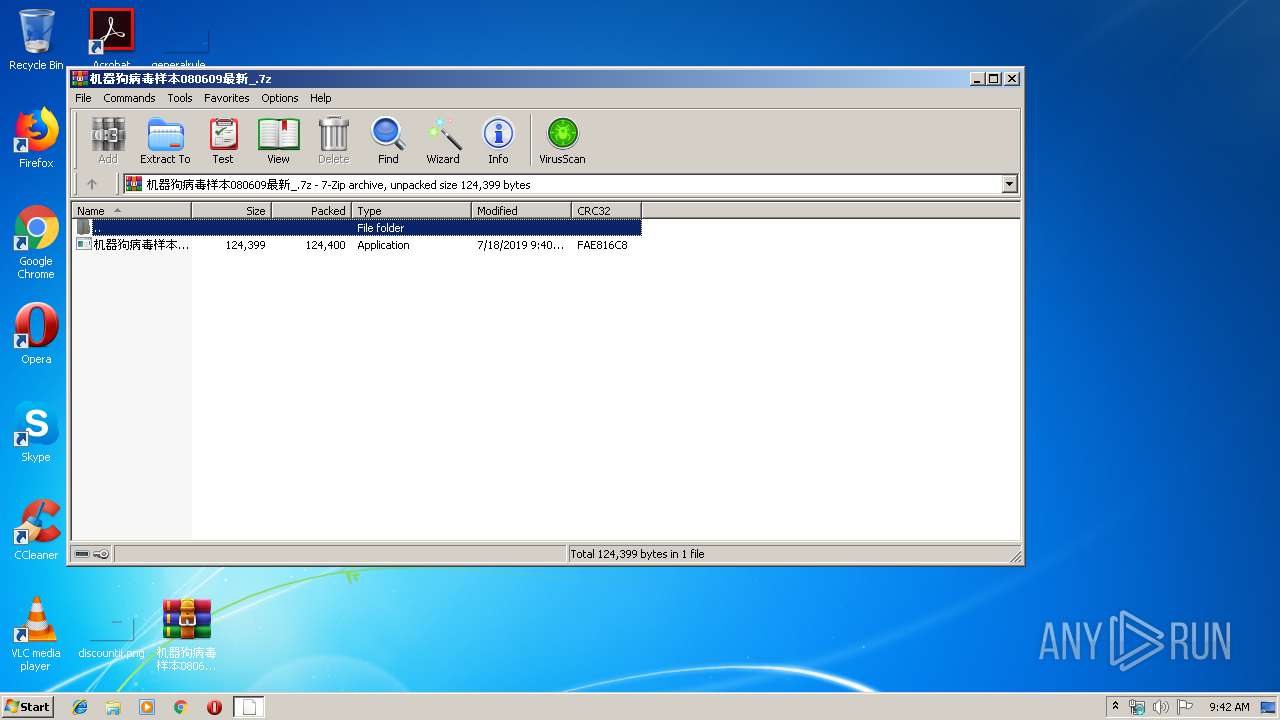
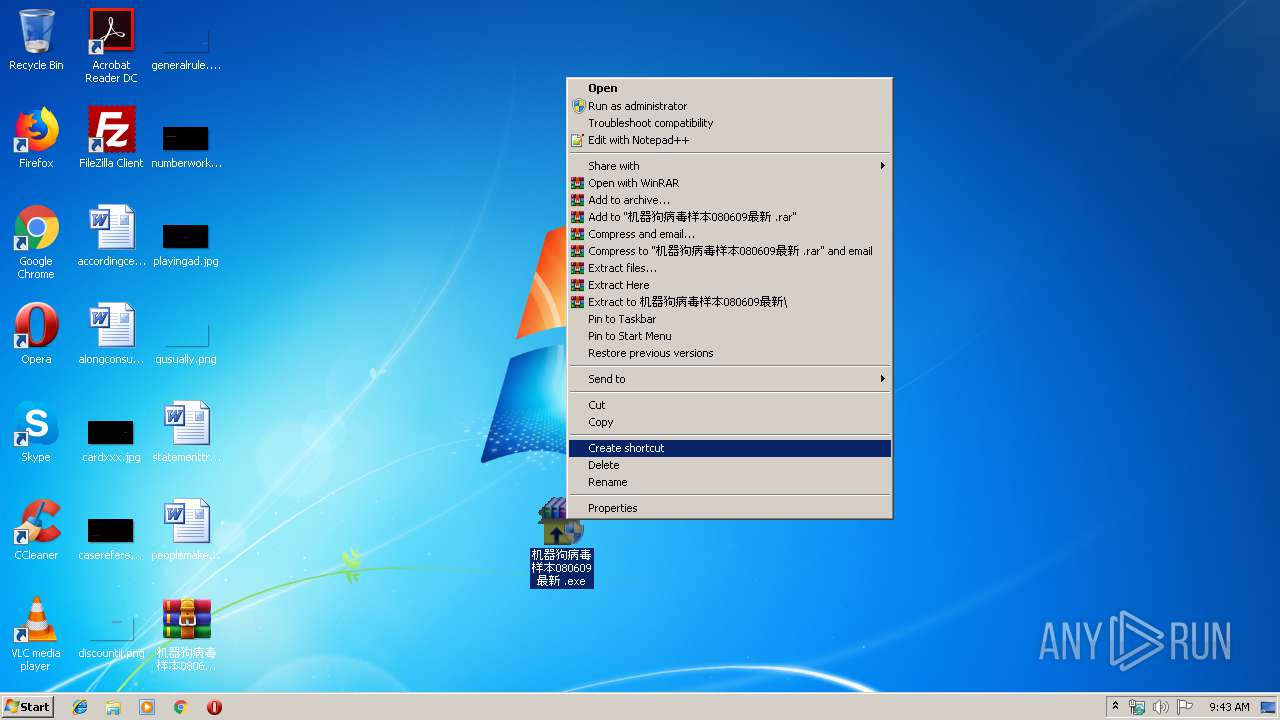
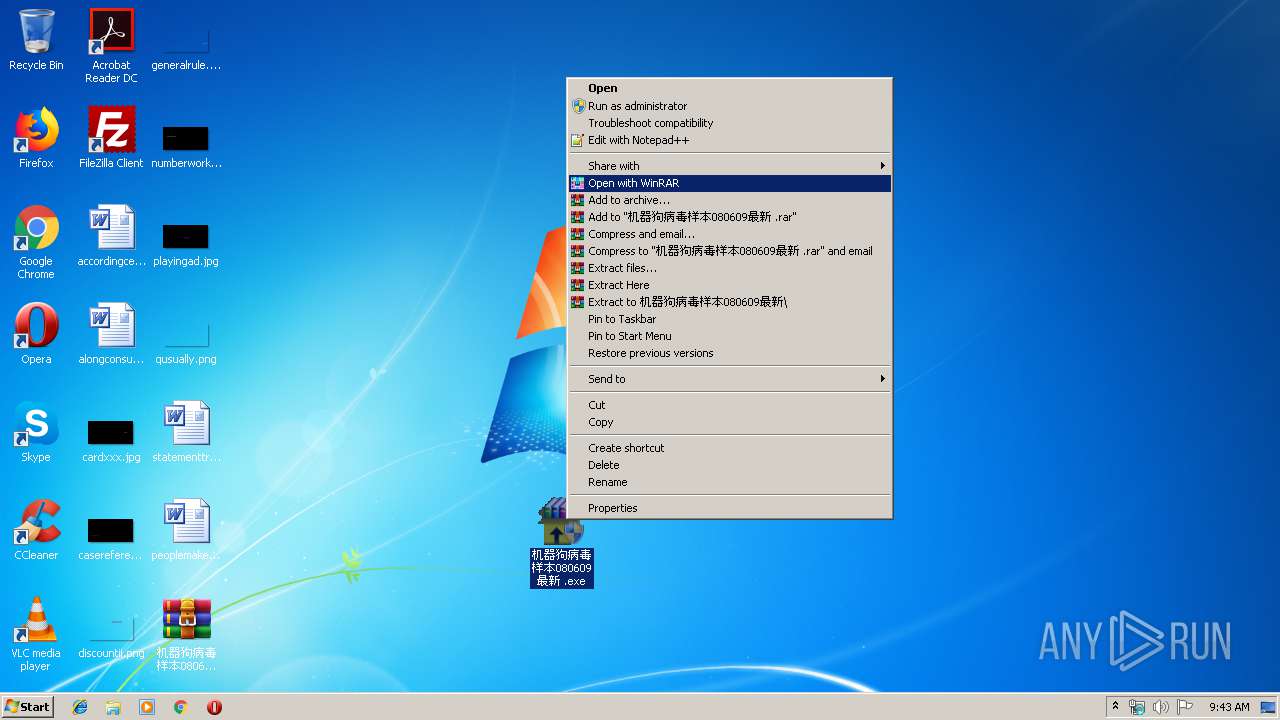
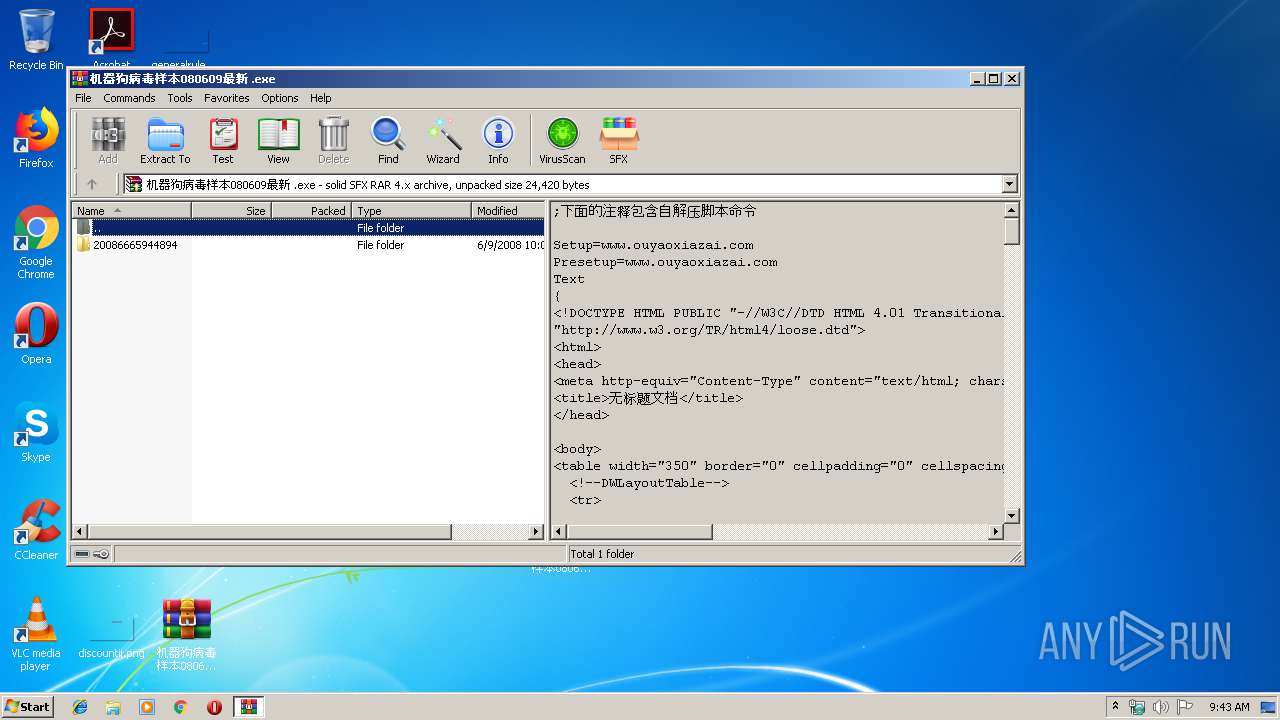
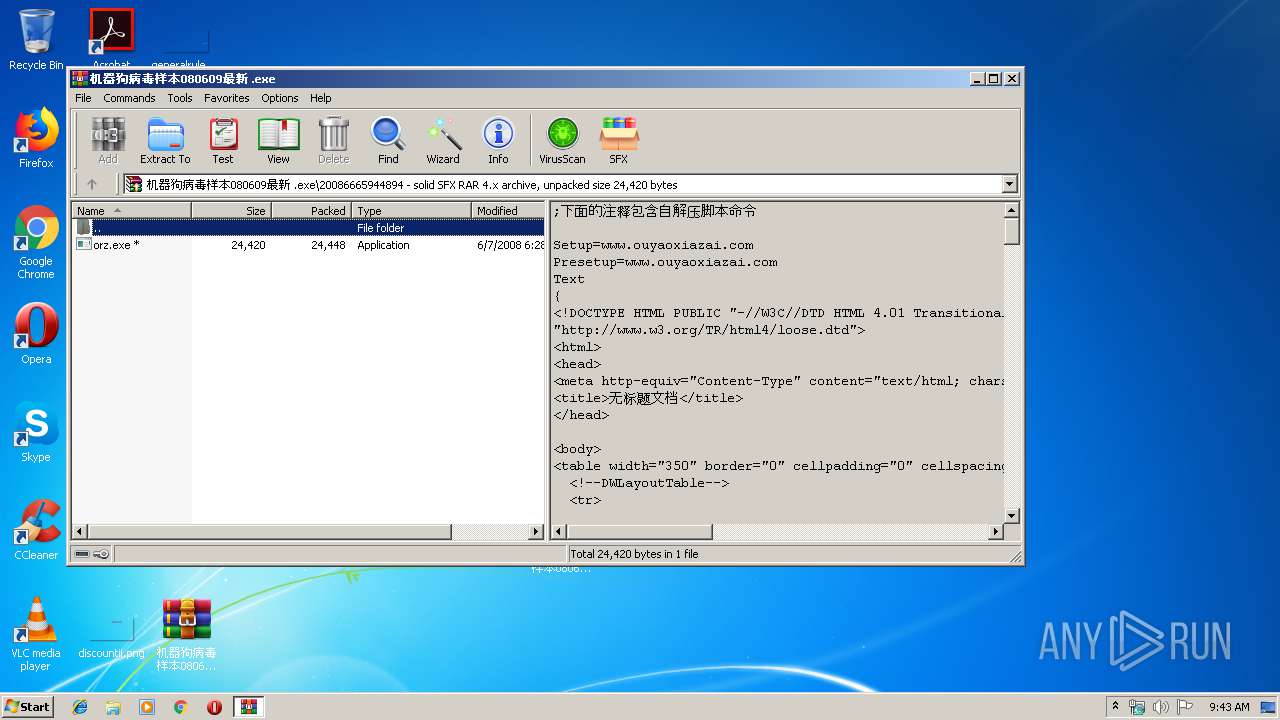
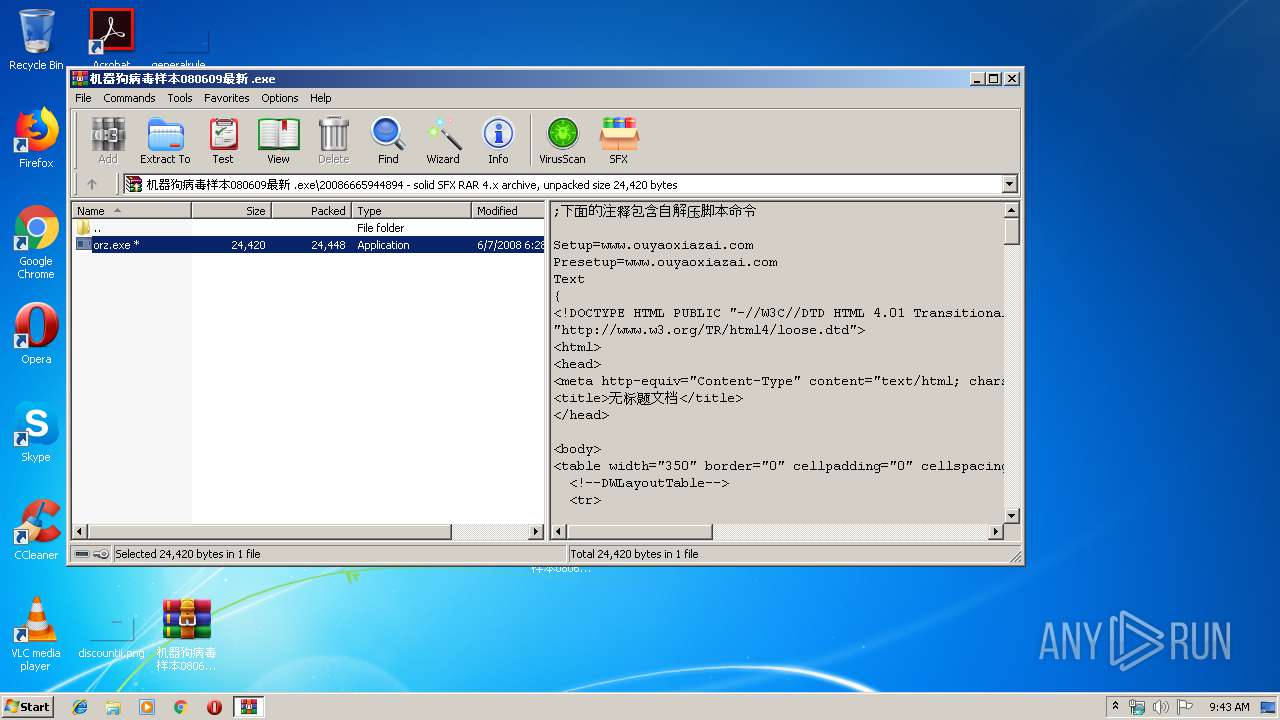
| File name: | 机器狗病毒样本080609最新_.7z |
| Full analysis: | https://app.any.run/tasks/b93bc2a1-d3b5-4bd0-9e90-d8cd90d50532 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2019, 08:42:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 33D8A25689079FFFD45176B85FF37CFE |
| SHA1: | BE7C826D2D5D2416E131B11952F4CCA2A83AE8F7 |
| SHA256: | 23B1AD3A2F082B9AC62E1AC218EAB6374E03B2E500B47CE5A593CB56B0888656 |
| SSDEEP: | 3072:Dt++UWlkcLrVR9r/xO5dV0hH/UCjvEBzu0KR:Dg+UWKcLrVR9LxIdehHcyEZuV |
MALICIOUS
Application was dropped or rewritten from another process
- 机器狗病毒样本080609最新 .exe (PID: 904)
- 机器狗病毒样本080609最新 .exe (PID: 2996)
- orz.exe (PID: 1352)
- orz.exe (PID: 1840)
- abzwtu.exe (PID: 2428)
Loads dropped or rewritten executable
- IEXPLORE.EXE (PID: 3884)
- explorer.exe (PID: 124)
- abzwtu.exe (PID: 2428)
- IEXPLORE.EXE (PID: 1540)
- SearchProtocolHost.exe (PID: 3148)
- SearchProtocolHost.exe (PID: 2892)
Changes Image File Execution Options
- abzwtu.exe (PID: 2428)
SUSPICIOUS
Creates files in the user directory
- explorer.exe (PID: 124)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3628)
- orz.exe (PID: 1352)
- orz.exe (PID: 1840)
- abzwtu.exe (PID: 2428)
Reads Internet Cache Settings
- explorer.exe (PID: 124)
Creates files in the Windows directory
- orz.exe (PID: 1840)
- abzwtu.exe (PID: 2428)
Starts CMD.EXE for commands execution
- orz.exe (PID: 1840)
Removes files from Windows directory
- abzwtu.exe (PID: 2428)
Starts Internet Explorer
- abzwtu.exe (PID: 2428)
Executed as Windows Service
- spoolsv.exe (PID: 2308)
INFO
Manual execution by user
- 机器狗病毒样本080609最新 .exe (PID: 904)
- WinRAR.exe (PID: 2540)
- 机器狗病毒样本080609最新 .exe (PID: 2996)
- orz.exe (PID: 1352)
- orz.exe (PID: 1840)
Reads Microsoft Office registry keys
- SearchProtocolHost.exe (PID: 3148)
- SearchProtocolHost.exe (PID: 2892)
Changes internet zones settings
- IEXPLORE.EXE (PID: 3884)
Reads internet explorer settings
- IEXPLORE.EXE (PID: 1540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
56
Monitored processes
14
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 904 | "C:\Users\admin\Desktop\机器狗病毒样本080609最新 .exe" | C:\Users\admin\Desktop\机器狗病毒样本080609最新 .exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
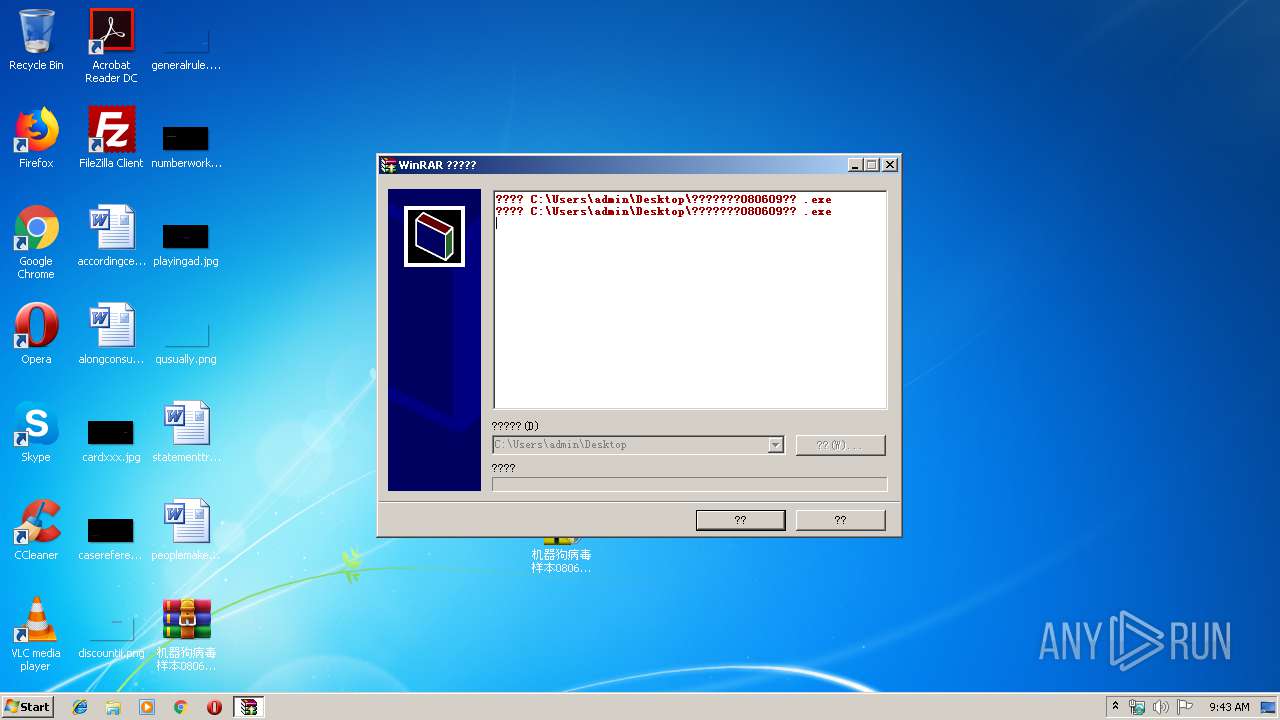
| 1352 | "C:\Users\admin\Desktop\orz.exe" | C:\Users\admin\Desktop\orz.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1540 | "C:\Program Files\Internet Explorer\IEXPLORE.EXE" SCODEF:3884 CREDAT:79873 | C:\Program Files\Internet Explorer\IEXPLORE.EXE | — | IEXPLORE.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1840 | "C:\Users\admin\Desktop\orz.exe" | C:\Users\admin\Desktop\orz.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2164 | cmd /c c:\_uniep.bat | C:\Windows\system32\cmd.exe | — | orz.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2308 | C:\Windows\System32\spoolsv.exe | C:\Windows\System32\spoolsv.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Spooler SubSystem App Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2428 | C:\Windows\system32\abzwtu.exe | C:\Windows\system32\abzwtu.exe | orz.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
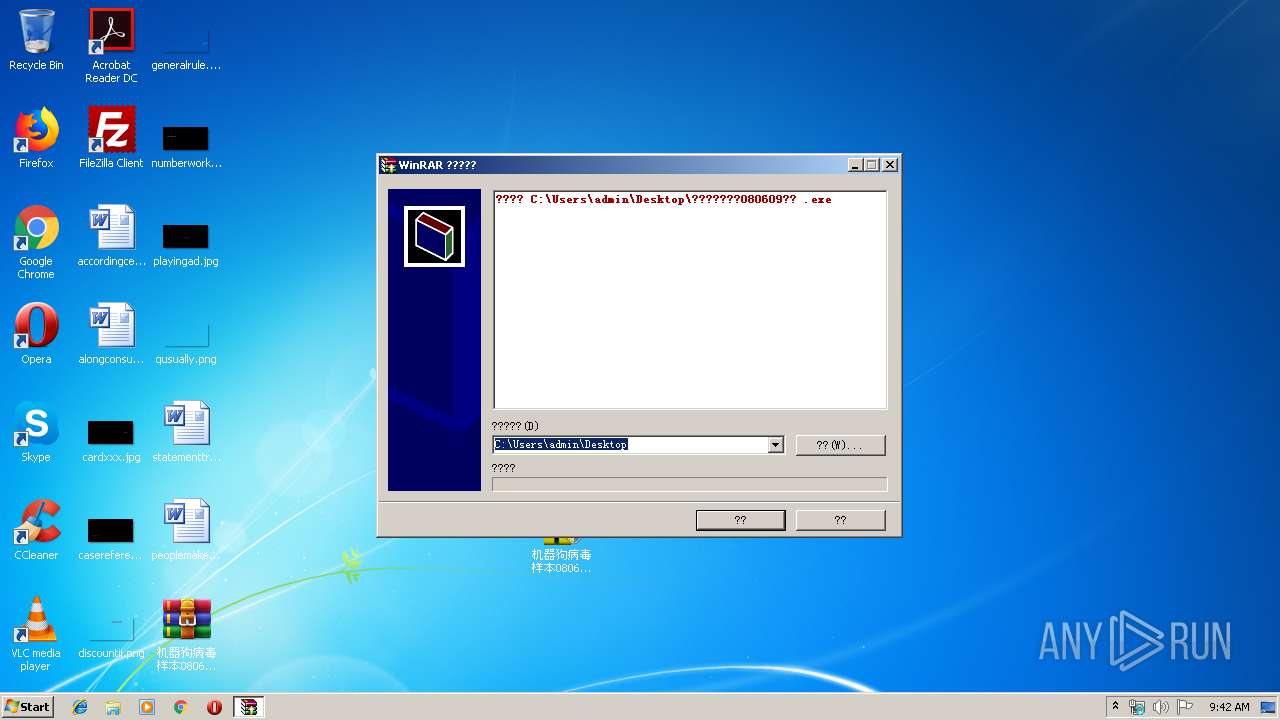
| 2540 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\机器狗病毒样本080609最新 .exe" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2892 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe_S-1-5-21-1302019708-1500728564-335382590-100010_ Global\UsGthrCtrlFltPipeMssGthrPipe_S-1-5-21-1302019708-1500728564-335382590-100010 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" "1" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 958
Read events
4 622
Write events
335
Delete events
1
Modification events
| (PID) Process: | (3628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3628) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\机器狗病毒样本080609最新_.7z | |||
| (PID) Process: | (3628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3628) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (124) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.7z\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (124) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.7z\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
7
Suspicious files
0
Text files
2
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2540.40642\20086665944894\orz.exe | — | |
MD5:— | SHA256:— | |||
| 1840 | orz.exe | C:\Users\admin\AppData\Local\Temp\_temp.dat | — | |
MD5:— | SHA256:— | |||
| 1840 | orz.exe | C:\_uniep.bat | — | |
MD5:— | SHA256:— | |||
| 2428 | abzwtu.exe | C:\Users\admin\AppData\Local\Temp\orz.exe | — | |
MD5:— | SHA256:— | |||
| 3884 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3884 | IEXPLORE.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3148 | SearchProtocolHost.exe | C:\Users\admin\Documents\Outlook Files\~Outlook Data File - NoMail.pst.tmp | — | |
MD5:— | SHA256:— | |||
| 2892 | SearchProtocolHost.exe | C:\Users\admin\Documents\Outlook Files\~Outlook Data File - NoMail.pst.tmp | — | |
MD5:— | SHA256:— | |||
| 124 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\机器狗病毒样本080609最新_.7z.lnk | lnk | |
MD5:— | SHA256:— | |||
| 3628 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3628.37039\机器狗病毒样本080609最新 .exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3884 | IEXPLORE.EXE | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3884 | IEXPLORE.EXE | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
txt.sonuher6.info |
| unknown |
www.bing.com |
| whitelisted |
txt.yinuoben7.info |
| unknown |
xtx.sonuher6.info |
| unknown |
xtx.yinuoben7.info |
| unknown |
tox.sonuher6.info |
| unknown |
tox.yinuoben7.info |
| unknown |