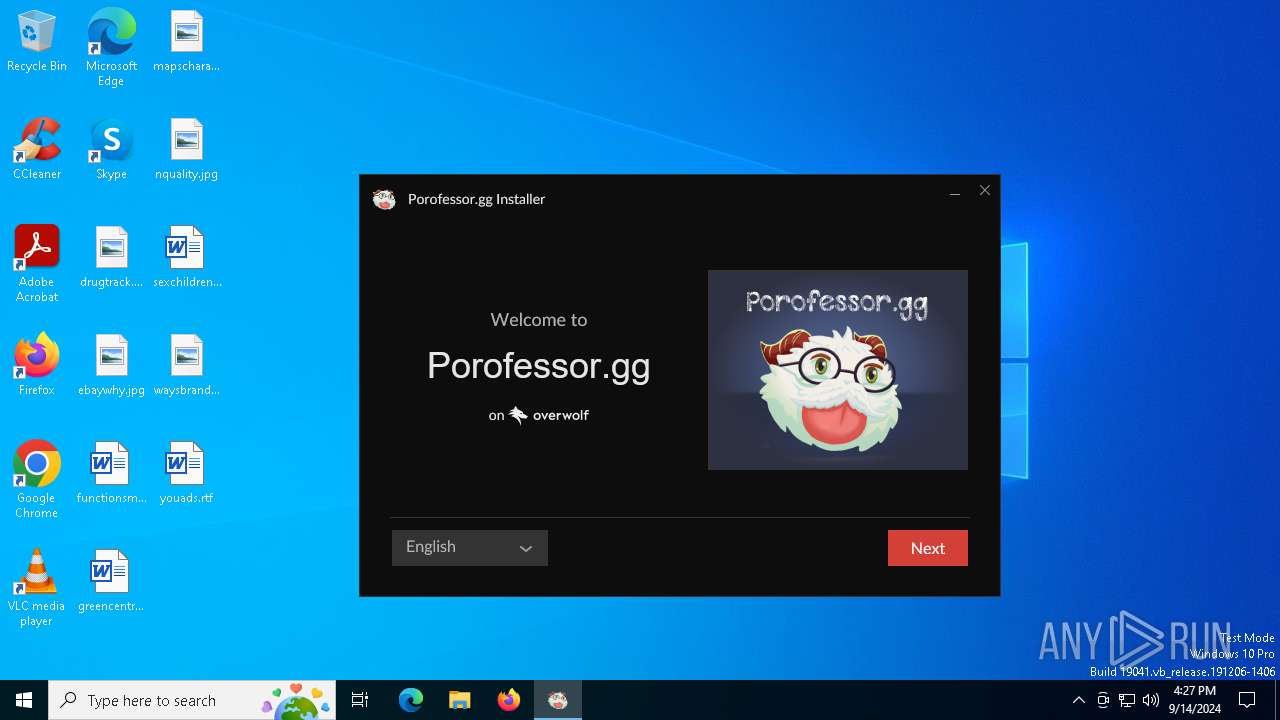
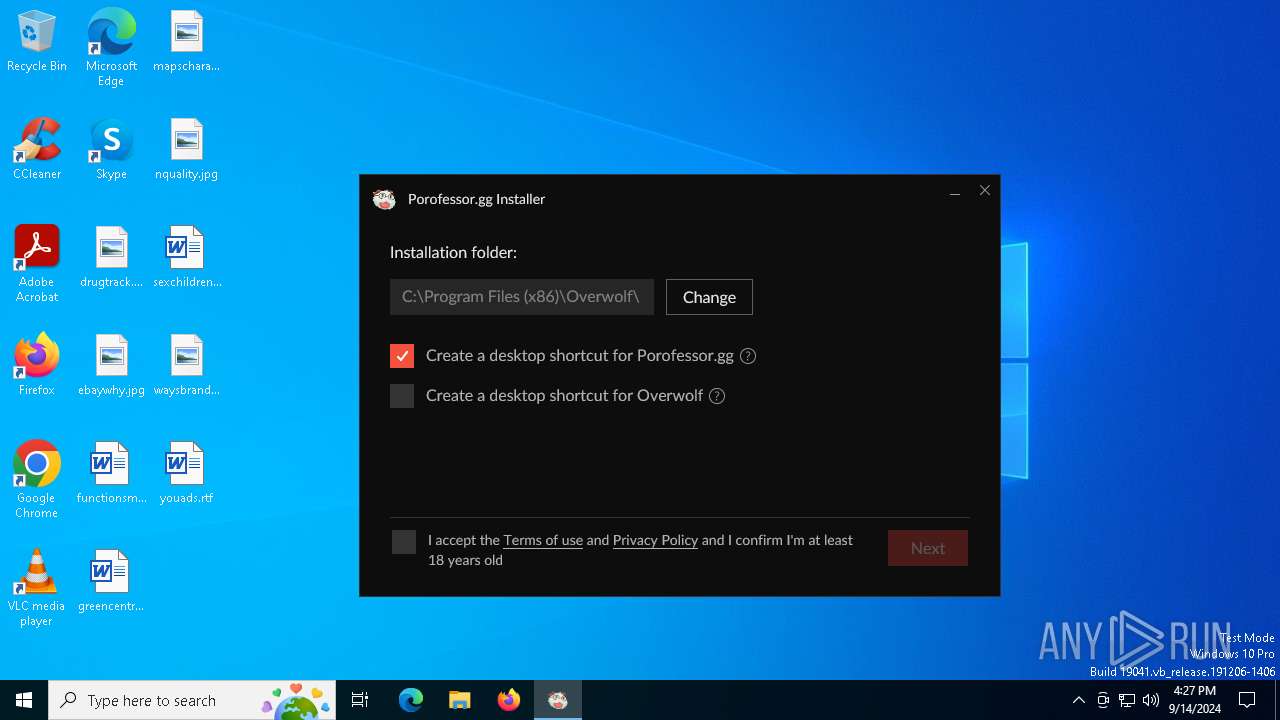
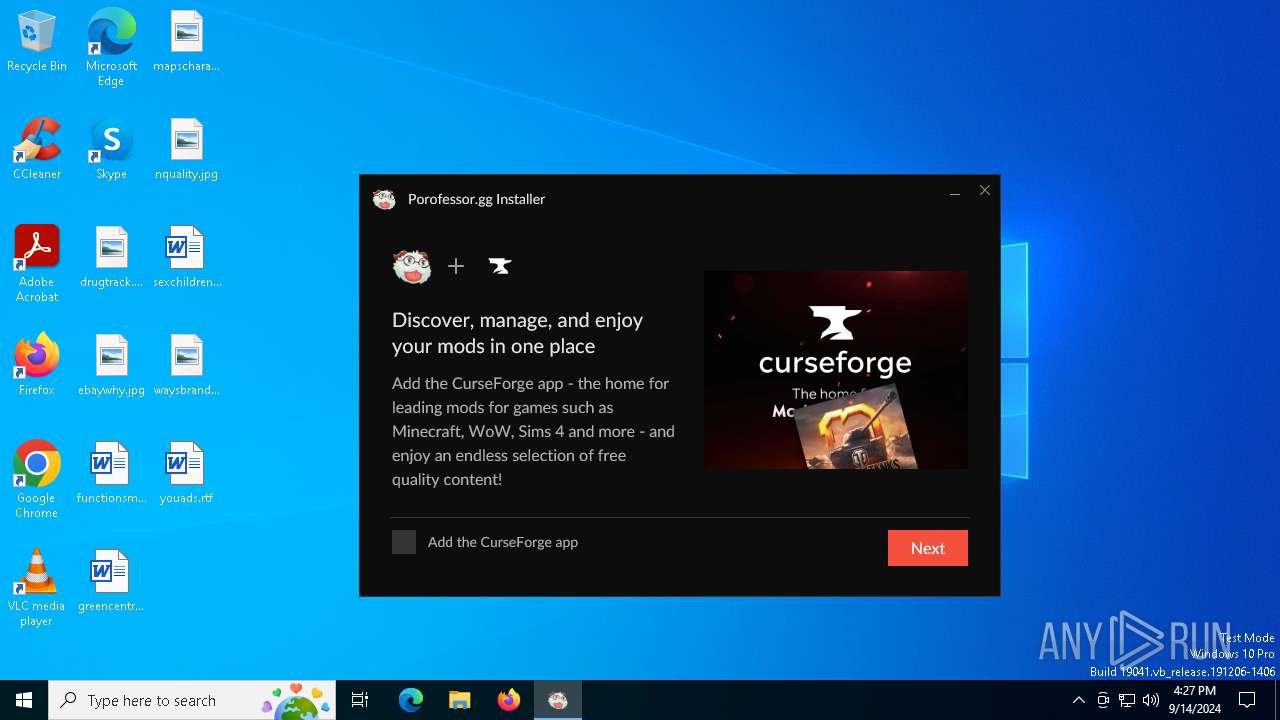
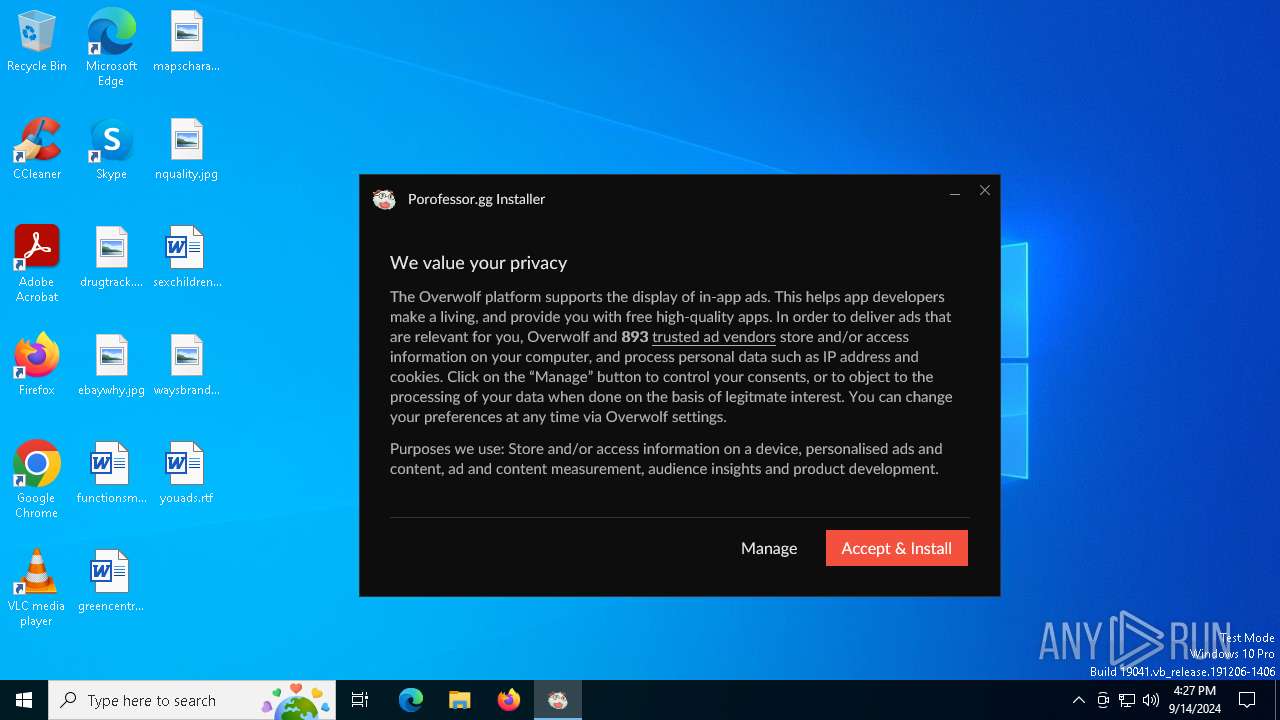
| File name: | Porofessor.gg - Installer.exe |
| Full analysis: | https://app.any.run/tasks/5b28aabe-3377-4781-bc5f-b2fd255e3256 |
| Verdict: | Malicious activity |
| Analysis date: | September 14, 2024, 16:27:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | C82469B121E07ED8F7868EF91A0F7641 |
| SHA1: | 674D605ECF58635CC9CC15F5A7E12EF5A90D673F |
| SHA256: | 23A41A0B304E4277A56F68D0176AA53A482E36263EBEB9763090B450E84BDCD5 |
| SSDEEP: | 98304:O/LL6J/A9nGcRa1xXcVsy3RxeLLCIJgap176MVhbD2bLd129hhoA6qT6p9BwCiqx:6b |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- Porofessor.gg - Installer.exe (PID: 6168)
- Porofessor.gg - Installer.exe (PID: 5548)
- OWInstaller.exe (PID: 6748)
The process creates files with name similar to system file names
- Porofessor.gg - Installer.exe (PID: 6168)
- Porofessor.gg - Installer.exe (PID: 5548)
Application launched itself
- Porofessor.gg - Installer.exe (PID: 6168)
Executable content was dropped or overwritten
- Porofessor.gg - Installer.exe (PID: 6168)
- Porofessor.gg - Installer.exe (PID: 5548)
Creates/Modifies COM task schedule object
- dxdiag.exe (PID: 7028)
Reads the date of Windows installation
- OWInstaller.exe (PID: 6748)
Reads Internet Explorer settings
- OWInstaller.exe (PID: 6748)
Checks Windows Trust Settings
- OWInstaller.exe (PID: 6748)
Reads Microsoft Outlook installation path
- OWInstaller.exe (PID: 6748)
INFO
Create files in a temporary directory
- Porofessor.gg - Installer.exe (PID: 6168)
- OWInstaller.exe (PID: 6748)
- Porofessor.gg - Installer.exe (PID: 5548)
Checks supported languages
- Porofessor.gg - Installer.exe (PID: 6168)
- Porofessor.gg - Installer.exe (PID: 5548)
- OWInstaller.exe (PID: 6748)
Creates files or folders in the user directory
- OWInstaller.exe (PID: 6748)
- dxdiag.exe (PID: 7028)
- Porofessor.gg - Installer.exe (PID: 5548)
Reads the computer name
- OWInstaller.exe (PID: 6748)
- Porofessor.gg - Installer.exe (PID: 6168)
- Porofessor.gg - Installer.exe (PID: 5548)
Reads the machine GUID from the registry
- OWInstaller.exe (PID: 6748)
Process checks computer location settings
- Porofessor.gg - Installer.exe (PID: 6168)
- OWInstaller.exe (PID: 6748)
Reads product name
- OWInstaller.exe (PID: 6748)
Disables trace logs
- OWInstaller.exe (PID: 6748)
Reads Environment values
- OWInstaller.exe (PID: 6748)
The process uses the downloaded file
- OWInstaller.exe (PID: 6748)
Checks proxy server information
- OWInstaller.exe (PID: 6748)
- dxdiag.exe (PID: 7028)
- Porofessor.gg - Installer.exe (PID: 5548)
Reads the software policy settings
- dxdiag.exe (PID: 7028)
- OWInstaller.exe (PID: 6748)
Reads security settings of Internet Explorer
- dxdiag.exe (PID: 7028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:57:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 186880 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x352d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.258.0.4 |
| ProductVersionNumber: | 2.258.0.4 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Overwolf Ltd. |
| FileDescription: | Porofessor |
| FileVersion: | 2.258.0.4 |
| LegalCopyright: | Copyright (C) 2021 Overwolf Ltd. All Rights Reserved. |
| LegalTrademarks: | - |
| ProductName: | Porofessor |
| ProductVersion: | 2.258.0.4 |
Total processes
132
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5548 | "C:\Users\admin\AppData\Local\Temp\Porofessor.gg - Installer.exe" /UAC:60202 /NCRC | C:\Users\admin\AppData\Local\Temp\Porofessor.gg - Installer.exe | Porofessor.gg - Installer.exe | ||||||||||||
User: admin Company: Overwolf Ltd. Integrity Level: HIGH Description: Porofessor Version: 2.258.0.4 Modules
| |||||||||||||||
| 6168 | "C:\Users\admin\AppData\Local\Temp\Porofessor.gg - Installer.exe" | C:\Users\admin\AppData\Local\Temp\Porofessor.gg - Installer.exe | explorer.exe | ||||||||||||
User: admin Company: Overwolf Ltd. Integrity Level: MEDIUM Description: Porofessor Version: 2.258.0.4 Modules
| |||||||||||||||
| 6748 | "C:\Users\admin\AppData\Local\Temp\nskA64B.tmp\OWinstaller.exe" Sel=1&Partner=3776&Extension=pibhbkkgefgheeglaeemkkfjlhidhcedalapdggh&Name=Porofessor.gg&UtmSource=porofessor-website&UtmMedium=download-button&UtmCampaign=download-button&Referer=porofessor.gg&Browser=chrome /UAC:60202 /NCRC -partnerCustomizationLevel 0 --app-name="Porofessor" -exepath C:\Users\admin\AppData\Local\Temp\Porofessor.gg - Installer.exe | C:\Users\admin\AppData\Local\Temp\nskA64B.tmp\OWInstaller.exe | Porofessor.gg - Installer.exe | ||||||||||||
User: admin Company: Overwolf Integrity Level: HIGH Description: Porofessor Installer Version: 2.258.0.8 Modules
| |||||||||||||||
| 7028 | "C:\WINDOWS\System32\DxDiag.exe" /tC:\Users\admin\AppData\Local\Overwolf\Temp\DxDiagOutput.txt | C:\Windows\System32\dxdiag.exe | OWInstaller.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft DirectX Diagnostic Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 476
Read events
11 317
Write events
138
Delete events
21
Modification events
| (PID) Process: | (5548) Porofessor.gg - Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5548) Porofessor.gg - Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5548) Porofessor.gg - Installer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6748) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Overwolf |
| Operation: | write | Name: | MUID |
Value: bb926e54-e3ca-40fd-ae90-2764341e7792 | |||
| (PID) Process: | (7028) dxdiag.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{EEB1CAE3-D0B2-446E-AEDE-727AA9089A1B}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (6748) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\OWinstaller_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6748) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\OWinstaller_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6748) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\OWinstaller_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6748) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\OWinstaller_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6748) OWInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\OWinstaller_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
32
Suspicious files
76
Text files
124
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6168 | Porofessor.gg - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsh9DC0.tmp\uac.dll | executable | |
MD5:861F7E800BB28F68927E65719869409C | SHA256:10A0E8CF46038AB3B2C3CF5DCE407B9A043A631CBDE9A5C8BCF0A54B2566C010 | |||
| 6168 | Porofessor.gg - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsh9DC0.tmp\System.dll | executable | |
MD5:51BD16A2EA23AE1E7A92CEDC6785C82E | SHA256:4DBC79D2B1C7987CC64BB5D014DB81BB5108BDD6D8BF3A5F820FAC1DED62BE33 | |||
| 6168 | Porofessor.gg - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsh9DC0.tmp\UserInfo.dll | executable | |
MD5:1DD4CA0F4A94155F8D46EC95A20ADA4A | SHA256:A27DC3069793535CB64123C27DCA8748983D133C8FA5AADDEE8CDBC83F16986D | |||
| 6168 | Porofessor.gg - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsh9DC0.tmp\log4net.dll | executable | |
MD5:F15C8A9E2876568B3910189B2D493706 | SHA256:AE9C8073C3357C490F5D1C64101362918357C568F6B9380A60B09A4A4C1FF309 | |||
| 6168 | Porofessor.gg - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsh9DC0.tmp\utils.dll | executable | |
MD5:C6B46A5FCDCCBF3AEFF930B1E5B383D4 | SHA256:251AB3E2690562DCFCD510642607F206E6DCF626D06D94B74E1FA8297B1050A0 | |||
| 6168 | Porofessor.gg - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsh9DC0.tmp\OverWolf.Client.CommonUtils.dll | executable | |
MD5:F927B95203A3D1D253938EAD1F8143C6 | SHA256:AC480A104D0EC21BB96EC6E5EA3418A3118EA80A07426DCD2E1E01FF41147F40 | |||
| 6168 | Porofessor.gg - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsh9DC0.tmp\Newtonsoft.Json.dll | executable | |
MD5:98CBB64F074DC600B23A2EE1A0F46448 | SHA256:7B44639CBFBC8DDAC8C7A3DE8FFA97A7460BEBB0D54E9FF2E1CCDC3A742C2B13 | |||
| 6168 | Porofessor.gg - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsh9DC0.tmp\OWInstaller.exe | executable | |
MD5:ED5782D57235038DBCAB36F301A48C2E | SHA256:79A6B6C704E5007F1A8D1DF3BF951FC3C05D957C8871B275B5448E307FFE2AD2 | |||
| 6168 | Porofessor.gg - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsh9DC0.tmp\CommandLine.dll | executable | |
MD5:29D9046304542E1CE30EBA022C49DFCC | SHA256:DD954BC5C2F8EAD7580EE492A242EA3F09DC07B601BFADD1AB5AC804FC54DA01 | |||
| 6168 | Porofessor.gg - Installer.exe | C:\Users\admin\AppData\Local\Temp\nsh9DC0.tmp\DotNetZip.dll | executable | |
MD5:190E712F2E3B065BA3D5F63CB9B7725E | SHA256:6C512D9943A225D686B26FC832589E4C8BEF7C4DD0A8BDFD557D5D27FE5BBA0F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
55
DNS requests
31
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6748 | OWInstaller.exe | GET | 200 | 216.58.206.78:80 | http://www.google-analytics.com/__utm.gif?utmwv=4.7.2&utmn=4344522&utmhn=&utmcs=UTF-8&utmsr=-&utmsc=-&utmul=-&utmje=0&utmfl=-&utmdt=&utmhid=74537082&utmr=/&utmp=/&utmac=UA-80584726-1&utmcc=__utma%3D0.1928497617.1726331249.1726331249.1726331249.2%3B%2B__utmz%3D0.1726331249.1.1.utmcsr%3D%28direct%29%7Cutmccn%3D%7Cutmcmd%3D%3B&utme=5%28Funnel2%2AInstaller%20Launched%2A2.0.50727%20SP2%2C%203.0%20SP2%2C%203.5%20SP1%2C%204%20Client%2C%204%20Full%2C%204.0%20Client%29%28%29&gaq=1&utmt=event | unknown | — | — | whitelisted |
5548 | Porofessor.gg - Installer.exe | GET | 200 | 18.65.39.36:80 | http://analyticsnew.overwolf.com/analytics/Counter?Name=installer_uac_action&Value=1&&Extra=%5b%7b%22Name%22%3a%22installer_version%22%2c%22Value%22%3a%222.258.0.4%22%7d%5d | unknown | — | — | whitelisted |
6748 | OWInstaller.exe | GET | 200 | 216.58.206.78:80 | http://www.google-analytics.com/__utm.gif?utmwv=4.7.2&utmn=112324055&utmhn=&utmcs=UTF-8&utmsr=-&utmsc=-&utmul=-&utmje=0&utmfl=-&utmdt=&utmhid=655887135&utmr=/&utmp=/&utmac=UA-18298709-8&utmcc=__utma%3D0.1928497617.1726331249.1726331249.1726331249.2%3B%2B__utmz%3D0.1726331249.1.1.utmcsr%3D%28direct%29%7Cutmccn%3D%7Cutmcmd%3D%3B&utme=5%28Funnel2%2AInstaller%20Launched%2A2.0.50727%20SP2%2C%203.0%20SP2%2C%203.5%20SP1%2C%204%20Client%2C%204%20Full%2C%204.0%20Client%29%28%29&gaq=1&utmt=event | unknown | — | — | whitelisted |
6748 | OWInstaller.exe | GET | 200 | 142.250.185.163:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
6856 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6748 | OWInstaller.exe | GET | 200 | 142.250.186.67:80 | http://o.pki.goog/wr2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTQtSEi8EX%2BbYUTXd8%2ByMxD3s1zQQU3hse7XkV1D43JMMhu%2Bw0OW1CsjACEGs31zQSL0RFCna%2BsoPon%2Bg%3D | unknown | — | — | whitelisted |
7028 | dxdiag.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl%20 | unknown | — | — | whitelisted |
6748 | OWInstaller.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
6112 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5516 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6856 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6164 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5548 | Porofessor.gg - Installer.exe | 18.65.39.36:80 | analyticsnew.overwolf.com | AMAZON-02 | US | whitelisted |
6748 | OWInstaller.exe | 216.58.206.78:80 | www.google-analytics.com | GOOGLE | US | whitelisted |
6748 | OWInstaller.exe | 18.65.39.36:443 | analyticsnew.overwolf.com | AMAZON-02 | US | whitelisted |
6748 | OWInstaller.exe | 18.239.83.31:443 | content.overwolf.com | — | US | whitelisted |
6748 | OWInstaller.exe | 18.239.94.53:443 | storeapi.overwolf.com | — | US | shared |
6748 | OWInstaller.exe | 18.65.41.80:80 | ocsp.rootca3.amazontrust.com | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
analyticsnew.overwolf.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
content.overwolf.com |
| whitelisted |
storeapi.overwolf.com |
| shared |
ocsp.rootca3.amazontrust.com |
| unknown |
www.overwolf.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
fonts.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5548 | Porofessor.gg - Installer.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2 ETPRO signatures available at the full report