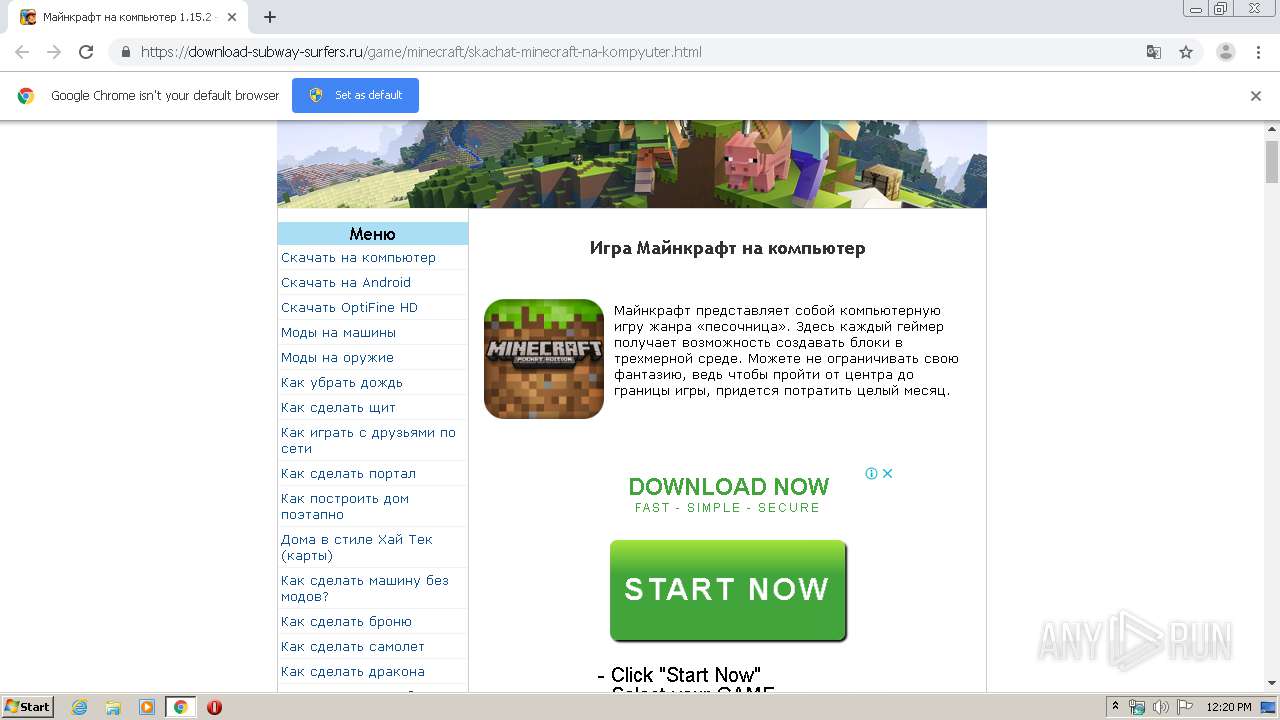
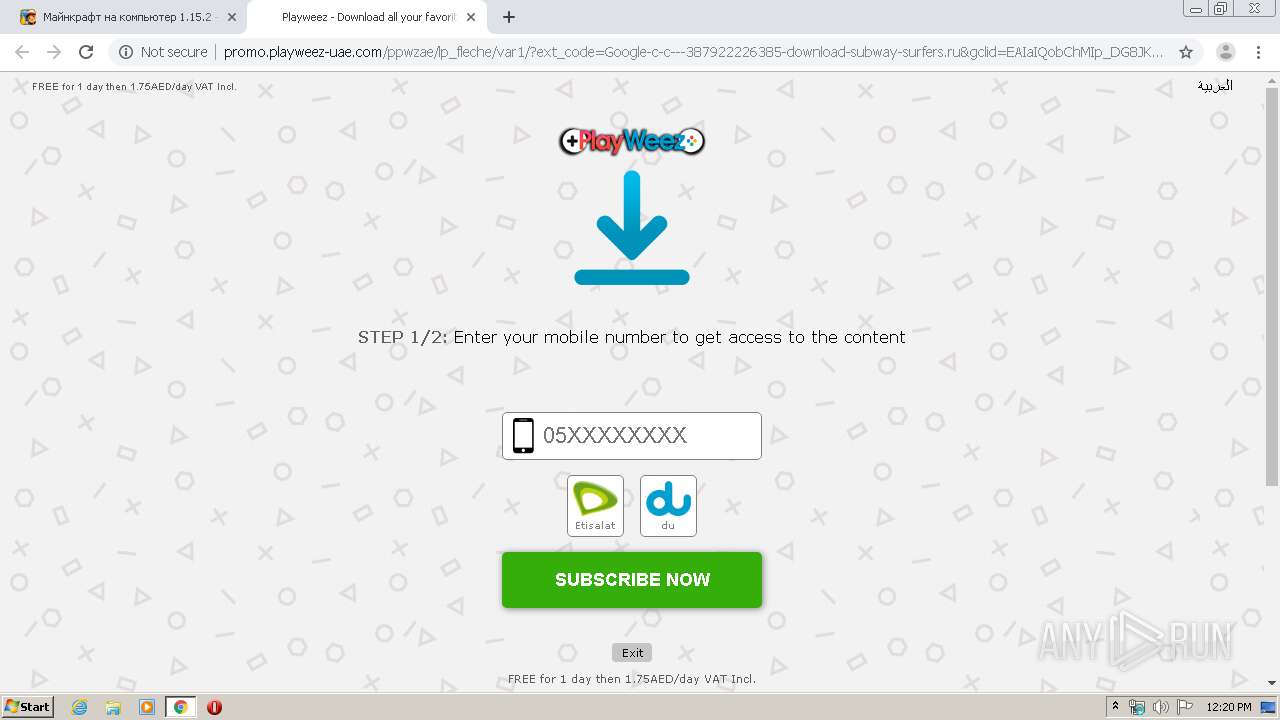
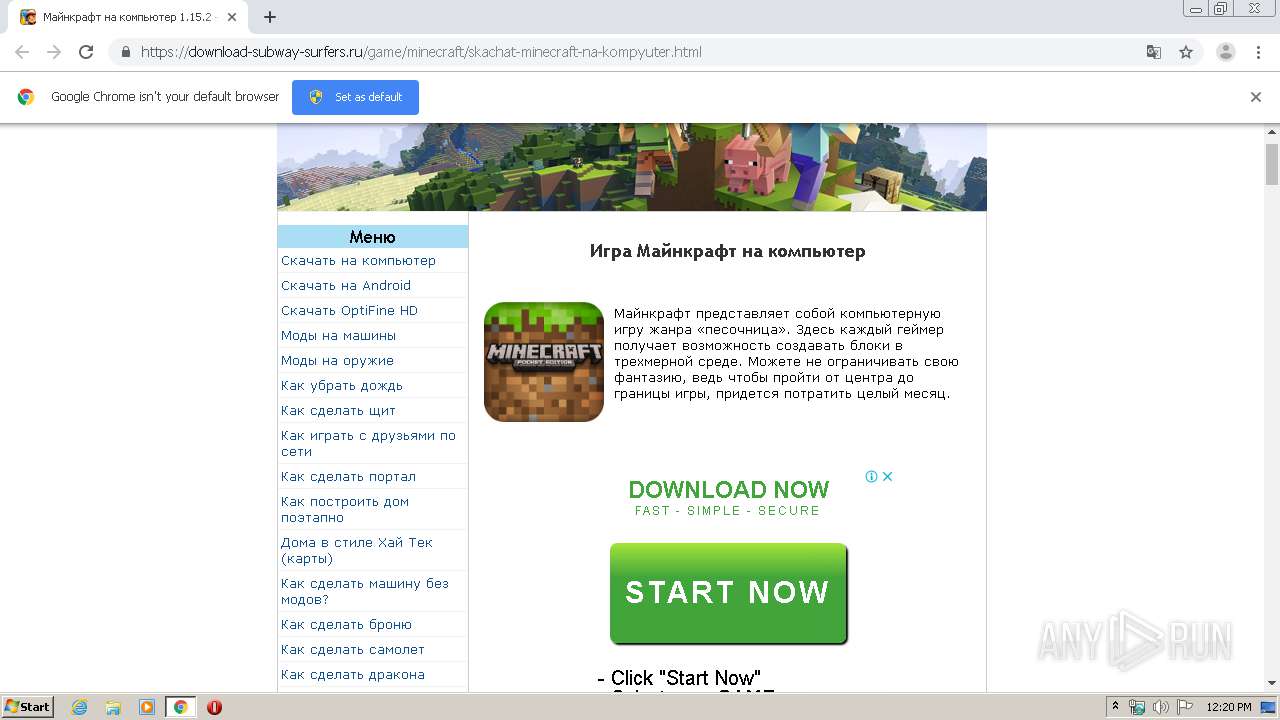
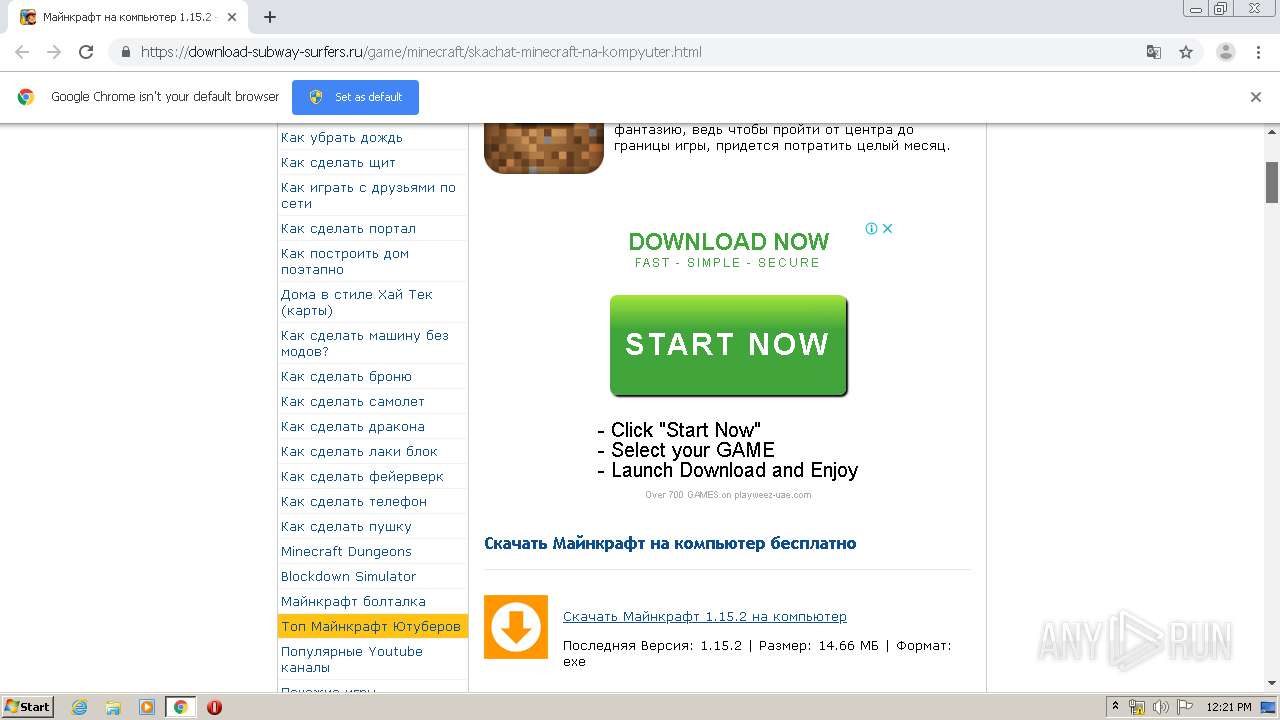
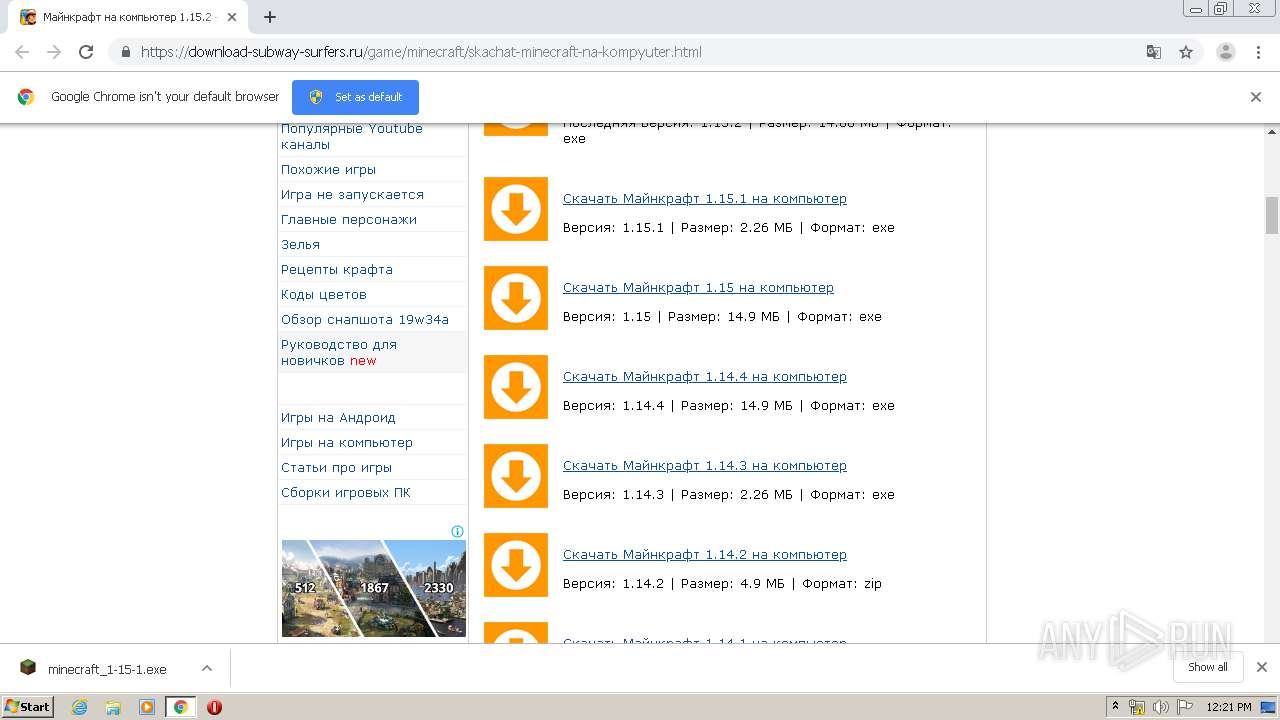
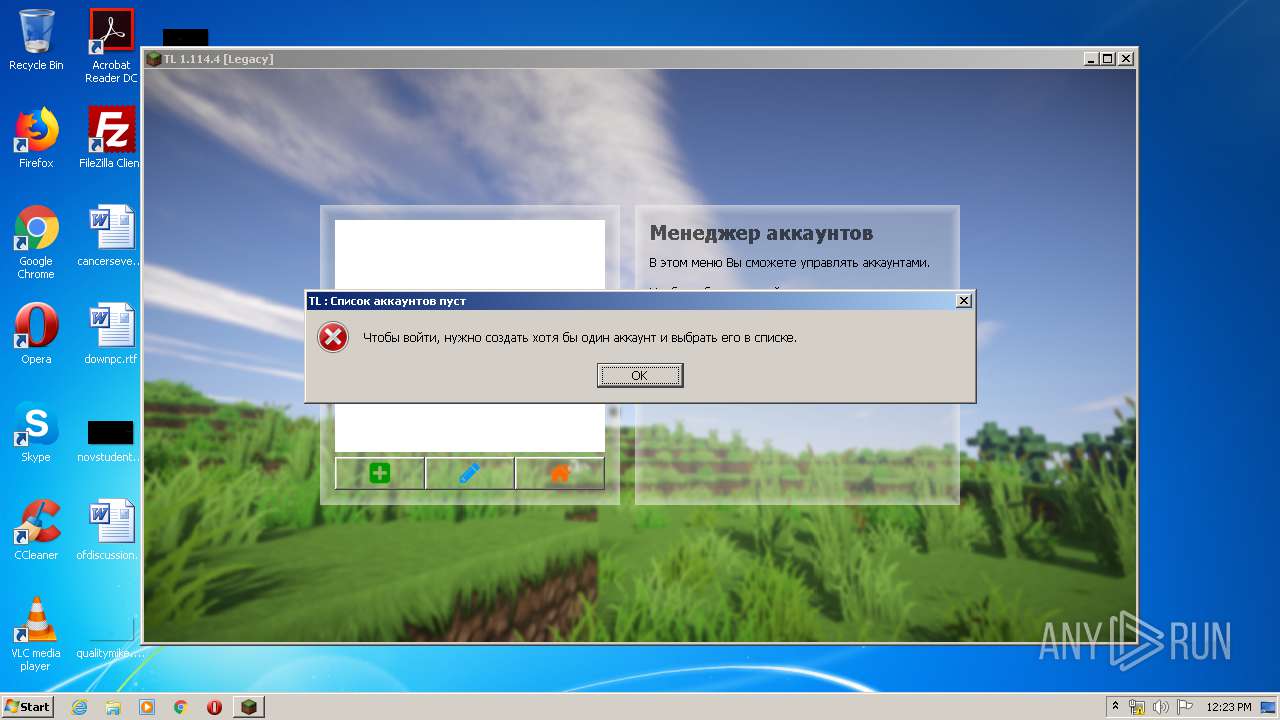
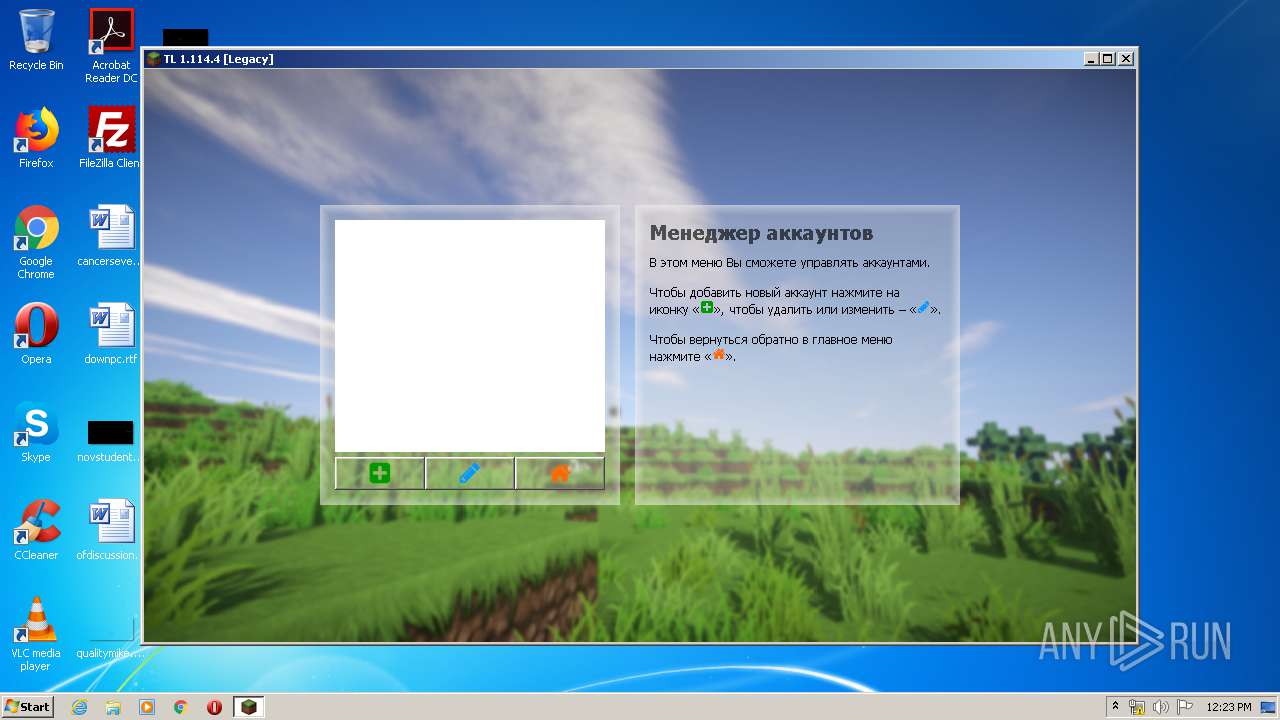
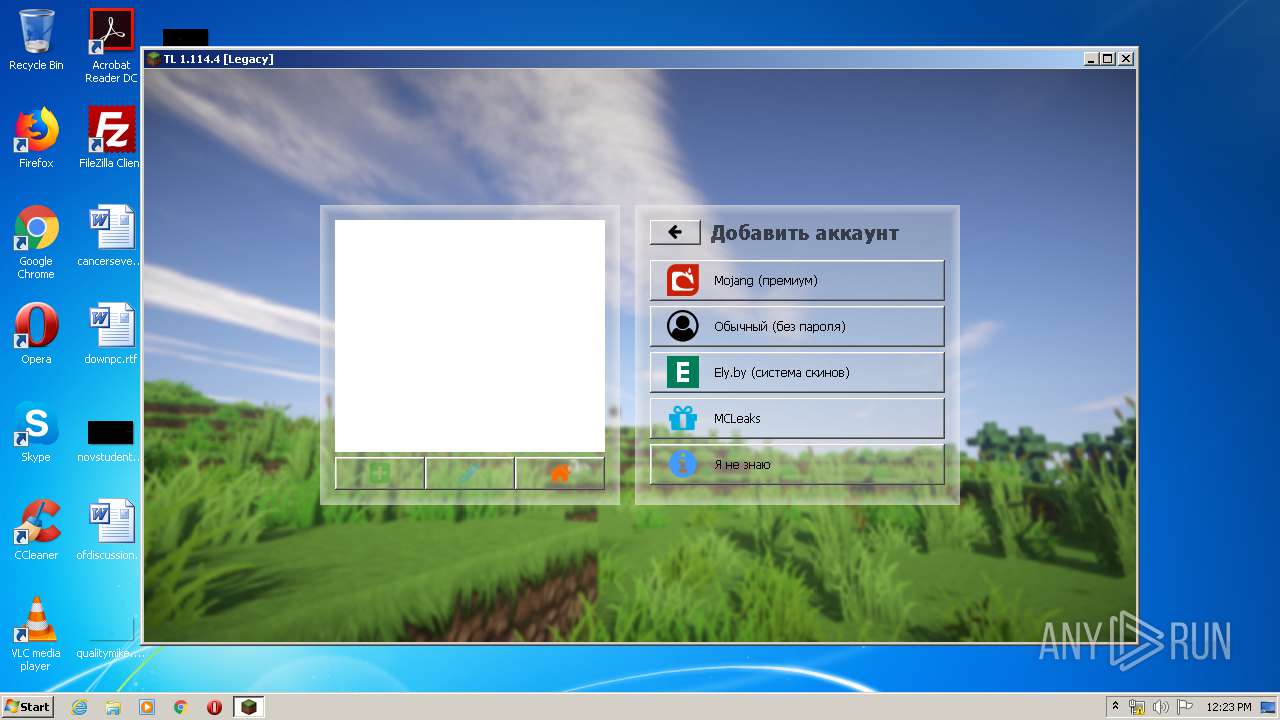
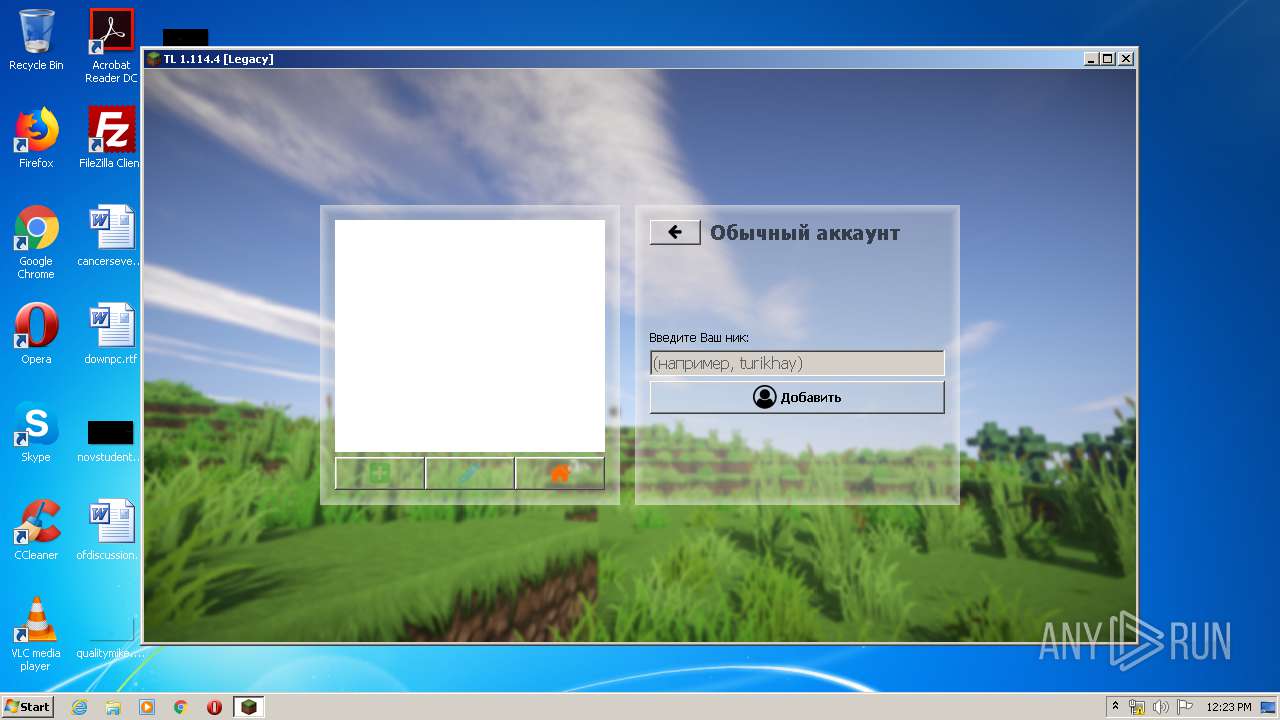
| URL: | https://download-subway-surfers.ru/game/minecraft/skachat-minecraft-na-kompyuter.html |
| Full analysis: | https://app.any.run/tasks/28caa85b-e3d3-479d-b68a-639b7e1d09e3 |
| Verdict: | Malicious activity |
| Analysis date: | May 08, 2020, 11:19:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 42092467F0531F3F2836852225122052 |
| SHA1: | 01A6B8FE2D683DA0F100FC05578D13AD6EAA63ED |
| SHA256: | 239181016E010568B4F0293693DFD56B5958E5789167C4AF19D853A0B3BFBE03 |
| SSDEEP: | 3:N8SEmWQH7jqHsKvN8GUhISV0IJ:2SYQHyMKvNkeSVP |
MALICIOUS
Application was dropped or rewritten from another process
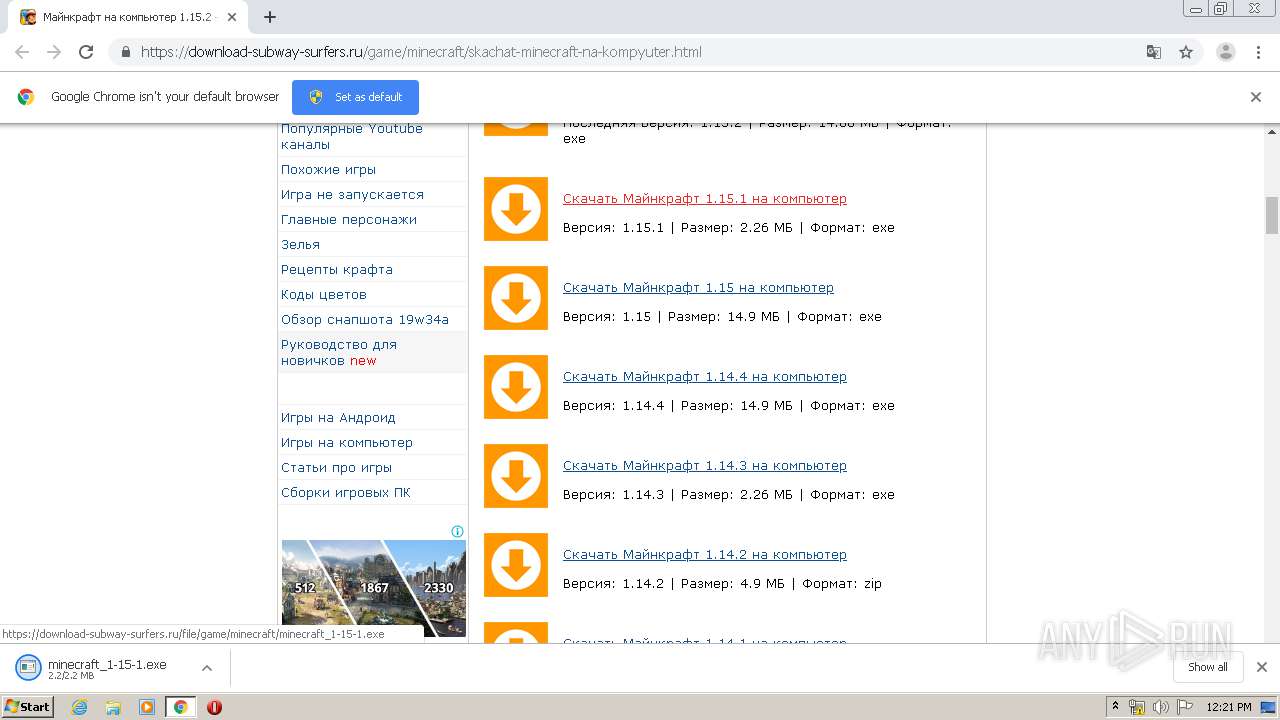
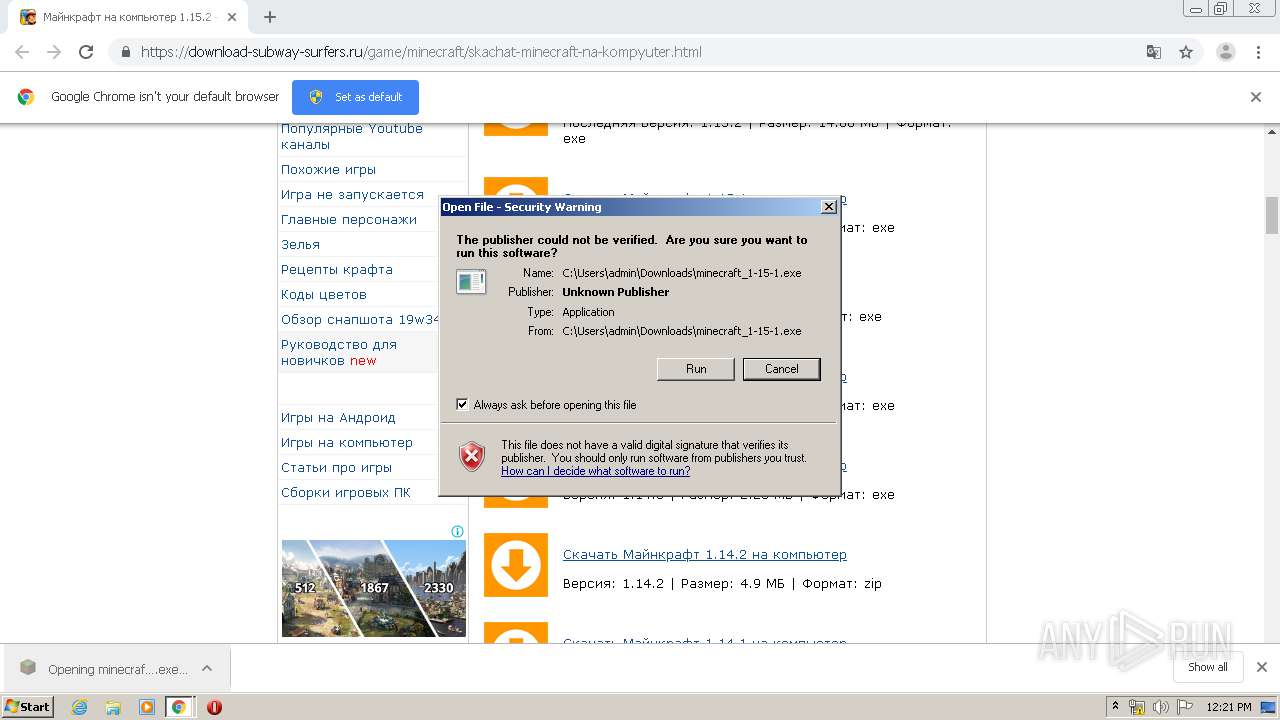
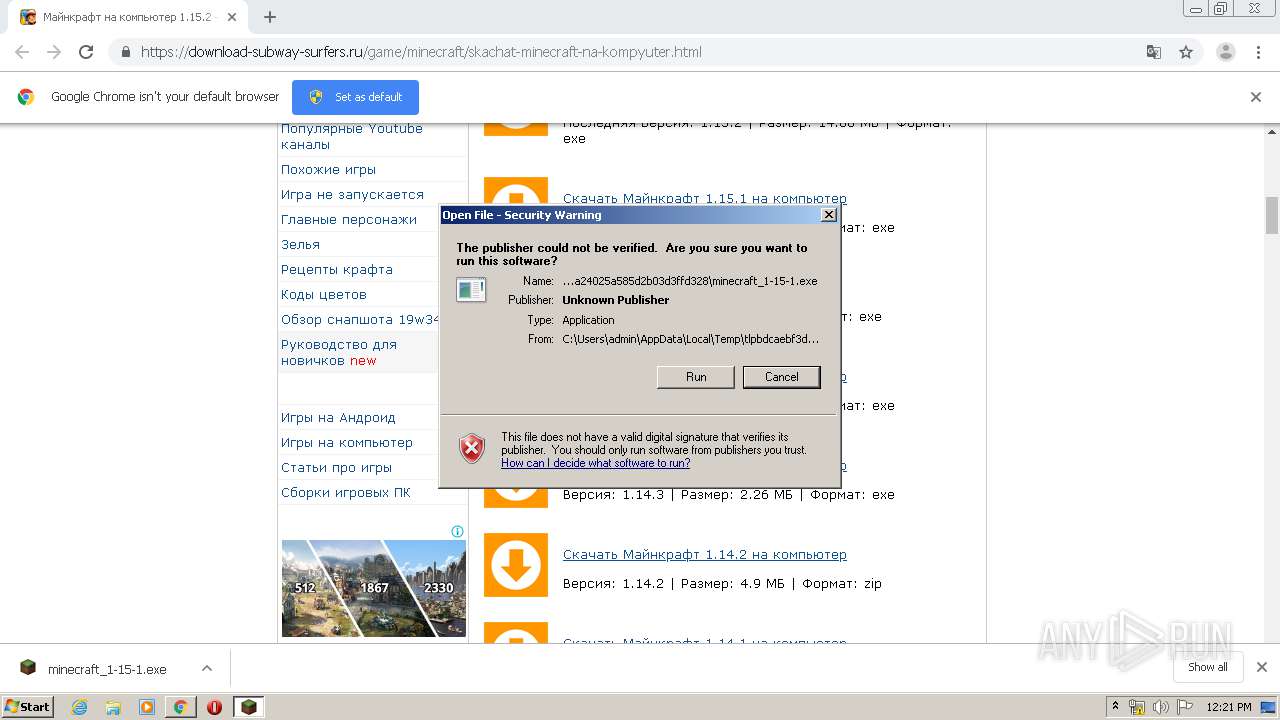
- minecraft_1-15-1.exe (PID: 3072)
- minecraft_1-15-1.exe (PID: 3884)
- javaw.exe (PID: 1792)
- javaw.exe (PID: 3276)
Loads dropped or rewritten executable
- javaw.exe (PID: 1792)
- minecraft_1-15-1.exe (PID: 3884)
- javaw.exe (PID: 3276)
Actions looks like stealing of personal data
- javaw.exe (PID: 3276)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 440)
Executable content was dropped or overwritten
- chrome.exe (PID: 440)
- chrome.exe (PID: 3092)
- minecraft_1-15-1.exe (PID: 3072)
- minecraft_1-15-1.exe (PID: 3884)
Starts itself from another location
- minecraft_1-15-1.exe (PID: 3072)
Reads Environment values
- minecraft_1-15-1.exe (PID: 3884)
Creates files in the program directory
- javaw.exe (PID: 1792)
Uses ICACLS.EXE to modify access control list
- javaw.exe (PID: 1792)
Starts application with an unusual extension
- javaw.exe (PID: 3276)
Executes scripts
- cmd.exe (PID: 3860)
Creates files in the user directory
- minecraft_1-15-1.exe (PID: 3884)
- javaw.exe (PID: 3276)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 3276)
INFO
Reads the hosts file
- chrome.exe (PID: 440)
- chrome.exe (PID: 3092)
Application launched itself
- chrome.exe (PID: 440)
Reads Internet Cache Settings
- chrome.exe (PID: 440)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 3092)
- javaw.exe (PID: 3276)
Reads settings of System Certificates
- minecraft_1-15-1.exe (PID: 3884)
- chrome.exe (PID: 3092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
86
Monitored processes
40
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "https://download-subway-surfers.ru/game/minecraft/skachat-minecraft-na-kompyuter.html" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,12754365783303283576,4879310694962724411,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17426277539784592149 --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3680 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,12754365783303283576,4879310694962724411,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7380478368670245555 --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3632 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 848 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1036,12754365783303283576,4879310694962724411,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7106852918822648081 --mojo-platform-channel-handle=4796 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 872 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1036,12754365783303283576,4879310694962724411,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=4019287114455621050 --mojo-platform-channel-handle=4016 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 984 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1036,12754365783303283576,4879310694962724411,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=3292786029283855085 --mojo-platform-channel-handle=4992 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1672 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,12754365783303283576,4879310694962724411,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9173819264081042146 --renderer-client-id=9 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3708 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1792 | "C:\Users\admin\AppData\Roaming\.tlauncher\jre\win86\bin\javaw.exe" -version | C:\Users\admin\AppData\Roaming\.tlauncher\jre\win86\bin\javaw.exe | — | minecraft_1-15-1.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1810.13 Modules
| |||||||||||||||
| 1812 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1036,12754365783303283576,4879310694962724411,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6687481105360613565 --mojo-platform-channel-handle=4884 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1852 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1036,12754365783303283576,4879310694962724411,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6632129596565956206 --mojo-platform-channel-handle=4808 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 885
Read events
1 747
Write events
133
Delete events
5
Modification events
| (PID) Process: | (440) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (440) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (440) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (440) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (440) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3232) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 440-13233410399887750 |
Value: 259 | |||
| (PID) Process: | (440) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (440) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (440) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3120-13213713943555664 |
Value: 0 | |||
| (PID) Process: | (440) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
174
Suspicious files
187
Text files
480
Unknown types
507
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5EB54060-1B8.pma | — | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | — | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\a4b9df57-3a0a-467d-8a7a-bdcdbd76bce5.tmp | — | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000028.dbtmp | — | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFa873c7.TMP | text | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 440 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFa875bb.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
166
DNS requests
90
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
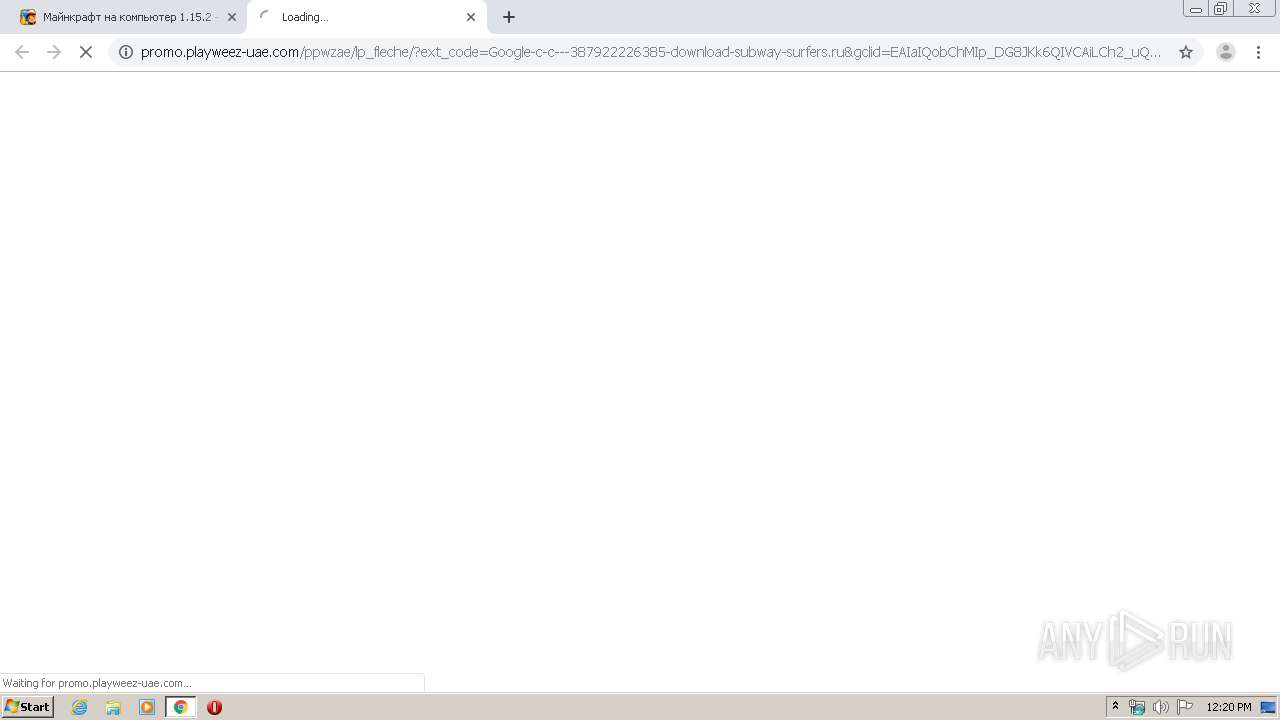
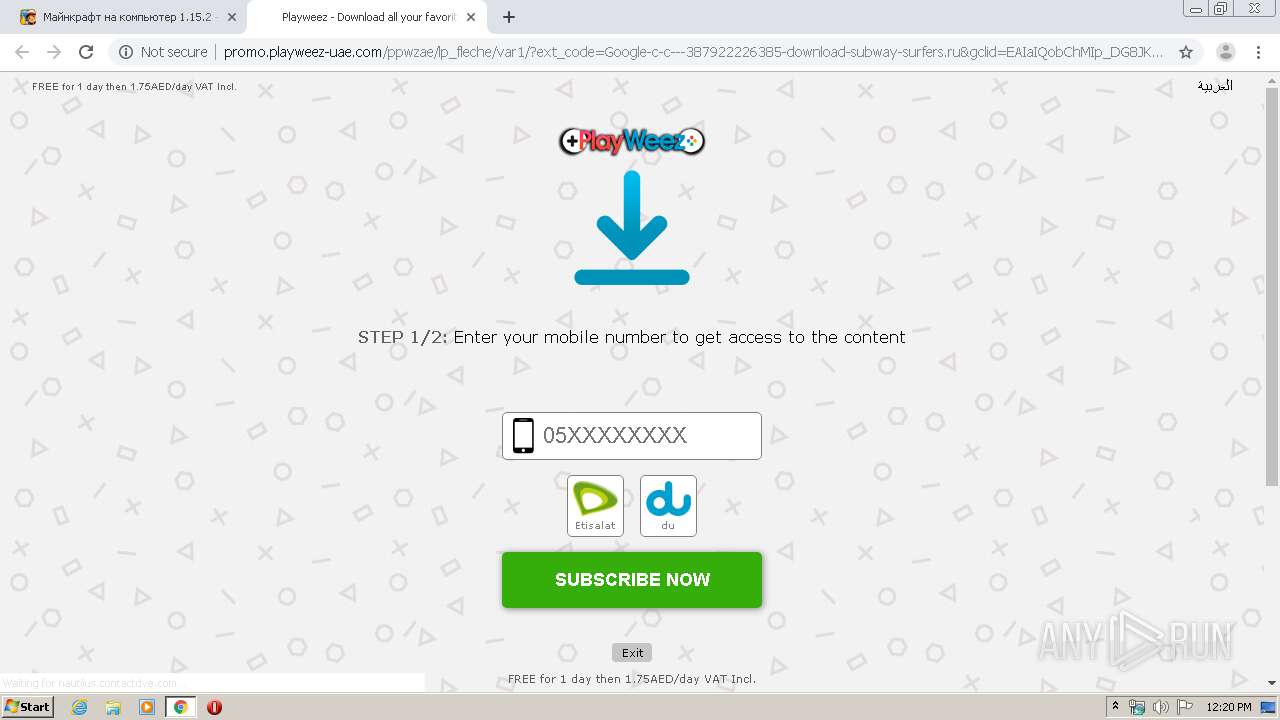
3092 | chrome.exe | GET | 302 | 34.250.182.35:80 | http://billing.virgopass.com/enrichment.php?service=enrichment&rid=64cf130a-99a0-44ed-8ac9-6600f5fa808c&Status=Error&Msisdn=&OperatorCode=&OrderId=64cf130a-99a0-44ed-8ac9-6600f5fa808c&Details=Failed+To+Get+MSISDN&Signature=ZhI9mnrAhwtxHvtSvA8y%3a4646fd6a5191f5b70871086ea63d0e60f62354e3502789b8d896db2b9cbc6a1d&SessionToken=Cz4zVRPvEaQVlMi4JjB9g | IE | — | — | unknown |
3092 | chrome.exe | GET | 302 | 41.178.51.21:80 | http://lookup.tpay.me/idxml.ashx/getmsisdn?redirectUrl=http%3A%2F%2Fbilling.virgopass.com%2Fenrichment.php%3Fservice%3Denrichment%26rid%3D64cf130a-99a0-44ed-8ac9-6600f5fa808c&date=2020-05-08+11%3A20%3A40Z&autoRedirect=true&orderId=64cf130a-99a0-44ed-8ac9-6600f5fa808c&signature=ZhI9mnrAhwtxHvtSvA8y%3Ab877304d609bc5f81ba3127220cdbcb345695cb9bb0c8872799bf8359aaf54cd | EG | — | — | unknown |
3092 | chrome.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ2xvBYPgmu%2FP%2FmXiVKe%2BjES00TfwQU78EqlQwy2vtzMNyKE9gVS%2FcT6PgCEG8uQSIolB1kqNt7vj9%2B2M4%3D | US | der | 278 b | whitelisted |
3092 | chrome.exe | GET | 200 | 13.224.186.35:80 | http://dszxbe84pigtp.cloudfront.net/nautilus/templates/AE/ppwzae/files/lp_fleche/download.png | US | image | 2.33 Kb | whitelisted |
3092 | chrome.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.trust-provider.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEHbYt4bR81JP7pU%2BcUA9mdU%3D | US | der | 471 b | whitelisted |
3092 | chrome.exe | GET | 302 | 172.217.21.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 521 b | whitelisted |
3092 | chrome.exe | GET | 200 | 173.194.183.103:80 | http://r2---sn-aigl6nek.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjY5QUFXTEQwc2RPVXhRY3picjhxblh1dw/7619.603.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mh=Qx&mip=185.217.117.152&mm=28&mn=sn-aigl6nek&ms=nvh&mt=1588936703&mv=m&mvi=1&pl=24&shardbypass=yes | US | crx | 816 Kb | whitelisted |
3092 | chrome.exe | GET | 200 | 13.224.186.35:80 | http://dszxbe84pigtp.cloudfront.net/nautilus/templates/AE/ppwzae/files/lp_fleche/Joystick2.png | US | image | 2.06 Kb | whitelisted |
3092 | chrome.exe | GET | 302 | 172.217.21.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjY5QUFXTEQwc2RPVXhRY3picjhxblh1dw/7619.603.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 526 b | whitelisted |
3092 | chrome.exe | GET | 200 | 13.225.87.18:80 | http://nautilus.contactdve.com/scripts/nautilayer.js | US | text | 43 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3092 | chrome.exe | 216.58.205.227:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3092 | chrome.exe | 37.140.192.22:443 | download-subway-surfers.ru | Domain names registrar REG.RU, Ltd | RU | malicious |
3092 | chrome.exe | 172.217.16.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
3092 | chrome.exe | 87.240.139.194:443 | clientservices.googleapis.com | VKontakte Ltd | RU | suspicious |
3092 | chrome.exe | 172.217.22.2:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
3092 | chrome.exe | 151.139.128.14:80 | ocsp.trust-provider.com | Highwinds Network Group, Inc. | US | suspicious |
3092 | chrome.exe | 216.58.206.2:443 | www.googletagservices.com | Google Inc. | US | whitelisted |
3092 | chrome.exe | 172.217.18.161:443 | tpc.googlesyndication.com | Google Inc. | US | whitelisted |
3092 | chrome.exe | 172.217.16.132:443 | www.google.com | Google Inc. | US | whitelisted |
3092 | chrome.exe | 216.58.212.142:443 | www.youtube.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download-subway-surfers.ru |
| suspicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
vk.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
top-fwz1.mail.ru |
| whitelisted |
adservice.google.ae |
| whitelisted |
adservice.google.com |
| whitelisted |
partner.googleadservices.com |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3276 | javaw.exe | A Network Trojan was detected | ET INFO JAVA - Java Archive Download |
3276 | javaw.exe | A Network Trojan was detected | ET INFO JAVA - Java Archive Download |
3276 | javaw.exe | A Network Trojan was detected | ET INFO JAVA - Java Archive Download |
3276 | javaw.exe | A Network Trojan was detected | ET INFO JAVA - Java Archive Download |
3276 | javaw.exe | A Network Trojan was detected | ET INFO JAVA - Java Archive Download |
3276 | javaw.exe | A Network Trojan was detected | ET INFO JAVA - Java Archive Download |
3276 | javaw.exe | A Network Trojan was detected | ET INFO JAVA - Java Archive Download |
3276 | javaw.exe | A Network Trojan was detected | ET INFO JAVA - Java Archive Download |
3276 | javaw.exe | A Network Trojan was detected | ET INFO JAVA - Java Archive Download |
3276 | javaw.exe | A Network Trojan was detected | ET INFO JAVA - Java Archive Download |
1 ETPRO signatures available at the full report