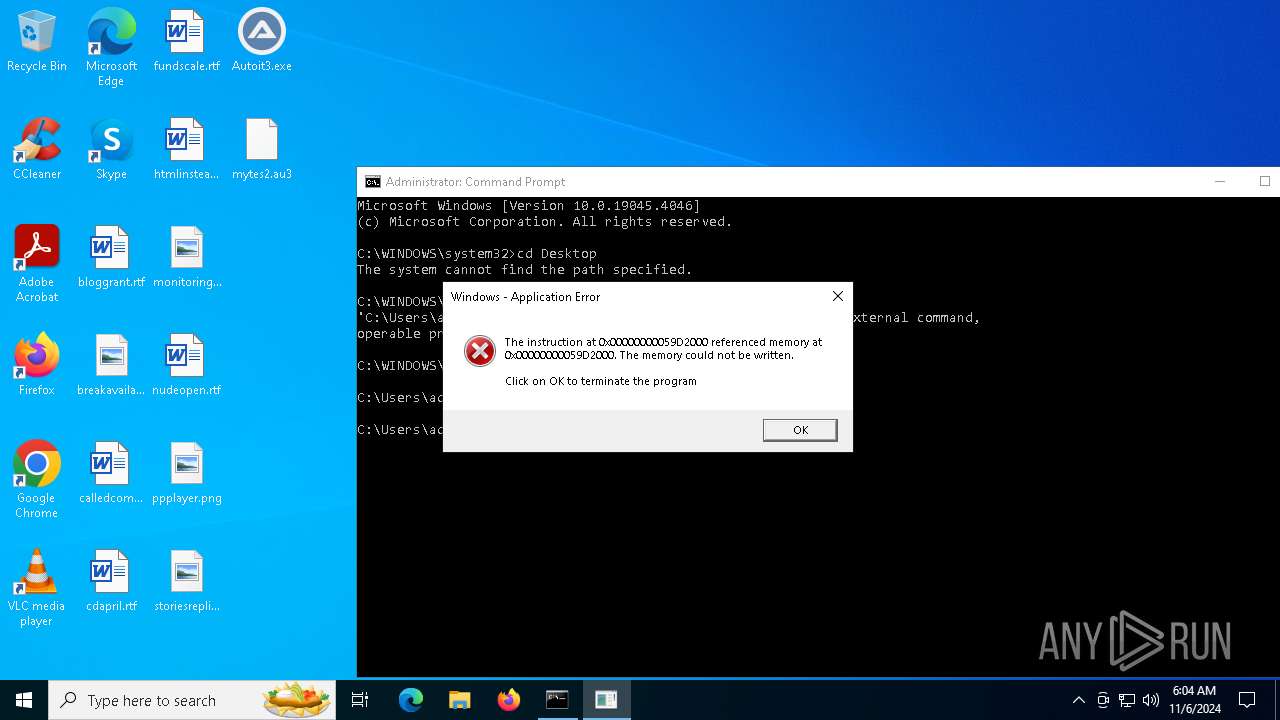
| File name: | Autoit3.exe |
| Full analysis: | https://app.any.run/tasks/cdc6b6aa-e7c8-4894-b2b9-e3bd1481e23a |
| Verdict: | Malicious activity |
| Threats: | DarkGate is a loader, which possesses extensive functionality, ranging from keylogging to crypto mining. Written in Delphi, this malware is known for the use of AutoIT scripts in its infection process. Thanks to this malicious software’s versatile architecture, it is widely used by established threat actors. |
| Analysis date: | November 06, 2024, 06:01:54 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | C56B5F0201A3B3DE53E561FE76912BFD |
| SHA1: | 2A4062E10A5DE813F5688221DBEB3F3FF33EB417 |
| SHA256: | 237D1BCA6E056DF5BB16A1216A434634109478F882D3B1D58344C801D184F95D |
| SSDEEP: | 12288:6pVWeOV7GtINsegA/hMyyzlcqikvAfcN9b2MyZa31twoPTdFxgawV2M01:6T3E53Myyzl0hMf1tr7Caw8M01 |
MALICIOUS
Runs injected code in another process
- Autoit3.exe (PID: 6420)
- MicrosoftEdgeUpdateCore.exe (PID: 4040)
Application was injected by another process
- MicrosoftEdgeUpdateCore.exe (PID: 3156)
- MicrosoftEdgeUpdateCore.exe (PID: 6868)
DARKGATE has been detected (YARA)
- MicrosoftEdgeUpdateCore.exe (PID: 7072)
- MicrosoftEdgeUpdateCore.exe (PID: 4040)
Changes the autorun value in the registry
- MicrosoftEdgeUpdateCore.exe (PID: 4040)
SUSPICIOUS
Reads security settings of Internet Explorer
- Autoit3.exe (PID: 6216)
The process verifies whether the antivirus software is installed
- Autoit3.exe (PID: 6420)
- MicrosoftEdgeUpdateCore.exe (PID: 4040)
Starts CMD.EXE for commands execution
- Autoit3.exe (PID: 6420)
Executable content was dropped or overwritten
- Autoit3.exe (PID: 6420)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 6808)
Accesses domain name via WMI (SCRIPT)
- WMIC.exe (PID: 5276)
Application launched itself
- MicrosoftEdgeUpdateCore.exe (PID: 4040)
Executes application which crashes
- MicrosoftEdgeUpdateCore.exe (PID: 6868)
INFO
Reads mouse settings
- Autoit3.exe (PID: 6216)
- Autoit3.exe (PID: 6420)
Checks supported languages
- Autoit3.exe (PID: 6216)
- Autoit3.exe (PID: 6420)
- MicrosoftEdgeUpdateCore.exe (PID: 4040)
- MicrosoftEdgeUpdateCore.exe (PID: 6868)
Reads the computer name
- Autoit3.exe (PID: 6216)
- MicrosoftEdgeUpdateCore.exe (PID: 4040)
- Autoit3.exe (PID: 6420)
Reads Windows Product ID
- Autoit3.exe (PID: 6420)
- MicrosoftEdgeUpdateCore.exe (PID: 4040)
Creates files or folders in the user directory
- Autoit3.exe (PID: 6420)
Manual execution by a user
- cmd.exe (PID: 3852)
Reads CPU info
- Autoit3.exe (PID: 6420)
- MicrosoftEdgeUpdateCore.exe (PID: 4040)
Creates files in the program directory
- Autoit3.exe (PID: 6420)
- cmd.exe (PID: 6808)
- MicrosoftEdgeUpdateCore.exe (PID: 4040)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 5276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:03:15 13:14:39+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 583680 |
| InitializedDataSize: | 317440 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x27ffa |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.3.14.5 |
| ProductVersionNumber: | 3.3.14.5 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| CompanyName: | AutoIt Team |
| Comments: | http://www.autoitscript.com/autoit3/ |
| FileDescription: | AutoIt v3 Script |
| FileVersion: | 3, 3, 14, 5 |
| InternalName: | AutoIt3.exe |
| LegalCopyright: | ©1999-2018 Jonathan Bennett & AutoIt Team |
| OriginalFileName: | AutoIt3.exe |
| ProductName: | AutoIt v3 Script |
| ProductVersion: | 3, 3, 14, 5 |
Total processes
147
Monitored processes
12
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3156 | "C:\Program Files (x86)\Microsoft\EdgeUpdate\1.3.185.17\MicrosoftEdgeUpdateCore.exe" | C:\Program Files (x86)\Microsoft\EdgeUpdate\1.3.185.17\MicrosoftEdgeUpdateCore.exe | SystemSettings.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Version: 1.3.185.17 | |||||||||||||||
| 3852 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | C:\Program Files (x86)\Microsoft\EdgeUpdate\1.3.185.17\MicrosoftEdgeUpdateCore.exe | C:\Program Files (x86)\Microsoft\EdgeUpdate\1.3.185.17\MicrosoftEdgeUpdateCore.exe | Autoit3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Update Version: 1.3.185.17 Modules
| |||||||||||||||
| 5160 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5276 | wmic ComputerSystem get domain | C:\Windows\SysWOW64\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6216 | "C:\Users\admin\Desktop\Autoit3.exe" | C:\Users\admin\Desktop\Autoit3.exe | — | explorer.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 1 Version: 3, 3, 14, 5 Modules
| |||||||||||||||
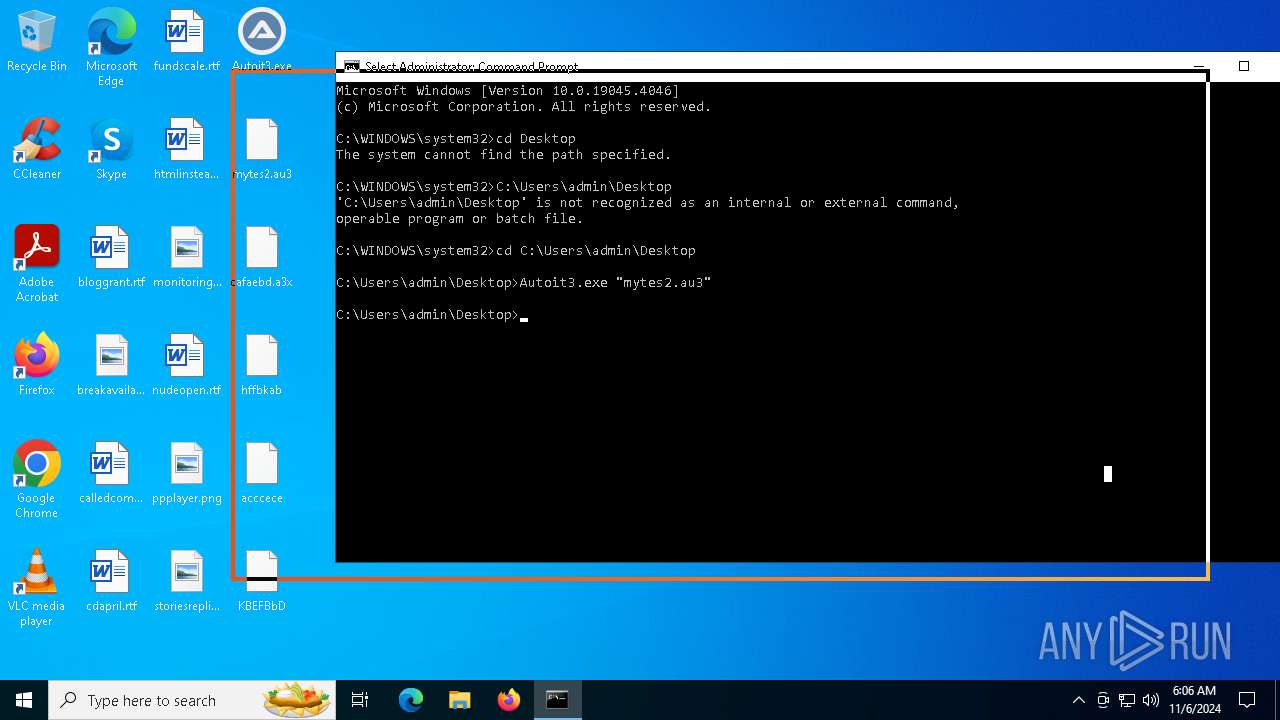
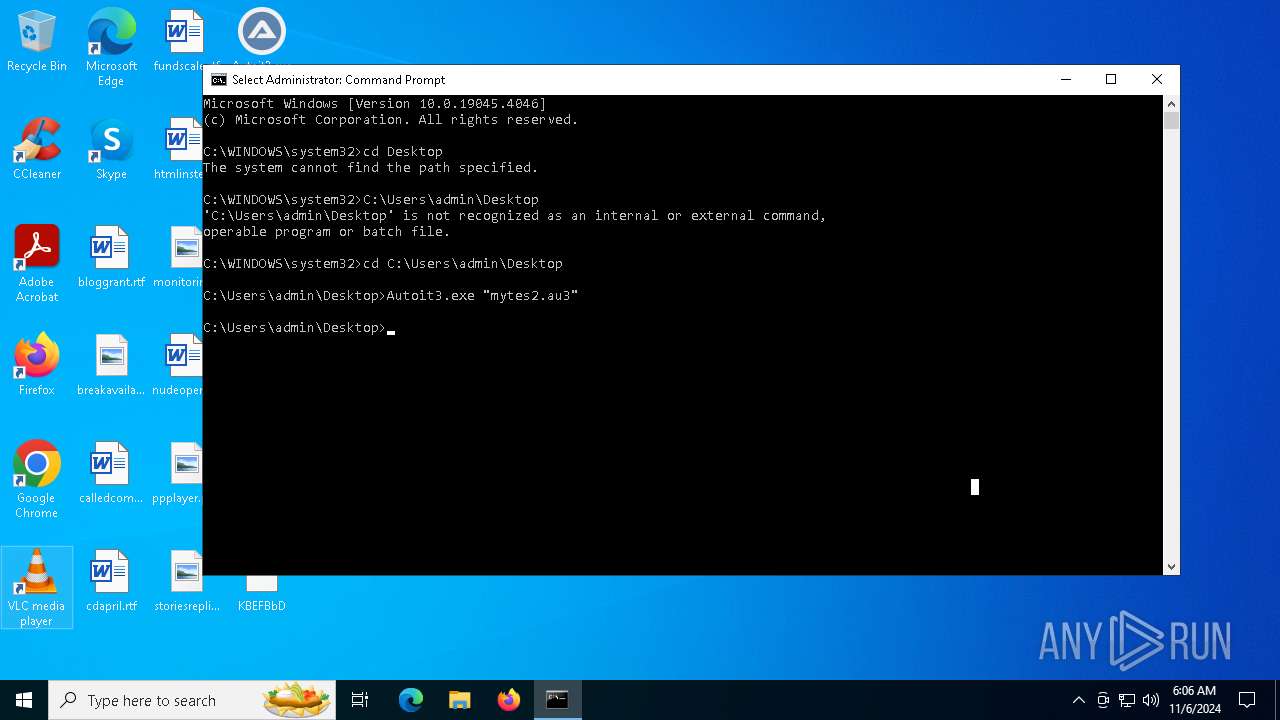
| 6420 | Autoit3.exe "mytes2.au3" | C:\Users\admin\Desktop\Autoit3.exe | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: HIGH Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 5 Modules
| |||||||||||||||
| 6724 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6808 | "c:\windows\system32\cmd.exe" /c wmic ComputerSystem get domain > C:\ProgramData\bfdaebh\efkfaae | C:\Windows\SysWOW64\cmd.exe | — | Autoit3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 437
Read events
4 402
Write events
34
Delete events
1
Modification events
| (PID) Process: | (6216) Autoit3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (6216) Autoit3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0400000000000000030000000E000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (6216) Autoit3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000000000005000000020000000100000003000000FFFFFFFF | |||
| (PID) Process: | (6216) Autoit3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (6216) Autoit3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 96 | |||
| (PID) Process: | (6216) Autoit3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (6216) Autoit3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (6216) Autoit3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | FFlags |
Value: | |||
| (PID) Process: | (6216) Autoit3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | IconSize |
Value: 16 | |||
| (PID) Process: | (6216) Autoit3.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\ComDlg\{7D49D726-3C21-4F05-99AA-FDC2C9474656} |
| Operation: | write | Name: | Sort |
Value: 000000000000000000000000000000000100000030F125B7EF471A10A5F102608C9EEBAC0A00000001000000 | |||
Executable files
1
Suspicious files
2
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6420 | Autoit3.exe | C:\ProgramData\bfdaebh\dbekkea.a3x | binary | |
MD5:D91891CAE02A24735853100A3511D74F | SHA256:E2C3B31EE3615E2F39843D035F1990B94C12AF1E42C34CE8E83C28B29C85567D | |||
| 6420 | Autoit3.exe | C:\ProgramData\bfdaebh\Autoit3.exe | executable | |
MD5:C56B5F0201A3B3DE53E561FE76912BFD | SHA256:237D1BCA6E056DF5BB16A1216A434634109478F882D3B1D58344C801D184F95D | |||
| 6420 | Autoit3.exe | C:\temp\dcbecca | text | |
MD5:44EC85A70133CF280A14031477B639A9 | SHA256:A5BAC4DFD6E677513ACBAB4AFD204E8493071C5AB12A78301A2B5B49865DFD51 | |||
| 6808 | cmd.exe | C:\ProgramData\bfdaebh\efkfaae | text | |
MD5:C8BBAD190EAAA9755C8DFB1573984D81 | SHA256:7F136265128B7175FB67024A6DDD7524586B025725A878C07D76A9D8AD3DC2AC | |||
| 4040 | MicrosoftEdgeUpdateCore.exe | C:\temp\dcbecca | text | |
MD5:FCE0CA06E4AF976FBB275C8B2AB2692E | SHA256:6E2E9179F7875E0975111863689BD9065FD8DABFF478A8B341D461C098766A6C | |||
| 7072 | MicrosoftEdgeUpdateCore.exe | C:\temp\fhbaaca | text | |
MD5:5AFD89ACA4F5249219BACA65FC7F5CE9 | SHA256:6C24A4DEBAB9B253281895741541C57531FD12CB19D5D703B4103125B0968B06 | |||
| 4040 | MicrosoftEdgeUpdateCore.exe | C:\ProgramData\bfdaebh\akfchbd | binary | |
MD5:B2AB4DFC77EA282EE15C03294EE29F30 | SHA256:E2ECABD2CFDE615134629F3F8FAA6C6CEFACE910404F0E74C56353A7091FF04C | |||
| 6420 | Autoit3.exe | C:\Users\admin\AppData\Roaming\KBEFBbD | text | |
MD5:9BAB60CDD690C8D682B97AC173B9856D | SHA256:EF15073CA1C73B7DE554D039579A86A51EFF5B0B00756A7127FCBD55CE96DE55 | |||
| 6420 | Autoit3.exe | C:\temp\fkcbadc | text | |
MD5:35465D086B65E6E300272EC2CC5D160D | SHA256:BB87B4A18476ADB4D14C216A4CEF235BD7025B5A4235A1E21B4E88BE21E95D48 | |||
| 4040 | MicrosoftEdgeUpdateCore.exe | C:\temp\fhbaaca | text | |
MD5:EDA871D51333BF57336E621C4FEFA604 | SHA256:1A8094251D3C2AF331AD47C278F70AD0E5CB72D01A7A5C19093202A657C3B73D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
39
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4836 | RUXIMICS.exe | GET | 200 | 104.85.249.160:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
5488 | MoUsoCoreWorker.exe | GET | 200 | 104.85.249.160:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.200.161.157:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
— | — | POST | — | 62.233.57.80:80 | http://44-35-63-31.internalsakamai.net/ | unknown | — | — | unknown |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
4836 | RUXIMICS.exe | GET | 200 | 23.200.161.157:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | GET | 200 | 23.200.161.157:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
— | — | GET | 200 | 23.200.161.157:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4836 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
5488 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4360 | SearchApp.exe | 2.18.29.177:443 | www.bing.com | Akamai International B.V. | PL | unknown |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | unknown |
5488 | MoUsoCoreWorker.exe | 104.85.249.160:80 | crl.microsoft.com | Akamai International B.V. | PL | unknown |
4836 | RUXIMICS.exe | 104.85.249.160:80 | crl.microsoft.com | Akamai International B.V. | PL | unknown |
5488 | MoUsoCoreWorker.exe | 23.200.161.157:80 | www.microsoft.com | AKAMAI-AS | PL | unknown |
4836 | RUXIMICS.exe | 23.200.161.157:80 | www.microsoft.com | AKAMAI-AS | PL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| unknown |
www.bing.com |
| unknown |
crl.microsoft.com |
| unknown |
ocsp.digicert.com |
| unknown |
google.com |
| unknown |
www.microsoft.com |
| unknown |
r.bing.com |
| unknown |
browser.pipe.aria.microsoft.com |
| unknown |
th.bing.com |
| unknown |
fp.msedge.net |
| unknown |